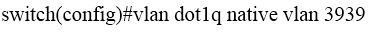300-115 Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the 300-115 exam? Start with our 300-115 Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a 300-115 practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free 300-115 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
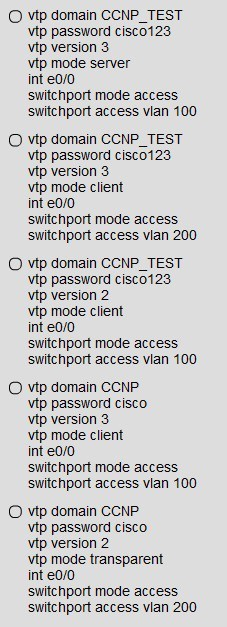
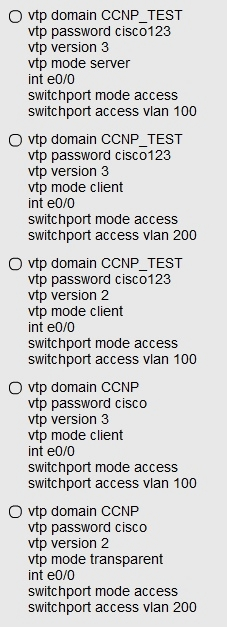
Which parameters are found in VTP advertisements? (Choose three.)
A. Password
B. VTP mode
C. IP address
D. Switch name
E. Revision number
F. Management domain name
Refer to the exhibit. Which configuration on the HSRP neighboring device ensures that it becomes the active HSRP device in the event that port fa1/1 on Switch_A goes down? A.B.
C.
D.
Which two statements about dynamic MAC address learning are true? (Choose two.)
A. Dynamically-learned MAC addresses can be cleared on a per-interface basis only.
B. It must be enabled on ports with port security enabled.
C. It can be disabled on a per-VLAN basis only.
D. Switch interfaces learn MAC addresses dynamically by default.
E. Dynamically-learned MAC addresses supersede static MAC addresses
Which statement about Layer 2 protocol participation of ports involved in a SPAN session is true?
A. Neither a SPAN source nor SPAN destination participates in any Layer 2 protocols.
B. A SPAN source does not participate in any Layer 2 protocols.
C. A SPAN destination does not participate in any Layer 2 protocols.
D. Both SPAN source and SPAN destination participate in any Layer 2 protocols.
Which will identify the master switch in stackwise?
A. The switch that is currently the stack master
B. The switch with the highest stack member priority value
C. The switch that uses the non-default interface-level configuration
D. The switch with the lower priority stack member priority value
The following commands have been issued on a Catalyst switch:Which of the following VLANs is allowed on the trunk?
A. VLAN 1 and VLANs 101 through 200
B. VLANs 101 through 200
C. VLANs 1 through 3000
D. VLANs 1 through 4094
Which two statements about extended-range VLANs are true? (Choose two.)
A. Created in VTP server mode in VTP version 3.
B. Created when switch is in VTP server mode.
C. They support pruning.
D. VTP version 3 stores extended-range VLAN in VLAN database.
E. VTP version 1 and 2 stores extended-range VLAN in VLAN database.
Which technique automatically limits VLAN traffic to only the switches that require it?
A. access lists
B. DTP in nonegotiate
C. VTP pruning
D. PBR
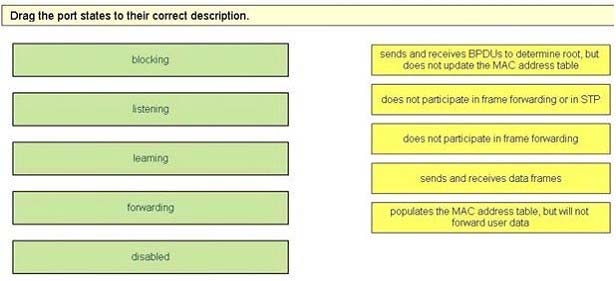
Drag and Drop Question - Select and Place:
Which two characteristics apply to Cisco Catalyst 6500 Series Switch supervisor redundancy using NSF? (Choose two.)
