XK0-004 Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the XK0-004 certification exam? Kickstart your success with our XK0-004 Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with XK0-004 practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free XK0-004 practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
An administrator needs to deploy 100 identical CentOS workstations via PXE boot. Which of the following should the administrator use to minimize the amount of interaction with the consoles needed?
A. Kickstart script
B. Ghost image on a distribution server
C. Hard disk duplicator
D. Hard disk duplicator
E. Ubiquity script
A junior Linux administrator is installing a new application with CPU architecture requirements that have the following specifications: ✑ x64 bit ✑ 3.0GHz speed ✑ Minimum quad core The administrator wants to leverage existing equipment but is unsure whether the requirements of these systems are adequate. The administrator issues the following command cat /proc/cpuinfo. The output of the command is as follows:Which of the following is the recommended course of action the administrator should take based on this output?
A. Install the application, as the system meets the application requirements
B. Procure new equipment that matches the recommended specifications
C. Recompile the Linux kernel to support the installation.
D. Reconfigure lib modules to support the new application.
A systems administrator wants to deploy several applications to the same server quickly. Each application should be abstracted from the host with its own dependencies and libraries and utilize a minimal footprint. Which of the following would be BEST in this scenario?
A. Virtual machines
B. Type 2 hypervisor
C. Chroot jails
D. Containers
A new IO card has been added to the security server to log the opening and closing of the main entrance. A switch is attached, so the interface card returns a 1 when the door is opened and a 0 when the door is closed. Which of the following describes the Linux device to which this switch is attached?
A. /dev/tty0
B. /dev/port
C. /dev/gpio
D. /dev/sg0
A user cannot write files to the /home/user directory. The junior Linux administrator runs the following commands:Which of the following BEST represents why the user cannot write files?
A. The filesystem is out of inodes.
B. The filesystem is out of file space.
C. The filesystem is not configured for the user to write to it.
D. The filesystem does not have a group write permission.
SIMULATION - A junior system administrator had trouble installing and running an Apache web server on a Linux server. You have been tasked with installing the Apache web server on the Linux server and resolving the issue that prevented the junior administrator from running Apache. INSTRUCTIONS - Install Apache and start the service. Verify that the Apache service is running with the defaults. Typing `help` in the terminal will show a list of relevant commands. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button. CentOS Command Prompt -
A user, jsmith, needs access to database files located on a server. Which of the following will add jsmith to the `dba` group and preserve existing group memberships?
A. usermod ג€”a ג€”G dba jsmith
B. usermod ג€”g dba jsmith
C. useradd ג€”g dba jsmith
D. groupmod dba ג€”u jsmith
Which of the following protocols are used to access the desktop environment on a remote system? (Choose two.)
A. CUPS
B. Cinnamon
C. NX
D. SPICE
E. YAML
F. Kerberos
A security administrator wants to display a warning banner before a user logs in. Which of the following files must be edited to make this happen?
