SC-300 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your SC-300 certification exam? Start your preparation the smart way with our SC-300 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for SC-300 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our SC-300 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
HOTSPOT - You have an Azure AD tenant that contains the groups shown in the following exhibit.Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
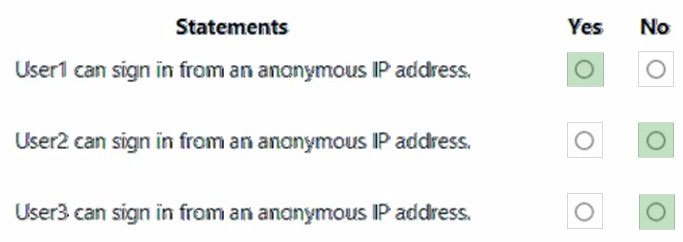
Overview - ADatum Corporation is a consulting company in Montreal. ADatum recently acquired a Vancouver-based company named Litware, Inc. Existing Environment. ADatum Environment The on-premises network of ADatum contains an Active Directory Domain Services (AD DS) forest named adatum.com. ADatum has a Microsoft 365 E5 subscription. The subscription contains a verified domain that syncs with the adatum.com AD DS domain by using Azure AD Connect. ADatum has an Azure Active Directory (Azure AD) tenant named adatum.com. The tenant has Security defaults disabled. The tenant contains the users shown in the following table.The tenant contains the groups shown in the following table.
Existing Environment. Litware Environment Litware has an AD DS forest named litware.com Existing Environment. Problem Statements ADatum identifies the following issues: • Multiple users in the sales department have up to five devices. The sales department users report that sometimes they must contact the support department to join their devices to the Azure AD tenant because they have reached their device limit. • A recent security incident reveals that several users leaked their credentials, a suspicious browser was used for a sign-in, and resources were accessed from an anonymous IP address. • When you attempt to assign the Device Administrators role to IT_Group1, the group does NOT appear in the selection list. • Anyone in the organization can invite guest users, including other guests and non-administrators. • The helpdesk spends too much time resetting user passwords. • Users currently use only passwords for authentication. Requirements. Planned Changes - ADatum plans to implement the following changes: • Configure self-service password reset (SSPR). • Configure multi-factor authentication (MFA) for all users. • Configure an access review for an access package named Package1. • Require admin approval for application access to organizational data. • Sync the AD DS users and groups of litware.com with the Azure AD tenant. • Ensure that only users that are assigned specific admin roles can invite guest users. • Increase the maximum number of devices that can be joined or registered to Azure AD to 10. Requirements. Technical Requirements ADatum identifies the following technical requirements: • Users assigned the User administrator role must be able to request permission to use the role when needed for up to one year. • Users must be prompted to register for MFA and provided with an option to bypass the registration for a grace period. • Users must provide one authentication method to reset their password by using SSPR. Available methods must include: - Email - Phone - Security questions - The Microsoft Authenticator app • Trust relationships must NOT be established between the adatum.com and litware.com AD DS domains. • The principle of least privilege must be used. You need to modify the settings of the User administrator role to meet the technical requirements. Which two actions should you perform for the role? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Select Require justification on activation.
B. Select Require ticket information on activation.
C. Modify the Expire eligible assignments after setting.
D. Set all assignments to Eligible.
E. Set all assignments to Active.
You need to resolve the issue of the sales department users. What should you configure for the Azure AD tenant?
A. the Device settings
B. the Access reviews settings
C. the User settings
D. Security defaults
HOTSPOT - You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1 and the users shown in the following table.The users have the devices shown in the following table.