A. supported by RIPv2, OSPF, IS-IS, and EIGRP
B. uses the FIB table
C. supports IPv4 and IPv6 multicast
D. prevents route flapping D
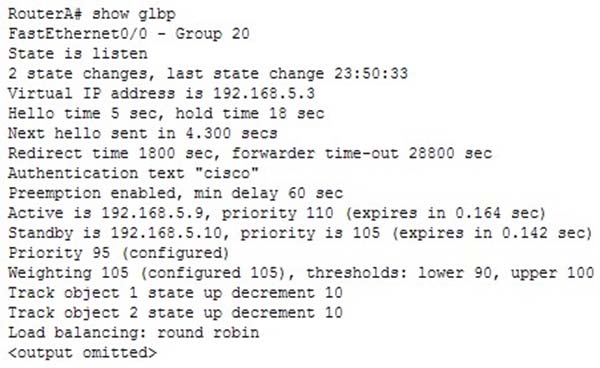
What command displays detailed information about the GLBP groups to which the switch belongs?
A. switch# show standby
B. switch# show glbp state
C. switch# show glbp
D. switch# show standby detail
Which two protocols can be automatically negotiated between switches for trunking? (Choose two.)
A. PPP
B. DTP
C. ISL
D. HDLC
E. DLCI
F. DOT1Q
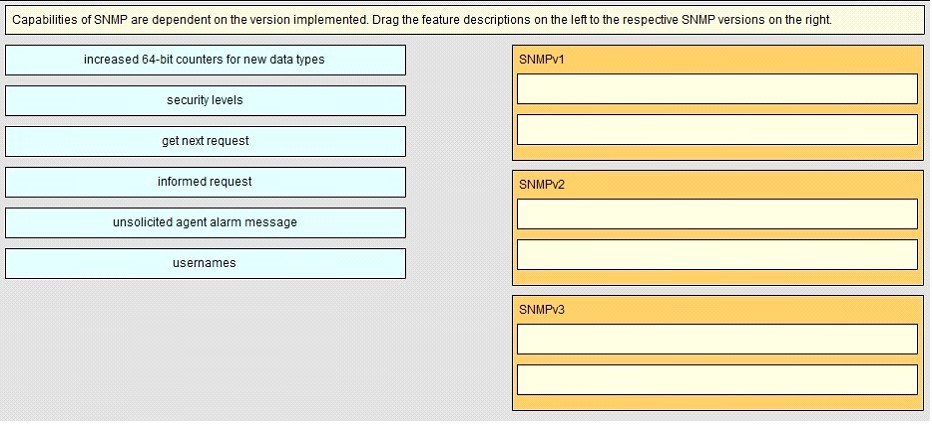
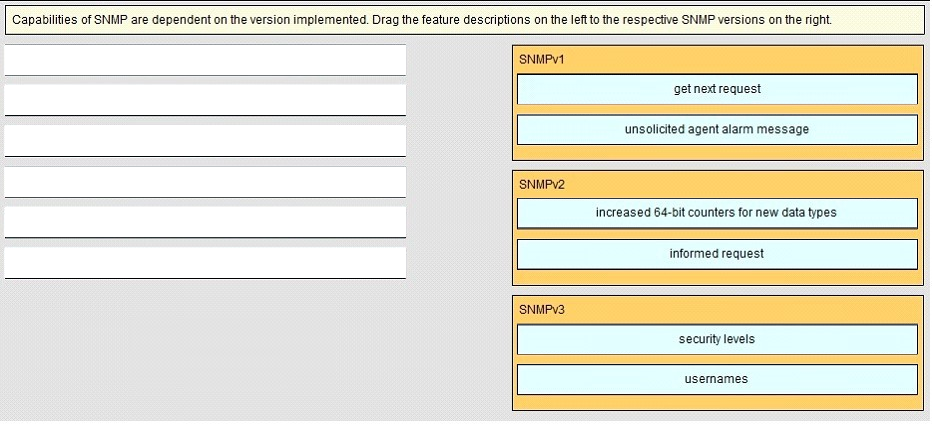
Drag and Drop Question - Select and Place:
Which two statements about frame LLDP is true?
A. Frame has destination multicast address
B. NA
C. Frame has CRC
An engineer needs to add a customer private VLAN to the network. What configuration is required to isolate the customer's traffic on the network?
