PCNSE Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your PCNSE certification? Our PCNSE Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an PCNSE dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our PCNSE Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
How can an administrator configure the firewall to automatically quarantine a device using GlobalProtect?
A. by adding the device’s Host ID to a quarantine list and configure GlobalProtect to prevent users from connecting to the GlobalProtect gateway from a quarantined device
B. by exporting the list of quarantined devices to a pdf or csv file by selecting PDF/CSV at the bottom of the Device Quarantine page and leveraging the appropriate XSOAR playbook
C. by using security policies, log forwarding profiles, and log settings
D. there is no native auto-quarantine feature so a custom script would need to be leveraged
An administrator has users accessing network resources through Citrix XenApp 7.x. Which User-ID mapping solution will map multiple users who are using Citrix to connect to the network and access resources?
A. Client Probing
B. Terminal Services agent
C. GlobalProtect
D. Syslog Monitoring
Which GlobalProtect gateway setting is required to enable split-tunneling by access route, destination domain, and application?
A. Satellite mode
B. Tunnel mode
C. No Direct Access to local networks
D. IPSec mode
Which two subscriptions are available when configuring Panorama to push dynamic updates to connected devices? (Choose two.)
A. Content-ID
B. User-ID
C. Applications and Threats
D. Antivirus
An administrator has a Palo Alto Networks NGFW. All security subscriptions and decryption are enabled and the system is running close to its resource limits. Knowing that using decryption can be resource-intensive, how can the administrator reduce the load on the firewall?
A. Use SSL Forward Proxy instead of SSL Inbound Inspection for decryption.
B. Use RSA instead of ECDSA for traffic that isn’t sensitive or high-priority.
C. Use the highest TLS protocol version to maximize security.
D. Use ECDSA instead of RSA for traffic that isn’t sensitive or high-priority.
An engineer troubleshooting a site-to-site VPN finds a Security policy dropping the peer’s IKE traffic at the edge firewall. Both VPN peers are behind a NAT, and NAT-T is enabled. How can the engineer remediate this issue?
A. Add a Security policy to allow UDP/500.
B. Add a Security policy to allow the IKE application.
C. Add a Security policy to allow the IPSec application.
D. Add a Security policy to allow UDP/4501.
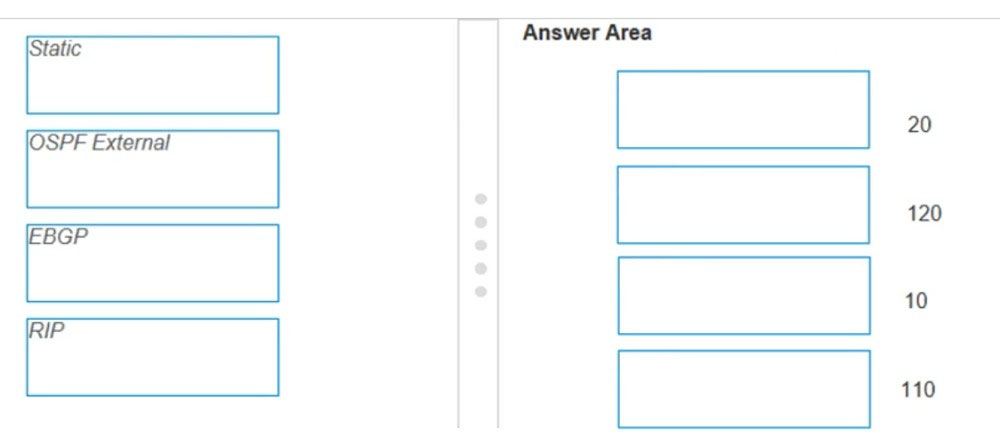
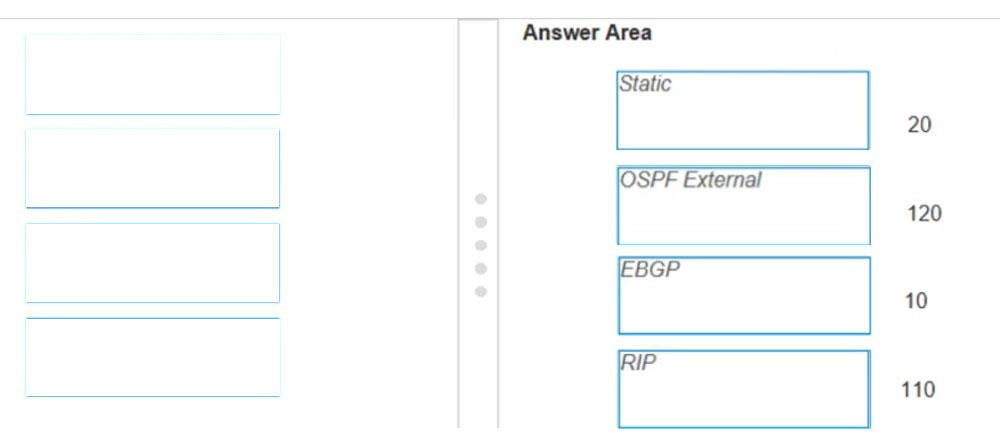
DRAG DROP - An engineer is troubleshooting traffic routing through the virtual router. The firewall uses multiple routing protocols, and the engineer is trying to determine routing priority. Match the default Administrative Distances for each routing protocol. Select and Place:
Which of the following commands would you use to check the total number of the sessions that are currently going through SSL Decryption processing?
