PCNSE Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the PCNSE exam? Start with our PCNSE Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a PCNSE practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free PCNSE practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
Which administrative authentication method supports authorization by an external service?
A. Certificates
B. LDAP
C. RADIUS
D. SSH keys
Which three settings are defined within the Templates object of Panorama? (Choose three.)
A. Setup
B. Virtual Routers
C. Interfaces
D. Security
E. Application Override
A firewall just submitted a file to WildFire for analysis. Assume a 5-minute window for analysis. The firewall is configured to check for verdicts every 5 minutes. How quickly will the firewall receive back a verdict?
A. More than 15 minutes
B. 5 minutes
C. 10 to 15 minutes
D. 5 to 10 minutes
What best describes the HA Promotion Hold Time?
A. the time that the passive firewall will wait before taking over as the active firewall after communications with the HA peer have been lost
B. the time that is recommended to avoid a failover when both firewalls experience the same link/path monitor failure simultaneously
C. the time that is recommended to avoid an HA failover due to the occasional flapping of neighboring devices
D. the time that a passive firewall with a low device priority will wait before taking over as the active firewall it the firewall is operational again
Where can a service route be configured for a specific destination IP?
A. Use Network > Virtual Routers, select the Virtual Router > Static Routes > IPv4
B. Use Device > Setup > Services > Services
C. Use Device > Setup > Services > Service Route Configuration > Customize > IPv4
D. Use Device > Setup > Services > Service Route Configuration > Customize > Destination
Before an administrator of a VM-500 can enable DoS and zone protection, what actions need to be taken?
A. Create a zone protection profile with flood protection configured to defend an entire egress zone against SYN, ICMP, ICMPv6, UDP, and other IP flood attacks.
B. Add a WildFire subscription to activate DoS and zone protection features.
C. Replace the hardware firewall, because DoS and zone protection are not available with VM-Series systems.
D. Measure and monitor the CPU consumption of the firewall data plane to ensure that each firewall is properly sized to support DoS and zone protection.
An administrator wants to upgrade a firewall HA pair to PAN-OS 10.1. The firewalls are currently running PAN-OS 8.1.17. Which upgrade path maintains synchronization of the HA session (and prevents network outage)?
A. Upgrade directly to the target major version.
B. Upgrade the HA pair to a base image.
C. Upgrade one major version at a time.
D. Upgrade two major versions at a time.
Which source is the most reliable for collecting User-ID user mapping?
A. Microsoft Active Directory
B. Microsoft Exchange
C. GlobalProtect
D. Syslog Listener
The profile is configured to provide granular defense against targeted flood attacks for specific critical systems that are accessed by users from the internet. Which profile is the engineer configuring?
A. Vulnerability Protection
B. DoS Protection
C. Packet Buffer Protection
D. Zone Protection
An administrator needs to upgrade an NGFW to the most current version of PAN-OSֲ® software. The following is occurring: ✑ Firewall has internet connectivity through e 1/1. ✑ Default security rules and security rules allowing all SSL and web-browsing traffic to and from any zone. ✑ Service route is configured, sourcing update traffic from e1/1. ✑ A communication error appears in the System logs when updates are performed. ✑ Download does not complete. What must be configured to enable the firewall to download the current version of PAN-OS software?
A. Static route pointing application PaloAlto-updates to the update servers
B. Security policy rule allowing PaloAlto-updates as the application
C. Scheduler for timed downloads of PAN-OS software
D. DNS settings for the firewall to use for resolution
What is the best definition of the Heartbeat Interval?
A. the interval during which the firewall will remain active following a link monitor failure
B. the frequency at which the HA peers exchange ping
C. the interval in milliseconds between hello packets
D. the frequency at which the HA peers check link or path availability
A firewall administrator has been tasked with ensuring that all Panorama-managed firewalls forward traffic logs to Panorama. In which section is this configured?
A. Templates > Device > Log Settings
B. Device Groups > Objects > Log Forwarding
C. Monitor > Logs > Traffic
D. Panorama > Managed Devices
Users have reported an issue when they are trying to access a server on your network. The requests aren't taking the expected route. You discover that there are two different static routes on the firewall for the server. What is used to determine which route has priority?
A. The first route installed
B. Bidirectional Forwarding Detection
C. The route with the lowest administrative distance
D. The route with the highest administrative distance
An administrator is building Security rules within a device group to block traffic to and from malicious locations. How should those rules be configured to ensure that they are evaluated with a high priority?
