PCNSA Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the PCNSA exam? Start with our PCNSA Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a PCNSA practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free PCNSA practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
An administrator would like to reference the same address object in Security policies on 100 Panorama managed firewalls, across 10 devices groups and five templates. Which configuration action should the administrator take when creating the address object?
A. Ensure that Disable Override is cleared.
B. Ensure that the Shared option is cleared.
C. Ensure that the Shared option is checked.
D. Tag the address object with the Global tag.
Which tab would an administrator click to create an address object?
A. Objects
B. Monitor
C. Device
D. Policies
Which action related to App-ID updates will enable a security administrator to view the existing security policy rule that matches new application signatures?
A. Review Policies
B. Review Apps
C. Pre-analyze
D. Review App Matches
Where can you apply URL Filtering policy in a Security policy rule?
A. Within the applications selection
B. Within a destination address
C. Within a service type
D. Within the actions tab
What is the main function of the Test Policy Match function?
A. ensure that policy rules are not shadowing other policy rules
B. confirm that rules meet or exceed the Best Practice Assessment recommendations
C. confirm that policy rules in the configuration are allowing donning the correct traffic
D. verify that policy rules from Expedition are valid
If a universal security rule was created for source zones A & B and destination zones A & B, to which traffic would the rule apply?
A. Some traffic between A & B
B. Some traffic within A
C. All traffic within zones A & B
D. Some traffic within B
Application groups enable access to what?
A. Applications that are explicitly unsanctioned for use within a company
B. Applications that are not explicitly unsanctioned and that an administrator wants users to be able to access
C. Applications that are explicitly sanctioned for use within a company
D. Applications that are not explicitly sanctioned and that an administrator wants users to be able to access
Which action results in the firewall blocking network traffic without notifying the sender?
A. Drop
B. Deny
C. No notification
D. Reset Client
Which Security profile would you apply to identify infected hosts on the protected network using DNS traffic?
A. URL filtering
B. vulnerability protection
C. anti-spyware
D. antivirus
What can be achieved by disabling the Share Unused Address and Service Objects with Devices setting on Panorama?
A. Increase the per-firewall capacity for address and service objects
B. Reduce the configuration and session synchronization time between HA pairs
C. Increase the backup capacity for configuration backups per firewall
D. Reduce the number of objects pushed to a firewall
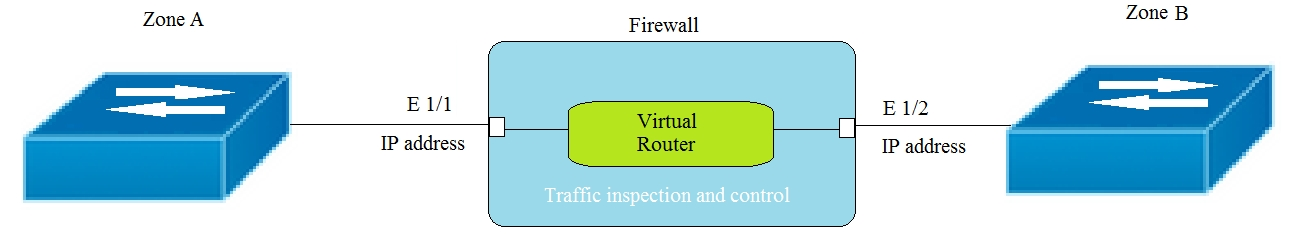
Given the topology, which zone type should zone A and zone B to be configured with?
A. Layer3
B. Ethernet
C. Layer2
D. Virtual Wire
Which two statements are true for the DNS Security service introduced in PAN-OS version 9.0? (Choose two.)
A. It is automatically enabled and configured.
B. It eliminates the need for dynamic DNS updates.
C. It functions like PAN-DB and requires activation through the app portal.
D. It removes the 100K limit for DNS entries for the downloaded DNS updates.
Which System log severity level would be displayed as a result of a user password change?
A. Low
B. Medium
C. High
D. Critical
An administrator would like to apply a more restrictive Security profile to traffic for file sharing applications. The administrator does not want to update the Security policy or object when new applications are released. Which object should the administrator use as a match condition in the Security policy?
A. the Online Storage and Backup URL category
B. the Content Delivery Networks URL category
C. an application group containing all of the file-sharing App-IDs reported in the traffic logs
D. an application filter for applications whose subcategory is file-sharing
An administrator wants to prevent users from unintentionally accessing malicious domains where data can be exfiltrated through established connections to remote systems. From the Pre-defined Categories tab within the URL Filtering profile, what is the right configuration to prevent such connections?
A. Set the hacking category to continue.
B. Set the phishing category to override.
C. Set the malware category to block.
D. Set the Command and Control category to block.
What allows a security administrator to preview the Security policy rules that match new application signatures?
