SC-900 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your SC-900 certification? Our SC-900 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an SC-900 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our SC-900 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
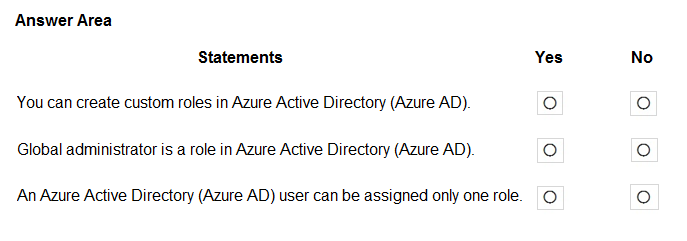
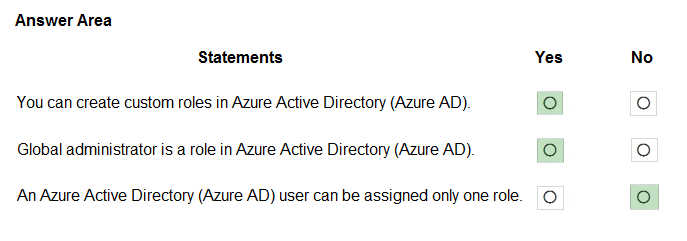
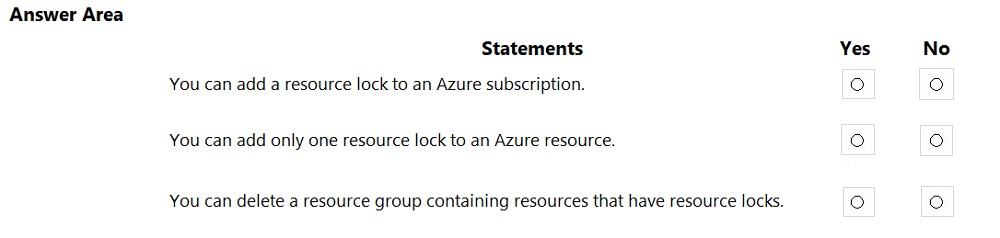
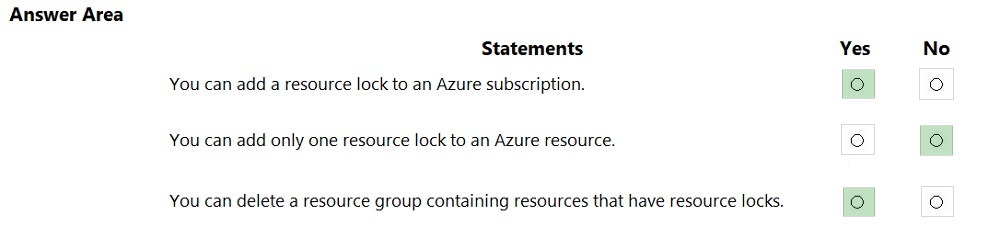
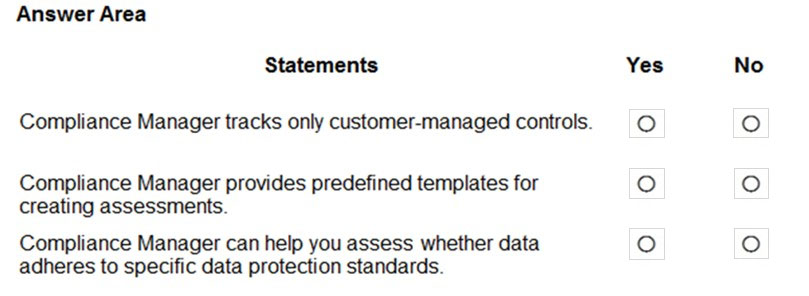
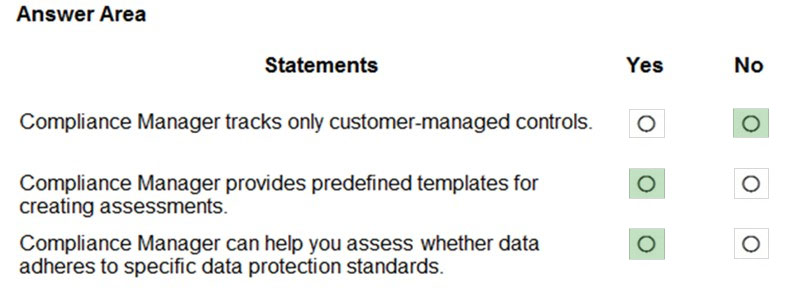
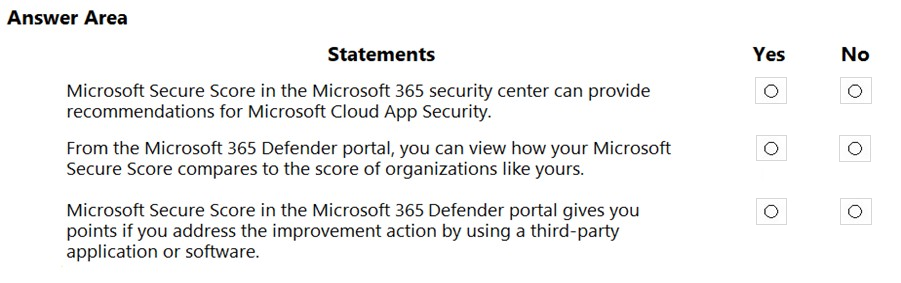
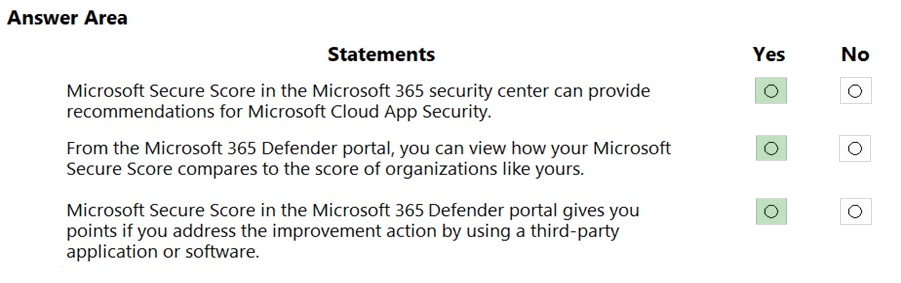
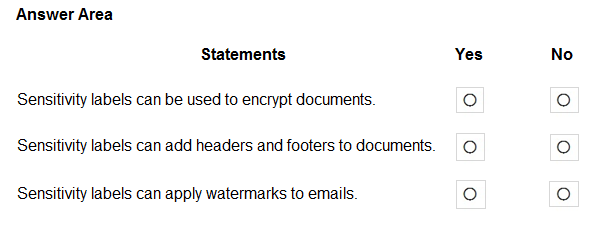