A. show session all filter ssl-decryption yes total-count yes
B. show session all ssl-decrypt yes count yes
C. show session all filter ssl-decrypt yes count yes
D. show session filter ssl-decryption yes total-count yes
An administrator is using Panorama to manage multiple firewalls. After upgrading all devices to the latest PAN-OS software, the administrator enables log forwarding from the firewalls to Panorama. However, pre-existing logs from the firewalls are not appearing in Panorama. Which action should be taken to enable the firewalls to send their pre-existing logs to Panorama?
A. Use the import option to pull logs.
B. Use the scp logdb export command.
C. Export the log database.
D. Use the ACC to consolidate the logs.
A client wants to detect the use of weak and manufacturer-default passwords for IoT devices. Which option will help the customer?
A. Configure a Data Filtering profile with alert mode.
B. Configure an Antivirus profile with alert mode.
C. Configure an Anti-Spyware profile with alert mode.
D. Configure a Vulnerability Protection profile with alert mode.
An administrator is considering deploying WildFire globally. What should the administrator consider with regards to the WildFire infrastructure?
A. To comply with data privacy regulations, WildFire signatures and verdicts are not shared globally.
B. Palo Alto Networks owns and maintains one global cloud and four WildFire regional clouds.
C. Each WildFire cloud analyzes samples independently of the other WildFire clouds.
D. The WildFire Global Cloud only provides bare metal analysis.
An administrator is required to create an application-based Security policy rule to allow Evernote. The Evernote application implicitly uses SSL and web browsing. What is the minimum the administrator needs to configure in the Security rule to allow only Evernote?
A. Create an Application Override using TCP ports 443 and 80.
B. Add the HTPP, SSL, and Evernote applications to the same Security policy.
C. Add the Evernote application to the Security policy rule, then add a second Security policy rule containing both HTTP and SSL.
D. Add only the Evernote application to the Security policy rule.
Which tool provides an administrator the ability to see trends in traffic over periods of time, such as threats detected in the last 30 days?
A. Session Browser
B. Application Command Center
C. TCP Dump
D. Packet Capture
When you import the configuration of an HA pair into Panorama, how do you prevent the import from affecting ongoing traffic?
A. Disable HA.
B. Disable the HA2 link.
C. Set the passive link state to “shutdown.”
D. Disable config sync.
If an administrator wants to decrypt SMTP traffic and possesses the server's certificate, which SSL decryption mode will allow the Palo Alto Networks NGFW to inspect traffic to the server?
A. TLS Bidirectional Inspection
B. SSL Inbound Inspection
C. SSH Forward Proxy
D. SMTP Inbound Decryption
An engineer decides to use Panorama to upgrade devices to PAN-OS 10.2. Which three platforms support PAN-OS 10.2? (Choose three.)
A. PA-220
B. PA-800 Series
C. PA-5000 Series
D. PA-500
E. PA-3400 Series
A firewall administrator wants to be able to see all NAT sessions that are going through a firewall with source NAT. Which CLI command can the administrator use?
