PCCET Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your PCCET certification exam? Start your preparation the smart way with our PCCET Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for PCCET exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our PCCET Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
What type of DNS record maps an IPV6 address to a domain or subdomain to another hostname?
A. SOA
B. NS
C. AAAA
D. MX
Which two statements are true about servers in a demilitarized zone (DMZ)? (Choose two.)
A. They can be accessed by traffic from the internet.
B. They are located in the internal network.
C. They can expose servers in the internal network to attacks.
D. They are isolated from the internal network.
DRAG DROP - Match the description with the VPN technology. Select and Place:
What is the primary purpose of a case management system?
A. To consolidate alerts into a single queue for streamlined incident handling
B. To incorporate an additional layer in the escalation procedure
C. To be a centralized tool pointing to other, separate alerting systems
D. To minimize the number of duplicate alerts
Which security component should you configure to block viruses not seen and blocked by the perimeter firewall?
A. endpoint antivirus software
B. strong endpoint passwords
C. endpoint disk encryption
D. endpoint NIC ACLs
What is the proper subnet mask for the network 192.168.55.0/27?
A. 255.255.255.192
B. 255.255.255.248
C. 255.255.255.224
D. 255.255.255.0
Which pillar of Prisma Cloud application security addresses ensuring that your cloud resources and SaaS applications are correctly configured?
A. visibility, governance, and compliance
B. network protection
C. dynamic computing
D. compute security
Which product from Palo Alto Networks enables organizations to prevent successful cyberattacks as well as simplify and strengthen security processes?
A. Expedition
B. AutoFocus
C. MineMeld
D. Cortex XDR
What does SOAR technology use to automate and coordinate workflows?
A. algorithms
B. Cloud Access Security Broker
C. Security Incident and Event Management
D. playbooks
Which type of organization benefits most from the features SD-WAN offers?
A. Businesses with one office and many remote employees
B. Small businesses in a single location
C. Large businesses with a single location
D. Businesses with several branches
Which Palo Alto Networks service is a scalable, cloud-based log repository that stores context-rich logs generated by Palo Alto Networks security products?
A. Cortex XDR
B. Cortex XSOAR
C. Cortex Data Lake
D. Cortex Xpanse
Which core component is used to implement a Zero Trust architecture?
A. VPN Concentrator
B. Content Identification
C. Segmentation Platform
D. Web Application Zone
What are three benefits of SD-WAN infrastructure? (Choose three.)
A. Improving performance of SaaS applications by requiring all traffic to be back-hauled through the corporate headquarters network
B. Promoting simplicity through the utilization of a centralized management structure
C. Utilizing zero-touch provisioning for automated deployments
D. Leveraging remote site routing technical support by relying on MPLS
E. Improving performance by allowing efficient access to cloud-based resources without requiring back-haul traffic to a centralized location
Which NGFW feature is used to provide continuous identification, categorization, and control of known and previously unknown SaaS applications?
A. User-ID
B. Device-ID
C. App-ID
D. Content-ID
Which of the following is a Routed Protocol?
A. Routing Information Protocol (RIP)
B. Transmission Control Protocol (TCP)
C. Internet Protocol (IP)
D. Domain Name Service (DNS)
Which Palo Alto Networks subscription service complements App-ID by enabling you to configure the next-generation firewall to identify and control access to websites and to protect your organization from websites hosting malware and phishing pages?
A. Threat Prevention
B. DNS Security
C. WildFire
D. URL Filtering
Which endpoint tool or agent can enact behavior-based protection?
A. AutoFocus
B. Cortex XDR
C. DNS Security
D. MineMeld
Which of the following is an AWS serverless service?
