PCNSA Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your PCNSA certification exam? Start your preparation the smart way with our PCNSA Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for PCNSA exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our PCNSA Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
The NetSec Manager asked to create a new firewall Local Administrator profile with customized privileges named New_Admin. This new administrator has to authenticate without inserting any username or password to access the WebUI. What steps should the administrator follow to create the New_Admin Administrator profile?
A. 1. Set the Authentication profile to Local.2. Select the “Use only client certificate authentication” check box.3. Set Role to Role Based.
B. 1. Select the “Use only client certificate authentication” check box.2. Set Role to Dynamic.3. Issue to the Client a Certificate with Certificate Name = New Admin
C. 1. Select the “Use only client certificate authentication” check box.2. Set Role to Dynamic.3. Issue to the Client a Certificate with Common Name = New_Admin
D. 1. Select the “Use only client certificate authentication” check box.2. Set Role to Role Based.3. Issue to the Client a Certificate with Common Name = New Admin
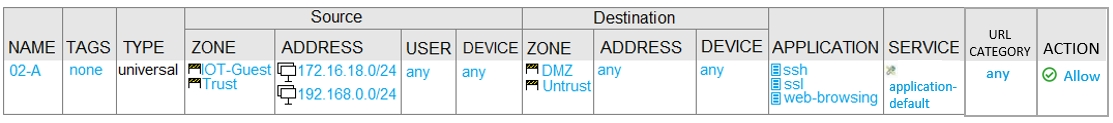
View the diagram. What is the most restrictive, yet fully functional rule, to allow general Internet and SSH traffic into both the DMZ and Untrust/Internet zones from each of the IOT/Guest and Trust Zones? A.
B.
C.
D.
Which action would an administrator take to ensure that a service object will be available only to the selected device group?
A. ensure that disable override is selected
B. uncheck the shared option
C. ensure that disable override is cleared
D. create the service object in the specific template
Which two configurations does an administrator need to compare in order to see differences between the active configuration and potential changes if committed? (Choose two.)
A. Device state
B. Active
C. Candidate
D. Running
At which point in the App-ID update process can you determine if an existing policy rule is affected by an App-ID update?
A. after clicking Check Now in the Dynamic Update window
B. after committing the firewall configuration
C. after installing the update
D. after downloading the update
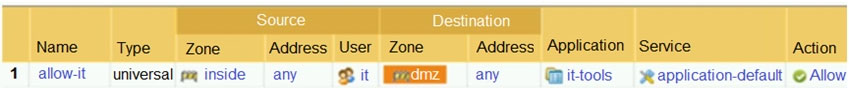
An administrator is reviewing the Security policy rules shown in the screenshot below. Which statement is correct about the information displayed?
A. Highlight Unused Rules is checked.
B. There are seven Security policy rules on this firewall.
C. The view Rulebase as Groups is checked.
D. Eleven rules use the “Infrastructure” tag.
Which rule type is appropriate for matching traffic occurring within a specified zone?
A. Universal
B. Shadowed
C. Intrazone
D. Interzone
By default, which action is assigned to the interzone-default rule?
A. Allow
B. Deny
C. Reset-client
D. Reset-server
What is used to monitor Security policy applications and usage?
A. Security profile
B. App-ID
C. Policy-based forwarding
D. Policy Optimizer
By default, what is the maximum number of templates that can be added to a template stack?
A. 6
B. 8
C. 10
D. 12
Which plane on a Palo Alto Networks Firewall provides configuration, logging, and reporting functions on a separate processor?
A. management
B. network processing
C. data
D. security processing
An administrator needs to allow users to use only certain email applications. How should the administrator configure the firewall to restrict users to specific email applications?
A. Create an application filter and filter it on the collaboration category.
B. Create an application filter and filter it on the collaboration category, email subcategory.
C. Create an application group and add the email applications to it.
D. Create an application group and add the email category to it.
Where in Panorama would Zone Protection profiles be configured?
A. Templates
B. Device Groups
C. Shared
D. Panorama tab
In order to fulfill the corporate requirement to backup the configuration of Panorama and the Panorama-managed firewalls securely, which protocol should you select when adding a new scheduled config export?