A. show session all filter nat source
B. show running nat-rule-ippool rule “rule_name”
C. show running nat-policy
D. show session all filter nat-rule-source
Which feature prevents the submission of corporate login information into website forms?
A. Data filtering
B. User-ID
C. File blocking
D. Credential phishing prevention
Which DoS protection mechanism detects and prevents session exhaustion attacks?
A. Packet Based Attack Protection
B. Flood Protection
C. Resource Protection
D. TCP Port Scan Protection
What are the two behavior differences between Highlight Unused Rules and the Rule Usage Hit counter when a firewall is rebooted? (Choose two.)
A. Rule Usage Hit counter will not be reset.
B. Highlight Unused Rules will highlight all rules.
C. Highlight Unused Rules will highlight zero rules.
D. Rule Usage Hit counter will reset.
A web server is hosted in the DMZ and the server is configured to listen for incoming connections on TCP port 443. A Security policies rules allowing access from the Trust zone to the DMZ zone needs to be configured to allow web-browsing access. The web server hosts its contents over HTTP(S). Traffic from Trust to DMZ is being decrypted with a Forward Proxy rule. Which combination of service and application, and order of Security policy rules, needs to be configured to allow cleartext web-browsing traffic to this server on tcp/443?
A. Rule #1: application: web-browsing; service: application-default; action: allow Rule #2: application: ssl; service: application-default; action: allow
B. Rule #1: application: web-browsing; service: service-http; action: allow Rule #2: application: ssl; service: application-default; action: allow
C. Rule # 1: application: ssl; service: application-default; action: allow Rule #2: application: web-browsing; service: application-default; action: allow
D. Rule #1: application: web-browsing; service: service-https; action: allow Rule #2: application: ssl; service: application-default; action: allow
Using the above screenshot of the ACC, what is the best method to set a global filter, narrow down Blocked User Activity, and locate the user(s) that could be compromised by a botnet?
A. Click the hyperlink for the ZeroAccess.Gen threat.
B. Click the source user with the highest threat count.
C. Click the left arrow beside the ZeroAccess.Gen threat.
D. Click the hyperlink for the botnet Threat Category.
A network security engineer needs to ensure that virtual systems can communicate with one another within a Palo Alto Networks firewall. Separate virtual routers (VRs) are created for each virtual system. In addition to confirming security policies, which three configuration details should the engineer focus on to ensure communication between virtual systems? (Choose three.)
A. Add a route with next hop next-vr by using the VR configured in the virtual system.
B. Layer 3 zones for the virtual systems that need to communicate.
C. Add a route with next hop set to none, and use the interface of the virtual systems that need to communicate.
D. Ensure the virtual systems are visible to one another.
E. External zones with the virtual systems added.
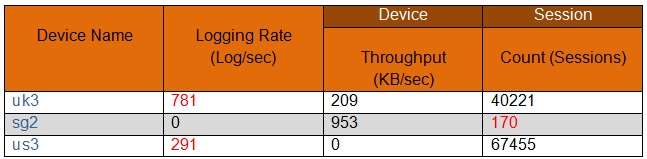
In the following image from Panorama, why are some values shown in red?
A. sg2 session count is the lowest compared to the other managed devices.
B. us3 has a logging rate that deviates from the administrator-configured thresholds.
C. uk3 has a logging rate that deviates from the seven-day calculated baseline.
D. sg2 has misconfigured session thresholds.
An engineer is tasked with deploying SSL Forward Proxy decryption for their organization. What should they review with their leadership before implementation?
A. Browser-supported cipher documentation
B. Cipher documentation supported by the endpoint operating system
C. URL risk-based category distinctions
D. Legal compliance regulations and acceptable usage policies
When overriding a template configuration locally on a firewall, what should you consider?
A. Panorama will update the template with the overridden value.
B. The firewall template will show that it is out of sync within Panorama.
C. Only Panorama can revert the override.
D. Panorama will lose visibility into the overridden configuration.
Which CLI command is used to simulate traffic going through the firewall and determine which Security policy rule, NAT translation, static route, or PBF rule will be triggered by the traffic?
A. check
B. find
C. test
D. sim
An administrator has a requirement to export decrypted traffic from the Palo Alto Networks NGFW to a third-party, deep-level packet inspection appliance. Which interface type and license feature are necessary to meet the requirement?
