SC-100 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the SC-100 certification? Take your preparation to the next level with our SC-100 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a SC-100 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic SC-100 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
DRAG DROP - Your company wants to optimize ransomware incident investigations. You need to recommend a plan to investigate ransomware incidents based on the Microsoft Detection and Response Team (DART) approach. Which three actions should you recommend performing in sequence in the plan? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
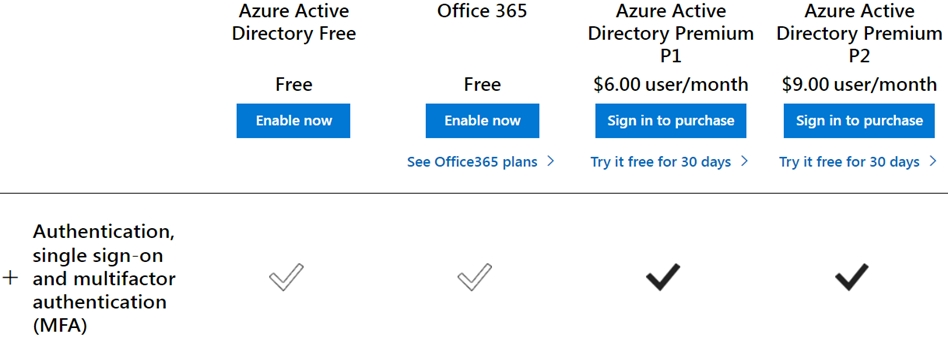
You have a customer that has a Microsoft 365 subscription and uses the Free edition of Azure Active Directory (Azure AD). The customer plans to obtain an Azure subscription and provision several Azure resources. You need to evaluate the customer's security environment. What will necessitate an upgrade from the Azure AD Free edition to the Premium edition?
A. Azure AD Privileged Identity Management (PIM)
B. role-based authorization
C. resource-based authorization
D. Azure AD Multi-Factor Authentication
29 DRAG DROP For a Microsoft cloud environment, you need to recommend a security architecture that follows the Zero Trust principles of the Microsoft Cybersecurity Reference Architectures (MCRA). Which security methodologies should you include in the recommendation? To answer, drag the appropriate methodologies to the correct principles. Each methodology may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
You have legacy operational technology (OT) devices and IoT devices. You need to recommend best practices for applying Zero Trust principles to the OT and IoT devices based on the Microsoft Cybersecurity Reference Architectures (MCRA). The solution must minimize the risk of disrupting business operations. Which two security methodologies should you include in the recommendation? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. active scanning
B. threat monitoring
C. software patching
D. passive traffic monitoring
HOTSPOT - What should you create in Azure AD to meet the Contoso developer requirements? Hot Area:
Your company plans to move all on-premises virtual machines to Azure. A network engineer proposes the Azure virtual network design shown in the following table.You need to recommend an Azure Bastion deployment to provide secure remote access to all the virtual machines. Based on the virtual network design, how many Azure Bastion subnets are required?
A. 1
B. 2
C. 3
D. 4
E. 5
HOTSPOT - You have a Microsoft 365 E5 subscription that uses Microsoft Purview, SharePoint Online, and OneDrive for Business. You need to recommend a ransomware protection solution that meets the following requirements: • Mitigates attacks that make copies of files, encrypt the copies, and then delete the original files • Mitigates attacks that encrypt files in place • Minimizes administrative effort What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
DRAG DROP - You have a Microsoft 365 subscription. You need to recommend a security solution to monitor the following activities: • User accounts that were potentially compromised • Users performing bulk file downloads from Microsoft SharePoint Online What should you include in the recommendation for each activity? To answer, drag the appropriate components to the correct activities. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
HOTSPOT - You have a Microsoft 365 E5 subscription that uses Microsoft Exchange Online. You need to recommend a solution to prevent malicious actors from impersonating the email addresses of internal senders. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription. You need to design a solution to block file downloads from Microsoft SharePoint Online by authenticated users on unmanaged devices. Which two services should you include in the solution? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Azure AD Conditional Access
B. Azure Data Catalog
C. Microsoft Purview Information Protection
D. Azure AD Application Proxy
E. Microsoft Defender for Cloud Apps
Your company is moving a big data solution to Azure. The company plans to use the following storage workloads: ✑ Azure Storage blob containers ✑ Azure Data Lake Storage Gen2 Azure Storage file shares -✑ Azure Disk Storage Which two storage workloads support authentication by using Azure Active Directory (Azure AD)? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Azure Storage file shares
B. Azure Disk Storage
C. Azure Storage blob containers
D. Azure Data Lake Storage Gen2
Your company has an on-premises network, an Azure subscription, and a Microsoft 365 E5 subscription. The company uses the following devices: ✑ Computers that run either Windows 10 or Windows 11 ✑ Tablets and phones that run either Android or iOS You need to recommend a solution to classify and encrypt sensitive Microsoft Office 365 data regardless of where the data is stored. What should you include in the recommendation?
