SC-400 Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the SC-400 exam? Start with our SC-400 Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a SC-400 practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free SC-400 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.You need to prevent users in the finance department from sharing files with users in the research department. Which type of policy should you configure?
A. communication compliance
B. information barrier
C. Conditional Access
D. insider risk management
DRAG DROP - You have a Microsoft 365 E5 subscription and use Microsoft Purview. The subscription contains the following users: • User1: Must be able to investigate policy matches, but unable to view the file content related to the match. • User2: Must be able to investigate policy matches and view the file content related to the match. • User3: Must be able to create, update, and delete Microsoft Priva Privacy Risk Management policies. You need to add each user to a role group. The solution must follow the principle of least privilege. To which role group should you add each user? To answer, drag the appropriate role groups to the correct users. Each group may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription. You create and run a content search from the Microsoft Purview compliance portal. You need to download the results of the content search. What should you obtain first?
A. a certificate
B. a password
C. an export key
D. a pin
HOTSPOT - You have a Microsoft 365 E5 subscription that contains the users shown in the following table.You need to delegate the following tasks: • Create and manage data loss prevention (DLP) policies. • Review classified content by using Content explorer. The solution must use the principle of least privilege. Which user should perform each task? To answer, drag the appropriate users to the correct tasks. Each user may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
HOTSPOT - You have a Microsoft 365 E5 subscription that contains the users shown in the following table.You need to delegate the following tasks: • Create and manage data loss prevention (DLP) policies. • Review classified content by using Content explorer. The solution must use the principle of least privilege. Which user should perform each task? To answer, drag the appropriate users to the correct tasks. Each user may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
You receive an email that contains a list of words that will be used for a sensitive information type. You need to create a file that can be used as the source of a keyword dictionary. In which format should you save the list?
A. a JSON file that has an element for each word
B. an ACCDB database file that contains a table named Dictionary
C. an XLSX file that contains one word in each cell of the first row
D. a text file that has one word on each line
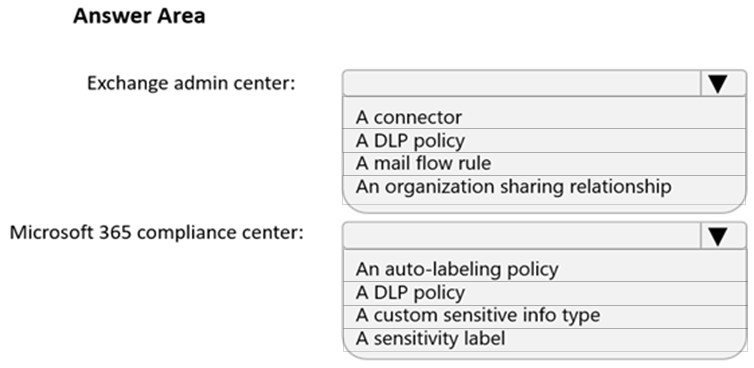
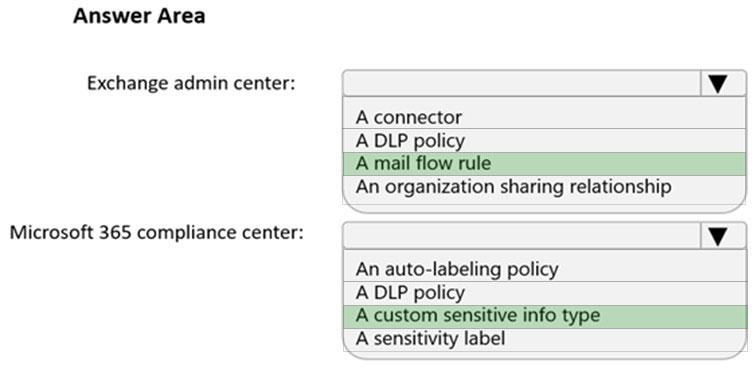
Overview - Fabrikam, Inc. is a consulting company that has a main office in Montreal and six branch offices in New York, Seattle, Miami, Houston, Los Angeles, and Vancouver. Existing Environment - Cloud Environment - Fabrikam has a Microsoft 365 tenant that contains the following resources: An on-premises Active Directory domain named corp.fabrikam.com that syncs to an Azure Active Directory (Azure AD) tenant Microsoft Cloud App Security connectors configured for all supported cloud applications used by the company Some users have company Dropbox accounts. Compliance Configuration - Fabrikam has the following in the Microsoft 365 compliance center: A data loss prevention (DLP) policy is configured. The policy displays a tooltip to users. Users can provide a business justification to override a DLP policy violation. The Azure Information Protection unified labeling scanner is installed and configured. A sensitivity label named Fabrikam Confidential is configured. An existing third-party records management system is managed by the compliance department. Human Resources (HR) Management System The HR department has an Azure SQL database that contains employee information. Each employee has a unique 12-character alphanumeric ID. The database contains confidential employee attributes including payroll information, date of birth, and personal contact details. On-Premises Environment - You have an on-premises file server that runs Windows Server 2019 and stores Microsoft Office documents in a shared folder named Data. All end-user computers are joined to the corp.fabrikam.com domain and run a third-party antimalware application. Business Processes - Sales