SCS-C01 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the SCS-C01 certification? Take your preparation to the next level with our SCS-C01 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a SCS-C01 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic SCS-C01 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
A security engineer needs to create an Amazon S3 bucket policy that restricts access to specific IP address ranges. The policy must allow only IP addresses in the range 10.24.34.0/23 to access the S3 bucket DOC-EXAMPLE-BUCKET and its objects. The policy must deny access to DOC-EXAMPLE-BUCKET from other IP address ranges. IAM policies will control the actions that principals can take in the S3 bucket. Which policy meets these requirements?
A.

B.

C.

D.

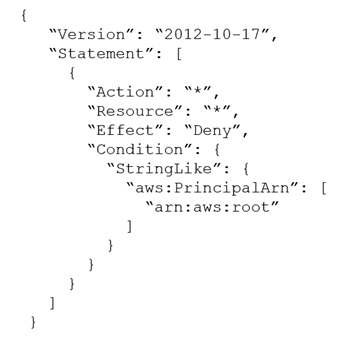
A company's security team suspects that an insider threat is present. The security team is basing its suspicion on activity that occurred in one of the company's AWS accounts. The activity was performed with the AWS account root user credentials. The root user has no access keys. The company uses AWS Organizations, and the account where the activity occurred is in an OU. A security engineer needs to take away the root user's ability to make any updates to the account. The root user password cannot be changed to accomplish this goal. Which solution will meet these requirements?
A. Attach the following SCP to the account:
B. Attach the following SCP to the account:
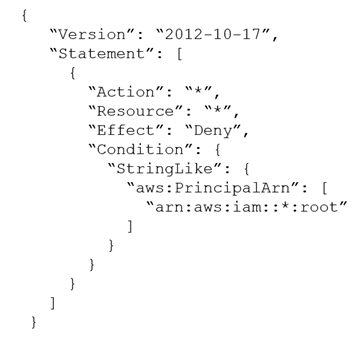
C. Attach the following SCP to the account:
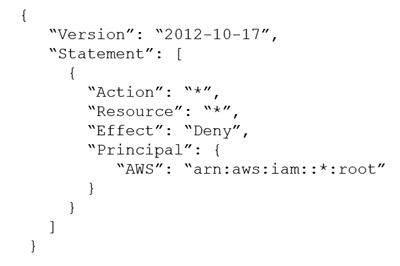
D. Attach the following inline IAM policy to the root user:
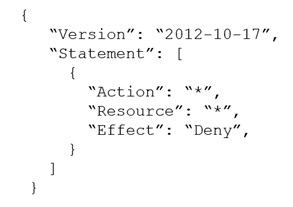
A company is observing frequent bursts of unusual traffic to its corporate website. The IP address ranges that inflate the requests keep changing, and the volumes of traffic are increasing. A security engineer needs to implement a solution to protect the website from a potential DDoS attack. The solution must rack the rate of requests from IP addresses. When the requests from a particular IP address exceed a specific rate, the solution must limit the amount of traffic that can reach the website from that IP address. Which solution will meet these requirements?
A. Setup Amazon Inspector on the backend servers. Create assessment targets with a rate-based configuration to block any offending IP address.
B. Create a rate-based rule in AWS WAF to block an IP address when that IP address exceeds the configured threshold rate.
C. Identity the offending client IP address ranges. Create a regular rule in AWS WAF to block the offending IP address ranges.
D. Create a rate-based rule in Amazon GuardDuty to block an IP address when that IP address exceeds the configured threshold rate
A security engineer is attempting to troubleshoot a problem. An application that runs on an Amazon EC2 instance in a VPC cannot communicate with an Amazon RDS DB instance in another subnet of the same VPC. The connection request is timing out. Which issues could be causing this problem? (Choose two.)
A. The application instance’s security group is not allowing outbound traffic.
B. The network ACL of the application instance’s subnet is not allowing traffic between the application and the DB instance.
C. The VPC’s route table is not configured correctly.
D. There is no peering connection between the application and the database.
E. The DB instance’s security group is not allowing outbound traffic.
A company's architecture requires that its three Amazon EC2 instances run behind an Application Load Balancer (ALB). The EC2 instances transmit sensitive data between each other. Developers use SSL certificates to encrypt the traffic between the public users and the ALB. However, the Developers are unsure of how to encrypt the data in transit between the ALB and the EC2 instances and the traffic between the EC2 instances. Which combination of activities must the company implement to meet its encryption requirements? (Choose two.)
A. Configure SSL/TLS on the EC2 instances and configure the ALB target group to use HTTPS.
B. Ensure that all resources are in the same VPC so the default encryption provided by the VPC is used to encrypt the traffic between the EC2 instances.
C. In the ALB, select the default encryption to encrypt the traffic between the ALB and the EC2 instances.
D. In the code for the application, include a cryptography library and encrypt the data before sending it between the EC2 instances.