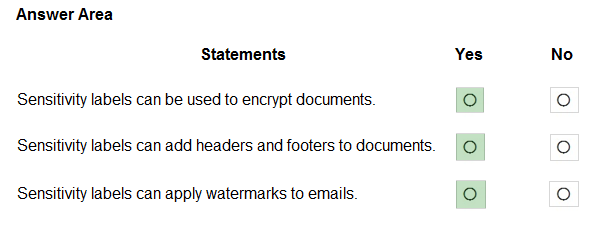
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
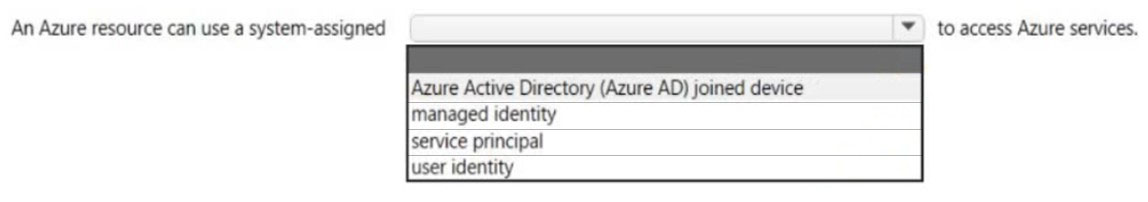
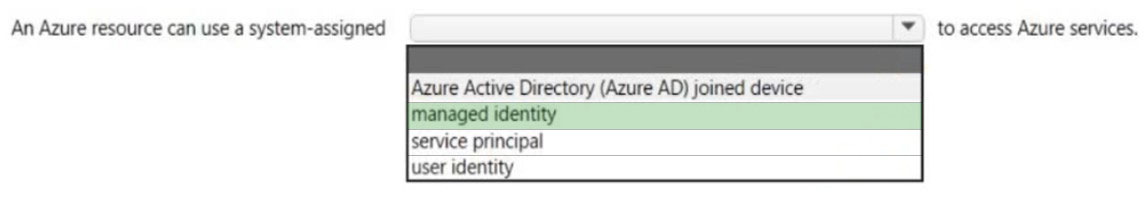
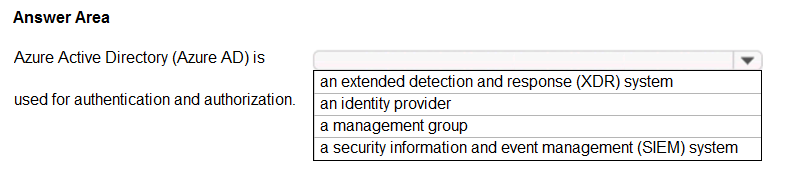
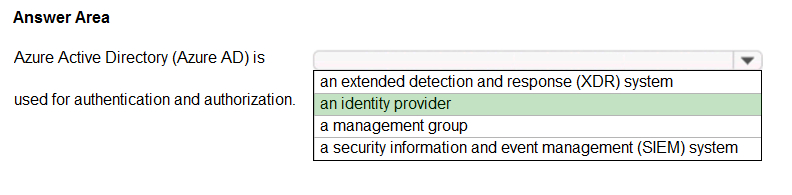
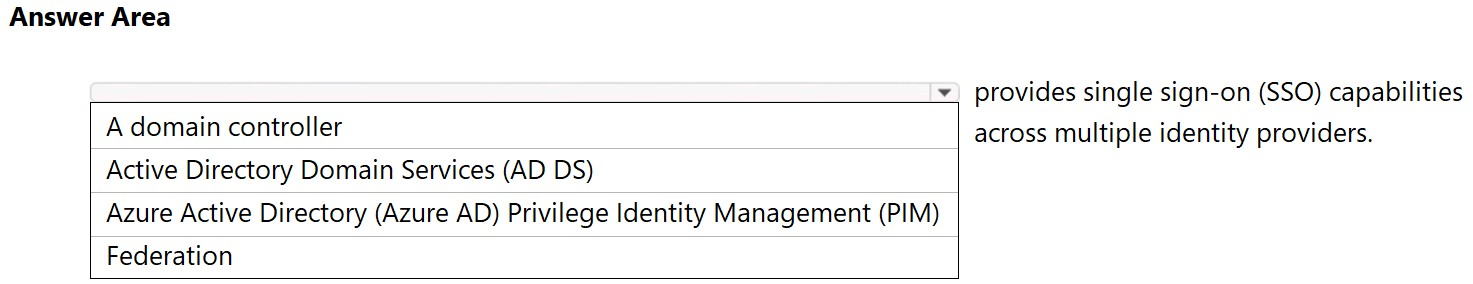