A. Decryption Mirror interface with the Threat Analysis license
B. Virtual Wire interface with the Decryption Port Export license
C. Tap interface with the Decryption Port Mirror license
D. Decryption Mirror interface with the associated Decryption Port Mirror license
An administrator needs firewall access on a trusted interface. Which two components are required to configure certificate-based, secure authentication to the web UI? (Choose two.)
A. server certificate
B. SSL/TLS Service Profile
C. certificate profile
D. SSH Service Profile
What is exchanged through the HA2 link?
A. hello heartbeats
B. User-ID information
C. session synchronization
D. HA state information
An administrator is configuring a Panorama device group. Which two objects are configurable? (Choose two.)
A. URL Filtering profiles
B. SSL/TLS profiles
C. Address groups
D. DNS Proxy
Which three settings are defined within the Templates object of Panorama? (Choose three.)
A. Setup
B. Virtual Routers
C. Interfaces
D. Security
E. Application Override
A web server is hosted in the DMZ, and the server is configured to listen for incoming connections only on TCP port 8080. A Security policy rule allowing access from the Trust zone to the DMZ zone need to be configured to enable we browsing access to the server. Which application and service need to be configured to allow only cleartext web-browsing traffic to thins server on tcp/8080?
A. application: web-browsing; service: application-default
B. application: web-browsing; service: service-https
C. application: ssl; service: any
D. application: web-browsing; service: (custom with destination TCP port 8080)
How does an administrator schedule an Applications and Threats dynamic update while delaying installation of the update for a certain amount of time?
A. Configure the option for ג€Thresholdג€.
B. Disable automatic updates during weekdays.
C. Automatically ג€download onlyג€ and then install Applications and Threats later, after the administrator approves the update.
D. Automatically ג€download and installג€ but with the ג€disable new applicationsג€ option used.
Which CLI command enables an administrator to check the CPU utilization of the dataplane?
A. show running resource-monitor
B. debug data-plane dp-cpu
C. show system resources
D. debug running resources
Which CLI command is used to determine how much disk space is allocated to logs?
A. debug log-receiver show
B. show system info
C. show system logdb-quota
D. show logging-status
Which feature of PAN-OS SD-WAN allows you to configure a bandwidth-intensive application to go directly to the internet through the branch's ISP link instead of going back to the data-center hub through the VPN tunnel, thus saving WAN bandwidth costs?
A. SD-WAN Full Mesh with branches only
B. SD-WAN direct internet access (DIA) links
C. SD-WAN Interface profile
D. VPN Cluster
An administrator just enabled HA Heartbeat Backup on two devices. However, the status on the firewall's dashboard is showing as down.What could an administrator do to troubleshoot the issue?
A. Go to Device > High Availability > General > HA Pair Settings > Setup and configuring the peer IP for heartbeat backup
B. Go to Device > High Availability > HA Communications > General > and check the Heartbeat Backup under Election Settings
C. Check peer IP address for heartbeat backup to Device > High Availability > HA Communications > Packet Forwarding settings
D. Check peer IP address in the permit list in Device > Setup > Management > Interfaces > Management Interface Settings
Which three options are supported in HA Lite? (Choose three.)
A. Virtual link
B. Active/passive deployment
C. Synchronization of IPsec security associations
D. Configuration synchronization
E. Session synchronization
For which two reasons would a firewall discard a packet as part of the packet flow sequence? (Choose two.)
A. ingress processing errors
B. rule match with action ג€denyג€
C. rule match with action ג€allowג€
D. equal-cost multipath
A network security engineer wants to prevent resource-consumption issues on the firewall. Which strategy is consistent with decryption best practices to ensure consistent performance?
A. Use Decryption profiles to downgrade processor-intensive ciphers to ciphers that are less processor-intensive
B. Use Decryption profiles to drop traffic that uses processor-intensive ciphers
C. Use PFS in a Decryption profile for higher-priority and higher-risk traffic, and use less processor-intensive decryption methods for lower-risk traffic
D. Use RSA in a Decryption profile for higher-priority and higher-risk traffic, and use less processor-intensive decryption methods for lower-risk traffic
What are three reasons why an installed session can be identified with the "application incomplete" tag? (Choose three.)
