SC-900 Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the SC-900 certification exam? Kickstart your success with our SC-900 Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with SC-900 practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free SC-900 practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
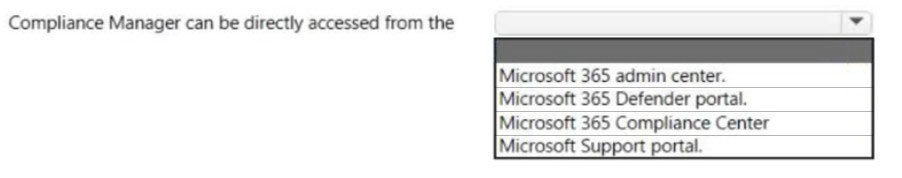
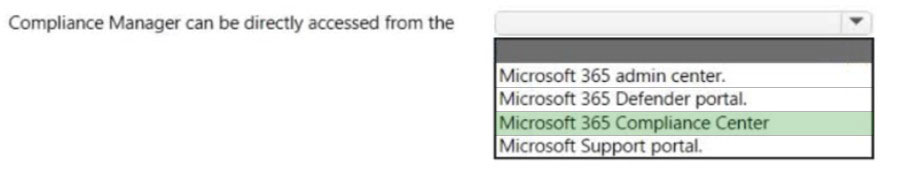
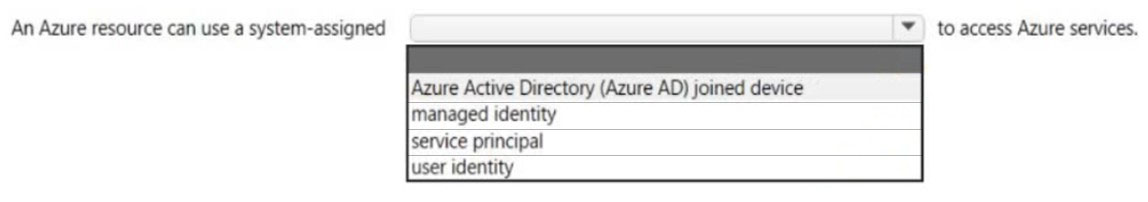
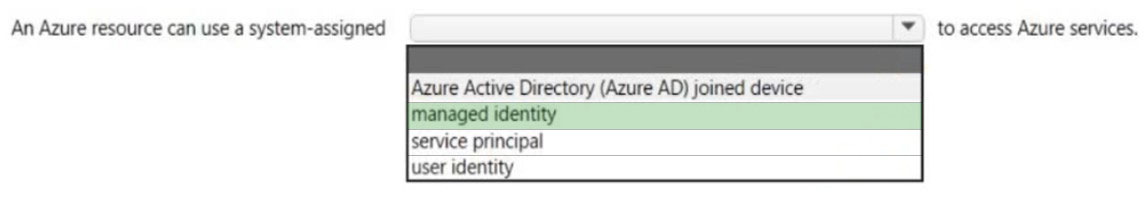
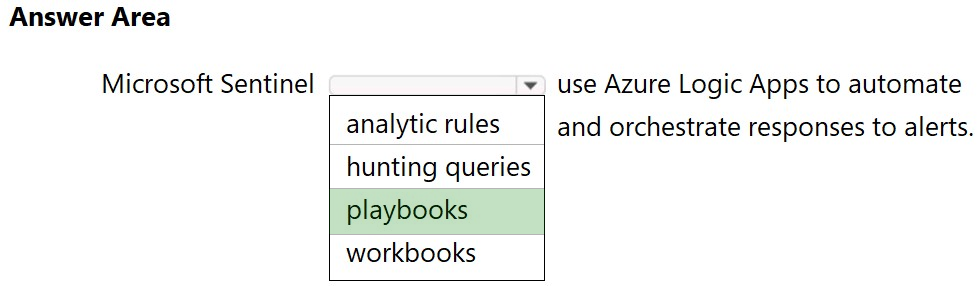
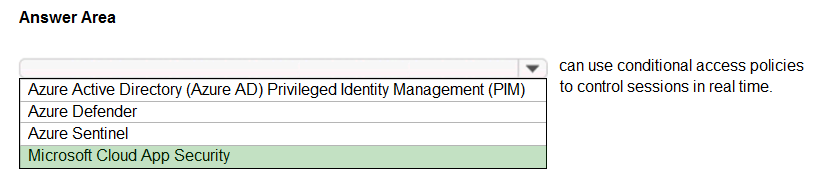
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
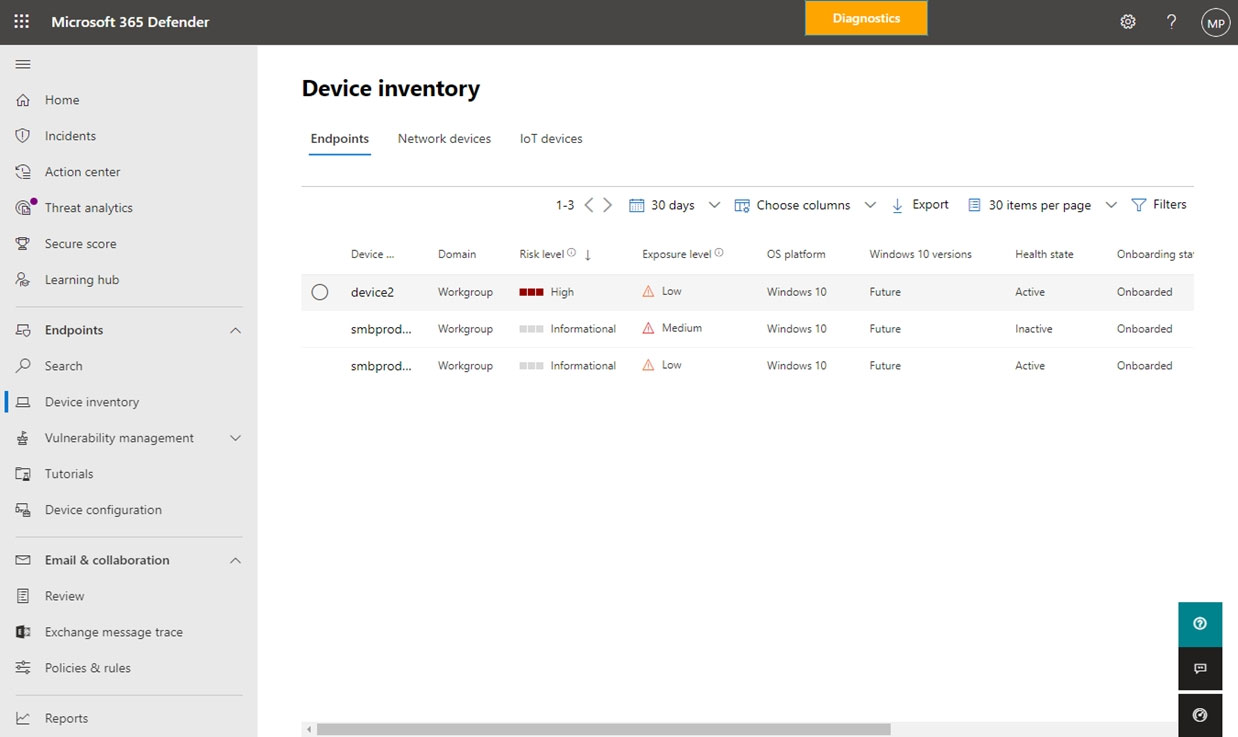
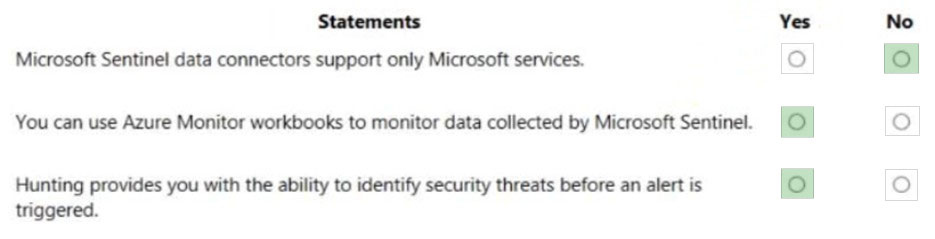
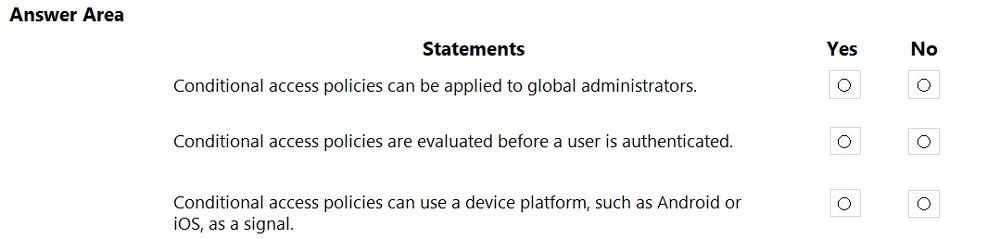
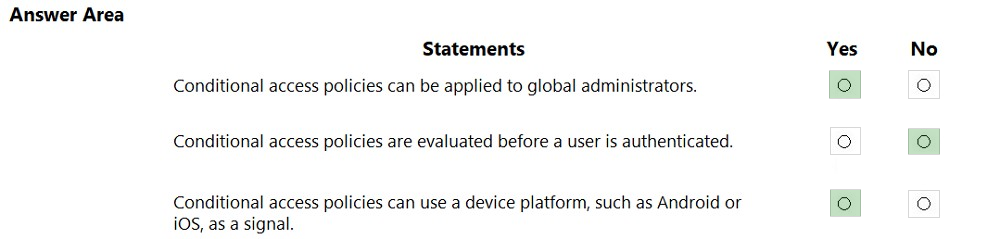