A. /etc/services
B. /etc/issue
C. /etc/hosts
D. /etc/motd
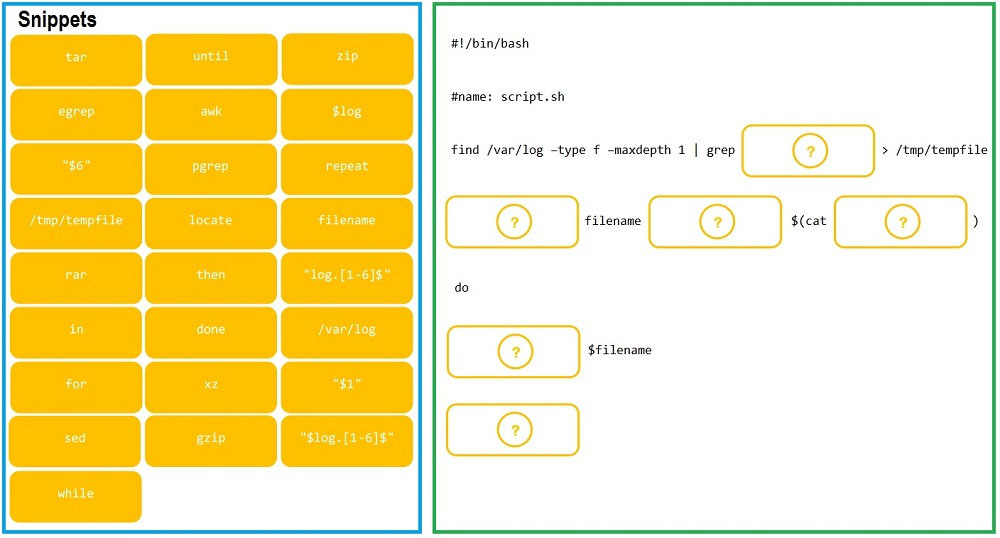
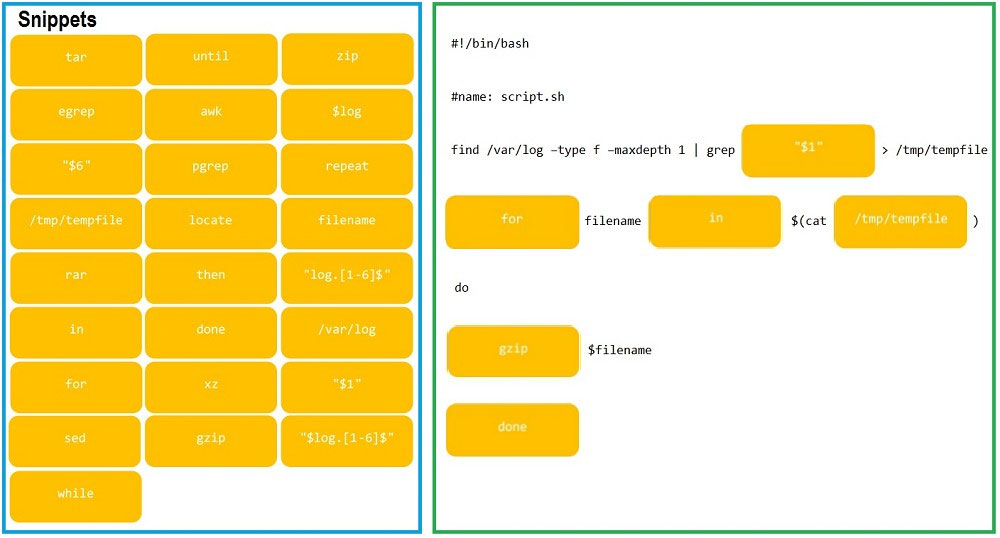
DRAG DROP - As a Systems Administrator, to reduce disk space, you were tasked to create a shell script that does the following: Add relevant content to /tmp/script.sh, so that it finds and compresses rotated files in /var/log without recursion. INSTRUCTIONS - Fill the blanks to build a script that performs the actual compression of rotated log files. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button. Select and Place:
An administrator is analyzing a Linux server which was recently hacked. Which of the following will the administrator use to find all unsuccessful login attempts?
A. nsswitch
B. faillock
C. pam_tally2
D. passwd
An administrator notices the HISTSIZE variable is 50, using the commands below: HISTSIZE=50 - export HISTSIZE The administrator rechecks the HISTSIZE value using echo HISTSIZE but gets no value. Which of the following commands should the administrator use to retrieve its value?
A. printenv | grep $HISTSIZE
B. echo HISTSIZE
C. printf HISTSIZE
D. grep $HISTSIZE
Joe, a user, creates a short shell script, shortscript.sh, and saves it in his home directory with default permissions and paths. He then attempts to run the script by typing ./shortscript.sh, but the command fails to execute. Which of the following commands would have allowed the script to run?