A. eDiscovery
B. Microsoft Information Protection
C. Compliance Manager
D. retention policies
Your company is designing an application architecture for Azure App Service Environment (ASE) web apps as shown in the exhibit. (Click the Exhibit tab.)Communication between the on-premises network and Azure uses an ExpressRoute connection. You need to recommend a solution to ensure that the web apps can communicate with the on-premises application server. The solution must minimize the number of public IP addresses that are allowed to access the on-premises network. What should you include in the recommendation?
A. Azure Traffic Manager with priority traffic-routing methods
B. Azure Firewall with policy rule sets
C. Azure Front Door with Azure Web Application Firewall (WAF)
D. Azure Application Gateway v2 with user-defined routes (UDRs)
You are designing the security standards for a new Azure environment. You need to design a privileged identity strategy based on the Zero Trust model. Which framework should you follow to create the design?
A. Microsoft Security Development Lifecycle (SDL)
B. Enhanced Security Admin Environment (ESAE)
C. Rapid Modernization Plan (RaMP)
D. Microsoft Operational Security Assurance (OSA)
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your on-premises network contains an e-commerce web app that was developed in Angular and Node,js. The web app uses a MongoDB database. You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone.You need to provide recommendations to secure the connection between the web app and the database. The solution must follow the Zero Trust model. Solution: You recommend implementing Azure Application Gateway with Azure Web Application Firewall (WAF). Does this meet the goal?
A. Yes
B. No
Your company is developing an invoicing application that will use Azure AD B2C. The application will be deployed as an App Service web app. You need to recommend a solution to the application development team to secure the application from identity-related attacks. Which two configurations should you recommend? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Azure AD Conditional Access integration with user flows and custom policies
B. smart account lockout in Azure AD B2C
C. access packages in Identity Governance
D. custom resource owner password credentials (ROPC) flows in Azure AD B2C
HOTSPOT - For a Microsoft cloud environment, you are designing a security architecture based on the Microsoft Cybersecurity Reference Architectures (MCRA). You need to protect against the following external threats of an attack chain: • An attacker attempts to exfiltrate data to external websites. • An attacker attempts lateral movement across domain-joined computers. What should you include in the recommendation for each threat? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Your company has an Azure subscription that uses Microsoft Defender for Cloud. The company signs a contract with the United States government. You need to review the current subscription for NIST 800-53 compliance. What should you do first?
A. From Defender for Cloud, enable Defender for Cloud plans.
B. From Defender for Cloud, review the Azure security baseline for audit report.
C. From Defender for Cloud, add a regulatory compliance standard.
D. From Microsoft Defender for Cloud Apps, create an access policy for cloud applications.
HOTSPOT - You use Azure Policy with Azure Repos to implement continuous integration and continuous deployment (CI/CD) workflows. You need to recommend best practices to secure the stages of the CI/CD workflows based on the Microsoft Cloud Adoption Framework for Azure. What should you include in the recommendation for each stage? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Azure subscription that has Microsoft Defender for Cloud enabled. You are evaluating the Azure Security Benchmark V3 report. In the Secure management ports controls, you discover that you have 0 out of a potential 8 points. You need to recommend configurations to increase the score of the Secure management ports controls. Solution: You recommend enabling the VMAccess extension on all virtual machines. Does this meet the goal?
A. Yes
B. No
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You are designing the encryption standards for data at rest for an Azure resource. You need to provide recommendations to ensure that the data at rest is encrypted by using AES-256 keys. The solution must support rotating the encryption keys monthly. Solution: For Azure SQL databases, you recommend Transparent Data Encryption (TDE) that uses Microsoft-managed keys. Does this meet the goal?