Contracts - Users in the sales department receive draft sales contracts from customers by email. The sales contracts are written by the customers and are not in a standard format. Employment Applications - Employment applications and resumes are received by HR department managers and stored in either mailboxes, Microsoft SharePoint Online sites, OneDrive for Business folders, or Microsoft Teams channels. The employment application form is downloaded from SharePoint Online and a serial number is assigned to each application. The resumes are written by the applicants and are in any format. Requirements - HR Requirements - You need to create a DLP policy that will notify the HR department of a DLP policy violation if a document that contains confidential employee attributes is shared externally. The DLP policy must use an Exact Data Match (EDM) classification derived from a CSV export of the HR department database. The HR department identifies the following requirements for handling employment applications: Resumes must be identified automatically based on similarities to other resumes received in the past. Employment applications and resumes must be deleted automatically two years after the applications are received. Documents and emails that contain an application serial number must be identified automatically and marked as an employment application. Sales Requirements - A sensitivity label named Sales Contract must be applied automatically to all draft and finalized sales contracts. Compliance Requirements - Fabrikam identifies the following compliance requirements: All DLP policies must be applied to computers that run Windows 10, with the least possible changes to the computers. Users in the compliance department must view the justification provided when a user receives a tooltip notification for a DLP violation. If a document that has the Fabrikam Confidential sensitivity label applied is uploaded to Dropbox, the file must be deleted automatically. The Fabrikam Confidential sensitivity label must be applied to existing Microsoft Word documents in the Data shared folder that have a document footer containing the following string: Company use only. Users must be able to manually select that email messages are sent encrypted. The encryption will use Office 365 Message Encryption (OME) v2. Any email containing an attachment that has the Fabrikam Confidential sensitivity label applied must be encrypted automatically by using OME. Existing policies configured in the third-party records management system must be replaced by using Records management in the Microsoft 365 compliance center. The compliance department plans to export the existing policies, and then produce a CSV file that contains matching labels and policies that are compatible with records management in Microsoft 365. The CSV file must be used to configure records management in Microsoft 365. Executive Requirements - You must be able to restore all email received by Fabrikam executives for up to three years after an email is received, even if the email was deleted permanently. HOTSPOT - You need to implement a solution to encrypt email. The solution must meet the compliance requirements. What should you create in the Exchange admin center and the Microsoft 365 compliance center? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
Your company has a Microsoft 365 tenant that uses a domain named contoso.com. The company uses Microsoft Office 365 Message Encryption (OME) to encrypt email sent to users in fabrikam.com. A user named User1 erroneously sends an email to user2@fabrikam.com . You need to prevent user2@fabrikam.com from accessing the email. What should you do?
A. Run the Get-MessageTrace cmdlet.
B. Run the Set-OMEMessageRevocation cmdlet.
C. Instruct User1 to delete the email from her Sent Items folder from Microsoft Outlook.
D. Run the New-ComplianceSearchAction cmdlet.
E. Instruct User1 to select Remove external access from Microsoft Outlook on the web.
You have a Microsoft 365 E5 tenant that has devices onboarded to Microsoft Defender for Endpoint as shown in the following table.You plan to start using Microsoft 365 Endpoint data loss protection (Endpoint DLP). Which devices support Endpoint DLP?
A. Device1 only
B. Device1 and Device2 only
C. Device1 and Device4 only
D. Device1, Device2, and Device4 only
E. Device1, Device2, Device3, and Device4
You have a Microsoft 365 subscription linked to a Microsoft Entra tenant that contains a user named User1. You need to grant User1 permission to search Microsoft 365 audit logs. The solution must use the principle of least privilege. Which role should you assign to User1?