A. chmod u+x shortscript.sh
B. source ./shortscript.sh
C. chmod 155 ~/shortscript.sh
D. chgrp shortscript.sh Joe
A user needs to modify the IP address of a laptop. Which of the following files can be used to configure the network interface named eth0?
A. /etc/sysconfig/network/interfaces.cnf
B. /system/config/interfaces
C. /etc/sysconfig/network-scripts/ifcfg-eth0
D. /system/networking/ifconfig
E. /etc/interfaces/eth0.conf
An administrator needs to look at a log for an application on a systemd-based system. There is no log for this application in /var/log. Which of the following is another way to view the application log on this system?
A. tail -f /var/log/secure
B. journalctl ג€”u application
C. systemctl application.service
D. watch /var/lib/application/
A technician wants to update the contents of the /etc/hosts.allow file. The technician reviews the following output:According to best practice, which of the following commands should the technician use?
A. setfacl u:user:w /etc/hosts.allow; vi hosts.allow
B. visudo /etc/hosts.allow
C. chgrp user /etc/hosts.allow; vi /etc/hosts.allow
D. sudo vi /etc/hosts.allow
E. chown user /etc/hosts.allow; vi /etc/hosts.allow
An administrator needs to create a file named hello in the home directory that contains the following text: it's me! Which of the following commands would accomplish this goal?
A. mkdir ~/hello touch ~/”it’s me!”
B. touch ~/hello echo “it’s me!” > ~/hello
C. mv ~/hello cp “it’s me!” > ~/hello
D. type ~/hello print “it’s me!”
When logging in, an administrator must use a temporary six-digit code that is displayed on a key fob. Which of the following has been implemented?
A. Biometrics
B. HOTP
C. PKI
D. Software token
A Linux administrator needs to remove a USB drive from a system. The unmount command fails, stating the device is busy. Which of the following commands will show the reason for this error?
A. lsusb | grep /mnt/usb
B. mount | grep /mnt/usb
C. ps aux | grep /mnt/usb
D. lsof | grep /mnt/usb
A Linux administrator is troubleshooting an issue with a shell script. Users in the accounting department are unable to run the script, but users in the sales department are not having issues. Users in both departments should be able to run the script. The administrator checks the permissions on the script and receives the following information: -r-xr-xr-- joe sales script.sh Which of the following commands should the administrator execute to resolve the problem?
A. chgrp accounting script.sh
B. chmod 644 script.sh
C. chown accounting script.sh
D. chmod a+x script.sh
A user creates a key pair to configure RSA authentication on a Linux server. Which of the following should the user do NEXT?
A. Copy the id_rsa.pub file contents to the server
B. Copy the id_rsa file contents to the server
C. Use ssh-add to install the id_rsa.pub on the client
D. Copy the known_hosts file contents to the client
E. Copy the known_hosts file contents to the server
Which of the following is modified to reconfigure the boot environment?
A. grub-mkconfig
B. grub.cfg
C. update-grub
D. grub2-mkconfig
A junior systems administrator needs to schedule a backup script named /scripts/backup.sh and make the correct changes to the crontab. Which of the following crontab entries would run the script every Monday at 2:05 a.m.?
A. 1 * * 5 2 /scripts/backup.sh
B. 2 5 * * 1 /scripts/backup.sh
C. 5 2 * * 1 /scripts/backup.sh
D. 1 * * 2 5 /scripts/backup.sh
E. 5 2 * * 0 /scripts/backup.sh
A systems administrator has received reports of intermittent network connectivity to a particular website. Which of the following is the BEST command to use to characterize the location and type of failure over the course of several minutes?
A. mtr www.comptia.org
B. tracert www.comptia.org
C. ping www.comptia.org
D. netstat www.comptia.org
A security audit concludes that an organization's database servers need to be hardened. As a result, an administrator obtains the following partial Nmap output from a database server.Which of the following commands should the administrator execute to mitigate security risks?