E. Configure AWS Direct Connect to provide an encrypted tunnel between the EC2 instances.
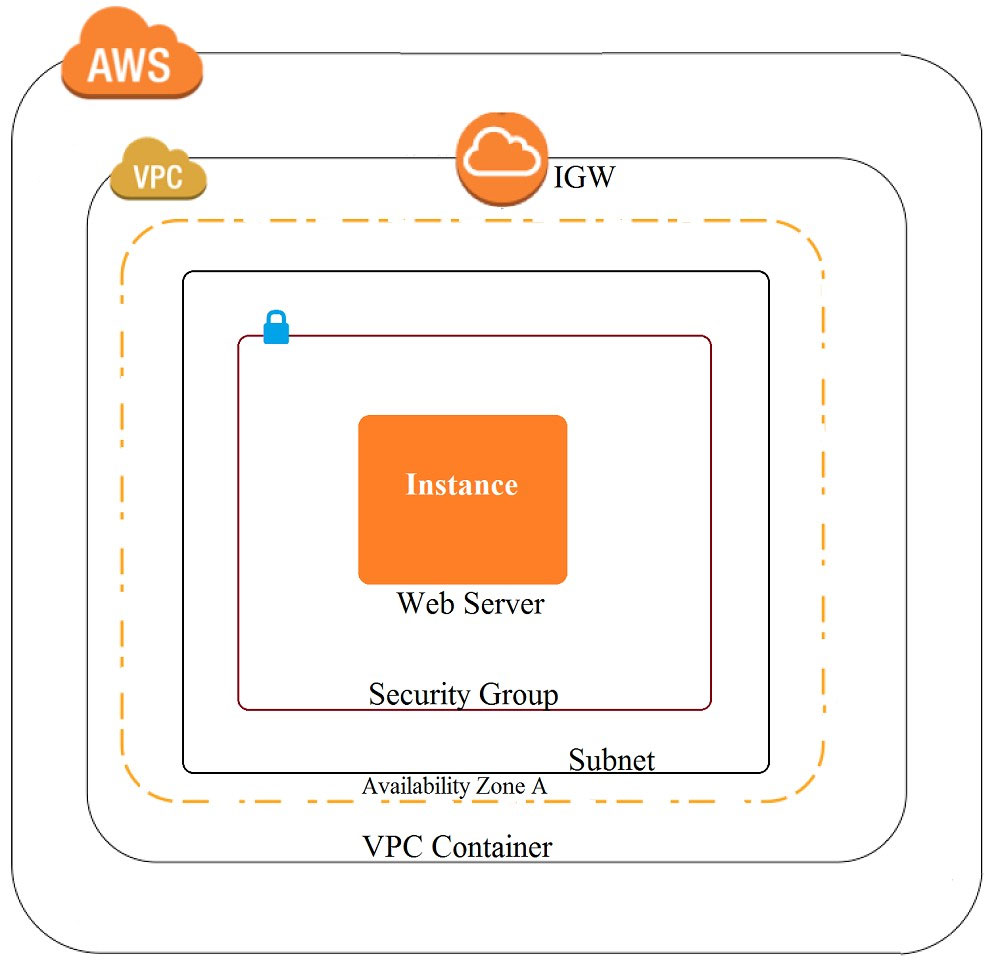
A company recently experienced a DDoS attack that prevented its web server from serving content. The website is static and hosts only HTML, CSS, and PDF files that users download. Based on the architecture shown in the image, what is the BEST way to protect the site against future attacks while minimizing the ongoing operational overhead?
A. Move all the files to an Amazon S3 bucket. Have the web server serve the files from the S3 bucket.
B. Launch a second Amazon EC2 instance in a new subnet. Launch an Application Load Balancer in front of both instances.
C. Launch an Application Load Balancer in front of the EC2 instance. Create an Amazon CloudFront distribution in front of the Application Load Balancer.
D. Move all the files to an S3 bucket. Create a CloudFront distribution in front of the bucket and terminate the web server.
For compliance reasons, an organization limits the use of resources to three specific AWS regions. It wants to be alerted when any resources are launched in unapproved regions. Which of the following approaches will provide alerts on any resources launched in an unapproved region?
A. Develop an alerting mechanism based on processing AWS CloudTrail logs.
B. Monitor Amazon S3 Event Notifications for objects stored in buckets in unapproved regions.
C. Analyze Amazon CloudWatch Logs for activities in unapproved regions.
D. Use AWS Trusted Advisor to alert on all resources being created.
A company wants to deploy an application in a private VPC that will not be connected to the internet. The company's security team will not allow bastion hosts or methods using SSH to log in to Amazon EC2 instances. The application team plans to use AWS Systems Manager Session Manager to connect to and manage the EC2 instances. Which combination of steps should the security team take? (Choose three.)
A. Make sure the Systems Manager Agent is installed and running on all EC2 instances inside the VPC.
B. Ensure the IAM role attached to the EC2 instances in the VPC allows access to Systems Manager.
C. Create an SCP that prevents the creation of SSH key pairs.
D. Launch a NAT gateway in the VPC. Update the routing policies to forward traffic to this NAT gateway.
E. Ensure proper VPC endpoints are in place for Systems Manager and Amazon EC2.
F. Ensure the VPC has a transit gateway attachment. Update the routing policies to forward traffic to this transit gateway.
A company has several production AWS accounts and a central security AWS account. The security account is used for centralized monitoring and has IAM privileges to all resources in every corporate account. All of the company's Amazon S3 buckets are tagged with a value denoting the data classification of their contents. A Security Engineer is deploying a monitoring solution in the security account that will enforce bucket policy compliance. The system must monitor S3 buckets in all production accounts and confirm that any policy change is in accordance with the bucket's data classification. If any change is out of compliance, the Security team must be notified quickly. Which combination of actions would build the required solution? (Choose three.)
A. Configure Amazon CloudWatch Events in the production accounts to send all S3 events to the security account event bus.
B. Enable Amazon GuardDuty in the security account, and join the production accounts as members.
C. Configure an Amazon CloudWatch Events rule in the security account to detect S3 bucket creation or modification events.
D. Enable AWS Trusted Advisor and activate email notifications for an email address assigned to the security contact.
E. Invoke an AWS Lambda function in the security account to analyze S3 bucket settings in response to S3 events, and send non-compliance notifications to the Security team.