A. Yes
B. No
A customer has a hybrid cloud infrastructure that contains a Microsoft 365 E5 subscription and an Azure subscription. All on-premises servers in the perimeter network are prevented from connecting directly to the internet. The customer recently recovered from a ransomware attack. The customer plans to deploy Microsoft Sentinel. You need to recommend solutions to meet the following requirements: ✑ Ensure that the security operations team can access the security logs and the operation logs. ✑ Ensure that the IT operations team can access only the operations logs, including the event logs of the servers in the perimeter network. Which two solutions should you include in the recommendation? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. a custom collector that uses the Log Analytics agent
B. the Azure Monitor agent
C. resource-based role-based access control (RBAC)
D. Azure Active Directory (Azure AD) Conditional Access policies
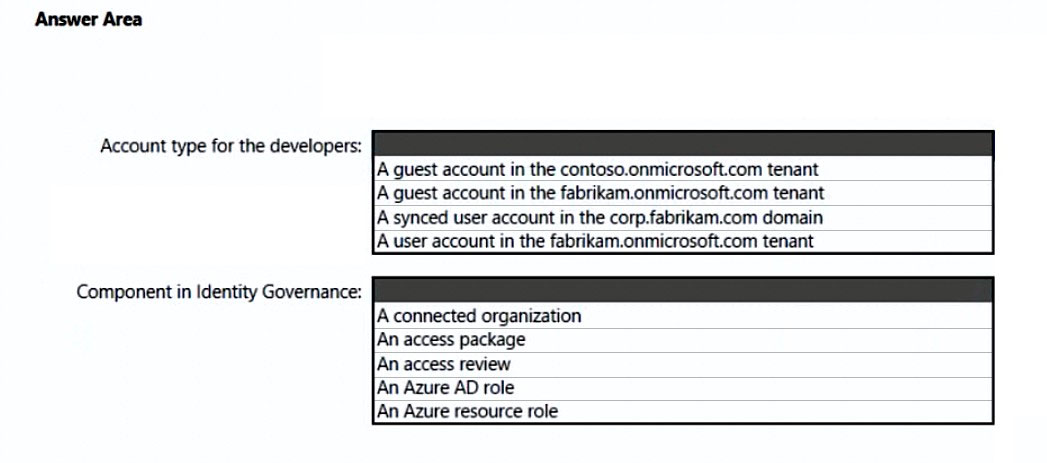
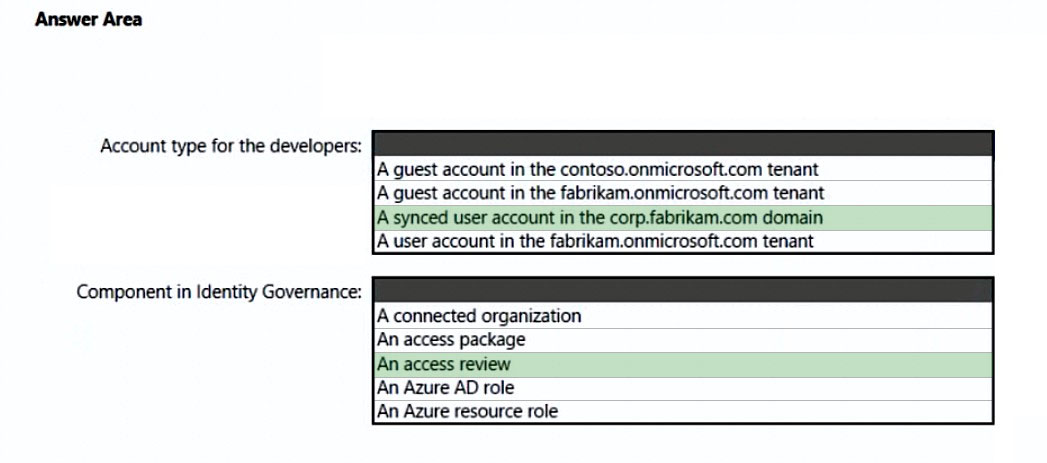
HOTSPOT - You are designing a privileged access strategy for a company named Contoso, Ltd. and its partner company named Fabrikam, Inc. Contoso has an Azure AD tenant named contoso.com. Fabrikam has an Azure AD tenant named fabrikam.com. Users at Fabrikam must access the resources in contoso.com. You need to provide the Fabrikam users with access to the Contoso resources by using access packages. The solution must meet the following requirements: • Ensure that the Fabrikam users can use the Contoso access packages without explicitly creating guest accounts in contoso.com. • Allow non-administrative users in contoso.com to create the access packages. What should you use for each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have the following on-premises servers that run Windows Server: • Two domain controllers in an Active Directory Domain Services (AD DS) domain • Two application servers named Server1 and Server2 that run ASP.NET web apps • A VPN server named Served that authenticates by using RADIUS and AD DS End users use a VPN to access the web apps over the internet. You need to redesign a user access solution to increase the security of the connections to the web apps. The solution must minimize the attack surface and follow the Zero Trust principles of the Microsoft Cybersecurity Reference Architectures (MCRA). What should you include in the recommendation?
