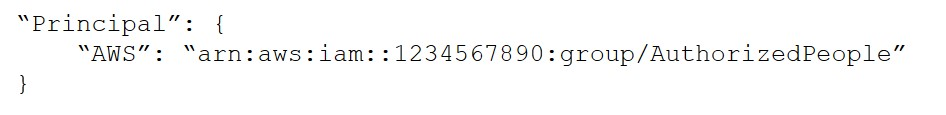SCS-C01 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your SCS-C01 certification exam? Start your preparation the smart way with our SCS-C01 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for SCS-C01 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our SCS-C01 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
A company is using Amazon Elastic Container Service (Amazon ECS) to run its container-based application on AWS. The company needs to ensure that the container images contain no severe vulnerabilities. The company also must ensure that only specific IAM roles and specific AWS accounts can access the container images. Which solution will meet these requirements with the LEAST management overhead?
A. Pull images from the public container registry. Publish the images to Amazon Elastic Container Registry (Amazon ECR) repositories with scan on push configured in a centralized AWS account. Use a CI/CD pipeline to deploy the images to different AWS accounts. Use identity-based policies to restrict access to which IAM principals can access the images.
B. Pull images from the public container registry. Publish the images to a private container registry that is hosted on Amazon EC2 instances in a centralized AWS account. Deploy host-based container scanning tools to EC2 instances that run Amazon ECS. Restrict access to the container images by using basic authentication over HTTPS.
C. Pull images from the public container registry. Publish the images to Amazon Elastic Container Registry (Amazon ECR) repositories with scan on push configured in a centralized AWS account. Use a CI/CD pipeline to deploy the images to different AWS accounts. Use repository policies and identity-based policies to restrict access to which IAM principals and accounts can access the images.
D. Pull images from the public container registry. Publish the images to AWS CodeArtifact repositories in a centralized AWS account. Use a CI/CD pipeline to deploy the images to different AWS accounts. Use repository policies and identity-based policies to restrict access to which IAM principals and accounts can access the images.
A company that builds document management systems recently performed a security review of its application on AWS. The review showed that uploads of documents through signed URLs into Amazon S3 could occur in the application without encryption in transit. A security engineer must implement a solution that prevents uploads that are not encrypted in transit. Which solution will meet this requirement?
A. Ensure that all client implementations are using HTTPS to upload documents into the application.
B. Configure the s3-bucket-ssl-requests-only managed rule in AWS Config.
C. Add an S3 bucket policy that denies all S3 actions for condition “aws:secureTransport”: “false”.
D. Add an S3 bucket ACL with a grantee of AllUsers, a permission of WRITE, and a condition of secureTransport.
A Security Architect is evaluating managed solutions for storage of encryption keys. The requirements are: -Storage is accessible by using only VPCs. -Service has tamper-evident controls. -Access logging is enabled. -Storage has high availability. Which of the following services meets these requirements?
A. Amazon S3 with default encryption
B. AWS CloudHSM
C. Amazon DynamoDB with server-side encryption
D. AWS Systems Manager Parameter Store
A company has two AWS accounts, each containing one VPC. The first VPC has a VPN connection with its corporate network. The second VPC, without a VPN, hosts an Amazon Aurora database cluster in private subnets. Developers manage the Aurora database from a bastion host in a public subnet as shown in the image.A security review has flagged this architecture as vulnerable, and a Security Engineer has been asked to make this design more secure. The company has a short deadline and a second VPN connection to the Aurora account is not possible. How can the Security Engineer securely set up the bastion host?
A. Move the bastion host to the VPC with VPN connectivity. Create a VPC peering relationship between the bastion host VPC and Aurora VPC.
B. Create an SSH port forwarding tunnel on the Developer’s workstation to the bastion host to ensure that only authorized SSH clients can access the bastion host.
C. Move the bastion host to the VPC with VPN connectivity. Create a cross-account trust relationship between the bastion VPC and Aurora VPC, and update the Aurora security group for the relationship.
D. Create an AWS Direct Connect connection between the corporate network and the Aurora account, and adjust the Aurora security group for this connection.
A Development team has built an experimental environment to test a simple static web application. It has built an isolated VPC with a private and a public subnet. The public subnet holds only an Application Load Balancer, a NAT gateway, and an internet gateway. The private subnet holds all of the Amazon EC2 instances. There are 3 different types of servers. Each server type has its own Security Group that limits access to only required connectivity. The Security Groups have both inbound and outbound rules applied. Each subnet has both inbound and outbound network ACLs applied to limit access to only required connectivity. Which of the following should the team check if a server cannot establish an outbound connection to the internet? (Choose three.)
A. The route tables and the outbound rules on the appropriate private subnet security group.
B. The outbound network ACL rules on the private subnet and the inbound network ACL rules on the public subnet.
C. The outbound network ACL rules on the private subnet and both the inbound and outbound rules on the public subnet.
D. The rules on any host-based firewall that may be applied on the Amazon EC2 instances.
E. The Security Group applied to the Application Load Balancer and NAT gateway.
F. That the 0.0.0.0/0 route in the private subnet route table points to the Internet gateway in the public subnet.
A security engineer is trying to use Amazon EC2 Image Builder to create an image of an EC2 instance. The security engineer has configured the pipeline to send logs to an Amazon S3 bucket. When the security engineer runs the pipeline, the build fails with the following error: “AccessDenied: Access Denied status code: 403”. The security engineer must resolve the error by implementing a solution that complies with best practices for least privilege access. Which combination of steps will meet these requirements? (Choose two.)
