PCCSE Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your PCCSE certification exam? Start your preparation the smart way with our PCCSE Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for PCCSE exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our PCCSE Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
Which two required request headers interface with Prisma Cloud API? (Choose two.)
A. Content-type:application/json
B. x-redlock-auth
C. >x-redlock-request-id
D. Content-type:application/xml
Which three AWS policy types and identities are used to calculate the net effective permissions? (Choose three.)
A. AWS IAM group
B. AWS IAM role
C. AWS service control policies (SCPs)
D. AWS IAM tag policy
E. AWS IAM User
Which statement accurately characterizes SSO Integration on Prisma Cloud?
A. Prisma Cloud supports IdP initiated SSO, and its SAML endpoint supports the POST and GET methods.
B. Okta, Azure Active Directory, PingID, and others are supported via SAML.
C. An administrator can configure different Identity Providers (IdP) for all the cloud accounts that Prisma Cloud monitors.
D. An administrator who needs to access the Prisma Cloud API can use SSO after configuration.
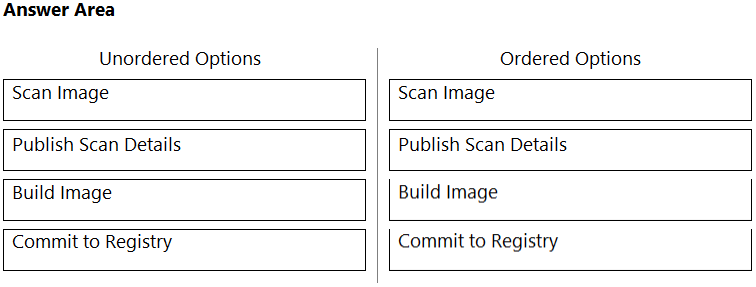
DRAG DROP - Order the steps involved in onboarding an AWS Account for use with Data Security feature. Select and Place:
The Unusual protocol activity (Internal) network anomaly is generating too many alerts. An administrator has been asked to tune it to the option that will generate the least number of events without disabling it entirely. Which strategy should the administrator use to achieve this goal?
A. Disable the policy
B. Set the Alert Disposition to Conservative
C. Change the Training Threshold to Low
D. Set Alert Disposition to Aggressive
The administrator wants to review the Console audit logs from within the Console. Which page in the Console should the administrator use to review this data, if it can be reviewed at all?
A. Navigate to Monitor > Events > Host Log Inspection
B. The audit logs can be viewed only externally to the Console
C. Navigate to Manage > Defenders > View Logs
D. Navigate to Manage > View Logs > History
Which RQL will trigger the following audit event activity?
A. event from cloud.audit_logs where operation = ConsoleLogin AND user = ‘root’
B. event from cloud.audit_logs where cloud.service = ‘s3.amazonaws.com’ AND json.rule = $.userAgent contains ‘parrot’
C. event from cloud.audit_logs where operation IN (‘cloudsql.instances.update’,‘cloudsql.sslCerts.create’,‘cloudsql.instances.create’,‘cloudsql.instance’)
D. event from cloud.audit_logs where operation IN (‘GetBucketWebsite’, ‘PutBucketWebsite’, ‘DeleteBucketWebsite’)
An administrator for Prisma Cloud needs to obtain a graphical view to monitor all connections, including connections across hosts and connections to any configured network objects. Which setting does the administrator enable or configure to accomplish this task?
A. ADEM
B. WAAS Analytics
C. Telemetry
D. Cloud Native Network Firewall
E. Host Insight
Given the following RQL:Which audit event snippet is identified by the RQL?
A.

B.

C.

D.

An administrator has access to a Prisma Cloud Enterprise. What are the steps to deploy a single container Defender on an ec2 node?
A. Pull the Defender image to the ec2 node, copy and execute the curl | bash script, and start the Defender to ensure it is running.
