PCNSA Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the PCNSA certification? Our PCNSA Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective PCNSA exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic PCNSA Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
Which security profile should be used to classify malicious web content?
A. URL Filtering
B. Web Content
C. Antivirus
D. Vulnerability Protection
Which object would an administrator create to enable access to all applications in the office-programs subcategory?
A. HIP profile
B. URL category
C. application group
D. application filter
Which two statements are correct about App-ID content updates? (Choose two.)
A. Updated application content might change how Security policy rules are enforced.
B. After an application content update, new applications must be manually classified prior to use.
C. Existing security policy rules are not affected by application content updates.
D. After an application content update, new applications are automatically identified and classified.
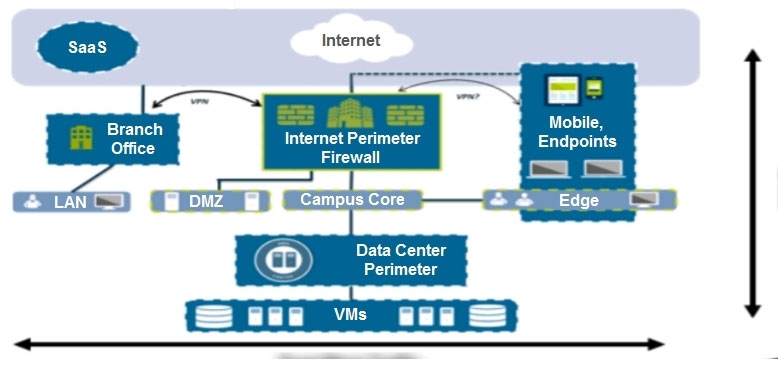
Given the network diagram, which two statements are true about traffic between the User and Server networks? (Choose two.)
A. Traffic is permitted through the default Intrazone “allow” rule.
B. Traffic restrictions are not possible because the networks are in the same zone.
C. Traffic is permitted through the default Interzone “allow” rule.
D. Traffic restrictions are possible by modifying Intrazone rules.
An administrator is troubleshooting traffic that should match the interzone-default rule. However, the administrator doesn't see this traffic in the traffic logs on the firewall. The interzone-default was never changed from its default configuration. Why doesn't the administrator see the traffic?
A. The interzone-default policy is disabled by default.
B. Traffic is being denied on the interzone-default policy.
C. Logging on the interzone-default policy is disabled.
D. The Log Forwarding profile is not configured on the policy.
An administrator wants to prevent users from submitting corporate credentials in a phishing attack. Which Security profile should be applied?
A. antivirus
B. anti-spyware
C. URL-filtering
D. vulnerability protection
An administrator notices that protection is needed for traffic within the network due to malicious lateral movement activity. Based on the image shown, which traffic would the administrator need to monitor and block to mitigate the malicious activity?
A. branch office traffic
B. north-south traffic
C. perimeter traffic
D. east-west traffic
Which two configurations does an administrator need to compare in order to see differences between the active configuration and potential changes if committed? (Choose two.)
A. Device state
B. Active
C. Candidate
D. Running
An administrator is troubleshooting an issue with Office365 and expects that this traffic traverses the firewall. When reviewing Traffic Log entries, there are no logs matching traffic from the test workstation. What might cause this issue?
A. Office365 traffic is logged in the System Log.
B. Office365 traffic is logged in the Authentication Log.
C. Traffic matches the interzone-default rule, which does not log traffic by default.
D. The firewall is blocking the traffic, and all blocked traffic is in the Threat Log.
What are two valid selections within an Antivirus profile? (Choose two.)
A. deny
B. drop
C. block-ip
D. default
Which file is used to save the running configuration with a Palo Alto Networks firewall?
A. running-config.xml
B. run-config.xml
C. running-configuration.xml
D. run-configuration.xml
To enable DNS sinkholing, which two addresses should be reserved? (Choose two.)
A. MAC
B. IPv6
C. Email
D. IPv4
When is an event displayed under threat logs?
A. When traffic matches a corresponding Security Profile
B. When traffic matches any Security policy
C. Every time a session is blocked
D. Every time the firewall drops a connection
URL categories can be used as match criteria on which two policy types? (Choose two.)
A. authentication
B. decryption
C. application override
D. NAT
Which component is a building block in a Security policy rule?
A. decryption profile
B. destination interface
C. timeout (min)
D. application
What is a prerequisite before enabling an administrative account which relies on a local firewall user database?
A. Configure an authentication profile.
B. Configure an authentication sequence.
C. Isolate the management interface on a dedicated management VLAN.
D. Configure an authentication policy.
Which two features can be used to tag a username so that it is included in a dynamic user group? (Choose two.)
A. GlobalProtect agent
B. XML API
C. User-ID Windows-based agent
D. log forwarding auto-tagging
Which type of administrator account cannot be used to authenticate user traffic flowing through the firewall's data plane?
A. Kerberos user
B. SAML user
C. local database user
D. local user
An administrator is reviewing the Security policy rules shown in the screenshot below. Which statement is correct about the information displayed?