A. Configure transparent mode
B. Enable VTP v3
C. Configure VTP in server mode
D. Disable VTP and manually configure the customer VLAN
In a switch stack is configured to use SDM template, where are the templates stored?
A. all stack members
B. stack master
C. flash memory
D. TFTP server
You need to create an implementation plan for providing Layer 3 redundancy in your switched network. You included Hot Standby Routing Protocol (HSRP) as the protocol to avoid first-hop router failure. However, your supervisor suggests including Virtual Router Redundancy Protocol (VRRP) instead of HSRP in the implementation plan. Which of the following statements is TRUE about the reasons for the suggested change in the implementation plan? (Choose two.)
A. HSRP works only on Cisco routers and VRRP works on both Cisco and non- Cisco routers.
B. HSRP works on both Cisco and non-Cisco routers and VRRP works only Cisco routers.
C. HSRP-enabled routers need to be configured manually to preempt the active router and VRRP-enabled routers preempt it automatically.
D. HSRP-enabled routers automatically preempt the active router and VRRP-enabled routers need to be configured manually to preempt the active router. AC
Refer to the exhibit.A multilayer switch has been configured to send and receive encapsulated and tagged frames. VLAN 2013 on the multilayer switch is configured as the native VLAN. Which option is the cause of the spanning-tree error?
A. VLAN spanning-tree in SW-2 is configured.
B. spanning-tree bpdu-filter is enabled.
C. 802.1q trunks are on both sides, both with native VLAN mismatch.
D. VLAN ID 1 should not be used for management traffic because its unsafe.
Which command configures VLAN 99 as an untagged VLAN on a trunk?
A. switchport trunk allowed vlan 99
B. switchport trunk pruning vlan except 99
C. switchport trunk native vlan 99
D. switchport access vlan 99
In a switch stack environment, what is the total bidirectional traffic flow between two logical counter-rotating paths?
A. 16 Gbps
B. 32 Gbps
C. 64 Gbps
D. 128 Gbps
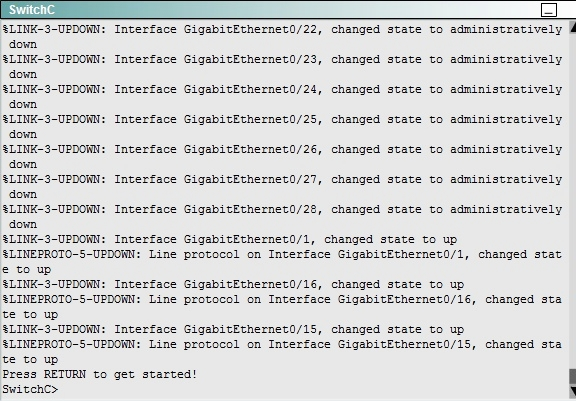
SIMULATION - You have been tasked with configuring multilayer SwitchC, which has a partial configuration and has been attached to RouterC as shown in the topology diagram. You need to configure SwitchC so that Hosts H1 and H2 can successfully ping the server S1. Also SwitchC needs to be able to ping server S1. Due to administrative restrictions and requirements you should not add/delete vlans or create