A. Publish the web apps by using Azure AD Application Proxy.
B. Configure the VPN to use Azure AD authentication.
C. Configure connectors and rules in Microsoft Defender for Cloud Apps.
D. Configure web protection in Microsoft Defender for Endpoint.
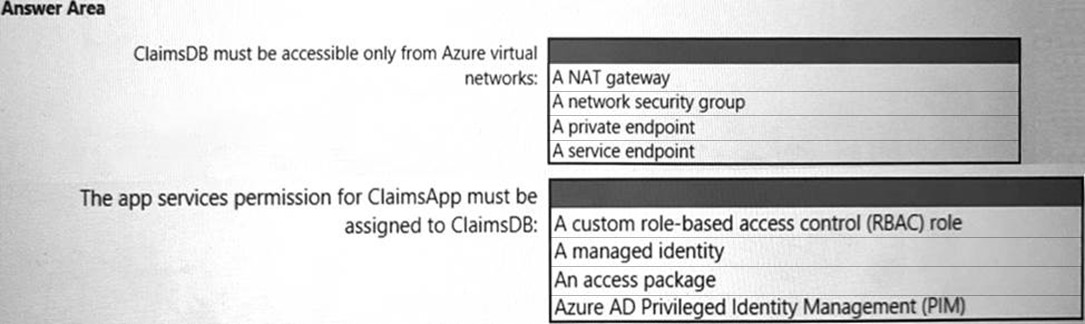
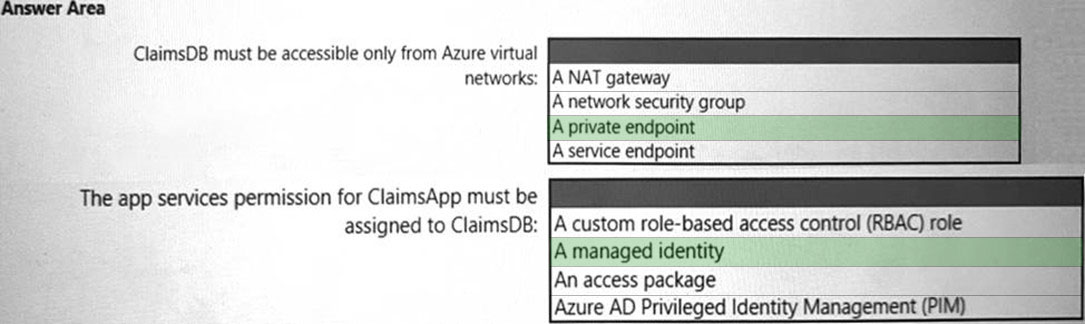
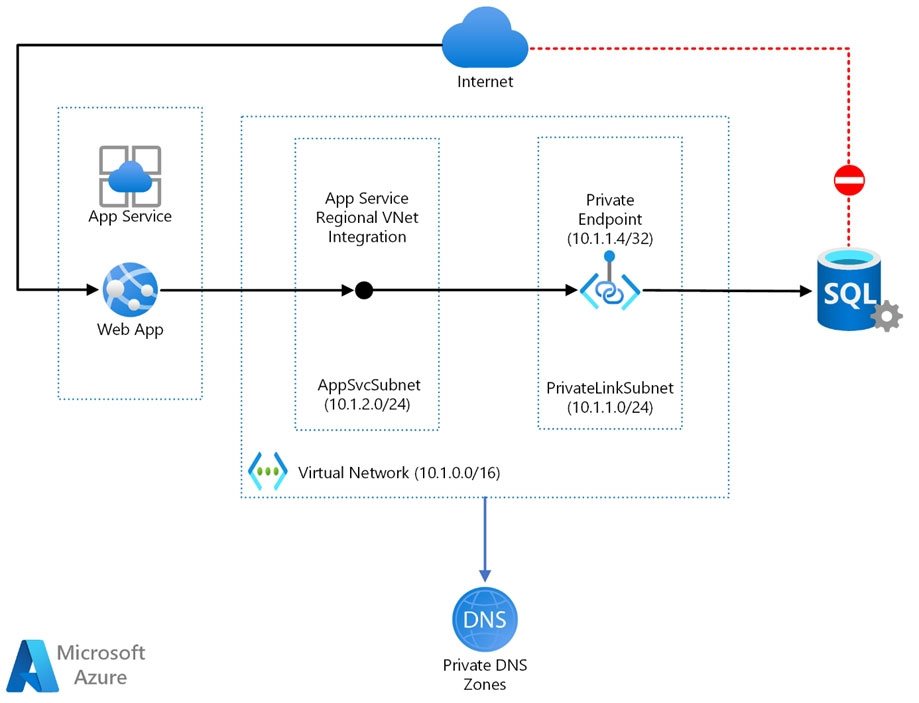
HOTSPOT - You need to recommend a solution to meet the requirements for connections to ClaimsDB. What should you recommend using for each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
For a Microsoft cloud environment, you are designing a security architecture based on the Microsoft Cloud Security Benchmark. What are three best practices for identity management based on the Azure Security Benchmark? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Manage application identities securely and automatically.
