PCNSE Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the PCNSE certification? Take your preparation to the next level with our PCNSE Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a PCNSE practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic PCNSE practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
Which version of GlobalProtect supports split tunneling based on destination domain, client process, and HTTP/HTTPS video streaming application?
A. GlobalProtect version 4.0 with PAN-OS 8.1
B. GlobalProtect version 4.1 with PAN-OS 8.1
C. GlobalProtect version 4.1 with PAN-OS 8.0
D. GlobalProtect version 4.0 with PAN-OS 8.0
Your company has 10 Active Directory domain controllers spread across multiple WAN links. All users authenticate to Active Directory. Each link has substantial network bandwidth to support all mission-critical applications. The firewall's management plane is highly utilized. Given this scenario, which type of User-ID agent is considered a best practice by Palo Alto Networks?
A. PAN-OS integrated agent
B. Citrix terminal server agent with adequate data-plane resources
C. Captive Portal
D. Windows-based User-ID agent on a standalone server
A firewall engineer creates a NAT rule to translate IP address 1.1.1.10 to 192.168.1.10. The engineer also plans to enable DNS rewrite so that the firewall rewrites the IPv4 address in a DNS response based on the original destination IP address and translated destination IP address configured for the rule. The engineer wants the firewall to rewrite a DNS response of 1.1.1.10 to 192.168.1.10. What should the engineer do to complete the configuration?
A. Enable DNS rewrite under the destination address translation in the Translated Packet section of the NAT rule with the direction Forward.
B. Create a U-Turn NAT to translate the destination IP address 1.1.1.10 to 192.168.1.10 with the destination port equal to UDP/53.
C. Enable DNS rewrite under the destination address translation in the Translated Packet section of the NAT rule with the direction Reverse.
D. Create a U-Turn NAT to translate the destination IP address 192.168.1.10 to 1.1.1.10 with the destination port equal to UDP/53.
Updates to dynamic user group membership are automatic therefore using dynamic user groups instead of static group objects allows you to:
A. respond to changes in user behaviour or potential threats using manual policy changes
B. respond to changes in user behaviour or potential threats without manual policy changes
C. respond to changes in user behaviour or potential threats without automatic policy changes
D. respond to changes in user behaviour and confirmed threats with manual policy changes
An administrator has been asked to configure a Palo Alto Networks NGFW to provide protection against external hosts attempting to exploit a flaw in an operating system on an internal system. Which Security Profile type will prevent this attack?
A. Vulnerability Protection
B. Anti-Spyware
C. URL Filtering
D. Antivirus
What is a feature of the PA-440 hardware platform?
A. It supports Zero Touch Provisioning to assist in automated deployments.
B. It supports 10GbE SFP+ modules.
C. It has twelve 1GbE Copper ports.
D. It has dedicated interfaces for high availability.
An engineer is reviewing the following high availability (HA) settings to understand a recent HA failover event.Which timer determines the frequency between packets sent to verify that the HA functionality on the other HA firewall is operational?
A. Hello Interval
B. Monitor Fail Hold Up Time
C. Heartbeat Interval
D. Promotion Hold Time
Which statement best describes the Automated Commit Recovery feature?
A. It performs a connectivity check between the firewall and Panorama after every configuration commit on the firewall. It reverts the configuration changes on the firewall if the check fails.
B. It restores the running configuration on a firewall if the last configuration commit fails.
C. It restores the running configuration on a firewall and Panorama if the last configuration commit fails.
D. It performs a connectivity check between the firewall and Panorama after every configuration commit on the firewall. It reverts the configuration changes on the firewall and on Panorama if the check fails.
In the New App Viewer under Policy Optimizer, what does the compare option for a specific rule allow an administrator to compare?
A. Applications configured in the rule with their dependencies
B. The security rule with any other security rule selected
C. Applications configured in the rule with applications seen from traffic matching the same rule
D. The running configuration with the candidate configuration of the firewall
A network security administrator wants to begin inspecting bulk user HTTPS traffic flows egressing out of the internet edge firewall. Which certificate is the best choice to configure as an SSL Forward Trust certificate?
