SC-900 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the SC-900 certification? Take your preparation to the next level with our SC-900 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a SC-900 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic SC-900 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
HOTSPOT - Which service should you use to view your Azure secure score? To answer, select the appropriate service in the answer area. Hot Area:
Which three authentication methods can be used by Azure Multi-Factor Authentication (MFA)? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. text message (SMS)
B. Microsoft Authenticator app
C. email verification
D. phone call
E. security question
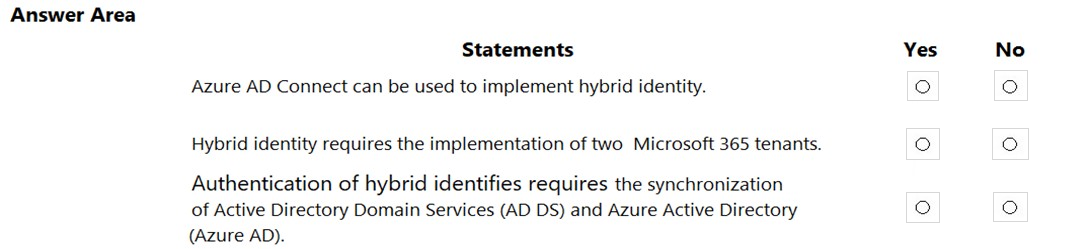
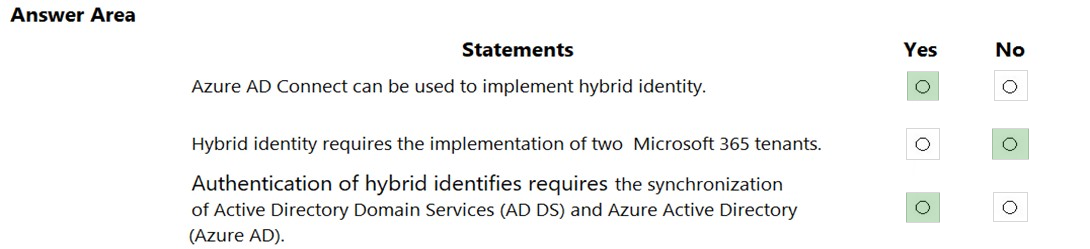
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
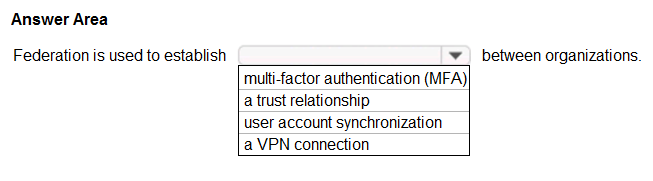
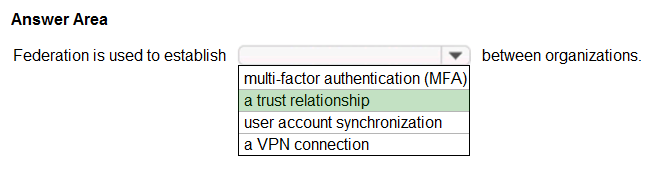
HOTSPOT - Select the answer that correctly completes the sentence.
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
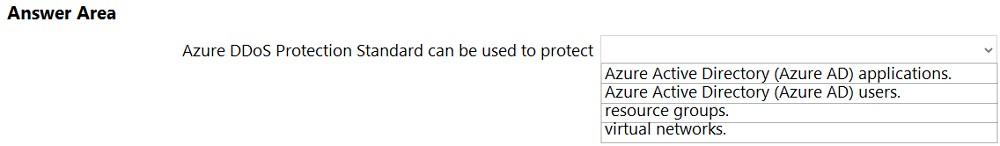
Which two types of resources can be protected by using Azure Firewall? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Azure virtual machines
B. Azure Active Directory (Azure AD) users
C. Microsoft Exchange Online inboxes
D. Azure virtual networks
E. Microsoft SharePoint Online sites
Which Microsoft Purview solution can be used to identify data leakage?