B. Manage the lifecycle of identities and entitlements.
C. Protect identity and authentication systems.
D. Enable threat detection for identity and access management.
E. Use a centralized identity and authentication system.
DRAG DROP - You have a hybrid Azure AD tenant that has pass-through authentication enabled. You are designing an identity security strategy. You need to minimize the impact of brute force password attacks and leaked credentials of hybrid identities. What should you include in the design? To answer, drag the appropriate features to the correct requirements. Each feature may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance. You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance. Solution: You recommend access restrictions that allow traffic from the Front Door service tags. Does this meet the goal?
A. Yes
B. No
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled. The Azure subscription contains 50 virtual machines. Each virtual machine runs different applications on Windows Server 2019. You need to recommend a solution to ensure that only authorized applications can run on the virtual machines. If an unauthorized application attempts to run or be installed, the application must be blocked automatically until an administrator authorizes the application. Which security control should you recommend?
A. app registrations in Azure Active Directory (Azure AD)
B. OAuth app policies in Microsoft Defender for Cloud Apps
C. Azure Security Benchmark compliance controls in Defender for Cloud
D. application control policies in Microsoft Defender for Endpoint
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled. The Azure subscription contains 50 virtual machines. Each virtual machine runs different applications on Windows Server 2019. You need to recommend a solution to ensure that only authorized applications can run on the virtual machines. If an unauthorized application attempts to run or be installed, the application must be blocked automatically until an administrator authorizes the application. Which security control should you recommend?
A. app registrations in Azure AD
B. Azure AD Conditional Access App Control policies
C. app discovery anomaly detection policies in Microsoft Defender for Cloud Apps
D. adaptive application controls in Defender for Cloud
You have an Azure subscription that contains several storage accounts. The storage accounts are accessed by legacy applications that are authenticated by using access keys. You need to recommend a solution to prevent new applications from obtaining the access keys of the storage accounts. The solution must minimize the impact on the legacy applications. What should you include in the recommendation?
A. Set the AllowSharedKeyAccess property to false.
B. Apply read-only locks on the storage accounts.
C. Set the AllowBlobPublicAccess property to false.
D. Configure automated key rotation.
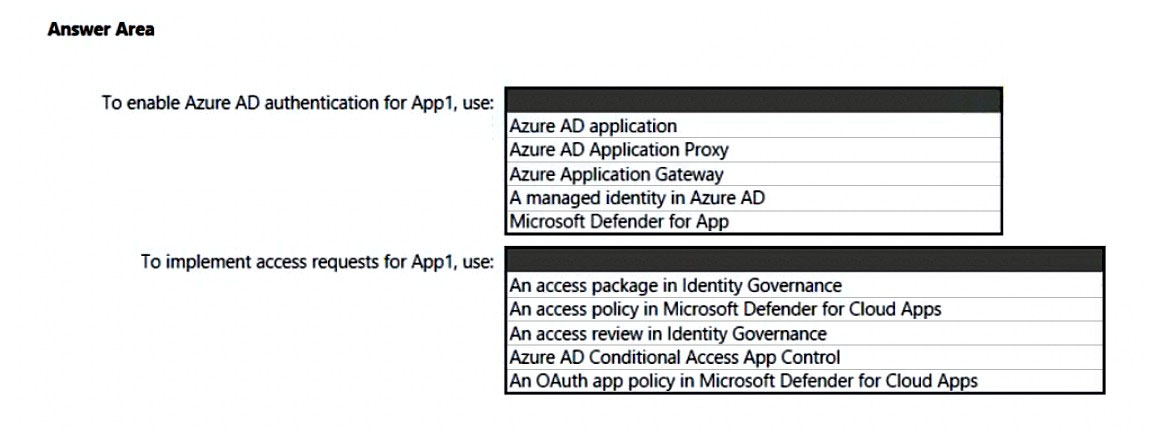
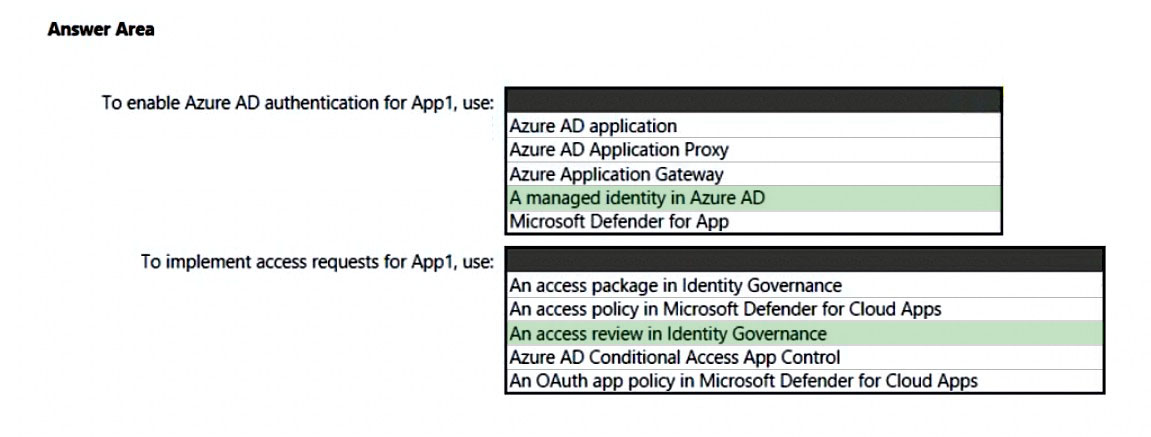
HOTSPOT - You are creating the security recommendations for an Azure App Service web app named App1. App1 has the following specifications: ✑ Users will request access to App1 through the My Apps portal. A human resources manager will approve the requests. ✑ Users will authenticate by using Azure Active Directory (Azure AD) user accounts. You need to recommend an access security architecture for App1. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
Your company plans to apply the Zero Trust Rapid Modernization Plan (RaMP) to its IT environment. You need to recommend the top three modernization areas to prioritize as part of the plan. Which three areas should you recommend based on RaMP? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. data, compliance, and governance
B. infrastructure and development
C. user access and productivity
D. operational technology (OT) and IoT
E. modern security operations
Your company has a hybrid cloud infrastructure. The company plans to hire several temporary employees within a brief period. The temporary employees will need to access applications and data on the company's on-premises network. The company's secutity policy prevents the use of personal devices for accessing company data and applications. You need to recommend a solution to provide the temporary employee with access to company resources. The solution must be able to scale on demand. What should you include in the recommendation?