A. the Reviewer role in the Microsoft Purview compliance portal
B. the View-Only Audit Logs role in the Exchange admin center
C. the Compliance Management role in the Exchange admin center
D. the Security Reader role in the Microsoft Entra admin center
HOTSPOT - You have a Microsoft 365 E5 subscription. You need to deploy a compliance solution that meets the following requirements: • Prevents users from performing data transfers that breach local regulations • Minimizes effort to respond to requests for a user's personal data What should you use in the Microsoft Purview compliance portal? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
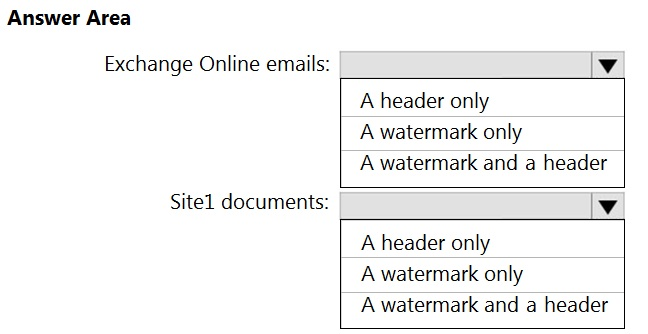
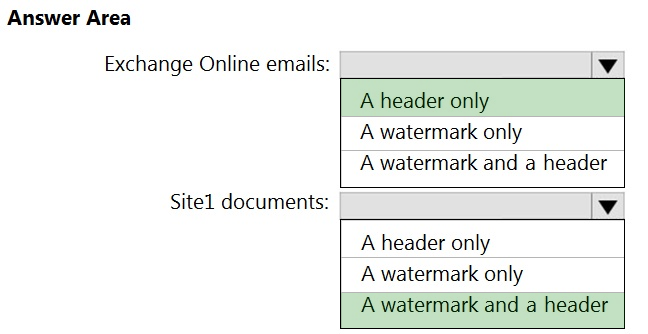
HOTSPOT - You have a Microsoft SharePoint Online site named Site1 and a sensitivity label named Sensitivity1. Sensitivity1 adds a watermark and a header to content. You create a policy to automatically apply Sensitivity1 to emails in Microsoft Exchange Online and Site1. How will Sensitivity1 mark matching emails and Site1 documents? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You have a Microsoft 365 subscription that contains two groups named Group1 and Group2. You have the compliance assessments shown in the following table.You have the improvement actions shown in the following table.
You perform the following actions: • Create and publish a retention label. • Implement security awareness training for all users. • For Action4, change Implementation status to Implemented. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 tenant and 500 computers that run Windows 10. The computers are onboarded to the Microsoft 365 compliance center. You discover that a third-party application named Tailspin_scanner.exe accessed protected sensitive information on multiple computers. Tailspin_scanner.exe is installed locally on the computers. You need to block Tailspin_scanner.exe from accessing sensitive documents without preventing the application from accessing other documents. Solution: From the Cloud App Security portal, you mark the application as Unsanctioned. Does this meet the goal?
A. Yes
B. No
HOTSPOT - You have a Microsoft SharePoint Online site named Site1 that contains the users shown in following table.You create the retention labels shown in the following table.
You publish the retention labels to Site1. Site1 contains the files shown in following table.
Which files can User1 delete on May 15, 2023, and which files can User2 delete on August 15, 2024? To answer, drag the appropriate files to the correct users. Each file may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription that contains 100 users and a Microsoft 365 group named Group1. All users have Windows 10 devices and use Microsoft SharePoint Online and Exchange Online. A sensitivity label named Label1 is published as the default label for Group1. You add two sublabels named Sublabel1 and Sublabel2 to Label1. You need to ensure that the settings in Sublabel1 are applied by default to Group1. What should you do?
A. Change the order of Sublabel1.
B. Modify the policy of Label1.
C. Delete the policy of Label1 and publish Sublabel1.
D. Duplicate all the settings from Sublabel1 to Label1.
You have a Microsoft 365 E5 subscription. You need to review the compliance of the subscription with the General Data Protection Regulation (GDPR) by using Compliance Manager. The solution must minimize administrative effort. What should you create first?
A. an assessment
B. an alert policy to monitor for score changes
C. a template
D. review assessments
You have a Microsoft 365 E5 subscription. Users access their mailbox by using the following apps: • Outlook Win32 • Outlook on the web • Outlook for iOS and Android You create a data loss prevention (DLP) policy named DLP1 that has the following settings: • Location: Exchange email • Status: On • User notifications: On • Notify users in Office 365 service with a policy tip: Enabled Which apps display a policy tip when content is matched by using DLP1?
A. Outlook Win32 only
B. Outlook on the web only
C. Outlook Win32 and Outlook on the web only
D. Outlook Win32 and Outlook for iOS and Android only
E. Outlook Win32, Outlook on the web, and Outlook for iOS and Android
You have a Microsoft 365 subscription. The Global Administrator role is assigned to your user account. You have a user named Admin1. You create an eDiscovery case named Case1. You need to ensure that Admin1 can view the results of Case1. What should you do first?
A. From the Microsoft Entra admin center, assign a role group to Admin1.
B. From the Microsoft Purview compliance portal, assign a role group to Admin1.
C. From the Microsoft 365 admin center, assign a role to Admin1.
HOTSPOT - You have a Microsoft 365 E5 subscription that contains two users named User1 and User2. You create the audit retention policies shown in the following table.The users perform the following actions: • User1 renames a Microsoft SharePoint Online site. • User2 sends an email message. How long will the audit log records be retained for each action? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You are configuring a file policy in Microsoft Cloud App Security. You need to configure the policy to apply to all files. Alerts must be sent to every file owner who is affected by the policy. The policy must scan for credit card numbers, and alerts must be sent to the Microsoft Teams site of the affected department. Solution: You use the Data Classification service inspection method and send alerts as email. Does this meet the goal?
A. Yes
B. No
You need to automatically apply a sensitivity label to documents that contain information about your company's network including computer names, IP addresses, and configuration information. Which two objects should you use? Each correct answer presents part of the solution. (Choose two.) NOTE: Each correct selection is worth one point.