A. A Machine Certificate for the firewall signed by the organization’s PKI
B. A web server certificate signed by the organization’s PKI
C. A subordinate Certificate Authority certificate signed by the organization’s PKI
D. A self-signed Certificate Authority certificate generated by the firewall
An engineer troubleshooting a site-to-site VPN finds a Security policy dropping the peer’s IKE traffic at the edge firewall. Both VPN peers are behind a NAT, and NAT-T is enabled. How can the engineer remediate this issue?
A. Add a Security policy to allow UDP/500.
B. Add a Security policy to allow the IKE application.
C. Add a Security policy to allow the IPSec application.
D. Add a Security policy to allow UDP/4501.
Which Security profile generates a packet threat type found in threat logs?
A. WildFire
B. Zone Protection
C. Anti-Spyware
D. Antivirus
Which configuration is backed up using the Scheduled Config Export feature in Panorama?
A. Panorama running configuration and running configuration of all managed devices
B. Panorama candidate configuration
C. Panorama candidate configuration and candidate configuration of all managed devices.
D. Panorama running configuration
Which two virtualization platforms officially support the deployment of Palo Alto Networks VM-Series firewalls? (Choose two.)
A. Red Hat Enterprise Virtualization (RHEV)
B. Kernel Virtualization Module (KVM)
C. Boot Strap Virtualization Module (BSVM)
D. Microsoft Hyper-V
After some firewall configuration changes, an administrator discovers that application identification has started failing. The administrator investigates further and notices that a high number of sessions were going to a discard state with the application showing as unknown-tcp. Which possible firewall change could have caused this issue?
A. enabling Forward segments that exceed the TCP App-ID inspection queue in Device > Setup > Content-ID > Content-ID Settings
B. enabling Forward segments that exceed the TCP content inspection queue in Device > Setup > Content-ID > Content-ID Settings
C. Jumbo frames were enabled on the firewall, which reduced the App-ID queue size and the number of available packet buffers.
D. Jumbo frames were disabled on the firewall, which reduced the queue sizes dedicated for out-of-order and application identification.
What does SSL decryption require to establish a firewall as a trusted third party and to establish trust between a client and server to secure SSL/TLS connection?
A. link state
B. profiles
C. stateful firewall connection
D. certificates
How can an administrator configure the firewall to automatically quarantine a device using GlobalProtect?
A. by adding the device’s Host ID to a quarantine list and configure GlobalProtect to prevent users from connecting to the GlobalProtect gateway from a quarantined device
B. by exporting the list of quarantined devices to a pdf or csv file by selecting PDF/CSV at the bottom of the Device Quarantine page and leveraging the appropriate XSOAR playbook
C. by using security policies, log forwarding profiles, and log settings
D. there is no native auto-quarantine feature so a custom script would need to be leveraged
An administrator needs to gather information about the CPU utilization on both the management plane and the data plane. Where does the administrator view the desired data?
A. Resources Widget on the Dashboard
B. Monitor > Utilization
C. Support > Resources
D. Application Command and Control Center
An administrator wants to perform HIP checks on the endpoints to ensure their security posture. Which license is required on all Palo Alto Networks next-generation firewalls that will be performing the HIP checks?
A. GlobalProtect Gateway
B. Current and Active Support License
C. Threat Prevention
D. GlobalProtect Portal
In SSL Forward Proxy decryption, which two certificates can be used for certificate signing? (Choose two.)
A. self-signed CA certificate
B. server certificate
C. wildcard server certificate
D. client certificate
E. enterprise CA certificate
Which Panorama mode should be used so that all logs are sent to, and only stored in, Cortex Data Lake?
A. Legacy
B. Management Only
C. Log Collector
D. Panorama
Which feature prevents the submission of corporate login information into website forms?
A. Data filtering
B. User-ID
C. File blocking
D. Credential phishing prevention
What is the maximum number of samples that can be submitted to WildFire manually per day?
A. 1,000
B. 2,000
C. 5,000
D. 15,000
How can packet buffer protection be configured?
