SCS-C01 Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the SCS-C01 exam? Start with our SCS-C01 Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a SCS-C01 practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free SCS-C01 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
A user is implementing a third-party web application on an Amazon EC2 instance. All client communications must be over HTTPS, and traffic must be terminated before it reaches the instance. Communication to the instance must be over port 80. Company policy requires that workloads reside in private subnets. Which solution meets these requirements?
A. Create an Application Load Balancer. Add an HTTP listener for port 80 to redirect traffic to HTTPS on port 443. Add another listener with an AWS Certificate Manager (ACM) certificate for termination and a rule that forwards to the target instance through port 80.
B. Allocate an Elastic IP address that has SSL termination activated. Associate the Elastic IP address with the instance on port 80.
C. Create a Gateway Load Balancer. Add an HTTP listener for port 80 to redirect traffic to HTTPS on port 443. Add another listener with an AWS Certificate Manager (ACM) certificate for termination and a rule that forwards to the target instance through port 80.
D. Implement a Network Load Balancer. Add an HTTP listener for port 80 to redirect traffic to HTTPS on port 443. Add another listener with an AWS Certificate Manager (ACM) certificate for termination and a rule that forwards to the target instance through port 80.
A security engineer needs to configure an Amazon S3 bucket policy to restrict access to an S3 bucket that is named DOC-EXAMPLE-BUCKET. The policy must allow access to only DOC-EXAMPLE-BUCKET from only the following endpoint: vpce-1a2b3c4d. The policy must deny all access to DOC-EXAMPLE-BUCKET if the specified endpoint is not used. Which bucket policy statement meets these requirements?
A.

B.

C.

D.

A company has a security team that manages its AWS Key Management Service (AWS KMS) CMKs. Members of the security team must be the only ones to administer the CMKs. The company's application team has a software process that needs temporary access to the CMKS occasionally. The security team must provide the application team’s software process access to the CMKs. Which solution meets these requirements with the LEAST overhead?
A. Export the CMK key material to an on-premises hardware security module (HSM). Give the application team access to the key material.
B. Edit the key policy that grants the security team access to the CMKs by adding the application team as principals. Revert this change when the application team no longer needs access.
C. Create a key grant to allow the application team to use the CMKs. Revoke the grant when the application team no longer needs access.
D. Create a new CMK by generating key material on premises. Import the key material to AWS KMS whenever the application team needs access. Grant the application team permissions to use the CMK.
A company recently performed an annual security assessment of its AWS environment. The assessment showed the audit logs are not available beyond 90 days and that unauthorized changes to IAM policies are made without detection. How should a Security Engineer resolve these issues?
A. Create an Amazon S3 lifecycle policy that archives AWS CloudTrail trail logs to Amazon S3 Glacier after 90 days. Configure Amazon Inspector to provide a notification when a policy change is made to resources.
B. Configure AWS Artifact to archive AWS CloudTrail logs. Configure AWS Trusted Advisor to provide a notification when a policy change is made to resources.
C. Configure Amazon CloudWatch to export log groups to Amazon S3. Configure AWS CloudTrail to provide a notification when a policy change is made to resources.
D. Create an AWS CloudTrail trail that stores audit logs in Amazon S3. Configure an AWS Config rule to provide a notification when a policy change is made to resources.
A security engineer must use AWS Key Management Service (AWS KMS) to design a key management solution for a set of Amazon Elastic Block Store (Amazon EBS) volumes that contain sensitive data. The solution needs to ensure that the key material automatically expires in 90 days. Which solution meets these criteria?
A. A customer managed CMK that uses customer provided key material
B. A customer managed CMK that uses AWS provided key material
C. An AWS managed CMK
D. Operation system-native encryption that uses GnuPG
A company has an AWS Lambda function that requires access to an Amazon S3 bucket. The company’s security policy requires that connections to Amazon S3 are over a private network and are secure. The company has configured a gateway VPC endpoint in the VPC to allow access to Amazon S3. The company has configured the Lambda function to run inside the VPC. Additionally, the company has configured the Lambda function to use a private subnet that has a route to the internet through a NAT gateway. Other resources in the VPC use this private subnet to access the internet successfully. When the Lambda function runs, it uses the NAT gateway instead of the gateway VPC endpoint to access Amazon S3. What can a security engineer do to ensure that the Lambda function uses the gateway VPC endpoint for Amazon S3?
A. Remove the route to the NAT gateway within the route table of the private subnet that the Lambda function uses.
B. Associate the gateway VPC endpoint with the route table of the private subnet that the Lambda function uses.
C. Adjust the gateway VPC endpoint policy to allow access from the Lambda function’s network interface address.
D. Configure the Lambda function’s security group to allow connections to the S3 network address space.
A company receives an email message from the AWS Abuse team. The message states that an IAM user in the company's AWS account has had an associated access key and secret access key pair published in public code repositories. The identified AM user is designated as a service account. The IAM user uses hardcoded credentials in a critical customer-facing production application. There are no signs of a compromise within the company's AWS account. The company's security team must address this situation by implementing a solution that minimizes application downtime. What is the correct order of actions for the security team to take to meet these requirements?
A. Delete any AWS Management Console credentials that are associated with the IAM user. Create a new access key and secret access key pair for the IAM user. Update the application to use the new credentials. Inactivate the publicly exposed IAM access key. Revoke any temporary AWS Security Token Service (AWS STS) credentials that are associated with the IAM user.
B. Revoke any temporary AWS Security Token Service (AWS STS) credentials that are associated with the IAM user. Inactivate the publicly exposed IAM access key. Create a new access key and secret access key pair for the IAM user. Update the application to use the new credentials. Delete any AWS Management Console credentials that are associated with the IAM user.