A. an Information protection auto-labeling policy
B. a custom trainable classifier
C. a sensitive info type that uses a regular expression
D. a data loss prevention (DLP) policy
E. a sensitive info type that uses keywords
F. a sensitivity label that has auto-labeling
You have a Microsoft SharePoint Online site named Site1 that contains a document library. The library contains more than 1,000 documents. Some of the documents are job applicant resumes. All the documents are in the English language. You plan to apply a sensitivity label automatically to any document identified as a resume. Only documents that contain work experience, education, and accomplishments must be labeled automatically. You need to identify and categorize the resumes. The solution must minimize administrative effort. What should you include in the solution?
A. a trainable classifier
B. an exact data match (EDM) classifier
C. a function
D. a keyword dictionary
HOTSPOT - You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1 and the users shown in the following table.Site1 includes a file named File1.docx. You create two retention labels named Retention1 and Retention2. You publish Retention1 to the following locations: • Exchange email • Included: User1 • Microsoft 365 Groups • Included: Group2 You publish Retention2 to the following locations: • Exchange email • Included: All recipients • SharePoint sites • Included: Site1 For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
HOTSPOT - You have a Microsoft 365 sensitivity label that is published to all the users in your Microsoft Entra tenant as shown in the following exhibit.For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription. You create a new trainable classifier. You need to train the classifier. Which source can you use to train the classifier?
A. a Microsoft SharePoint Online site
B. an on-premises Microsoft SharePoint Server site
C. an NFS file share
D. an Azure Files share
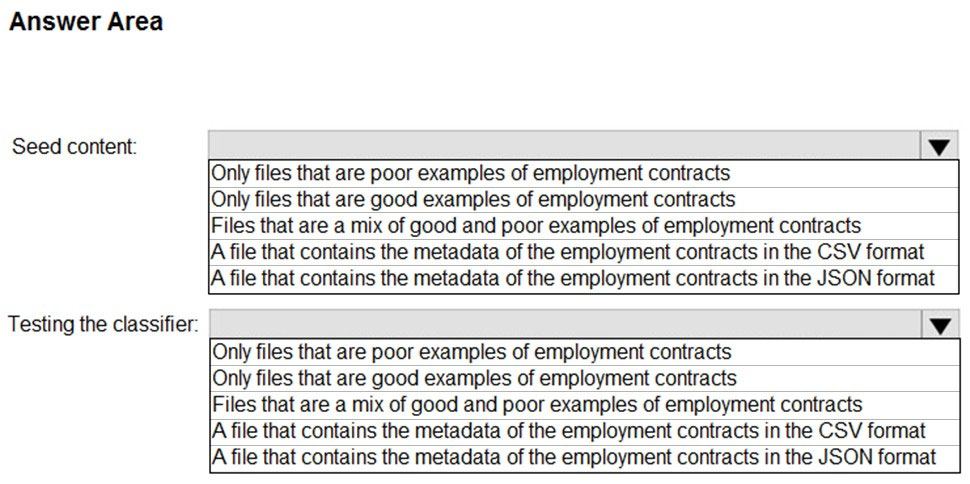
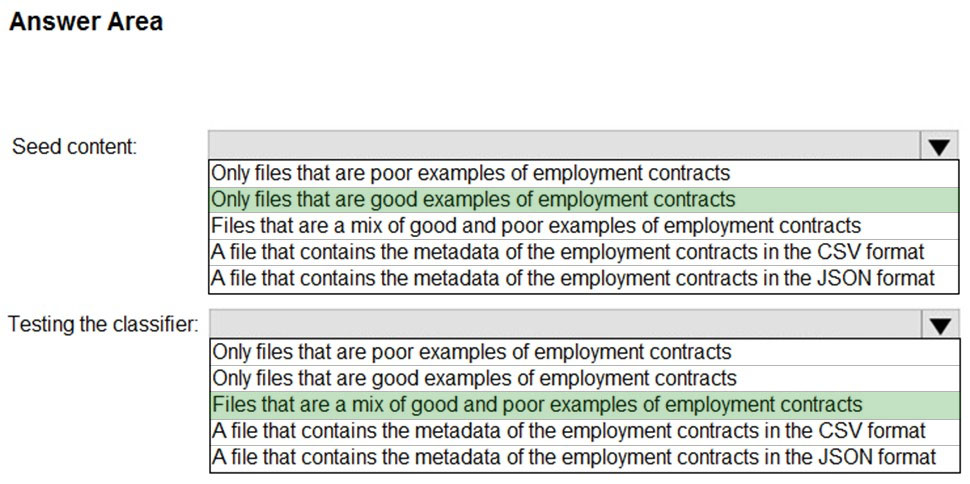
HOTSPOT - You plan to implement a sensitive information type based on a trainable classifier. The sensitive information type will identify employment contracts. You need to copy the required files to Microsoft SharePoint Online folders to train the classifier. What should you use to seed content and test the classifier? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 E5 tenant that has data loss prevention (DLP) policies. You need to create a report that includes the following: • Documents that have a matched DLP policy. • Documents that have had a sensitivity label changed. • Documents that have had a sensitivity label changed. What should you use?
