SC-100 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your SC-100 certification exam? Start your preparation the smart way with our SC-100 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for SC-100 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our SC-100 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
Your company has an Azure subscription that has enhanced security enabled for Microsoft Defender for Cloud. The company signs a contract with the United States government. You need to review the current subscription for NIST 800-53 compliance. What should you do first?
A. From Defender for Cloud, enable Defender for Cloud plans.
B. From Azure Policy, assign a built-in initiative that has a scope of the subscription.
C. From Microsoft Defender for Cloud Apps, create an access policy for cloud applications.
D. From Azure Policy, assign a built-in policy definition that has a scope of the subscription.
You have a Microsoft 365 tenant. Your company uses a third-party software as a service (SaaS) app named App1 that is integrated with an Azure AD tenant. You need to design a security strategy to meet the following requirements: • Users must be able to request access to App1 by using a self-service request. • When users request access to App1, they must be prompted to provide additional information about their request. • Every three months, managers must verify that the users still require access to App1. What should you include in the design?
A. Microsoft Entra Identity Governance
B. connected apps in Microsoft Defender for Cloud Apps
C. access policies in Microsoft Defender for Cloud Apps
D. Azure AD Application Proxy
HOTSPOT - You have an Azure subscription and an on-premises datacenter. The datacenter contains 100 servers that run Windows Server. All the servers are backed up to a Recovery Services vault by using Azure Backup and the Microsoft Azure Recovery Services (MARS) agent. You need to design a recovery solution for ransomware attacks that encrypt the on-premises servers. The solution must follow Microsoft Security Best Practices and protect against the following risks: • A compromised administrator account used to delete the backups from Azure Backup before encrypting the servers • A compromised administrator account used to disable the backups on the MARS agent before encrypting the servers What should you use for each risk? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You need to recommend a solution for securing the landing zones. The solution must meet the landing zone requirements and the business requirements. What should you configure for each landing zone?
A. an ExpressRoute gateway
B. Microsoft Defender for Cloud
C. an Azure Private DNS zone
D. Azure DDoS Protection Standard
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You have an Amazon Web Services (AWS) implementation. You plan to extend the Azure security strategy to the AWS implementation. The solution will NOT use Azure Arc. Which three services can you use to provide security for the AWS resources? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Microsoft Defender for Containers
B. Microsoft Defender for servers
C. Azure Active Directory (Azure AD) Conditional Access
D. Azure Active Directory (Azure AD) Privileged Identity Management (PIM)
E. Azure Policy
You are designing a ransomware response plan that follows Microsoft Security Best Practices. You need to recommend a solution to limit the scope of damage of ransomware attacks without being locked out. What should you include in the recommendation?
A. device compliance policies
B. Privileged Access Workstations (PAWs)
C. Customer Lockbox for Microsoft Azure
D. emergency access accounts
You have a Microsoft 365 E5 subscription. You need to recommend a solution to add a watermark to email attachments that contain sensitive data. What should you include in the recommendation?
A. Microsoft Defender for Cloud Apps
B. Microsoft Information Protection
C. insider risk management
D. Azure Purview
You have a Microsoft 365 subscription. You need to design a solution to block file downloads from Microsoft SharePoint Online by authenticated users on unmanaged devices. Which two services should you include in the solution? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Azure AD Conditional Access
B. Azure Data Catalog
C. Microsoft Purview Information Protection
D. Azure AD Application Proxy
E. Microsoft Defender for Cloud Apps
You have an Azure subscription that contains virtual machines, storage accounts, and Azure SQL databases. All resources are backed up multiple times a day by using Azure Backup. You are developing a strategy to protect against ransomware attacks. You need to recommend which controls must be enabled to ensure that Azure Backup can be used to restore the resources in the event of a successful ransomware attack. Which two controls should you include in the recommendation? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Enable soft delete for backups.