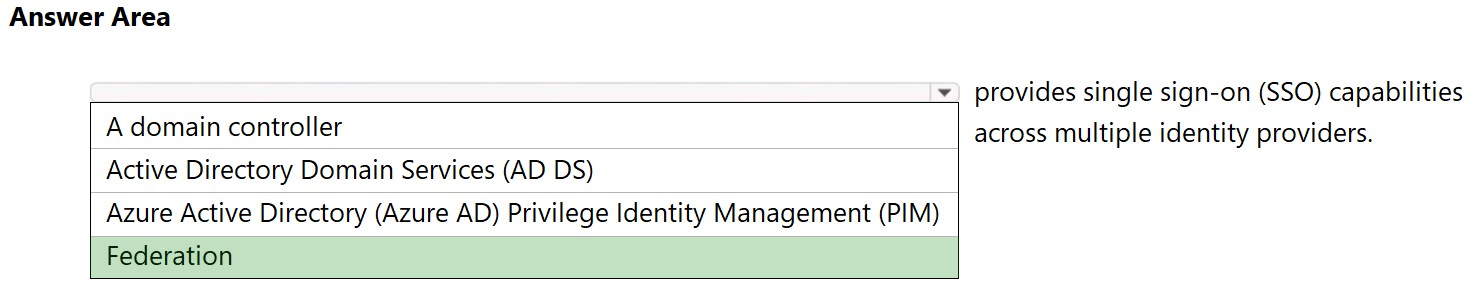
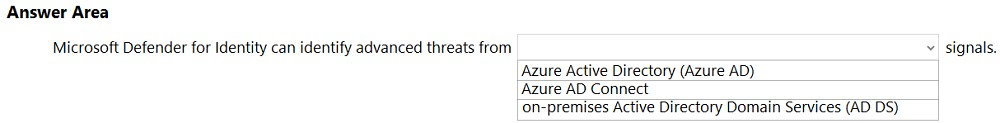
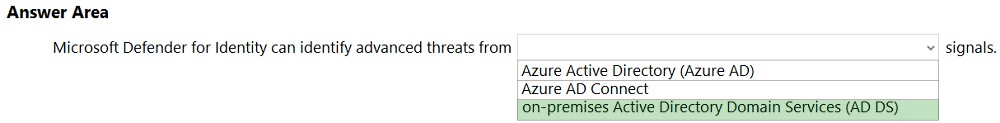
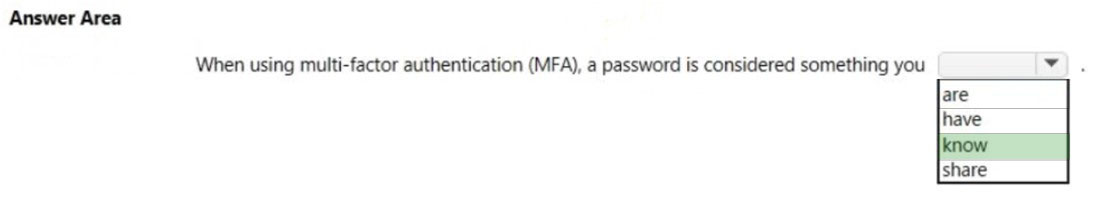
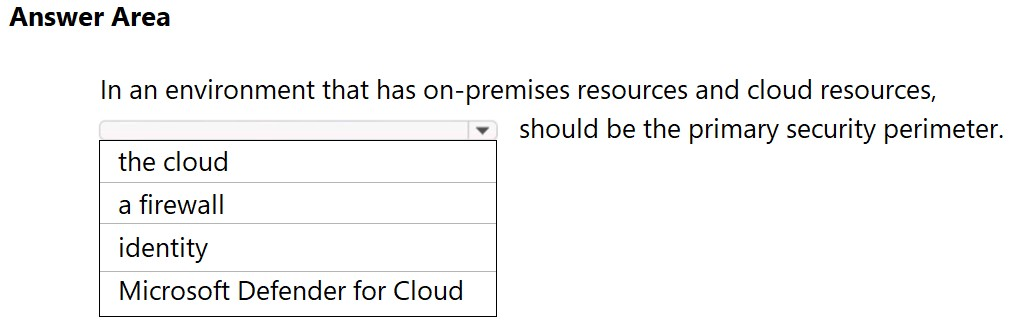
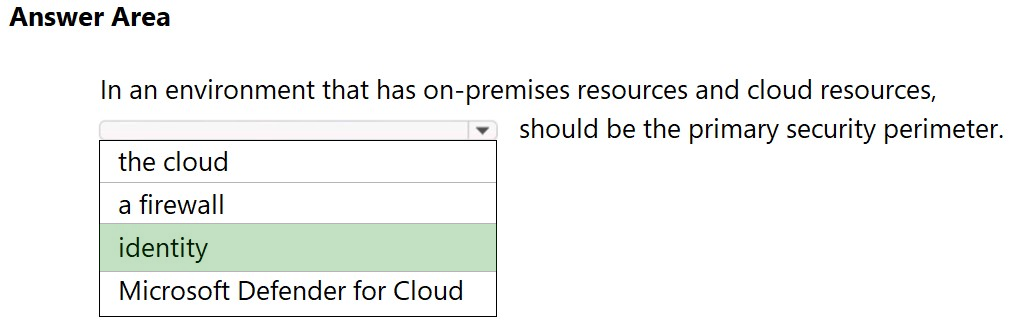
HOTSPOT - Select the answer that correctly completes the sentence.
