Network+ Practice Test – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the Network+ certification? Our Network+ Practice Test resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective Network+ Practice Test is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic Network+ Practice Test that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
A customer called the help desk to report a network issue. The customer recently added a hub between the switch and the router in order to duplicate the traffic flow to a logging device. After adding the hub, all the other network components that were connected to the switch slowed more than expected. Which of the following is the MOST likely cause of the issue?
A. Duplex mismatch
B. Flow control failure
C. STP malfunction
D. 802.1Q disabled
A fiber patch cable, which was being stored in an unsecure telecommunications closet with janitorial supplies, was damaged and caused an outage. A network technician replaced the broken cable with a new cable from a sealed bag. However, this solution did not resolve the outage. Which of the following is the MOST likely explanation?
A. Incorrect pinout
B. Incorrect transceivers
C. Reversed transmit and receive
D. Dirty optical cables
An ISP configured an internet connection to provide 20Mbps, but actual data rates are occurring at 10Mbps and causing a significant delay in data transmission. Which of the following specifications should the ISP check?
A. Throughput
B. Latency
C. Bandwidth
D. Jitter
Which of the following describes the ability of a corporate IT department to expand its cloud-hosted VM environment with minimal effort?
A. Scalability
B. Load balancing
C. Multitenancy
D. Geo-redundancy
Which of the following can be used to decrease latency during periods of high utilization of a firewall?
A. Hot site
B. Content inspection
C. HA pair
D. VRRP
A customer calls the help desk to report that a Windows PC is unable to open any websites or access any server shares. The help desk technician suspects there is an issue with the configuration. Which of the following commands should the technician issue FIRST to troubleshoot the issue?
A. tracert
B. netstat
C. arp
D. ipconfig
E. nmap
A network technician needs to select an AP that will support at least 1.3Gbps and 5GHz only. Which of the following wireless standards must the AP support to meet the requirements?
A. B
B. AC
C. AX
D. N
E. G
Which of the following devices would be used to extend the range of a wireless network?
A. A repeater
B. A media converter
C. A router
D. A switch
Which of the following redundant devices creates broadcast storms when connected together on a high-availability network?
A. Switches
B. Routers
C. Access points
D. Servers
A user from a remote office is reporting slow file transfers. Which of the following tools will an engineer MOST likely use to get detailed measurement data?
A. Packet capture
B. iPerf
C. SIEM log review
D. Internet speed test
A technician is investigating a misconfiguration on a Layer 3 switch. When the technician logs in and runs a command, the following data is shown:Which of the following commands generated this output?
A. show route
B. show config
C. show interface
D. tcpdump
E. netstat -s