A. Highlight Unused Rules is checked.
B. There are seven Security policy rules on this firewall.
C. The view Rulebase as Groups is checked.
D. Eleven rules use the “Infrastructure” tag.
How can a complete overview of the logs be displayed to an administrator who has permission in the system to view them?
A. Select the unified log entry in the side menu.
B. Modify the number of columns visible on the page.
C. Modify the number of logs visible on each page.
D. Select the system logs entry in the side menu.
Which operations are allowed when working with App-ID application tags?
A. Predefined tags may be deleted.
B. Predefined tags may be augmented by custom tags.
C. Predefined tags may be modified.
D. Predefined tags may be updated by WildFire dynamic updates.
Your company occupies one floor in a single building. You have two Active Directory domain controllers on a single network. The firewall's management plane is only slightly utilized. Which User-ID agent is sufficient in your network?
A. Windows-based agent deployed on each domain controller
B. PAN-OS integrated agent deployed on the firewall
C. Citrix terminal server agent deployed on the network
D. Windows-based agent deployed on the internal network a domain member
Which interface types are assigned to IEEE 802.1Q VLANs?
A. Tunnel interfaces
B. Layer 2 subinterfaces
C. Layer 3 subinterfaces
D. Loopback interfaces
Starting with PAN-OS version 9.1, application dependency information is now reported in which two locations? (Choose two.)
A. on the App Dependency tab in the Commit Status window
B. on the Policy Optimizer’s Rule Usage page
C. on the Application tab in the Security Policy Rule creation window
D. on the Objects > Applications browser pages
You receive notification about new malware that infects hosts through malicious files transferred by FTP. Which Security profile detects and protects your internal networks from this threat after you update your firewall’s threat signature database?
A. Data Filtering profile applied to outbound Security policy rules.
B. Vulnerability Protection profile applied to outbound Security policy rules.
C. URL Filtering profile applied to inbound Security policy rules.
D. Antivirus profile applied to inbound Security policy rules.
Prior to a maintenance-window activity, the administrator would like to make a backup of only the running configuration to an external location. What command in Device > Setup > Operations would provide the most operationally efficient way to achieve this outcome?
A. export named configuration snapshot
B. save named configuration snapshot
C. export device state
D. save candidate config
Which path in PAN-OS 10.2 is used to schedule a content update to managed devices using Panorama?
A. Panorama > Device Deployment > Dynamic Updates > Schedules > Add
B. Panorama > Device Deployment > Content Updates > Schedules > Add
C. Panorama > Dynamic Updates > Device Deployment > Schedules > Add
D. Panorama > Content Updates > Device Deployment > Schedules > Add
When an ethernet interface is configured with an IPv4 address, which type of zone is it a member of?
A. Layer 3
B. Virtual Wire
C. Tap
D. Tunnel
An administrator wants to prevent hacking attacks through DNS queries to malicious domains. Which two DNS policy actions can the administrator choose in the Anti-Spyware Security Profile? (Choose two.)
A. deny
B. block
C. sinkhole
D. override
Which type of DNS signatures are used by the firewall to identify malicious and command-and-control domains?
A. DNS Malicious signatures
B. DNS Security signatures
C. DNS Malware signatures
D. DNS Block signatures
What are two differences between an application group and an application filter? (Choose two.)
A. Application groups enable access to sanctioned applications explicitly, while application filters enable access to sanctioned applications implicitly.
B. Application groups are static, while application filters are dynamic.
C. Application groups dynamically group applications based on attributes, while application filters contain applications that are statically grouped.
D. Application groups can be added to application filters, while application filters cannot be added to application groups.
In which section of the PAN-OS GUI does an administrator configure URL Filtering profiles?
A. Network
B. Policies
C. Objects
D. Device
An administrator needs to create a Security policy rule that matches DNS traffic within the LAN zone, and also needs to match DNS traffic within the DMZ zone. The administrator does not want to allow traffic between the DMZ and LAN zones. Which Security policy rule type should they use?
A. interzone
B. intrazone
C. default
D. universal
What is the main function of Policy Optimizer?
A. reduce load on the management plane by highlighting combinable security rules
B. migrate other firewall vendors’ security rules to Palo Alto Networks configuration
C. eliminate ג€Log at Session Startג€ security rules
D. convert port-based security rules to application-based security rules
Identify the correct order to configure the PAN-OS integrated USER-ID agent. 3. add the service account to monitor the server(s) 2. define the address of the servers to be monitored on the firewall 4. commit the configuration, and verify agent connection status 1. create a service account on the Domain Controller with sufficient permissions to execute the User- ID agent
A. 2-3-4-1
B. 1-4-3-2
C. 3-1-2-4
D. 1-3-2-4
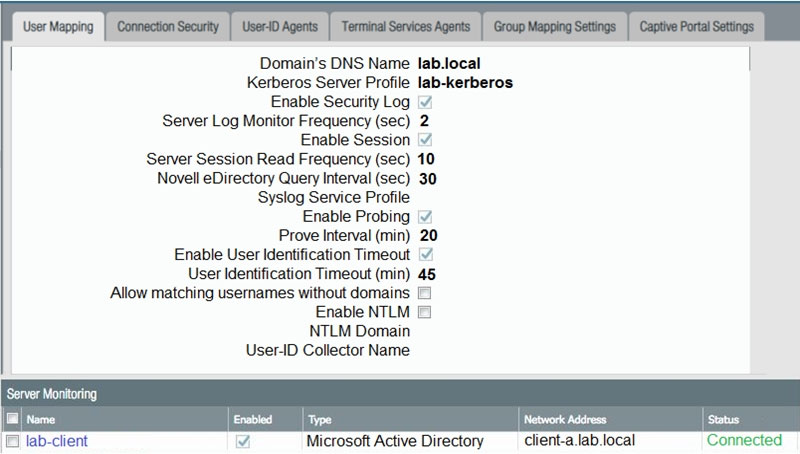
Based on the graphic, which statement accurately describes the output shown in the Server Monitoring panel?