F. Configure event notifications on S3 buckets for PUT, POST, and DELETE events.
A company is running a dynamic website by using an Application Load Balancer (ALB). A security engineer notices that bots from different IP addresses are using brute-force attacks to invoke a service endpoint frequently. What is the FASTEST way to mitigate this problem?
A. Create an AWS Lambda function to process ALB logs. Block the bots’ IP addresses in the ALB’s security group.
B. Create an AWS WAF web ACL for the ALAdd a rate-based rule to the web ACL to block the bots.
C. Create an ALB listener rule. Combine source-ip and path-pattern as the conditions to match bots. Specify a fixed-response action to return an HTTP 403 status.
D. Create an AWS WAF web ACL for the ALB. Add a rate-based rule to a rule group to block the bots. Attach the rule to the web ACL.
Amazon CloudWatch Logs agent is successfully delivering logs to the CloudWatch Logs service. However, logs stop being delivered after the associated log stream has been active for a specific number of hours. What steps are necessary to identify the cause of this phenomenon? (Choose two.)
A. Ensure that file permissions for monitored files that allow the CloudWatch Logs agent to read the file have not been modified.
B. Verify that the OS Log rotation rules are compatible with the configuration requirements for agent streaming.
C. Configure an Amazon Kinesis producer to first put the logs into Amazon Kinesis Streams.
D. Create a CloudWatch Logs metric to isolate a value that changes at least once during the period before logging stops.
E. Use AWS CloudFormation to dynamically create and maintain the configuration file for the CloudWatch Logs agent.
An AWS account administrator created an IAM group and applied the following managed policy to require that each individual user authenticate using multi-factor authentication:After implementing the policy, the administrator receives reports that users are unable to perform Amazon EC2 commands using the AWS CLI. What should the administrator do to resolve this problem while still enforcing multi-factor authentication?
A. Change the value of aws:MultiFactorAuthPresent to true.
B. Instruct users to run the aws sts get-session-token CLI command and pass the multi-factor authentication –serial-number and –token-code parameters. Use these resulting values to make API/CLI calls.
C. Implement federated API/CLI access using SAML 2.0, then configure the identity provider to enforce multi-factor authentication.
D. Create a role and enforce multi-factor authentication in the role trust policy. Instruct users to run the sts assume-role CLI command and pass –serial-number and –token-code parameters. Store the resulting values in environment variables. Add sts:AssumeRole to NotAction in the policy.
A company’s security engineer needs to restrict access to AWS so that the company can deploy resources only in the eu-west-1 Region. The company uses AWS Organizations and has applied the following SCP at the organization’s root level:The company uses Amazon S3, Amazon Route 53, Amazon CloudFront, and AWS Identity and Access Management (IAM). These services must still work in eu-west-1. Which entry should the security engineer remove from the NotAction element in the Deny policy to achieve this goal?
A. s3:*
B. iam:*
C. cloudfront:*
D. route53:*
A company stores data on an Amazon EBS volume attached to an Amazon EC2 instance. The data is asynchronously replicated to an Amazon S3 bucket. Both the EBS volume and the S3 bucket are encrypted with the same AWS KMS Customer Master Key (CMK). A former employee scheduled a deletion of that CMK before leaving the company. The company's Developer Operations department learns about this only after the CMK has been deleted. Which steps must be taken to address this situation?
A. Copy the data directly from the EBS encrypted volume before the volume is detached from the EC2 instance.
B. Recover the data from the EBS encrypted volume using an earlier version of the KMS backing key.
C. Make a request to AWS Support to recover the S3 encrypted data.
D. Make a request to AWS Support to restore the deleted CMK, and use it to recover the data.
A company has multiple departments. Each department has its own AWS account. All these accounts belong to the same organization in AWS Organizations. A large .csv file is stored in an Amazon S3 bucket in the sales department's AWS account. The company wants to allow users from the other accounts to access the .csv file’s content through the combination of AWS Glue and Amazon Athena. However, the company does not want to allow users from the other accounts to access other files in the same folder. Which solution will meet these requirements?
A. Apply a user policy in the other accounts to allow AWS Glue and Athena to access the .csv file.
B. Use S3 Select to restrict access to the .csv file. In AWS Glue Data Catalog, use S3 Select as the source of the AWS Glue database.
C. Define an AWS Glue Data Catalog resource policy in AWS Glue to grant cross-account S3 object access to the .csv file.
D. Grant AWS Glue access to Amazon S3 in a resource-based policy that specifies the organization as the principal.
A company decides to use AWS Key Management Service (AWS KMS) for data encryption operations. The company must create a KMS key and automate the rotation of the key. The company also needs the ability to deactivate the key and schedule the key for deletion. Which solution will meet these requirements?
A. Create an asymmetric customer managed KMS key. Enable automatic key rotation.
B. Create a symmetric customer managed KMS key. Disable the envelope encryption option.
C. Create a symmetric customer managed KMS key. Enable automatic key rotation.
D. Create an asymmetric customer managed KMS key. Disable the envelope encryption option.
A security engineer is working for a parent company that provides hosting and services to client companies. The parent company maintains an organization in AWS Organizations for all client company accounts. The parent company adds any new accounts to the organization when the new accounts are created. The parent company currently uses IAM users to administer the client company accounts. As more client accounts are added, the administration of the IAM accounts takes more time. The security engineer must design a solution to reduce the amount of time that the parent company spends on administration and access provisioning for client accounts. Which combination of steps should the security engineer take to meet these requirements? (Choose two.)