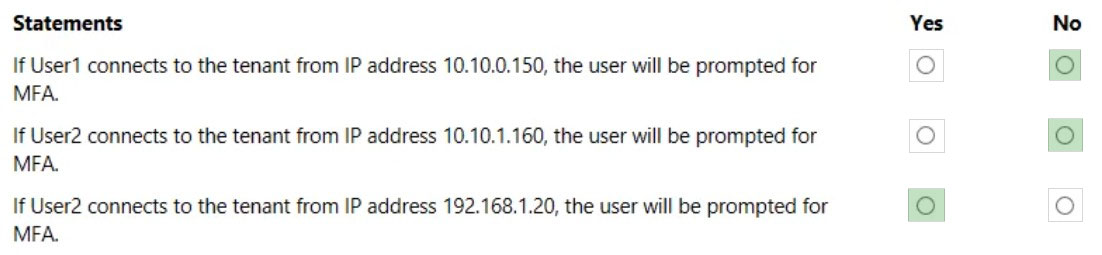
You create the following two Conditional Access policies: • Name: CAPolicy1 • Assignments o Users or workload identities: Group1 o Cloud apps or actions: Office 365 SharePoint Online o Conditions Filter for devices: Exclude filtered devices from the policy Rule syntax: device.displayName -startsWith “Device” o Access controls Grant: Block access Session: 0 controls selected o Enable policy: On • Name: CAPolicy2 • Assignments o Users or workload identities: Group2 o Cloud apps or actions: Office 365 SharePoint Online o Conditions: 0 conditions selected • Access controls o Grant: Grant access Require multifactor authentication o Session: 0 controls selected • Enable policy: On All users confirm that they can successfully authenticate using MFA. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You have an Azure AD tenant that contains an access package named Package1 and a user named User1. Package1 is configured as shown in the following exhibit.You need to ensure that User1 can modify the review frequency of Package1. The solution must use the principle of least privilege. Which role should you assign to User1?
A. Security administrator
B. Privileged role administrator
C. External Identity Provider administrator
D. User administrator
You have a Microsoft Exchange organization that uses an SMTP address space of contoso.com. Several users use their contoso.com email address for self-service sign-up to Azure AD. You gain global administrator privileges to the Azure AD tenant that contains the self-signed users. You need to prevent the users from creating user accounts in the contoso.com Azure AD tenant for self-service sign-up to Microsoft 365 services. Which PowerShell cmdlet should you run?
A. Update-MgOrganization
B. Update-MgPolicyPermissionGrantPolicyExclude
C. Update-MgDomain
D. Update-MgDomainFederationConfiguration
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You use Azure Monitor to analyze Azure Active Directory (Azure AD) activity logs. You receive more than 100 email alerts each day for failed Azure AD user sign-in attempts. You need to ensure that a new security administrator receives the alerts instead of you. Solution: From Azure AD, you modify the Diagnostics settings. Does this meet the goal?
A. Yes
B. No
Your company has two divisions named Contoso East and Contoso West. The Microsoft 365 identity architecture for both divisions is shown in the following exhibit.You need to assign users from the Contoso East division access to Microsoft SharePoint Online sites in the Contoso West tenant. The solution must not require additional Microsoft 365 licenses. What should you do?
A. Configure Azure AD Application Proxy in the Contoso West tenant.
B. Invite the Contoso East users as guests in the Contoso West tenant.
C. Deploy a second Azure AD Connect server to Contoso East and configure the server to sync the Contoso East Active Directory forest to the Contoso West tenant.
D. Configure the existing Azure AD Connect server in Contoso East to sync the Contoso East Active Directory forest to the Contoso West tenant.
HOTSPOT - Overview - ADatum Corporation is a consulting company in Montreal. ADatum recently acquired a Vancouver-based company named Litware, Inc. Existing Environment. ADatum Environment The on-premises network of ADatum contains an Active Directory Domain Services (AD DS) forest named adatum.com. ADatum has a Microsoft 365 E5 subscription. The subscription contains a verified domain that syncs with the adatum.com AD DS domain by using Azure AD Connect. ADatum has an Azure Active Directory (Azure AD) tenant named adatum.com. The tenant has Security defaults disabled. The tenant contains the users shown in the following table.The tenant contains the groups shown in the following table.