A. Ensure that the following policies are attached to the IAM role that the security engineer is using: EC2InstanceProfileForImageBuilder, EC2InstanceProfileForImageBuilderECRContainerBuilds, and AmazonSSMManagedInstanceCore.
B. Ensure that the following policies are attached to the instance profile for the EC2 instance: EC2InstanceProfileForImageBuilder, EC2InstanceProfileForImageBuilderECRContainerBuilds, and AmazonSSMManagedInstanceCore.
C. Ensure that the AWSImageBuilderFullAccess policy is attached to the instance profile for the EC2 instance.
D. Ensure that the security engineer’s IAM role has the s3:PutObject permission for the S3 bucket.
E. Ensure that the instance profile for the EC2 instance has the s3:PutObject permission for the S3 bucket.
A company finds that one of its Amazon EC2 instances suddenly has a high CPU usage. The company does not know whether the EC2 instance is compromised or whether the operating system is performing background cleanup. Which combination of steps should a security engineer take before investigating the issue? (Choose three.)
A. Disable termination protection for the EC2 instance if termination protection has not been disabled.
B. Enable termination protection for the EC2 instance if termination protection has not been enabled.
C. Take snapshots of the Amazon Elastic Block Store (Amazon EBS) data volumes that are attached to the EC2 instance.
D. Remove all snapshots of the Amazon Elastic Block Store (Amazon EBS) data volumes that are attached to the EC2 instance.
E. Capture the EC2 instance metadata, and then tag the EC2 instance as under quarantine.
F. Immediately remove any entries in the EC2 instance metadata that contain sensitive information.
A company needs to provide digital evidence to a security engineer for analysis. The evidence must be encrypted and the immutability of the source data must be maintained. What is the MOST secure solution that meets these requirements?
A. Upload the digital evidence to a new Amazon S3 bucket. Set up an S3 Lifecycle configuration to move the data to S3 Glacier. Configure S3 Glacier with a vault lock policy.
B. Upload the digital evidence to a new Amazon S3 bucket with S3 Object Lock enabled. Implement server-side encryption with AWS Key Management Service (AWS KMS).
C. Upload the digital evidence to a new Amazon S3 bucket Configure an S3 bucket policy. Enable S3 Versioning and MFA Delete. Use S3 presigned URLs.
D. Launch an Amazon EC2 instance. Store the digital evidence on an attached Amazon Elastic Block Store (Amazon EBS) volume. Enable termination protection, isolate the EC2 instance and take a snapshot of the EBS volume.
A security engineer has noticed that VPC Flow Logs are getting a lot of REJECT traffic originating from a single Amazon EC2 instance in an Auto Scaling group. The security engineer is concerned that this EC2 instance may be compromised. What immediate action should the security engineer take?
A. Remove the instance from the Auto Scaling group. Close the security group with ingress only from a single forensic IP address to perform an analysis.
B. Remove the instance from the Auto Scaling group. Change the network ACL rules to allow traffic only from a single forensic IP address to perform an analysis. Add a rule to deny all other traffic.
C. Remove the instance from the Auto Scaling group. Enable Amazon GuardDuty in that AWS account. Install the Amazon Inspector agent on the suspicious EC2 instance to perform a scan.
D. Take a snapshot of the suspicious EC2 instance. Create a new EC2 instance from the snapshot in a closed security group with ingress only from a single forensic IP address to perform an analysis.
During a manual review of system logs from an Amazon Linux EC2 instance, a Security Engineer noticed that there are sudo commands that were never properly alerted or reported on the Amazon CloudWatch Logs agent. Why were there no alerts on the sudo commands?
A. There is a security group blocking outbound port 80 traffic that is preventing the agent from sending the logs.
B. The IAM instance profile on the EC2 instance was not properly configured to allow the CloudWatch Logs agent to push the logs to CloudWatch.
C. CloudWatch Logs status is set to ON versus SECURE, which prevents if from pulling in OS security event logs.
D. The VPC requires that all traffic go through a proxy, and the CloudWatch Logs agent does not support a proxy configuration.
A company wants to gain better control of its large number of AWS accounts by establishing a centralized location where the accounts can be managed. The company also wants to prevent any users outside the company-owned AWS accounts from accessing a company Amazon S3 bucket. Which solution meets these requirements with the LEAST amount of operational overhead?
A. Implement an organization in AWS Organizations. Build a detective control by monitoring AWS CloudTrail logs for attempts to access the S3 bucket from IP addresses outside the company.
B. Deploy an AWS Control Tower landing zone, and migrate the accounts. Create an S3 bucket policy that restricts access to only a principal list of accounts that have been manually entered.
C. Create an organization in AWS Organizations. Invite the AWS accounts to join the organization. Create a resource policy that includes a PrincipalOrgID condition key for the S3 bucket.
D. Invite all of the company’s AWS accounts into AWS Control Tower. Use AWS Control Tower’s automatic protection for the AWS accounts to deny access from external users.
A company is hosting multiple applications within a single VPC in its AWS account. The applications are running behind an Application Load Balancer that is associated with an AWS WAF web ACL. The company's security team has identified that multiple port scans are originating from a specific range of IP addresses on the internet. A security engineer needs to deny access from the offending IP addresses. Which solution will meet these requirements?
A. Modify the AWS WAF web ACL with an IP set match rule statement to deny incoming requests from the IP address range.
B. Add a rule to all security groups to deny the incoming requests from the IP address range.
C. Modify the AWS WAF web ACL with a rate-based rule statement to deny incoming requests from the IP address range.
D. Configure the AWS WAF web ACL with regex match conditions. Specify a pattern set to deny the incoming requests based on the match condition.