An IT technician is working on a support ticket regarding an unreachable website. The technician has utilized the ping command to the website, but the site is still unreachable. Which of the following tools should the technician use NEXT?
A. ipconfig
B. tracert
C. arp
D. netstat
HOTSPOT You have been tasked with implementing an ACL on the router that will: 1. Permit the most commonly used secure remote access technologies from the management network to all other local network segments. 2. Ensure the user subnet cannot use the most commonly used remote access technologies in the Linux and Windows Server segments. 3. Prohibit any traffic that has not been specifically allowed. INSRUCTIONS Use the drop-downs to complete the ACL. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.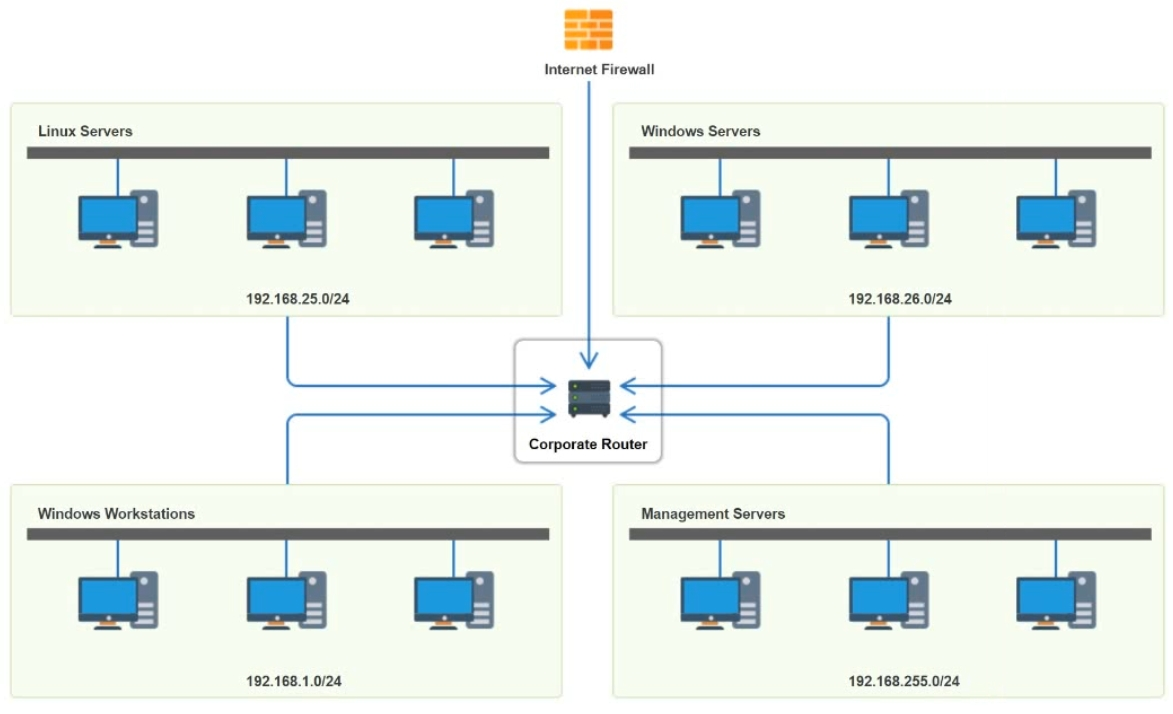
Which of the following types of planes propagates routing information in an SDWAN solution?
A. Orchestration plane
B. Management plane
C. Control plane
D. Data plane
A technician is running new Cat 5e cables to a server room. Which of the following tools should the technician use to terminate the cables at the patch panel?
A. Multimeter
B. Cable crimper
C. Toner probe
D. Punchdown tool
A disaster recovery team needs a solution that would best meet the following requirements: · The server infrastructure has been pre-installed · The fail-over location offers basic life support. · The fail-over location provides basic network connectivity. · Minimizing cost is preferred over quicker business recovery times · The expected time for services to be fully operational is days. Which of the following sites would meet the requirements?
A. Cold site
B. Cloud site
C. Warm site
D. Hot site
A technician troubleshoots a computer that has intermittent network connectivity and notices the termination point is loose. The technician also observes that the patch cable has already been replaced. Which of the following should the technician do NEXT?
A. Use a tone generator to trace the cable
B. Use a multimeter to determine if PoE is available on the switchport
C. Use a cable crimper to replace the RJ45 connector on the patch cable
D. Use a punchdown tool to reseat the copper in the wall jack
A company wants to invest in new hardware for the core network infrastructure. The management team requires that the infrastructure be capable of being repaired in less than 60 minutes if any major part fails. Which of the following metrics is MOST likely associated with this requirement?
A. RPO
B. MTTR
C. FHRP
D. MTBF
Which of the following devices and encapsulations are found at the data link layer? (Choose two.)
A. Session
B. Frame
C. Firewall
D. Switch
E. Packet
F. Router
After rebooting an AP, a user is no longer able to connect to the enterprise LAN. A technician plugs a laptop in to the same network jack and receives the IP 169.254.0.200. Which of the following is MOST likely causing the issue?
A. DHCP scope exhaustion
B. Signal attenuation
C. Channel overlap
D. Improper DNS configuration
A network administrator is concerned about a rainbow table being used to help access network resources. Which of the following must be addressed to reduce the likelihood of a rainbow table being effective?