trunk links. Company policies forbid the use of static or default routing. All routes must be learned via EIGRP 65010 routing protocol. You do not have access to RouteC. RouterC is correctly configured. No trunking has been configured on RouterC. Routed interfaces should use the lowest host on a subnet when possible. The following subnets are available to implement this solution: 10.10.10.0/24 190.200.250.32/27 190.200.250.64/27 Hosts H1 and H2 are configured with the correct IP address and default gateway. SwitchC uses Cisco as the enable password. Routing must only be enabled for the specific subnets shown in the diagram. Note: Due to administrative restrictions and requirements you should not add or delete VLANs, changes VLAN port assignments or create trunks. Company policies forbid the use of static or default routing. All routes must be learned via the EIGRP routing protocol.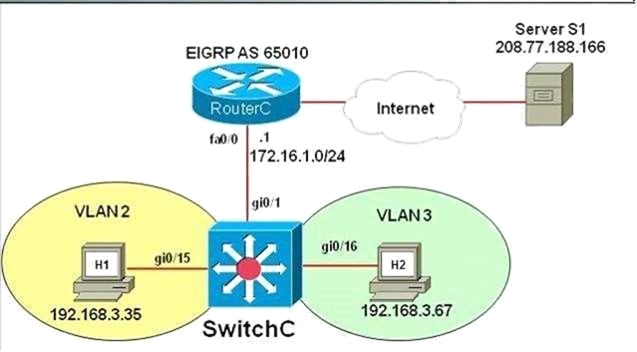
You have been asked to install and configure a new switch in a customer network. Use the console access to the existing and new switches to configure and verify correct device configuration.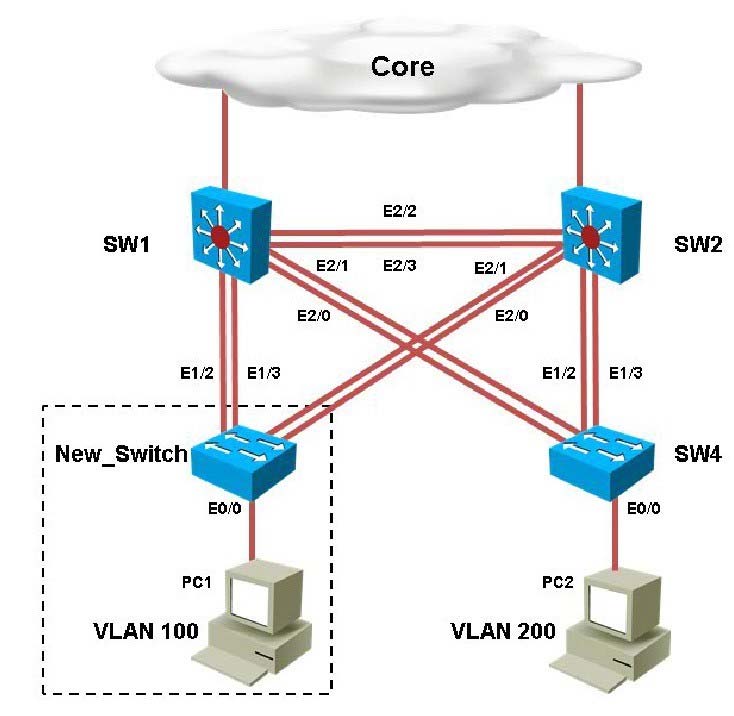


You are connecting the New_Switch to the LAN topology; the switch has been partially configured and you need to complete the rest of configuration to enable PC1 communication with PC2. Which of the configuration is correct?
A. Option A
B. Option B
C. Option C
D. Option D
E. Option E
Refer to the exhibit.Switch A, B, and C are trunked together and have been properly configured for VTP. Switch C receives VLAN information from the VTP server Switch A, but Switch B does not receive any VLAN information. What is the most probable cause of this behavior?
A. Switch B is configured in transparent mode.
B. Switch B is configured with an access port to Switch A, while Switch C is configured with a trunk port to Switch B.
C. The VTP revision number of the Switch B is higher than that of Switch A.
D. The trunk between Switch A and Switch B is misconfigured.
If EtherChannel guard is configured on a device, which result happens when the device detects a misconfiguration on a connected device?
A. Spanning tree is disabled for the VLANs associated with the EtherChannel.
B. The port generates a syslog message.
C. The EhterChannel configuration is removed from the running configuration of the device.
D. The port is error disabled.
Which form of centralized device authentication allows each AAA feature to function separately?