A. at zone level to protect firewall resources and ingress zones, but not at the device level
B. at the interface level to protect firewall resources
C. at the device level (globally) to protect firewall resources and ingress zones, but not at the zone level
D. at the device level (globally) and, if enabled globally, at the zone level
An administrator sees several inbound sessions identified as unknown-tcp in the Traffic logs. The administrator determines that these sessions are form external users accessing the company's proprietary accounting application. The administrator wants to reliably identify this traffic as their accounting application and to scan this traffic for threats. Which option would achieve this result?
A. Create a custom App-ID and enable scanning on the advanced tab.
B. Create an Application Override policy.
C. Create a custom App-ID and use the ג€ordered conditionsג€ check box.
D. Create an Application Override policy and a custom threat signature for the application.
Which two methods can be configured to validate the revocation status of a certificate? (Choose two.)
A. CRL
B. CRT
C. OCSP
D. Cert-Validation-Profile
E. SSL/TLS Service Profile
Which three multi-factor authentication methods can be used to authenticate access to the firewall? (Choose three.)
A. One-time password
B. User certificate
C. SMS
D. Voice
E. Fingerprint
A consultant deploys a PAN-OS 11.0 VM-Series firewall with the Web Proxy feature in Transparent Proxy mode. Which three elements must be in place before a transparent web proxy can function? (Choose three.)
A. User-ID for the proxy zone
B. DNS Security license
C. Prisma Access explicit proxy license
D. Cortex Data Lake license
E. Authentication Policy Rule set to default-web-form
An engineer decides to use Panorama to upgrade devices to PAN-OS 10.2. Which three platforms support PAN-OS 10.2? (Choose three.)
A. PA-220
B. PA-800 Series
C. PA-5000 Series
D. PA-500
E. PA-3400 Series
An engineer wants to configure aggregate interfaces to increase bandwidth and redundancy between the firewall and switch. Which statement is correct about the configuration of the interfaces assigned to an aggregated interface group?
A. They can have different hardware media such as the ability to mix fiber optic and copper.
B. They can have a different interface type such as Layer 3 or Layer 2.
C. They can have a different interface type from an aggregate interface group.
D. They can have a different bandwidth.
An organization's administrator has the funds available to purchase more firewalls to increase the organization's security posture. The partner SE recommends placing the firewalls as close as possible to the resources that they protect. Is the SE's advice correct, and why or why not?