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
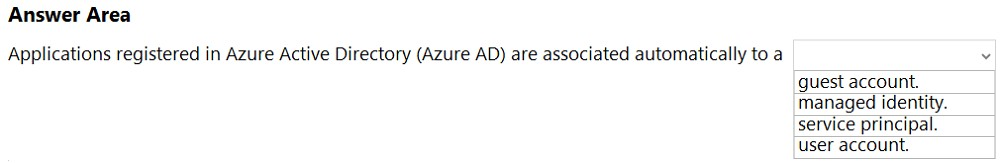
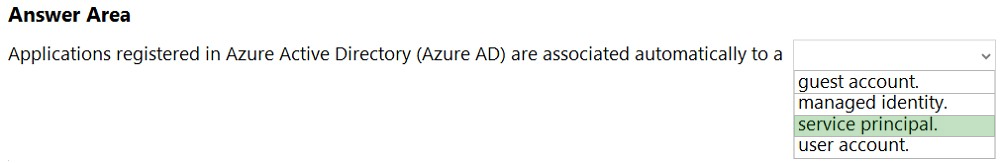
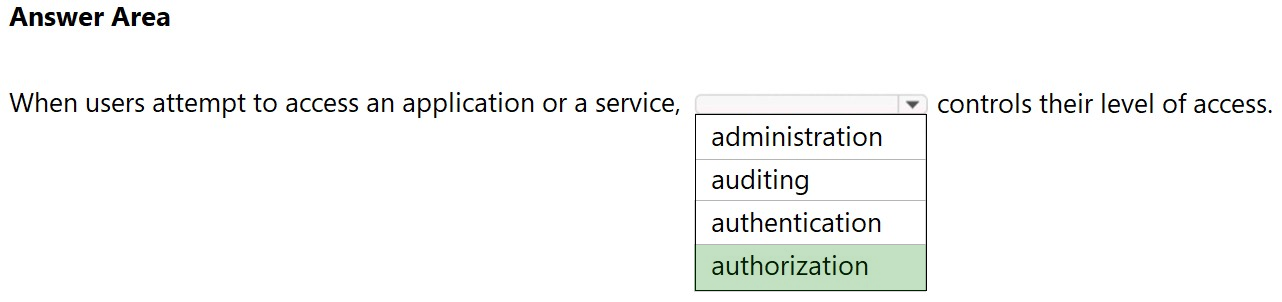
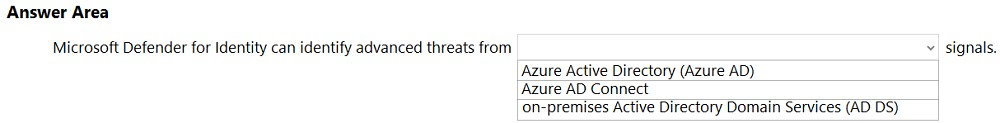
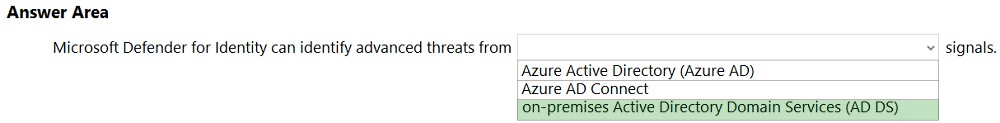
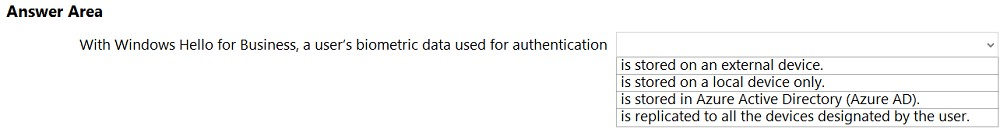
HOTSPOT - Select the answer that correctly completes the sentence.
