300-115 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your 300-115 certification exam? Start your preparation the smart way with our 300-115 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for 300-115 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our 300-115 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
On which interface can port security be configured?
A. static trunk ports
B. destination port for SPAN
C. EtherChannel port group
D. dynamic access point
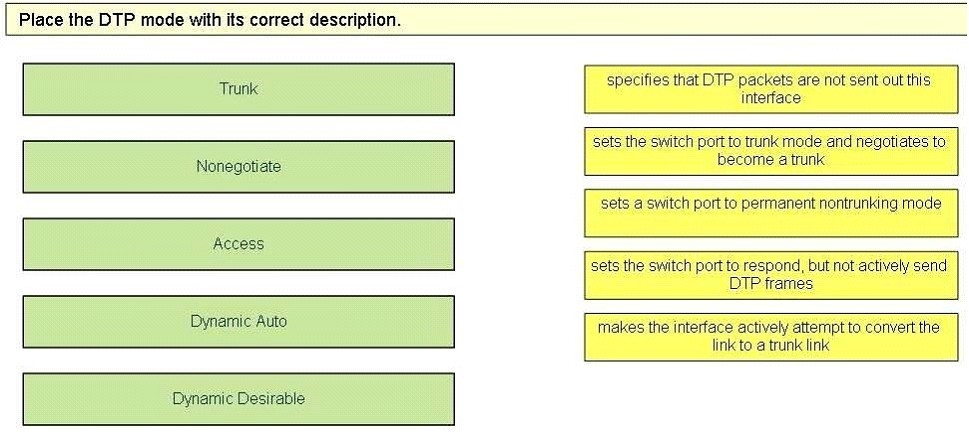
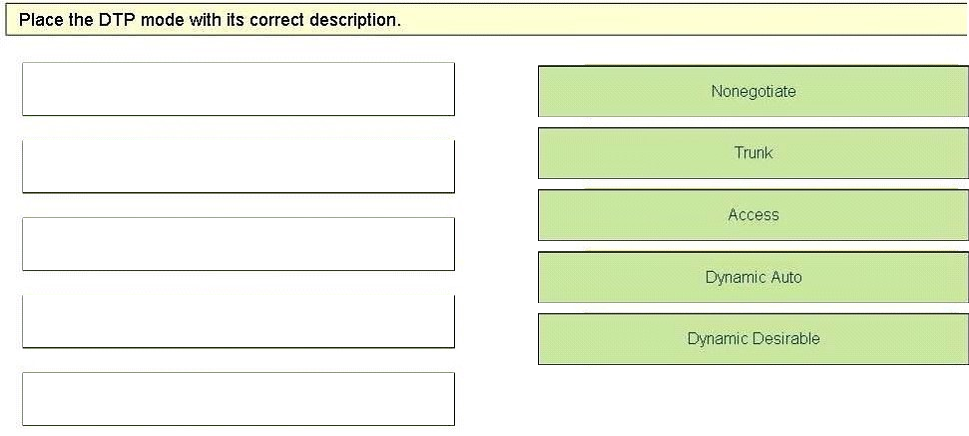
Drag and Drop Question - Select and Place:
You have been asked to install and configure a new switch in a customer network. Use the console access to the existing and new switches to configure and verify correct device configuration.Refer to the configuration. For which configured VLAN are untagged frames sent over trunk between SW1 and SW2?
A. VLAN1
B. VLAN 99
C. VLAN 999
D. VLAN 40
E. VLAN 50
F. VLAN 200
G. VLAN 300
You have been asked to install and configure a new switch in a customer network. Use the console access to the existing and new switches to configure and verify correct device configuration.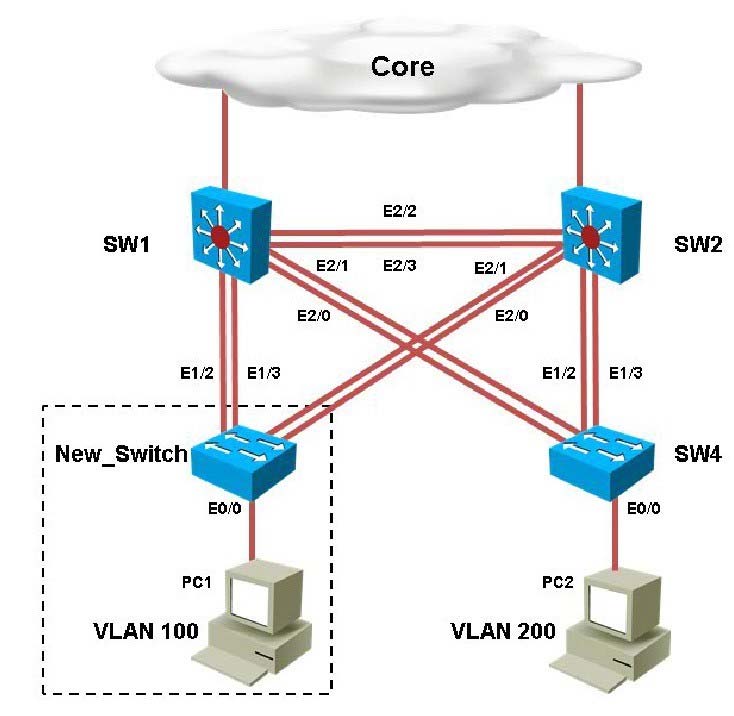


You are connecting the New_Switch to the LAN topology; the switch has been partially configured and you need to complete the rest of configuration to enable PC1 communication with PC2. Which of the configuration is correct?