Existing Environment. Litware Environment Litware has an AD DS forest named litware.com Existing Environment. Problem Statements ADatum identifies the following issues: • Multiple users in the sales department have up to five devices. The sales department users report that sometimes they must contact the support department to join their devices to the Azure AD tenant because they have reached their device limit. • A recent security incident reveals that several users leaked their credentials, a suspicious browser was used for a sign-in, and resources were accessed from an anonymous IP address. • When you attempt to assign the Device Administrators role to IT_Group1, the group does NOT appear in the selection list. • Anyone in the organization can invite guest users, including other guests and non-administrators. • The helpdesk spends too much time resetting user passwords. • Users currently use only passwords for authentication. Requirements. Planned Changes - ADatum plans to implement the following changes: • Configure self-service password reset (SSPR). • Configure multi-factor authentication (MFA) for all users. • Configure an access review for an access package named Package1. • Require admin approval for application access to organizational data. • Sync the AD DS users and groups of litware.com with the Azure AD tenant. • Ensure that only users that are assigned specific admin roles can invite guest users. • Increase the maximum number of devices that can be joined or registered to Azure AD to 10. Requirements. Technical Requirements ADatum identifies the following technical requirements: • Users assigned the User administrator role must be able to request permission to use the role when needed for up to one year. • Users must be prompted to register for MFA and provided with an option to bypass the registration for a grace period. • Users must provide one authentication method to reset their password by using SSPR. Available methods must include: - Email - Phone - Security questions - The Microsoft Authenticator app • Trust relationships must NOT be established between the adatum.com and litware.com AD DS domains. • The principle of least privilege must be used. You need to support the planned changes and meet the technical requirements for MFA. Which feature should you use, and how long before the users must complete the registration? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure AD tenant. You need to ensure that only users from specific external domains can be invited as guests to the tenant. Which settings should you configure?
A. External collaboration settings
B. All identity providers
C. Cross-tenant access settings
D. Linked subscriptions
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 tenant. All users must use the Microsoft Authenticator app for multi-factor authentication (MFA) when accessing Microsoft 365 services. Some users report that they received an MFA prompt on their Microsoft Authenticator app without initiating a sign-in request. You need to block the users automatically when they report an MFA request that they did not initiate. Solution: From the Azure portal, you configure the Notifications settings for multi-factor authentication (MFA). Does this meet the goal?
A. Yes
B. No
You have an Azure Active Directory (Azure AD) tenant. You configure self-service password reset (SSPR) by using the following settings: • Require users to register when signing in: Yes • Number of methods required to reset: 1 What is a valid authentication method available to users?
A. a smartcard
B. a mobile app code
C. a mobile app notification
D. an email to an address outside your organization
You have an Azure Active Directory (Azure AD) tenant. For the tenant, Users can register applications is set to No. A user named Admin1 must deploy a new cloud app named App1. You need to ensure that Admin1 can register App1 in Azure AD. The solution must use the principle of least privilege. Which role should you assign to Admin1?
A. Managed Application Contributor for Subscription1.
B. Application developer in Azure AD.
C. Cloud application administrator in Azure AD.
D. App Configuration Data Owner for Subscription1.
Your company has a Microsoft 365 tenant. The company has a call center that contains 300 users. In the call center, the users share desktop computers and might use a different computer every day. The call center computers are NOT configured for biometric identification. The users are prohibited from having a mobile phone in the call center. You need to require multi-factor authentication (MFA) for the call center users when they access Microsoft 365 services. What should you include in the solution?
A. a named network location
B. the Microsoft Authenticator app
C. Windows Hello for Business authentication
D. FIDO2 tokens
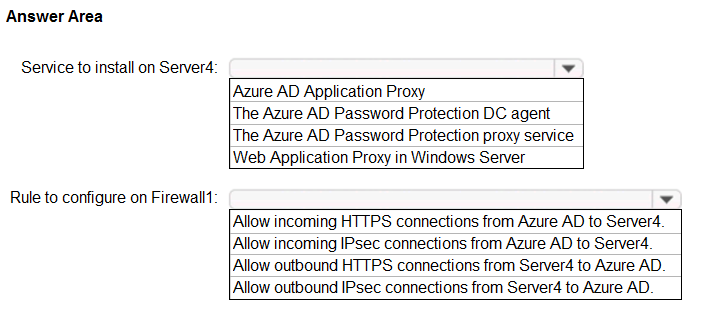
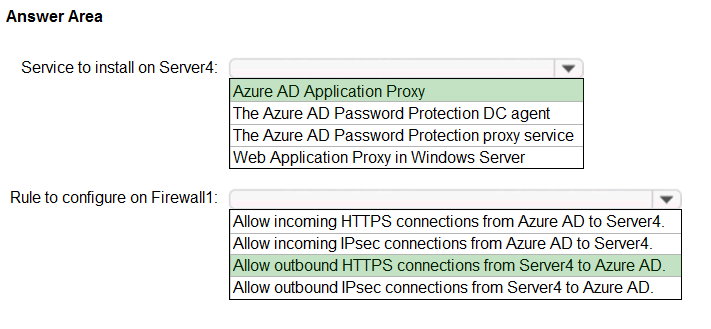
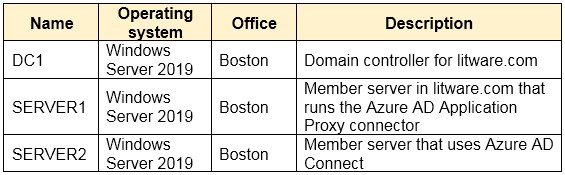
HOTSPOT - You have an on-premises datacenter that contains the hosts shown in the following table.The Active Directory forest syncs to an Azure Active Directory (Azure AD) tenant. Multi-factor authentication (MFA) is enforced for Azure AD. You need to ensure that you can publish App1 to Azure AD users. What should you configure on Server4 and Firewall1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You have an Azure subscription. You need to create two custom roles named Role1 and Role2. The solution must meet the following requirements: • Users that are assigned Role1 can create or delete instances of Azure Container Apps. • Users that are assigned Role2 can enforce adaptive network hardening rules. Which resource provider permissions are required for each role? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT - How should the access be setup to the on-premises applications? Hot Area:
You have a Microsoft Entra tenant. You need to query risky user activity for the tenant. How long will the logs of risky user activity be retained?