A. local database
B. TACACS+
C. Kerberos
D. RADIUS
You have been asked to install and configure a new switch in a customer network. Use the console access to the existing and new switches to configure and verify correct device configuration.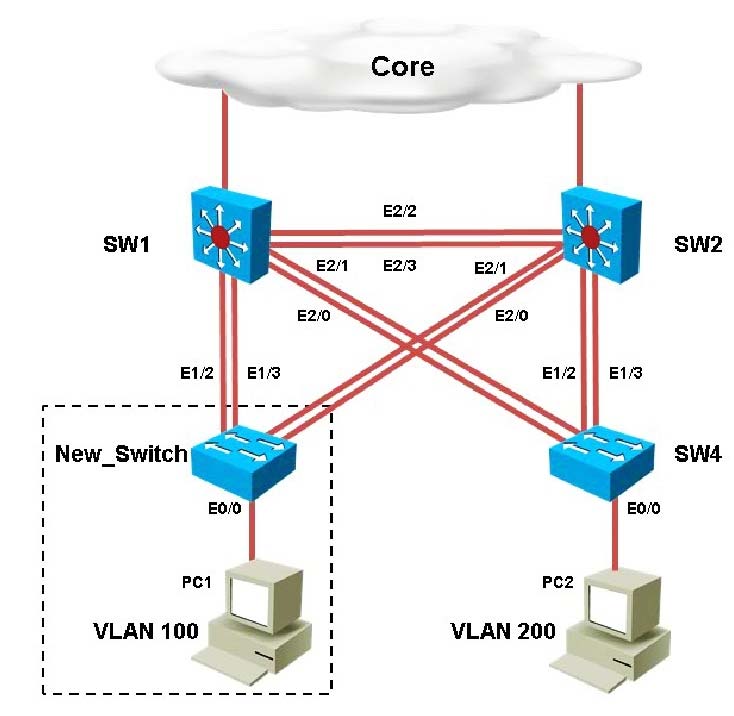

You are connecting the New_Switch to the LAN topology; the switch has been partially configured and you need to complete the rest of configuration to enable PC1 communication with PC2. Which of the configuration is correct?
A. Option A
B. Option B
C. Option C
D. Option D
E. Option E
Which type of attack can be mitigated by dynamic ARP inspection?
A. DDoS attacks
B. viruses
C. Trojan infiltration
D. smurf attacks
E. man-in-the-middle attacks
F. worm infiltration
Which two commands or command sequences configure a switch so that it tags native VLAN 3939? (Choose two.) A.B.
C.
D.
E.
Which two statements about VRRP are true? (Choose two.)
A. It requires each device in the group to participate in the same dynamic routing protocol.
B. Preemption is not supported.
C. It can use a single virtual address to provide default gateway redundancy.
D. It uses a shared VIP to support default gateway redundancy.
E. It support clear-text authentication only.
Which two port err-disabled recovery options are used to detect the reason? (Choose two.)
A. show errdisable detect
B. show errdisable recovery
C. error-disable notifications/traps are active by default.
D. error-disable notifications/traps are disabled by default.
E. error-disable notifications/traps is never possible.
Which two restrictions of the port security feature are true? (Choose two.)
A. trunk ports
B. SPAN ports
C. tunnel ports
D. EtherChannel
E. private VLANs
Refer to the exhibit.An engineer is configuring EtherChannel between two switches and notices the console message on switch 2. Based on the output, which option describes the reason for this error?
A. Switch 1 does not have enough member ports configured.
B. Switch 2 has too many member ports configured.
C. The port channel interface numbers do not match.
D. The EtherChannel protocols do not match.
If you have a new switch (that runs spanning-tree mode pvst+) connect to the exist switch, which statement is true?
A. It will not work between two switches.
B. It will work, the new switch will communicate to the existing switch with PVST+
C. It will work, the new switch will communicate to the existing switch with Rapid-PVST
D. It will work, the new switch will communicate to the existing switch with MSTP
What Cisco switch features are designed to work together to mitigate ARP spoofing attacks? (Choose two.)
A. DHCP snooping
B. port security
C. 802.1x
D. DAI
What happens if you apply this command "vlan dot1q tag native"?
A. packet will be dropped
B. packet go to default vlan
C. packet go to native vlan
Which two StackWise configuration setting types are applied at the system level? (Choose two.)
A. 802.1x settings
B. speed/duplex settings
C. port-security settings
D. VLAN settings
E. SNMP settings
Which two device types does DHCP snooping treat as untrusted in an ISP environment? (Choose two.)
A. provider devices
B. customer edge devices
C. user-facing provider edge devices
D. end host devices
E. provider edge devices
Which two mandatory TLV types does LLDP advertise? (Choose two.)
A. Native VLAN TLV
B. Platform TLV
C. Network TLV
D. Hostname TLV
E. Port ID TLV
F. Chassis ID TLV
Which IOS commands are entered in interface configuration mode to configure a switch port to actively negotiate to be an 802.1Q trunk port? (Choose two.)