A. Option A
B. Option B
C. Option C
D. Option D
E. Option E
Your customer has asked you to come in and verify the operation of routers R1 and R2 which are configured to use HSRP. They have questions about how these two devices will perform in the event of a device failure.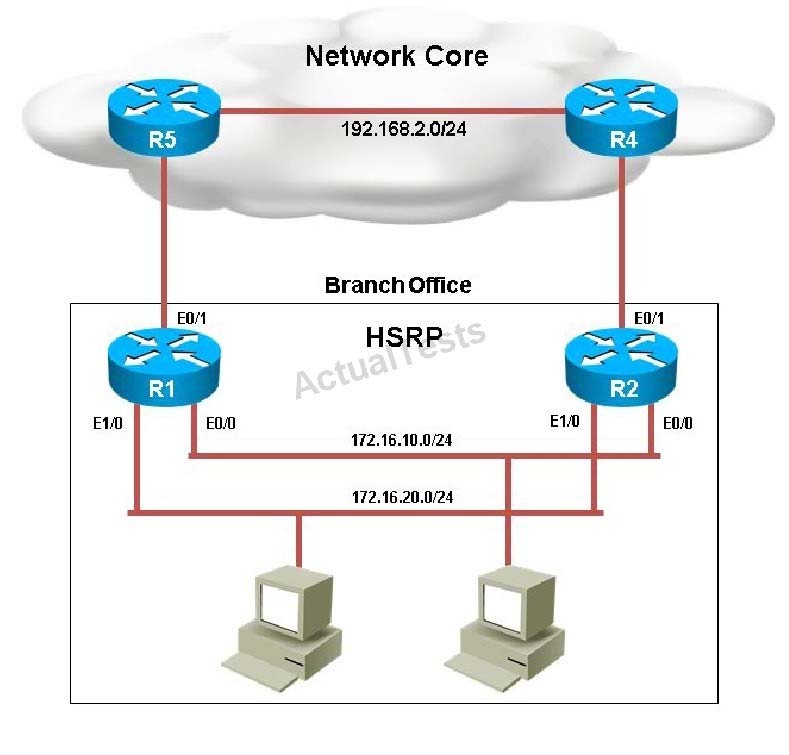
What issue is causing Router R1 and R2 to both be displayed as the HSRP active router for group 2?
A. The HSRP group number mismatch
B. The HSRP group authentication is misconfigured
C. The HSRP Hello packets are blocked
D. The HSRP timers mismatch
E. The HSRP group priorities are different
Which command should you enter to configure a device as an NTP server?
A. ntp server
B. ntp peer
C. ntp master
D. ntp authenticate
What is the maximum number of 10 Gigabit Ethernet connections that can be utilized in an EtherChannel for the virtual switch link?
A. 4
B. 6
C. 8
D. 12
Which device type can act as a client in a system that uses TACACS+?
A. end user wireless device
B. router
C. end user workstation
D. AD server
What is the benefit of UDLD?
A. provides backup for fiber
B. help in preventing loops
C. removes loops
D. determines switch path
You have been asked to install and configure a new switch in a customer network. Use the console access to the existing and new switches to configure and verify correct device configuration.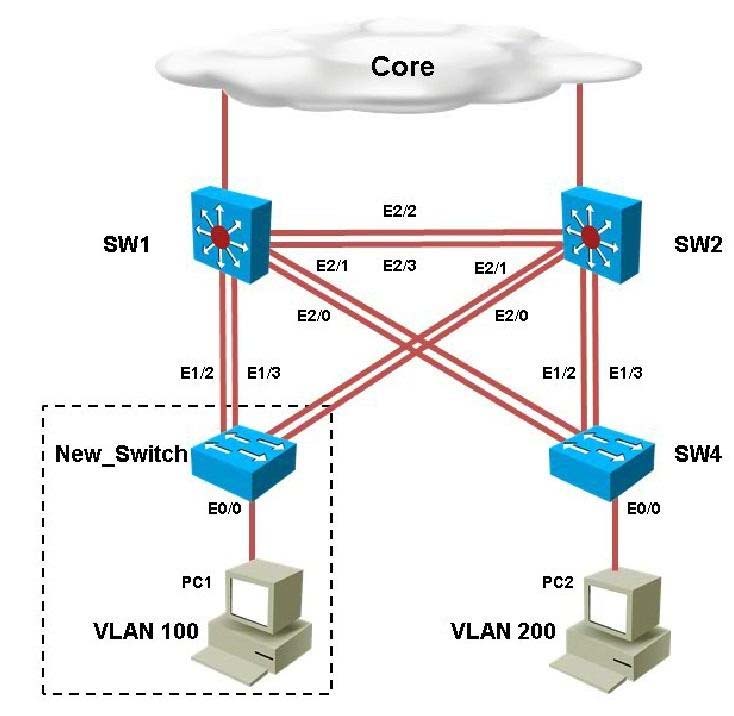

Examine the VTP configuration. You are required to configure private VLANs for a new server deployment connecting to the SW4 switch. Which of the following configuration steps will allow creating private VLANs?