A. Create the appropriate rules with a Block action and apply them at the top of the local firewall Security rules
B. Create the appropriate rules with a Block action and apply them at the top of the Security Pre-Rules
C. Create the appropriate rules with a Block action and apply them at the top of the Security Post-Rules
D. Create the appropriate rules with a Block action and apply them at the top of the Default Rules
A network security engineer must implement Quality of Service policies to ensure specific levels of delivery guarantees for various applications in the environment. They want to ensure that they know as much as they can about QoS before deploying. Which statement about the QoS feature is correct?
A. QoS can be used in conjunction with SSL decryption
B. QoS is only supported on hardware firewalls
C. QoS is only supported on firewalls that have a single virtual system configured
D. QoS can be used on firewalls with multiple virtual systems configured
Based on the screenshots above, and with no configuration inside the Template Stack itself, what access will the device permit on its Management port?
A. The firewall will allow HTTP Telnet, HTTPS, SSH, and Ping from IP addresses defined as $permitted-subnet-1.
B. The firewall will allow HTTP Telnet, HTTPS, SSH, and Ping from IP addresses defined as $permitted-subnet-2.
C. The firewall will allow HTTP, Telnet, SNMP, HTTPS, SSH and Ping from IP addresses defined as $permitted-subnet-1 and $permitted-subnet-2.
D. The firewall will allow HTTP, Telnet, HTTPS, SSH, and Ping from IP addresses defined as $permitted-subnet-1 and $permitted-subnet-2.
Refer to the exhibit. A web server in the DMZ is being mapped to a public address through DNAT.Which Security policy rule will allow traffic to flow to the web server?
A. Untrust (any) to Untrust (10.1.1.100), web browsing ג€” Allow
B. Untrust (any) to Untrust (1.1.1.100), web browsing ג€” Allow
C. Untrust (any) to DMZ (1.1.1.100), web browsing ג€” Allow
D. Untrust (any) to DMZ (10.1.1.100), web browsing ג€” Allow
Decrypted packets from the website https://www.microsoft.com will appear as which application and service within the Traffic log?
A. web-browsing and 443
B. SSL and 80
C. SSL and 443
D. web-browsing and 80
An engineer is reviewing the following high availability (HA) settings to understand a recent HA failover event.Which timer determines the frequency between packets sent to verify that the HA functionality on the other HA firewall is operational?
A. Hello Interval
B. Monitor Fail Hold Up Time
C. Heartbeat Interval
D. Promotion Hold Time
An organization has recently migrated its infrastructure and configuration to NGFWs, for which Panorama manages the devices. The organization is coming from a L2-L4 firewall vendor, but wants to use App-ID while identifying policies that are no longer needed. Which Panorama tool can help this organization?
A. Test Policy Match
B. Application Groups
C. Policy Optimizer
D. Config Audit
Which two subscriptions are available when configuring Panorama to push dynamic updates to connected devices? (Choose two.)
A. Content-ID
B. User-ID
C. Applications and Threats
D. Antivirus
A firewall administrator is investigating high packet buffer utilization in the company firewall. After looking at the threat logs and seeing many flood attacks coming from a single source that are dropped by the firewall, the administrator decides to enable packet buffer protection to protect against similar attacks. The administrator enables packet buffer protection globally in the firewall but still sees a high packet buffer utilization rate. What else should the administrator do to stop packet buffers from being overflowed?