A VPC endpoint for Amazon CloudWatch Logs was recently added to a company's VPC. The company's system administrator has verified that private DNS is enabled and that the appropriate route tables and security groups have been updated. The role attached to the Amazon EC2 instance is:The CloudWatch Logs agent is running and attempting to write to a CloudWatch Logs stream in the same AWS account. However, no logs are being updated in CloudWatch Logs. What is the likely cause of this issue?
A. The EC2 instance role is not allowing the appropriate Put actions.
B. The EC2 instance role policy is incorrect and should be changed to:
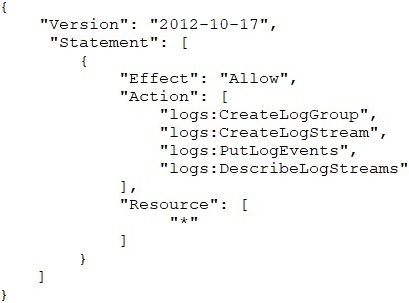
C. The CloudWatch Logs endpoint policy is not allowing the appropriate Put actions.
D. The CloudWatch Logs resource policy is not allowing the appropriate List actions.
A company has a web server in the AWS Cloud. The company will store the content for the web server in an Amazon S3 bucket. A security engineer must use an Amazon CloudFront distribution to speed up delivery of the content. None of the files can be publicly accessible from the S3 bucket direct. Which solution will meet these requirements?
A. Configure the permissions on the individual files in the S3 bucket so that only the CloudFront distribution has access to them.
B. Create an origin access identity (OAI). Associate the OAI with the CloudFront distribution. Configure the S3 bucket permissions so that only the OAI can access the files in the S3 bucket.
C. Create an S3 role in AWS Identity and Access Management (IAM). Allow only the CloudFront distribution to assume the role to access the files in the S3 bucket.
D. Create an S3 bucket policy that uses only the CloudFront distribution ID as the principal and the Amazon Resource Name (ARN) as the target.
An IAM user with fill EC2 permissions could bot start an Amazon EC2 instance after it was stopped for a maintenance task. Upon starting the instance, the instance state would change to `Pending`, but after a few seconds, it would switch back to `Stopped`. An inspection revealed that the instance has attached Amazon EBS volumes that were encrypted by using a Customer Master Key (CMK). When these encrypted volumes were detached, the IAM user was able to start the EC2 instances. The IAM user policy is as follows:What additional items need to be added to the IAM user policy? (Choose two.)
A. kms:GenerateDataKey
B. kms:Decrypt
C. kms:CreateGrant
D. ג€Conditionג€: { ג€Boolג€: { ג€kms:ViaServiceג€: ג€ec2.us-west-2.amazonaws.comג€ } }
E. ג€Conditionג€: { ג€Boolג€: { ג€kms:GrantIsForAWSResourceג€: true } }
The Security Engineer has discovered that a new application that deals with highly sensitive data is storing Amazon S3 objects with the following key pattern, which itself contains highly sensitive data. Pattern: "randomID_datestamp_PII.csv" Example: "1234567_12302017_000-00-0000 csv" The bucket where these objects are being stored is using server-side encryption (SSE). Which solution is the most secure and cost-effective option to protect the sensitive data?
A. Remove the sensitive data from the object name, and store the sensitive data using S3 user-defined metadata.
B. Add an S3 bucket policy that denies the action s3:GetObject
C. Use a random and unique S3 object key, and create an S3 metadata index in Amazon DynamoDB using client-side encrypted attributes.
D. Store all sensitive objects in Binary Large Objects (BLOBS) in an encrypted Amazon RDS instance.
A company is using Amazon Route 53 Resolver for its hybrid DNS infrastructure. The company has set up Route 53 Resolver forwarding rules for authoritative domains that are hosted on on-premises DNS servers. A new security mandate requires the company to implement a solution to log and query DNS traffic that goes to the on-premises DNS servers. The logs must show details of the source IP address of the instance from which the query originated. The logs also must show the DNS name that was requested in Route 53 Resolver. Which solution will meet these requirements?
A. Use VPC Traffic Mirroring. Configure all relevant elastic network interfaces as the traffic source, include amazon-dns in the mirror filter, and set Amazon CloudWatch Logs as the mirror target. Use CloudWatch Insights on the mirror session logs to run queries on the source IP address and DNS name.
B. Configure VPC flow logs on all relevant VPCs. Send the logs to an Amazon S3 bucket. Use Amazon Athena to run SQL queries on the source IP address and DNS name.
C. Configure Route 53 Resolver query logging on all relevant VPCs. Send the logs to Amazon CloudWatch Logs. Use CloudWatch Insights to run queries on the source IP address and DNS name.
D. Modify the Route 53 Resolver rules on the authoritative domains that forward to the on-premises DNS servers. Send the logs to an Amazon S3 bucket. Use Amazon Athena to run SQL queries on the source IP address and DNS name.
A company has recently recovered from a security incident that required the restoration of Amazon EC2 instances from snapshots. After performing a gap analysis of its disaster recovery procedures and backup strategies, the company is concerned that, next time, it will not be able to recover the EC2 instances if the AWS account was compromised and Amazon EBS snapshots were deleted. All EBS snapshots are encrypted using an AWS KMS CMK. Which solution would solve this problem?
A. Create a new Amazon S3 bucket. Use EBS lifecycle policies to move EBS snapshots to the new S3 bucket. Move snapshots to Amazon S3 Glacier using lifecycle policies, and apply Glacier Vault Lock policies to prevent deletion.
