SC-400 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the SC-400 certification? Take your preparation to the next level with our SC-400 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a SC-400 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic SC-400 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
HOTSPOT - You have a Microsoft 365 subscription. You create a retention label named Label1 as shown in the following exhibit.You publish Label1 to SharePoint sites. Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
HOTSPOT - You plan to provide a user named User1 with the ability to view data loss prevention (DLP) reports. You need to identify the following: • Which role you should assign to User1 • Which tool you should use to assign the role What should you identify? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription. You plan to implement information barriers (IBs). You need to create an IB segment named Segment1. What should you use to define Segment1?
A. a user group filter
B. a distribution list group
C. a Microsoft 365 group
D. an administrative unit
You have a Microsoft 365 tenant that uses records management. You use a retention label to mark legal files stored in a Microsoft SharePoint Online document library as regulatory records. What can you do to the legal files?
A. Remove the retention label of the files.
B. Edit the content of the files.
C. Move the files to a different folder within the document library.
D. Change the retention label of the files.
HOTSPOT - You have a Microsoft 365 E5 subscription that contains the devices shown in the following table.You need to onboard the devices to Microsoft Purview. The solution must ensure that you can apply Endpoint data loss prevention (Endpoint DLP) policies to the devices. What can you use to onboard each device? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT - You have a Microsoft 365 subscription. You are creating a retention policy named Retention1 as shown in the exhibit. (Click the Exhibit tab.)You apply Retention1 to SharePoint sites and OneDrive accounts. Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains the adaptive scopes shown in the following table.You create the retention policies shown in the following table.
Which retention policies support a preservation lock?
A. RPolicy2 only
B. RPolicy3 only
C. RPolicy1 and RPolicy2 only
D. RPolicy1 and RPolicy3 only
E. RPolicy1, RPolicy2, and RPolicy3
HOTSPOT - You have a Microsoft 365 E5 subscription that contains two users named User1 and User2 and a group named Group1. User1 is a member of Group1. The subscription contains the sensitivity labels shown in the following table.You have a sensitivity label policy named Policy1 that is published to User1 and User2. The policy includes the following labels: • General • Confidential • Confidential/Low • Confidential/High • Confidential/Medium For Policy1, the default label for documents is Confidential/Low. You have a sensitivity label policy named Policy2 that is published to Group1. The policy includes the following labels: • Secret • General • Secret/Low • Secret/High • Secret/Medium For Policy2, the default label for documents is Secret/Low. You have a sensitivity label policy named Policy3 that is published to User1 and User2. The policy includes the following labels: • Secret • General • Secret/Low • Secret/High • Secret/Medium For Policy3, the default label for documents is Secret/Medium. The order of the policies is shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 tenant. You have a Microsoft SharePoint Online site that contains employment contracts in a folder named EmploymentContracts. All the files in EmploymentContracts are marked as records. You need to recommend a process to ensure that when a record is updated, the previous version of the record is kept as a version of the updated record. What should you recommend?
A. Upload an updated file plan that contains the record definition.
B. Unlock the record, modify the record, and then lock the record.
C. Create a copy of the record and enter a version in the file metadata.
D. Create a new label policy associated to an event that will apply to the record.
You have a Microsoft 365 tenant that has data loss prevention (DLP) policies. You need to review DLP policy matches for the tenant. What should you use?
A. Content explorer
B. Activity explorer
C. Compliance Manager
D. records management events
You have a Microsoft 365 E5 subscription. You plan to implement retention policies for Microsoft Teams. Which item types can be retained?
A. voice memos from the Teams mobile client
B. embedded images
C. code snippets
You have a Microsoft 365 E5 subscription. You plan to implement retention policies for Microsoft Teams. Which item types can be retained?