A. No. Firewalls provide new defense and resilience to prevent attackers at every stage of the cyberattack lifecycle, independent of placement.
B. Yes. Firewalls are session-based, so they do not scale to millions of CPS.
C. No. Placing firewalls in front of perimeter DDoS devices provides greater protection for sensitive devices inside the network.
D. Yes. Zone Protection profiles can be tailored to the resources that they protect via the configuration of specific device types and operating systems.
Which two features can be used to tag a username so that it is included in a dynamic user group? (Choose two.)
A. log forwarding auto-tagging
B. XML API
C. GlobalProtect agent
D. User-ID Windows-based agent
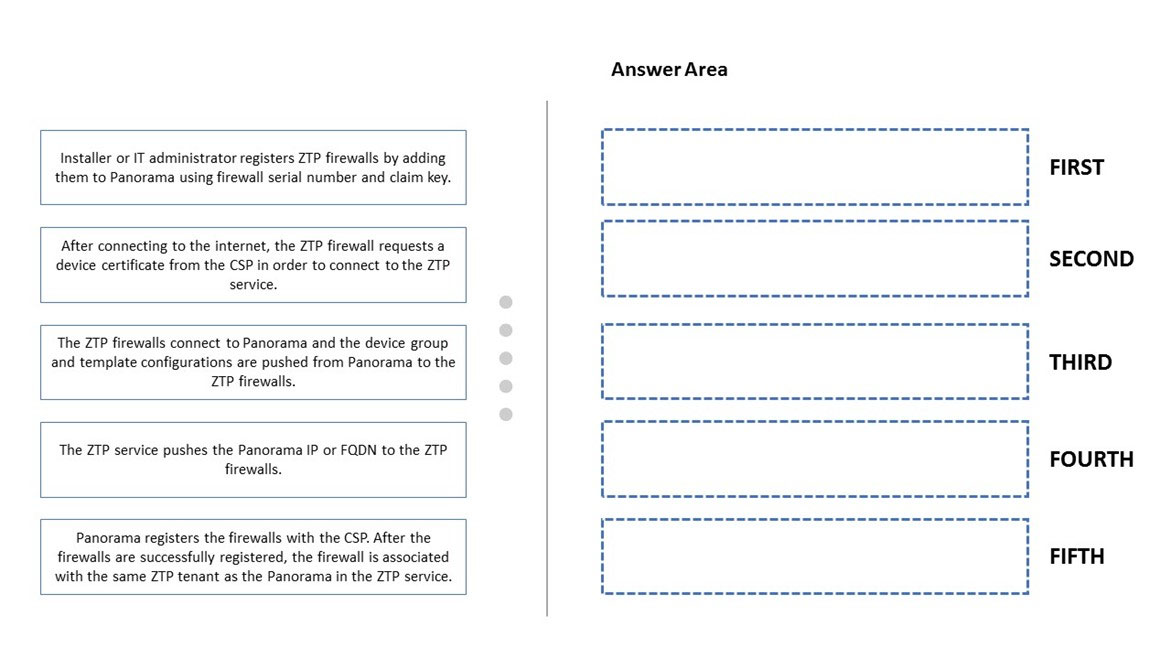
DRAG DROP - Place the steps to onboard a ZTP firewall into Panorama/CSP/ZTP-Service in the correct order. Select and Place:
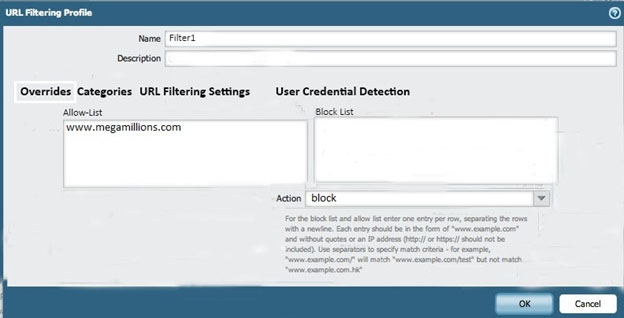
An administrator needs to determine why users on the trust zone cannot reach certain websites. The only information available is shown on the following image. Which configuration change should the administrator make? A.B.
C.
D.
E.
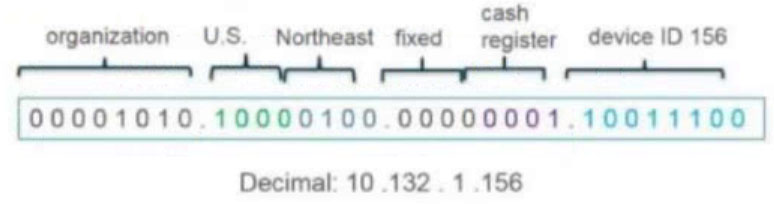
What type of address object would be useful for internal devices where the addressing structure assigns meaning to certain bits in the address, as illustrated in the diagram?
A. IP Netmask
B. IP Range
C. IP Address
D. IP Wildcard Mask
How is an address object of type IP range correctly defined?
A. 192 168 40 1-192 168 40 255
B. 192.168 40 1/24
C. 192.168 40 1, 192.168 40.255
D. 192 168 40 1-255
As a best practice, logging at session start should be used in which case?
A. While troubleshooting
B. Only on Deny rules
C. Only when log at session end is enabled
D. On all Allow rules
An Administrator is configuring Authentication Enforcement and they would like to create an exemption rule to exempt a specific group from authentication. Which authentication enforcement object should they select?
A. default-no-captive-portal
B. default-authentication-bypass
C. default-browser-challenge
D. default-web-form
Which statement regarding HA timer settings is true?
A. Use the Moderate profile for typical failover timer settings
B. Use the Critical profile for faster failover timer settings
C. Use the Aggressive profile for slower failover timer settings
D. Use the Recommended profile for typical failover timer settings
An engineer wants to forward all decrypted traffic on a PA-850 firewall to a forensic tool with a decrypt mirror interface. Which statement is true regarding the configuration of the Decryption Port Mirroring feature?