C. Inactivate the publicly exposed IAM access key. Create a new access key and secret access key pair for the IAM user. Update the application to use the new credentials. Revoke any temporary AWS Security Token Service (AWS STS) credentials that are associated with the IAM user. Delete any AWS Management Console credentials that are associated with the IAM user.
D. Delete any AWS Management Console credentials that are associated with the IAM user. Create a new access key and secret access key pair for the IAM user. Inactivate the publicly exposed IAM access key. Revoke any temporary AWS Security Token Service (AWS STS) credentials that are associated with the IAM user. Update the application to use the new credentials.
A company's architecture requires that its three Amazon EC2 instances run behind an Application Load Balancer (ALB). The EC2 instances transmit sensitive data between each other. Developers use SSL certificates to encrypt the traffic between the public users and the ALB. However, the Developers are unsure of how to encrypt the data in transit between the ALB and the EC2 instances and the traffic between the EC2 instances. Which combination of activities must the company implement to meet its encryption requirements? (Choose two.)
A. Configure SSL/TLS on the EC2 instances and configure the ALB target group to use HTTPS.
B. Ensure that all resources are in the same VPC so the default encryption provided by the VPC is used to encrypt the traffic between the EC2 instances.
C. In the ALB, select the default encryption to encrypt the traffic between the ALB and the EC2 instances.
D. In the code for the application, include a cryptography library and encrypt the data before sending it between the EC2 instances.
E. Configure AWS Direct Connect to provide an encrypted tunnel between the EC2 instances.
A company runs a cron job on an Amazon EC2 instance on a predefined schedule. The cron job calls a bash script that encrypts a 2 KB file. A security engineer creates an AWS Key Management Service (AWS KMS) CMK with a key policy. The key policy and the EC2 instance role have the necessary configuration for this job. Which process should the bash script use to encrypt the file?
A. Use the aws kms encrypt command to encrypt the file by using the existing CMK.
B. Use the aws kms create-grant command to generate a grant for the existing CMK.
C. Use the aws kms encrypt command to generate a data key. Use the plaintext data key to encrypt the file.
D. Use the aws kms generate-data-key command to generate a data key. Use the encrypted data key to encrypt the file.
Auditors for a health care company have mandated that all data volumes be encrypted at rest. Infrastructure is deployed mainly via AWS CloudFormation; however, third-party frameworks and manual deployment are required on some legacy systems. What is the BEST way to monitor, on a recurring basis, whether all EBS volumes are encrypted?
A. On a recurring basis, update all IAM user policies to require that EC2 instances are created with an encrypted volume.
B. Configure an AWS Config rule to run on a recurring basis for volume encryption.
C. Set up Amazon Inspector rules for volume encryption to run on a recurring schedule.
D. Use CloudWatch Logs to determine whether instances were created with an encrypted volume.
A company is collecting AWS CloudTrail log data from multiple AWS accounts by managing individual trails in each account and forwarding log data to a centralized Amazon S3 bucket residing in a log archive account. After CloudTrail introduced support for AWS Organizations trails, the company decided to further centralize management and automate deployment of the CloudTrail logging capability across all of its AWS accounts. The company's security engineer created an AWS Organizations trail in the master account, enabled server-side encryption with AWS KMS managed keys (SSE- KMS) for the log files, and specified the same bucket as the storage location. However, the engineer noticed that logs recorded by the new trail were not delivered to the bucket. Which factors could cause this issue? (Choose two.)
A. The CMK key policy does not allow CloudTrail to make encrypt and decrypt API calls against the key.
B. The CMK key policy does not allow CloudTrail to make GenerateDatakey API calls against the key.
C. The IAM role used by the CloudTrail trail does not have permissions to make PutObject API calls against a folder created for the Organizations trail.
D. The S3 bucket policy does not allow CloudTrail to make PutObject API calls against a folder created for the Organizations trail.
E. The CMK key policy does not allow the IAM role used by the CloudTrail trail to use the key for cryptographical operations.
A security engineer is attempting to assign a virtual multi-factor authentication (MFA) device to an IAM user whose current virtual MFA device is faulty. The security engineer receives an error message that indicates that the security engineer is not authorized to perform iam:DeleteVirtualMFADevice. The IAM role that the security engineer is using has the correct permissions to delete, list, and create a virtual MFA device. The IAM user also has permissions to delete their own virtual MFA device, but only if the IAM user is authenticated with MFA. What should the security engineer do to resolve this issue?
A. Modify the policy for the IAM user to allow the IAM user to delete the virtual MFA device without using MFA authentication.
B. Sign in as the AWS account root user. Modify the MFA device by using the IAM console to generate a new synchronization quick response (QR) code.
C. Use the AWS CLI or AWS API to find the ARN of the virtual MFA device and to delete the device.
D. Sign in as the AWS account root user. Delete the virtual MFA device by using the IAM console.
A company is hosting multiple applications within a single VPC in its AWS account. The applications are running behind an Application Load Balancer that is associated with an AWS WAF web ACL. The company's security team has identified that multiple port scans are originating from a specific range of IP addresses on the internet. A security engineer needs to deny access from the offending IP addresses. Which solution will meet these requirements?
A. Modify the AWS WAF web ACL with an IP set match rule statement to deny incoming requests from the IP address range.
B. Add a rule to all security groups to deny the incoming requests from the IP address range.
C. Modify the AWS WAF web ACL with a rate-based rule statement to deny incoming requests from the IP address range.
D. Configure the AWS WAF web ACL with regex match conditions. Specify a pattern set to deny the incoming requests based on the match condition.
Some highly sensitive analytics workloads are to be moved to Amazon EC2 hosts. Threat modeling has found that a risk exists where a subnet could be maliciously or accidentally exposed to the internet. Which of the following mitigations should be recommended?
A. Use AWS Config to detect whether an Internet Gateway is added and use an AWS Lambda function to provide auto-remediation.