A. Password policy
B. Remote access policy
C. Acceptable use policy
D. Data loss prevention policy
HOTSPOT A network technician needs to resolve some issues with a customer's SOHO network. The customer reports that some of the PCs are not connecting to the network, while others appear to be working as intended. INSTRUCTIONS Troubleshoot all the network components. Review the cable test results first, then diagnose by clicking on the appropriate PC, server, and Layer 2 switch. Identify any components with a problem and recommend a solution to correct each problem. If at any time you would like to bring back the initial state of the simulation, please dick the Reset All button.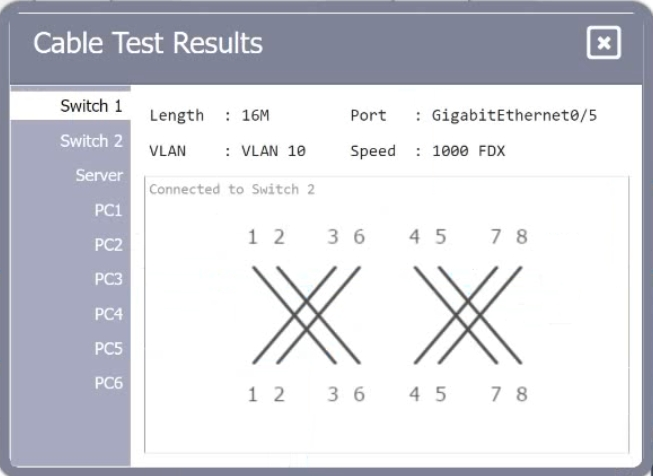
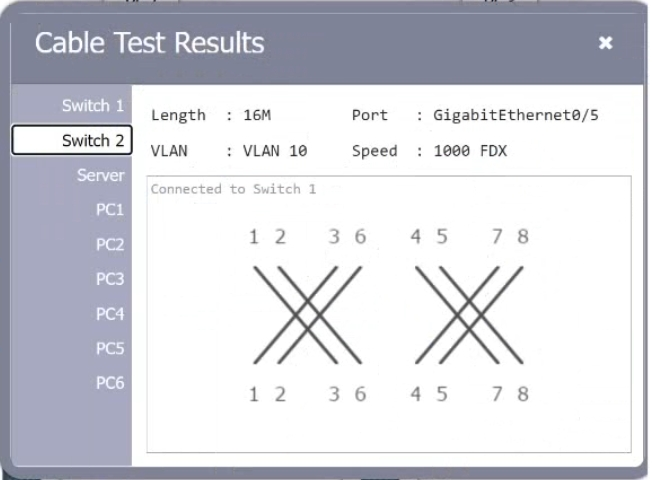
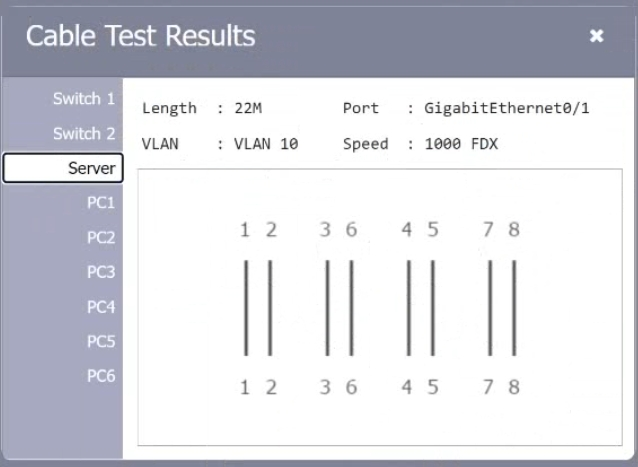
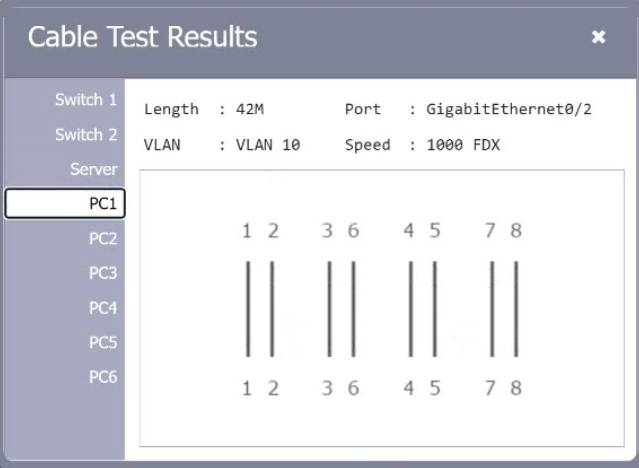
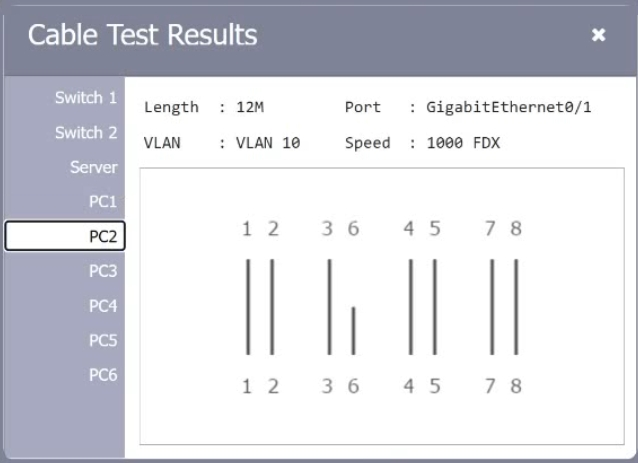
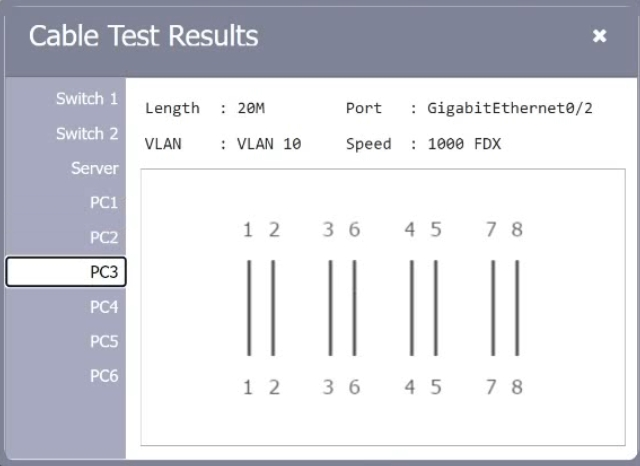
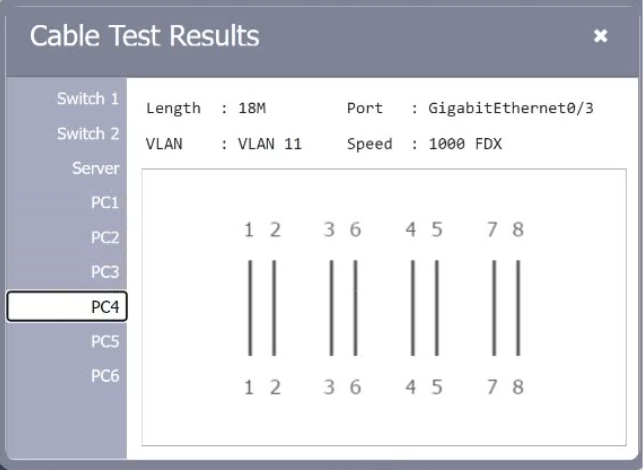
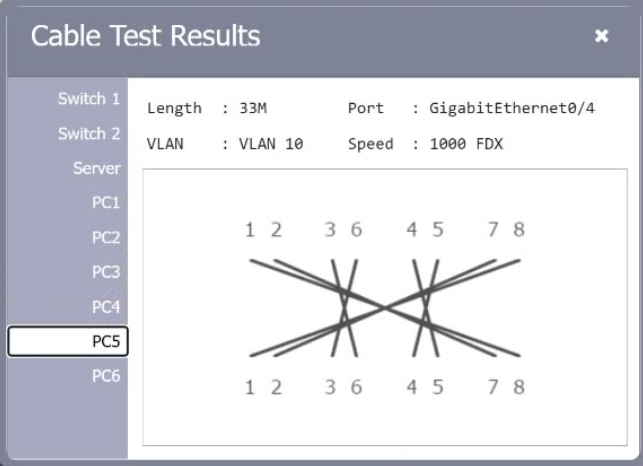


A customer reports there is no access to resources following the replacement of switches. A technician goes to the site to examine the configuration and discovers redundant links between two switches. Which of the following is the reason the network is not functional?
A. The ARP cache has become corrupt.
B. CSMA/CD protocols have failed.
C. STP is not configured.
D. The switches are incompatible models.
Users are reporting poor wireless performance in some areas of an industrial plant. The wireless controller is measuring a low EIRP value compared to the recommendations noted on the most recent site survey. Which of the following should be verified or replaced for the EIRP value to meet the site survey's specifications? (Choose two.)
A. AP transmit power
B. Channel utilization
C. Signal loss
D. Update ARP tables
E. Antenna gain
F. AP association time
A coffee shop owner hired a network consultant to provide recommendations for installing a new wireless network. The coffee shop customers expect high speeds even when the network is congested. Which of the following standards should the consultant recommend?
A. 802.11ac
B. 802.11ax
C. 802.11g
D. 802.11n
A network technician is hired to review all the devices within a network and make recommendations to improve network efficiency. Which of the following should the technician do FIRST before reviewing and making any recommendations?