A. Apply DOS profile to security rules allow traffic from outside.
B. Enable packet buffer protection for the affected zones.
C. Add the default Vulnerability Protection profile to all security rules that allow traffic from outside.
D. Add a Zone Protection profile to the affected zones
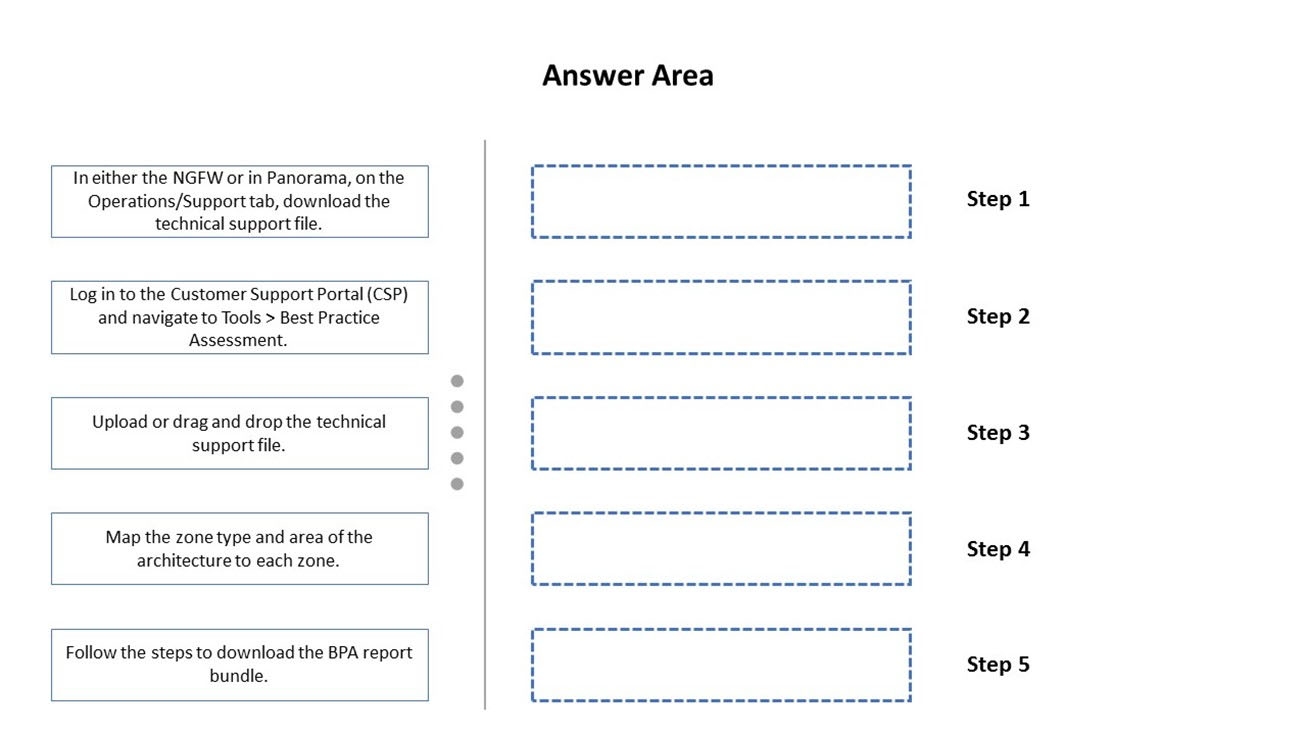
DRAG DROP - Below are the steps in the workflow for creating a Best Practice Assessment in a firewall and Panorama configuration. Place the steps in order. Select and Place:
An organization wishes to roll out decryption but gets some resistance from engineering leadership regarding the guest network. What is a common obstacle for decrypting traffic from guest devices?
A. Guest devices may not trust the CA certificate used for the forward trust certificate
B. Guests may use operating systems that can’t be decrypted
C. The organization has no legal authority to decrypt their traffic
D. Guest devices may not trust the CA certificate used for the forward untrust certificate
A user at an internal system queries the DNS server for their web server with a private IP of 10.250.241.131 in the DMZ. The DNS server returns an address of the web servers public address, 200.1.1.10. In order to reach the web server, which security rule and U-Turn NAT rule must be configured on the firewall?