A. insider risk management
B. Compliance Manager
C. communication compliance
D. eDiscovery
Which score measures an organization’s progress in completing actions that help reduce risks associated to data protection and regulatory standards?
A. Adoption Score
B. Microsoft Secure Score
C. Secure score in Microsoft Defender for Cloud
D. Compliance score
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
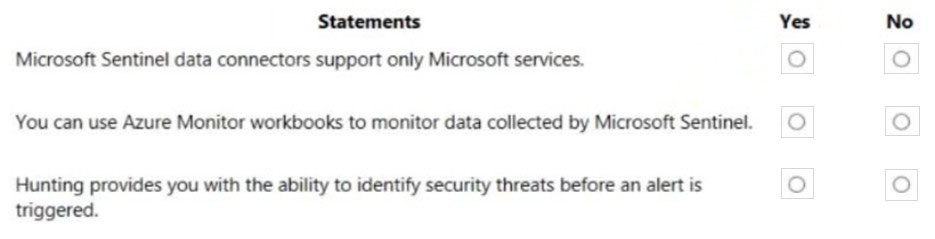
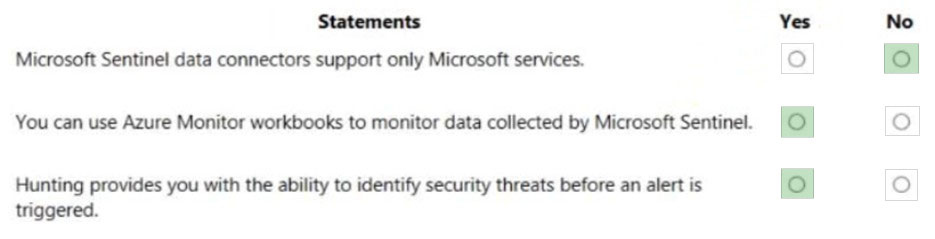
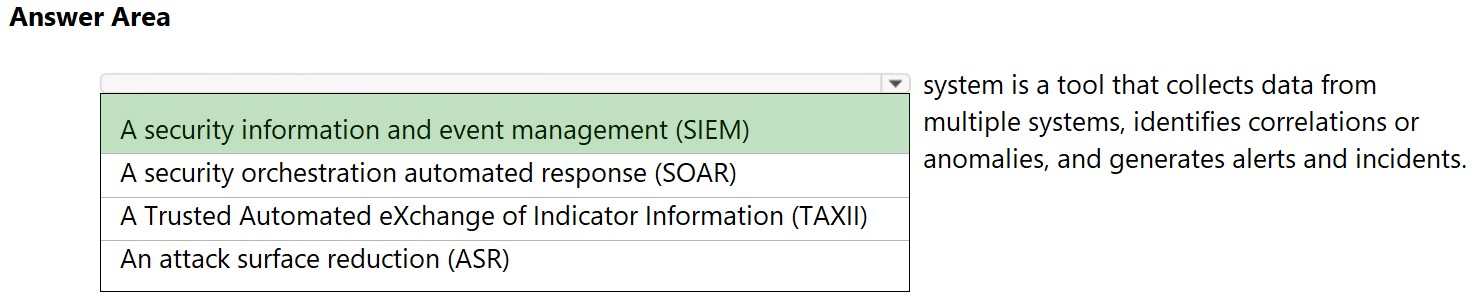
What do you use to provide real-time integration between Azure Sentinel and another security source?
A. Azure AD Connect
B. a Log Analytics workspace
C. Azure Information Protection
D. a connector
Which Microsoft Defender for Cloud metric displays the overall security health of an Azure subscription?
A. secure score
B. resource health
C. completed controls
D. the status of recommendations
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
What feature in Microsoft Defender for Endpoint provides the first line of defense against cyberthreats by reducing the attack surface?
