SY0-501 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the SY0-501 certification? Take your preparation to the next level with our SY0-501 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a SY0-501 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic SY0-501 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
An administrator has concerns regarding the traveling sales team who works primarily from smart phones. Given the sensitive nature of their work, which of the following would BEST prevent access to the data in case of loss or theft?
A. Enable screensaver locks when the phones are not in use to prevent unauthorized access
B. Configure the smart phones so that the stored data can be destroyed from a centralized location
C. Configure the smart phones so that all data is saved to removable media and kept separate from the device
D. Enable GPS tracking on all smart phones so that they can be quickly located and recovered
A security team has downloaded a public database of the largest collection of password dumps on the Internet. This collection contains the cleartext credentials of every major breach for the last four years. The security team pulls and compares users' credentials to the database and discovers that more than 30% of the users were still using passwords discovered in this list. Which of the following would be the BEST combination to reduce the risks discovered?
A. Password length, password encryption, password complexity
B. Password complexity, least privilege, password reuse
C. Password reuse, password complexity, password expiration
D. Group policy, password history, password encryption
When used together, which of the following qualify as two-factor authentication?
A. Password and PIN
B. Smart card and PIN
C. Proximity card and smart card
D. Fingerprint scanner and iris scanner
A recent penetration test revealed several issues with a public-facing website used by customers. The testers were able to: ✑ Enter long lines of code and special characters ✑ Crash the system ✑ Gain unauthorized access to the internal application server ✑ Map the internal network The development team has stated they will need to rewrite a significant portion of the code used, and it will take more than a year to deliver the finished product. Which of the following would be the BEST solution to introduce in the interim?
A. Content fileting
B. WAF
C. TLS
D. IPS/IDS
E. UTM
A security analyst is working on a project that requires the implementation of a stream cipher. Which of the following should the analyst use?
A. Hash function
B. Elliptic curve
C. Symmetric algorithm
D. Public key cryptography
Which of the following types of security testing is the MOST cost-effective approach used to analyze existing code and identity areas that require patching?
A. Black box
B. Gray box
C. White box
D. Red team
E. Blue team
Employees receive a benefits enrollment email from the company's human resources department at the beginning of each year. Several users have reported receiving the email but are unable to log in to the website with their usernames and passwords. Users who enter the URL for the human resources website can log in without issue. Which of the following security issues is occurring?
A. Several users’ computers were not configured to use HTTPS to access the website
B. The human resources servers received a large number of requests, resulting in a DoS
C. The internal DNS server was compromised, directing users to a hacker’s server
D. Users received a social engineering email and were directed to an external website
An office manager found a folder that included documents with various types of data relating to corporate clients. The office manager notified the data included dates of birth, addresses, and phone numbers for the clients. The office manager then reported this finding to the security compliance officer. Which of the following portions of the policy would the security officer need to consult to determine if a breach has occurred?
A. Public
B. Private
C. PHI
D. PII
Joe, a new employee, discovered a thumb drive with the company's logo on it while walking in the parking lot. Joe was curious as to the contents of the drive and placed it into his work computer. Shortly after accessing the contents, he noticed the machine was running slower, started to reboot, and displayed new icons on the screen. Which of the following types of attacks occurred?
A. Social engineering
B. Brute force attack
C. MITM
D. DoS
A security consultant is setting up a new electronic messaging platform and wants to ensure the platform supports message integrity validation. Which of the following protocols should the consultant recommend?
A. S/MIME
B. DNSSEC
C. RADIUS
D. 802.11x
Which of the following is the BEST use of a WAF?
A. To protect sites on web servers that are publicly accessible
B. To allow access to web services of internal users of the organization
C. To maintain connection status of all HTTP requests
D. To deny access to all websites with certain contents
A new security policy in an organization requires that all file transfers within the organization be completed using applications that provide secure transfer. Currently, the organization uses FTP and HTTP to transfer files. Which of the following should the organization implement in order to be compliant with the new policy?
A. Replace FTP with SFTP and replace HTTP with TLS
B. Replace FTP with FTPS and replaces HTTP with TFTP
C. Replace FTP with SFTP and replace HTTP with Telnet
D. Replace FTP with FTPS and replaces HTTP with IPSec
When attempting to secure a mobile workstation, which of the following authentication technologies rely on the user's physical characteristics? (Choose two.)
A. MAC address table
B. Retina scan
C. Fingerprint scan
D. Two-factor authentication
E. CAPTCHA
F. Password string
An employee receives an email, which appears to be from the Chief Executive Officer (CEO), asking for a report of security credentials for all users. Which of the following types of attack is MOST likely occurring?
A. Policy violation
B. Social engineering
C. Whaling
D. Spear phishing
A small enterprise decides to implement a warm site to be available for business continuity in case of a disaster. Which of the following BEST meets its requirements?