A. a content search
B. an eDiscovery case
C. communication compliance reports
D. Activity explorer
You need to recommend a solution that meets the compliance requirements for Dropbox. What should you recommend?
A. Create a file policy in Cloud App Security that uses the built-in DLP inspection method.
B. Edit an existing retention label that enforces the item deletion settings.
C. Create a retention label that enforces the item deletion settings.
D. Create a DLP policy that applies to devices.
HOTSPOT - You have a Microsoft SharePoint Online site named Site1 that contains the files shown in the following table.You have a data loss prevention (DLP) policy named DLP1 that has the advanced DLP rules shown in the following table.
You apply DLP1 to Site1. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You are evaluating the technical requirements for the DLP reports. Which user can currently view the DLP reports?
A. Admin4
B. Admin1
C. Admin5
D. Admin2
E. Admin3
You are configuring a retention label named Label1 as shown in the following exhibit.You need to ensure that documents that have Label1 applied are deleted three years after the end of your company's fiscal year. What should you do?
A. Create a new event type.
B. Select Only delete items when they reach a certain age.
C. Modify the Retention period setting.
D. Set At the ends of the retention period to Trigger a disposition review.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 subscription. You have a user named User1. Several users have full access to the mailbox of User1. Some email messages sent to User1 appear to have been read and deleted before the user viewed them. When you search the audit log in the Microsoft Purview compliance portal to identify who signed in to the mailbox of User1, the results are blank. You need to ensure that you can view future sign-ins to the mailbox of User1. Solution: You run the Set-MailboxFolderPermission -Identity "User1" -User User1@contoso.com -AccessRights Owner command. Does that meet the goal?
A. Yes
B. No
You plan to implement sensitivity labels for Microsoft Teams. You need to ensure that you can view and apply sensitivity labels to new Microsoft Teams sites. What should you do first?
A. Run the Set-SPOSite cmdlet.
B. Create a new sensitivity label scoped to Groups & sites.
C. Run the Execute-AzureAdLabelSync cmdlet.
D. Configure the EnableMIPLabels Azure Active Directory (Azure AD) setting.
Overview - Fabrikam, Inc. is a consulting company that has a main office in Montreal and six branch offices in New York, Seattle, Miami, Houston, Los Angeles, and Vancouver. Existing Environment - Cloud Environment - Fabrikam has a Microsoft 365 tenant that contains the following resources: An on-premises Active Directory domain named corp.fabrikam.com that syncs to an Azure Active Directory (Azure AD) tenant. Microsoft Cloud App Security connectors configured for all supported cloud applications used by the company. Some users have company Dropbox accounts. Compliance Configuration - Fabrikam has the following in the Microsoft 365 compliance center: A data loss prevention (DLP) policy is configured. The policy displays a tooltip to users. Users can provide a business justification to override a DLP policy violation. The Azure Information Protection unified labeling scanner is installed and configured. A sensitivity label named Fabrikam Confidential is configured. An existing third-party records management system is managed by the compliance department. Human Resources (HR) Management System The HR department has an Azure SQL database that contains employee information. Each employee has a unique 12-character alphanumeric ID. The database contains confidential employee attributes including payroll information, date of birth, and personal contact details. On-Premises Environment - You have an on-premises file server that runs Windows Server 2019 and stores Microsoft Office documents in a shared folder named Data. All end-user computers are joined to the corp.fabrikam.com domain and run a third-party antimalware application. Business Processes - Sales Contracts - Users in the sales department receive draft sales contracts from customers by email. The sales contracts are written by the customers and are not in a standard format. Employment Applications - Employment applications and resumes are received by HR department managers and stored in either mailboxes, Microsoft SharePoint Online sites, OneDrive for Business folders, or Microsoft Teams channels. The employment application form is downloaded from SharePoint Online and a serial number is assigned to each application. The resumes are written by the applicants and are in any format. Requirements - HR Requirements - You need to create a DLP policy that will notify the HR department of a DLP policy violation if a document that contains confidential employee attributes is shared externally. The DLP policy must use an Exact Data Match (EDM) classification derived from a CSV export of the HR department database. The HR department identifies the following requirements for handling employment applications: Resumes must be identified automatically based on similarities to other resumes received in the past. Employment applications and resumes must be deleted automatically two years after the applications are received. Documents and emails that contain an application serial number must be identified automatically and marked as an employment application. Sales Requirements - A sensitivity label named Sales Contract must be applied automatically to all draft and finalized sales contracts. Compliance Requirements - Fabrikam identifies the following compliance requirements: All DLP policies must be applied to computers that run Windows 10, with the least possible changes to the computers. Users in the compliance department must view the justification provided when a user receives a tooltip notification for a DLP violation. If a document that has the Fabrikam Confidential sensitivity label applied is uploaded to Dropbox, the file must be deleted automatically. The Fabrikam Confidential sensitivity label must be applied to existing Microsoft Word documents in the Data shared folder that have a document footer containing the following string: Company use only. Users must be able to manually select that email messages are sent encrypted. The encryption will use Office 365 Message Encryption (OME) v2. Any email containing an attachment that has the Fabrikam Confidential sensitivity label applied must be encrypted automatically by using OME. Existing policies configured in the third-party records management system must be replaced by using Records management in the Microsoft 365 compliance center. The compliance department plans to export the existing policies, and then produce a CSV file that contains matching labels and policies that are compatible with records management in Microsoft 365. The CSV file must be used to configure records management in Microsoft 365. Executive Requirements - You must be able to restore all email received by Fabrikam executives for up to three years after an email is received, even if the email was deleted permanently. You need to recommend a solution that meets the executive requirements. What should you recommend?