B. Require PINs for critical operations.
C. Encrypt backups by using customer-managed keys (CMKs).
D. Perform offline backups to Azure Data Box.
E. Use Azure Monitor notifications when backup configurations change.
HOTSPOT - You have an Azure SQL database named DB1 that contains customer information. A team of database administrators has full access to DB1. To address customer inquiries, operators in the customer service department use a custom web app named App1 to view the customer information. You need to design a security strategy for DB1. The solution must meet the following requirement: • When the database administrators access DB1 by using SQL management tools, they must be prevented from viewing the content of the CreditCard attribute of each customer record. • When the operators view customer records in App1, they must view only the last four digits of the CreditCard attribute. What should you include in the design? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT - Your company plans to follow DevSecOps best practices of the Microsoft Cloud Adoption Framework for Azure to integrate DevSecOps processes into continuous integration and continuous deployment (CI/CD) DevOps pipelines. You need to recommend which security-related tasks to integrate into each stage of the DevOps pipelines. What should recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure subscription that has Microsoft Defender for Cloud enabled. Suspicious authentication activity alerts have been appearing in the Workload protections dashboard. You need to recommend a solution to evaluate and remediate the alerts by using workflow automation. The solution must minimize development effort. What should you include in the recommendation?
A. Azure Monitor webhooks
B. Azure Event Hubs
C. Azure Functions apps
D. Azure Logics Apps
Your company has a third-party security information and event management (SIEM) solution that uses Splunk and Microsoft Sentinel. You plan to integrate Microsoft Sentinel with Splunk. You need to recommend a solution to send security events from Microsoft Sentinel to Splunk. What should you include in the recommendation?
A. a Microsoft Sentinel data connector
B. Azure Event Hubs
C. a Microsoft Sentinel workbook
D. Azure Data Factory
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Azure subscription that has Microsoft Defender for Cloud enabled. You are evaluating the Azure Security Benchmark V3 report. In the Secure management ports controls, you discover that you have 0 out of a potential 8 points. You need to recommend configurations to increase the score of the Secure management ports controls. Solution: You recommend enabling adaptive network hardening. Does this meet the goal?
A. Yes
B. No
Your company has an Azure subscription that uses Microsoft Defender for Cloud. The company signs a contract with the United States government. You need to review the current subscription for NIST 800-53 compliance. What should you do first?
A. From Microsoft Sentinel, configure the Microsoft Defender for Cloud data connector.
B. From Microsoft Defender for Cloud Apps, create an access policy for cloud applications.
C. From Defender for Cloud, enable Defender for Cloud plans.
D. From Defender for Cloud, add a regulatory compliance standard.
Your company has a hybrid cloud infrastructure that contains an on-premises Active Directory Domain Services (AD DS) forest, a Microsoft 365 subscription, and an Azure subscription. The company's on-premises network contains internal web apps that use Kerberos authentication. Currently, the web apps are accessible only from the network. You have remote users who have personal devices that run Windows 11. You need to recommend a solution to provide the remote users with the ability to access the web apps. The solution must meet the following requirements: ✑ Prevent the remote users from accessing any other resources on the network. ✑ Support Azure Active Directory (Azure AD) Conditional Access. ✑ Simplify the end-user experience. What should you include in the recommendation?
A. Azure AD Application Proxy
B. web content filtering in Microsoft Defender for Endpoint
C. Microsoft Tunnel
D. Azure Virtual WAN
Your company is developing an invoicing application that will use Azure Active Directory (Azure AD) B2C. The application will be deployed as an App Service web app. You need to recommend a solution to the application development team to secure the application from identity-related attacks. Which two configurations should you recommend? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Azure AD workbooks to monitor risk detections
B. Azure AD Conditional Access integration with user flows and custom policies
C. smart account lockout in Azure AD B2C
D. access packages in Identity Governance
E. custom resource owner password credentials (ROPC) flows in Azure AD B2C
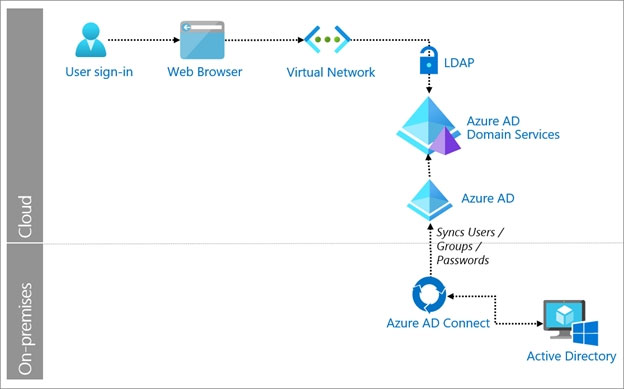
You have an on-premises network that has several legacy applications. The applications perform LDAP queries against an existing directory service. You are migrating the on-premises infrastructure to a cloud-only infrastructure. You need to recommend an identity solution for the infrastructure that supports the legacy applications. The solution must minimize the administrative effort to maintain the infrastructure. Which identity service should you include in the recommendation?