A. Provision an external identity provider (IdP) for the parent company. Implement AWS Single Sign-On (AWS SSO) with the IdP as the identity source for AWS SSO.
B. Provision an external identity provider (IdP) for each client company. Implement AWS Single Sign-On (AWS SSO) with the IdPs as the identity source for AWS SSO.
C. Provision an external identity provider (IdP) for the parent company. Implement AWS Single Sign-On (AWS SSO) with employee IAM roles as the identity source for AWS SSO.
D. In the AWS Single Sign-On console, select the users who require access to client accounts. Assign these users to the accounts.
E. In the IAM console, select the users who require access to client accounts. Assign these users to the accounts.
A company is designing a multi-account structure for its development teams. The company is using AWS Organizations and AWS Single Sign-On (AWS SSO). The company must implement a solution so that the development teams can use only specific AWS Regions and so that each AWS account allows access to only specific AWS services. Which solution will meet these requirements with the LEAST operational overhead?
A. Use AWS SSO to set up service-linked roles with IAM policy statements that include the Condition, Resource, and NotAction elements to allow access to only the Regions and services that are needed.
B. Deactivate AWS Security Token Service (AWS STS) in Regions that the developers are not allowed to use.
C. Create SCPs that include the Condition, Resource, and NotAction elements to allow access to only the Regions and services that are needed.
D. For each AWS account, create tailored identity-based policies for AWS SSO. Use statements that include the Condition, Resource, and NotAction elements to allow access to only the Regions and services that are needed.
A company is hosting multiple applications within a single VPC in its AWS account. The applications are running behind an Application Load Balancer that is associated with an AWS WAF web ACL. The company's security team has identified that multiple port scans are originating from a specific range of IP addresses on the internet. A security engineer needs to deny access from the offending IP addresses. Which solution will meet these requirements?
A. Modify the AWS WAF web ACL with an IP set match rule statement to deny incoming requests from the IP address range.
B. Add a rule to all security groups to deny the incoming requests from the IP address range.
C. Modify the AWS WAF web ACL with a rate-based rule statement to deny incoming requests from the IP address range.
D. Configure the AWS WAF web ACL with regex match conditions. Specify a pattern set to deny the incoming requests based on the match condition.
A Website currently runs on Amazon EC2, with mostly static content on the site. Recently, the site was subjected to a DDoS attack, and a Security Engineer was tasked with redesigning the edge security to help mitigate this risk in the future. What are some ways the Engineer could achieve this? (Choose three.)
A. Use AWS X-Ray to inspect the traffic going to the EC2 instances.
B. Move the static content to Amazon S3, and front this with an Amazon CloudFront distribution.
C. Change the security group configuration to block the source of the attack traffic.
D. Use AWS WAF security rules to inspect the inbound traffic.
E. Use Amazon Inspector assessment templates to inspect the inbound traffic.
F. Use Amazon Route 53 to distribute traffic.
A Security Engineer is working with a Product team building a web application on AWS. The application uses Amazon S3 to host the static content, Amazon API Gateway to provide RESTful services; and Amazon DynamoDB as the backend data store. The users already exist in a directory that is exposed through a SAML identity provider. Which combination of the following actions should the Engineer take to enable users to be authenticated into the web application and call APIs? (Choose three.)
A. Create a custom authorization service using AWS Lambda.
B. Configure a SAML identity provider in Amazon Cognito to map attributes to the Amazon Cognito user pool attributes.
C. Configure the SAML identity provider to add the Amazon Cognito user pool as a relying party.
D. Configure an Amazon Cognito identity pool to integrate with social login providers.
E. Update DynamoDB to store the user email addresses and passwords.
F. Update API Gateway to use a COGNITO_USER_POOLS authorizer.
A company has an application that stores data in an Amazon S3 bucket. In the same AWS account, the company deploys a new data analysis application on Amazon EC2 with an instance profile attached. The analysis application is able to get a list of S3 objects but is unable to read the data. The following IAM policy is attached to the instance role:Which solution will give the analysis application the ability to read the data in the S3 bucket?
A. Add the s3:GetObjectVersion action to the list of actions in the policy that is attached to the instance role.
B. Add the following IAM policy to the instance role:

C. Create a bucket policy for the data bucket. Add the following statement to the bucket policy:

D. Update the application to write objects with the bucket-owner-full-control ACL.
A security engineer recently enabled the me-south-1 Region. The security engineer is now assuming an IAM role and is making an API call to an endpoint in me-south-1. The API call returns the following error: “AuthFailure: AWS was not able to validate the provided access credentials”. Which solutions will resolve this error? (Choose two.)
A. Add the iam:SetSecurityTokenServicePreferences action to the security engineer’s IAM role.
B. Use the AWS Security Token Service (AWS STS) endpoint in me-south-1 to obtain an STS token.
C. Use the AWS Security Token Service (AWS STS) endpoint in the us-east-1 Region to obtain an STS token.
D. Manually activate the AWS Security Token Service (AWS STS) endpoint in me-south-1.
E. Change the AWS Security Token Service (AWS STS) global endpoint to issue Region-compatible session tokens.
A company hosts a web-based application that captures and stores sensitive data in an Amazon DynamoDB table. The company needs to implement a solution that provides end-to-end data protection and the ability to detect unauthorized data changes. Which solution will meet these requirements?
A. Use an AWS Key Management Service (AWS KMS) customer managed key. Encrypt the data at rest.
B. Use AWS Private Certificate Authority. Encrypt the data in transit.
C. Use the DynamoDB Encryption Client. Use client-side encryption. Sign the table items.
D. Use the AWS Encryption SDK. Use client-side encryption. Sign the table items.
A company wants to implement a content delivery network for an upcoming product launch. The origin for distribution is an object store outside of AWS and requires the Authorization header from the request to be passed to it. How can a security engineer meet this requirement in the LEAST amount of time?