A. From the Microsoft 365 compliance center, create a DLP policy.
B. From the Exchange admin center, enable archive mailboxes.
C. From the Microsoft 365 compliance center, create a retention label.
D. From the Microsoft 365 compliance center, create a retention policy.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You recently discovered that the developers at your company emailed Azure Storage keys in plain text to third parties. You need to ensure that when Azure Storage keys are emailed, the emails are encrypted. Solution: You create a data loss prevention (DLP) policy that has all locations selected. Does this meet the goal?
A. Yes
B. No
You have a Microsoft 365 tenant that uses 100 data loss prevention (DLP) policies. A Microsoft Exchange administrator frequently investigates emails that were blocked due to DLP policy violations. You need recommend which DLP report the Exchange administrator can use to identify how many messages were blocked based on each DLP policy. Which report should you recommend?
A. Third-party DLP policy matches
B. DLP policy matches
C. DLP incidents
D. False positive and override
DRAG DROP - You have a Microsoft 365 E5 subscription. You need to prevent the sharing of sensitive information in Microsoft Teams. Which entities can you protect by applying a data loss prevention (DLP) policy to each resource? To answer, drag the appropriate activities to the correct entity. Each activity may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains a device named Device1. You need to enable Endpoint data loss prevention (Endpoint DLP) for Device1. What should you do first in the Microsoft Purview compliance portal?
A. Turn on device onboarding.
B. Add a Microsoft Purview Information Protection scanner cluster.
C. Onboard Device1 to Microsoft Purview.
D. Create a Microsoft Purview Information Barriers (IBs) segment.
E. Enable Microsoft Priva Privacy Risk Management.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 tenant and 500 computers that run Windows 10. The computers are onboarded to the Microsoft 365 compliance center. You discover that a third-party application named Tailspin_scanner.exe accessed protected sensitive information on multiple computers. Tailspin_scanner.exe is installed locally on the computers. You need to block Tailspin_scanner.exe from accessing sensitive documents without preventing the application from accessing other documents. Solution: From the Microsoft Defender for Cloud Apps portal, you create an app discovery policy. Does this meet the goal?
A. Yes
B. No
You have a Microsoft 365 tenant that contains the users shown in the following table.You configure a retention label to trigger a disposition review at the end of the retention period. Which users can access the Disposition tab in the Microsoft 365 compliance center to review the content?
A. User1 only
B. User2 only
C. User3 only
D. User1 and User3
E. User3 and User4
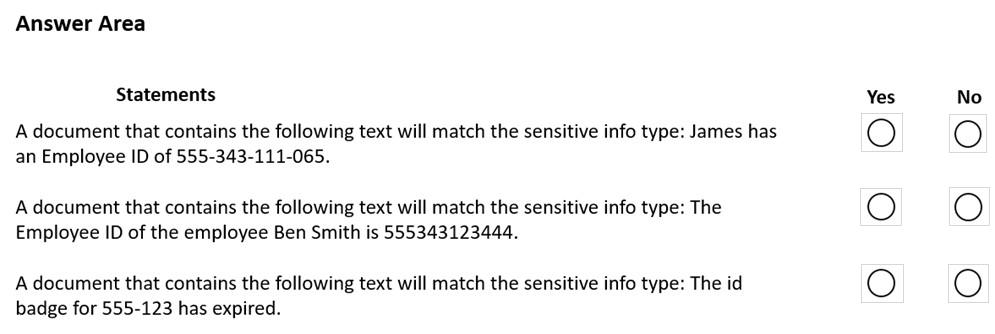
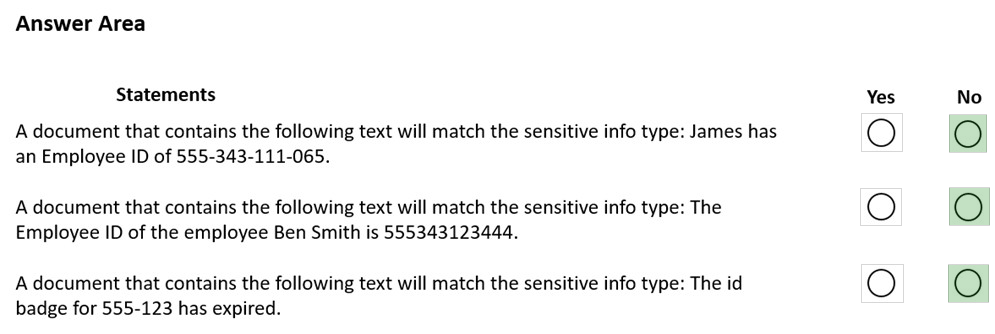
HOTSPOT - You have a Microsoft 365 tenant that uses data loss prevention (DLP) to protect sensitive information. You create a new custom sensitive info type that has the matching element shown in the following exhibit.The supporting elements are configured as shown in the following exhibit.