A. Azure Active Directory (Azure AD) B2C
B. Azure Active Directory Domain Services (Azure AD DS)
C. Azure Active Directory (Azure AD)
D. Active Directory Domain Services (AD DS)
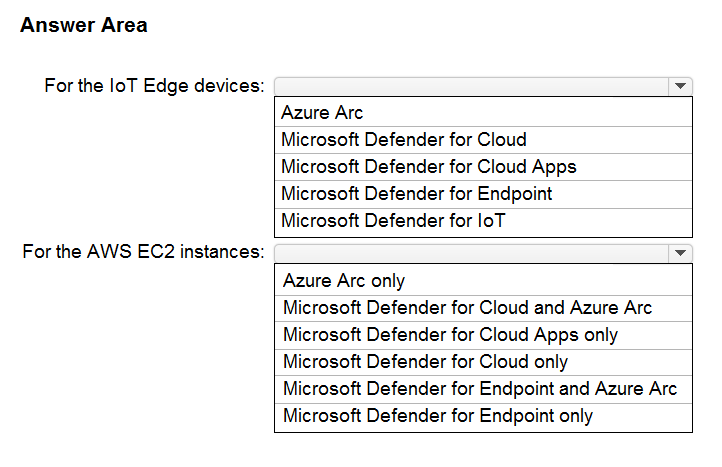
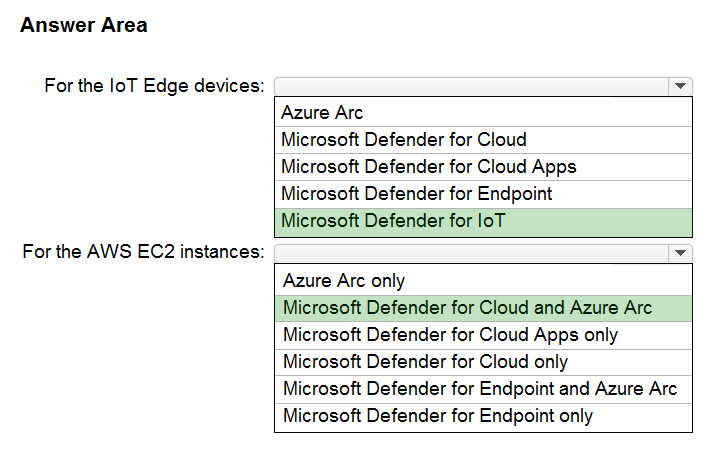
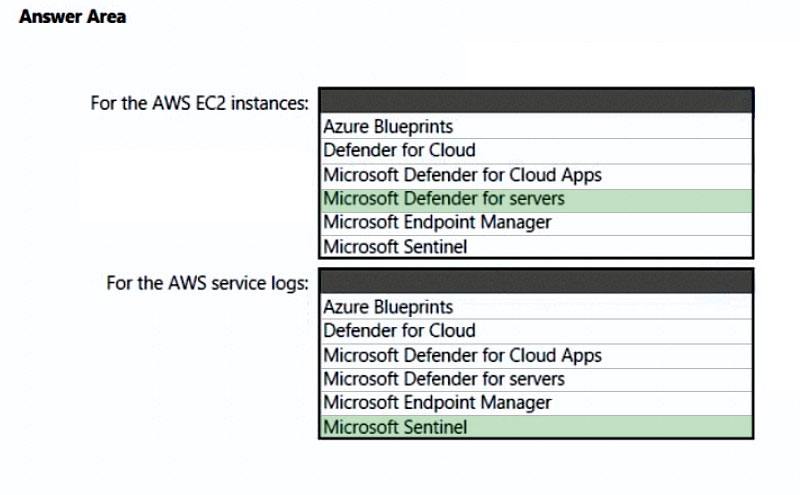
HOTSPOT - Your company has a multi-cloud environment that contains a Microsoft 365 subscription, an Azure subscription, and Amazon Web Services (AWS) implementation. You need to recommend a security posture management solution for the following components: ✑ Azure IoT Edge devices AWS EC2 instances -Which services should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - For a Microsoft cloud environment, you are designing a security architecture based on the Microsoft Cybersecurity Reference Architectures (MCRA). You need to protect against the following external threats of an attack chain: • An attacker attempts to exfiltrate data to external websites. • An attacker attempts lateral movement across domain-joined computers. What should you include in the recommendation for each threat? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
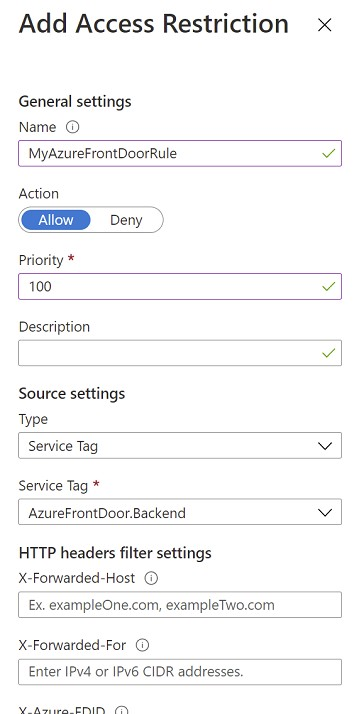
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance. You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance. Solution: You recommend access restrictions that allow traffic from the Front Door service tags. Does this meet the goal?