A. Deploy Azure Virtual Desktop, Azure Active Directory (Azure AD) Conditional Access, and Microsoft Defender for Cloud Apps.
B. Redesign the VPN infrastructure by adopting a split tunnel configuration.
C. Deploy Microsoft Endpoint Manager and Azure Active Directory (Azure AD) Conditional Access.
D. Migrate the on-premises applications to cloud-based applications.
HOTSPOT - You have an Azure subscription and an on-premises datacenter. The datacenter contains 100 servers that run Windows Server. All the servers are backed up to a Recovery Services vault by using Azure Backup and the Microsoft Azure Recovery Services (MARS) agent. You need to design a recovery solution for ransomware attacks that encrypt the on-premises servers. The solution must follow Microsoft Security Best Practices and protect against the following risks: • A compromised administrator account used to delete the backups from Azure Backup before encrypting the servers • A compromised administrator account used to disable the backups on the MARS agent before encrypting the servers What should you use for each risk? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a customer that has a Microsoft 365 subscription and an Azure subscription. The customer has devices that run either Windows, iOS, Android, or macOS. The Windows devices are deployed on-premises and in Azure. You need to design a security solution to assess whether all the devices meet the customer's compliance rules. What should you include in the solution?
A. Microsoft Sentinel
B. Microsoft Purview Information Protection
C. Microsoft Intune
D. Microsoft Defender for Endpoint
A customer uses Azure to develop a mobile app that will be consumed by external users as shown in the following exhibit.You need to design an identity strategy for the app. The solution must meet the following requirements: ✑ Enable the usage of external IDs such as Google, Facebook, and Microsoft accounts. ✑ Use a customer identity store. ✑ Support fully customizable branding for the app. Which service should you recommend to complete the design?
A. Azure Active Directory (Azure AD) B2B
B. Azure Active Directory Domain Services (Azure AD DS)
C. Azure Active Directory (Azure AD) B2C
D. Azure AD Connect
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled. The Azure subscription contains 50 virtual machines. Each virtual machine runs different applications on Windows Server 2019. You need to recommend a solution to ensure that only authorized applications can run on the virtual machines. If an unauthorized application attempts to run or be installed, the application must be blocked automatically until an administrator authorizes the application. Which security control should you recommend?
A. OAuth app policies in Microsoft Defender for Cloud Apps
B. Azure Security Benchmark compliance controls in Defender for Cloud
C. application control policies in Microsoft Defender for Endpoint
D. app discovery anomaly detection policies in Microsoft Defender for Cloud Apps
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your on-premises network contains an e-commerce web app that was developed in Angular and Node,js. The web app uses a MongoDB database. You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone.You need to provide recommendations to secure the connection between the web app and the database. The solution must follow the Zero Trust model. Solution: You recommend implementing Azure Key Vault to store credentials. Does this meet the goal?
A. Yes
B. No
Your company finalizes the adoption of Azure and is implementing Microsoft Defender for Cloud. You receive the following recommendations in Defender for Cloud ✑ Access to storage accounts with firewall and virtual network configurations should be restricted. ✑ Storage accounts should restrict network access using virtual network rules. ✑ Storage account should use a private link connection. ✑ Storage account public access should be disallowed. You need to recommend a service to mitigate identified risks that relate to the recommendations. What should you recommend?