A. Disable VTP pruning on SW1 only
B. Disable VTP pruning on SW2 only
C. Disable VTP pruning on SW4 only
D. Disable VTP pruning on SW2, SW4 and New_Switch
E. Disable VTP pruning on New_Switch and SW4 only.
A network engineer is extending a LAN segment between two geographically separated data centers. Which enhancement to a spanning-tree design prevents unnecessary traffic from crossing the extended LAN segment?
A. Modify the spanning-tree priorities to dictate the traffic flow.
B. Create a Layer 3 transit VLAN to segment the traffic between the sites.
C. Use VTP pruning on the trunk interfaces.
D. Configure manual trunk pruning between the two locations.
How to recover err-disable after an UDLD failure?
A. UDLD reset
B. Err-disable auto recovery
C. Shut and no shutdown (restart)
D. Reboot the switch
E. UDLD recovery
A network engineer is trying to deploy a PC on a network. The engineer observes that when the PC is connected to the network, it takes 30 to 60 seconds for the PC to see any activity on the network interface card. Which Layer 2 enhancement can be used to eliminate this delay?
A. Configure port duplex and speed to auto negotiation.
B. Configure port to duplex full and speed 1000.
C. Configure spanning-tree portfast.
D. Configure no switchport.
Which of the following features does GLBP provide, but not HSRP and VRRP? (Choose all that apply.)
A. Support for single active router
B. Support for automatic load balancing
C. Support for multiple gateways
D. Support for interface tracking
Which two command sequences must you enter on a pair of switches so that they negotiate an EtherChannel using the Cisco proprietary port-aggregation protocol? (Choose two.) A.B.
C.
D.
E.
Instructions: ✑ Enter IOS commands on the device to verify network operation and answer the multiple-choice questions. ✑ THIS TASK DOES NOT REQUIRE DEVICE CONFIGURATION. ✑ Click on R1 and R2 to gain access to the consoles of these devices. No console or enable passwords are required. ✑ To access the multiple-choice questions, click on the numbered boxes on the left of the top panel. ✑ There are four multiple-choice questions with this task. Be sure to answer all four questions before selecting the Next button Scenario: Your customer has asked you to come in and verify the operation of routers R1 and R2 which are configured to use HSRP. They have questions about how these two devices will perform in the event of a device failure. Click on the devices or the tabs at the bottom of the screens to access the CLI to answer their questions.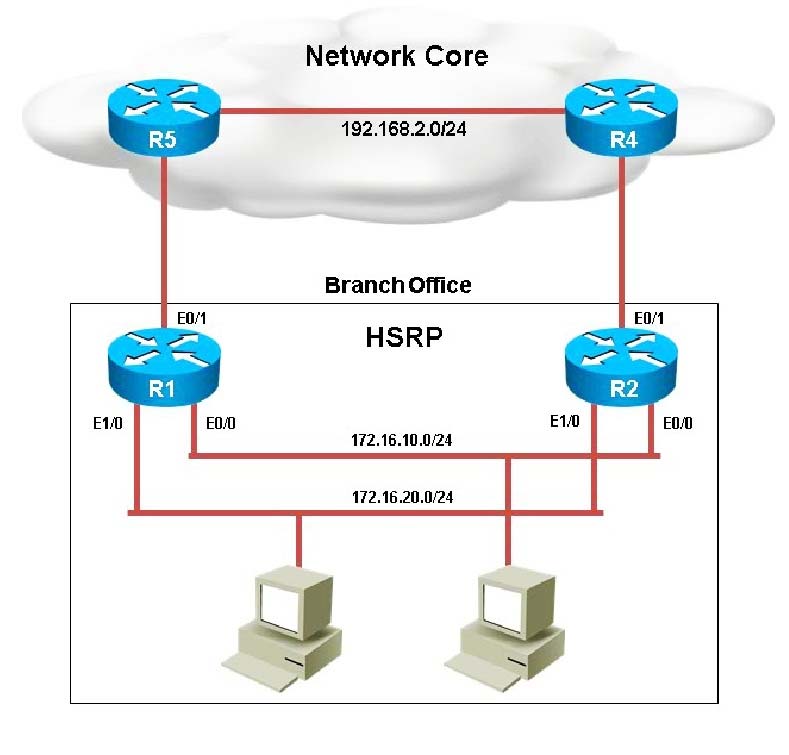
What issue is causing Router R1 and R2 to both be displayed as the HSRP active router for group 2?