A. NAT Rule: Source Zone: Untrust_L3 Source IP: Any Destination Zone: DMZ Destination IP: 200.1.1.10 Destination Translation address: 10.250.241.131 Security Rule: Source IP: Any Destination Zone: DMZ Destination IP: 10.250.241.131
B. NAT Rule: Source Zone: Trust_L3 Source IP: Any Destination Zone: DMZ Destination IP: 200.1.1.10 Destination Translation address: 10.250.241.131 Security Rule: Source Zone: Untrust-L3 Source IP: Any Destination Zone: DMZ Destination IP: 10.250.241.131
C. NAT Rule: Source Zone: Untrust_L3 Source IP: Any Destination Zone: Untrust_L3 Destination IP: 200.1.1.10 Destination Translation address: 10.250.241.131 Security Rule: Source Zone: Untrust-L3 Source IP: Any Destination Zone: DMZ Destination IP: 10.250.241.131
D. NAT Rule: Source Zone: Trust_L3 Source IP: Any Destination Zone: Untrust_L3 Destination IP: 200.1.1.10 Destination Translation address: 10.250.241.131 Security Rule: Source Zone: Trust-L3 Source IP: Any Destination Zone: DMZ Destination IP: 200.1.1.10
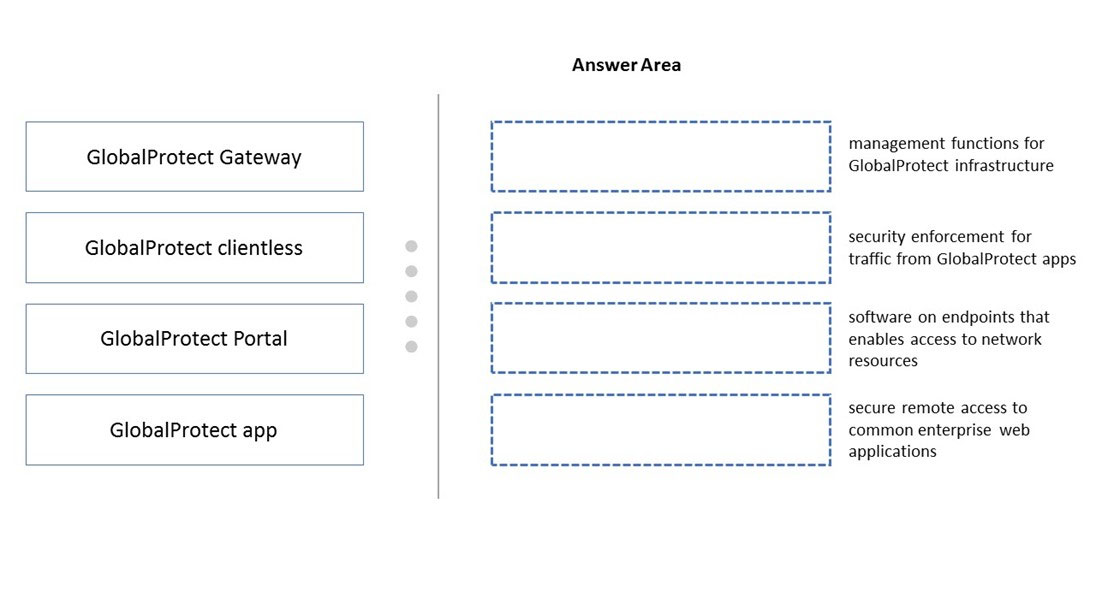
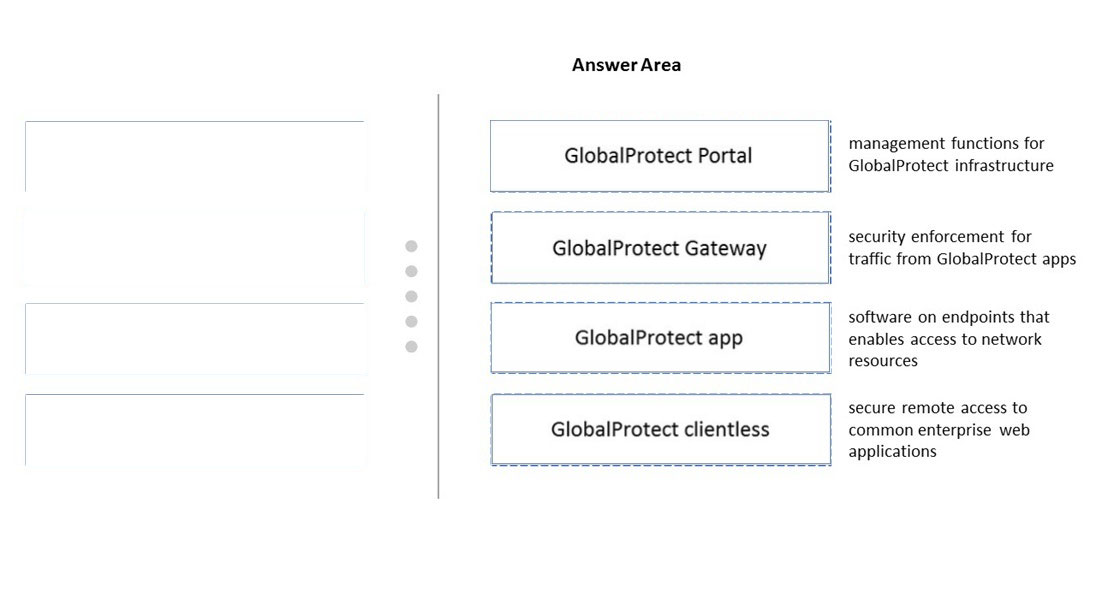
DRAG DROP - Match each GlobalProtect component to the purpose of that component. Select and Place:
An administrator wants a new Palo Alto Networks NGFW to obtain automatic application updates daily, so it is configured to use a scheduler for the application database. Unfortunately, they required the management network to be isolated so that it cannot reach the Internet. Which configuration will enable the firewall to download and install application updates automatically?