A. Yes
B. No
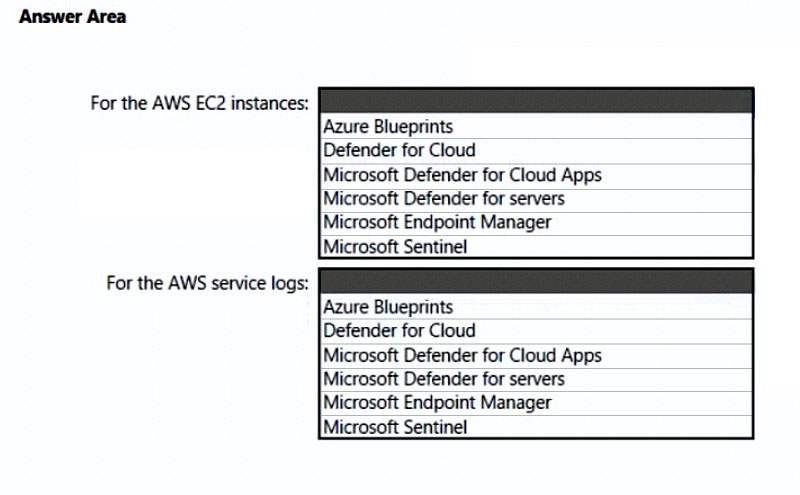
HOTSPOT - You need to recommend a solution to meet the AWS requirements. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You are designing a security operations strategy based on the Zero Trust framework. You need to minimize the operational load on Tier 1 Microsoft Security Operations Center (SOC) analysts. What should you do?
A. Enable built-in compliance policies in Azure Policy.
B. Enable self-healing in Microsoft 365 Defender.
C. Automate data classification.
D. Create hunting queries in Microsoft 365 Defender.
You are creating an application lifecycle management process based on the Microsoft Security Development Lifecycle (SDL). You need to recommend a security standard for onboarding applications to Azure. The standard will include recommendations for application design, development, and deployment. What should you include during the application design phase?
A. software decomposition by using Microsoft Visual Studio Enterprise
B. dynamic application security testing (DAST) by using Veracode
C. threat modeling by using the Microsoft Threat Modeling Tool
D. static application security testing (SAST) by using SonarQube
Your company plans to apply the Zero Trust Rapid Modernization Plan (RaMP) to its IT environment. You need to recommend the top three modernization areas to prioritize as part of the plan. Which three areas should you recommend based on RaMP? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. data, compliance, and governance
B. infrastructure and development
C. user access and productivity
D. operational technology (OT) and IoT
E. modern security operations
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your on-premises network contains an e-commerce web app that was developed in Angular and Node,js. The web app uses a MongoDB database. You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone.You need to provide recommendations to secure the connection between the web app and the database. The solution must follow the Zero Trust model. Solution: You recommend creating private endpoints for the web app and the database layer. Does this meet the goal?
