PCNSA Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your PCNSA certification? Our PCNSA Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an PCNSA dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our PCNSA Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
What are three characteristics of the Palo Alto Networks DNS Security service? (Choose three.)A. It requires an active subscription to a third-party DNS Security service
B. It requires a valid URL Filtering license
C. It uses techniques such as DGA/DNS tunneling detection and machine learning
D. It requires a valid Threat Prevention license
E. It enables users to access real-time protections using advanced predictive analytics
What allows a security administrator to preview the Security policy rules that match new application signatures?A. Policy Optimizer--New App Viewer
B. Dynamic Updates--Review App
C. Review Release Notes
D. Dynamic Updates--Review Policies
Which object would an administrator create to enable access to all applications in the office-programs subcategory?A. HIP profile
B. URL category
C. application group
D. application filter
What must be considered with regards to content updates deployed from Panorama?A. Content update schedulers need to be configured separately per device group.
B. Panorama can only install up to five content versions of the same type for potential rollback scenarios.
C. A PAN-OS upgrade resets all scheduler configurations for content updates.
D. Panorama can only download one content update at a time for content updates of the same type.
An administrator configured a Security policy rule where the matching condition includes a single application and the action is set to deny.
What deny action will the firewall perform?A. Discard the session’s packets and send a TCP reset packet to let the client know the session has been terminated
B. Drop the traffic silently
C. Perform the default deny action as defined in the App-ID database for the application
D. Send a TCP reset packet to the client- and server-side devices
Which Palo Alto Networks component provides consolidated policy creation and centralized management?A. GlobalProtect
B. Panorama
C. Prisma SaaS
D. AutoFocus
Which DNS Query action is recommended for traffic that is allowed by Security policy and matches Palo Alto Networks Content DNS Signatures?A. block
B. sinkhole
C. allow
D. alert
Which URL Filtering Profile action does not generate a log entry when a user attempts to access a URL?A. Override
B. Allow
C. Block
D. Continue
An administrator has configured a Security policy where the matching condition includes a single application, and the action is drop.
If the application's default deny action is reset-both, what action does the firewall take?A. It silently drops the traffic.
B. It silently drops the traffic and sends an ICMP unreachable code.
C. It sends a TCP reset to the server-side device.
D. It sends a TCP reset to the client-side and server-side devices.
What are the two ways to implement an exception to an external dynamic list? (Choose two.)A. Edit the external dynamic list by removing the entries to exclude.
B. Select the entries to exclude from the List Entries list.
C. Manually add an entry to the Manual Exceptions list.
D. Edit the external dynamic list by adding the “-“ symbol before the entries to exclude.
An administrator would like to override the default deny action for a given application, and instead would like to block the traffic.
Which security policy action causes this?A. Drop
B. Drop, send ICMP Unreachable
C. Reset both
D. Reset client
Your company has 10 Active Directory domain controllers spread across multiple WAN links. All users authenticate to Active Directory. Each link has substantial network bandwidth to support all mission-critical applications. The firewall's management plane is highly utilized.
Given the scenario, which type of User-ID agent is considered a best practice by Palo Alto Networks?A. Windows-based agent on a domain controller
B. Captive Portal
C. Citrix terminal server agent with adequate data-plane resources
D. PAN-OS integrated agent
Which user mapping method could be used to discover user IDs in an environment with multiple Windows domain controllers?A. Active Directory monitoring
B. Windows session monitoring
C. Windows client probing
D. domain controller monitoring
What are two differences between an implicit dependency and an explicit dependency in App-ID? (Choose two.)A. An implicit dependency does not require the dependent application to be added in the security policy
B. An implicit dependency requires the dependent application to be added in the security policy
C. An explicit dependency does not require the dependent application to be added in the security policy
D. An explicit dependency requires the dependent application to be added in the security policy
Given the image, which two options are true about the Security policy rules. (Choose two.)