A. HTTPS
B. SMB v3
C. SCP
D. FTP
An administrator would like to use App-ID's deny action for an application and would like that action updated with dynamic updates as new content becomes available. Which security policy action causes this?
A. Reset server
B. Reset both
C. Deny
D. Drop
Based on the screenshot, what is the purpose of the Included Groups?
A. They are groups that are imported from RADIUS authentication servers.
B. They are the only groups visible based on the firewall’s credentials.
C. They contain only the users you allow to manage the firewall.
D. They are used to map users to groups.
In which profile should you configure the DNS Security feature?
A. Anti-Spyware Profile
B. Zone Protection Profile
C. Antivirus Profile
D. URL Filtering Profile
What are three valid information sources that can be used when tagging users to dynamic user groups? (Choose three.)
A. firewall logs
B. custom API scripts
C. Security Information and Event Management Systems (SIEMS), such as Splunk
D. biometric scanning results from iOS devices
E. DNS Security service
Palo Alto Networks firewall architecture accelerates content inspection performance while minimizing latency using which two components? (Choose two.)
A. Network Processing Engine
B. Policy Engine
C. Parallel Processing Hardware
D. Single Stream-based Engine
What is a prerequisite before enabling an administrative account which relies on a local firewall user database?
A. Configure an authentication profile.
B. Configure an authentication sequence.
C. Isolate the management interface on a dedicated management VLAN.
D. Configure an authentication policy.
Refer to the exhibit. A web server in the DMZ is being mapped to a public address through DNAT.Which Security policy rule will allow traffic to flow to the web server?
A. Untrust (any) to DMZ (10.1.1.100), web browsing – Allow
B. Untrust (any) to Untrust (1.1.1.100), web browsing – Allow
C. Untrust (any) to Untrust (10.1.1.100), web browsing – Allow
D. Untrust (any) to DMZ (1.1.1.100), web browsing – Allow
In which threat profile object would you configure the DNS Security service?
A. Antivirus
B. Anti-Spyware
C. WildFire
D. URL Filtering
Which path is used to save and load a configuration with a Palo Alto Networks firewall?
A. Device>Setup>Services
B. Device>Setup>Management
C. Device>Setup>Operations
D. Device>Setup>Interfaces
Selecting the option to revert firewall changes will replace what settings?
A. the candidate configuration with settings from the running configuration
B. dynamic update scheduler settings
C. the running configuration with settings from the candidate configuration
D. the device state with settings from another configuration
An administrator is reviewing the Security policy rules shown in the screenshot. Why are the two fields in the Security policy EDL-Deny highlighted in red?
A. Because antivirus inspection is enabled for this policy
B. Because the destination zone, address, and device are all “any”
C. Because the action is Deny
D. Because the Security-EDL tag has been assigned the red color
According to best practices, how frequently should WildFire updates he made to perimeter firewalls?
A. every 10 minutes
B. every minute
C. every 5 minutes
D. in real time
The compliance officer requests that all evasive applications need to be blocked on all perimeter firewalls out to the internet. The firewall is configured with two zones: 1. trust for internal networks 2. untrust to the internet Based on the capabilities of the Palo Alto Networks NGFW, what are two ways to configure a security policy using App-ID to comply with this request? (Choose two.)
A. Create a deny rule at the top of the policy from trust to untrust with service application-default and add an application filter with the evasive characteristic
B. Create a deny rule at the top of the policy from trust to untrust over any service and select evasive as the application
C. Create a deny rule at the top of the policy from trust to untrust with service application-default and select evasive as the application
D. Create a deny rule at the top of the policy from trust to untrust over any service and add an application filter with the evasive characteristic
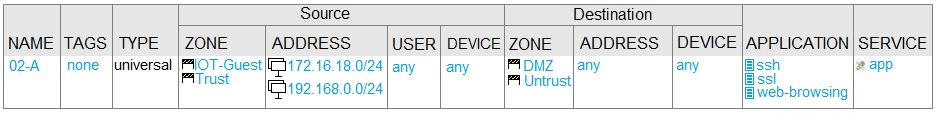
Given the network diagram, traffic should be permitted for both Trusted and Guest users to access general Internet and DMZ servers using SSH, web-browsing and SSL applications. Which policy achieves the desired results? A.