A. Beta
B. Kappa
C. Delta
D. Lambda
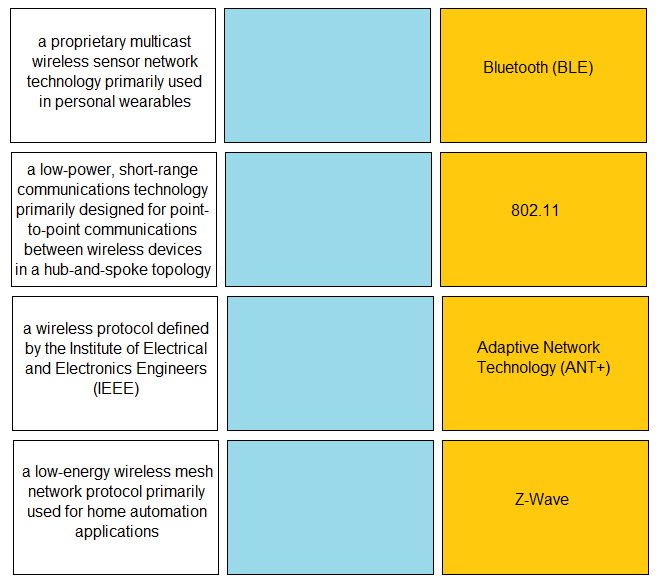
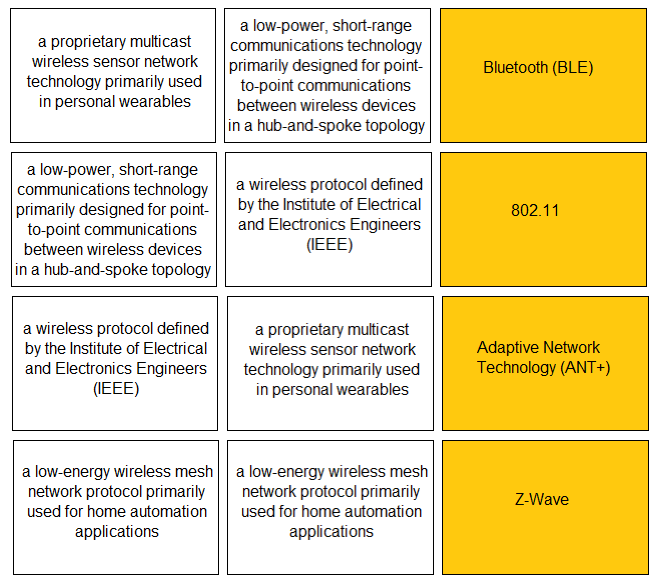
DRAG DROP - Match the IoT connectivity description with the technology. Select and Place:
Which SOAR feature coordinates across technologies, security teams, and external users for centralized data visibility and action?
A. Case management
B. Integrations
C. Ticketing system
D. Playbooks
Which product from Palo Alto Networks extends the Security Operating Platform with the global threat intelligence and attack context needed to accelerate analysis, forensics, and hunting workflows?
A. Global Protect
B. WildFire
C. AutoFocus
D. STIX
Before incorporating the DevSecOps process, when was security applied in the software-development lifecycle?
A. In every step of the lifecycle
B. Right in the middle
C. Right at the end, after the development ended
D. Right at the beginning, before the development started
Which characteristic of serverless computing enables developers to quickly deploy application code?
A. Uploading cloud service autoscaling services to deploy more virtual machines to run their application code based on user demand
B. Uploading the application code itself, without having to provision a full container image or any OS virtual machine components
C. Using cloud service spot pricing to reduce the cost of using virtual machines to run their application code
D. Using Container as a Service (CaaS) to deploy application containers to run their code.
Which Palo Alto subscription service identifies unknown malware, zero-day exploits, and advanced persistent threats (APTs) through static and dynamic analysis in a scalable, virtual environment?