B. Execute the curl | bash script on the ec2 node.
C. Configure the cloud credential in the console and allow cloud discovery to auto-protect the ec2 node.
D. Generate DaemonSet file and apply DaemonSet to the twistlock namespace.
A customer wants to turn on Auto Remediation. Which policy type has the built-in CLI command for remediation?
A. Anomaly
B. Audit Event
C. Network
D. Config
Where are Top Critical CVEs for deployed images found?
A. Defend → Vulnerabilities → Code Repositories
B. Defend → Vulnerabilities → Images
C. Monitor → Vulnerabilities → Vulnerabilities Explorer
D. Monitor → Vulnerabilities → Images
Which container image scan is constructed correctly?
A. twistcli images scan –docker-address https://us-west1.cloud.twistlock.com/us-3-123456789 myimage/latest
B. twistcli images scan –address https://us-west1.cloud.twistlock.com/us-3-123456789 myimage/latest
C. twistcli images scan –address https://us-west1.cloud.twistlock.com/us-3-123456789 –container myimage/latest
D. twistcli images scan –address https://us-west1.cloud.twistlock.com/us-3-123456789 –container myimage/latest –details
An administrator sees that a runtime audit has been generated for a Container. The audit message is `DNS resolution of suspicious name wikipedia.com. type A`. Why would this message appear as an audit?
A. The DNS was not learned as part of the Container model or added to the DNS allow list.
B. This is a DNS known to be a source of malware.
C. The process calling out to this domain was not part of the Container model.
D. The Layer7 firewall detected this as anomalous behavior.
Given the following information, which twistcli command should be run if an administrator were to exec into a running container and scan it from within using an access token for authentication? • Console is located at https://prisma-console.mydomain.local • Token is: TOKEN_VALUE • Report ID is: REPORT_ID • Container image running is: myimage:latest
A. twistcli images scan –address https://prisma-console.mydomain.local –token TOKEN_VALUE –containerized –details myimage:latest
B. twistcli images scan –console-address https://prisma-console.mydomain.local –auth-token TOKEN_VALUE –containerized –vulnerability-details REPORT_ID
C. twistcli images scan –address https://prisma-console.mydomain.local –token TOKEN_VALUE –containerized –details REPORT_ID
D. twistcli images scan –console-address https://prisma-console.mydomain.local –auth-token MY_TOKEN –local-scan –details myimage:latest
Which file extension type is supported for Malware scanning in Prisma Cloud Data Security (PCDS)?
A. .bat
B. .apk
C. .vb
D. .py
On which cloud service providers can you receive new API release information for Prisma Cloud?
A. AWS, Azure, GCP, Oracle, IBM
B. AWS, Azure, GCP, Oracle, Alibaba
C. AWS, Azure, GCP, IBM
D. AWS, Azure, GCP, IBM, Alibaba
DRAG DROP - Put the steps of integrating Okta with Prisma Cloud in the right order in relation to CIEM or SSO okra integration.
A customer is deploying Defenders to a Fargate environment. It wants to understand the vulnerabilities in the image it is deploying. How should the customer automate vulnerability scanning for images deployed to Fargate?
A. Set up a vulnerability scanner on the registry
B. Embed a Fargate Defender to automatically scan for vulnerabilities
C. Designate a Fargate Defender to serve a dedicated image scanner
D. Use Cloud Compliance to identify misconfigured AWS accounts
A customer has Prisma Cloud Enterprise and host Defenders deployed. What are two options that allow an administrator to upgrade Defenders? (Choose two.)
A. with auto-upgrade, the host Defender will auto-upgrade.
B. auto deploy the Lambda Defender.
C. click the update button in the web-interface.
D. generate a new DaemonSet file.
The InfoSec team wants to be notified via email each time a Security Group is misconfigured. Which Prisma Cloud tab should you choose to complete this request?
A. Notifications
B. Policies
C. Alert Rules
D. Events
What is the function of the external ID when onboarding a new Amazon Web Services (AWS) account in Prisma Cloud?