B.
C.
D.
The CFO found a USB drive in the parking lot and decide to plug it into their corporate laptop. The USB drive had malware on it that loaded onto their computer and then contacted a known command and control (CnC) server, which ordered the infected machine to begin Exfiltrating data from the laptop. Which security profile feature could have been used to prevent the communication with the CnC server?
A. Create an anti-spyware profile and enable DNS Sinkhole
B. Create an antivirus profile and enable DNS Sinkhole
C. Create a URL filtering profile and block the DNS Sinkhole category
D. Create a security policy and enable DNS Sinkhole
Review the screenshot below. Based on the information it contains, which protocol decoder will detect a machine-learning match, create a Threat log entry, and permit the traffic?
A. smb
B. imap
C. ftp
D. http2
An administrator is troubleshooting an issue with an accounts payable application. Which log setting could be temporarily configured to improve visibility?
A. Log at Session Start and Log at Session End both enabled
B. Log at Session Start and Log at Session End both disabled
C. Log at Session Start enabled, Log at Session End disabled
D. Log at Session Start disabled, Log at Session End enabled
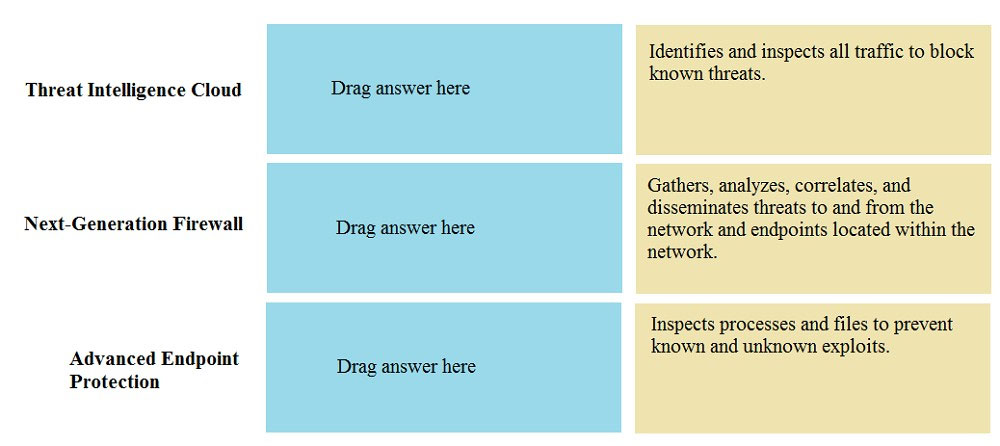
DRAG DROP - Match the Palo Alto Networks Security Operating Platform architecture to its description. Select and Place:
What do you configure if you want to set up a group of objects based on their ports alone?
A. address groups
B. custom objects
C. application groups
D. service groups
Which security profile should be used to classify malicious web content?
A. URL Filtering
B. Web Content
C. Antivirus
D. Vulnerability Protection
Which System log severity level would be displayed as a result of a user password change?
A. Low
B. Medium
C. High
D. Critical
An administrator is implementing an exception to an external dynamic list by adding an entry to the list manually. The administrator wants to save the changes, but the OK button is grayed out. What are two possible reasons the OK button is grayed out? (Choose two.)
A. The entry matches a list entry.
B. The entry doesn’t match a list entry.
C. The entry contains wildcards.
D. The entry is duplicated.
What can be used as match criteria for creating a dynamic address group?
A. MAC addresses
B. IP addresses
C. Usernames
D. Tags
Which link in the web interface enables a security administrator to view the Security policy rules that match new application signatures?