A. 30 days
B. 60 days
C. 90 days
D. 180 days
You have an Azure AD tenant that contains the external user shown in the following exhibit.You update the email address of the user. You need to ensure that the user can authenticate by using the updated email address. What should you do for the user?
A. Modify the Authentication methods settings.
B. Reset the password.
C. Revoke the active sessions.
D. Reset the redemption status.
You have an Azure subscription named Sub1 that uses Microsoft Entra Permissions Management. Sub1 contains a user named User1. User1 is granted multiple permissions across Sub1. You need to replace all the permissions granted to User1 with read-only permissions. The solution must minimize administrative effort. What should you do on the Remediation tab in Permissions Management?
A. From the Role/Policy Template subtab, create a template.
B. From the My Requests subtab, create a new request.
C. From the Roles/Policies subtab, create a role.
D. From the Permissions subtab, use a quick action.
You have a Microsoft 365 E5 subscription. You need to create a Microsoft Defender for Cloud Apps session policy. What should you do first?
A. From the Microsoft Defender for Cloud Apps portal, select User monitoring.
B. From the Microsoft Defender for Cloud Apps portal, select App onboarding/maintenance.
C. From the Azure Active Directory admin center, create a Conditional Access policy.
D. From the Microsoft Defender for Cloud Apps portal, create a continuous report.
You have 2,500 users who are assigned Microsoft Office 365 Enterprise E3 licenses. The licenses are assigned to individual users. From the Groups blade in the Azure Active Directory admin center, you assign Microsoft 365 Enterprise E5 licenses to the users. You need to remove the Office 365 Enterprise E3 licenses from the users by using the least amount of administrative effort. What should you use?
A. the Administrative units blade in the Azure Active Directory admin center
B. the Set-AzureAdUser cmdlet
C. the Groups blade in the Azure Active Directory admin center
D. the Set-MsolUserLicense cmdlet
A company uses Dynamics 365 Supply Chain Management master planning. The company plans to run master planning throughout the day. Planning Optimization is not configured. The company administrator reports that they are not able to configure any master planning features or enable master planning in Dynamics 365. You need to implement Planning Optimization. What should you do first?
A. Place the environment into maintenance mode.
B. Deallocate the current environment.
C. Enable the Planning Optimization configuration key.
D. Set the value of the Use Planning Optimization field to yes.
E. Activate the Planning Optimization license.
A user named User1 receives an error message when attempting to access the Microsoft Defender for Cloud Apps portal. You need to identify the cause of the error. The solution must minimize administrative effort. What should you use?
A. Log Analytics
B. sign-in logs
C. audit logs
D. provisioning logs
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains an Azure AD enterprise application named App1. A contractor uses the credentials of user1@outlook.com . You need to ensure that you can provide the contractor with access to App1. The contractor must be able to authenticate as user1@outlook.com . What should you do?
A. Run the New-AzureADMSInvitation cmdlet.
B. Configure the External collaboration settings.
C. Add a WS-Fed identity provider.
D. Implement Azure AD Connect.
You have an Azure subscription that contains a user-assigned managed identity named Managed1 in the East US Azure region. The subscription contains the resources shown in the following table.Which resources can use Managed1 as their identity?