A. The HSRP group number mismatch
B. The HSRP group authentication is misconfigured
C. The HSRP Hello packets are blocked
D. The HSRP timers mismatch
E. The HSRP group priorities are different
Your customer has asked you to come in and verify the operation of routers R1 and R2 which are configured to use HSRP. They have questions about how these two devices will perform in the event of a device failure. Click on the devices or the tabs at the bottom of the screens to access the CLI to answer their questions.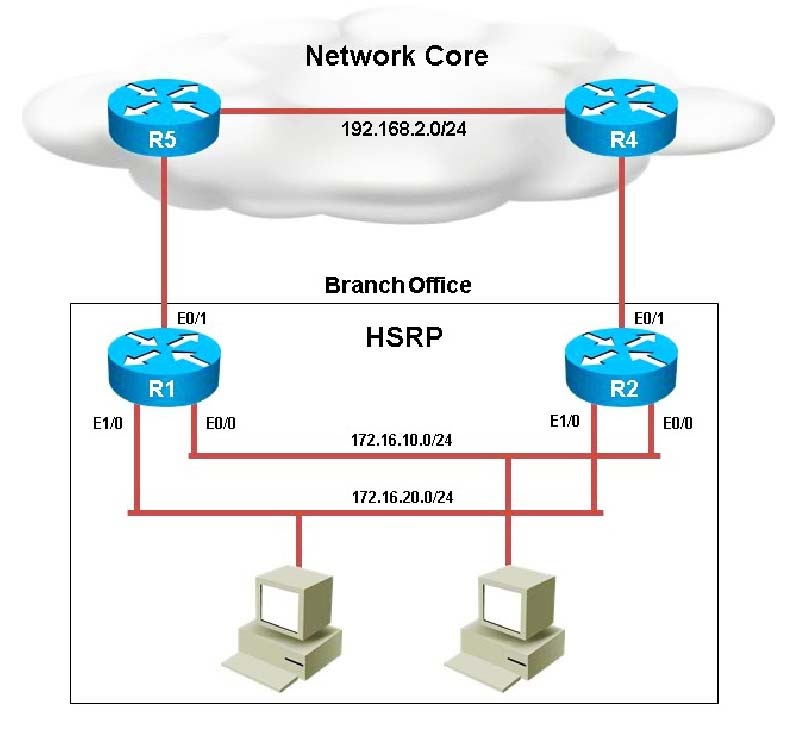
What is the virtual mac-address of HSRP group 1?
A. 0000.0c07.ac02
B. 4000.0000.0010
C. 0000.0c07.ac01
D. 4000.0000.ac01
E. 4000.0000.ac02
F. 0000.0c07.0010
What happens spoofed packet or something like untrusted packet is detected? (Choose three)
A. log
B. deletes
C. intercepts
D. accepts
E. discad
Which two limitations of IP Source Guard are true? (Choose two.)
A. It is supported only on packets switched in hardware.
B. It is supported only on ingress Layer 2 ports.
C. It is supported only on egress Layer 3 ports.
D. It is supported only an PAgP EtherChannels.
E. It is supported only on ingress Layer 3 ports.
Examine the configuration shown below in a partial output of the show run command executed from Router 5.With this configuration, which of the following is true?
A. if POS 1/0 goes down, Router 5 will become the AVG.
B. if POS 1/0 goes down, Router 5 will relinquish its role as AVG.
C. if POS 1/0 and POS 2/0 go down, Router 5 will relinquish its role as AVG.
D. if POS 1/0 and POS 2/0 go down, Router 5 will become the AVG. C
What does the interface subcommand switchport voice vlan 222 indicate?