The confidence level and character proximity are configured as shown in the following exhibit.
For each of the following statements, select Yes if statement is true. Otherwise, select No NOTE: Each correct selection is worth one point. Hot Area:
Overview - Contoso, Ltd. is a consulting company that has a main office in Montreal and three branch offices in Seattle, Boston, and Johannesburg. Existing Environment - Microsoft 365 Environment - Contoso has a Microsoft 365 E5 tenant. The tenant contains the administrative user accounts shown in the following table.Users store data in the following locations: SharePoint sites OneDrive accounts Exchange email Exchange public folders Teams chats Teams channel messages When users in the research department create documents, they must add a 10-digit project code to each document. Project codes that start with the digits 999 are confidential. SharePoint Online Environment - Contoso has four Microsoft SharePoint Online sites named Site1, Site2, Site3, and Site4. Site2 contains the files shown in the following table.
Two users named User1 and User2 are assigned roles for Site2 as shown in the following table.
Site3 stores documents related to the company's projects. The documents are organized in a folder hierarchy based on the project. Site4 has the following two retention policies applied: Name: Site4RetentionPolicy1 - Locations to apply the policy: Site4 - Delete items older than: 2 years - Delete content based on: When items were created Name: Site4RetentionPolicy2 - Locations to apply the policy: Site4 - Retain items for a specific period: 4 years - Start the retention period based on: When items were created - At the end of the retention period: Do nothing Problem Statements - Management at Contoso is concerned about data leaks. On several occasions, confidential research department documents were leaked. Requirements - Planned Changes - Contoso plans to create the following data loss prevention (DLP) policy: Name: DLPpolicy1 Locations to apply the policy: Site2 Conditions: - Content contains any of these sensitive info types: SWIFT Code - Instance count: 2 to any Actions: Restrict access to the content Technical Requirements - Contoso must meet the following technical requirements: All administrative users must be able to review DLP reports. Whenever possible, the principle of least privilege must be used. For all users, all Microsoft 365 data must be retained for at least one year. Confidential documents must be detected and protected by using Microsoft 365. Site1 documents that include credit card numbers must be labeled automatically. All administrative users must be able to create Microsoft 365 sensitivity labels. After a project is complete, the documents in Site3 that relate to the project must be retained for 10 years. You need to meet the retention requirement for the users' Microsoft 365 data. What is the minimum number of retention policies that you should use?
A. 1
B. 2
C. 3
D. 4
E. 6
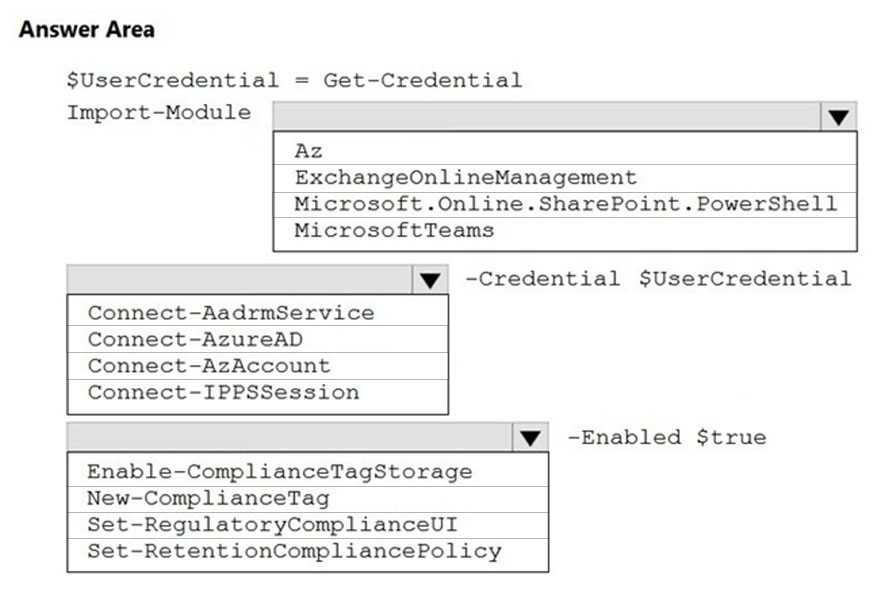