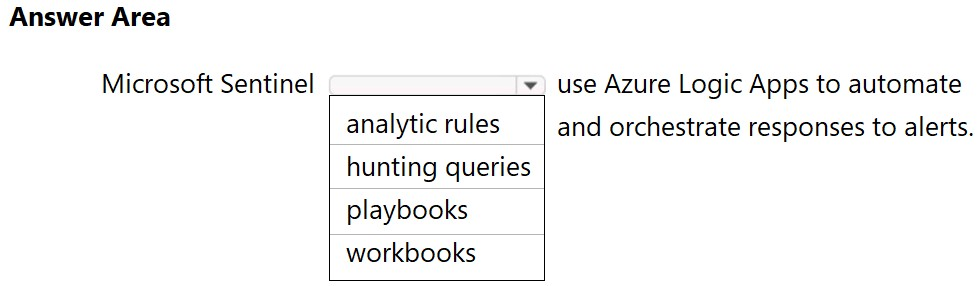
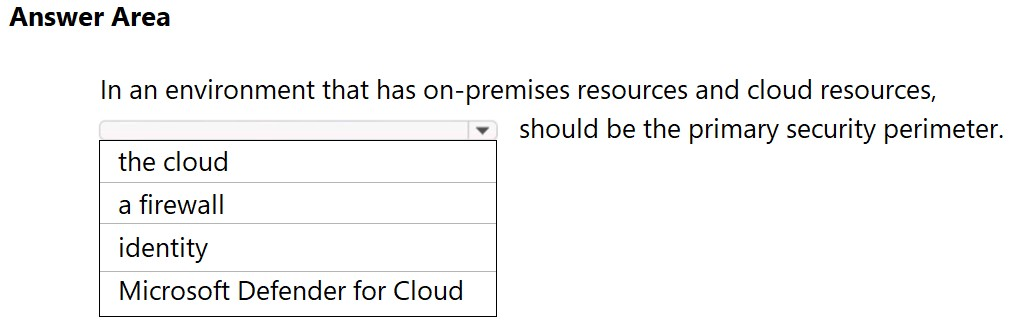
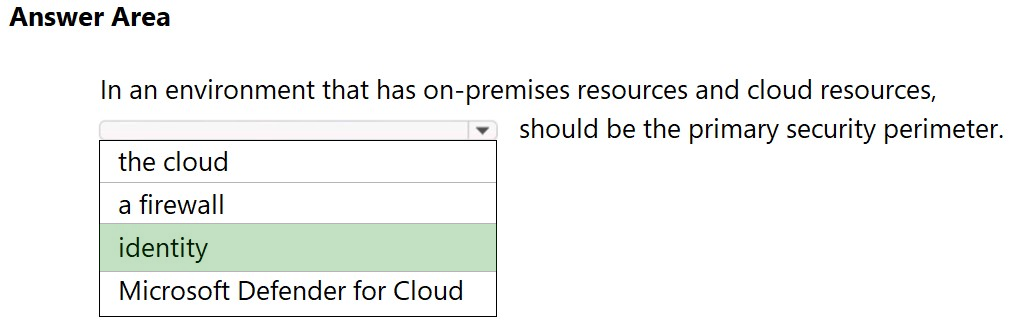
HOTSPOT - Select the answer that correctly completes the sentence.
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
What are three uses of Microsoft Cloud App Security? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. to discover and control the use of shadow IT
B. to provide secure connections to Azure virtual machines
C. to protect sensitive information hosted anywhere in the cloud
D. to provide pass-through authentication to on-premises applications
E. to prevent data leaks to noncompliant apps and limit access to regulated data
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
Which score measures an organization's progress in completing actions that help reduce risks associated to data protection and regulatory standards?