A. It is a unique identifier needed only when Monitor & Protect mode is selected.
B. It is the resource name for the Prisma Cloud Role.
C. It is a UUID that establishes a trust relationship between the Prisma Cloud account and the AWS account in order to extract data.
D. It is the default name of the PrismaCloudApp stack.
Review this admission control policy:
match[{"msg": msg}] {
input.request.operation == "CREATE"
input.request.kind.kind == "Pod"
input.request.resource.resource == "pods"
input.request.object.spec.containers[_].securityContext.privileged msg := "Privileged"
}
Which response to this policy will be achieved when the effect is set to `block`?
A. The policy will block all pods on a Privileged host.
B. The policy will replace Defender with a privileged Defender.
C. The policy will alert only the administrator when a privileged pod is created.
D. The policy will block the creation of a privileged pod.
Which policy type in Prisma Cloud can protect against malware?
A. Data
B. Config
C. Network
D. Event
Which two variables must be modified to achieve automatic remediation for identity and access management (IAM) alerts in the Amazon Web Services (AWS) Cloud? (Choose two.)
A. API_ENDPOINT
B. SB_QUEUE_KEY_NAME
C. SQS_QUEUE_NAME
D. alert_id
The development team wants to fail CI jobs where a specific CVE is contained within the image. How should the development team configure the pipeline or policy to produce this outcome?
A. Set the specific CVE exception as an option in Jenkins or twistcli.
B. Set the specific CVE exception as an option in Defender running the scan.
C. Set the specific CVE exception as an option using the magic string in the Console.
D. Set the specific CVE exception in Console’s CI policy.
Which statement is true about obtaining Console images for Prisma Cloud Compute Edition?
A. To retrieve Prisma Cloud Console images using basic auth: 1. Access registry.paloaltonetworks.com, and authenticate using ‘docker login’. 2. Retrieve the Prisma Cloud Console images using ‘docker pull’.
B. To retrieve Prisma Cloud Console images using basic auth: 1. Access registry.twistlock.com, and authenticate using ‘docker login’. 2. Retrieve the Prisma Cloud Console images using ‘docker pull’.
C. To retrieve Prisma Cloud Console images using URL auth: 1. Access registry-url-auth.twistlock.com, and authenticate using the user certificate. 2. Retrieve the Prisma Cloud Console images using ‘docker pull’.
D. To retrieve Prisma Cloud Console images using URL auth: 1. Access registry-auth.twistlock.com, and authenticate using the user certificate. 2. Retrieve the Prisma Cloud Console images using ‘docker pull’.
What happens when a role is deleted in Prisma Cloud?
A. The access key associated with that role is automatically deleted.
B. Any integrations that use the access key to make calls to Prisma Cloud will stop working.
C. The users associated with that role will be deleted.
D. Any user who uses that key will be deleted.
Which RQL query is used to detect certain high-risk activities executed by a root user in AWS?
A. event from cloud.audit_logs where operation IN ( ‘ChangePassword’, ‘ConsoleLogin’, ‘DeactivateMFADevice’, ‘DeleteAccessKey’ , ‘DeleteAlarms’ ) AND user = ‘root’
B. event from cloud.security_logs where operation IN ( ‘ChangePassword’, ‘ConsoleLogin’, ‘DeactivateMFADevice’, ‘DeleteAccessKey’ , ‘DeleteAlarms’ ) AND user = ‘root’
C. config from cloud.audit_logs where operation IN ( ‘ChangePassword’, ‘ConsoleLogin’, ‘DeactivateMFADevice’, ‘DeleteAccessKey’, ‘DeleteAlarms’ ) AND user = ‘root’
D. event from cloud.audit_logs where Risk.Level = ‘high’ AND user = ‘root’
DRAG DROP - Move the steps to the correct order to set up and execute a serverless scan using AWS DevOps.
DRAG DROP - What is the order of steps in a Jenkins pipeline scan? (Drag the steps into the correct order of occurrence, from the first step to the last.) Select and Place:
How often do Defenders share logs with Console?