A. Policy Optimizer–New App Viewer
B. Dynamic Updates–Review App
C. Review Release Notes
D. Dynamic Updates–Review Policies
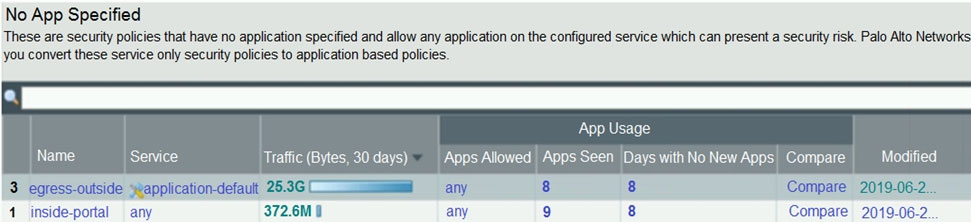
Based on the screenshot presented, which column contains the link that when clicked, opens a window to display all applications matched to the policy rule?
A. Apps Allowed
B. Service
C. Name
D. Apps Seen
Why should a company have a File Blocking profile that is attached to a Security policy?
A. To block uploading and downloading of any type of files
B. To block uploading and downloading of specific types of files
C. To detonate files in a sandbox environment
D. To analyze file types
When HTTPS for management and GlobalProtect are enabled on the same interface, which TCP port is used for management access?
A. 80
B. 8443
C. 4443
D. 443
When is the content inspection performed in the packet flow process?
A. after the application has been identified
B. after the SSL Proxy re-encrypts the packet
C. before the packet forwarding process
D. before session lookup
Which information is included in device state other than the local configuration?
A. uncommitted changes
B. audit logs to provide information of administrative account changes
C. system logs to provide information of PAN-OS changes
D. device group and template settings pushed from Panorama
How many zones can an interface be assigned with a Palo Alto Networks firewall?
A. two
B. three
C. four
D. one
You receive notification about new malware that infects hosts through malicious files transferred by FTP. Which Security profile detects and protects your internal networks from this threat after you update your firewall’s threat signature database?
A. Data Filtering profile applied to outbound Security policy rules.
B. Vulnerability Protection profile applied to outbound Security policy rules.
C. URL Filtering profile applied to inbound Security policy rules.
D. Antivirus profile applied to inbound Security policy rules.
After making multiple changes to the candidate configuration of a firewall, the administrator would like to start over with a candidate configuration that matches the running configuration. Which command in Device > Setup > Operations would provide the most operationally efficient way to accomplish this?
A. Revert to running configuration
B. Load named configuration snapshot
C. Revert to last saved configuration
D. Import named config snapshot
Which two statements correctly describe how pre-rules and local device rules are viewed and modified? (Choose two.)
A. Pre-rules can be modified by the local administrator or by a Panorama administrator who has switched to a local firewall.
B. Pre-rules and local device rules can be modified in Panorama.
C. Pre-rules can be viewed on managed firewalls.
D. Pre-rules are modified in Panorama only, and local device rules are modified on local firewalls only.
Which two features implement one-to-one translation of a source IP address while allowing the source port to change? (Choose two.)
A. Dynamic IP
B. Dynamic IP and Port (DIPP)
C. Static IP
D. Dynamic IP / Port Fallback
To protect against illegal code execution, which Security profile should be applied?
A. Antivirus profile on allowed traffic
B. Antivirus profile on denied traffic
C. Vulnerability Protection profile on allowed traffic
D. Vulnerability Protection profile on denied traffic
Which two rule types allow the administrator to modify the destination zone? (Choose two.)
A. interzone
B. shadowed
C. intrazone
D. universal
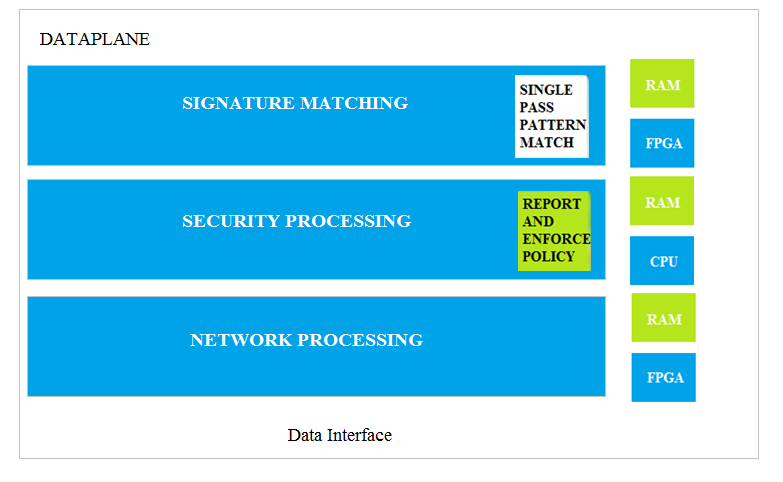
Which dataplane layer of the graphic shown provides pattern protection for spyware and vulnerability exploits on a Palo Alto Networks Firewall?
A. Signature Matching
B. Network Processing
C. Security Processing
D. Data Interfaces
What are the two ways to implement an exception to an external dynamic list? (Choose two.)