A. WebApp1 only
B. storage1 and WebApp1 only
C. VM1 and WebApp1 only
D. VM1, storage1, and WebApp1
You have an Azure Active Directory (Azure AD) tenant named contoso.com. You plan to bulk invite Azure AD business-to-business (B2B) collaboration users. Which two parameters must you include when you create the bulk invite? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. email address
B. redirection URL
C. username
D. shared key
E. password
You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.You add an enterprise application named App1 to Azure AD and set User1 as the owner of App1. App1 requires admin consent to access Azure AD before the app can be used. You configure the Admin consent requests settings as shown in the following exhibit.
Admin1, Admin2, Admin3, and User’ are added as reviewers. Which users can review and approve the admin consent requests?
A. Admin1 only
B. Admin1, Admin2 and Admin3 only
C. Admin1, Admin2, and User1 only
D. Admin1 and Admin2 only
E. Admin1, Admin2, Admin3, and User1
HOTSPOT - You have an Azure subscription that contains the resources shown in the following table.You need to configure access to Vault1. The solution must meet the following requirements: • Ensure that User1 can manage and create keys in Vault1. • Ensure that User2 can access a certificate stored in Vault1. • Use the principle of least privilege. Which role should you assign to each user? To answer select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure Active Directory (Azure AD) tenant. You configure self-service password reset (SSPR) by using the following settings: ✑ Require users to register when signing in: Yes ✑ Number of methods required to reset: 1 What is a valid authentication method available to users?
A. a Microsoft Teams chat
B. a mobile app notification
C. a mobile app code
D. an FIDO2 security token
You have an Azure AD tenant. You configure User consent settings to allow users to provide consent to apps from verified publishers. You need to ensure that the users can only provide consent to apps that require low impact permissions. What should you do?
A. Create an enterprise application collection.
B. Create an access review.
C. Create an access package.
D. Configure permission classifications.
You have an Azure Active Directory (Azure AD) tenant that contains a user named SecAdmin1. SecAdmin1 is assigned the Security administrator role. SecAdmin1 reports that she cannot reset passwords from the Azure AD Identity Protection portal. You need to ensure that SecAdmin1 can manage passwords and invalidate sessions on behalf of non-administrative users. The solution must use the principle of least privilege. Which role should you assign to SecAdmin1?
A. Authentication administrator
B. Helpdesk administrator
C. Privileged authentication administrator
D. Security operator
You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.User1 is the owner of Group1. You create an access review that has the following settings: ✑ Users to review: Members of a group ✑ Scope: Everyone ✑ Group: Group1 ✑ Reviewers: Members (self) Which users can perform access reviews for User3?
A. User1, User2, and User3
B. User3 only
C. User1 only
D. User1 and User2 only
HOTSPOT - You have an Azure AD tenant. You perform the tasks shown in the following table.On April 5, an administrator deletes App1, App2, App3, and App4. You need to restore the apps and the settings. Which apps can you restore on April 16, and which settings can you restore for App4 on April 16? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant: that contains the users shown in the following table.In Azure. AD Identity Protection, you configure a user risk policy that has the following settings: ✑ Assignments: - Users: Group1 - User risk: Low and above ✑ Controls: - Access: Block access ✑ Enforce policy: On In Azure AD Identify Protection, you configure a sign-in risk policy that has the following settings: ✑ Assignments: - Users: Group2 - Sign-in risk: Low and above ✑ Controls: - Access: Require multi-factor authentication ✑ Enforce policy: On For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You have an Azure Active Directory (Azure AD) tenant that contains the users shown in, the following table.The User settings for enterprise applications have the following configurations: ✑ Users can consent to apps accessing company data on their behalf: No ✑ Users can consent to apps accessing company data for the groups they own: No ✑ Users can request admin consent to apps they are unable to consent to: Yes Who can review admin consent requests: Admin2, User2
User1 attempts, to add an app that requires consent to access company data. Which user can provide consent?
A. User1
B. User2
C. Admin1
D. Admin2
You have 2,500 users who are assigned Microsoft Office 365 Enterprise E3 licenses. The licenses are assigned to individual users. From the Groups blade in the Azure Active Directory admin center, you assign Microsoft 365 Enterprise E5 licenses to a group that includes all the users. You need to remove the Office 365 Enterprise E3 licenses from the users by using the least amount of administrative effort. What should you use?