A. DNS Security
B. URL Filtering
C. WildFire
D. Threat Prevention
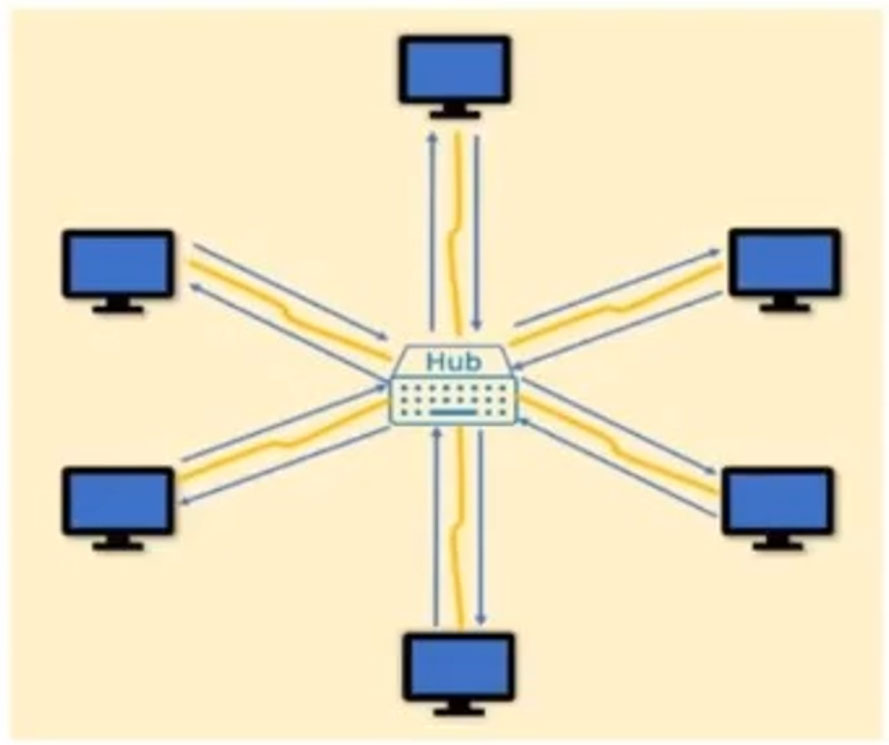
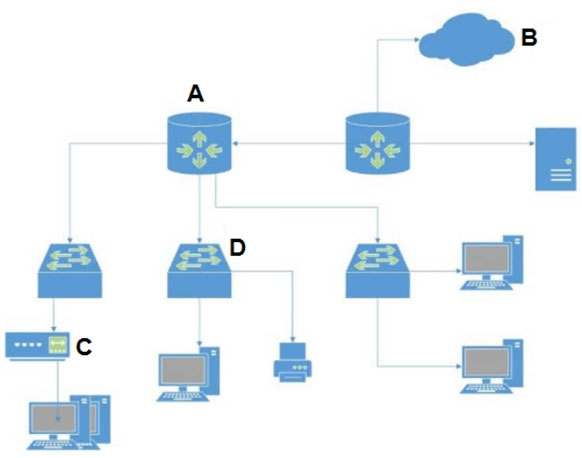
Which type of LAN technology is being displayed in the diagram?
A. Star Topology
B. Spine Leaf Topology
C. Mesh Topology
D. Bus Topology
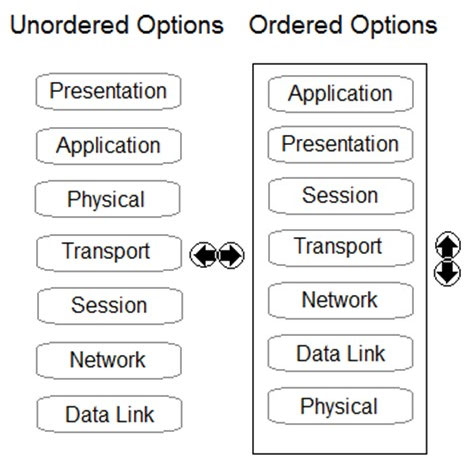
DRAG DROP - Order the OSI model with Layer7 at the top and Layer1 at the bottom. Select and Place:
From which resource does Palo Alto Networks AutoFocus correlate and gain URL filtering intelligence?
A. Unit 52
B. PAN-DB
C. BrightCloud
D. MineMeld
Which endpoint product from Palo Alto Networks can help with SOC visibility?
A. STIX
B. Cortex XDR
C. WildFire
D. AutoFocus
What is required for a SIEM to operate correctly to ensure a translated flow from the system of interest to the SIEM data lake?
A. connectors and interfaces
B. infrastructure and containers
C. containers and developers
D. data center and UPS
In addition to integrating the network and endpoint components, what other component does Cortex integrate to speed up IoC investigations?
A. Computer
B. Switch
C. Infrastructure
D. Cloud
How does adopting a serverless model impact application development?
A. costs more to develop application code because it uses more compute resources
B. slows down the deployment of application code, but it improves the quality of code development
C. reduces the operational overhead necessary to deploy application code
D. prevents developers from focusing on just the application code because you need to provision the underlying infrastructure to run the code
Which organizational function is responsible for security automation and eventual vetting of the solution to help ensure consistency through machine-driven responses to security issues?
A. NetOps
B. SecOps
C. SecDevOps
D. DevOps
Which type of IDS/IPS uses a baseline of normal network activity to identify unusual patterns or levels of network activity that may be indicative of an intrusion attempt?