A. iptables -A INPUT -p tсp –dport 23 -j DROP
B. iptables -A OUTPUT -p udp –dport 123 -j DROP
C. iptables -A INPUT -p tcp –sport 23 -j ACCEPT
D. iptables -A INPUT -p tcp –dport 3306 -j ACCEPT
An administrator finds a text file that is using too much disk space. The administrator runs lsof | grep bigfile.txt and gets the following return:Which of the following should the administrator do NEXT to prepare to delete the file and free up disk space?
A. pkill app.py
B. logout –force comptia
C. kill -9 7339
D. kill -HUP 12288
A Linux administrator needs to know the MAC address of the server's gateway. Which of the following commands should the administrator run to obtain this information?
A. arp -gw
B. arp -a
C. arp -gwi
D. arp -gtw
Which of the following are classified as Linux GUI servers? (Choose two.)
A. VNC
B. KDE
C. Gnome
D. Wayland
E. MATE
F. X11
A system shows high utilization of swap space but low utilization of physical memory. Which of the following commands should an administrator run to free up usable swap space?
A. mkswap ; swapon -a
B. free && swapon -a
C. swapoff -a && swapon -a
D. swapon -a ; swapoff -a
A Linux user needs to create a file named newfile in the home directory that mirrors the contents of the /etc/resolv.conf file. Which of the following commands would accomplish this task?
A. cat /etc/resolv.conf > /home/user/newfile
B. echo /etc/resolv.conf > /home/user/newfile
C. grep /etc/resolv.conf /home/user/newfile
A Linux administrator is checking connectivity between two servers in separate subnets: Server A: 10.1.2.20 (source) Server B: 10.2.1.10 (destination on port 8080) The administrator tried to run the curl 10.2.1.10:8080 command on server A and received the following output: curl: (7) Failed to connect to 10.2.1.10 port 8080: Connection refused. The administrator checked on server B and confirmed nothing is listening on port 8080. Which of the following commands, when run on server B, would have allowed the administrator to test the connection successfully?
A. tcpdump ‘tcp port 8080’
B. ss -l -p dport=8080 dst 10.2.1.10
C. nc -l -p 8080 10.2.1.10
D. nmap -v -p 8080 10.2.1.10
A junior Linux administrator receives a request to add a user, Ann, to the secondary group `cashiers`. Ann is also a member of the secondary group, `managers`. The administrator issues the following command: usermod -G cashiers Ann Later, Ann reports that she is unable to access any of the files or directories in `managers`. Which of the following commands should the administrator issue to resolve Ann's group memberships?
A. usermod -G cashiers,managers Ann
B. usermod -g cashiers,managers Ann
C. groupmod -G Ann cashiers,managers
D. groupmod -ga Ann cashiers,managers
A Linux administrator is configuring a server to log security events for the ping command while allowing the request to occur. The Linux server is using AppArmor to manage its security services. Which of the following commands is the BEST option?
A. aa-complain /bin/ping
B. aa-disable /bin/ping
C. aa-unconfined /bin/ping
D. aa-enforce /bin/ping
A junior administrator needs to unload an older video kernel module. Which of the following commands would BEST accomplish this task?
A. modprobe
B. insmod
C. rmmod
D. chmod
E. depmod
A systems administrator needs to install a new piece of hardware that requires a new driver. The driver should be manually installed. Which of the following describes the order of commands required to obtain module information, install the module, and check the log for any errors during module installation?
A. lsmod, modprobe, modinfo
B. modinfo, insmod, modprobe
C. modinfo, insmod, dmesg
D. lsmod, insmod, dmesg
An administrator is attempting to block SSH connections to 192.168.10.24 using the Linux firewall. After implementing a rule, a connection refused error is displayed when attempting to SSH to 192.168.10.24. Which of the following rules was MOST likely implemented?