A. the Set-AzureADGroup cmdlet
B. the Identity Governance blade in the Azure Active Directory admin center
C. the Set-WindowsProductKey cmdlet
D. the Set-MsolUserLicense cmdlet
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Cloud Apps. You plan to increase app security for the subscription. You need to identify which apps do NOT require user authentication. What should you do in the Microsoft 365 Defender portal?
A. Review the cloud app catalog.
B. Create an OAuth policy and review alerts.
C. Create a snapshot Cloud Discovery report.
D. Create a discovered app query.
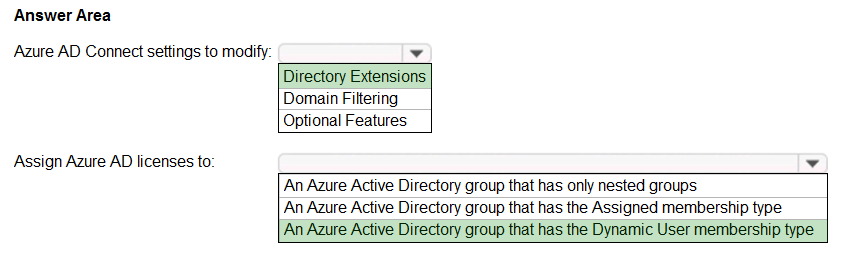
HOTSPOT - You need to configure the assignment of Azure AD licenses to the Litware users. The solution must meet the licensing requirements. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains an Azure AD enterprise application named App1. A contractor uses the credentials of user1@outlook.com . You need to ensure that you can provide the contractor with access to App1. The contractor must be able to authenticate as user1@outlook.com . What should you do?
A. Run the New-AzADUser cmdlet.
B. Configure the External collaboration settings.
C. Add a WS-Fed identity provider.
D. Create a guest user account in contoso.com.
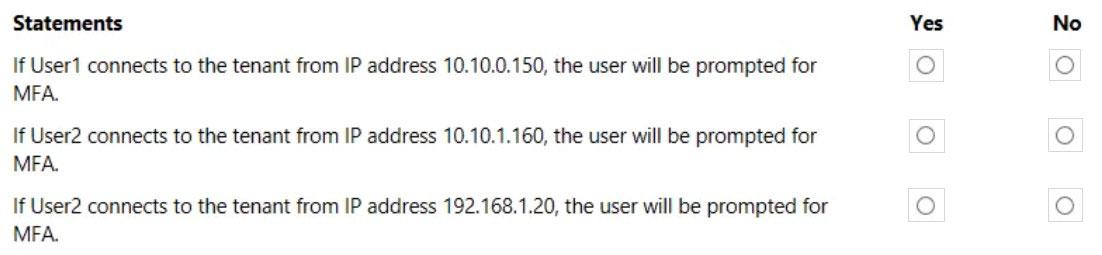
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.You have the locations shown in the following table.
The tenant contains a named location that has the following configurations: ✑ Name: Location1 ✑ Mark as trusted location: Enabled IPv4 range: 10.10.0.0/16 -
MFA has a trusted IP address range of 193.17.17.0/24. ✑ Name: CAPolicy1 ✑ Assignments - Users or workload identities: Group1 - Cloud apps or actions: All cloud apps ✑ Conditions - Locations: All trusted locations ✑ Access controls - Grant - Grant access: Require multi-factor authentication - Session: 0 controls selected ✑ Enable policy: On For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft Exchange organization that uses an SMTP address space of contoso.com. Several users use their contoso.com email address for self-service sign-up to Azure Active Directory (Azure AD). You gain global administrator privileges to the Azure AD tenant that contains the self-signed users. You need to prevent the users from creating user accounts in the contoso.com Azure AD tenant for self-service sign-up to Microsoft 365 services. Which PowerShell cmdlet should you run?
A. Set-MsolCompanySettings
B. Set-MsolDomainFederationSettings
C. Update-MsolfederatedDomain
D. Set-MsolDomain
You have an Azure Active Directory (Azure AD) tenant named contoso.com that has Azure AD Identity Protection enabled. You need to implement a sign-in risk remediation policy without blocking user access. What should you do first?
A. Configure access reviews in Azure AD.
B. Enforce Azure AD Password Protection.
C. Configure self-service password reset (SSPR) for all users.
D. Implement multi-factor authentication (MFA) for all users.
You have an Azure AD Premium P2 tenant. You create a Log Analytics workspace. You need to ensure that you can view Azure AD audit log information by using Azure Monitor. What should you do first?