A. automated remediation
B. automated investigation
C. advanced hunting
D. network protection
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
In the Microsoft Cloud Adoption Framework for Azure, which two phases are addressed before the Ready phase? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Plan
B. Manage
C. Adopt
D. Govern
E. Define Strategy
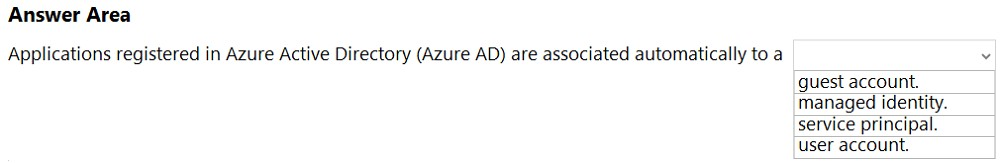
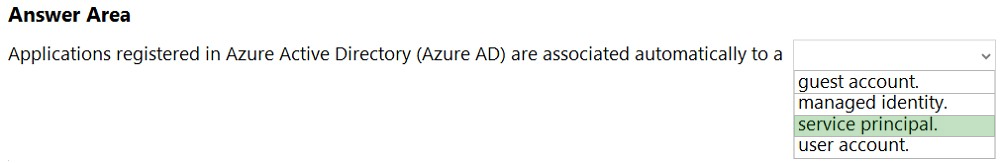
Which type of identity is created when you register an application with Active Directory (Azure AD)?
A. a user account
B. a user-assigned managed identity
C. a system-assigned managed identity
D. a service principal
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
Which score measures an organization's progress in completing actions that help reduce risks associated to data protection and regulatory standards?
A. Microsoft Secure Score
B. Productivity Score
C. Secure score in Azure Security Center
D. Compliance score
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
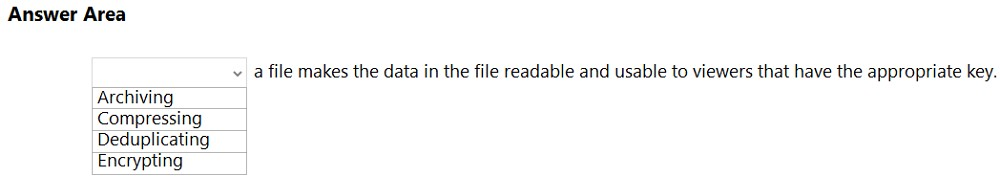
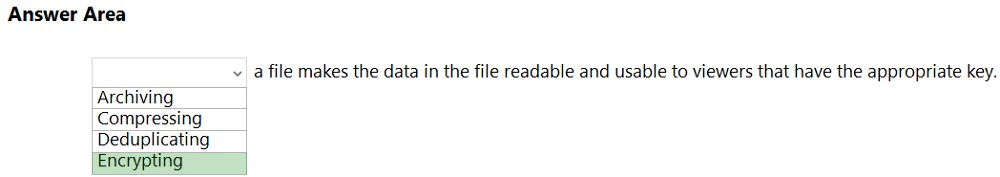
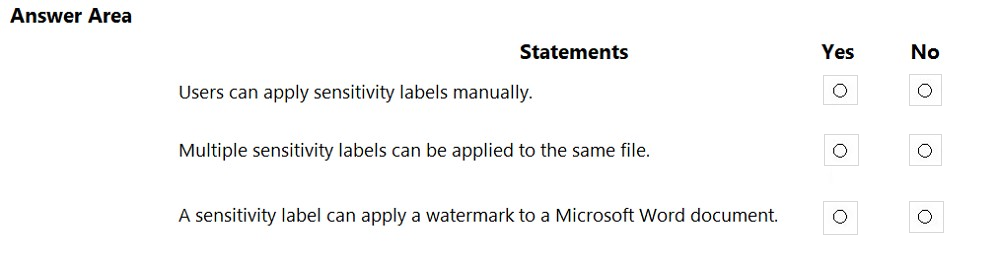
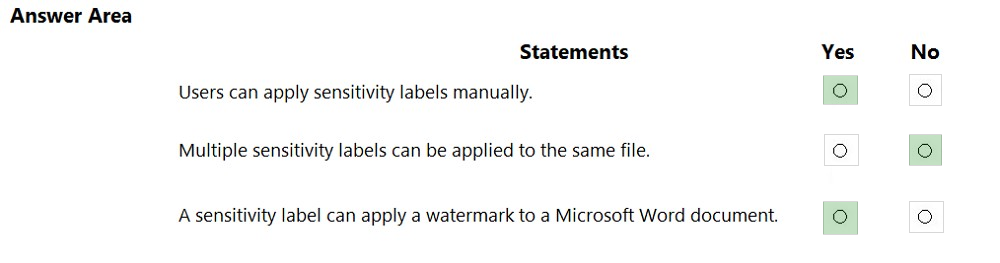
What can you specify in Microsoft 365 sensitivity labels?