A. Every 10 minutes
B. Every 30 minutes
C. Every 1 hour
D. Real time
A customer has a development environment with 50 connected Defenders. A maintenance window is set for Monday to upgrade 30 stand-alone Defenders in the development environment, but there is no maintenance window available until Sunday to upgrade the remaining 20 stand-alone Defenders. Which recommended action manages this situation?
A. Go to Manage > Defender > Manage, then click Defenders, and use the Scheduler to choose which Defenders will be automatically upgraded during the maintenance window.
B. Find a maintenance window that is suitable to upgrade all stand-alone Defenders in the development environment.
C. Upgrade a subset of the Defenders by clicking the individual Actions > Upgrade button in the row that corresponds to the Defender that should be upgraded during the maintenance window.
D. Open a support case with Palo Alto Networks to arrange an automatic upgrade.
A security team has a requirement to ensure the environment is scanned for vulnerabilities. What are three options for configuring vulnerability policies? (Choose three.)
A. individual actions based on package type
B. output verbosity for blocked requests
C. apply policy only when vendor fix is available
D. individual grace periods for each severity level
E. customize message on blocked requests
An administrator wants to retrieve the compliance policies for images scanned in a continuous integration (CI) pipeline. Which endpoint will successfully execute to enable access to the images via API?
A. GET /api/v22.01/policies/compliance
B. GET /api/v22.01/policies/compliance/ci
C. GET /api/v22.01/policies/compliance/ci/images
D. GET /api/v22.01/policies/compliance/ci/serverless
Which two IDE plugins are supported by Prisma Cloud as part of its DevOps Security? (Choose two.)
A. BitBucket
B. Visual Studio Code
C. CircleCI
D. IntelliJ
A Prisma Cloud administrator is tasked with pulling a report via API. The Prisma Cloud tenant is located on app2.prismacloud.io. What is the correct API endpoint?
A. https://api.prismacloud.io
B. https://api2.eu.prismacloud.io
C. httsp://api.prismacloud.cn
D. https://api2.prismacloud.io
Which command correctly outputs scan results to stdout in tabular format and writes scan results to a JSON file while still sending the results to Console?
A. $ twistcli images scan–address –user –password –stdout-tabular–output-file scan-results.jsonnginx:latest
B. $ twistcli images scan–address –username –password –details–json-output scan-results.jsonnginx:latest
C. $ twistcli images scan–address –user –password –details–file-output scan-results.jsonnginx:latest
D. $ twistcli images scan–address –u –p –details–output-file scan-results.jsonnginx:latest
Given an existing ECS Cluster, which option shows the steps required to install the Console in Amazon ECS?
A. The console cannot natively run in an ECS cluster. A onebox deployment should be used.
B. Download and extract the release tarball Ensure that each node has its own storage for Console data Create the Console task definition Deploy the task definition
C. Download and extract release tarball Download task from AWS Create the Console task definition Deploy the task definition
D. Download and extract the release tarball Create an EFS file system and mount to each node in the cluster Create the Console task definition Deploy the task definition
An administrator sees that a runtime audit has been generated for a host. The audit message is: `Service postfix attempted to obtain capability SHELL by executing /bin/sh /usr/libexec/postfix/postfix-script.stop. Low severity audit, event is automatically added to the runtime model` Which runtime host policy rule is the root cause for this runtime audit?
A. Custom rule with specific configuration for file integrity
B. Custom rule with specific configuration for networking
C. Default rule that alerts on capabilities
D. Default rule that alerts on suspicious runtime behavior
Which policy type provides information about connections from suspicious IPs in a customer database?
A. Anomaly
B. Threat detection
C. Network
D. AutoFocus
Which RQL query type is invalid?
A. Event
B. IAM
C. Incident
D. Config
Anomaly policy uses which two logs to identify unusual network and user activity? (Choose two.)
A. Network flow
B. Audit
C. Traffic
D. Users
What is an example of an outbound notification within Prisma Cloud?