A. Modify the Diagnostics settings for Azure AD.
B. Run the Update-MgOrganization cmdlet.
C. Run the Update-MgDomain cmdlet.
D. Create an Azure AD workbook.
You have a Microsoft 365 E5 subscription that contains three users named User1, User2, and User3 and a Microsoft SharePoint Online site named Site1. The subscription contains the devices shown in the following table.The users sign in to the devices as shown in the following table.
You have a Conditional Access policy that has the following settings: • Name: CA1 • Assignments o Users and groups: User1, User2, User3 o Cloud apps or actions: SharePoint - Site1 • Access controls o Session: Use app enforced restrictions From the SharePoint admin center, you configure Access control for unmanaged devices to allow limited, web-only access. Which users will have full access to Site1?
A. User1 only
B. User2 only
C. User3only
D. User1 and User2 only
E. User1, User2, and User3
You have an Azure AD tenant that contains the users shown in the following table.You need to compare the role permissions of each user. The solution must minimize administrative effort. What should you use?
A. the Microsoft 365 Defender portal
B. the Microsoft 365 admin center
C. the Microsoft Entra admin center
D. the Microsoft Purview compliance portal
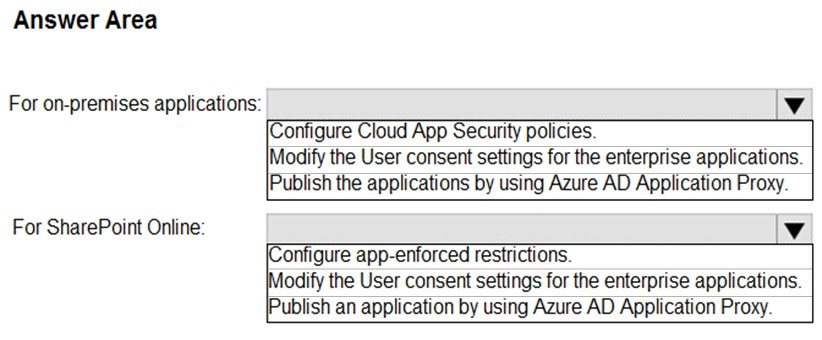
HOTSPOT - You need to implement on-premises application and SharePoint Online restrictions to meet the authentication requirements and the access requirements. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
Overview - ADatum Corporation is a consulting company in Montreal. ADatum recently acquired a Vancouver-based company named Litware, Inc. Existing Environment. ADatum Environment The on-premises network of ADatum contains an Active Directory Domain Services (AD DS) forest named adatum.com. ADatum has a Microsoft 365 E5 subscription. The subscription contains a verified domain that syncs with the adatum.com AD DS domain by using Azure AD Connect. ADatum has an Azure Active Directory (Azure AD) tenant named adatum.com. The tenant has Security defaults disabled. The tenant contains the users shown in the following table.The tenant contains the groups shown in the following table.
Existing Environment. Litware Environment Litware has an AD DS forest named litware.com Existing Environment. Problem Statements ADatum identifies the following issues: • Multiple users in the sales department have up to five devices. The sales department users report that sometimes they must contact the support department to join their devices to the Azure AD tenant because they have reached their device limit. • A recent security incident reveals that several users leaked their credentials, a suspicious browser was used for a sign-in, and resources were accessed from an anonymous IP address. • When you attempt to assign the Device Administrators role to IT_Group1, the group does NOT appear in the selection list. • Anyone in the organization can invite guest users, including other guests and non-administrators. • The helpdesk spends too much time resetting user passwords. • Users currently use only passwords for authentication. Requirements. Planned Changes - ADatum plans to implement the following changes: • Configure self-service password reset (SSPR). • Configure multi-factor authentication (MFA) for all users. • Configure an access review for an access package named Package1. • Require admin approval for application access to organizational data. • Sync the AD DS users and groups of litware.com with the Azure AD tenant. • Ensure that only users that are assigned specific admin roles can invite guest users. • Increase the maximum number of devices that can be joined or registered to Azure AD to 10. Requirements. Technical Requirements ADatum identifies the following technical requirements: • Users assigned the User administrator role must be able to request permission to use the role when needed for up to one year. • Users must be prompted to register for MFA and provided with an option to bypass the registration for a grace period. • Users must provide one authentication method to reset their password by using SSPR. Available methods must include: - Email - Phone - Security questions - The Microsoft Authenticator app • Trust relationships must NOT be established between the adatum.com and litware.com AD DS domains. • The principle of least privilege must be used. You need to implement the planned changes for litware.com. What should you configure?