A. Knowledge-based
B. Signature-based
C. Behavior-based
D. Database-based
Which network device breaks networks into separate broadcast domains?
A. Hub
B. Layer 2 switch
C. Router
D. Wireless access point
How can local systems eliminate vulnerabilities?
A. Patch systems and software effectively and continuously.
B. Create preventative memory-corruption techniques.
C. Perform an attack on local systems.
D. Test and deploy patches on a focused set of systems.
In SecOps, what are two of the components included in the identify stage? (Choose two.)
A. Initial Research
B. Change Control
C. Content Engineering
D. Breach Response
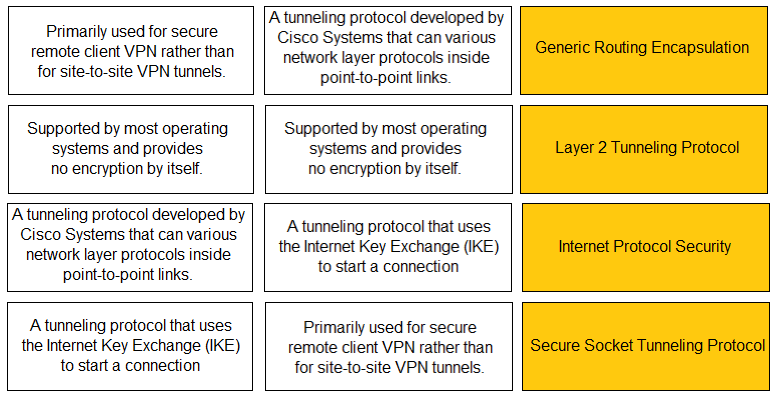
DRAG DROP - Match each tunneling protocol to its definition.
Layer 4 of the TCP/IP Model corresponds to which three Layer(s) of the OSI Model? (Choose three.)
A. Transport
B. Presentation
C. Session
D. Application
E. Network
Which Palo Alto Networks product provides playbooks with 300+ multivendor integrations that help solve any security use case?
A. Cortex XSOAR
B. Prisma Cloud
C. AutoFocus
D. Cortex XDR
What are three benefits of the cloud native security platform? (Choose three.)
A. Increased throughput
B. Exclusivity
C. Agility
D. Digital transformation
E. Flexibility
Which network firewall operates up to Layer 4 (Transport layer) of the OSI model and maintains information about the communication sessions which have been established between hosts on trusted and untrusted networks?
A. Group policy
B. Stateless
C. Stateful
D. Static packet-filter
Systems that allow for accelerated incident response through the execution of standardized and automated playbooks that work upon inputs from security technology and other data flows are known as what?
A. XDR
B. STEP
C. SOAR
D. SIEM
SecOps consists of interfaces, visibility, technology, and which other three elements? (Choose three.)
A. People
B. Accessibility
C. Processes
D. Understanding
E. Business
Web 2.0 applications provide which type of service?
A. SaaS
B. FWaaS
C. IaaS
D. PaaS
Which pillar of Prisma Cloud application security does vulnerability management fall under?
A. dynamic computing
B. identity security
C. compute security
D. network protection
Which statement describes DevOps?
A. DevOps is its own separate team
B. DevOps is a set of tools that assists the Development and Operations teams throughout the software delivery process
C. DevOps is a combination of the Development and Operations teams
D. DevOps is a culture that unites the Development and Operations teams throughout the software delivery process
Which classification of IDS/IPS uses a database of known vulnerabilities and attack profiles to identify intrusion attempts?
A. Statistical-based
B. Knowledge-based
C. Behavior-based
D. Anomaly-based
Which option is a Prisma Access security service?
A. Compute Security
B. Firewall as a Service (FWaaS)
C. Virtual Private Networks (VPNs)
D. Software-defined wide-area networks (SD-WANs)
In the attached network diagram, which device is the switch?
A. A
B. B
C. C
D. D
Which three layers of the OSI model correspond to the Application Layer (L4) of the TCP/IP model?
A. Session, Transport, Network
B. Application, Presentation, and Session
C. Physical, Data Link, Network
D. Data Link, Session, Transport
Access Full PCCET Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete PCCET Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our PCCET mock test free today—and take a major step toward exam success!