A. There was no application data after the TCP connection was established.
B. The client sent a TCP segment with the PUSH flag set.
C. The TCP connection was terminated without identifying any application data.
D. There is not enough application data after the TCP connection was established.
E. The TCP connection did not fully establish.
A firewall engineer reviews the PAN-OS GlobalProtect application and sees that it implicitly uses web-browsing and depends on SSL. When creating a new rule, what is needed to allow the application to resolve dependencies?
A. Add SSL application to the same rule.
B. SSL and web-browsing must both be explicitly allowed.
C. Add SSL and web-browsing applications to the same rule.
D. Add web-browsing application to the same rule.
With the default TCP and UDP settings on the firewall, what will be the identified application in the following session?
A. insufficient-data
B. incomplete
C. not-applicable
D. unknown-tcp
Refer to the exhibit.An administrator is using DNAT to map two servers to a single public IP address. Traffic will be steered to the specific server based on the application, where Host A (10.1.1.100) receives HTTP traffic and Host B (10.1.1.101) receives SSH traffic. Which two Security policy rules will accomplish this configuration? (Choose two.)
A. Untrust (Any) to Untrust (10.1.1.1), web-browsing ג€” Allow
B. Untrust (Any) to Untrust (10.1.1.1), ssh ג€” Allow
C. Untrust (Any) to DMZ (1.1.1.100), web-browsing ג€” Allow
D. Untrust (Any) to DMZ (1.1.1.100), ssh ג€” Allow
E. Untrust (Any) to DMZ (10.1.1.100, 10.1.1.101), ssh, web-browsing ג€” Allow
What are two benefits of nested device groups in Panorama? (Choose two.)
A. Reuse of the existing Security policy rules and objects
B. Requires configuring both function and location for every device
C. All device groups inherit settings from the Shared group
D. Overwrites local firewall configuration
Which GlobalProtect component must be configured to enable Clientless VPN?
A. GlobalProtect satellite
B. GlobalProtect app
C. GlobalProtect portal
D. GlobalProtect gateway
The following objects and policies are defined in a device group hierarchy.Dallas-Branch has Dallas-FW as a member of the Dallas-Branch device-group NYC-DC has NYC-FW as a member of the NYC-DC device-group What objects and policies will the Dallas-FW receive if "Share Unused Address and Service Objects" is enabled in Panorama?
A. Address Objects -Shared Address1 -Branch Address1 Policies -Shared Policy1 -Branch Policy1
B. Address Objects -Shared Address1 -Shared Address2 -Branch Address1 Policies -Shared Policy1 -Shared Policy2 -Branch Policy1
C. Address Objects -Shared Address1 -Shared Address2 -Branch Address1 -DC Address1 Policies -Shared Policy1 -Shared Policy2 -Branch Policy1
D. Address Objects -Shared Address1 -Shared Address2 -Branch Address1 Policies -Shared Policy1 -Branch Policy1
A company requires that a specific set of ciphers be used when remotely managing their Palo Alto Networks appliances. Which profile should be configured in order to achieve this?
A. Certificate profile
B. SSL/TLS Service profile
C. SSH Service profile
D. Decryption profile
An administrator wants to configure the Palo Alto Networks Windows User-ID agent to map IP addresses to usernames. The company uses four Microsoft Active Directory servers and two Microsoft Exchange servers, which can provide logs for login events. All six servers have IP addresses assigned from the following subnet: 192.168.28.32/27. The Microsoft Active Directory servers reside in 192.168.28.32/28, and the Microsoft Exchange servers reside in 192.168.28.48/28. What information does the administrator need to provide in the User Identification > Discovery section?
A. the IP-address and corresponding server type (Microsoft Active Directory or Microsoft Exchange) for each of the six servers
B. network 192.168.28.32/28 with server type Microsoft Active Directory and network 192.168.28.48/28 with server type Microsoft Exchange
C. one IP address of a Microsoft Active Directory server and “Auto Discover” enabled to automatically obtain all five of the other servers
D. network 192.168.28.32/27 with server type Microsoft
Access Full PCNSE Dump Free
Looking for even more practice questions? Click here to access the complete PCNSE Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our PCNSE dump free questions — and get one step closer to exam success!