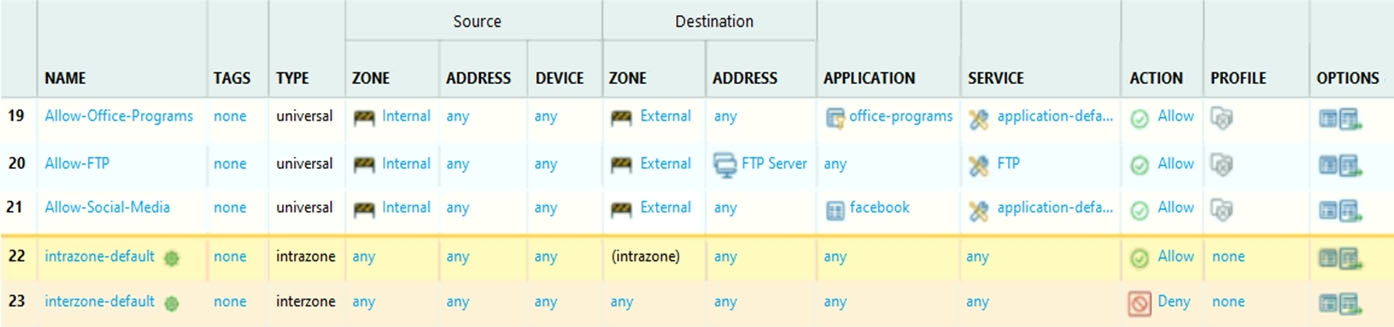
A. The Allow-Office-Programs rule is using an Application Filter.
B. In the Allow-FTP policy, FTP is allowed using App-ID.
C. The Allow-Office-Programs rule is using an Application Group.
D. The Allow-Social-Media rule allows all of Facebook's functions.
Where within the firewall GUI can all existing tags be viewed?A. Policies > Tags
B. Network > Tags
C. Objects > Tags
D. Monitor > Tags
An administrator would like to override the default deny action for a given application, and instead would like to block the traffic.
Which security policy action causes this?A. Drop
B. Drop, send ICMP Unreachable
C. Reset both
D. Reset server
An administrator is trying to implement an exception to an external dynamic list manually. Some entries are shown underlined in red.
What would cause this error?A. Entries contain symbols.
B. Entries are wildcards.
C. Entries contain regular expressions.
D. Entries are duplicated.
You receive notification about new malware that infects hosts through malicious files transferred by FTP.
Which Security profile detects and protects your internal networks from this threat after you update your firewall's threat signature database?A. URL Filtering profile applied to inbound Security policy rules.
B. Data Filtering profile applied to outbound Security policy rules.
C. Antivirus profile applied to inbound Security policy rules.
D. Vulnerability Protection profile applied to outbound Security policy rules.
An administrator is creating a NAT policy.
Which combination of address and zone are used as match conditions? (Choose two.)A. Pre-NAT address
B. Pre-NAT zone
C. Post-NAT address
D. Post-NAT zone
Which interface type is used to monitor traffic and cannot be used to perform traffic shaping?A. Layer 2
B. Tap
C. Layer 3
D. Virtual Wire
Which profile must be applied to the Security policy rule to block spyware on compromised hosts from trying to phone-home or beacon out to external command-and-control (C2) servers?A. Anti-spyware
B. File blocking
C. WildFire
D. URL filtering
How does the Policy Optimizer policy view differ from the Security policy view?A. It provides sorting options that do not affect rule order
B. It specifies applications seen by rules
C. It displays rule utilization
D. It details associated zones
Palo Alto Networks firewall architecture accelerates content inspection performance while minimizing latency using which two components? (Choose two.)A. Network Processing Engine
B. Policy Engine
C. Parallel Processing Hardware
D. Single Stream-based Engine
Which Security profile can be used to configure sinkhole IPs m the DNS Sinkhole settings?A. Vulnerability Protection
B. Anti-Spyware
C. Antivirus
D. URL Filtering
A Panorama administrator would like to create an address object for the DNS server located in the New York City office, but does not want this object added to the other Panorama managed firewalls.
Which configuration action should the administrator take when creating the address object?A. Tag the address object with the New York Office tag.