B. Use AWS Systems Manager to distribute a configuration that performs local backups of all attached disks to Amazon S3.
C. Create a new AWS account with limited privileges. Allow the new account to access the AWS KMS key used to encrypt the EBS snapshots, and copy the encrypted snapshots to the new account on a recurring basis.
D. Use AWS Backup to copy EBS snapshots to Amazon S3.
A large government organization is moving to the cloud and has specific encryption requirements. The first workload to move requires that a customer's data be immediately destroyed when the customer makes that request. Management has asked the security team to provide a solution that will securely store the data, allow only authorized applications to perform encryption and decryption, and allow for immediate destruction of the data. Which solution will meet these requirements?
A. Use AWS Secrets Manager and an AWS SDK to create a unique secret for the customer-specific data.
B. Use AWS Key Management Service (AWS KMS) and the AWS Encryption SDK to generate and store a data encryption key for each customer.
C. Use AWS Key Management Service (AWS KMS) with service-managed keys to generate and store customer-specific data encryption keys.
D. Use AWS Key Management Service (AWS KMS) and create an AWS CloudHSM custom key store. Use CloudHSM to generate and store a new CMK for each customer.
A company does not allow the permanent installation of SSH keys onto an Amazon Linux 2 EC2 instance. However, three employees who have IAM user accounts require access to the EC2 instance. The employees must use an SSH session to perform critical duties. How can a security engineer provide the appropriate access to the EC2 instance to meet these requirements?
A. Use AWS Systems Manager Inventory to select the EC2 instance and connect. Provide the IAM user accounts with the permissions to use Systems Manager Inventory.
B. Use AWS Systems Manager Run Command to open an SSH connection to the EC2 instance. Provide the IAM user accounts with the permissions to use Run Command.
C. Use AWS Systems Manager Session Manager. Provide the IAM user accounts with the permissions to use Systems Manager Session Manager.
D. Connect to the EC2 instance as the ec2-user through the AWS Management Console’s EC2 SSH client method. Provide the IAM user accounts with access to use the EC2 service in the AWS Management Console.
A company has a requirement that none of its Amazon RDS resources can be publicly accessible. A security engineer needs to set up monitoring for this requirement and must receive a near-real-time notification if any RDS resource is noncompliant. Which combination of steps should the security engineer take to meet these requirements? (Choose three.)
A. Configure RDS event notifications on each RDS resource. Target an AWS Lambda function that notifies AWS Config of a change to the RDS public access setting
B. Configure the rds-instance-public-access-check AWS Config managed rule to monitor the RDS resources.
C. Configure the Amazon EventBridge (Amazon CloudWatch Events) rule to target an Amazon Simple Notification Service (Amazon SNS) topic to provide a notification to the security engineer.
D. Configure RDS event notifications to post events to an Amazon Simple Queue Service (Amazon SQS) queue. Subscribe the SQS queue to an Amazon Simple Notification Service (Amazon SNS) topic to provide a notification to the security engineer.
E. Configure an Amazon EventBridge (Amazon CloudWatch Events) rule that is invoked by a compliance change event from the rds-instance-public-access-check rule.
F. Configure an Amazon EventBridge (Amazon CloudWatch Events) rule that is invoked when the AWS Lambda function notifies AWS Config of an RDS event change.
A company uses Amazon GuardDuty to detect threats and malicious activities in AWS accounts. The company has subscribed to a third-party threat intelligence list uploaded to an Amazon S3 bucket. How should the security engineer efficiently use the threat list across all company AWS accounts?
A. Ensure the S3 bucket policy allows all company AWS accounts access to the threat list. Use an AWS Lambda function to automatically add the threat list to all company AWS accounts.
B. Ensure GuardDuty is in master-member configuration. Add the threat list to the master account referencing the S3 object that contains the threat list.
C. Ensure all accounts are part of the same organization in AWS Organizations. Add the threat list to any company account within AWS Organizations.
D. Ensure the threat list in the S3 bucket is publicly accessible. Use an Amazon CloudWatch Events event on GuardDuty findings to match IPs against the threat list.
A company has hundreds of AWS accounts, and a centralized Amazon S3 bucket used to collect AWS CloudTrail logs for all of these accounts. A Security Engineer wants to create a solution that will enable the company to run ad hoc queries against its CloudTrail logs dating back 3 years from when the trails were first enabled in the company's AWS account. How should the company accomplish this with the least amount of administrative overhead?
A. Run an Amazon EMR cluster that uses a MapReduce job to examine the CloudTrail trails.
B. Use the events history feature of the CloudTrail console to query the CloudTrail trails.
C. Write an AWS Lambda function to query the CloudTrail trails. Configure the Lambda function to be executed whenever a new file is created in the CloudTrail S3 bucket.
D. Create an Amazon Athena table that looks at the S3 bucket the CloudTrail trails are being written to. Use Athena to run queries against the trails.
A company wants to prevent SSH access through the use of SSH key pairs for any Amazon Linux 2 Amazon EC2 instances in its AWS account. However, a system administrator occasionally will need to access these EC2 instances through SSH in an emergency. For auditing purposes, the company needs to record any commands that a user runs in an EC2 instance. What should a security engineer do to configure access to these EC2 instances to meet these requirements?
A. Use the EC2 serial console. Configure the EC2 serial console to save all commands that are entered to an Amazon S3 bucket. Provide the EC2 instances with an IAM role that allows the EC2 serial console to access Amazon S3. Configure an IAM account for the system administrator. Provide an IAM policy that allows the IAM account to use the EC2 serial console,
B. Use EC2 Instance Connect. Configure EC2 Instance Connect to save all commands that are entered to Amazon CloudWatch Logs. Provide the EC2 instances with an IAM role that allows the EC2 Instances to access CloudWatch Logs. Configure an IAM account for the system administrator. Provide an IAM policy that allows the IAM account to use EC2 Instance Connect.