B. Within the Amazon VPC configuration, mark the VPC as private and disable Elastic IP addresses.
C. Use IPv6 addressing exclusively on the EC2 hosts, as this prevents the hosts from being accessed from the internet.
D. Move the workload to a Dedicated Host, as this provides additional network security controls and monitoring.
An organization has a system in AWS that allows a large number of remote workers to submit data files. File sizes vary from a few kilobytes to several megabytes. A recent audit highlighted a concern that data files are not encrypted while in transit over untrusted networks. Which solution would remediate the audit finding while minimizing the effort required?
A. Upload an SSL certificate to IAM, and configure Amazon CloudFront with the passphrase for the private key.
B. Call KMS.Encrypt() in the client, passing in the data file contents, and call KMS.Decrypt() server-side.
C. Use AWS Certificate Manager to provision a certificate on an Elastic Load Balancing in front of the web service’s servers.
D. Create a new VPC with an Amazon VPC VPN endpoint, and update the web service’s DNS record.
A company has a single AWS account and uses an Amazon EC2 instance to test application code. The company recently discovered that the instance was compromised. The instance was serving up malware. The analysis of the instance showed that the instance was compromised 35 days ago. A security engineer must implement a continuous monitoring solution that automatically notifies the company’s security team about compromised instances through an email distribution list for high severity findings. The security engineer must implement the solution as soon as possible. Which combination of steps should the security engineer take to meet these requirements? (Choose three.)
A. Enable AWS Security Hub in the AWS account.
B. Enable Amazon GuardDuty in the AWS account.
C. Create an Amazon Simple Notification Service (Amazon SNS) topic. Subscribe the security team’s email distribution list to the topic.
D. Create an Amazon Simple Queue Service (Amazon SQS) queue. Subscribe the security team’s email distribution list to the queue.
E. Create an Amazon EventBridge (Amazon CloudWatch Events) rule for GuardDuty findings of high severity. Configure the rule to publish a message to the topic.
F. Create an Amazon EventBridge (Amazon CloudWatch Events) rule for Security Hub findings of high severity. Configure the rule to publish a message to the queue.
A security engineer needs to ensure their company's use of AWS meets AWS security best practices. As part of this, the AWS account root user must not be used for daily work. The root user must be monitored for use, and the security team must be alerted as quickly as possible if the root user is used. Which solution meets these requirements?
A. Set up an Amazon CloudWatch Events rule that triggers an Amazon SNS notification.
B. Create root user access keys. Use an AWS Lambda function to parse AWS CloudTrail logs from Amazon S3 and generate notifications using Amazon SNS.
C. Set up a rule in AWS Config to trigger root user events. Trigger an AWS Lambda function and generate notifications using Amazon SNS.
D. Use Amazon Inspector to monitor the usage of the root user and generate notifications using Amazon SNS.
A company's security information events management (SIEM) tool receives new AWS CloudTrail logs from an Amazon S3 bucket that is configured to send all object created event notifications to an Amazon SNS topic. An Amazon SQS queue is subscribed to this SNS topic. The company's SIEM tool then polls this SQS queue for new messages using an IAM role and fetches new log events from the S3 bucket based on the SQS messages. After a recent security review that resulted in restricted permissions, the SIEM tool has stopped receiving new CloudTrail logs. Which of the following are possible causes of this issue? (Choose three.)
A. The SQS queue does not allow the SQS:SendMessage action from the SNS topic.
B. The SNS topic does not allow the SNS:Publish action from Amazon S3.
C. The SNS topic is not delivering raw messages to the SQS queue.
D. The S3 bucket policy does not allow CloudTrail to perform the PutObject action.
E. The IAM role used by the SIEM tool does not have permission to subscribe to the SNS topic.
F. The IAM role used by the SIEM tool does not allow the SQS:DeleteMessage action.
A security team is working on a solution that will use Amazon EventBridge (Amazon CloudWatch Events) to monitor new Amazon S3 objects. The solution will monitor for public access and for changes to any S3 bucket policy or setting that result in public access. The security team configures EventBridge to watch for specific API calls that are logged from AWS CloudTrail. EventBridge has an action to send an email notification through Amazon Simple Notification Service (Amazon SNS) to the security team immediately with details of the API call. Specifically, the security team wants EventBridge to watch for the s3:PutObjectAcl, s3:DeleteBucketPolicy, and s3:PutBucketPolicy API invocation logs from CloudTrail. While developing the solution in a single account, the security team discovers that the s3:PutObjectAcl API call does not invoke an EventBridge event. However, the s3:DeleteBucketPolicy API call and the s3:PutBucketPolicy API call do invoke an event. The security team has enabled CloudTrail for AWS management events with a basic configuration in the AWS Region in which EventBridge is being tested. Verification of the EventBridge event pattern indicates that the pattern is set up correctly. The security team must implement a solution so that the s3:PutObjectAcl API call will invoke an EventBridge event. The solution must not generate false notifications. Which solution will meet these requirements?
A. Modify the EventBridge event pattern by selecting Amazon S3. Select All Events as the event type.
B. Modify the EventBridge event pattern by selecting Amazon S3. Select Bucket Level Operations as the event type.
C. Enable CloudTrail Insights to identify unusual API activity.
D. Enable CloudTrail to monitor data events for read and write operations to S3 buckets.
A company uses Microsoft Active Directory for access management for on-premises resources, and wants to use the same mechanism for accessing its AWS accounts. Additionally, the Development team plans to launch a public-facing application for which they need a separate authentication solution. Which combination of the following would satisfy these requirements? (Choose two.)