A. The port is configured for both data and voice traffic.
B. The port is fully dedicated to forwarding voice traffic.
C. The port operates as an FXS telephony port.
D. Voice traffic is directed to VLAN 222.
Instructions - ✑ Enter IOS commands on the device to verify network operation and answer the multiple-choice questions. ✑ THIS TASK DOES NOT REQUIRE DEVICE CONFIGURATION. ✑ Click on SW1, SW2, New_Switch or SW4 to gain access to the consoles of these devices. No console or enable passwords are required. ✑ To access the multiple-choice questions, click on the numbered boxes on the left of the top panel. ✑ There are four multiple-choice questions with this task. Be sure to answer all four questions before selecting the Next button Scenario - You have been asked to install and configure a new switch in a customer network. Use the console access to the existing and new switches to configure and verify correct device configuration. Topology -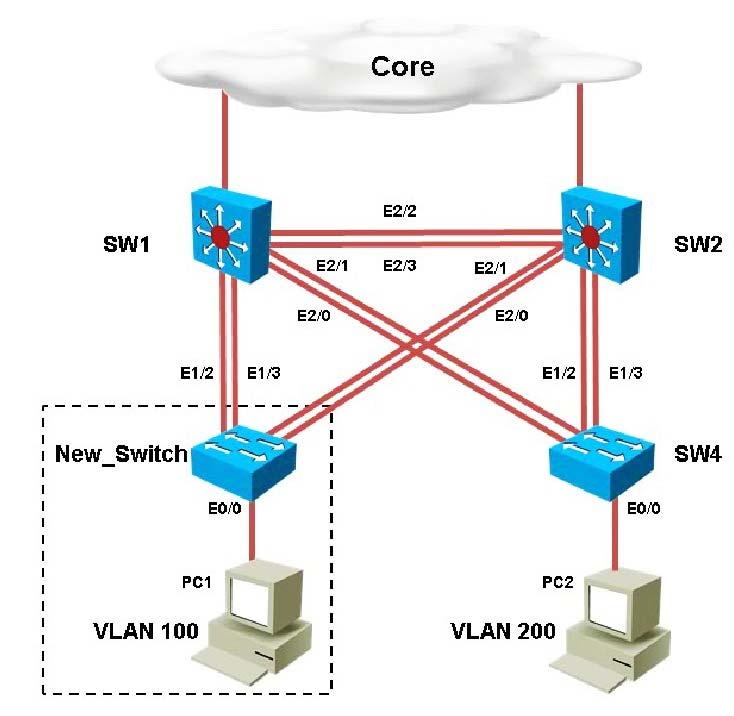


You are adding new VLANs. VLAN500 and VLAN600 to the topology in such way that you need to configure SW1 as primary root for VLAN 500 and secondary for VLAN 600 and SW2 as primary root for VLAN 600 and secondary for VLAN 500. Which configuration step is valid?
A. Configure VLAN 500 & VLAN 600 on both SW1 & SW2
B. Configure VLAN 500 and VLAN 600 on SW1 only
C. Configure VLAN 500 and VLAN 600 on SW2 only
D. Configure VLAN 500 and VLAN 600 on SW1 ,SW2 and SW4
E. On SW2; configure vtp mode as off and configure VLAN 500 and VLAN 600; configure back to vtp server mode.
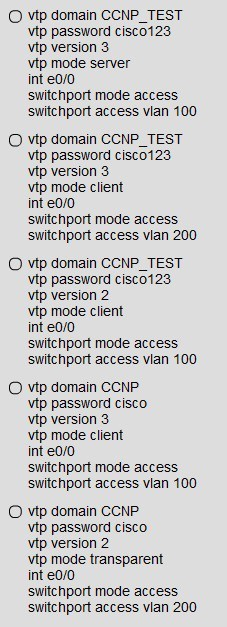
A new network that consists of several switches has been connected together via trunking interfaces. If all switches currently have the default VTP domain name "null", which statement describes what happens when"a do"ain name is configured on one of the switches?
A. The switch with the non-default domain name restores back to “null” upon reboot.
B. Switches with higher revisio” num”ers does not accept the new domain name.
C. VTP summary advertisements are sent out of all ports with the new domain name.
D. All other switches with the default domain name become VTP clients.
Which Cisco StackWise feature is supported?
A. using different SDM templates on each switch
B. using different versions of the Cisco IOS on each switch
C. using mixed software feature set on all members
D. using same software feature set on all members
Which feature rate-limits DHCP traffic?
A. DHCP Snooping
B. DHCP Acknowledge
C. DHCP Request
D. DHCP Spoofing
Your customer has asked you to come in and verify the operation of routers R1 and R2 which are configured to use HSRP. They have questions about how these two devices will perform in the event of a device failure.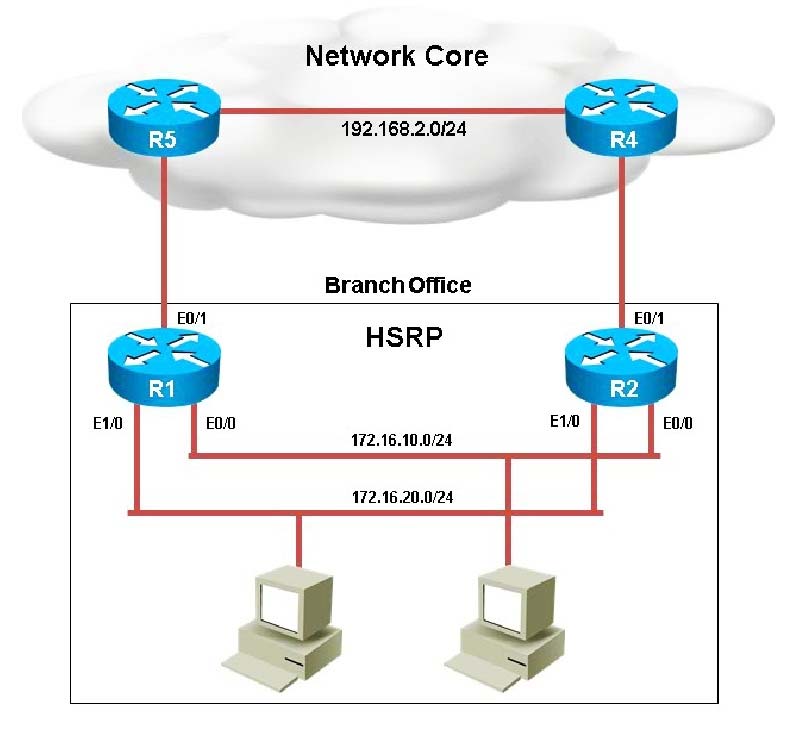
What is the virtual mac-address of HSRP group 1?
