SY0-501 Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the SY0-501 certification exam? Kickstart your success with our SY0-501 Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with SY0-501 practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free SY0-501 practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
An employee uses RDP to connect back to the office network. If RDP is misconfigured, which of the following security exposures would this lead to?
A. A virus on the administrator’s desktop would be able to sniff the administrator’s username and password.
B. Result in an attacker being able to phish the employee’s username and password.
C. A social engineering attack could occur, resulting in the employee’s password being extracted.
D. A man in the middle attack could occur, resulting the employee’s username and password being captured.
A consumer purchases an exploit from the dark web. The exploit targets the online shopping cart of a popular website, allowing the shopper to modify the price of an item at checkout. Which of the following BEST describes this type of user?
A. Insider
B. Script kiddie
C. Competitor
D. Hacktivist
E. APT
An audit found that an organization needs to implement job rotation to be compliant with regulatory requirements. To prevent unauthorized access to systems after an individual changes roles or departments, which of the following should the organization implement?
A. Permission auditing and review
B. Exit interviews
C. Offboarding
D. Multifactor authentication
A technician must configure a firewall to block external DNS traffic from entering a network. Which of the following ports should they block on the firewall?
A. 53
B. 110
C. 143
D. 443
A network technician is trying to determine the source of an ongoing network based attack. Which of the following should the technician use to view IPv4 packet data on a particular internal network segment?
A. Proxy
B. Protocol analyzer
C. Switch
D. Firewall
A Chief Information Security Officer (CISO) asks the security architect to design a method for contractors to access the company's internal wiki, corporate directory, and email services securely without allowing access to systems beyond the scope of their project. Which of the following methods would BEST fit the needs of the CISO?
A. VPN
B. PaaS
C. IaaS
D. VDI
A company is examining possible locations for a hot site. Which of the following considerations is of MOST concern if the replication technology being used is highly sensitive to network latency?
A. Connection to multiple power substations
B. Location proximity to the production site
C. Ability to create separate caged space
D. Positioning of the site across international borders
Which of the following is MOST likely the security impact of continuing to operate end-of-life systems?
A. Higher total cost of ownership due to support costs
B. Denial of service due to patch availability
C. Lack of vendor support for decommissioning
D. Support for legacy protocols
A technician is auditing network security by connecting a laptop to open hardwired jacks within the facility to verify they cannot connect. Which of the following is being tested?