A. Set up domain controllers on Amazon EC2 to extend the on-premises directory to AWS.
B. Establish network connectivity between on-premises and the user’s VPC.
C. Use Amazon Cognito user pools for application authentication.
D. Use AD Connector for application authentication.
E. Set up federated sign-in to AWS through ADFS and SAML.
A company is operating a website using Amazon CloudFront. CloudFront serves some content from Amazon S3 and other content from web servers running on Amazon EC2 instances behind an Application Load Balancer (ALB). Amazon DynamoDB is used as the data store. The company already uses AWS Certificate Manager (ACM) to store a public TLS certificate that can optionally secure connections between the website users and CloudFront. The company has a new requirement to enforce end-to-end encryption in transit. Which combination of steps should the company take to meet this requirement? (Choose three.)
A. Update the CloudFront distribution, configuring it to optionally use HTTPS when connecting to origins on Amazon S3.
B. Update the web application configuration on the web servers to use HTTPS instead of HTTPS when connecting to DynamoDB.
C. Update the CloudFront distribution to redirect HTTP connections to HTTPS.
D. Configure the web servers on the EC2 instances to listen using HTTPS using the public ACM TLS certificate. Update the ALB to connect to the target group using HTTPS.
E. Update the ALB listener to listen using HTTPS using the public ACM TLS certificate. Update the CloudFront distribution to connect to the HTTPS listener.
F. Create a TLS certificate. Configure the web servers on the EC2 instances to use HTTPS only with that certificate. Update the ALB to connect to the target group using HTTPS.
A development team is using an AWS Key Management Service (AWS KMS) CMK to try to encrypt and decrypt a secure string parameter from AWS Systems Manager Parameter Store. However, the development team receives an error message on each attempt. Which issues that are related to the CMK could be reasons for the error? (Choose two.)
A. The CMK is used in the attempt does not exist.
B. The CMK is used in the attempt needs to be rotated.
C. The CMK is used in the attempt is using the CMK’s key ID instead of the CMK ARN.
D. The CMK is used in the attempt is not enabled.
E. The CMK is used in the attempt is using an alias.
A company has two web applications that run on Amazon EC2 and Amazon S3. The applications failed an HTTP security audit, and users are reporting latency issues. The applications need to deliver web content at low latencies while improving security and privacy for users and content providers. The company must implement a solution that does not require changes to the application code. Which combination of actions should the company take to meet these requirements? (Choose two.)
A. Deploy Amazon API Gateway. Cache the endpoint’s responses.
B. Configure Amazon API Gateway with a request parameter-based AWS Lambda authorizer to add HTTP security headers on origin responses.
C. Write a Lambda@Edge function to add HTTP security headers on origin responses.
D. Configure Amazon CloudFront. Create a distribution for the EC2 and S3 origins.
E. Implement an Application Load Balancer (ALB) to honor the connection header from the incoming client request after forwarding the response back to the client.
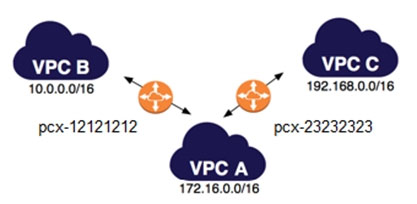
A company has multiple VPCs in their account that are peered, as shown in the diagram. A Security Engineer wants to perform penetration tests of the Amazon EC2 instances in all three VPCs. How can this be accomplished? (Choose two.)
A. Deploy a pre-authorized scanning engine from the AWS Marketplace into VPC B, and use it to scan instances in all three VPCs. Do not complete the penetration test request form.
B. Deploy a pre-authorized scanning engine from the Marketplace into each VPC, and scan instances in each VPC from the scanning engine in that VPC. Do not complete the penetration test request form.
C. Create a VPN connection from the data center to VPC A. Use an on-premises scanning engine to scan the instances in all three VPCs. Complete the penetration test request form for all three VPCs.
D. Create a VPN connection from the data center to each of the three VPCs. Use an on-premises scanning engine to scan the instances in each VPC. Do not complete the penetration test request form.
E. Create a VPN connection from the data center to each of the three VPCs. Use an on-premises scanning engine to scan the instances in each VPC. Complete the penetration test request form for all three VPCs.
An audit determined that a company's Amazon EC2 instance security group violated company policy by allowing unrestricted incoming SSH traffic. A security engineer must implement a near-real-time monitoring and alerting solution that will notify administrators of such violations. Which solution meets these requirements with the MOST operational efficiency?
A. Create a recurring Amazon Inspector assessment run that runs every day and uses the Network Reachability package. Create an Amazon CloudWatch rule that invokes an AWS Lambda function when an assessment rum starts. Configure the Lambda function to retrieve and evaluate the assessment run report when it completes. Configure the Lambda function also to publish an Amazon Simple Notification Service (Amazon SNS) notification is there are any violations for unrestricted incoming SSH traffic.
B. Use the restricted-ssh AWS Config managed rule that is invoked by security group configuration changes that are not compliant. Use the AWS Config remediation feature to publish a message to an Amazon Simple Notification Service (Amazon SNS) topic.
C. Configure VPC Flow Logs for the VPC, and specify an Amazon CloudWatch Logs group. Subscribe the CloudWatch Logs group to an AWS Lambda function that parses new log entries, detects successful connections on port 22, and publishes a notification through Amazon Simple Notification Service (Amazon SNS).
D. Create a recurring Amazon Inspector assessment run that runs every day and uses the Security Best Practices package. Create an Amazon CloudWatch rule that invokes an AWS Lambda function when an assessment rum starts. Configure the Lambda function to retrieve and evaluate the assessment run report when it completes. Configure the Lambda function also to publish an Amazon Simple Notification Service (Amazon SNS) notification is there are any violations for unrestricted incoming SSH traffic.
A company maintains an open-source application that is hosted on a public GitHub repository. While creating a new commit to the repository, an engineer uploaded their AWS access key and secret access keys. The engineer reported the mistake to a manager, and the manager immediately disabled the access key. The company needs to assess the impact of the exposed access key. A security engineer must recommend a solution that requires the least possible managerial overhead. Which solution meets these requirements?