A. voice memos from the Teams mobile client
B. embedded images
C. code snippets
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1. Site1 contains a file named File1. You have a retention policy named Retention1 that has the following settings: • Retention items for a specific period o Retention period: 5 years o At the end of the retention period: Delete items automatically Retention1 is applied to Site1. You need to ensure that File1 is deleted automatically after seven years. The solution must NOT affect the retention of other files on Site1. What should you do first?
A. Move File1 to a new folder and configure the access control list (ACL) entries for File1.
B. Create a new retention policy.
C. Create and publish a new retention label.
D. Move File1 to a new folder and list the excluded locations for Retention1.
HOTSPOT - You have a Microsoft 365 E5 subscription. You are evaluating Data Protection Baseline compliance by using Compliance Manager. You need to identify improvement actions that meet the following requirements: • Provide data loss prevention (DLP) policy recommendations. • Provide Data Protection Baseline recommendations. Which filter should you use for each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription. You have a team named Team1 in Microsoft Teams. You plan to place all the content in Team1 on hold. You need to identify which mailbox and which Microsoft SharePoint site collection are associated to Team1. Which cmdlet should you use?
A. Get-UnifiedGroup
B. Get-TeamChannel
C. Get-MailUser
D. Get-Team
You have a Microsoft 365 subscription. The Global Administrator role is assigned to your user account. You have a user named Admin1. You create an eDiscovery case named Case1. You need to ensure that Admin1 can view the results of Case1. What should you do first?
A. From the Microsoft Entra admin center, assign a role group to Admin1.
B. From the Microsoft Purview compliance portal, assign a role group to Admin1.
C. From the Microsoft 365 admin center, assign a role to Admin1.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 tenant and 500 computers that run Windows 10. The computers are onboarded to the Microsoft 365 compliance center. You discover that a third-party application named Tailspin_scanner.exe accessed protected sensitive information on multiple computers. Tailspin_scanner.exe is installed locally on the computers. You need to block Tailspin_scanner.exe from accessing sensitive documents without preventing the application from accessing other documents. Solution: From the Cloud App Security portal, you create an app discovery policy. Does this meet the goal?
A. Yes
B. No
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You recently discovered that the developers at your company emailed Azure Storage keys in plain text to third parties. You need to ensure that when Azure Storage keys are emailed, the emails are encrypted. Solution: You configure a mail flow rule that matches the text patterns. Does this meet the goal?
A. Yes
B. No
HOTSPOT - You have a Microsoft 365 subscription that contains a sensitivity label named Contoso Confidential. You publish Contoso Confidential to all users. Contoso Confidential is configured as shown in the Configuration exhibit. (Click the Configuration tab.)The Encryption settings of Contoso Confidential are configured as shown in the Encryption exhibit. (Click the Encryption tab.)
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 subscription. You have a user named User1. Several users have full access to the mailbox of User1. Some email messages sent to User1 appear to have been read and deleted before the user viewed them. When you search the audit log in the Microsoft Purview compliance portal to identify who signed in to the mailbox of User1, the results are blank. You need to ensure that you can view future sign-ins to the mailbox of User1. Solution: You run the Set-AuditConfig -Workload Exchange command. Does that meet the goal?
A. Yes
B. No
SIMULATION - Use the following login credentials as needed: To enter your username, place your cursor in the Sign in box and click on the username below. To enter your password, place your cursor in the Enter password box and click on the password below. Microsoft 365 Username: admin@123456789.onmicrosoft.com Microsoft 365 Password: ********** If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab. The following information is for technical support purposes only: Lab Instance: 12345678 - You plan to automatically apply a watermark to the documents of a project named Falcon. You need to create a label that will add a watermark of “Project Falcon” in red, size-12 font diagonally across the documents. To complete this task, sign in to the appropriate admin center.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 E5 subscription. You need to identify resumes that are stored in the subscription by using a built-in trainable classifier. Solution: You create a data loss prevention (DLP) policy. Does this meet the goal?