C. Use an EC2 key pair with an EC2 instance that needs SSH access. Access the EC2 instance with this key pair by using SSH. Configure the EC2 instance to save all commands that are entered to Amazon CloudWatch Logs. Provide the EC2 instance with an IAM role that allows the EC2 instance to access Amazon S3 and CloudWatch Logs.
D. Use AWS Systems Manager Session Manager. Configure Session Manager to save all commands that are entered in a session to an Amazon S3 bucket. Provide the EC2 instances with an IAM role that allows Systems Manager to manage the EC2 instances. Configure an IAM account for the system administrator. Provide an IAM policy that allows the IAM account to use Session Manager.
A company is outsourcing its operational support to an external company. The company's security officer must implement an access solution for delegating operational support that minimizes overhead. Which approach should the security officer take to meet these requirements?
A. Implement Amazon Cognito identity pools with a role that uses a policy that denies the actions related to Amazon Cognito API management. Allow the external company to federate through its identity provider.
B. Federate AWS Identity and Access Management (IAM) with the external company’s identity provider. Create an IAM role and attach a policy with the necessary permissions.
C. Create an IAM group for the external company. Add a policy to the group that denies IAM modifications. Securely provide the credentials to the external company.
D. Use AWS SSO with the external company’s identity provider. Create an IAM group to map to the identity provider user group, and attach a policy with the necessary permissions.
A Security Engineer is defining the logging solution for a newly developed product. Systems Administrators and Developers need to have appropriate access to event log files in AWS CloudTrail to support and troubleshoot the product. Which combination of controls should be used to protect against tampering with and unauthorized access to log files? (Choose two.)
A. Ensure that the log file integrity validation mechanism is enabled.
B. Ensure that all log files are written to at least two separate Amazon S3 buckets in the same account.
C. Ensure that Systems Administrators and Developers can edit log files, but prevent any other access.
D. Ensure that Systems Administrators and Developers with job-related need-to-know requirements only are capable of viewing ג€” but not modifying ג€” the log files.
E. Ensure that all log files are stored on Amazon EC2 instances that allow SSH access from the internal corporate network only.
An organization has a multi-petabyte workload that it is moving to Amazon S3, but the CISO is concerned about cryptographic wear-out and the blast radius if a key is compromised. How can the CISO be assured that AWS KMS and Amazon S3 are addressing the concerns? (Choose two.)
A. There is no API operation to retrieve an S3 object in its encrypted form.
B. Encryption of S3 objects is performed within the secure boundary of the KMS service.
C. S3 uses KMS to generate a unique data key for each individual object.
D. Using a single master key to encrypt all data includes having a single place to perform audits and usage validation.
E. The KMS encryption envelope digitally signs the master key during encryption to prevent cryptographic wear-out.
A security administrator is setting up a new AWS account. The security administrator wants to secure the data that a company stores in an Amazon S3 bucket. The security administrator also wants to reduce the chance of unintended data exposure and the potential for misconfiguration of objects that are in the S3 bucket. Which solution will meet these requirements with the LEAST operational overhead?
A. Configure the S3 Block Public Access feature for the AWS account.
B. Configure the S3 Block Public Access feature for all objects that are in the bucket.
C. Deactivate ACLs for objects that are in the bucket.D> Use AWS PrivateLink for Amazon S3 to access the bucket.
A company will store sensitive documents in three Amazon S3 buckets based on a data classification scheme of `Sensitive,` `Confidential,` and `Restricted.` The security solution must meet all of the following requirements: ✑ Each object must be encrypted using a unique key. ✑ Items that are stored in the `Restricted` bucket require two-factor authentication for decryption. ✑ AWS KMS must automatically rotate encryption keys annually. Which of the following meets these requirements?
A. Create a Customer Master Key (CMK) for each data classification type, and enable the rotation of it annually. For the ג€Restrictedג€ CMK, define the MFA policy within the key policy. Use S3 SSE-KMS to encrypt the objects.
B. Create a CMK grant for each data classification type with EnableKeyRotation and MultiFactorAuthPresent set to true. S3 can then use the grants to encrypt each object with a unique CMK.
C. Create a CMK for each data classification type, and within the CMK policy, enable rotation of it annually, and define the MFA policy. S3 can then create DEK grants to uniquely encrypt each object within the S3 bucket.
D. Create a CMK with unique imported key material for each data classification type, and rotate them annually. For the ג€Restrictedג€ key material, define the MFA policy in the key policy. Use S3 SSE-KMS to encrypt the objects.
Two Amazon EC2 instances in different subnets should be able to connect to each other but cannot. It has been confirmed that other hosts in the same subnets are able to communicate successfully, and that security groups have valid ALLOW rules in place to permit this traffic. Which of the following troubleshooting steps should be performed?
A. Check inbound and outbound security groups, looking for DENY rules
B. Check inbound and outbound Network ACL rules, looking for DENY rules
C. Review the rejected packet reason codes in the VPC Flow Logs
D. Use AWS X-Ray to trace the end-to-end application flow
A company is using AWS Organizations. The company wants to restrict AWS usage to the eu-west-1 Region for all accounts under an OU that is named "development." The solution must persist restrictions to existing and new AWS accounts under the development OU. Which solution meets these requirements?