A. Analyze an AWS Identity and Access Management (IAM) use report from AWS Trusted Advisor to see when the access key was last used.
B. Analyze Amazon CloudWatch Logs for activity by searching for the access key.
C. Analyze VPC flow logs for activity by searching for the access key.
D. Analyze a credential report in AWS Identity and Access Management (IAM) to see when the access key was last used.
A recent security audit found that AWS CloudTrail logs are insufficiently protected from tampering and unauthorized access. Which actions must the Security Engineer take to access these audit findings? (Choose three.)
A. Ensure CloudTrail log file validation is turned on.
B. Configure an S3 lifecycle rule to periodically archive CloudTrail logs into Glacier for long-term storage.
C. Use an S3 bucket with tight access controls that exists in a separate account.
D. Use Amazon Inspector to monitor the file integrity of CloudTrail log files.
E. Request a certificate through ACM and use a generated certificate private key to encrypt CloudTrail log files.
F. Encrypt the CloudTrail log files with server-side encryption AWS KMS-managed keys (SSE-KMS).
During a recent security audit, it was discovered that multiple teams in a large organization have placed restricted data in multiple Amazon S3 buckets, and the data may have been exposed. The auditor has requested that the organization identify all possible objects that contain personally identifiable information (PII) and then determine whether this information has been accessed. What solution will allow the Security team to complete this request?
A. Using Amazon Athena, query the impacted S3 buckets by using the PII query identifier function. Then, create a new Amazon CloudWatch metric for Amazon S3 object access to alert when the objects are accessed.
B. Enable Amazon Macie on the S3 buckets that were impacted, then perform data classification. For identified objects that contain PII, use the research function for auditing AWS CloudTrail logs and S3 bucket logs for GET operations.
C. Enable Amazon GuardDuty and enable the PII rule set on the S3 buckets that were impacted, then perform data classification. Using the PII findings report from GuardDuty, query the S3 bucket logs by using Athena for GET operations.
D. Enable Amazon Inspector on the S3 buckets that were impacted, then perform data classification. For identified objects that contain PII, query the S3 bucket logs by using Athena for GET operations.
A security engineer needs to implement an intrusion detection system (IDS) for a shipping company. The findings from the system must generate alerts that can be sent to an email distribution group that the company’s operations team uses. The security engineer must maximize the coverage that the IDS provides. Which combination of steps should the security engineer take to meet these requirements? (Choose two.)
A. Create an AWS CloudTrail trail to capture management events and Amazon S3 data events. Create VPC flow logs for all VPCs. Specify for the flow logs to capture all traffic.
B. Create an AWS CloudTrail trail to capture management events and Amazon S3 data events. Create VPC flow logs for all VPCS. Specify for the flow logs to capture accepted traffic.
C. Configure Amazon GuardDuty. Create an Amazon EventBridge (Amazon CloudWatch Events) rule to forward finding events to an Amazon Simple Notification Service (Amazon SNS) topic
D. Configure AWS Security Hub. Create an Amazon EventBridge (Amazon CloudWatch Events) rue to forward finding events to an Amazon Simple Notification Service (Amazon SNS) topic.
E. Create an AWS CloudTrail trail to capture management events and Amazon S3 data events. Configure an AWS Lambda function to analyze VPC flow logs and to inspect all flow log traffic that matches the ACCEPT filter type.
A Security Engineer is asked to update an AWS CloudTrail log file prefix for an existing trail. When attempting to save the change in the CloudTrail console, the Security Engineer receives the following error message: `There is a problem with the bucket policy.` What will enable the Security Engineer to save the change?
A. Create a new trail with the updated log file prefix, and then delete the original trail. Update the existing bucket policy in the Amazon S3 console with the new log file prefix, and then update the log file prefix in the CloudTrail console.
B. Update the existing bucket policy in the Amazon S3 console to allow the Security Engineer’s Principal to perform PutBucketPolicy, and then update the log file prefix in the CloudTrail console.
C. Update the existing bucket policy in the Amazon S3 console with the new log file prefix, and then update the log file prefix in the CloudTrail console.
D. Update the existing bucket policy in the Amazon S3 console to allow the Security Engineer’s Principal to perform GetBucketPolicy, and then update the log file prefix in the CloudTrail console.
A company hosts business-critical applications on Amazon EC2 instances in a VPC. The VPC uses default DHCP options sets. A security engineer needs to log all DNS queries that internal resources make in the VPC. The security engineer also must create a list of the most common DNS queries over time. Which solution will meet these requirements?
A. Install the Amazon CloudWatch agent on each EC2 instance in the VPC. Use the CloudWatch agent to stream the DNS query logs to an Amazon CloudWatch Logs log group. Use CloudWatch metric filters to automatically generate metrics that list the most common DNS queries.
B. Install a BIND DNS server in the VPC. Create a bash script to list the DNS request number of common DNS queries from the BIND logs.
C. Create VPC flow logs for all subnets in the VPStream the flow logs to an Amazon CloudWatch Logs log group. Use CloudWatch Logs Insights to list the most common DNS queries for the log group in a custom dashboard.
D. Configure Amazon Route 53 Resolver query logging. Add an Amazon CloudWatch Logs log group as the destination. Use Amazon CloudWatch Contributor Insights to analyze the data and create time series that display the most common DNS queries.
A company is running batch workloads that use containers on Amazon Elastic Container Service (Amazon ECS). The company needs a secure solution for storing API keys that are required for integration with external services. The company's security policy states that API keys must not be stored or transmitted in plaintext. The company's IT team currently rotates the API keys manually. A security engineer must recommend a solution that meets the security requirements and automates the rotation of the API keys Which solution should the security engineer recommend?