A. Microsoft Secure Score
B. Productivity Score
C. Secure score in Azure Security Center
D. Compliance score
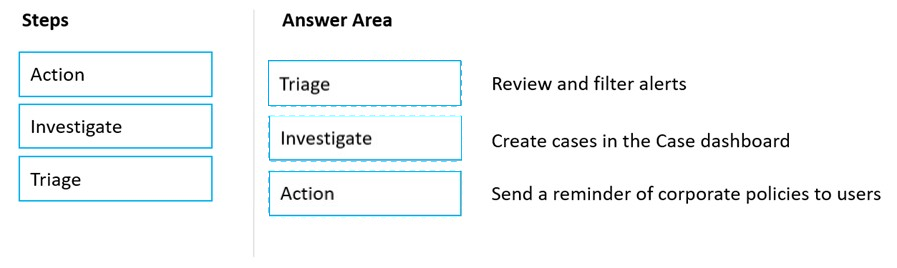
DRAG DROP - Match the Microsoft Purview Insider Risk Management workflow step to the appropriate task. To answer, drag the appropriate step from the column on the left to its task on the right. Each step may be used once, more than once, or not at all. NOTE: Each correct match is worth one point.
HOTSPOT - Select the answer that correctly completes the sentence.
What is a characteristic of a sensitivity label in Microsoft 365?
A. encrypted
B. restricted to predefined categories
C. persistent
You have an Azure subscription that contains multiple resources. You need to assess compliance and enforce standards for the existing resources. What should you use?
A. Azure Blueprints
B. the Anomaly Detector service
C. Microsoft Sentinel
D. Azure Policy
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
What should you use to ensure that the members of an Azure Active Directory group use multi-factor authentication (MFA) when they sign in?
A. Azure role-based access control (Azure RBAC)
B. Azure Active Directory (Azure AD) Privileged Identity Management (PIM)
C. Azure Active Directory (Azure AD) Identity Protection
D. a conditional access policy
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
Which two cards are available in the Microsoft 365 Defender portal? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Devices at risk
B. Compliance Score
C. Service Health
D. User Management
E. Users at risk
What is the maximum number of resources that Azure DDoS Protection Standard can protect without additional costs?
A. 50
B. 100
C. 500
D. 1000
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
What is Azure Key Vault used for?
A. to deploy a cloud-based network security service that protects Azure virtual network resources
B. to protect cloud-based applications from cyber threats and vulnerabilities
C. to safeguard cryptographic keys and other secrets used by cloud apps and services
D. to provide secure and seamless RDP/SSH connectivity to Azure virtual machines via TLS from the Azure portal
Which Microsoft 365 feature can you use to restrict users from sending email messages that contain lists of customers and their associated credit card numbers?
A. retention policies
B. data loss prevention (DLP) policies
C. conditional access policies
D. information barriers
Microsoft 365 Endpoint data loss prevention (Endpoint DLP) can be used on which operating systems?
A. Windows 10 and newer only
B. Windows 10 and newer and Android only
C. Windows 10 and newer and iOS only
D. Windows 10 and newer, Android, and iOS
You need to ensure repeatability when creating new resources in an Azure subscription. What should you use?
A. Microsoft Sentinel
B. Azure Policy
C. Azure Batch
D. Azure Blueprints
DRAG DROP - Match the Microsoft 365 insider risk management workflow step to the appropriate task. To answer, drag the appropriate step from the column on the left to its task on the right. Each step may be used once, more than once, or not at all. NOTE: Each correct match is worth one point. Select and Place:
DRAG DROP - Match the types of compliance score actions to the appropriate tasks. To answer, drag the appropriate action type from the column on the left to its task on the right. Each type may be used once, more than once, or not at all. NOTE: Each correct match is worth one point.
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
Which Microsoft 365 compliance center feature can you use to identify all the documents on a Microsoft SharePoint Online site that contain a specific key word?
A. Audit
B. Compliance Manager
C. Content Search
D. Alerts
You have an Azure subscription that contains a Log Analytics workspace. You need to onboard Microsoft Sentinel. What should you do first?
A. Create a hunting query.
B. Correlate alerts into incidents.
C. Connect to your data sources.
D. Create a custom detection rule.
Which Microsoft portal provides information about how Microsoft cloud services comply with regulatory standard, such as International Organization for Standardization (ISO)?
A. the Microsoft 365 admin center
B. Azure Cost Management + Billing
C. Microsoft Service Trust Portal
D. the Microsoft Purview compliance portal
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
What can you use to protect against malicious links sent in email messages, chat messages, and channels?