What should you use in the Microsoft 365 Defender portal to view security trends and track the protection status of identities?
A. Attack simulator
B. Reports
C. Hunting
D. Incidents
HOTSPOT - Select the answer that correctly completes the sentence.
Which three authentication methods can be used by Azure Multi-Factor Authentication (MFA)? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. text message (SMS)
B. Microsoft Authenticator app
C. email verification
D. phone call
E. security question
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
What are two capabilities of Microsoft Defender for Endpoint? Each correct selection presents a complete solution. NOTE: Each correct selection is worth one point.
A. automated investigation and remediation
B. transport encryption
C. shadow IT detection
D. attack surface reduction
What can you use to ensure that all the users in a specific group must use multi-factor authentication (MFA) to sign to Azure Active Directory (Azure AD)?
A. Azure Policy
B. a communication compliance policy
C. a Conditional Access policy
D. a user risk policy
What can you protect by using the information protection solution in the Microsoft 365 compliance center?
A. computers from zero-day exploits
B. users from phishing attempts
C. files from malware and viruses
D. sensitive data from being exposed to unauthorized users
HOTSPOT - Select the answer that correctly completes the sentence.
You need to connect to an Azure virtual machine by using Azure Bastion. What should you use?
A. PowerShell remoting
B. the Azure portal
C. the Remote Desktop Connection client
D. an SSH client
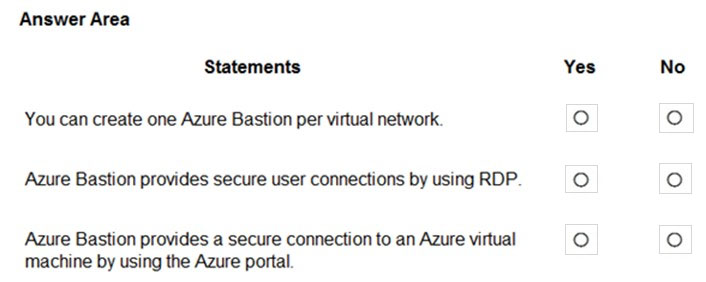
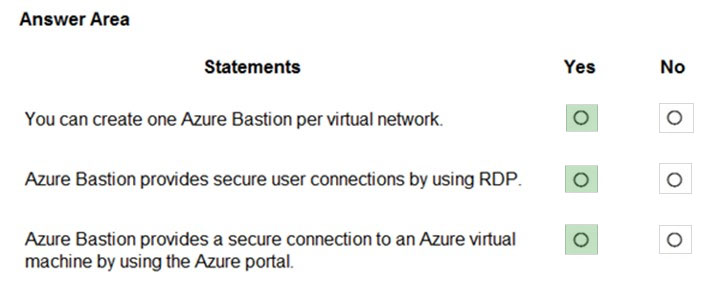
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
Which two Azure resources can a network security group (NSG) be associated with? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. a virtual network subnet
B. a network interface
C. a resource group
D. a virtual network
E. an Azure App Service web app
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Which Microsoft Defender for Cloud metric displays the overall security health of an Azure subscription?
A. secure score
B. resource health
C. completed controls
D. the status of recommendations
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
What are two reasons to deploy multiple virtual networks instead of using just one virtual network? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. to meet governance policies
B. to connect multiple types of resources
C. to separate the resources for budgeting
D. to isolate the resources
HOTSPOT - Select the answer that correctly completes the sentence.
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 E3 subscription. You plan to audit user activity by using the unified audit log and Basic Audit. For how long will the audit records be retained?
A. 15 days
B. 30 days
C. 90 days
D. 180 days
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
What can you use to scan email attachments and forward the attachments to recipients only if the attachments are free from malware?
A. Microsoft Defender for Office 365
B. Microsoft Defender Antivirus
C. Microsoft Defender for Identity
D. Microsoft Defender for Endpoint
HOTSPOT - Select the answer that correctly completes the sentence.