A. Yes
B. No
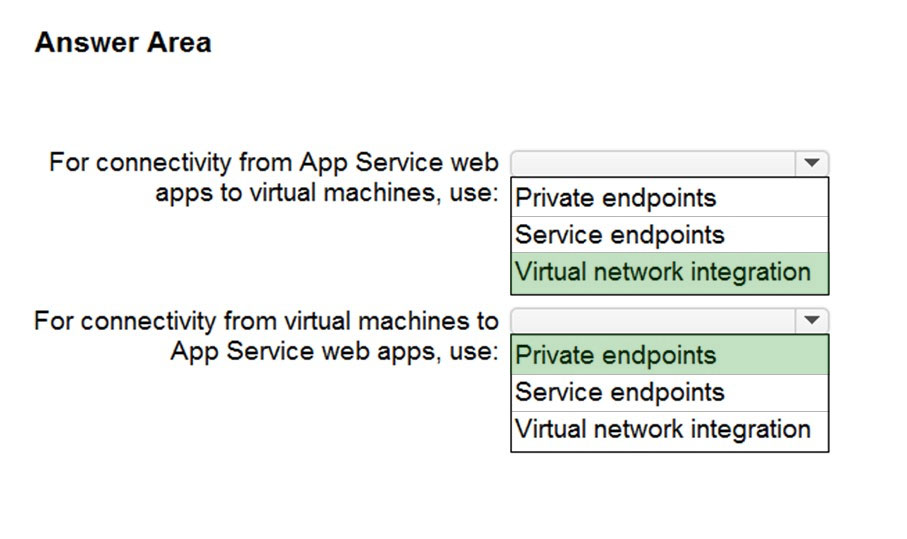
HOTSPOT - You need to recommend a strategy for App Service web app connectivity. The solution must meet the landing zone requirements. What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance. You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance. Solution: You recommend access restrictions that allow traffic from the Front Door service tags. Does this meet the goal?
A. Yes
B. No
You receive a security alert in Microsoft Defender for Cloud as shown in the exhibit. (Click the Exhibit tab.)After remediating the threat, which policy definition should you assign to prevent the threat from reoccurring?
A. Storage account public access should be disallowed
B. Azure Key Vault Managed HSM should have purge protection enabled
C. Storage accounts should prevent shared key access
D. Storage account keys should not be expired
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled. The Azure subscription contains 50 virtual machines. Each virtual machine runs different applications on Windows Server 2019. You need to recommend a solution to ensure that only authorized applications can run on the virtual machines. If an unauthorized application attempts to run or be installed, the application must be blocked automatically until an administrator authorizes the application. Which security control should you recommend?
A. Azure AD Conditional Access App Control policies
B. Azure Security Benchmark compliance controls in Defender for Cloud
C. app protection policies in Microsoft Endpoint Manager
D. application control policies in Microsoft Defender for Endpoint
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your on-premises network contains an e-commerce web app that was developed in Angular and Node,js. The web app uses a MongoDB database. You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone.You need to provide recommendations to secure the connection between the web app and the database. The solution must follow the Zero Trust model. Solution: You recommend implementing Azure Key Vault to store credentials. Does this meet the goal?
A. Yes
B. No
You are designing the security standards for containerized applications onboarded to Azure. You are evaluating the use of Microsoft Defender for Containers. In which two environments can you use Defender for Containers to scan for known vulnerabilities? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Linux containers deployed to Azure Container Instances
B. Windows containers deployed to Azure Kubernetes Service (AKS)
C. Windows containers deployed to Azure Container Registry
D. Linux containers deployed to Azure Container Registry
E. Linux containers deployed to Azure Kubernetes Service (AKS)
You have a Microsoft 365 tenant. Your company uses a third-party software as a service (SaaS) app named App1. App1 supports authenticating users by using Azure AD credentials. You need to recommend a solution to enable users to authenticate to App1 by using their Azure AD credentials. What should you include in the recommendation?
A. Azure AD Application Proxy
B. Azure AD B2C
C. an Azure AD enterprise application
D. a relying party trust in Active Directory Federation Services (AD FS)
You need to recommend a solution to meet the security requirements for the InfraSec group. What should you use to delegate the access?
A. a subscription
B. a custom role-based access control (RBAC) role
C. a resource group
D. a management group
Your company uses Azure Pipelines and Azure Repos to implement continuous integration and continuous deployment (CI/CD) workflows for the deployment of applications to Azure. You are updating the deployment process to align with DevSecOps controls guidance in the Microsoft Cloud Adoption Framework for Azure. You need to recommend a solution to ensure that all code changes are submitted by using pull requests before being deployed by the CI/CD workflow. What should you include in the recommendation?
A. custom roles in Azure Pipelines
B. branch policies in Azure Repos
C. Azure policies
D. custom Azure roles
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled. The Azure subscription contains 50 virtual machines. Each virtual machine runs different applications on Windows Server 2019. You need to recommend a solution to ensure that only authorized applications can run on the virtual machines. If an unauthorized application attempts to run or be installed, the application must be blocked automatically until an administrator authorizes the application. Which security control should you recommend?