A. Migrate the objects to Amazon S3. Create a new AWS Global Accelerator accelerator that has a listener on port 443 and an endpoint group that points to the origin distribution.
B. Create a new Amazon CloudFront distribution. Create a new CloudFront custom header for X-Amz-Authorization. Attach the header to the distribution.
C. Create a new Amazon CloudFront distribution. Create a new CloudFront cache policy with a header whitelist for the Authorization header. Attach the policy to the distribution.
D. Migrate the objects to Amazon S3. Create a new Amazon CloudFront distribution. Create a new CloudFront cache policy with a header whitelist for the Authorization header. Attach the policy to the distribution.
A company’s security engineer is configuring AWS Single Sign-On (AWS SSO) to give employees the ability to access multiple AWS accounts that are part of an organization in AWS Organizations. Persistent network connectivity exists between the organization's management account where AWS SSO is configured and an existing on-premises Active Directory instance. The security engineer wants to enable employee authentication by using the existing on-premises Active Directory instance. What is the MOST operationally efficient solution that meets these requirements?
A. Deploy the default AWS SSO user directory. Establish a two-way trust relationship between AWS SSO and the existing Active Directory instance.
B. Deploy an AWS managed Active Directory instance in the organization’s management account. Establish a two-way trust relationship with the existing Active Directory instance.
C. Deploy a self-managed Active Directory instance in the organization’s management account. Establish a two-way trust relationship with the existing Active Directory instance.
D. Deploy an AWS managed Active Directory instance in the organization’s management account. Establish a one-way trust relationship with the existing Active Directory instance.
A company has five AWS accounts and wants to use AWS CloudTrail to log API calls. The log files must be stored in an Amazon S3 bucket that resides in a new account specifically built for centralized services with a unique top-level prefix for each trail. The configuration must also enable detection of any modification to the logs. Which of the following steps will implement these requirements? (Choose three.)
A. Create a new S3 bucket in a separate AWS account for centralized storage of CloudTrail logs, and enable ג€Log File Validationג€ on all trails.
B. Use an existing S3 bucket in one of the accounts, apply a bucket policy to the new centralized S3 bucket that permits the CloudTrail service to use the “s3: PutObject” action and the “s3 GetBucketACL” action, and specify the appropriate resource ARNs for the CloudTrail trails.
C. Apply a bucket policy to the new centralized S3 bucket that permits the CloudTrail service to use the “s3 PutObject” action and the “s3 GelBucketACL” action, and specify the appropriate resource ARNs for the CloudTrail trails.
D. Use unique log file prefixes for trails in each AWS account.
E. Configure CloudTrail in the centralized account to log all accounts to the new centralized S3 bucket.
F. Enable encryption of the log files by using AWS Key Management Service
Example.com is hosted on Amazon EC2 instance behind an Application Load Balancer (ALB). Third-party host intrusion detection system (HIDS) agents that capture the traffic of the EC2 instance are running on each host. The company must ensure they are using privacy enhancing technologies for users, without losing the assurance the third-party solution offers. What is the MOST secure way to meet these requirements?
A. Enable TLS pass through on the ALB, and handle decryption at the server using Elliptic Curve Diffie-Hellman (ECDHE) cipher suites.
B. Create a listener on the ALB that uses encrypted connections with Elliptic Curve Diffie-Hellman (ECDHE) cipher suites, and pass the traffic in the clear to the server.
C. Create a listener on the ALB that uses encrypted connections with Elliptic Curve Diffie-Hellman (ECDHE) cipher suites, and use encrypted connections to the servers that do not enable Perfect Forward Secrecy (PFS).
D. Create a listener on the ALB that does not enable Perfect Forward Secrecy (PFS) cipher suites, and use encrypted connections to the servers using Elliptic Curve Diffie-Hellman (ECDHE) cipher suites.
A company needs to restrict access to Amazon DynamoDB tables in the us-east1 Region for account 0123456789. All users must be denied permission to work with DynamoDB tables in us-east-1 unless the users access the tables through the following endpoint: vpce-11aa22bb. Which IAM statement will enforce this requirement?
A.

B.

C.

D.

A company wants to encrypt the private network between its on-premises environment and AWS. The company also wants a consistent network experience for its employees. What should the company do to meet these requirements?
A. Establish an AWS Direct Connect connection with AWS and set up a Direct Connect gateway. In the Direct Connect gateway configuration, enable IPsec and BGP, and then leverage native AWS network encryption between Availability Zones and Regions.
B. Establish an AWS Direct Connect connection with AWS and set up a Direct Connect gateway. Using the Direct Connect gateway, create a private virtual interface and advertise the customer gateway private IP addresses. Create a VPN connection using the customer gateway and the virtual private gateway.
C. Establish a VPN connection with the AWS virtual private cloud over the Internet.
D. Establish an AWS Direct Connect connection with AWS and establish a public virtual interface. For prefixes that need to be advertised, enter the customer gateway public IP addresses. Create a VPN connection over Direct Connect using the customer gateway and the virtual private gateway.
The Security Engineer for a mobile game has to implement a method to authenticate users so that they can save their progress. Because most of the users are part of the same OpenID-Connect compatible social media website, the Security Engineer would like to use that as the identity provider. Which solution is the SIMPLEST way to allow the authentication of users using their social media identities?