A. iptables ג€”A ג€”p tcp ג€”d 192.168.10.24 ג€”-dport 22 ג€”j REJECT
B. iptables ג€”A ג€”p tcp ג€”d 192.168.10.24 ג€”-dport 22 ג€”j DROP
C. iptables ג€”A ג€”p tcp ג€”d 192.168.10.24 ג€”-dport 22 ג€”j FORWARD
D. iptables ג€”A ג€”p tcp ג€”d 192.168.10.24 ג€”-dport 22 ג€”j REFUSE
A Linux administrator wants to obtain a list of files and subdirectories in the /etc directory that contain the word `services`. Once the files and subdirectories are discovered, they should be listed alphabetically in the /var/tmp/foundservices file. Which of the following shell scripts will accomplish this task?
A. #/bin/bash find /etc ג€”name services | sort > /var/tmp/foundservices
B. #/bin/bash locate /etc ג€”sort ג€”name services > /var/tmp/foundservices
C. #/bin/bash find ג€”name services ג€”sort /var/tmp/foundservices
The grub2-mkconfig command is used to generate a new GRUB2 configuration after:
A. resizing the /boot filesystem.
B. changing the /etc/default/grub file.
C. changing the /boot/grub2/grub.cfg file.
D. installing new software from a package.
A systems engineer scheduled an at job that will reboot a critical server. A developer states the processes will not complete for another three hours. Which of the following will help the systems engineer to remove the job?
A. atq atrm
B. at -q atrm
C. atq atrm
D. at -q atrm
A user sent the following log to the help desk:Which of the following should the help desk technician do to resolve this issue?
A. chmod 700 /home/user02/.ssh
B. chown -R user01 /home/user02
C. chmod u+x /home/user02
D. chmod 600 /home/user02/.bash_profile
A systems administrator needs to examine the output of all kernel-related events since the system was booted. Which of the following would BEST display this information?
A. dmesg
B. modinfo
C. systemctl
D. logger
A new user has been added to a Linux machine. Which of the following directories would contain the user's default files?
A. /etc/login.defs
B. /etc/passwd
C. /etc/skel
D. /etc/inittab
An administrator wants to prevent the accidental deletion of a business-critical application log file without affecting the functionality of the application and its logging. Which of the following commands would BEST accomplish this goal?
A. setfacl -m u:application:w application.log
B. chattr +a application.log
C. chown nobody application.log
D. chmod 400 application.log
An administrator needs to create a shared directory in which all users are able to read, write, and execute its content but none of the regular users are able to delete any content. Which of the following permissions should be applied to this shared directory?
A. rwxrwxrwt
B. rwxrwxrws
C. rwxrwxrwx
D. rwxrwxrw*
A systems administrator needs to prevent the root account from being used to log in to a Linux server via SSH. Which of the following configuration files does the systems administrator need to edit to perform this task?
A. /etc/passwd
B. /etc/sshd_config
C. ~/.ssh/config
D. /etc/sysconfig/sshd
A junior Linux administrator needs to ensure a service will start on system boot. Which of the following commands should be used to accomplish this task?
A. chkconfig on
B. systemctl bootup
C. service enable
D. crontab install
A junior systems administrator needs to make a packet capture file that will only capture HTTP protocol data to a file called test.pcap. Which of the following commands would allow the administrator to accomplish this task?
A. netcat -p 80 -w test.pcap
B. tshark -r test.pcap -o http
C. tcpdump -i eth0 port 80 -r test.pcap
D. tcpdump -i eth0 port 80 -w test.pcap
Which of the following is a file that can define how to build deploy, and install various components for a Linux application hosted in a cloud environment?
A. OVF
B. YAML
C. Virsh
D. VMM
Which of the following servers provides encrypted tunnel SOCKS services?
A. SNMP
B. VPN
C. CA
D. SSH
A Linux administrator needs to switch from text mode to GUI. Which of the following runlevels will start the GUI by default?
A. Runlevel 3
B. Runlevel 4
C. Runlevel 5
D. Runlevel 6
Free Access Full XK0-004 Practice Questions Free
Want more hands-on practice? Click here to access the full bank of XK0-004 practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your XK0-004 certification journey!