A. A fully operational site that has all the equipment in place and full data backup tapes on site
B. A site used for its data backup storage that houses a full-time network administrator
C. An operational site requiring some equipment to be relocated as well as data transfer to the site
D. A site staffed with personnel requiring both equipment and data to be relocated there in case of disaster.
An organization employee resigns without giving adequate notice. The following day, it is determined that the employee is still in possession of several company- owned mobile devices. Which of the following could have reduced the risk of this occurring? (Choose two.)
A. Proper offboarding procedures
B. Acceptable use policies
C. Non-disclosure agreements
D. Exit interviews
E. Background checks
F. Separation of duties
Which of the following scenarios would make a DNS sinkhole effective in thwarting an attack?
A. An attacker is sniffing traffic to port 53, and the server is managed using unencrypted usernames and passwords.
B. An organization is experiencing excessive traffic on port 53 and suspects an attacker is trying to DoS the domain name server.
C. Malware is trying to resolve an unregistered domain name to determine if it is running in an isolated sandbox.
D. DNS routing tables have been compromised, and an attacker is rerouting traffic to malicious websites.
A Chief Information Officer (CIO) drafts an agreement between the organization and its employees. The agreement outlines ramifications for releasing information without consent and/or approvals. Which of the following BEST describes this type of agreement?
A. ISA
B. NDA
C. MOU
D. SLA
A security analyst is reviewing an assessment report that includes software versions, running services, supported encryption algorithms, and permission settings. Which of the following produced the report?
A. Vulnerability scanner
B. Protocol analyzer
C. Network mapper
D. Web inspector
A penetration tester is crawling a target website that is available to the public. Which of the following represents the actions the penetration tester is performing?
A. URL hijacking
B. Reconnaissance
C. White box testing
D. Escalation of privilege
A security analyst needs to generate a server certificate to be used for 802.1X and secure RDP connections. The analyst is unsure what is required to perform the task and solicits help from a senior colleague. Which of the following is the FIRST step the senior colleague will most likely tell the analyst to perform to accomplish this task?
A. Create an OCSP
B. Generate a CSR
C. Create a CRL
D. Generate a .pfx file.
A security administrator has configured a RADIUS and a TACACS+ server on the company's network. Network devices will be required to connect to the TACACS + server for authentication and send accounting information to the RADIUS server. Given the following information: RADIUS IP: 192.168.20.45 - TACACS+ IP: 10.23.65.7 - Which of the following should be configured on the network clients? (Choose two.)
A. Accounting port: TCP 389
B. Accounting port: UDP 1812
C. Accounting port: UDP 1813
D. Authentication port: TCP 49
E. Authentication port: TCP 88
F. Authentication port: UDP 636
An organization has hired a new remote workforce. Many new employees are reporting that they are unable to access the shared network resources while traveling. They need to be able to travel to and from different locations on a weekly basis. Shared offices are retained at the headquarters location. The remote workforce will have identical file and system access requirements, and must also be able to log in to the headquarters location remotely. Which of the following BEST represent how the remote employees should have been set up initially? (Choose two.)
A. User-based access control
B. Shared accounts
C. Group-based access control
D. Mapped drives
E. Individual accounts
F. Location-based policies
An organization is struggling to differentiate threats from normal traffic and access to systems. A security engineer has been asked to recommend a system that will aggregate data and provide metrics that will assist in identifying malicious actors or other anomalous activity throughout the environment. Which of the following solutions should the engineer recommend?
A. Web application firewall
B. SIEM
C. IPS
D. UTM
E. File integrity monitor
While performing a penetration test, the technicians want their efforts to go unnoticed for as long as possible while they gather useful data about the network they are assessing. Which of the following would be the BEST choice for the technicians?
A. Vulnerability scanner
B. Offline password cracker
C. Packet sniffer
D. Banner grabbing
A company is developing a new secure technology and requires computers being used for development to be isolated. Which of the following should be implemented to provide the MOST secure environment?
A. A perimeter firewall and IDS
B. An air gapped computer network
C. A honeypot residing in a DMZ
D. An ad hoc network with NAT
E. A bastion host
An application developer has neglected to include input validation checks in the design of the company's new web application. An employee discovers that repeatedly submitting large amounts of data, including custom code, to an application will allow the execution of the custom code at the administrator level. Which of the following BEST identifies this application attack?
A. Cross-site scripting
B. Clickjacking
C. Buffer overflow
D. Replay
A Chief Security Office's (CSO's) key priorities are to improve preparation, response, and recovery practices to minimize system downtime and enhance organizational resilience to ransomware attacks. Which of the following would BEST meet the CSO's objectives?