A. Yes
B. No
HOTSPOT - You plan to provide a user named User1 with the ability to view data loss prevention (DLP) reports. You need to identify the following: • Which role you should assign to User1 • Which tool you should use to assign the role What should you identify? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription. You need to identify personal data stored in the subscription and control the transfer of personal data between users and groups. Which type of license should you acquire?
A. Microsoft Purview Audit (Premium)
B. Priva Privacy Risk Management
C. Microsoft 365 E5 Compliance
D. Priva Subject Rights Requests
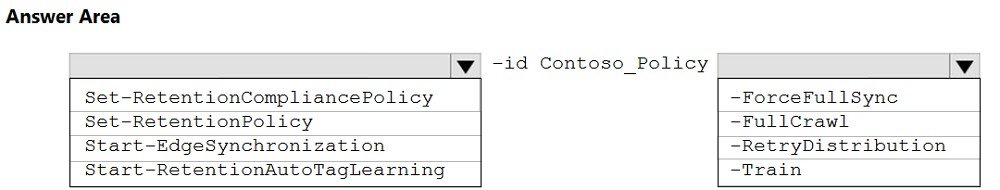
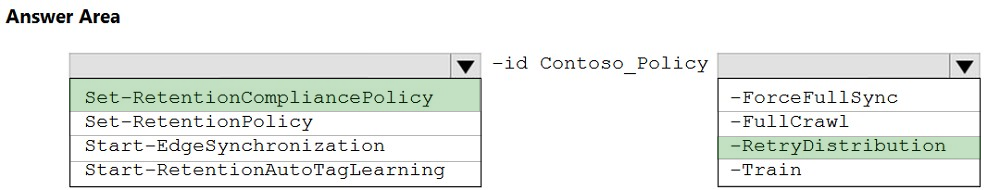
HOTSPOT - You create a retention label policy named Contoso_Policy that contains the following labels: ✑ 10 years then delete ✑ 5 years then delete ✑ Do not retain Contoso_Policy is applied to content in Microsoft SharePoint Online sites. After a couple of days, you discover the following messages on the Properties page of the label policy: ✑ Status: Off (Error) ✑ It's taking longer than expected to deploy the policy You need to reinitiate the policy. How should you complete the command? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
A user reports that she can no longer access a Microsoft Excel file named Northwind Customer Data.xlsx. From the Cloud App Security portal, you discover the alert shown in the exhibit.You restore the file from quarantine. You need to prevent files that match the policy from being quarantined. Files that match the policy must generate an alert. What should you do?
A. Modify the policy template.
B. Assign the Global reader role to the file owners.
C. Exclude file matching by using a regular expression.
D. Update the governance action.
HOTSPOT - You have a Microsoft 365 E5 subscription that contains a user named User1 and the groups shown in the following table.You have the Compliance Manager improvement action shown in the following exhibit.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
HOTSPOT - You have a Microsoft 365 E5 tenant that contains a trainable classifier named Classifier1. You need to increase the accuracy of Classifier1. The solution must use the principle of least privilege. Which feature should you use and to which role group should you be added? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 tenant. You discover that email does NOT use Microsoft Office 365 Message Encryption (OME). You need to ensure that OME can be applied to email. What should you do first?
A. Enable Microsoft Defender for Office 365.
B. Activate Azure Information Protection.
C. Activate Azure Rights Management (Azure RMS).
D. Create an Azure key vault.
You have a Microsoft 365 E5 subscription that uses Yammer. You need to create a Microsoft Purview communication compliance policy that will detect inappropriate images in Yammer conversations. What should you do first?