A. Azure Policy
B. Azure Network Watcher
C. Azure Storage Analytics
D. Microsoft Sentinel
Your company plans to provision blob storage by using an Azure Storage account. The blob storage will be accessible from 20 application servers on the internet. You need to recommend a solution to ensure that only the application servers can access the storage account. What should you recommend using to secure the blob storage?
A. managed rule sets in Azure Web Application Firewall (WAF) policies
B. inbound rules in network security groups (NSGs)
C. firewall rules for the storage account
D. inbound rules in Azure Firewall
E. service tags in network security groups (NSGs)
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled. The Azure subscription contains 50 virtual machines. Each virtual machine runs different applications on Windows Server 2019. You need to recommend a solution to ensure that only authorized applications can run on the virtual machines. If an unauthorized application attempts to run or be installed, the application must be blocked automatically until an administrator authorizes the application. Which security control should you recommend?
A. Azure AD Conditional Access App Control policies
B. Azure Security Benchmark compliance controls in Defender for Cloud
C. app protection policies in Microsoft Endpoint Manager
D. application control policies in Microsoft Defender for Endpoint
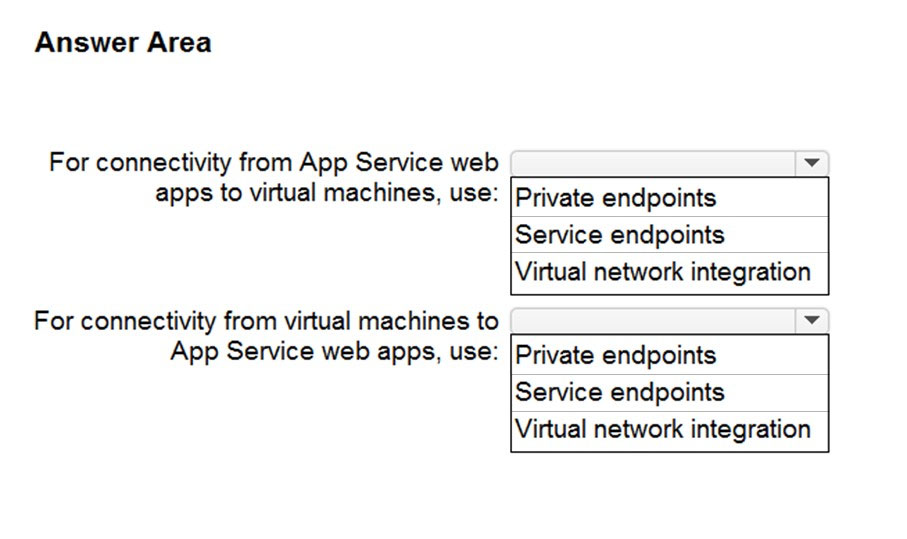
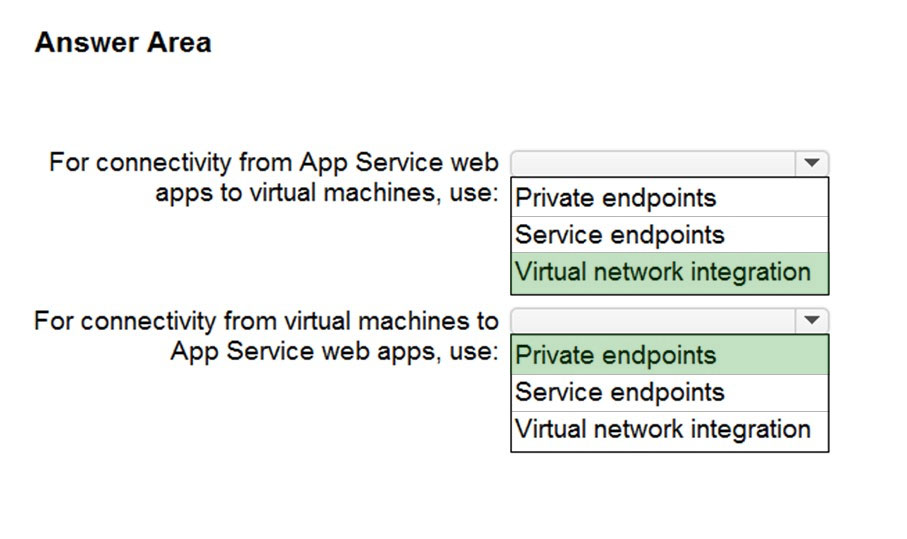
HOTSPOT - You need to recommend a strategy for App Service web app connectivity. The solution must meet the landing zone requirements. What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have an on-premises network and a Microsoft 365 subscription. You are designing a Zero Trust security strategy. Which two security controls should you include as part of the Zero Trust solution? Each correct answer presents part of the solution. NOTE: Each correct answer is worth one point.