A. app discovery anomaly detection policies in Microsoft Defender for Cloud Apps
B. Azure Security Benchmark compliance controls in Defender for Cloud
C. app registrations in Azure AD
D. application control policies in Microsoft Defender for Endpoint
You are designing security for an Azure landing zone. Your company identifies the following compliance and privacy requirements: ✑ Encrypt cardholder data by using encryption keys managed by the company. ✑ Encrypt insurance claim files by using encryption keys hosted on-premises. Which two configurations meet the compliance and privacy requirements? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Store the cardholder data in an Azure SQL database that is encrypted by using Microsoft-managed keys.
B. Store the insurance claim data in Azure Blob storage encrypted by using customer-provided keys.
C. Store the cardholder data in an Azure SQL database that is encrypted by using keys stored in Azure Key Vault Managed HSM.
D. Store the insurance claim data in Azure Files encrypted by using Azure Key Vault Managed HSM.
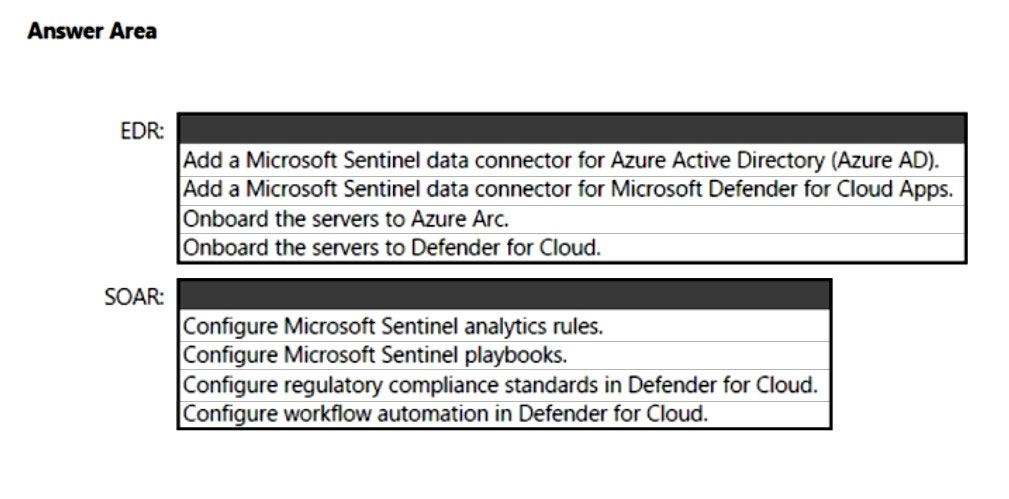
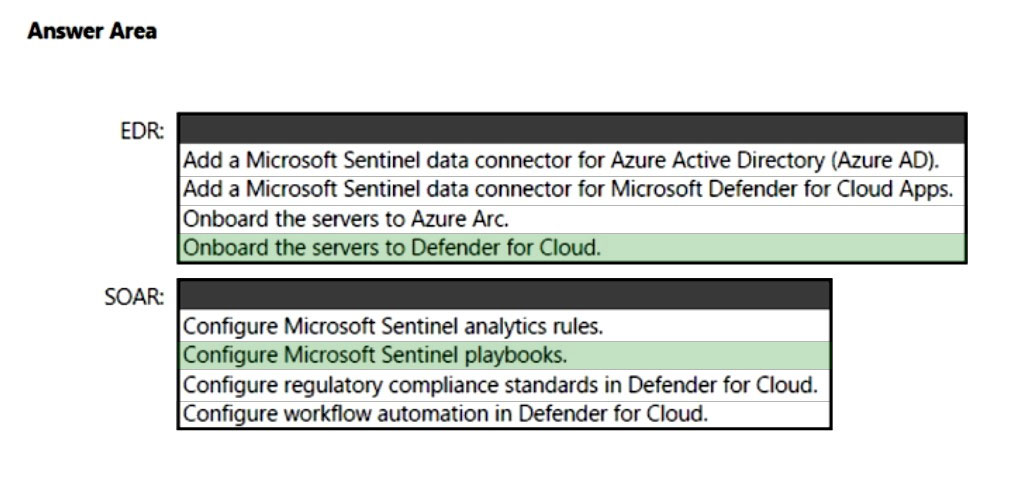
HOTSPOT - You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled. The Azure subscription contains a Microsoft Sentinel workspace. Microsoft Sentinel data connectors are configured for Microsoft 365, Microsoft 365 Defender, Defender for Cloud, and Azure. You plan to deploy Azure virtual machines that will run Windows Server. You need to enable extended detection and response (EDR) and security orchestration, automation, and response (SOAR) capabilities for Microsoft Sentinel. How should you recommend enabling each capability? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
Your company has an Azure subscription that has enhanced security enabled for Microsoft Defender for Cloud. The company signs a contract with the United States government. You need to review the current subscription for NIST 800-53 compliance. What should you do first?