A. The engineer should install the Decryption Port Mirror license and reboot the firewall.
B. The PA-850 firewall does not support decrypt mirror interface, so the engineer needs to upgrade the firewall to PA-3200 series.
C. The engineer must assign an IP from the same subnet with the forensic tool to the decrypt mirror interface.
D. The engineer must assign the related virtual-router to the decrypt mirror interface.
You have upgraded your Panorama and Log Collectors to 10.2.x. Before upgrading your firewalls using Panorama, what do you need do?
A. Commit and Push the configurations to the firewalls.
B. Refresh your licenses with Palo Alto Network Support ג€” Panorama/Licenses/Retrieve License Keys from License Server.
C. Refresh the Master Key in Panorama/Master Key and Diagnostic.
D. Re-associate the firewalls in Panorama/Managed Devices/Summary.
An internal audit team has requested additional information to be included inside traffic logs forwarded from Palo Alto Networks firewalls to an internal syslog server. Where can the firewall engineer define the data to be added into each forwarded log?
A. Custom Log Format within Device > Server Profiles > Syslog
B. Built-in Actions within Objects > Log Forwarding Profile
C. Logging and Reporting Settings within Device > Setup > Management
D. Data Patterns within Objects > Custom Objects
How does an administrator schedule an Applications and Threats dynamic update while delaying installation of the update for a certain amount of time?
A. Configure the option for ג€Thresholdג€.
B. Disable automatic updates during weekdays.
C. Automatically ג€download onlyג€ and then install Applications and Threats later, after the administrator approves the update.
D. Automatically ג€download and installג€ but with the ג€disable new applicationsג€ option used.
An engineer is configuring SSL Inbound Inspection for public access to a company’s application. Which certificate(s) need to be installed on the firewall to ensure that inspection is performed successfully?
A. Intermediate CA(s) and End-entity certificate
B. Root CA and Intermediate CA(s)
C. Self-signed certificate with exportable private key
D. Self-signed CA and End-entity certificate
Which Panorama feature protects logs against data loss if a Panorama server fails?
A. Panorama Collector Group with Log Redundancy ensures that no logs are lost if a server fails inside the Collector Group.
B. Panorama Collector Group automatically ensures that no logs are lost if a server fails inside the Collector Group.
C. Panorama HA with Log Redundancy ensures that no logs are lost if a server fails inside the HA Cluster.
D. Panorama HA automatically ensures that no logs are lost if a server fails inside the HA Cluster.
You have upgraded Panorama to 10.2 and need to upgrade six Log Collectors. When upgrading Log Collectors to 10.2, you must do what?
A. Upgrade the Log Collectors one at a time.
B. Add Panorama Administrators to each Managed Collector.
C. Upgrade all the Log Collectors at the same time.
D. Add a Global Authentication Profile to each Managed Collector.
Which protection feature is available only in a Zone Protection Profile?
A. SYN Flood Protection using SYN Flood Cookies
B. ICMP Flood Protection
C. Port Scan Protection
D. UDP Flood Protections
An administrator connected a new fiber cable and transceiver to interface Ethernet1/1 on a Palo Alto Networks firewall. However, the link does not seem to be coming up. If an administrator were to troubleshoot, how would they confirm the transceiver type, tx-power, rx-power, vendor name, and part number via the CLI?
A. show system state filter sw.dev.interface.config
B. show chassis status slot s1
C. show system state filter-pretty sys.s1.*
D. show system state filter ethernet1/1
Which three authentication services can an administrator use to authenticate admins into the Palo Alto Networks NGFW without defining a corresponding admin account on the local firewall? (Choose three.)
A. Kerberos
B. PAP
C. SAML
D. TACACS+
E. RADIUS
F. LDAP
Which CLI command is used to simulate traffic going through the firewall and determine which Security policy rule, NAT translation, static route, or PBF rule will be triggered by the traffic?
A. check
B. find
C. test
D. sim
Free Access Full PCNSE Practice Exam Free
Looking for additional practice? Click here to access a full set of PCNSE practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your PCNSE certification journey!