A. Always allow connections from the on-premises network.
B. Disable passwordless sign-in for sensitive accounts.
C. Block sign-in attempts from unknown locations.
D. Block sign-in attempts from noncompliant devices.
You have an Azure subscription that contains virtual machines, storage accounts, and Azure SQL databases. All resources are backed up multiple times a day by using Azure Backup. You are developing a strategy to protect against ransomware attacks. You need to recommend which controls must be enabled to ensure that Azure Backup can be used to restore the resources in the event of a successful ransomware attack. Which two controls should you include in the recommendation? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Enable soft delete for backups.
B. Require PINs for critical operations.
C. Encrypt backups by using customer-managed keys (CMKs).
D. Perform offline backups to Azure Data Box.
E. Use Azure Monitor notifications when backup configurations change.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Azure subscription that has Microsoft Defender for Cloud enabled. You are evaluating the Azure Security Benchmark V3 report. In the Secure management ports controls, you discover that you have 0 out of a potential 8 points. You need to recommend configurations to increase the score of the Secure management ports controls. Solution: You recommend enabling just-in-time (JIT) VM access on all virtual machines. Does this meet the goal?
A. Yes
B. No
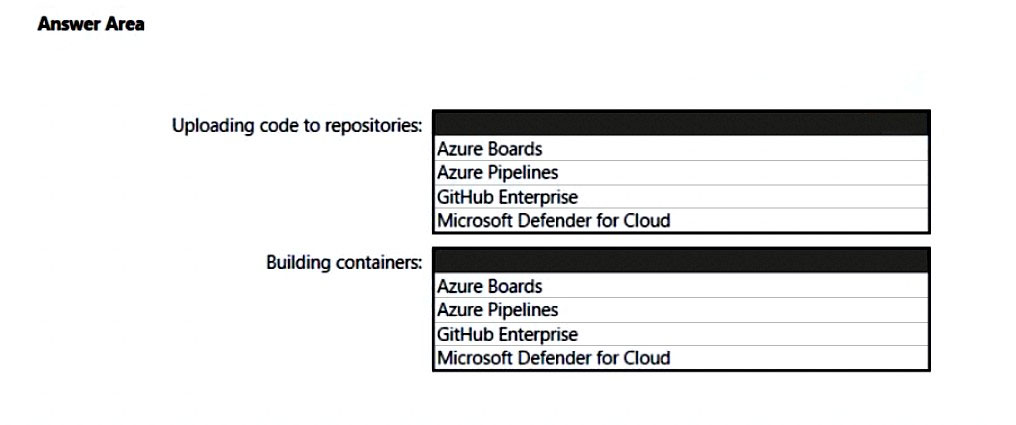
HOTSPOT - Your company has an Azure App Service plan that is used to deploy containerized web apps. You are designing a secure DevOps strategy for deploying the web apps to the App Service plan. You need to recommend a strategy to integrate code scanning tools into a secure software development lifecycle. The code must be scanned during the following two phases: ✑ Uploading the code to repositories ✑ Building containers Where should you integrate code scanning for each phase? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
Your company has a third-party security information and event management (SIEM) solution that uses Splunk and Microsoft Sentinel. You plan to integrate Microsoft Sentinel with Splunk. You need to recommend a solution to send security events from Microsoft Sentinel to Splunk. What should you include in the recommendation?
A. a Microsoft Sentinel data connector
B. Azure Event Hubs
C. a Microsoft Sentinel workbook
D. Azure Data Factory
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Azure subscription that has Microsoft Defender for Cloud enabled. You are evaluating the Azure Security Benchmark V3 report. In the Secure management ports controls, you discover that you have 0 out of a potential 8 points. You need to recommend configurations to increase the score of the Secure management ports controls. Solution: You recommend enabling adaptive network hardening. Does this meet the goal?
A. Yes
B. No
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled. The Azure subscription contains 50 virtual machines. Each virtual machine runs different applications on Windows Server 2019. You need to recommend a solution to ensure that only authorized applications can run on the virtual machines. If an unauthorized application attempts to run or be installed, the application must be blocked automatically until an administrator authorizes the application. Which security control should you recommend?
A. adaptive application controls in Defender for Cloud
B. app protection policies in Microsoft Endpoint Manager
C. OAuth app policies in Microsoft Defender for Cloud Apps
D. Azure Active Directory (Azure AD) Conditional Access App Control policies
Free Access Full SC-100 Practice Exam Free
Looking for additional practice? Click here to access a full set of SC-100 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your SC-100 certification journey!