A. Microsoft Defender for Cloud Apps
B. Microsoft Defender for Office 365
C. Microsoft Defender for Endpoint
D. Microsoft Defender for Identity
Which three authentication methods can be used by Azure Multi-Factor Authentication (MFA)? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. text message (SMS)
B. Microsoft Authenticator app
C. email verification
D. phone call
E. security question
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
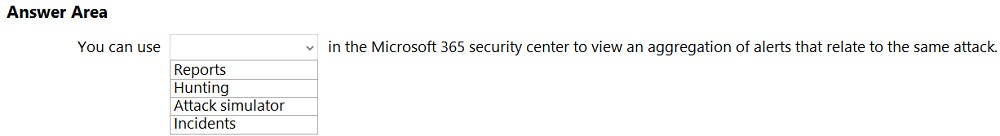
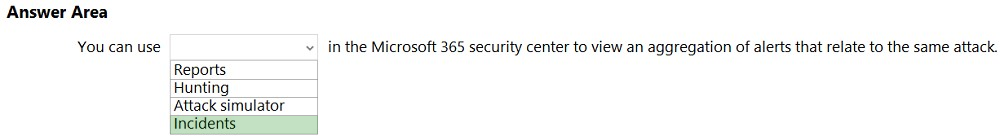
What should you use in the Microsoft 365 Defender portal to view security trends and track the protection status of identities?
A. Reports
B. Incidents
C. Hunting
D. Secure score
Which three forms of verification can be used with Azure AD Multi-Factor Authentication (MFA)? Each correct answer presents a complete solution. NOTE: Each correct answer is worth one point.
A. security questions
B. the Microsoft Authenticator app
C. SMS messages
D. a smart card
E. Windows Hello for Business
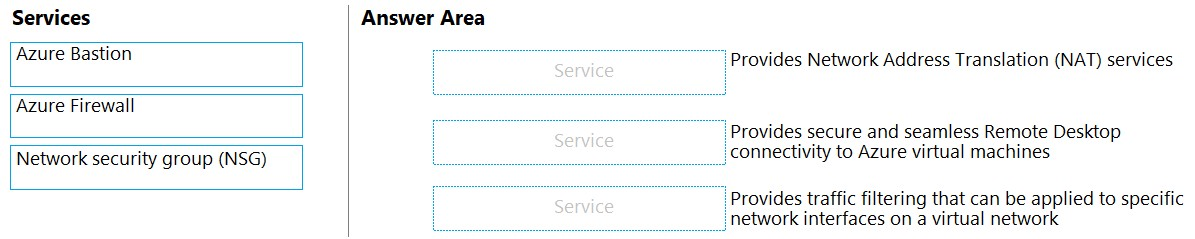
DRAG DROP - Match the Azure networking service to the appropriate description. To answer, drag the appropriate service from the column on the left to its description on the right. Each service may be used once, more than once, or not at all. NOTE: Each correct match is worth one point. Select and Place:
HOTSPOT - Select the answer that correctly completes the sentence.
When a user authenticates by using passwordless sign-in, what should the user select in the Microsoft Authenticator app?
A. an answer to a security question
B. a number
C. an alphanumeric key
D. a passphrase
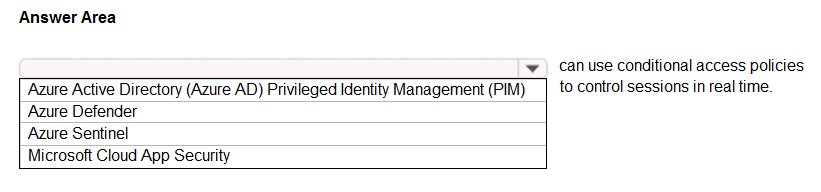
What can you use to provide a user with a two-hour window to complete an administrative task in Azure?
A. Azure Active Directory (Azure AD) Privileged Identity Management (PIM)
B. Azure Multi-Factor Authentication (MFA)
C. Azure Active Directory (Azure AD) Identity Protection
D. conditional access policies
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
You plan to implement a security strategy and place multiple layers of defense throughout a network infrastructure. Which security methodology does this represent?
A. threat modeling
B. identity as the security perimeter
C. defense in depth
D. the shared responsibility model
HOTSPOT - Select the answer that correctly completes the sentence.
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
You need to create a data loss prevention (DLP) policy. What should you use?
A. the Microsoft 365 Compliance center
B. the Microsoft Endpoint Manager admin center
C. the Microsoft 365 admin center
D. the Microsoft 365 Defender portal
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
Free Access Full SC-900 Practice Questions Free
Want more hands-on practice? Click here to access the full bank of SC-900 practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your SC-900 certification journey!