A. Amazon Cognito
B. AssumeRoleWithWebIdentity API
C. Amazon Cloud Directory
D. Active Directory (AD) Connector
A company uses Amazon GuardDuty to detect threats and malicious activities in AWS accounts. The company has subscribed to a third-party threat intelligence list uploaded to an Amazon S3 bucket. How should the security engineer efficiently use the threat list across all company AWS accounts?
A. Ensure the S3 bucket policy allows all company AWS accounts access to the threat list. Use an AWS Lambda function to automatically add the threat list to all company AWS accounts.
B. Ensure GuardDuty is in master-member configuration. Add the threat list to the master account referencing the S3 object that contains the threat list.
C. Ensure all accounts are part of the same organization in AWS Organizations. Add the threat list to any company account within AWS Organizations.
D. Ensure the threat list in the S3 bucket is publicly accessible. Use an Amazon CloudWatch Events event on GuardDuty findings to match IPs against the threat list.
A security engineer is configuring AWS Config for an AWS account that uses a new 1AM entity. When the security engineer tries to configure AWS Config rules and automatic remediation options, errors occur. In the AWS CloudTrail logs, the security engineer sees the following error message: "Insufficient delivery policy to s3 bucket: DOC-EXAMPLE-BUCKET, unable to write to bucket, provided s3 key prefix is 'null'." Which combination of steps should the security engineer take to remediate this issue? (Choose two.)
A. Check the Amazon S3 bucket policy. Verify that the policy allows the config.amazonaws.com service to write to the target bucket.
B. Verify that the IAM entity has the permissions necessary to perform the s3:GetBucketAcl and s3:PutObject* operations to write to the target bucket.
C. Verify that the Amazon S3 bucket policy has the permissions necessary to perform the s3:GetBucketAcl and s3:PutObject* operations to write to the target bucket.
D. Check the policy that is associated with the IAM entity. Verify that the policy allows the config.amazonaws.com service to write to the target bucket.
E. Verify that the AWS Config service role has permissions to invoke the BatchGetResourceConfig action instead of the GetResourceConfigHistory action and s3:PutObject* operation.
A security engineer is analyzing Amazon GuardDuty findings. The security engineer observes an Impact value for ThreatPurpose in a GuardDuty finding. What does this value indicate?
A. An adversary has compromised an AWS resource so that the resource is capable of contacting its home command and control (C&C) server to receive further instructions for malicious activity.
B. GuardDuty is detecting activity or activity patterns that are different from the established baseline for a particular AWS resource.
C. GuardDuty is detecting activity or activity patterns that suggest that an adversary is attempting to manipulate, interrupt, or destroy the company’s systems and data.
D. GuardDuty is detecting activity or activity patterns that an adversary might use to expand its knowledge of the company’s systems and internal networks.
A company had one of its Amazon EC2 key pairs compromised. A Security Engineer must identify which current Linux EC2 instances were deployed and used the compromised key pair. How can this task be accomplished?
A. Obtain the list of instances by directly querying Amazon EC2 using: aws ec2 describe-instances –filters “Name=key- name,Values=KEYNAMEHERE”.
B. Obtain the fingerprint for the key pair from the AWS Management Console, then search for the fingerprint in the Amazon Inspector logs.
C. Obtain the output from the EC2 instance metadata using: curl http://169.254.169.254/latest/meta-data/public-keys/0/.
D. Obtain the fingerprint for the key pair from the AWS Management Console, then search for the fingerprint in Amazon CloudWatch Logs using: aws logs filter-log-events.
A Security Administrator has a website hosted in Amazon S3. The Administrator has been given the following requirements: ✑ Users may access the website by using an Amazon CloudFront distribution. ✑ Users may not access the website directly by using an Amazon S3 URL. Which configurations will support these requirements? (Choose two.)
A. Associate an origin access identity with the CloudFront distribution.
B. Implement a ג€Principalג€: ג€cloudfront.amazonaws.comג€ condition in the S3 bucket policy.
C. Modify the S3 bucket permissions so that only the origin access identity can access the bucket contents.
D. Implement security groups so that the S3 bucket can be accessed only by using the intended CloudFront distribution.
E. Configure the S3 bucket policy so that it is accessible only through VPC endpoints, and place the CloudFront distribution into the specified VPC.
An Amazon S3 bucket is encrypted using an AWS KMS CMK. An IAM user is unable to download objects from the S3 bucket using the AWS Management Console; however, other users can download objects from the S3 bucket. Which policies should the Security Engineer review and modify to resolve this issue? (Choose three.)
A. The CMK policy
B. The VPC endpoint policy
C. The S3 bucket policy
D. The S3 ACL
E. The IAM policy
A Developer signed in to a new account within an AWS Organizations organizational unit (OU) containing multiple accounts. Access to the Amazon S3 service is restricted with the following SCP:How can the Security Engineer provide the Developer with Amazon S3 access without affecting other accounts?
A. Move the SCP to the root OU of Organizations to remove the restriction to access Amazon S3.
B. Add an IAM policy for the Developer, which grants S3 access.
C. Create a new OU without applying the SCP restricting S3 access. Move the Developer account to this new OU.
D. Add an allow list for the Developer account for the S3 service.
A company’s security engineer must record when specific AWS Lambda functions are invoked. The logs must include the AWS principal that invoked the function. External sources and the company’s developers deliver the Lambda function code by using a variety of languages such as Python, Node.js, and Golang. The security engineer has created an AWS CloudTrail trail with default configuration for the AWS account. Which solution will meet these requirements with the LEAST operational overhead?