A. how long files must be preserved
B. when to archive an email message
C. which watermark to add to files
D. where to store files
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
What is Azure Key Vault used for?
A. to deploy a cloud-based network security service that protects Azure virtual network resources
B. to protect cloud-based applications from cyber threats and vulnerabilities
C. to safeguard cryptographic keys and other secrets used by cloud apps and services
D. to provide secure and seamless RDP/SSH connectivity to Azure virtual machines via TLS from the Azure portal
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
Which compliance feature should you use to identify documents that are employee resumes?
A. pre-trained classifiers
B. Activity explorer
C. eDiscovery
D. Content explorer
What can you use to provide threat detection for Azure SQL Managed Instance?
A. Microsoft Secure Score
B. application security groups
C. Microsoft Defender for Cloud
D. Azure Bastion
You need to create a data loss prevention (DLP) policy. What should you use?
A. the Microsoft 365 Compliance center
B. the Microsoft Endpoint Manager admin center
C. the Microsoft 365 admin center
D. the Microsoft 365 Defender portal
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
DRAG DROP - You need to identify which cloud service models place the most responsibility on the customer in a shared responsibility model. In which order should you list the service models from the most customer responsibility to the least? To answer, move all models from the list of models to the answer area and arrange them in the correct order.
HOTSPOT - Select the answer that correctly completes the sentence.
HOTSPOT - Select the answer that correctly completes the sentence.
Which two tasks can you implement by using data loss prevention (DLP) policies in Microsoft 365? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Display policy tips to users who are about to violate your organization’s policies.
B. Enable disk encryption on endpoints.
C. Protect documents in Microsoft OneDrive that contain sensitive information.
D. Apply security baselines to devices.
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
Microsoft 365 Endpoint data loss prevention (Endpoint DLP) can be used on which operating systems?
A. Windows 10 and newer only
B. Windows 10 and newer and Android only
C. Windows 10 and newer and macOS only
D. Windows 10 and newer, Android, and macOS
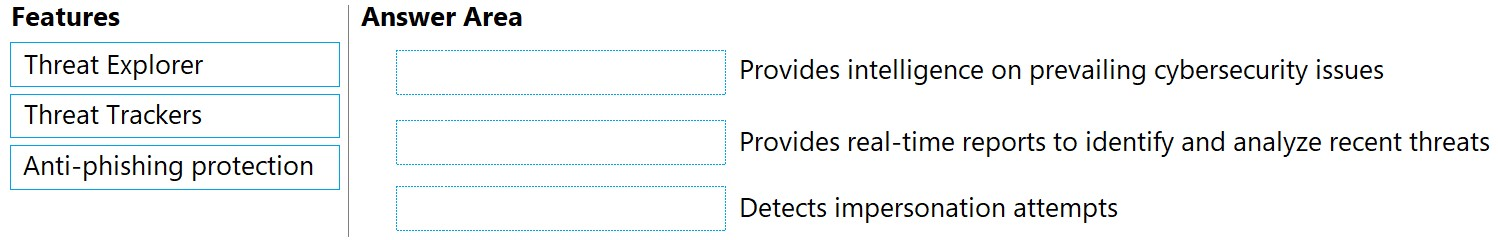
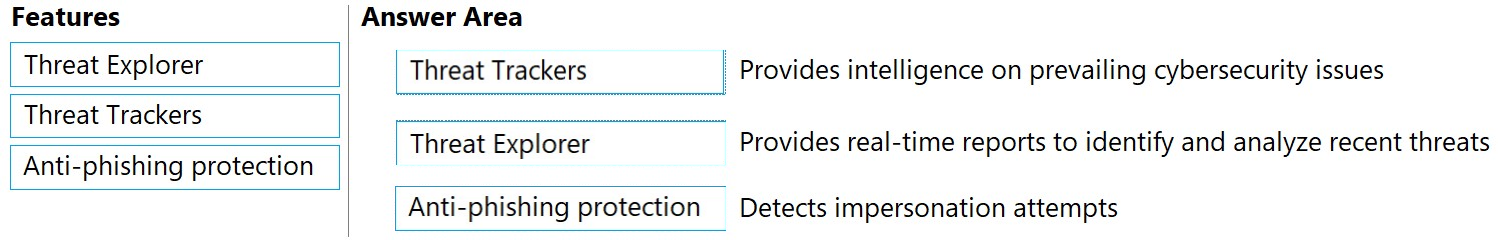
DRAG DROP - Match the Microsoft Defender for Office 365 feature to the correct description. To answer, drag the appropriate feature from the column on the left to its description on the right. Each feature may be used once, more than once, or not at all. NOTE: Each correct match is worth one point. Select and Place:
HOTSPOT - Select the answer that correctly completes the sentence.
You have an Azure subscription. You need to implement approval-based, time-bound role activation. What should you use?
A. access reviews in Azure AD
B. Azure AD Privileged Identity Management (PIM)
C. Azure AD Identity Protection
D. Conditional access in Azure AD
HOTSPOT - Select the answer that correctly completes the sentence.
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You plan to move resources to the cloud. You are evaluating the use of Infrastructure as a service (IaaS), Platform as a service (PaaS), and Software as a service (SaaS) cloud models. You plan to manage only the data, user accounts, and user devices for a cloud-based app. Which cloud model will you use?
A. SaaS
B. PaaS
C. IaaS
Which portal contains the solution catalog?
A. Microsoft Purview compliance portal
B. Microsoft 365 Defender portal
C. Microsoft 365 admin center
D. Microsoft 365 Apps admin center
HOTSPOT - Select the answer that correctly completes the sentence.
Which Microsoft 365 compliance feature can you use to encrypt content automatically based on specific conditions?
A. Content Search
B. sensitivity labels
C. retention policies
D. eDiscovery
HOTSPOT - Select the answer that correctly completes the sentence.
HOTSPOT - Select the answer that correctly completes the sentence.
In the shared responsibility model for an Azure deployment, what is Microsoft solely responsible for managing?
A. the management of mobile devices
B. the permissions for the user data stored in Azure
C. the creation and management of user accounts
D. the management of the physical hardware
In a Core eDiscovery workflow, what should you do before you can search for content?
A. Create an eDiscovery hold.
B. Run Express Analysis.
C. Configure attorney-client privilege detection.
D. Export and download results.
Which Azure Active Directory (Azure AD) feature can you use to restrict Microsoft Intune-managed devices from accessing corporate resources?
A. network security groups (NSGs)
B. Azure AD Privileged Identity Management (PIM)
C. conditional access policies
D. resource locks
Which Azure Active Directory (Azure AD) feature can you use to provide just-in-time (JIT) access to manage Azure resources?
A. conditional access policies
B. Azure AD Identity Protection
C. Azure AD Privileged Identity Management (PIM)
D. authentication method policies
Free Access Full SC-900 Practice Exam Free
Looking for additional practice? Click here to access a full set of SC-900 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your SC-900 certification journey!