A. Layer 3 routing
B. Port security
C. Secure IMAP
D. S/MIME
A security engineer is analyzing the following line of JavaScript code that was found in a comment field on a web forum, which was recently involved in a security breach:
Given the line of code above, which of the following BEST represents the attack performed during the breach?
A. CSRF
B. DDoS
C. DoS
D. XSS
A Chief Executive Officer (CEO) suspects someone in the lab testing environment is stealing confidential information after working hours when no one else is around. Which of the following actions can help to prevent this specific threat?
A. Implement time-of-day restrictions.
B. Audit file access times.
C. Secretly install a hidden surveillance camera.
D. Require swipe-card access to enter the lab.
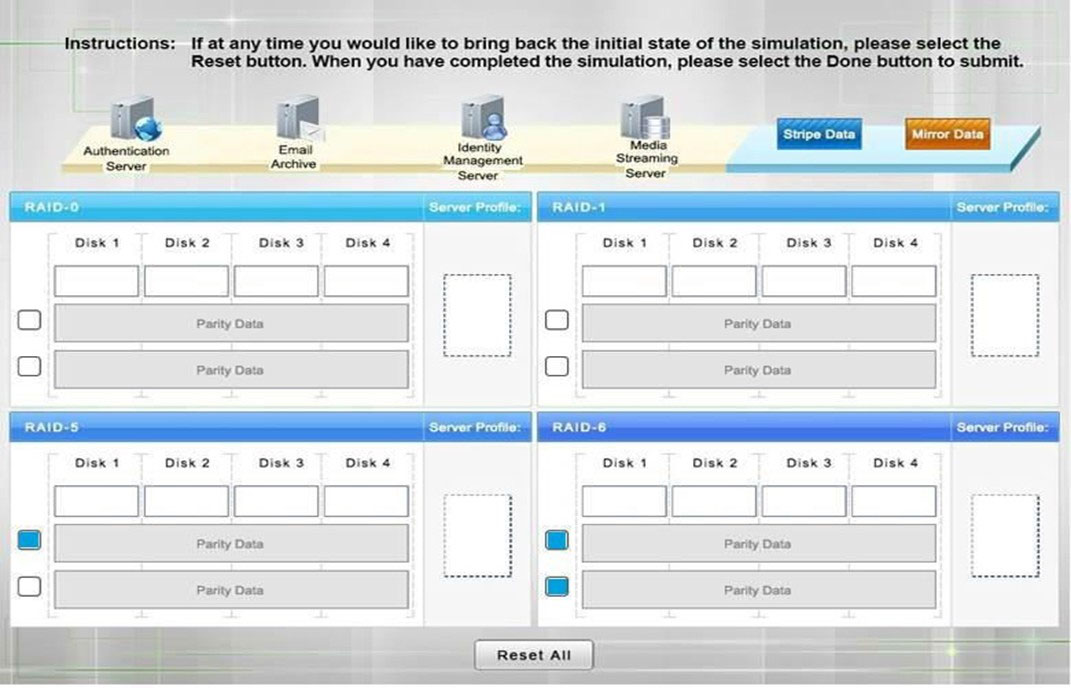
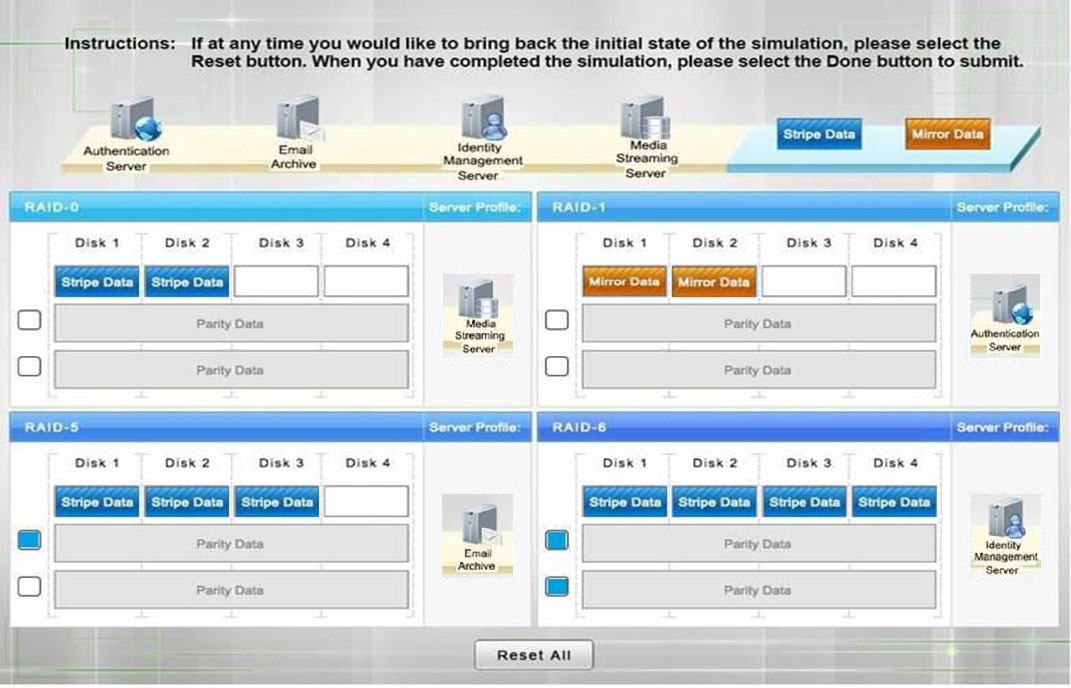
DRAG DROP - A security administrator is given the security and availability profiles for servers that are being deployed. 1. Match each RAID type with the correct configuration and MINIMUM number of drives. 2. Review the server profiles and match them with the appropriate RAID type based on integrity, availability, I/O, storage requirements. Instructions: ✑ All drive definitions can be dragged as many times as necessary ✑ Not all placeholders may be filled in the RAID configuration boxes ✑ If parity is required, please select the appropriate number of parity checkboxes ✑ Server profiles may be dragged only once If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue. Select and Place:
A systems administrator found a suspicious file in the root of the file system. The file contains URLs, usernames, passwords, and text from other documents being edited on the system. Which of the following types of malware would generate such a file?
A. Keylogger
B. Rootkit
C. Bot
D. RAT
An organization requires users to provide their fingerprints to access an application. To improve security, the application developers intend to implement multifactor authentication. Which of the following should be implemented?
A. Use a camera for facial recognition
B. Have users sign their name naturally
C. Require a palm geometry scan
D. Implement iris recognition
Which of the following serves to warn users against downloading and installing pirated software on company devices?
A. AUP
B. NDA
C. ISA
D. BPA
While performing surveillance activities, an attacker determines that an organization is using 802.1X to secure LAN access. Which of the following attack mechanisms can the attacker utilize to bypass the identified network security?
A. MAC spoofing
B. Pharming
C. Xmas attack
D. ARP poisoning
Which of the following would allow for the QUICKEST restoration of a server into a warm recovery site in a case in which server data mirroring is not enabled?
A. Full backup
B. Incremental backup
C. Differential backup
D. Snapshot
An organization would like to set up a more robust network access system. The network administrator suggests the organization move to a certificate-based authentication setup in which a client-side certificate is used while connecting. Which of the following EAP types should be used to meet these criteria?