A. switchport trunk dot1q
B. switchport mode dynamic auto
C. switchport trunk allowed vlan
D. switchport mode trunk
E. switchport trunk encapsulation dot1q
Which command do you enter so that the default authentication group on a device falls back to the case-sensitive local user database when the initial authentication fails?
A. aaa authentication login default group tacacs+ radius local
B. aaa authentication exec default group tacacs+ local if-authenticated
C. aaa authentication login default group tacacs+ local-case if-authenticated
D. aaa authentication exec default group tacacs+ if-authenticated local
What is the benefit of UDLD?
A. provides backup for fiber
B. help in preventing loops
C. removes loops
D. determines switch path
Drag and Drop Question - Select and Place:
Drag and Drop Question - Select and Place:
An EtherChannel bundle has been established between a Cisco switch and a corporate web server. The network administrator noticed that only one of the EtherChannel links is being utilized to reach the web server. What should be done on the Cisco switch to allow for better EtherChannel utilization to the corporate web server?
A. Enable Cisco Express Forwarding to allow for more effective traffic sharing over the EtherChannel bundle.
B. Adjust the EtherChannel load-balancing method based on destination IP addresses.
C. Disable spanning tree on all interfaces that are participating in the EtherChannel bundle.
D. Use link-state tracking to allow for improved load balancing of traffic upon link failure to the server.
E. Adjust the EtherChannel load-balancing method based on source IP addresses.
When IP Source Guard with source IP filtering is enabled on an interface, which feature must be enabled on the access VLAN for that interface?
A. DHCP snooping
B. storm control
C. spanning-tree portfast
D. private VLAN
Your customer has asked you to come in and verify the operation of routers R1 and R2 which are configured to use HSRP. They have questions about how these two devices will perform in the event of a device failure.What is the virtual mac-address of HSRP group 1?
A. 0000.0c07.ac02
B. 4000.0000.0010
C. 0000.0c07.ac01
D. 4000.0000.ac01
E. 4000.0000.ac02
F. 0000.0c07.0010
Technician moves PC from one switch port to another switch port. After the move, the new switch port goes errdisabled. Why?
A. Security violation
B. Duplex mismatch
C. different vlan
In which two ways can a port respond to a port-security violation? (Choose two.)
A. The port enters the err-disabled state
B. The port enters the shutdown state
C. The port triggers an EEM script to notify support staff and continues to forward traffic normally
D. The SecurityViolation counter is incremented and the port sends an SNMP trap
E. The SecurityViolation counter is incremented and the port sends a critical syslog message to the console
F. The port immediately begins to drop all traffic
Which two statements about HSRP is true? (Choose two.)
A. It required all the groups to have the same routing protocols.
B. It must have an IP address that is active.
C. It must have the same virtual MAC address for all groups.
D. It must have the same VIP address in all groups.
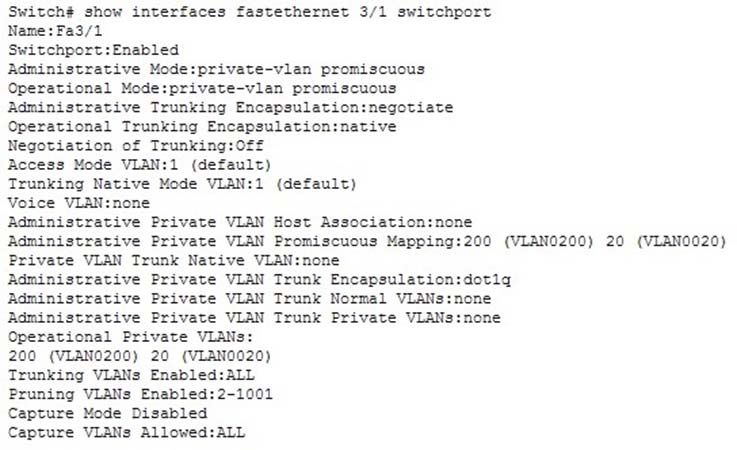
What command should be used to view the private VLANs configured on ports and the private VLAN mappings?
A. show vlan brief
B. show pvlan
C. show interfaces switchport
D. show mac-address-table
Free Access Full 300-115 Practice Test Free Questions
If you’re looking for more 300-115 practice test free questions, click here to access the full 300-115 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your 300-115 certification journey!