A. 0000.0c07.ac02
B. 4000.0000.0010
C. 0000.0c07.ac01
D. 4000.0000.ac01
E. 4000.0000.ac02
F. 0000.0c07.0010
If VLAN 99 is set to trunk, how can you set it to untagged from trunk VLAN 99?
A. switchport access vlan 99
B. switchport vlan 99 access
C. switchport vlan 99 allow access
D. switchport allow access vlan 99
What Cisco switch features are designed to work together to mitigate ARP spoofing attacks? (Choose two.)
A. DHCP snooping
B. port security
C. 802.1x
D. DAI
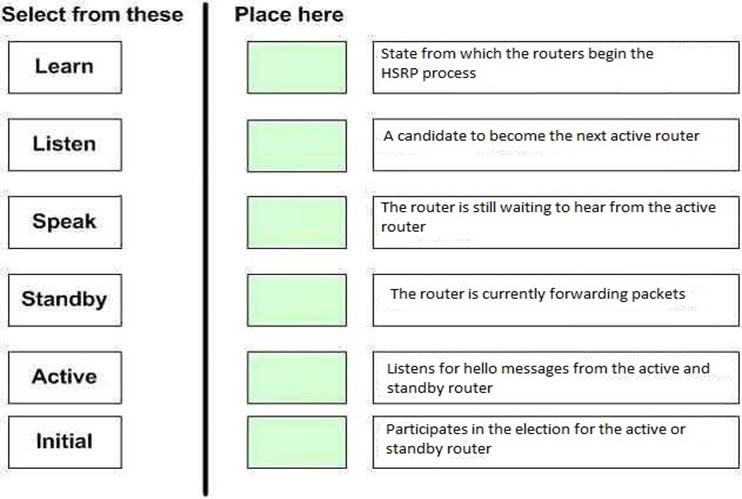
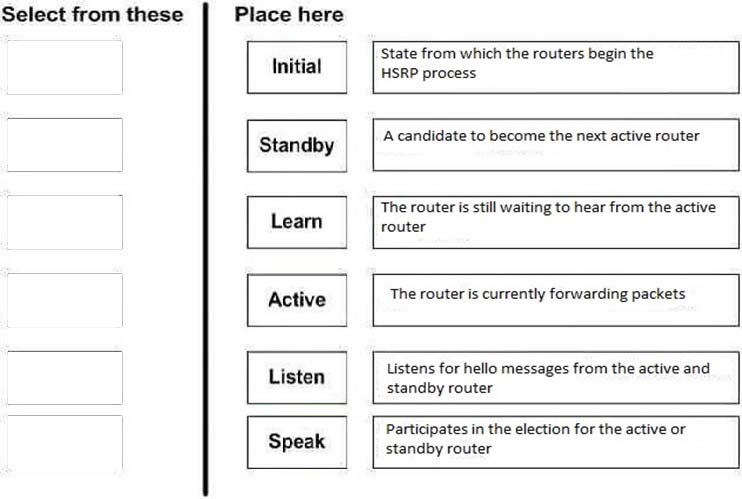
DRAG DROP - Match the HSRP states on the left with the correct definition on the right. Select and Place: Select and Place:
You have been asked to install and configure a new switch in a customer network. Use the console access to the existing and new switches to configure and verify correct device configuration.


Refer to the configuration. For which configured VLAN are untagged frames sent over trunk between SW1 and SW2?
A. VLAN1
B. VLAN 99
C. VLAN 999
D. VLAN 40
E. VLAN 50
F. VLAN 200
G. VLAN 300
Which statements about RSPAN are true? (Choose two.)
A. It supports MAC address learning.
B. RSPAN VLANS can carry RSPAN traffic only.
C. only one RSPAN VLAN can be configured per device.
D. RSPAN VLANs are exempt from VTP pruning.
E. MAC address learning is not supported
F. RSPAN uses are GRE tunnel to transmit captured traffic.
Which two statements about Cisco Discovery Protocol are true? (Choose two.)