HOTSPOT - Select the answer that correctly completes the sentence.
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Which service includes Microsoft Secure Score for Devices?
A. Microsoft Defender for IoT
B. Microsoft Defender for Endpoint
C. Microsoft Defender for Identity
D. Microsoft Defender for Office 365
DRAG DROP - Match the types of Conditional Access signals to the appropriate definitions. To answer, drag the appropriate Conditional Access signal type from the column on the left to its definition on the right. Each signal type may be used once, more than once, or not at all. NOTE: Each correct match is worth one point.
Which type of identity is created when you register an application with Active Directory (Azure AD)?
A. a user account
B. a user-assigned managed identity
C. a system-assigned managed identity
D. a service principal
HOTSPOT - Select the answer that correctly completes the sentence.
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
DRAG DROP - Match the pillars of Zero Trust to the appropriate requirements. To answer, drag the appropriate pillar from the column on the left to its requirement on the right. Each pillar may be used once, more than once, or not at all. NOTE: Each correct match is worth one point.
Which Microsoft portal provides information about how Microsoft cloud services comply with regulatory standard, such as International Organization for Standardization (ISO)?
A. the Microsoft Endpoint Manager admin center
B. Azure Cost Management + Billing
C. Microsoft Service Trust Portal
D. the Azure Active Directory admin center
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
You need to keep a copy of all files in a Microsoft SharePoint site for one year, even if users delete the files from the site. What should you apply to the site?
A. a retention policy
B. an insider risk policy
C. a data loss prevention (DLP) policy
D. a sensitivity label policy
What are three uses of Microsoft Cloud App Security? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. to discover and control the use of shadow IT
B. to provide secure connections to Azure virtual machines
C. to protect sensitive information hosted anywhere in the cloud
D. to provide pass-through authentication to on-premises applications
E. to prevent data leaks to noncompliant apps and limit access to regulated data
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
Which feature provides the extended detection and response (XDR) capability of Azure Sentinel?
A. integration with the Microsoft 365 compliance center
B. support for threat hunting
C. integration with Microsoft 365 Defender
D. support for Azure Monitor Workbooks
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
What is Azure Key Vault used for?
A. to deploy a cloud-based network security service that protects Azure virtual network resources
B. to protect cloud-based applications from cyber threats and vulnerabilities
C. to safeguard cryptographic keys and other secrets used by cloud apps and services
D. to provide secure and seamless RDP/SSH connectivity to Azure virtual machines via TLS from the Azure portal
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
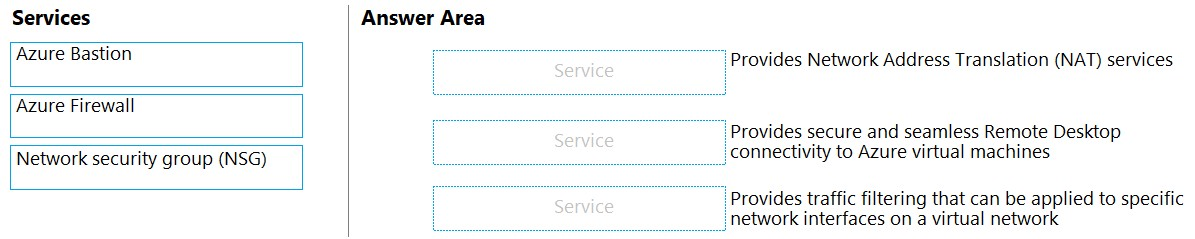
DRAG DROP - Match the Azure networking service to the appropriate description. To answer, drag the appropriate service from the column on the left to its description on the right. Each service may be used once, more than once, or not at all. NOTE: Each correct match is worth one point. Select and Place:
Which score measures an organization's progress in completing actions that help reduce risks associated to data protection and regulatory standards?
A. Microsoft Secure Score
B. Productivity Score
C. Secure score in Azure Security Center
D. Compliance score
In the Microsoft Cloud Adoption Framework for Azure, which two phases are addressed before the Ready phase? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Plan
B. Manage
C. Adopt
D. Govern
E. Define Strategy
Access Full SC-900 Dump Free
Looking for even more practice questions? Click here to access the complete SC-900 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our SC-900 dump free questions — and get one step closer to exam success!