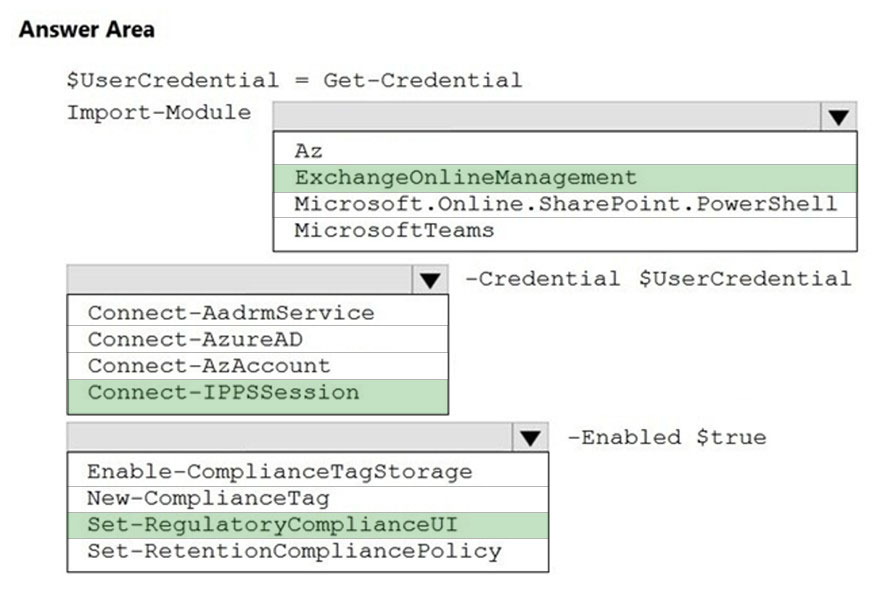
HOTSPOT - While creating a retention label, you discover that the following options are missing: ✑ Mark items as a record ✑ Mark items as a regulatory record You need to ensure that the options are available when you create retention labels in the Microsoft 365 compliance center. How should you complete the PowerShell script? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
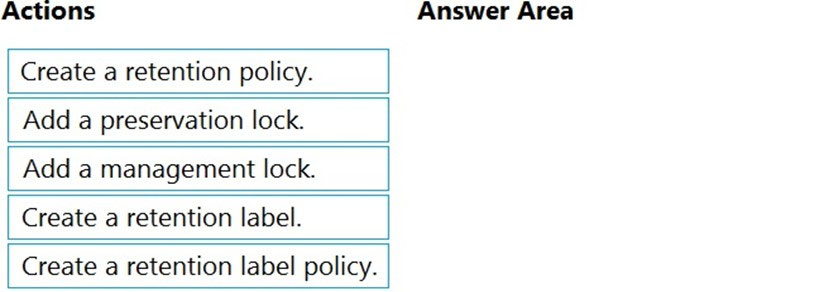
DRAG DROP - You have a Microsoft 365 tenant. A new regulatory requirement states that all documents containing a patent ID be labeled, retained for 10 years, and then deleted. The policy used to apply the retention settings must never be disabled or deleted by anyone. You need to implement the regulatory requirement. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. (Choose three.) Select and Place:
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1. You need to implement Microsoft Purview data lifecycle management. What should you create first?
A. a sensitivity label policy
B. a retention label
C. a data loss prevention (DLP) policy
D. an auto-labeling policy
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1. Site1 contains a file named File1. You have a retention policy named Retention1 that has the following settings: • Retention items for a specific period o Retention period: 5 years o At the end of the retention period: Delete items automatically Retention1 is applied to Site1. You need to ensure that File1 is deleted automatically after seven years. The solution must NOT affect the retention of other files on Site1. What should you do first?
A. Move File1 to a new folder and configure the access control list (ACL) entries for File1.
B. Create a new retention policy.
C. Create and publish a new retention label.
D. Move File1 to a new folder and list the excluded locations for Retention1.
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1. You need to implement Microsoft Purview data lifecycle management. What should you create first?
A. a sensitivity label policy
B. a retention label
C. a data loss prevention (DLP) policy
D. an auto-labeling policy
You have a Microsoft 365 subscription. You need to be notified by email whenever an administrator starts an eDiscovery search. What should you do from the Microsoft Purview compliance portal?
A. From Records management create event type.
B. From eDiscovery, create an eDiscovery case.
C. From Content search, create a new search.
D. From Policies, create an alert policy.
You have a Microsoft 365 subscription. You create a new trainable classifier. You need to train the classifier. Which source can you use to train the classifier?
A. a Microsoft SharePoint Online site
B. an on-premises Microsoft SharePoint Server site
C. an NFS file share
D. an Azure Files share
Free Access Full SC-400 Practice Test Free Questions
If you’re looking for more SC-400 practice test free questions, click here to access the full SC-400 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your SC-400 certification journey!