A. It is not supported with SNMP
B. It runs on OSI Layer 2
C. It is supported on Frame Relay subinterfaces
D. It uses a TLV to advertise the native VLAN
E. It runs on OSI Layer 1
Instructions - To configure a switch click on the console host icon in the topology. You can click on the buttons to view the different windows. Each of the windows can be minimized by clicking on the [-]. You can also reposition a window by dragging it by the title bar. Most commands that use the "Control" or "Escape" keys are not supported and are not necessary to complete this simulation. The help command does not display all commands of the help system. Scenario - You work for SWITCH.com. They have just added a new switch (SwitchB) to the existing network as shown in the topology diagram. RouterA is currently configured correctly and is providing the routing function for devices on SwitchA and SwitchB. SwitchA is currently configured correctly, but will need to be modified to support the addition of SwitchB. SwitchB has a minimal configuration. You have been tasked with competing the needed configuring of SwitchA and SwitchB. SwitchA and SwitchB use cisco as the enable password. All commands must be entered at the physical interface level. Configuration Requirement for SwitchA: ✑ The VTP and STP configuration modes on SwitchA should not be modified. ✑ SwitchA needs to be the root switch for vlans 11, 12, 13, 21, 22, and 23. All other vlans should be left are their default values. Configuration Requirement for SwitchB: ✑ Vlan 21 - Name: Marketing - will support wo servers attached to fa0/9 and fa0/10 ✑ Vlan 22 - Name: Sales - will support two servers attached to fa0/13 and fa0/14 ✑ Vlan 23 - Name: Engineering - will support two servers attached to fa0/15 and fa0/16 ✑ Access ports that connect to server should transition immediately to forwarding state upon detecting the connection of a device. ✑ SwitchB VTP mode needs to be the same as SwitchA. ✑ SwitchB must operate in the same spanning tree mode as SwitchA. ✑ No routing is to be configured on SwitchB ✑ Only the SVl Vlan 1 is to be configured and it is to use address 192.168.1.11/24 Inter-switch Connectivity Configuration Requirements ✑ For operational and security reasons trunking should be unconditional and Vlans 1, 21, 22, and 23 should tagged when traversing the trunk link. ✑ The two trunks between SwitchA and SwitchB need to be configured in a mode that allows for the maximum use of their bandwidth for all vlans. This mode should be done with a non-proprietary protocol, with SwitchA controlling activation. ✑ Propagation of unnecessary broadcasts should be limited using manual pruning on this trunk link. Topology -Refer to the exhibit.
Which configuration ensures that the Cisco Discovery Protocol packet update frequency sent from DSW1 to ALS1 is half of the default value?
A. DSW1(config)#cdp timer 90
B. DSW1(config-if)#cdp holdtime 60
C. DSW1(config)#cdp timer 30
D. DSW1(config)#cdp holdtime 90
E. DSW1(config-if)#cdp holdtime 30
F. DSW1(config-if)#cdp timer 60
You have been asked to install and configure a new switch in a customer network. Use the console access to the existing and new switches to configure and verify correct device configuration.Examine the VTP configuration. You are required to configure private VLANs for a new server deployment connecting to the SW4 switch. Which of the following configuration steps will allow creating private VLANs?
A. Disable VTP pruning on SW1 only
B. Disable VTP pruning on SW2 only
C. Disable VTP pruning on SW4 only
D. Disable VTP pruning on SW2, SW4 and New_Switch
E. Disable VTP pruning on New_Switch and SW4 only.
You are configuring an interface, and you want to enable Layer 3 mode on an EtherChannel. Which task must you perform?
A. issue the no switchport command
B. Set the channel group to desirable
C. Set the channel group to active
D. Issue the ip address command
In which two ways can a port respond to a port-security violation? (Choose two.)
A. The port enters the err-disabled state
B. The port enters the shutdown state
C. The port triggers an EEM script to notify support staff and continues to forward traffic normally
D. The SecurityViolation counter is incremented and the port sends an SNMP trap
E. The SecurityViolation counter is incremented and the port sends a critical syslog message to the console
F. The port immediately begins to drop all traffic
Which statement about the configuration of MST on an IOS switch is true?
A. When MST is enabled, RSTP is automatically enabled and MST will use BPDU version 4, maximum of 16 instances of MST can exist.
B. When MST is enabled, RSTP is automatically disabled and MST will use BPDU version 4, maximum of 16 instances of MST can exist.
C. When MST is enabled, RSTP is automatically disabled and MST will use BPDU version 2, maximum of 16 instances of MST can exist.
D. When MST is enabled, RSTP is automatically enabled and MST will use BPDU version 2, maximum of 16 instances of MST can exist.
Which two commands configure SPAN to monitor outgoing traffic across multiple interfaces? (Choose two.)