A. Use a secure string parameter in AWS Systems Manager Parameter Store. Activate the feature for automatic rotation.
B. Use Amazon EC2 user data for storing the API keys. Set up a scheduled AWS Lambda function to automatically rotate the API keys.
C. Use AWS Fargate to store the API keys. Set up a scheduled AWS Lambda function to automatically rotate the API keys.
D. Use AWS Secrets Manager to store the API keys. Reference the API keys in the container definition.
A company has several workloads running on AWS. Employees are required to authenticate using on-premises ADFS and SSO to access the AWS Management Console. Developers migrated an existing legacy web application to an Amazon EC2 instance. Employees need to access this application from anywhere on the internet, but currently, there is no authentication system built into the application. How should the Security Engineer implement employee-only access to this system without changing the application?
A. Place the application behind an Application Load Balancer (ALB). Use Amazon Cognito as authentication for the ALB. Define a SAML-based Amazon Cognito user pool and connect it to ADFS.
B. Implement AWS SSO in the master account and link it to ADFS as an identity provider. Define the EC2 instance as a managed resource, then apply an IAM policy on the resource.
C. Define an Amazon Cognito identity pool, then install the connector on the Active Directory server. Use the Amazon Cognito SDK on the application instance to authenticate the employees using their Active Directory user names and passwords.
D. Create an AWS Lambda custom authorizer as the authenticator for a reverse proxy on Amazon EC2. Ensure the security group on Amazon EC2 only allows access from the Lambda function.
A company requires deep packet inspection on encrypted traffic to its web servers in its VPC. Which solution will meet this requirement?
A. Decrypt traffic by using an Application Load Balancer (ALB) that is configured for TLS termination. Configure the ALB to send the traffic to an AWS Network Firewall endpoint for the deep packet inspection.
B. Decrypt traffic by using a Network Load Balancer (NLB) that is configured for TLS termination. Configure the NLB to send the traffic to an AWS Network Firewall endpoint for the deep packet inspection.
C. Decrypt traffic by using an Application Load Balancer (ALB) that is configured for TLS termination. Configure the ALB to send the traffic to an AWS WAF endpoint for the deep packet inspection.
D. Decrypt traffic by using a Network Load Balancer (NLB) that is configured for TLS termination. Configure the NLB to send the traffic to an AWS WAF endpoint for the deep packet inspection.
A company's application uses Amazon DynamoDB to store data. The company's security policy requires all data to be encrypted at rest. The security policy also requires the company to use an on-premises hardware security module (HSM) to generate and manage the company's encryption keys. A security engineer uses the on-premises HSM to generate an encryption key. What should the security engineer do next to meet these requirements?
A. Generate a new AWS Key Management Service (AWS KMS) customer managed key. Import the new key material. Grant DynamoDB access to use the key. Create a new DynamoDB table, and select the new key as the encryption key. Import the data into DynamoDB.
B. Generate a new AWS Key Management Service (AWS KMS) customer managed key. Import the new key material. Create a new DynamoDB table, and select the new key as the encryption key. Disable the KMS key after table creation. Import the data into DynamoDB.
C. Generate a new AWS Key Management Service (AWS KMS) AWS managed key. Import the new key material. Grant DynamoDB access to use the key. Create a new DynamoDB table, and select the new key as the encryption key. Import the data into DynamoDB.
D. Generate a new AWS Key Management Service (AWS KMS) AWS managed key. Import the new key material. Use the AWS SDK integration with AWS KMS to encrypt the data locally by using the new KMS key. Create a new DynamoDB table, and select the new key as the encryption key. Disable the KMS key after table creation. Import the data into DynamoDB.
A company uses SAML federation with AWS Identity and Access Management (IAM) to provide internal users with SSO for their AWS accounts. The company's identity provider certificate was rotated as part of its normal lifecycle. Shortly after, users started receiving the following error when attempting to log in: "Error: Response Signature Invalid (Service: AWSSecurityTokenService; Status Code: 400; Error Code: InvalidIdentityToken)" A security engineer needs to address the immediate issue and ensure that it will not occur again. Which combination of steps should the security engineer take to accomplish this? (Choose two.)
A. Download a new copy of the SAML metadata file from the identity provider. Create a new IAM identity provider entity. Upload the new metadata file to the new IAM identity provider entity.
B. During the next certificate rotation period and before the current certificate expires, add a new certificate as the secondary to the identity provider. Generate a new metadata file and upload it to the IAM identity provider entity. Perform automated or manual rotation of the certificate when required.
C. Download a new copy of the SAML metadata file from the identity provider. Upload the new metadata to the IAM identity provider entity configured for the SAML integration in question.
D. During the next certificate rotation period and before the current certificate expires, add a new certificate as the secondary to the identity provider. Generate a new copy of the metadata file and create a new IAM identity provider entity. Upload the metadata file to the new IAM identity provider entity. Perform automated or manual rotation of the certificate when required.
E. Download a new copy of the SAML metadata file from the identity provider. Create a new IAM identity provider entity. Upload the new metadata file to the new IAM identity provider entity. Update the identity provider configurations to pass a new IAM identity provider entity name in the SAML assertion.
A company is designing the security architecture for a global latency-sensitive web application it plans to deploy to AWS. A security engineer needs to configure a highly available and secure two-tier architecture. The security design must include controls to prevent common attacks such as DDoS, cross-site scripting, and SQL injection. Which solution meets these requirements?
A. Create an Application Load Balancer (ALB) that uses public subnets across multiple Availability Zones within a single Region. Point the ALB to an Auto Scaling group with Amazon EC2 instances in private subnets across multiple Availability Zones within the same Region. Create an Amazon CloudFront distribution that uses the ALB as its origin. Create appropriate AWS WAF ACLs and enable them on the CloudFront distribution.