A. Download and install application updates cannot be done automatically if the MGT port cannot reach the Internet.
B. Configure a service route for Palo Alto Networks Services that uses a dataplane interface that can route traffic to the Internet, and create a Security policy rule to allow the traffic from that interface to the update servers if necessary.
C. Configure a Policy Based Forwarding policy rule for the update server IP address so that traffic sourced from the management interfaced destined for the update servers goes out of the interface acting as your Internet connection.
D. Configure a Security policy rule to allow all traffic to and from the update servers.
A firewall administrator is configuring an IPSec tunnel between Site A and Site B. The Site A firewall uses a DHCP assigned address on the outside interface of the firewall, and the Site B firewall uses a static IP address assigned to the outside interface of the firewall. However, the use of dynamic peering is not working. Refer to the two sets of configuration settings provided. Which two changes will allow the configurations to work? (Choose two.) Site A configuration:Site B configuration:
A. Match IKE version on both firewalls.
B. Configure Local Identification on Site B firewall.
C. Enable NAT Traversal on Site B firewall.
D. Disable passive mode on Site A firewall.
Which Security policy rule will allow an admin to block facebook chat but allow Facebook in general?
A. Deny application facebook-chat before allowing application facebook
B. Deny application facebook on top
C. Allow application facebook on top
D. Allow application facebook before denying application facebook-chat
A network security engineer configured IP multicast in the virtual router to support a new application. Users in different network segments are reporting that they are unable to access the application. What must be enabled to allow an interface to forward multicast traffic?
A. IGMP
B. SSM
C. BFD
D. PIM
Which two features can be used to tag a username so that it is included in a dynamic user group? (Choose two.)
A. log forwarding auto-tagging
B. XML API
C. GlobalProtect agent
D. User-ID Windows-based agent
An organization's administrator has the funds available to purchase more firewalls to increase the organization's security posture. The partner SE recommends placing the firewalls as close as possible to the resources that they protect. Is the SE's advice correct, and why or why not?
A. No. Firewalls provide new defense and resilience to prevent attackers at every stage of the cyberattack lifecycle, independent of placement.
B. Yes. Firewalls are session-based, so they do not scale to millions of CPS.
C. No. Placing firewalls in front of perimeter DDoS devices provides greater protection for sensitive devices inside the network.
D. Yes. Zone Protection profiles can be tailored to the resources that they protect via the configuration of specific device types and operating systems.
A network administrator is trying to prevent domain username and password submissions to phishing sites on some allowed URL categories. Which set of steps does the administrator need to take in the URL Filtering profile to prevent credential phishing on the firewall?
A. Choose the URL categories in the User Credential Submission column and set action to block Select the User credential Detection tab and select Use Domain Credential Filter Commit
B. Choose the URL categories in the User Credential Submission column and set action to block Select the User credential Detection tab and select use IP User Mapping Commit
C. Choose the URL categories on Site Access column and set action to block Click the User credential Detection tab and select IP User Mapping Commit
D. Choose the URL categories in the User Credential Submission column and set action to block Select the URL filtering settings and enable Domain Credential Filter Commit
An administrator needs to validate that policies that will be deployed will match the appropriate rules in the device-group hierarchy. Which tool can the administrator use to review the policy creation logic and verify that unwanted traffic is not allowed?
A. Preview Changes
B. Policy Optimizer
C. Managed Devices Health
D. Test Policy Match
An administrator creates an application-based security policy rule and commits the change to the firewall. Which two methods should be used to identify the dependent applications for the respective rule? (Choose two.)
A. Review the App Dependency application list from the Commit Status view.
B. Open the security policy rule and review the Depends On application list.
C. Reference another application group containing similar applications.
D. Use the show predefined xpath command and review the output.
Which PAN-OSֲ® policy must you configure to force a user to provide additional credentials before he is allowed to access an internal application that contains highly-sensitive business data?