A. Use email-filtering software and centralized account management, patch high-risk systems, and restrict administration privileges on fileshares.
B. Purchase cyber insurance from a reputable provider to reduce expenses during an incident.
C. Invest in end-user awareness training to change the long-term culture and behavior of staff and executives, reducing the organization’s susceptibility to phishing attacks.
D. Implement application whitelisting and centralized event-log management, and perform regular testing and validation of full backups.
Joe, the security administrator, sees this in a vulnerability scan report: "The server 10.1.2.232 is running Apache 2.2.20 which may be vulnerable to a mod_cgi exploit.` Joe verifies that the mod_cgi module is not enabled on 10.1.2.232. This message is an example of:
A. a threat.
B. a risk.
C. a false negative.
D. a false positive.
A security analyst is performing a BIA. The analyst notes that in a disaster, failover systems must be up and running within 30 minutes. The failover systems must use backup data that is no older than one hour. Which of the following should the analyst include in the business continuity plan?
A. A maximum MTTR of 30 minutes
B. A maximum MTBF of 30 minutes
C. A maximum RTO of 60 minutes
D. A maximum RPO of 60 minutes
E. An SLA guarantee of 60 minutes
Which of the following implements a stream cipher?
A. File-level encryption
B. IKEv2 exchange
C. SFTP data transfer
D. S/MIME encryption
A systems administrator has installed a new UTM that is capable of inspecting SSL/TLS traffic for malicious payloads. All inbound network traffic coming from the Internet and terminating on the company's secure web servers must be inspected. Which of the following configurations would BEST support this requirement?
A. The web servers’ CA full certificate chain must be installed on the UTM.
B. The UTM certificate pair must be installed on the web servers.
C. The web servers’ private certificate must be installed on the UTM.
D. The UTM and web servers must use the same certificate authority.
Multiple employees receive an email with a malicious attachment that begins to encrypt their hard drives and mapped shares on their devices when it is opened. The network and security teams perform the following actions: ✑ Shut down all network shares. ✑ Run an email search identifying all employees who received the malicious message. ✑ Reimage all devices belonging to users who opened the attachment. Next, the teams want to re-enable the network shares. Which of the following BEST describes this phase of the incident response process?
A. Eradication
B. Containment
C. Recovery
D. Lessons learned
Which of the following is a random value appended to a credential that makes the credential less susceptible to compromise when hashed?
A. Nonce
B. Salt
C. OTP
D. Block cipher
E. IV
Which of the following is the BEST way for home users to mitigate vulnerabilities associated with IoT devices on their home networks?
A. Power off the devices when they are not in use.
B. Prevent IoT devices from contacting the Internet directly.
C. Apply firmware and software updates upon availability.
D. Deploy a bastion host on the home network.
Which of the following use the SSH protocol?
A. Stelnet
B. SCP
C. SNMP
D. FTPS
E. SSL
F. SFTP
A security analyst believes an employee's workstation has been compromised. The analyst reviews the system logs, but does not find any attempted logins. The analyst then runs the diff command, comparing the C:WindowsSystem32 directory and the installed cache directory. The analyst finds a series of files that look suspicious. One of the files contains the following commands:Which of the following types of malware was used?
A. Worm
B. Spyware
C. Logic bomb
D. Backdoor
Given the following requirements: ✑ Help to ensure non-repudiation ✑ Capture motion in various formats Which of the following physical controls BEST matches the above descriptions?
A. Camera
B. Mantrap
C. Security guard
D. Motion sensor
A company would like to prevent the use of a known set of applications from being used on company computers. Which of the following should the security administrator implement?
A. Whitelisting
B. Anti-malware
C. Application hardening
D. Blacklisting
E. Disable removable media
A systems administrator wants to protect data stored on mobile devices that are used to scan and record assets in a warehouse. The control must automatically destroy the secure container of mobile devices if they leave the warehouse. Which of the following should the administrator implement? (Choose two.)