B. Create an Application Load Balancer (ALB) that uses private subnets across multiple Availability Zones within a single Region. Point the ALB to an Auto Scaling group with Amazon EC2 instances in private subnets across multiple Availability Zones within the same Region. Create an Amazon CloudFront distribution that uses the ALB as its origin. Create appropriate AWS WAF ACLs and enable them on the CloudFront distribution.
C. Create an Application Load Balancer (ALB) that uses public subnets across multiple Availability Zones within a single Region. Point the ALB to an Auto Scaling group with Amazon EC2 instances in private subnets across multiple Availability Zones within the same Region. Create appropriate AWS WAF ACLs and enable them on the ALB.
D. Create an Application Load Balancer (ALB) that uses private subnets across multiple Availability Zones within a single Region. Point the ALB to an Auto Scaling group with Amazon EC2 instances in private subnets across multiple Availability Zones within the same Region. Create appropriate AWS WAF ACLs and enable them on the ALB.
A company uses multiple AWS accounts managed with AWS Organizations. Security engineers have created a standard set of security groups for all these. accounts. The security policy requires that these security groups be used for all applications and delegates modification authority to the security team only. A recent security audit found that the security groups are inconsistently implemented across accounts and that unauthorized changes have been made to the security groups. A security engineer needs to recommend a solution to improve consistency and to prevent unauthorized changes in the individual accounts in the future. Which solution should the security engineer recommend?
A. Use AWS Resource Access Manager to create shared resources for each required security group and apply an IAM policy that permits read-only access to the security groups only.
B. Create an AWS CloudFormation template that creates the required security groups. Execute the template as part of configuring new accounts. Enable Amazon Simple Notification Service (Amazon SNS) notifications when changes occur.
C. Use AWS Firewall Manager to create a security group policy, enable the policy feature to identify and revert local changes, and enable automatic remediation.
D. Use AWS Control Tower to edit the account factory template to enable the share security groups option. Apply an SCP to the OU or individual accounts that prohibits security group modifications from local account users.
A security engineer is developing automation that uses an AWS Lambda function to add tags to non-compliant IAM users and IAM roles. During testing, the function fails to perform the tagging action. When the security engineer attempts to look at the associated Amazon CloudWatch log group, no logs are being generated. After additional troubleshooting, the security engineer determines that the issue is related to the associated Lambda execution role. Which statement should the security engineer add to the Lambda execution role to ensure functionality while following the principle of least privilege?
A.

B.

C.

D.

A company is using Amazon Route 53 Resolver for its hybrid DNS infrastructure. The company has set up Route 53 Resolver forwarding rules for authoritative domains that are hosted on on-premises DNS servers. A new security mandate requires the company to implement a solution to log and query DNS traffic that goes to the on-premises DNS servers. The logs must show details of the source IP address of the instance from which the query originated. The logs also must show the DNS name that was requested in Route 53 Resolver. Which solution will meet these requirements?
A. Use VPC Traffic Mirroring. Configure all relevant elastic network interfaces as the traffic source, include amazon-dns in the mirror filter, and set Amazon CloudWatch Logs as the mirror target. Use CloudWatch Insights on the mirror session logs to run queries on the source IP address and DNS name.
B. Configure VPC flow logs on all relevant VPCs. Send the logs to an Amazon S3 bucket. Use Amazon Athena to run SQL queries on the source IP address and DNS name.
C. Configure Route 53 Resolver query logging on all relevant VPCs. Send the logs to Amazon CloudWatch Logs. Use CloudWatch Insights to run queries on the source IP address and DNS name.
D. Modify the Route 53 Resolver rules on the authoritative domains that forward to the on-premises DNS servers. Send the logs to an Amazon S3 bucket. Use Amazon Athena to run SQL queries on the source IP address and DNS name.
A security engineer has noticed an unusually high amount of traffic coming from a single IP address. This was discovered by analyzing the Application Load Balancer's access logs. How can the security engineer limit the number of requests from a specific IP address without blocking the IP address?
A. Add a rule to the Application Load Balancer to route the traffic originating from the IP address in question and show a static webpage.
B. Implement a rate-based rule with AWS WAF.
C. Use AWS Shield to limit the originating traffic hit rate.
D. Implement the GeoLocation feature in Amazon Route 53.
A Security Engineer has created an Amazon CloudWatch event that invokes an AWS Lambda function daily. The Lambda function runs an Amazon Athena query that checks AWS CloudTrail logs in Amazon S3 to detect whether any IAM user accounts or credentials have been created in the past 30 days. The results of the Athena query are created in the same S3 bucket. The Engineer runs a test execution of the Lambda function via the AWS Console, and the function runs successfully. After several minutes, the Engineer finds that his Athena query has failed with the error message: `Insufficient Permissions`. The IAM permissions of the Security Engineer and the Lambda function are shown below: Security Engineer -Lambda function execution role -
What is causing the error?
A. The Lambda function does not have permissions to start the Athena query execution.
B. The Security Engineer does not have permissions to start the Athena query execution.
C. The Athena service does not support invocation through Lambda.
D. The Lambda function does not have permissions to access the CloudTrail S3 bucket.
Which approach will generate automated security alerts should too many unauthorized AWS API requests be identified?
A. Create an Amazon CloudWatch metric filter that looks for API call error codes and then implement an alarm based on that metric’s rate.
B. Configure AWS CloudTrail to stream event data to Amazon Kinesis. Configure an AWS Lambda function on the stream to alarm when the threshold has been exceeded.
C. Run an Amazon Athena SQL query against CloudTrail log files. Use Amazon QuickSight to create an operational dashboard.
D. Use the Amazon Personal Health Dashboard to monitor the account’s use of AWS services, and raise an alert if service error rates increase.