A. Update the Lambda function code to extract the AWS principal from the Lambda context and to write a log entry when the function to be monitored is invoked.
B. Use Amazon EventBridge (Amazon CloudWatch Events) to configure a rule and custom pattern for lambda:invoke events with a filter on the functions to monitor. Invoke another Lambda function to write the EventBridge (CloudWatch Events) data to Amazon CloudWatch Logs.
C. Modify the existing CloudTrail trail. Configure the existing CloudTrail trail to monitor Lambda functions as data events.
D. Create a Lambda layer that provides CloudTrail with a log event that includes the Lambda context when the function is invoked. Attach this layer to all Lambda functions that must be monitored.
A company hosts business-critical applications on Amazon EC2 instances in a VPC. The VPC uses default DHCP options sets. A security engineer needs to log all DNS queries that internal resources make in the VPC. The security engineer also must create a list of the most common DNS queries over time. Which solution will meet these requirements?
A. Install the Amazon CloudWatch agent on each EC2 instance in the VPC. Use the CloudWatch agent to stream the DNS query logs to an Amazon CloudWatch Logs log group. Use CloudWatch metric filters to automatically generate metrics that list the most common DNS queries.
B. Install a BIND DNS server in the VPC. Create a bash script to list the DNS request number of common DNS queries from the BIND logs.
C. Create VPC flow logs for all subnets in the VPStream the flow logs to an Amazon CloudWatch Logs log group. Use CloudWatch Logs Insights to list the most common DNS queries for the log group in a custom dashboard.
D. Configure Amazon Route 53 Resolver query logging. Add an Amazon CloudWatch Logs log group as the destination. Use Amazon CloudWatch Contributor Insights to analyze the data and create time series that display the most common DNS queries.
Which of the following minimizes the potential attack surface for applications?
A. Use security groups to provide stateful firewalls for Amazon EC2 instances at the hypervisor level.
B. Use network ACLs to provide stateful firewalls at the VPC level to prevent access to any specific AWS resource.
C. Use AWS Direct Connect for secure trusted connections between EC2 instances within private subnets.
D. Design network security in a single layer within the perimeter network (also known as DMZ, demilitarized zone, and screened subnet) to facilitate quicker responses to threats.
A company uses AWS Key Management Service (AWS KMS). During an attempt to attach an encrypted Amazon Elastic Block Store (Amazon EBS) volume to an Amazon EC2 instance, the attachment fails. The company discovers that a customer managed key has become unusable because the key material for the key was deleted. The company needs the data that is on the EBS volume. A security engineer must recommend a solution to decrypt the EBS volume's encrypted data key. The solution must also attach the volume to the EC2 instance. Which solution will meet these requirements?
A. Import new key material into the key. Attach the EBS volume.
B. Restore the EBS volume from a snapshot that was taken before the deletion of the key material.
C. Reimport the same key material that originally was imported into the key. Attach the EBS volume.
D. Create a new key. Import new key material. Attach the EBS volume.
A company in France uses Amazon Cognito with the Cognito Hosted UI as an identity broker for sign-in and sign-up processes. The company is marketing an application and expects that all the application's users will come from France. When the company launches the application, the company's security team observes fraudulent sign-ups for the application. Most of the fraudulent registrations are from users outside of France. The security team needs a solution to perform custom validation at sign-up. Based on the results of the validation, the solution must accept or deny the registration request. Which combination of steps will meet these requirements? (Choose two.)
A. Create a pre sign-up AWS Lambda trigger. Associate the Amazon Cognito function with the Amazon Cognito user pool.
B. Use a geographic match rule statement to configure an AWS WAF web ACL. Associate the web ACL with the Amazon Cognito user pool.
C. Configure an app client for the application’s Amazon Cognito user pool. Use the app client ID to validate the requests in the hosted UI.
D. Update the application’s Amazon Cognito user pool to configure a geographic restriction setting.
E. Use Amazon Cognito to configure a social identity provider (IdP) to validate the requests on the hosted UI.
A water utility company uses a number of Amazon EC2 instances to manage updates to a fleet of 2,000 Internet of Things (IoT) field devices that monitor water quality. These devices each have unique access credentials. An operational safety policy requires that access to specific credentials is independently auditable. What is the MOST cost-effective way to manage the storage of credentials?
A. Use AWS Systems Manager to store the credentials as Secure Strings Parameters. Secure by using an AWS KMS key.
B. Use AWS Key Management System to store a master key, which is used to encrypt the credentials. The encrypted credentials are stored in an Amazon RDS instance.
C. Use AWS Secrets Manager to store the credentials.
D. Store the credentials in a JSON file on Amazon S3 with server-side encryption.
A company is running an application on Amazon EC2 instances in an Auto Scaling group. The application stores logs locally. A security engineer noticed that logs were lost after a scale-in event. The security engineer needs to recommend a solution to ensure the durability and availability of log data. All logs must be kept for a minimum of 1 year for auditing purposes. What should the security engineer recommend?
A. Within the Auto Scaling lifecycle, add a hook to create an attach an Amazon Elastic Block Store (Amazon EBS) log volume each time an EC2 instance is created. When the instance is terminated, the EBS volume can be reattached to another instance for log review.
B. Create an Amazon Elastic File System (Amazon EFS) file system and add a command in the user data section of the Auto Scaling launch template to mount the EFS file system during EC2 instance creation. Configure a process on the instance to copy the logs once a day from an instance Amazon Elastic Block Store (Amazon EBS) volume to a directory in the EFS file system.
C. Build the Amazon CloudWatch agent into the AMI used in the Auto Scaling group. Configure the CloudWatch agent to send the logs to Amazon CloudWatch Logs for review.