B. Ensure that Disable Override is cleared.
C. Ensure that the Shared option is checked.
D. Ensure that the Shared option is cleared.
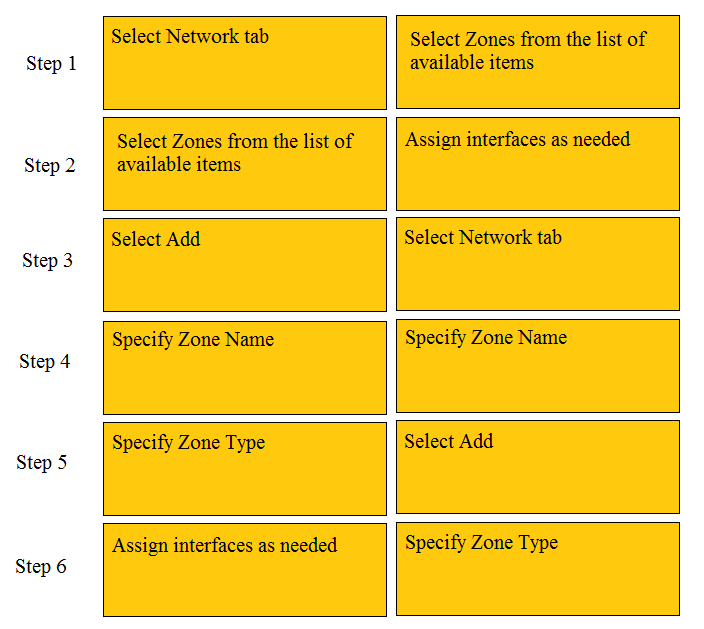
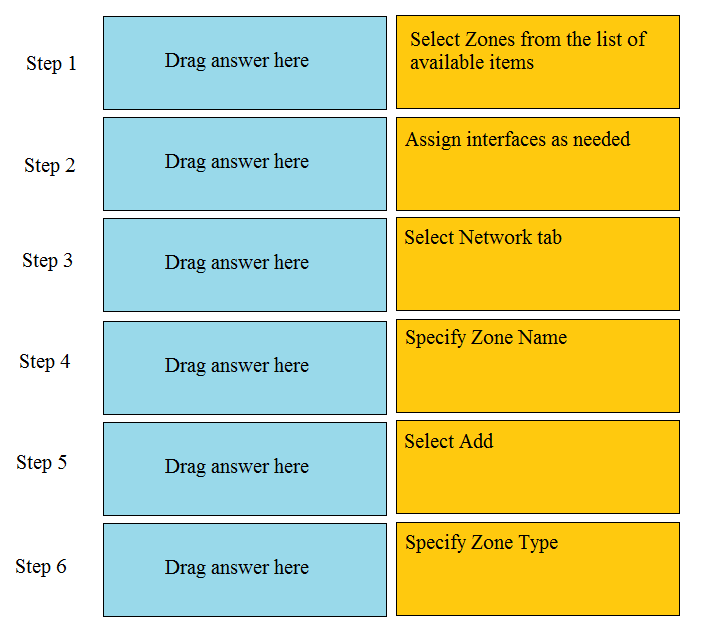
DRAG DROP -
Order the steps needed to create a new security zone with a Palo Alto Networks firewall.
Select and Place:
Which verdict may be assigned to a WildFire sample?A. Phishing
B. Spyware
C. PUP
D. Malware
Prior to a maintenance-window activity, the administrator would like to make a backup of only the running configuration to an external location.
What command in Device > Setup > Operations would provide the most operationally efficient way to achieve this outcome?A. export named configuration snapshot
B. save named configuration snapshot
C. export device state
D. save candidate config
Which tab would an administrator click to create an address object?A. Objects
B. Monitor
C. Device
D. Policies
Which protocol is used to map usernames to user groups when User-ID is configured?A. TACACS+
B. SAML
C. LDAP
D. RADIUS
What is an advantage for using application tags?A. They are helpful during the creation of new zones.
B. They help content updates automate policy updates.
C. They help with the creation of interfaces.
D. They help with the design of IP address allocations in DHCP.
Which three interface deployment methods can be used to block traffic flowing through the Palo Alto Networks firewall? (Choose three.)A. Tap
B. HA
C. Layer 3
D. Layer 2
E. Virtual Wire
Which action should be taken to identify threats that have been detected by using inline cloud analysis?A. Filter Threat logs by Type
B. Filter Threat logs by Application
C. Filter Threat logs by Action
D. Filter Threat logs by Threat Category
Where can you apply URL Filtering policy in a Security policy rule?A. Within the applications selection
B. Within a destination address
C. Within a service type
D. Within the actions tab
A website is unexpectedly allowed due to miscategorization.
What are two ways to resolve this issue for a proper response? (Choose two.)A. Create a URL category and assign the affected URL.Update the active URL Filtering profile site access setting for the custom URL category to block.