A. EAP-TLS
B. EAP-FAST
C. EAP-MD5
D. EAP-TTLS
A security program manager wants to actively test the security posture of a system. The system is not yet in production and has no uptime requirement or active user base. Which of the following methods will produce a report which shows vulnerabilities that were actually exploited?
A. Peer review
B. Component testing
C. Penetration testing
D. Vulnerability testing
A government contracting company issues smartphones to employees to enable access to corporate resources. Several employees will need to travel to a foreign country for business purposes and will require access to their phones. However, the company recently received intelligence that its intellectual property is highly desired by the same country's government. Which of the following MDM configurations would BEST reduce the disk of compromise while on foreign soil?
A. Disable firmware OTA updates.
B. Disable location services.
C. Disable push notification services.
D. Disable wipe.
A company is terminating an employee for misbehavior. Which of the following steps is MOST important in the process of disengagement from this employee?
A. Obtain a list of passwords used by the employee.
B. Generate a report on outstanding projects the employee handled.
C. Have the employee surrender company identification.
D. Have the employee sign an NDA before departing.
Which of the following is a technical preventive control?
A. Two-factor authentication
B. DVR-supported cameras
C. Acceptable-use MOTD
D. Syslog server
Which of the following describes the maximum amount of time a mission essential function can operate without the systems it depends on before significantly impacting the organization?
A. MTBF
B. MTTR
C. RTO
D. RPO
A company network is currently under attack. Although security controls are in place to stop the attack, the security administrator needs more information about the types of attacks being used. Which of the following network types would BEST help the administrator gather this information?
A. DMZ
B. Guest network
C. Ad hoc
D. Honeynet
Which of the following security controls does an iris scanner provide?
A. Logical
B. Administrative
C. Corrective
D. Physical
E. Detective
F. Deterrent
The help desk is receiving numerous password change alerts from users in the accounting department. These alerts occur multiple times on the same day for each of the affected users' accounts. Which of the following controls should be implemented to curtail this activity?
A. Password Reuse
B. Password complexity
C. Password History
D. Password Minimum age
A director of IR is reviewing a report regarding several recent breaches. The director compiles the following statistic's -Initial IR engagement time frame -Length of time before an executive management notice went out -Average IR phase completion The director wants to use the data to shorten the response time. Which of the following would accomplish this?
A. CSIRT
B. Containment phase
C. Escalation notifications
D. Tabletop exercise
Which of the following strategies should a systems architect use to minimize availability risks due to insufficient storage capacity?
A. High availability
B. Scalability
C. Distributive allocation
D. Load balancing
A bank requires tellers to get manager approval when a customer wants to open a new account. A recent audit shows that there have been four cases in the previous year where tellers opened accounts without management approval. The bank president thought separation of duties would prevent this from happening. In order to implement a true separation of duties approach the bank could:
A. Require the use of two different passwords held by two different individuals to open an account
B. Administer account creation on a role based access control approach
C. Require all new accounts to be handled by someone else other than a teller since they have different duties
D. Administer account creation on a rule based access control approach
A member of the human resources department received the following email message after sending an email containing benefit and tax information to a candidate: `Your message has been quarantined for the following policy violation: external potential_PII. Please contact the IT security administrator for further details`. Which of the following BEST describes why this message was received?
A. The DLP system flagged the message.
B. The mail gateway prevented the message from being sent to personal email addresses.
C. The company firewall blocked the recipient’s IP address.
D. The file integrity check failed for the attached files.
A company was recently audited by a third party. The audit revealed the company's network devices were transferring files in the clear. Which of the following protocols should the company use to transfer files?
A. HTTPS
B. LDAPS
C. SCP
D. SNMPv3
While performing a penetration test, the technicians want their efforts to go unnoticed for as long as possible while they gather useful data about the network they are assessing. Which of the following would be the BEST choice for the technicians?
A. Vulnerability scanner
B. Offline password cracker
C. Packet sniffer
D. Banner grabbing
During a forensic investigation, which of the following must be addressed FIRST according to the order of volatility?
A. Hard drive
B. RAM
C. Network attached storage
D. USB flash drive
Which of the following is the proper way to quantify the total monetary damage resulting from an exploited vulnerability?
A. Calculate the ALE
B. Calculate the ARO
C. Calculate the MTBF
D. Calculate the TCO
A technician needs to implement a system which will properly authenticate users by their username and password only when the users are logging in from a computer in the office building. Any attempt to authenticate from a location other than the office building should be rejected. Which of the following MUST the technician implement?
A. Dual factor authentication
B. Transitive authentication
C. Single factor authentication
D. Biometric authentication
A security analyst is specifying requirements for a wireless network. The analyst must explain the security features provided by various architecture choices. Which of the following is provided by PEAP, EAP-TLS, and EAP-TTLS?