A. AWS Inspector
B. Qualys
C. Tenable
D. PagerDuty
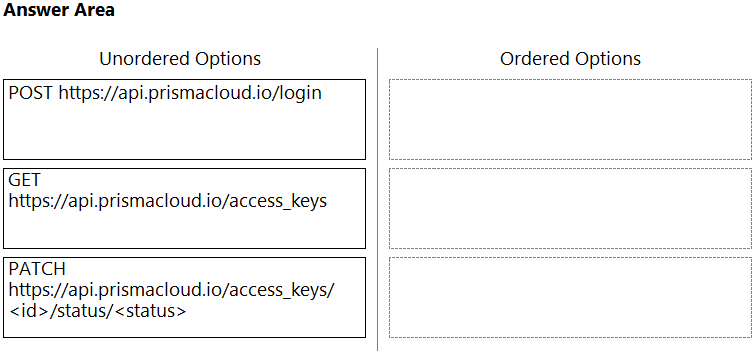
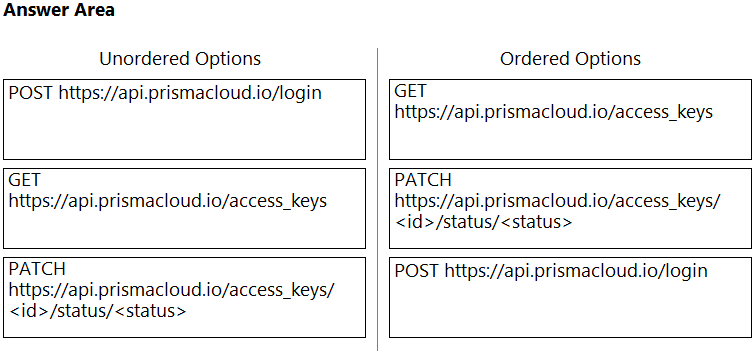
DRAG DROP - An administrator needs to write a script that automatically deactivates access keys that have not been used for 30 days. In which order should the API calls be used to accomplish this task? (Drag the steps into the correct order from the first step to the last.) Select and Place:
Given the following RQL: event from cloud.audit_logs where operation IN (‘CreateCryptoKey’, ‘DestroyCryptoKeyVersion’, ‘v1.compute.disks.createSnapshot’) Which audit event snippet is identified?
A.

B.

C.

D.

Which IAM RQL query would correctly generate an output to view users who enabled console access with both access keys and passwords?
A. config from network where api.name = ‘aws-iam-get-credential-report’ AND json.rule = cert_1_active is true or cert_2_active is true and password_enabled equals “true”
B. config from cloud.resource where api.name = ‘aws-iam-get-credential-report’ AND json.rule = access_key_1_active is true or access_key_2_active is true and password_enabled equals “true”
C. config from cloud.resource where api.name = ‘aws-iam-get-credential-report’ AND json.rule = access_key_1_active is false or access_key_2_active is true and password_enabled equals “*”
D. config where api.name = ‘aws-iam-get-credential-report’ AND json.rule= access_key_1_active is true or access_key_2_active is true and password_enabled equals “true”
An administrator needs to detect and alert on any activities performed by a root account. Which policy type should be used?
A. config-run
B. config-build
C. network
D. audit event
Which two CI/CD plugins are supported by Prisma Cloud as part of its Code Security? (Choose two.)
A. Checkov
B. Visual Studio Code
C. CircleCI
D. IntelliJ
A customer has a requirement to scan serverless functions for vulnerabilities. What is the correct option to configure scanning?
A. Configure serverless radar from the Defend > Compliance > Cloud Platforms page.
B. Embed serverless Defender into the function.
C. Configure a function scan policy from the Defend > Vulnerabilities > Functions page.
D. Use Lambda layers to deploy a Defender into the function.
Access Full PCCSE Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete PCCSE Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our PCCSE mock test free today—and take a major step toward exam success!