A company has complex connectivity rules governing ingress, egress, and communications between Amazon EC2 instances. The rules are so complex that they cannot be implemented within the limits of the maximum number of security groups and network access control lists (network ACLs). What mechanism will allow the company to implement all required network rules without incurring additional cost?
A. Configure AWS WAF rules to implement the required rules.
B. Use the operating system built-in, host-based firewall to implement the required rules.
C. Use a NAT gateway to control ingress and egress according to the requirements.
D. Launch an EC2-based firewall product from the AWS Marketplace, and implement the required rules in that product.
Example.com is hosted on Amazon EC2 instance behind an Application Load Balancer (ALB). Third-party host intrusion detection system (HIDS) agents that capture the traffic of the EC2 instance are running on each host. The company must ensure they are using privacy enhancing technologies for users, without losing the assurance the third-party solution offers. What is the MOST secure way to meet these requirements?
A. Enable TLS pass through on the ALB, and handle decryption at the server using Elliptic Curve Diffie-Hellman (ECDHE) cipher suites.
B. Create a listener on the ALB that uses encrypted connections with Elliptic Curve Diffie-Hellman (ECDHE) cipher suites, and pass the traffic in the clear to the server.
C. Create a listener on the ALB that uses encrypted connections with Elliptic Curve Diffie-Hellman (ECDHE) cipher suites, and use encrypted connections to the servers that do not enable Perfect Forward Secrecy (PFS).
D. Create a listener on the ALB that does not enable Perfect Forward Secrecy (PFS) cipher suites, and use encrypted connections to the servers using Elliptic Curve Diffie-Hellman (ECDHE) cipher suites.
A corporate cloud security policy states that communications between the company's VPC and KMS must travel entirely within the AWS network and not use public service endpoints. Which combination of the following actions MOST satisfies this requirement? (Choose two.)
A. Add the aws:sourceVpce condition to the AWS KMS key policy referencing the company’s VPC endpoint ID.
B. Remove the VPC internet gateway from the VPC and add a virtual private gateway to the VPC to prevent direct, public internet connectivity.
C. Create a VPC endpoint for AWS KMS with private DNS enabled.
D. Use the KMS Import Key feature to securely transfer the AWS KMS key over a VPN.
E. Add the following condition to the AWS KMS key policy: “aws:SourceIp”: “10.0.0.0/16”.
During a recent internal investigation, it was discovered that all API logging was disabled in a production account, and the root user had created new API keys that appear to have been used several times. What could have been done to detect and automatically remediate the incident?
A. Using Amazon Inspector, review all of the API calls and configure the inspector agent to leverage SNS topics to notify security of the change to AWS CloudTrail, and revoke the new API keys for the root user.
B. Using AWS Config, create a config rule that detects when AWS CloudTrail is disabled, as well as any calls to the root user create-api-key. Then use a Lambda function to re-enable CloudTrail logs and deactivate the root API keys.
C. Using Amazon CloudWatch, create a CloudWatch event that detects AWS CloudTrail deactivation and a separate Amazon Trusted Advisor check to automatically detect the creation of root API keys. Then use a Lambda function to enable AWS CloudTrail and deactivate the root API keys.
D. Using Amazon CloudTrail, create a new CloudTrail event that detects the deactivation of CloudTrail logs, and a separate CloudTrail event that detects the creation of root API keys. Then use a Lambda function to enable CloudTrail and deactivate the root API keys.
A company's engineering team is developing a new application that creates AWS Key Management Service (AWS KMS) CMK grants for users. Immediately after a grant is created, users must be able to use the CMK to encrypt a 512-byte payload. During load testing, a bug appears intermittently where AccessDeniedExceptions are occasionally triggered when a user first attempts to encrypt using the CMK. Which solution should the company's security specialist recommend?
A. Instruct users to implement a retry mechanism every 2 minutes until the call succeeds.
B. Instruct the engineering team to consume a random grant token from users, and to call the CreateGrant operation, passing it the grant token. Instruct users to use that grant token in their call to encrypt.
C. Instruct the engineering team to create a random name for the grant when calling the CreateGrant operation. Return the name to the users and instruct them to provide the name as the grant token in the call to encrypt.
D. Instruct the engineering team to pass the grant token returned in the CreateGrant response to users. Instruct users to use that grant token in their call to encrypt.
A company has decided to use encryption in its AWS account to secure the objects in Amazon S3 using server-side encryption. Object sizes range from 16,000 B to 5 MB. The requirements are as follows: ✑ The key material must be generated and stored in a certified Federal Information Processing Standard (FIPS) 140-2 Level 3 machine. ✑ The key material must be available in multiple Regions. Which option meets these requirements?
A. Use an AWS KMS customer managed key and store the key material in AWS with replication across Regions.
B. Use an AWS customer managed key, import the key material into AWS KMS using in-house AWS CloudHSM, and store the key material securely in Amazon S3.
C. Use an AWS KMS custom key store backed by AWS CloudHSM clusters, and copy backups across Regions.
D. Use AWS CloudHSM to generate the key material and backup keys across Regions. Use the Java Cryptography Extension (JCE) and Public Key Cryptography Standards #11 (PKCS #11) encryption libraries to encrypt and decrypt the data.
A security alert has been raised for an Amazon EC2 instance in a customer account that is exhibiting strange behavior. The Security Engineer must first isolate the EC2 instance and then use tools for further investigation. What should the Security Engineer use to isolate and research this event? (Choose three.)
A. AWS CloudTrail
B. Amazon Athena
C. AWS Key Management Service (AWS KMS)
D. VPC Flow Logs
E. AWS Firewall Manager
F. Security groups
Free Access Full SCS-C01 Practice Test Free Questions
If you’re looking for more SCS-C01 practice test free questions, click here to access the full SCS-C01 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your SCS-C01 certification journey!