A. Edit the external dynamic list by removing the entries to exclude.
B. Select the entries to exclude from the List Entries list.
C. Manually add an entry to the Manual Exceptions list.
D. Edit the external dynamic list by adding the “-“ symbol before the entries to exclude.
Recently changes were made to the firewall to optimize the policies and the security team wants to see if those changes are helping. What is the quickest way to reset the hit counter to zero in all the security policy rules?
A. At the CLI enter the command reset rules and press Enter
B. Highlight a rule and use the Reset Rule Hit Counter > Selected Rules for each rule
C. Reboot the firewall
D. Use the Reset Rule Hit Counter > All Rules option
Which object would an administrator create to enable access to all applications in the office-programs subcategory?
A. HIP profile
B. URL category
C. application group
D. application filter
What is used to monitor Security policy applications and usage?
A. Security profile
B. App-ID
C. Policy-based forwarding
D. Policy Optimizer
All users from the internal zone must be allowed only Telnet access to a server in the DMZ zone. Complete the two empty fields in the Security policy rules that permits only this type of access. Source Zone: Internal - Destination Zone: DMZ Zone - Application: _________? Service: ____________? Action: allow - (Choose two.)
A. Service = ג€application-defaultג€
B. Service = ג€service-telnetג€
C. Application = ג€Telnetג€
D. Application = ג€anyג€
To use Active Directory to authenticate administrators, which server profile is required in the authentication profile?
A. domain controller
B. TACACS+
C. LDAP
D. RADIUS
Within the WildFire Analysis profile, which three items are configurable? (Choose three.)
A. FileType
B. Direction
C. Service
D. Application
E. Objects
Which User-ID agent would be appropriate in a network with multiple WAN links, limited network bandwidth, and limited firewall management plane resources?
A. Windows-based agent deployed on the internal network
B. PAN-OS integrated agent deployed on the internal network
C. Citrix terminal server deployed on the internal network
D. Windows-based agent deployed on each of the WAN Links
You receive notification about a new malware that infects hosts. An infection results in the infected host attempting to contact a command-and-control server. Which Security Profile detects and prevents this threat from establishing a command-and-control connection?
A. Vulnerability Protection Profile applied to outbound Security policy rules.
B. Anti-Spyware Profile applied to outbound security policies.
C. Antivirus Profile applied to outbound Security policy rules
D. Data Filtering Profile applied to outbound Security policy rules.
Which two protocols are available on a Palo Alto Networks Firewall Interface Management Profile? (Choose two.)
A. HTTPS
B. RDP
C. SCP
D. SSH
Which stage of the cyber attack lifecycle makes it important to provide ongoing education to users on spear phishing links, unknown emails, and risky websites?
A. reconnaissance
B. delivery
C. installation
D. exploitation
What is the default action for the SYN Flood option within the DoS Protection profile?
A. Reset-client
B. Alert
C. Sinkhole
D. Random Early Drop
In a Security policy, what is the quickest way to reset all policy rule hit counters to zero?
A. Highlight each rule and use the Reset Rule Hit Counter > Selected Rules
B. Reboot the firewall
C. Use the Reset Rule Hit Counter > All Rules option
D. Use the CLI enter the command reset rules all
An administrator wants to filter access to www.paloaltonetworks.com via a custom URL category. Which syntax would match this?
A. https://paloaltonetworks.com
B. #.paloaltonetworks.com
C. http://paloaltonetworks.com
D. *.paloaltonetworks.com
What are three valid ways to map an IP address to a username? (Choose three.)
A. a user connecting into a GlobalProtect gateway using a GlobalProtect Agent
B. WildFire verdict reports
C. DHCP Relay logs
D. using the XML API
E. usernames inserted inside HTTP Headers
Palo Alto Networks firewall architecture accelerates content inspection performance while minimizing latency using which two components? (Choose two.)
A. Network Processing Engine
B. Policy Engine
C. Parallel Processing Hardware
D. Single Stream-based Engine
An administrator is configuring a NAT rule. At a minimum, which three forms of information are required? (Choose three.)
A. source zone
B. name
C. destination interface
D. destination zone
E. destination address
Which Security profile must be added to Security policies to enable DNS Signatures to be checked?
A. URL Filtering
B. Vulnerability Protection
C. Anti-Spyware
D. Antivirus
What are two differences between an implicit dependency and an explicit dependency in App-ID? (Choose two.)
A. An implicit dependency does not require the dependent application to be added in the security policy
B. An implicit dependency requires the dependent application to be added in the security policy
C. An explicit dependency does not require the dependent application to be added in the security policy
D. An explicit dependency requires the dependent application to be added in the security policy
Which verdict may be assigned to a WildFire sample?
A. Phishing
B. Spyware
C. PUP
D. Malware
An administrator is trying to implement an exception to an external dynamic list manually. Some entries are shown underlined in red. What would cause this error?
A. Entries contain symbols.
B. Entries are wildcards.
C. Entries contain regular expressions.
D. Entries are duplicated.
Free Access Full PCNSA Practice Test Free Questions
If you’re looking for more PCNSA practice test free questions, click here to access the full PCNSA practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your PCNSA certification journey!