A. Include the following SCP on the development OU:

B. Include the following SCP on the development account:

C. Include the following SCP on the development OU:

D. Include the following SCP on the development OU:

A security engineer is evaluating a company’s use of AWS Key Management Service (AWS KMS). The security engineer must implement a hybrid solution with two sets of keys to meet the following requirements: • Set 1: The company needs granular control over the keys so that the company can maintain a copy of the keys in the key management infrastructure and reimport the keys at any time. The company needs the ability to set the expiration period to 3 days for the keys. • Set 2: No restrictions exist regarding immediate key deletion. A waiting period of 14 days is acceptable for keys to be marked deleted. Which solution will meet these requirements?
A. Use imported keys for Set 1. Use AWS managed keys for Set 2. For Set 1, set an expiration period and manually delete the keys after the expiration period has elapsed.
B. Use imported keys for Set 1. Use AWS managed keys for Set 2. For Set 1, set an expiration period. AWS will automatically delete the keys after the expiration period has elapsed.
C. Use AWS managed keys for Set 1. Use imported keys for Set 2. For Set 1, set an expiration period and manually delete the keys after the expiration period has elapsed.
D. Use AWS managed keys for Set 1. Use imported keys for Set 2. For Set 1, set an expiration period. AWS will automatically delete the keys after the expiration period has elapsed.
A Solutions Architect is designing a web application that uses Amazon CloudFront, an Elastic Load Balancing Application Load Balancer, and an Auto Scaling group of Amazon EC2 instances. The load balancer and EC2 instances are in the US West (Oregon) region. It has been decided that encryption in transit is necessary by using a customer-branded domain name from the client to CloudFront and from CloudFront to the load balancer. Assuming that AWS Certificate Manager is used, how many certificates will need to be generated?
A. One in the US West (Oregon) region and one in the US East (Virginia) region.
B. Two in the US West (Oregon) region and none in the US East (Virginia) region.
C. One in the US West (Oregon) region and none in the US East (Virginia) region.
D. Two in the US East (Virginia) region and none in the US West (Oregon) region.
A company has Windows Amazon EC2 instances in a VPC that are joined to on-premises Active Directory servers for domain services. The security team has enabled Amazon GuardDuty on the AWS account to alert on issues with the instances. During a weekly audit of network traffic, the Security Engineer notices that one of the EC2 instances is attempting to communicate with a known command-and- control server but failing. This alert does not show up in GuardDuty. Why did GuardDuty fail to alert to this behavior?
A. GuardDuty did not have the appropriate alerts activated.
B. GuardDuty does not see these DNS requests.
C. GuardDuty only monitors active network traffic flow for command-and-control activity.
D. GuardDuty does not report on command-and-control activity.
A company uses Amazon Route 53 to create a public DNS zone for the domain example.com in Account A. The company creates another public DNS zone for the subdomain dev.example.com in Account B. A security engineer creates a wildcard certificate (*.dev.example.com) with DNS validation by using AWS Certificate Manager (ACM). The security engineer validates that the corresponding CNAME records have been created in the zone for dev.example.com in Account B. After all these operations are completed, the certificate status is still pending validation. What should the security engineer do to resolve this issue?
A. Purchase a valid wildcard certificate authority (CA) certificate that supports managed renewal. Import this certificate into ACM in Account B.
B. Add NS records for the subdomain dev.example.com to the Route 53 parent zone example.com in Account A.
C. Use AWS Certificate Manager Private Certificate Authority to create a subordinate certificate authority (CA). Use ACM to generate a private certificate that supports managed renewal.
D. Resend the email message that requests ownership validation of dev.example.com.
A company has multiple accounts in the AWS Cloud. Users in the developer account need to have access to specific resources in the production account. What is the MOST secure way to provide this access?
A. Create one IAM user in the production account. Grant the appropriate permissions to the resources that are needed. Share the password only with the users that need access.
B. Create cross-account access with an IAM role in the developer account. Grant the appropriate permissions to this role. Allow users in the developer account to assume this role to access the production resources.
C. Create cross-account access with an IAM user account in the production account. Grant the appropriate permissions to this user account. Allow users in the developer account to use this user account to access the production resources.
D. Create cross-account access with an IAM role in the production account. Grant the appropriate permissions to this role. Allow users in the developer account to assume this role to access the production resources.
A company wants to implement host-based security for Amazon EC2 instances and containers in Amazon Elastic Container Registry (Amazon ECR). The company has deployed AWS Systems Manager Agent (SSM Agent) on the EC2 instances. All the company's AWS accounts are in one organization in AWS Organizations. The company will analyze the workloads for software vulnerabilities and unintended network exposure. The company will push any findings to AWS Security Hub, which the company has configured for the organization. The company must deploy the solution to all member accounts, including new accounts, automatically. When new workloads come online, the solution must scan the workloads. Which solution will meet these requirements?
A. Use SCPs to configure scanning of EC2 instances and ECR containers for all accounts in the organization.
B. Configure a delegated administrator for Amazon GuardDuty for the organization. Create an Amazon EventBridge rule to initiate analysis of ECR containers.
C. Configure a delegated administrator for Amazon Inspector for the organization. Configure automatic scanning for new member accounts.
D. Configure a delegated administrator for Amazon Inspector for the organization. Create an AWS Config rule to initiate analysis of ECR containers.
A company uses AWS Organizations. The company has teams that use an AWS CloudHSM hardware security module (HSM) that is hosted in a central AWS account. One of the teams creates its own new dedicated AWS account and wants to use the HSM that is hosted in the central account. How should a security engineer share the HSM that is hosted in the central account with the new dedicated account?