A. Azure AD Connect cloud sync between the Azure AD tenant and litware.com
B. Azure AD Connect to include the litware.com domain
C. staging mode in Azure AD Connect for the litware.com domain
HOTSPOT - Overview - Contoso, Ltd. is a consulting company that has a main office in Montreal and branch offices in London and Seattle. Contoso has a partnership with a company named Fabrikam, Inc. Fabrikam has an Azure Active Directory (Azure AD) tenant named fabrikam.com. Existing Environment. Existing Environment The on-premises network of Contoso contains an Active Directory domain named contoso.com. The domain contains an organizational unit (OU) named Contoso_Resources. The Contoso_Resources OU contains all users and computers. The contoso.com Active Directory domain contains the relevant users shown in the following table.Contoso also includes a marketing department that has users in each office. Existing Environment. Microsoft 365/Azure Environment Contoso has an Azure AD tenant named contoso.com that has the following associated licenses: • Microsoft Office 365 Enterprise E5 • Enterprise Mobility + Security E5 • Windows 10 Enterprise E3 • Project Plan 3 Azure AD Connect is configured between Azure AD and Active Directory Domain Services (AD DS). Only the Contoso_Resources OU is synced. Helpdesk administrators routinely use the Microsoft 365 admin center to manage user settings. User administrators currently use the Microsoft 365 admin center to manually assign licenses. All users have all licenses assigned besides the following exceptions: • The users in the London office have the Microsoft 365 Phone System license unassigned. • The users in the Seattle office have the Yammer Enterprise license unassigned. Security defaults are disabled for contoso.com. Contoso uses Azure AD Privileged Identity Management (PIM) to protect administrative roles. Existing Environment. Problem Statements Contoso identifies the following issues: • Currently, all the helpdesk administrators can manage user licenses throughout the entire Microsoft 365 tenant. • The user administrators report that it is tedious to manually configure the different license requirements for each Contoso office. • The helpdesk administrators spend too much time provisioning internal and guest access to the required Microsoft 365 services and apps. • Currently, the helpdesk administrators can perform tasks by using the User administrator role without justification or approval. • When the Logs node is selected in Azure AD, an error message appears stating that Log Analytics integration is not enabled. Requirements. Planned Changes - Contoso plans to implement the following changes: • Implement self-service password reset (SSPR). • Analyze Azure audit activity logs by using Azure Monitor. • Simplify license allocation for new users added to the tenant. • Collaborate with the users at Fabrikam on a joint marketing campaign. • Configure the User administrator role to require justification and approval to activate. • Implement a custom line-of-business Azure web app named App1. App1 will be accessible from the internet and authenticated by using Azure AD accounts. • For new users in the marketing department, implement an automated approval workflow to provide access to a Microsoft SharePoint Online site, group, and app. Contoso plans to acquire a company named ADatum Corporation. One hundred new ADatum users will be created in an Active Directory OU named Adatum. The users will be located in London and Seattle. Requirements. Technical Requirements Contoso identifies the following technical requirements: • All users must be synced from AD DS to the contoso.com Azure AD tenant. • App1 must have a redirect URI pointed to https://contoso.com/auth-response. • License allocation for new users must be assigned automatically based on the location of the user. • Fabrikam users must have access to the marketing department’s SharePoint site for a maximum of 90 days. • Administrative actions performed in Azure AD must be audited. Audit logs must be retained for one year. • The helpdesk administrators must be able to manage licenses for only the users in their respective office. • Users must be forced to change their password if there is a probability that the users’ identity was compromised. You need to meet the technical requirements for license management by the help desk administrators. What should you create first, and which tool should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You need to sync the ADatum users. The solution must meet the technical requirements. What should you do?
A. From the Microsoft Azure Active Directory Connect wizard, select Customize synchronization options.
B. From PowerShell, run Set-ADSyncScheduler.
C. From PowerShell, run Start-ADSyncSyncCycle.
D. From the Microsoft Azure Active Directory Connect wizard, select Change user sign-in.
Access Full SC-300 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete SC-300 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our SC-300 mock test free today—and take a major step toward exam success!