A. Configure Hybrid Mode for Yammer.
B. Configure Native Mode for Yammer.
C. Configure the Yammer network admin settings.
D. Assign each user a Yammer license.
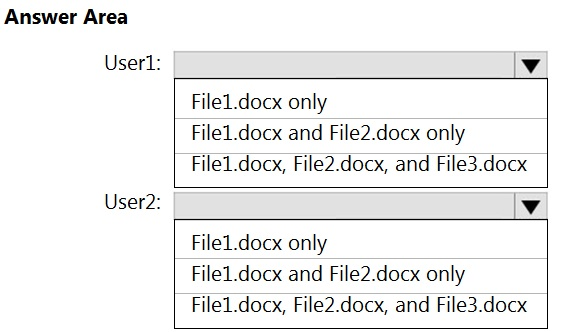
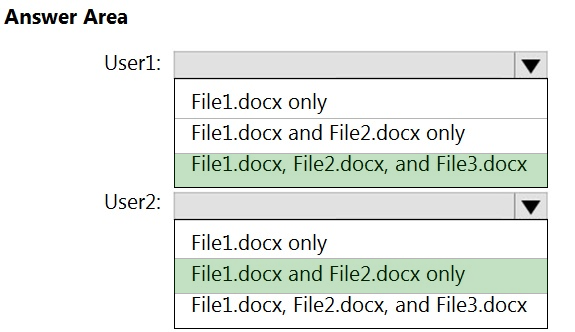
HOTSPOT - You have a Microsoft SharePoint Online site that contains the following files.Users are assigned roles for the site as shown in the following table.
Which files can User1 and User2 view? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You have a Microsoft 365 E5 subscription. You are implementing insider risk management. You need to create an insider risk management notice template and format the message body of the notice template. How should you configure the template? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains a user named User1. You need to ensure that all email messages that contain attachments are encrypted automatically by using Microsoft Purview Message Encryption. What should you create?
A. a sensitivity label
B. an information barrier segment
C. a data loss prevention (DLP) policy
D. a mail flow rule
HOTSPOT - You have a Microsoft 365 E5 subscription. You have the alerts shown in the following exhibit.Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 tenant that has devices onboarded to Microsoft Defender for Endpoint as shown in the following table.You plan to start using Microsoft 365 Endpoint data loss protection (Endpoint DLP). Which devices support Endpoint DLP?
A. Device5 only
B. Device2 only
C. Device1, Device2, Device3, Device4, and Device5
D. Device3 and Device4 only
E. Device1 and Device2 only
You have a Microsoft 365 subscription linked to a Microsoft Entra tenant that contains a user named User1. You need to grant User1 permission to search Microsoft 365 audit logs. The solution must use the principle of least privilege. Which role should you assign to User1?
A. the Reviewer role in the Microsoft Purview compliance portal
B. the View-Only Audit Logs role in the Exchange admin center
C. the Compliance Management role in the Exchange admin center
D. the Security Reader role in the Microsoft Entra admin center
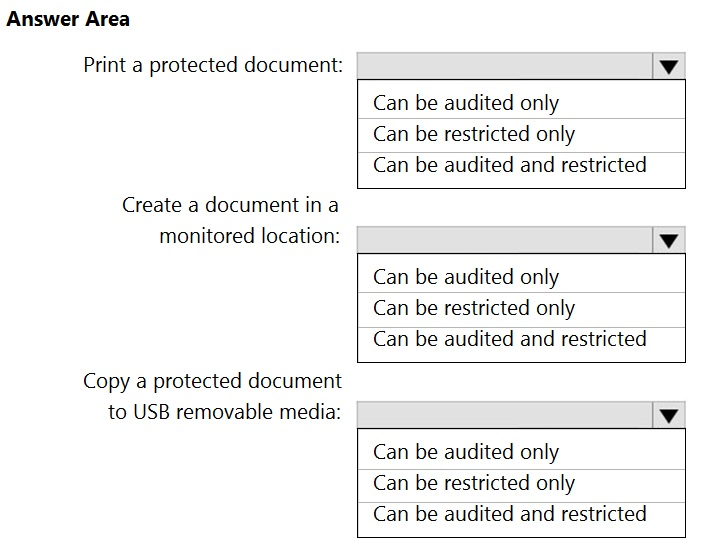
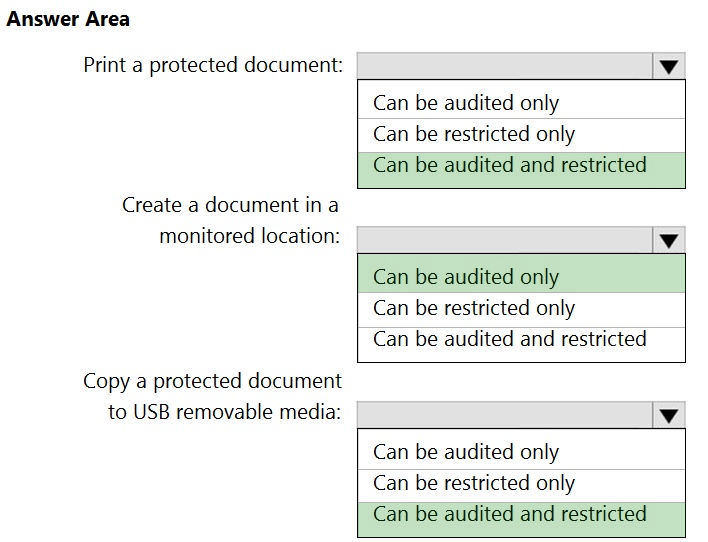
HOTSPOT - You plan to implement Microsoft 365 Endpoint data loss prevention (Endpoint DLP). You need to identify which end user activities can be audited on the endpoints, and which activities can be restricted on the endpoints. What should you identify for each activity? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 tenant that has devices onboarded to Microsoft Defender for Endpoint as shown in the following table.You plan to start using Microsoft 365 Endpoint data loss protection (Endpoint DLP). Which devices support Endpoint DLP?