A. Use AWS Resource Access Manager (AWS RAM) to share the VPC subnet ID of the HSM that is hosted in the central account with the new dedicated account. Configure the CloudHSM security group to accept inbound traffic from the private IP addresses of client instances in the new dedicated account.
B. Use AWS Identity and Access Management (IAM) to create a cross-account role to access the CloudHSM cluster that is in the central account. Create a new IAM user in the new dedicated account. Assign the cross-account role the new IAM user.
C. Use AWS Single Sign-On to create an AWS Security Token Service (AWS STS) token to authenticate from the new dedicated account to the central account. Use the cross-account permissions that are assigned to the STS token to invoke an operation on the HSM in the central account.
D. Use AWS Resource Access Manager (AWS RAM) to share the ID of the HSM that is hosted in the central account with the new dedicated account. Configure the CloudHSM security group to accept inbound traffic from the private IP addresses of client instances in the new dedicated account.
A company wants to use AWS Systems Manager Patch Manager to patch Amazon EC2 instances that run Amazon Linux 2. The EC2 instances are running in a single AWS account. No internet connectivity is allowed from any EC2 instances in the account. A security engineer has configured the relevant settings in Patch Manager. The security engineer now needs to ensure that the EC2 instances can connect to the Systems Manager endpoint. Which combination of steps must the security engineer take to meet these requirements? (Choose three.)
A. Create a gateway VPC endpoint for com.amazonaws.[region].s3.
B. Create VPC endpoints for com.amazonaws.[region].ec2messages and com.amazonaws.[region].ssm.
C. Create a NAT gateway.
D. Update the route tables to route Systems Manager traffic through the NAT gateway.
E. Update the route tables with a route to the gateway VPC endpoint.
F. Update the route tables to route the update traffic through the NAT gateway.
A security engineer needs to create an Amazon S3 bucket policy to grant least privilege read access to IAM user accounts that are named User1, User2 and User3. These IAM user accounts are members of the AuthorizedPeople IAM group. The security engineer drafts the following S3 bucket policy:When the security engineer tries to add the policy to the S3 bucket, the following message appears: `Missing required field Principal.` The security engineer is adding a Principal element to the policy. The addition must provide read access to only User1, User2 and User3. Which solution meets these requirements? A.
B.
C.
D.
A company has decided to migrate sensitive documents from on-premises data centers to Amazon S3. Currently, the hard drives are encrypted to meet a compliance requirement regarding data encryption. The CISO wants to improve security by encrypting each file using a different key instead of a single key. Using a different key would limit the security impact of a single exposed key. Which of the following requires the LEAST amount of configuration when implementing this approach?
A. Place each file into a different S3 bucket. Set the default encryption of each bucket to use a different AWS KMS customer managed key.
B. Put all the files in the same S3 bucket. Using S3 events as a trigger, write an AWS Lambda function to encrypt each file as it is added using different AWS KMS data keys.
C. Use the S3 encryption client to encrypt each file individually using S3-generated data keys.
D. Place all the files in the same S3 bucket. Use server-side encryption with AWS KMS-managed keys (SSE-KMS) to encrypt the data.
A security engineer is working for a parent company that provides hosting and services to client companies. The parent company maintains an organization in AWS Organizations for all client company accounts. The parent company adds any new accounts to the organization when the new accounts are created. The parent company currently uses IAM users to administer the client company accounts. As more client accounts are added, the administration of the IAM accounts takes more time. The security engineer must design a solution to reduce the amount of time that the parent company spends on administration and access provisioning for client accounts. Which combination of steps should the security engineer take to meet these requirements? (Choose two.)
A. Provision an external identity provider (IdP) for the parent company. Implement AWS Single Sign-On (AWS SSO) with the IdP as the identity source for AWS SSO.
B. Provision an external identity provider (IdP) for each client company. Implement AWS Single Sign-On (AWS SSO) with the IdPs as the identity source for AWS SSO.
C. Provision an external identity provider (IdP) for the parent company. Implement AWS Single Sign-On (AWS SSO) with employee IAM roles as the identity source for AWS SSO.
D. In the AWS Single Sign-On console, select the users who require access to client accounts. Assign these users to the accounts.
E. In the IAM console, select the users who require access to client accounts. Assign these users to the accounts.
A company has deployed Amazon GuardDuty and now wants to implement automation for potential threats. The company has decided to start with RDP brute force attacks that come from Amazon EC2 instances in the company’s AWS environment. A security engineer needs to implement a solution that blocks the detected communication from a suspicious instance until investigation and potential remediation can occur. Which solution will meet these requirements?
A. Configure GuardDuty to send the event to an Amazon Kinesis data stream. Process the event with an Amazon Kinesis Data Analytics for Apache Flink application that sends a notification to the company through Amazon Simple Notification Service (Amazon SNS). Add rules to the network ACL to block traffic to and from the suspicious instance.
B. Configure GuardDuty to send the event to Amazon EventBridge (Amazon CloudWatch Events). Deploy an AWS WAF web ACL. Process the event with an AWS Lambda function that sends a notification to the company through Amazon Simple Notification Service (Amazon SNS) and adds a web ACL rule to block traffic to and from the suspicious instance.
C. Enable AWS Security Hub to ingest GuardDuty findings and send the event to Amazon EventBridge (Amazon CloudWatch Events). Deploy AWS Network Firewall. Process the event with an AWS Lambda function that adds a rule to a Network Firewall firewall policy to block traffic to and from the suspicious instance.
D. Enable AWS Security Hub to ingest GuardDuty findings. Configure an Amazon Kinesis data stream as an event destination for Security Hub. Process the event with an AWS Lambda function that replaces the security group of the suspicious instance with a security group that does not allow any connections.