A. From Defender for Cloud, enable Defender for Cloud plans.
B. From Azure Policy, assign a built-in initiative that has a scope of the subscription.
C. From Defender for Cloud, review the secure score recommendations.
D. From Microsoft Defender for Cloud Apps, create an access policy for cloud applications.
Your company plans to deploy several Azure App Service web apps. The web apps will be deployed to the West Europe Azure region. The web apps will be accessed only by customers in Europe and the United States. You need to recommend a solution to prevent malicious bots from scanning the web apps for vulnerabilities. The solution must minimize the attack surface. What should you include in the recommendation?
A. Azure Firewall Premium
B. Azure Traffic Manager and application security groups
C. Azure Application Gateway Web Application Firewall (WAF)
D. network security groups (NSGs)
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You need to enforce ISO 27001:2013 standards for the subscription. The solution must ensure that noncompliant resources are remediated automatically. What should you use?
A. Azure Policy
B. Azure Blueprints
C. the regulatory compliance dashboard in Defender for Cloud
D. Azure role-based access control (Azure RBAC)
You need to recommend a solution to scan the application code. The solution must meet the application development requirements. What should you include in the recommendation?
A. GitHub Advanced Security
B. Azure Key Vault
C. Azure DevTest Labs
D. Application Insights in Azure Monitor
You have an on-premises datacenter and an Azure Kubernetes Service (AKS) cluster named AKS1. You need to restrict internet access to the public endpoint of AKS1. The solution must ensure that AKS1 can be accessed only from the public IP addresses associated with the on-premises datacenter. What should you use?
A. a private endpoint
B. a network security group (NSG)
C. a service endpoint
D. an authorized IP range
You use Azure Pipelines with Azure Repos to implement continuous integration and continuous deployment (CI/CD) workflows for the deployment of applications to Azure. You need to recommend what to include in dynamic application security testing (DAST) based on the principles of the Microsoft Cloud Adoption Framework for Azure. What should you recommend?
A. unit testing
B. penetration testing
C. dependency checks
D. threat modeling
Your company is developing a modern application that will un as an Azure App Service web app. You plan to perform threat modeling to identity potential security issues by using the Microsoft Threat Modeling Tool. Which type of diagram should you create?
A. system flow
B. data flow
C. process flow
D. network flow