A. Review App Matches
B. Review Apps
C. Pre-analyze
D. Review Policies
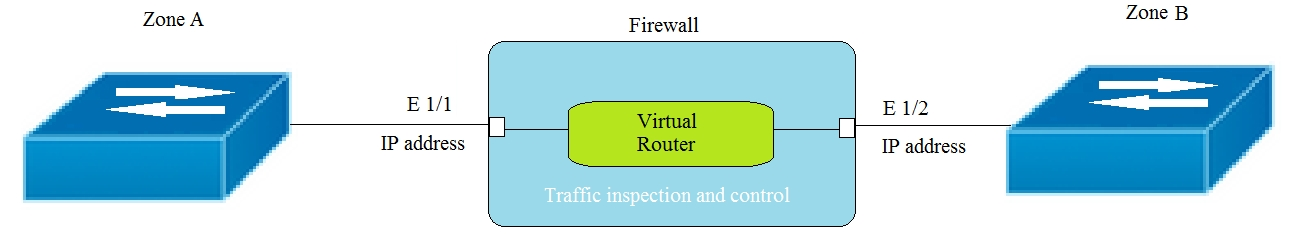
The Palo Alto Networks NGFW was configured with a single virtual router named VR-1. What changes are required on VR-1 to route traffic between two interfaces on the NGFW?
A. Add static routes to route between the two interfaces
B. Add interfaces to the virtual router
C. Add zones attached to interfaces to the virtual router
D. Enable the redistribution profile to redistribute connected routes
Which data flow direction is protected in a zero-trust firewall deployment that is not protected in a perimeter-only firewall deployment?
A. north-south
B. inbound
C. outbound
D. east-west
An administrator would like to protect against inbound threats such as buffer overflows and illegal code execution. Which Security profile should be used?
A. Vulnerability protection
B. Anti-spyware
C. URL filtering
D. Antivirus
An administrator reads through the following Applications and Threats Content Release Notes before an update:Which rule would continue to allow the file upload to confluence after the update?
A.

B.

C.

D.

Given the topology, which zone type should zone A and zone B to be configured with?
A. Layer3
B. Ethernet
C. Layer2
D. Virtual Wire
Which Security profile can be used to detect and block compromised hosts from trying to communicate with external command-and-control (C2) servers?
A. URL Filtering
B. Antivirus
C. Vulnerability
D. Anti-Spyware
A network administrator is required to use a dynamic routing protocol for network connectivity. Which three dynamic routing protocols are supported by the NGFW Virtual Router for this purpose? (Choose three.)
A. OSPF
B. EIGRP
C. IS-IS
D. BGP
E. RIP
When creating an address object, which option is available to select from the Type drop-down menu?
A. IPv6 Address
B. IP Netmask
C. IPv4 Address
D. IP Address Class
In which section of the PAN-OS GUI does an administrator configure URL Filtering profiles?
A. Network
B. Policies
C. Objects
D. Device
A company moved its old port-based firewall to a new Palo Alto Networks NGFW 60 days ago. Which utility should the company use to identify out-of-date or unused rules on the firewall?
A. Rule Usage Filter > No App Specified
B. Rule Usage Filter >Hit Count > Unused in 30 days
C. Rule Usage Filter > Unused Apps
D. Rule Usage Filter > Hit Count > Unused in 90 days
Which statement is true regarding a Best Practice Assessment?
A. It runs only on firewalls.
B. It shows how current configuration compares to Palo Alto Networks recommendations.
C. When guided by an authorized sales engineer, it helps determine the areas of greatest risk where you should focus prevention activities.
D. It provides a set of questionnaires that help uncover security risk prevention gaps across all areas of network and security architecture.
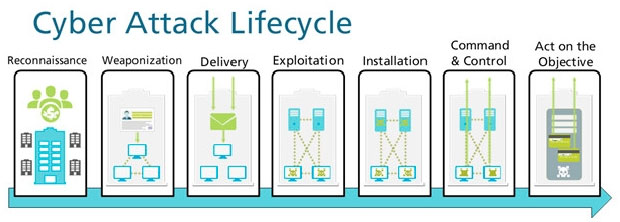
Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can run malicious code against a targeted machine.
A. Exploitation
B. Installation
C. Reconnaissance
D. Act on Objective
Access Full PCNSA Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete PCNSA Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our PCNSA mock test free today—and take a major step toward exam success!