A company recently set up Amazon GuardDuty and is receiving a high number of findings from IP addresses within the company. A security engineer has verified that these IP addresses are trusted and allowed. Which combination of steps should the security engineer take to configure GuardDuty so that it does not produce findings for these IP addresses? (Choose two.)
A. Create a plaintext configuration file that contains the trusted IP addresses.
B. Create a JSON configuration file that contains the trusted IP addresses.
C. Upload the configuration file directly to GuardDuty.
D. Upload the configuration file to Amazon S3. Add a new trusted IP list to GuardDuty that points to the file.
E. Manually copy and paste the configuration file data into the trusted IP list in GuardDuty.
A user is implementing a third-party web application on an Amazon EC2 instance. All client communications must be over HTTPS, and traffic must be terminated before it reaches the instance. Communication to the instance must be over port 80. Company policy requires that workloads reside in private subnets. Which solution meets these requirements?
A. Create an Application Load Balancer. Add an HTTP listener for port 80 to redirect traffic to HTTPS on port 443. Add another listener with an AWS Certificate Manager (ACM) certificate for termination and a rule that forwards to the target instance through port 80.
B. Allocate an Elastic IP address that has SSL termination activated. Associate the Elastic IP address with the instance on port 80.
C. Create a Gateway Load Balancer. Add an HTTP listener for port 80 to redirect traffic to HTTPS on port 443. Add another listener with an AWS Certificate Manager (ACM) certificate for termination and a rule that forwards to the target instance through port 80.
D. Implement a Network Load Balancer. Add an HTTP listener for port 80 to redirect traffic to HTTPS on port 443. Add another listener with an AWS Certificate Manager (ACM) certificate for termination and a rule that forwards to the target instance through port 80.
A company's application uses standard tier secure string parameters from AWS Systems Manager Parameter Store. The application is receiving error messages when the company tries to update a parameter. The parameter uses an AWS Key Management Service (AWS KMS) customer managed key for encryption and decryption. What are the reasons for the error messages? (Choose two.)
A. The application does not have the kms:Encrypt permission for the customer managed key.
B. The customer managed key is already being used to encrypt another secure string parameter.
C. Standard tier secure string parameters cannot use a customer managed key for encryption.
D. The customer managed key that is specified in the application has its key state set to Disabled.
E. The customer managed key that is specified in the application is using a key alias instead of a key ID.
A company hosts a web-based application that captures and stores sensitive data in an Amazon DynamoDB table. A security audit reveals that the application does not provide end-to-end data protection or the ability to detect unauthorized data changes. The software engineering team needs to make changes that will address the audit findings. Which set of steps should the software engineering team take?
A. Use an AWS Key Management Service (AWS CMK) CMK. Encrypt the data at rest.
B. Use AWS Certificate Manager (ACM) Private Certificate Authority. Encrypt the data in transit.
C. Use a DynamoDB encryption client. Use client-side encryption and sign the table items.
D. Use the AWS Encryption SDK. Use client-side encryption and sign the table items.
A company plans to migrate a sensitive dataset to Amazon S3. A Security Engineer must ensure that the data is encrypted at rest. The encryption solution must enable the company to generate its own keys without needing to manage key storage or the encryption process. What should the Security Engineer use to accomplish this?
A. Server-side encryption with Amazon S3-managed keys (SSE-S3)
B. Server-side encryption with AWS KMS-managed keys (SSE-KMS)
C. Server-side encryption with customer-provided keys (SSE-C)
D. Client-side encryption with an AWS KMS-managed CMK
A company is implementing a new application in a new AWS account. A VPC and subnets have been created for the application. The application has been peered to an existing VPC in another account in the same AWS Region for database access. Amazon EC2 instances will regularly be created and terminated in the application VPC, but only some of them will need access to the databases in the peered VPC over TCP port 1521. A security engineer must ensure that only the EC2 instances than need access to the databases can access them through the network. How can the security engineer implement this solution?
A. Create a new security group in the database VPC and create an inbound rule that allows all traffic from the IP address range of the application VPC. Add a new network ACL rule on the database subnets. Configure the rule to TCP port 1521 from the IP address range of the application VPC. Attach the new security group to the database instances that the application instances need to access.
B. Create a new security group in the application VPC with an inbound rule that allows the IP address range of the database VPC over TCP port 1521. Create a new security group in the database VPC with an inbound rule that allows the IP address range of the application VPC over port 1521. Attach the new security group to the database instances and the application instances that need database access.
C. Create a new security group in the application VPC with no inbound rules. Create a new security group in the database VPC with an inbound rule that allows TCP port 1521 from the new application security group in the application VPC. Attach the application security group to the application instances that need database access, and attach the database security group to the database instances.
D. Create a new security group in the application VPC with an inbound rule that allows the IP address range of the database VPC over TCP port 1521. Add a new network ACL rule on the database subnets. Configure the rule to allow all traffic from the IP address range of the application VPC. Attach the new security group to the application instances that need database access.
The security engineer implemented a new vault stock policy for 10TB of data and called initiate-vault-lock 12 hours ago. The audit team identified a typo that is allowing incorrect access to the vault. What is the MOST cost-effective way to correct this?
A. Call the abort-vault-lock operation, fix the typo, and call the initiate-vault-lock again.
B. Copy the vault data to Amazon S3, delete the vault, and create a new vault with the data.
C. Update the policy, keeping the vault lock in place.
D. Update the policy, and call initiate-vault-lock again to apply the new policy.
Access Full SCS-C01 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete SCS-C01 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our SCS-C01 mock test free today—and take a major step toward exam success!