A. monitor session 1 destination interface gigabitethernet1/0/2 rx
B. monitor session 1 source vlan 10 – 20 tx
C. monitor session 1 destination interface gigabitethernet1/0/2
D. monitor session 1 source interface gigabitethernet1/0/1 tx
E. monitor session 1 source interface gigabitethernet1/0/1 rx
CORRECT TEXT - Scenario: You work for SWITCH.com. They have just added a new switch (SwitchB) to the existing network as shown in the topology diagram. RouterA is currently configured correctly and is providing the routing function for devices on SwitchA and SwitchB. SwitchA is currently configured correctly, but will need to be modified to support the addition of SwitchB. SwitchB has a minimal configuration. You have been tasked with competing the needed configuring of SwitchA and SwitchB. SwitchA and SwitchB use Cisco as the enable password. Configuration Requirements for SwitchA The VTP and STP configuration modes on SwitchA should not be modified. SwitchA needs to be the root switch for vlans 11, 12, 13, 21, 22 and 23. All other vlans should be left are their default values. Configuration Requirements for SwitchB Vlan 21 - Name: Marketing - will support two servers attached to fa0/9 and fa0/10 Vlan 22 - Name: Sales - will support two servers attached to fa0/13 and fa0/14 Vlan 23 -Name: Engineering -will support two servers attached to fa0/15 and fa0/16 Access ports that connect to server should transition immediately to forwarding state upon detecting the connection of a device. SwitchB VTP mode needs to be the same as SwitchA. SwitchB must operate in the same spanning tree mode as SwitchA No routing is to be configured on SwitchB Only the SVI vlan 1 is to be configured and it is to use address 192.168.1.11/24 Inter-switch Connectivity Configuration Requirements For operational and security reasons trunking should be unconditional and Vlans 1, 21, 22 and 23 should tagged when traversing the trunk link. The two trunks between SwitchA and SwitchB need to be configured in a mode that allows for the maximum use of their bandwidth for all vlans. This mode should be done with a non- proprietary protocol, with SwitchA controlling activation. Propagation of unnecessary broadcasts should be limited using manual pruning on this trunk link.A. B. C. D.
Which statement about the default behavior of a Cisco switch MAC address table is true?
A. MAC addresses are not learned on extended VLANs.
B. MAC addresses are aged out of the MAC table after 600 seconds.
C. MAC addresses are associated with a VLAN.
D. MAC address filtering is enabled on trunk ports.
Refer to the exhibit.Which login credentials are required when connecting to the console port in this output?
A. none required
B. username cisco with password cisco
C. no username with password linepass
D. login authentication default
A network is running VTPv2. After verifying all VTP settings, the network engineer notices that the new switch is not receiving the list of VLANs from the server. Which action resolves this problem?
A. Reload the new switch.
B. Restart the VTP process on the new switch.
C. Reload the VTP server.
D. Verify connected trunk ports.
Which command can you enter to set the time between BPDUs in an MST environment by route bridge?
A. spanning-tree mst 1 cost 5
B. spanning-tree mst mst forward-time 5
C. spanning-tree mst hello-time 2
D. spanning-tree mst max-age 20
How do you configure loop guard?
A. (config)#spanning-tree loop guard default
B. (config-if)#spanning-tree loop
C. (config)#spanning-tree loop-guard default
D. (config-if)#spanning-tree guard loop
DRAG DROP - Drag and Drop - STP Timer Delay (Concepts Only) ✑ Diameter of the STP Domain (dia) ✑ Bridge Transit Delay (transit delay) ✑ BPDU Transmission Delay (bpdu_delay) Select and Place: Select and Place:
What is the link called between a VSS?
A. VSL (Virtual Switch Link)
B. SVI
C. DCSP
D. VLAN
Which two functions of DHCP snooping are true? (Choose two.)
A. It rate-limits DHCP traffic from trusted and untrusted sources.
B. It listens to multicast messages between senders and receiver.
C. It helps build the route table.
D. It filters invalid messages from untrusted sources.
E. It correlates IP address to hostnames.
Which two statements about configuring EtherChannels are true? (Choose two.)
A. They can be configured with the no switchport command to place them in Layer 3 mode.
B. They can be configured to send Layer 2 packets.
C. They can be configured to operate with up to links in a single channel.
D. They can be configured to passively negotiate a channel with a connected peer.
E. They can be configured to load-balance traffic based on Layer 7 information.
How many Active Virtual Gateways (AVG) can be used in a GLBP protocol?
A. Only one AVG can be elected on a switch
B. Two AVG could be elected on a switch
C. Two AVG just could be elected in GLBP v2
D. GLBP supports 8 AVGs per group
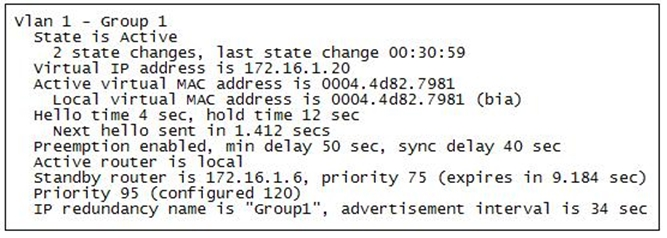
The partial output displayed in the exhibit is a result of what IOS command? (Click on the Exhibit(s) button.)
A. switch# show running-config
B. switch# show standby vlan1 active brief
C. switch# show hsrp 1
D. switch# show standby
Access Full 300-115 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete 300-115 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our 300-115 mock test free today—and take a major step toward exam success!