A. Device5 only
B. Device2 only
C. Device1, Device2, Device3, Device4, and Device5
D. Device3 and Device4 only
E. Device1 and Device2 only
HOTSPOT - You have a Microsoft 365 subscription that contains the users shown in the following table.You create the data loss prevention (DLP) policies shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.You need to prevent users in the finance department from sharing files with users in the research department. Which type of policy should you configure?
A. communication compliance
B. information barrier
C. Conditional Access
D. insider risk management
You have a Microsoft 365 E5 tenant that contains the policies shown in the following table.A file named File1 has all the policies applied. How long will File1 be retained?
A. File1 will be deleted automatically after seven years.
B. File1 will be deleted automatically after five years.
C. File1 will be retained until the file is deleted manually.
D. File1 will be deleted automatically after 10 years.
You need to be alerted when users share sensitive documents from Microsoft OneDrive to any users outside your company. What should you do?
A. From the Microsoft Purview compliance portal, start a data investigation.
B. From the Microsoft Defender for Cloud Apps portal, create a file policy.
C. From the Azure Active Directory admin center, configure an Identity Protection policy.
D. From the Exchange admin center, create a data loss prevention (DLP) policy.
You need to create a retention policy to delete content after seven years from the following locations: ✑ Exchange Online email ✑ SharePoint Online sites ✑ OneDrive accounts Microsoft 365 groups -✑ Teams channel messages ✑ Teams chats What is the minimum number of retention policies that you should create?
A. 1
B. 2
C. 3
D. 4
HOTSPOT - You have a Microsoft SharePoint Online site that contains the following files.Users are assigned roles for the site as shown in the following table.
Which files can User1 and User2 view? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 E5 subscription. You are implementing insider risk management. You need to maximize the amount of historical data that is collected when an event is triggered. What is the maximum number of days that historical data can be collected?
A. 30
B. 60
C. 90
D. 180
You have a Microsoft 365 E5 subscription that contains a data loss prevention (DLP) policy named DLP1. DLP1 has a rule that triggers numerous alerts. You need to reduce the number of alert notifications that are generated. The solution must maintain the sensitivity of DLP1. What should you do?