A. Key rotation
B. Mutual authentication
C. Secure hashing
D. Certificate pinning
An organization handling highly confidential information needs to update its systems. Which of the following is the BEST method to prevent data compromise?
A. Wiping
B. Degaussing
C. Shredding
D. Purging
To determine the ALE of a particular risk, which of the following must be calculated? (Choose two.)
A. ARO
B. ROI
C. RPO
D. SLE
E. RTO
A systems administrator wants to generate a self-signed certificate for an internal website. Which of the following steps should the systems administrator complete prior to installing the certificate on the server?
A. Provide the private key to a public CA.
B. Provide the public key to the internal CA.
C. Provide the public key to a public CA.
D. Provide the private key to the internal CA.
E. Provide the public/private key pair to the internal CA
F. Provide the public/private key pair to a public CA.
A security team has downloaded a public database of the largest collection of password dumps on the Internet. This collection contains the cleartext credentials of every major breach for the last four years. The security team pulls and compares users' credentials to the database and discovers that more than 30% of the users were still using passwords discovered in this list. Which of the following would be the BEST combination to reduce the risks discovered?
A. Password length, password encryption, password complexity
B. Password complexity, least privilege, password reuse
C. Password reuse, password complexity, password expiration
D. Group policy, password history, password encryption
Given the information below: MD5HASH document.doc 049eab40fd36caadlfab10b3cdf4a883 [1] Which of the following concepts are described above? (Choose two.)
A. Salting
B. Collision
C. Steganography
D. Hashing
E. Key stretching
A security administrator is configuring a RADIUS server for wireless authentication. The configuration must ensure client credentials are encrypted end-to-end between the client and the authenticator. Which of the following protocols should be configured on the RADIUS server? (Choose two.)
A. PAP
B. MSCHAP
C. PEAP
D. NTLM
E. SAML
Which of the following occurs when the security of a web application relies on JavaScript for input validation?
A. The integrity of the data is at risk.
B. The security of the application relies on antivirus.
C. A host-based firewall is required.
D. The application is vulnerable to race conditions.
A cryptographer has developed a new proprietary hash function for a company and solicited employees to test the function before recommending its implementation. An employee takes the plaintext version of a document and hashes it, then changes the original plaintext document slightly and hashes it, and continues repeating this process until two identical hash values are produced from two different documents. Which of the following BEST describes this cryptographic attack?
A. Brute force
B. Known plaintext
C. Replay
D. Collision
Given the log output: Max 15 00:15:23.431 CRT: #SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: msmith] [Source: 10.0.12.45] [localport: 23] at 00:15:23:431 CET Sun Mar 15 2015 Which of the following should the network administrator do to protect data security?
A. Configure port security for logons
B. Disable telnet and enable SSH
C. Configure an AAA server
D. Disable password and enable RSA authentication
A security analyst is determining the point of compromise after a company was hacked. The analyst checks the server logs and sees that a user account was logged in at night, and several large compressed files were exfiltrated. The analyst then discovers the user last logged in four years ago and was terminated. Which of the following should the security analyst recommend to prevent this type of attack in the future? (Choose two.)
A. Review and update the firewall settings
B. Restrict the compromised user account
C. Disable all user accounts that are not logged in to for 180 days
D. Enable a login banner prohibiting unauthorized use
E. Perform an audit of all company user accounts
F. Create a honeypot to catch the hacker
A system administrator wants to implement an internal communication system that will allow employees to send encrypted messages to each other. The system must also support non- repudiation. Which of the following implements all these requirements?
A. Bcrypt
B. Blowfish
C. PGP
D. SHA
Phishing emails frequently take advantage of high-profile catastrophes reported in the news. Which of the following principles BEST describes the weakness being exploited?
A. Intimidation
B. Scarcity
C. Authority
D. Social proof
A penetration tester was able to connect to a company's internal network and perform scans and staged attacks for the duration of the testing period without being noticed. The SIEM did not alert the security team to the presence of the penetration tester's devices on the network. Which of the following would provide the security team with notification in a timely manner?
A. Implement rogue system detection and sensors
B. Create a trigger on the IPS and alert the security team when unsuccessful logins occur
C. Decrease the correlation threshold for alerts on the SIEM
D. Run a credentialed vulnerability scan
The Chief Technology Officer (CTO) of a company, Ann, is putting together a hardware budget for the next 10 years. She is asking for the average lifespan of each hardware device so that she is able to calculate when she will have to replace each device. Which of the following categories BEST describes what she is looking for?
A. ALE
B. MTTR
C. MTBF
D. MTTF
Free Access Full SY0-501 Practice Questions Free
Want more hands-on practice? Click here to access the full bank of SY0-501 practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your SY0-501 certification journey!