A. Geofencing
B. Remote wipe
C. Near-field communication
D. Push notification services
E. Containerization
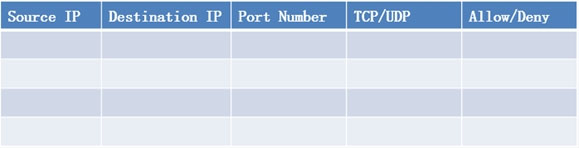
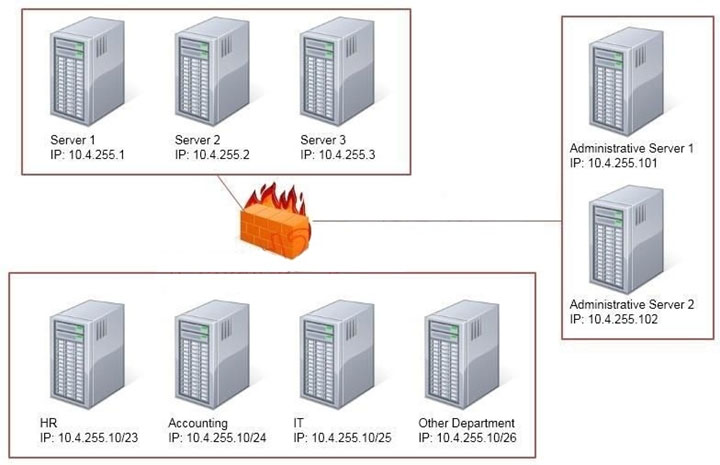
SIMULATION - Task: Configure the firewall (fill out the table) to allow these four rules: ✑ Only allow the Accounting computer to have HTTPS access to the Administrative server. ✑ Only allow the HR computer to be able to communicate with the Server 2 System over SCP. Allow the IT computer to have access to both the Administrative Server 1 and Administrative Server 2
A network technician is setting up a new branch for a company. The users at the new branch will need to access resources securely as if they were at the main location. Which of the following networking concepts would BEST accomplish this?
A. Virtual network segmentation
B. Physical network segmentation
C. Site-to-site VPN
D. Out-of-band access
E. Logical VLANs
An organization's internal auditor discovers that large sums of money have recently been paid to a vendor that management does not recognize. The IT security department is asked to investigate the organizations the organization's ERP system to determine how the accounts payable module has been used to make these vendor payments. The IT security department finds the following security configuration for the accounts payable module: ✑ New Vendor Entry `" Required Role: Accounts Payable Clerk ✑ New Vendor Approval `" Required Role: Accounts Payable Clerk ✑ Vendor Payment Entry `" Required Role: Accounts Payable Clerk ✑ Vendor Payment Approval `" Required Role: Accounts Payable Manager Which of the following changes to the security configuration of the accounts payable module would BEST mitigate the risk? A.B.
C.
D.
A security analyst is performing a quantitative risk analysis. The risk analysis should show the potential monetary loss each time a threat or event occurs. Given this requirement, which of the following concepts would assist the analyst in determining this value? (Choose two.)
A. ALE
B. AV
C. ARO
D. EF
E. ROI
After a merger between two companies a security analyst has been asked to ensure that the organization's systems are secured against infiltration by any former employees that were terminated during the transition. Which of the following actions are MOST appropriate to harden applications against infiltration by former employees? (Choose two.)
A. Monitor VPN client access
B. Reduce failed login out settings
C. Develop and implement updated access control policies
D. Review and address invalid login attempts
E. Increase password complexity requirements
F. Assess and eliminate inactive accounts
An email recipient is unable to open a message encrypted through PKI that was sent from another organization. Which of the following does the recipient need to decrypt the message?
A. The sender’s private key
B. The recipient’s private key
C. The recipient’s public key
D. The CA’s root certificate
E. The sender’s public key
F. An updated CRL
An organization requires users to provide their fingerprints to access an application. To improve security, the application developers intend to implement multifactor authentication. Which of the following should be implemented?
A. Use a camera for facial recognition
B. Have users sign their name naturally
C. Require a palm geometry scan
D. Implement iris recognition
A small company's Chief Executive Officer (CEO) has asked its Chief Security Officer (CSO) to improve the company's security posture quickly with regard to targeted attacks. Which of the following should the CSO conduct FIRST?
A. Survey threat feeds from services inside the same industry.
B. Purchase multiple threat feeds to ensure diversity and implement blocks for malicious traffic
C. Conduct an internal audit against industry best practices to perform a qualitative analysis.
D. Deploy a UTM solution that receives frequent updates from a trusted industry vendor.
A security analyst is hardening a web server, which should allow a secure certificate-based session using the organization's PKI infrastructure. The web server should also utilize the latest security techniques and standards. Given this set of requirements, which of the following techniques should the analyst implement to BEST meet these requirements? (Choose two.)
A. Install an X- 509-compliant certificate.
B. Implement a CRL using an authorized CA.
C. Enable and configure TLS on the server.
D. Install a certificate signed by a public CA.
E. Configure the web server to use a host header.
A security analyst discovers that a company's username and password database was posted on an Internet forum. The username and passwords are stored in plain text. Which of the following would mitigate the damage done by this type of data exfiltration in the future?
A. Create DLP controls that prevent documents from leaving the network
B. Implement salting and hashing.
C. Configure the web content filter to block access to the forum.
D. Increase password complexity requirements.
Free Access Full SY0-501 Practice Exam Free
Looking for additional practice? Click here to access a full set of SY0-501 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your SY0-501 certification journey!