A. Change the mode of DLP1 to Test without notifications.
B. Modify the rule and increase the instance count.
C. Modify the rule and configure an alert threshold.
D. Modify the rule and set the priority to the highest value.
DRAG DROP - You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Cloud Apps. You plan to deploy a Defender for Cloud Apps file policy that will be triggered when the following conditions are met: • A file is shared externally. • A file is labeled as internal only. Which filter should you use for each condition? To answer, drag the appropriate filters to the correct conditions. Each filter may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
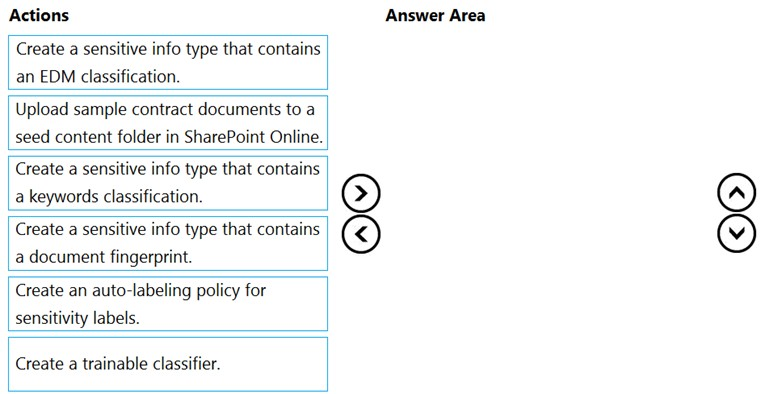
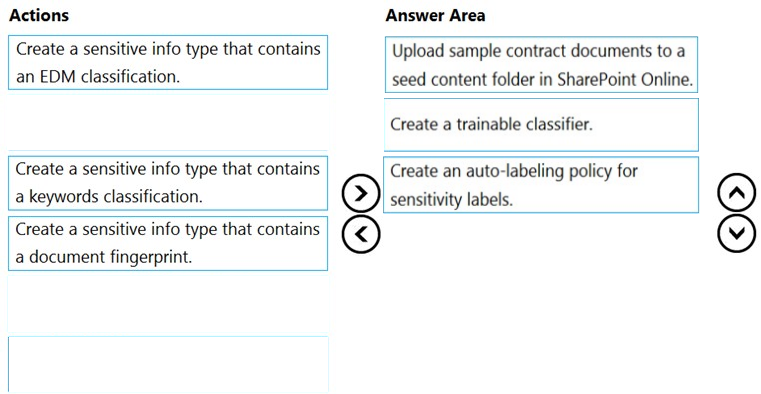
DRAG DROP - You need to recommend a solution that meets the sales requirements. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. (Choose three.) Select and Place:
SIMULATION - Use the following login credentials as needed: To enter your username, place your cursor in the Sign in box and click on the username below. To enter your password, place your cursor in the Enter password box and click on the password below. Microsoft 365 Username: admin@123456789.onmicrosoft.com Microsoft 365 Password: ********** If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab. The following information is for technical support purposes only: Lab Instance: 12345678 - You need to provide users with the ability to manually classify files that contain product information that are stored in SharePoint Online sites. The solution must meet the following requirements: • The users must be able to apply a classification of Product1 to the files. • Any authenticated user must be able to open files classified as Product1. • Files classified as Product1 must be encrypted. To complete this task, sign in to the appropriate admin center.
You need to recommend a solution that meets the compliance requirements for protecting the documents in the Data shared folder. What should you recommend?
A. From the Microsoft 365 compliance center, configure an auto-labeling policy.
B. From Azure Information Protection, configure a content scan job.
C. From the Microsoft 365 compliance center, configure a Content Search query.
D. From the Microsoft 365 compliance center, configure a DLP policy.
Free Access Full SC-400 Practice Exam Free
Looking for additional practice? Click here to access a full set of SC-400 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your SC-400 certification journey!