A. The User-ID agent is connected to a domain controller labeled lab-client.
B. The host lab-client has been found by the User-ID agent.
C. The host lab-client has been found by a domain controller.
D. The User-ID agent is connected to the firewall labeled lab-client.
An administrator has configured a Security policy where the matching condition includes a single application, and the action is drop. If the application's default deny action is reset-both, what action does the firewall take?
A. It silently drops the traffic.
B. It silently drops the traffic and sends an ICMP unreachable code.
C. It sends a TCP reset to the server-side device.
D. It sends a TCP reset to the client-side and server-side devices.
An administrator is creating a Security policy rule and sees that the destination zone is grayed out. While creating the rule, which option was selected to cause this?
A. Interzone
B. Source zone
C. Universal (default)
D. Intrazone
Where within the URL Filtering security profile must a user configure the action to prevent credential submissions?
A. URL Filtering > Categories
B. URL Filtering > URL Filtering Settings
C. URL Filtering > Inline Categorization
D. URL Filtering > HTTP Header Insertion
The compliance officer requests that all evasive applications need to be blocked on all perimeter firewalls out to the internet. The firewall is configured with two zones: 1. trust for internal networks 2. untrust to the internet Based on the capabilities of the Palo Alto Networks NGFW, what are two ways to configure a security policy using App-ID to comply with this request? (Choose two.)
A. Create a deny rule at the top of the policy from trust to untrust with service application-default and add an application filter with the evasive characteristic
B. Create a deny rule at the top of the policy from trust to untrust over any service and select evasive as the application
C. Create a deny rule at the top of the policy from trust to untrust with service application-default and select evasive as the application
D. Create a deny rule at the top of the policy from trust to untrust over any service and add an application filter with the evasive characteristic
At which stage of the Cyber-Attack Lifecycle would the attacker attach an infected PDF file to an email?
A. Delivery
B. Reconnaissance
C. Command and Control
D. Exploitation
How are Application Filters or Application Groups used in firewall policy?
A. An Application Group is a static way of grouping applications and cannot be configured as a nested member of Application Group.
B. An Application Group is a dynamic way of grouping applications and can be configured as a nested member of an Application Group.
C. An Application Filter is a dynamic way to group applications and can be configured as a nested member of an Application Group.
D. An Application Filter is a static way of grouping applications and can be configured as a nested member of an Application Group.
By default, which action is assigned to the interzone-default rule?
A. Allow
B. Deny
C. Reset-client
D. Reset-server
The PowerBall Lottery has reached an unusually high value this week. Your company has decided to raise morale by allowing employees to access the PowerBall Lottery website (www.powerball.com) for just this week. However, the company does not want employees to access any other websites also listed in the URL filtering `gambling` category. Which method allows the employees to access the PowerBall Lottery website but without unblocking access to the `gambling` URL category?
A. Add just the URL www.powerball.com to a Security policy allow rule.
B. Manually remove powerball.com from the gambling URL category.
C. Add *.powerball.com to the URL Filtering allow list.
D. Create a custom URL category, add *.powerball.com to it and allow it in the Security Profile.
An administrator needs to add capability to perform real time signature lookups to block or sinkhole all known malware domains. Which type of single, unified engine will get this result?
A. Content ID
B. App-ID
C. Security Processing Engine
D. User-ID
Which URL Filtering Profile action does not generate a log entry when a user attempts to access a URL?
A. Override
B. Allow
C. Block
D. Continue
For the firewall to use Active Directory to authenticate users, which Server Profile is required in the Authentication Profile?
A. TACACS+
B. RADIUS
C. LDAP
D. SAML
An administrator needs to allow users to use only certain email applications. How should the administrator configure the firewall to restrict users to specific email applications?
A. Create an application filter and filter it on the collaboration category.
B. Create an application filter and filter it on the collaboration category, email subcategory.
C. Create an application group and add the email applications to it.
D. Create an application group and add the email category to it.
How many zones can an interface be assigned with a Palo Alto Networks firewall?
A. two
B. three
C. four
D. one
Which statement applies to the Intrazone Security policy rule?
A. The traffic within the same security zone will not be allowed.
B. It requires a Zone Protection profile to be applied.
C. It applies regardless of whether it is from the same security zone or a different one.
D. It applies to all matching traffic within the specified source security zones.
Access Full PCNSA Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of PCNSA exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your PCNSA certification journey!