B. Review the categorization of the website on https://urlfiltering paloaltonetworks.com.Submit for "request change", identifying the appropriate categorization, and wait for confirmation before testing again.
C. Identify the URL category being assigned to the website.Edit the active URL Filtering profile and update that category's site access settings to block.
D. Create a URL category and assign the affected URL.Add a Security policy with a URL category qualifier of the custom URL category below the original policy.Set the policy action to Deny.
The PowerBall Lottery has reached an unusually high value this week. Your company has decided to raise morale by allowing employees to access the PowerBall
Lottery website (www.powerball.com) for just this week. However, the company does not want employees to access any other websites also listed in the URL filtering `gambling` category.
Which method allows the employees to access the PowerBall Lottery website but without unblocking access to the `gambling` URL category?A. Add just the URL www.powerball.com to a Security policy allow rule.
B. Manually remove powerball.com from the gambling URL category.
C. Add *.powerball.com to the URL Filtering allow list.
D. Create a custom URL category, add *.powerball.com to it and allow it in the Security Profile.
Which Palo Alto Networks component provides consolidated policy creation?A. Policy Optimizer
B. Prisma SaaS
C. GlobalProtect
D. Panorama
Which stage of the cyber attack lifecycle makes it important to provide ongoing education to users on spear phishing links, unknown emails, and risky websites?A. reconnaissance
B. delivery
C. installation
D. exploitation
An administrator is investigating a log entry for a session that is allowed and has the end reason of aged-out.
Which two fields could help in determining if this is normal? (Choose two.)A. IP Protocol
B. Packets sent/received
C. Decrypted
D. Action
What are three valid ways to map an IP address to a username? (Choose three.)A. a user connecting into a GlobalProtect gateway using a GlobalProtect Agent
B. WildFire verdict reports
C. DHCP Relay logs
D. using the XML API
E. usernames inserted inside HTTP Headers
Which link in the web interface enables a security administrator to view the Security policy rules that match new application signatures?A. Review App Matches
B. Review Apps
C. Pre-analyze
D. Review Policies
An administrator would like to determine the default deny action for the application dns-over-https.
Which action would yield the information?A. View the application details in beacon.paloaltonetworks.com
B. Check the action for the Security policy matching that traffic
C. Check the action for the decoder in the antivirus profile
D. View the application details in Objects > Applications
An administrator is troubleshooting an issue with Office365 and expects that this traffic traverses the firewall.
When reviewing Traffic Log entries, there are no logs matching traffic from the test workstation.
What might cause this issue?A. Office365 traffic is logged in the System Log.
B. Office365 traffic is logged in the Authentication Log.
C. Traffic matches the interzone-default rule, which does not log traffic by default.
D. The firewall is blocking the traffic, and all blocked traffic is in the Threat Log.
Which administrator type provides more granular options to determine what the administrator can view and modify when creating an administrator account?A. Root
B. Dynamic
C. Role-based
D. Superuser
Which two statements are correct about App-ID content updates? (Choose two.)A. Updated application content might change how Security policy rules are enforced.
B. After an application content update, new applications must be manually classified prior to use.
C. Existing security policy rules are not affected by application content updates.
D. After an application content update, new applications are automatically identified and classified.
What are the three DNS Security categories available to control DNS traffic? (Choose three.)A. Parked Domains
B. Spyware Domains
C. Vulnerability Domains
D. Phishing Domains
E. Malware Domains
Which User-ID mapping method should be used for an environment with users that do not authenticate to Active Directory?A. Windows session monitoring
B. passive server monitoring using the Windows-based agent
C. Captive Portal
D. passive server monitoring using a PAN-OS integrated User-ID agent
An address object of type IP Wildcard Mask can be referenced in which part of the configuration?A. Security policy rule
B. ACC global fitter
C. NAT address pool
D. external dynamic list
What is the function of an application group object?A. It contains applications that you want to treat similarly in policy
B. It groups applications dynamically based on application attributes that you define
C. It represents specific ports and protocols for an application
D. It identifies the purpose of a rule or configuration object and helps you better organize your rulebase
Access Full PCNSA Dump Free
Looking for even more practice questions? Click here to access the complete PCNSA Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our PCNSA dump free questions — and get one step closer to exam success!