A. Security policy
B. Decryption policy
C. Authentication policy
D. Application Override policy
An administrator has been asked to configure a Palo Alto Networks NGFW to provide protection against worms and trojans. Which Security Profile type will protect against worms and trojans?
A. Anti-Spyware
B. Instruction Prevention
C. File Blocking
D. Antivirus
Which statement is true regarding a heatmap in a BPA report?
A. When guided by authorized sales engineer, it helps determine the areas of the greatest security risk.
B. It runs only on firewalls.
C. It provides a percentage of adoption for each assessment area.
D. It provides a set of questionnaires that help uncover security risk prevention gaps across all areas of network and security architecture.
An organization conducts research on the benefits of leveraging the Web Proxy feature of PAN-OS 11.0. What are two benefits of using an explicit proxy method versus a transparent proxy method? (Choose two.)
A. No client configuration is required for explicit proxy, which simplifies the deployment complexity.
B. Explicit proxy supports interception of traffic using non-standard HTTPS ports.
C. It supports the X-Authenticated-User (XAU) header, which contains the authenticated username in the outgoing request.
D. Explicit proxy allows for easier troubleshooting, since the client browser is aware of the existence of the proxy.
A company has configured a URL Filtering profile with override action on their firewall. Which two profiles are needed to complete the configuration? (Choose two.)
A. Decryption
B. HTTP Server
C. SSL/TLS Service
D. Interface Management
What is the purpose of the firewall decryption broker?
A. decrypt SSL traffic and then send it as cleartext to a security chain of inspection tools.
B. force decryption of previously unknown cipher suites
C. reduce SSL traffic to a weaker cipher before sending it to a security chain of inspection tools.
D. inspect traffic within IPsec tunnels
How does Panorama prompt VMWare NSX to quarantine an infected VM?
A. HTTP Server Profile
B. Syslog Server Profile
C. Email Server Profile
D. SNMP Server Profile
Which three firewall states are valid? (Choose three.)
A. Active
B. Functional
C. Pending
D. Passive
E. Suspended
In a template, you can configure which two objects? (Choose two.)
A. Monitor profile
B. application group
C. SD-WAN path quality profile
D. IPsec tunnel
An administrator has enabled OSPF on a virtual router on the NGFW. OSPF is not adding new routes to the virtual router. Which two options enable the administrator to troubleshoot this issue? (Choose two.)
A. View Runtime Stats in the virtual router.
B. View System logs.
C. Add a redistribution profile to forward as BGP updates.
D. Perform a traffic pcap at the routing stage.
In a firewall, which three decryption methods are valid? (Choose three.)
A. SSL Outbound Proxyless Inspection
B. SSL Inbound Inspection
C. SSH Proxy
D. SSL Inbound Proxy
E. Decryption Mirror
An engineer needs to see how many existing SSL decryption sessions are traversing a firewall. What command should be used?
A. debug sessions | match proxy
B. debug dataplane pool statistics | match proxy
C. show dataplane pool statistics | match proxy
D. show sessions all
An administrator has created an SSL Decryption policy rule that decrypts SSL sessions on any port. Which log entry can the administrator use to verify that sessions are being decrypted?
A. In the details of the Traffic log entries
B. Decryption log
C. Data Filtering log
D. In the details of the Threat log entries
An engineer has discovered that certain real-time traffic is being treated as best effort due to it exceeding defined bandwidth. Which QoS setting should the engineer adjust?
A. QoS interface: Egress Guaranteed
B. QoS profile: Egress Max
C. QoS profile: Egress Guaranteed
D. QoS interface: Egress Max
A firewall engineer is configuring quality of service (QoS) policy for the IP address of a specific server in an effort to limit the bandwidth consumed by frequent downloads of large files from the internet. Which combination of pre-NAT and/or post-NAT information should be used in the QoS rule?
A. Pre-NAT source IP address -Pre-NAT source zone
B. Post-NAT source IP address -Pre-NAT source zone
C. Pre-NAT source IP address -Post-NAT source zone
D. Post-NAT source IP address -Post-NAT source zone
Free Access Full PCNSE Practice Test Free Questions
If you’re looking for more PCNSE practice test free questions, click here to access the full PCNSE practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your PCNSE certification journey!