D. Within the Auto Scaling lifecycle, add a lifecycle hook at the terminating state transition and alert the engineering team by using a lifecycle notification to Amazon Simple Notification Service (Amazon SNS). Configure the hook to remain in the Terminating:Wait state for 1 hour to allow manual review of the security logs prior to instance termination.
A company allows users to download its mobile app onto their phones. The app is MQTT based and connects to AWS IoT Core to subscribe to specific client-related topics. Recently, the company discovered that some malicious attackers have been trying to get a Trojan horse onto legitimate mobile phones. The Trojan horse poses as the authentic application and uses a client ID with injected special characters to gain access to topics outside the client’s privilege scope. Which combination of actions should the company take to prevent this threat? (Choose two.)
A. In the application, use an IoT thing name as the client ID to connect the device to AWS IoT Core.
B. In the application, add a client ID check. Disconnect from the server if any special character is detected.
C. Apply an AWS IoT Core policy that allows “AWSIoTWirelessDataAccess” with the principal set to “client/${iot:Connection.Thing.ThingName}”.
D. Apply an AWS IoT Core policy to the device to allow “iot:Connect” with the resource set to “client/${iot:ClientId}”.
E. Apply an AWS IoT Core policy to the device to allow “iot:Connect” with the resource set to “client/${iot:Connection.Thing.ThingName}”.
A company wants to protect its website from man-in-the-middle attacks by using Amazon CloudFront. Which solution will meet these requirements with the LEAST operational overhead?
A. Use the SimpleCORS managed response headers policy.
B. Use a Lambda@Edge function to add the Strict-Transport-Security response header.
C. Use the SecurityHeadersPolicy managed response headers policy.
D. Include the X-XSS-Protection header in a custom response headers policy.
A software-as-a-service (SaaS) company hosts an application on AWS in a VPC. External customers will use the application on their own Amazon EC2 instances. To access the application, the customers need to install a client application on an EC2 instance in a VPC in their AWS accounts. A security engineer is designing a solution to allow communication between the client software and the SaaS application. The solution must maximize scalability and security. Which combination of actions will meet these requirements? (Choose two.)
A. Create a Network Load Balancer (NLB) in the VPC in the SaaS company account. Use the NLB for TLS termination and load balancing. Use EC2 instances as targets for the NLB.
B. Create a Network Load Balancer (NLB) in the VPCs in the customer accounts. Use the NLB for TLS termination and load balancing. Use EC2 instances as targets for the NLB.
C. Create an AWS PrivateLink endpoint service in the VPCs in the customer accounts. Create a PrivateLink interface endpoint in the VPC in the SaaS company account.
D. Create an AWS PrivateLink endpoint service in the VPC in the SaaS company account. Create a PrivateLink interface endpoint in the VPCs in the customer accounts.
E. Create a VPC peering connection between the VPC in the SaaS company account and the VPCs in the customer accounts. Create the required routes for a VPC peering connection.
A company’s public Application Load Balancer (ALB) recently experienced a DDoS attack. To mitigate this issue. the company deployed Amazon CloudFront in front of the ALB so that users would not directly access the Amazon EC2 instances behind the ALB. The company discovers that some traffic is still coming directly into the ALB and is still being handled by the EC2 instances. Which combination of steps should the company take to ensure that the EC2 instances will receive traffic only from CloudFront? (Choose two.)
A. Configure CloudFront to add a cache key policy to allow a custom HTTP header that CloudFront sends to the ALB.
B. Configure CloudFront to add a custom: HTTP header to requests that CloudFront sends to the ALB.
C. Configure the ALB to forward only requests that contain the custom HTTP header.
D. Configure the ALB and CloudFront to use the X-Forwarded-For header to check client IP addresses.
E. Configure the ALB and CloudFront to use the same X.509 certificate that is generated by AWS Certificate Manager (ACM).
A security engineer configures Amazon S3 Cross-Region Replication (CRR) for all objects that are in an S3 bucket in the us-east-1 Region. Some objects in this S3 bucket use server-side encryption with AWS KMS keys (SSE-KMS) for encryption at rest. The security engineer creates a destination S3 bucket in the us-west-2 Region. The destination S3 bucket is in the same AWS account as the source S3 bucket. The security engineer also creates a customer managed key in us-west-2 to encrypt objects at rest in the destination S3 bucket. The replication configuration is set to use the key in us-west-2 to encrypt objects in the destination S3 bucket. The security engineer has provided the S3 replication configuration with an IAM role to perform the replication in Amazon S3. After a day, the security engineer notices that no encrypted objects from the source S3 bucket are replicated to the destination S3 bucket. However, all the unencrypted objects are replicated. Which combination of steps should the security engineer take to remediate this issue? (Choose three.)
A. Change the replication configuration to use the key in us-east-1 to encrypt the objects that are in the destination S3 bucket.
B. Grant the IAM role the kms:Encrypt permission for the key in us-east-1 that encrypts source objects.
C. Grant the IAM role the s3:GetObjectVersionForReplication permission for objects that are in the source S3 bucket.
D. Grant the IAM role the kms:Decrypt permission for the key in us-east-1 that encrypts source objects.
E. Change the key policy of the key in us-east-1 to grant the kms:Decrypt permission to the security engineer’s IAM account.
F. Grant the IAM role the kms:Encrypt permission for the key in us-west-2 that encrypts objects that are in the destination S3 bucket.
Free Access Full SCS-C01 Practice Exam Free
Looking for additional practice? Click here to access a full set of SCS-C01 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your SCS-C01 certification journey!