HOTSPOT - Your company wants to optimize using Azure to protect its resources from ransomware. You need to recommend which capabilities of Azure Backup and Azure Storage provide the strongest protection against ransomware attacks. The solution must follow Microsoft Security Best Practices. What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You need to design a strategy for securing the SharePoint Online and Exchange Online data. The solution must meet the application security requirements. Which two services should you leverage in the strategy? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Azure AD Conditional Access
B. access reviews in Azure AD
C. Microsoft Defender for Cloud
D. Microsoft Defender for Cloud Apps
E. Microsoft Defender for Endpoint
HOTSPOT - Your network contains an on-premises Active Directory Domain Services (AD DS) domain. The domain contains a server that runs Windows Server and hosts shared folders. The domain syncs with Azure AD by using Azure AD Connect. Azure AD Connect has group writeback enabled. You have a Microsoft 365 subscription that uses Microsoft SharePoint Online. You have multiple project teams. Each team has an AD DS group that syncs with Azure AD. Each group has permissions to a unique SharePoint Online site and a Windows Server shared folder for its project. Users routinely move between project teams. You need to recommend an Azure AD Identity Governance solution that meets the following requirements: • Project managers must verify that their project group contains only the current members of their project team. • The members of each project team must only have access to the resources of the project to which they are assigned. • Users must be removed from a project group automatically if the project manager has NOT verified the group's membership for 30 days. • Administrative effort must be minimized. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
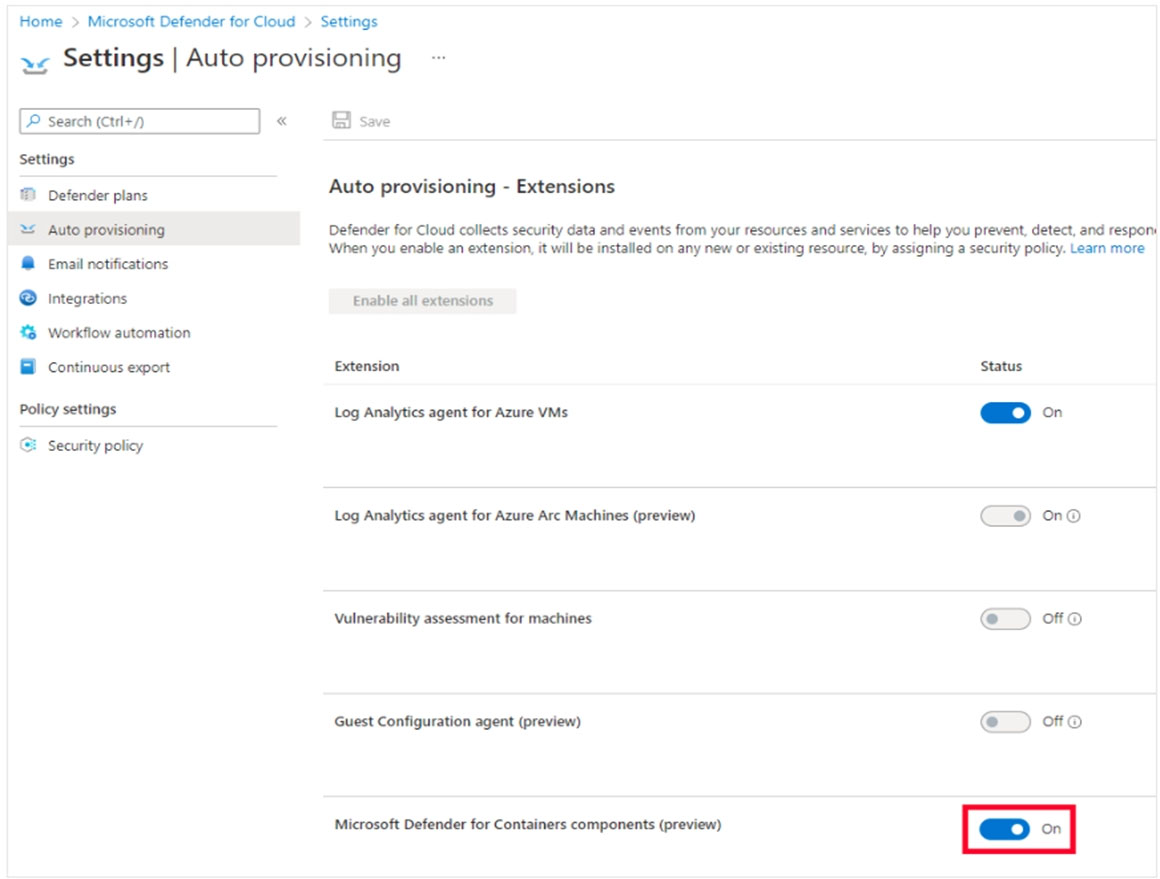
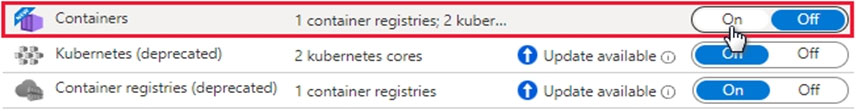
A customer is deploying Docker images to 10 Azure Kubernetes Service (AKS) resources across four Azure subscriptions. You are evaluating the security posture of the customer. You discover that the AKS resources are excluded from the secure score recommendations. You need to produce accurate recommendations and update the secure score. Which two actions should you recommend in Microsoft Defender for Cloud? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Enable Defender plans.
B. Configure auto provisioning.
C. Add a workflow automation.
D. Assign regulatory compliance policies.
E. Review the inventory.
Your company has devices that run either Windows 10, Windows 11, or Windows Server. You are in the process of improving the security posture of the devices. You plan to use security baselines from the Microsoft Security Compliance Toolkit. What should you recommend using to compare the baselines to the current device configurations?
A. Microsoft Intune
B. Local Group Policy Object (LGPO)
C. Windows Autopilot
D. Policy Analyzer
Access Full SC-100 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete SC-100 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our SC-100 mock test free today—and take a major step toward exam success!