A. Capture a network baseline.
B. Perform an environmental review.
C. Read the network logs.
D. Run a bandwidth test.
A company has multiple offices around the world. The computer rooms in some office locations are too warm. Dedicated sensors are in each room, but the process of checking each sensor takes a long time. Which of the following options can the company put in place to automate temperature readings with internal resources?
A. Implement NetFlow.
B. Hire a programmer to write a script to perform the checks.
C. Utilize ping to measure the response.
D. Use SNMP with an existing collector server.
Which of the following architectures reduces network latency by enforcing a limit on the number of switching devices on the frame's path between any internal hosts?
A. Spine and leaf
B. Software-defined network
C. Three-tiered
D. Collapsed core
A network administrator is decommissioning a server. Which of the following will the network administrator MOST likely consult?
A. Onboarding and offboarding policies
B. Business continuity plan
C. Password requirements
D. Change management documentation
A technician is investigating an issue with connectivity at customer's location. The technician confirms that users can access resources locally but not over the internet. The technician theorizes that the local router has failed and investigates further. The technician's testing results show that the router is functional; however, users still are unable to reach resources on the internet. Which of the following describes what the technician should do NEXT?
A. Document the lessons learned.
B. Escalate the issue.
C. Identify the symptoms.
D. Question users for additional information.
On a network with redundant switches, a network administrator replaced one of the switches but was unable to get a connection with another switch. Which of the following should the administrator check after successfully testing the cable that was wired for TIA/EIA-568A on both ends?
A. If MDIX is enabled on the new switch
B. If PoE is enabled
C. If a plenum cable is being used
D. If STP is disabled on the switches
The lack of a formal process to grant network permissions to different profiles of employees and contractors is leading to an increasing number of security incidents. Non-uniform and overly permissive network accesses are being granted. Which of the following would be the MOST appropriate method to improve the security of the environment?
A. Change the default permissions to implicit deny.
B. configure uniform ACLs to employees and NAC for contractors.
C. Deploy an RDP server tofficentralize the access to the network.
D. Implement role-based access control.
A new office space is being designed. The network switches are up, but no services are running yet. A network engineer plugs in a laptop configured as a DHCP client to a switch. Which of the following IP addresses should be assigned to the laptop?
A. 10.1.1.1
B. 169.254.1.128
C. 172.16.128.128
D. 192.168.0.1
An organization requires the ability to send encrypted email messages to a partner from an email server that is hosted on premises. The organization prefers to use the standard default ports when creating firewall rules. Which of the following ports should be open to satisfy the requirements?
A. 110
B. 143
C. 587
D. 636
Which of the following BEST describes a split-tunnel client-to-server VPN connection?
A. The client sends all network traffic down the VPN tunnel.
B. The client has two different IP addresses that can be connected to a remote site from two different ISPs to ensure availability.
C. The client sends some network traffic down the VPN tunnel and other traffic to the local gateway.
D. The client connects to multiple remote sites at the same time.
Which of the following is the MOST secure connection used to inspect and provide controlled internet access when remote employees are connected to the corporate network?
A. Site-to-site VPN
B. Full-tunnel VPN
C. Split-tunnel VPN
D. SSH
An engineer is troubleshooting poor performance on the network that occurs during work hours. Which of the following should the engineer do to improve performance?
A. Replace the patch cables.
B. Create link aggregation.
C. Create separation rules on the firewall.
D. Create subinterfaces on the existing port.
A network technician is troubleshooting a network issue for employees who have reported issues with speed when accessing a server in another subnet. The server is in another building that is 410ft (125m) away from the employees' building. The 10GBASE-T connection between the two buildings uses Cat 5e. Which of the following BEST explains the speed issue?
A. The connection type is not rated for that distance.
B. A broadcast storm is occurring on the subnet.
C. The cable run has interference on it.
D. The connection should be made using a Cat 6 cable.
Which of the following is a security flaw in an application or network?
A. A threat
B. A vulnerability
C. An exploit
D. A risk
An administrator is investigating reports of network slowness in a building. While looking at the uplink interface statistics in the switch's CLI, the administrator discovers the uplink is at 100% utilization. However, the administrator is unsure how to identify what traffic is causing the saturation. Which of the following tools should the administrator utilize to identify the source and destination addresses of the traffic?
A. SNMP
B. Traps
C. Syslog
D. NetFlow
Two new network switches located in different buildings are connected together with single-mode fiber. However, no link exists between the two switches. Which of the following steps should the technician perform FIRST to troubleshoot the issue?
A. Reverse TX/RX on the fiber patch cord at one building.
B. Replace the fiber patch cords in both buildings.
C. Clean the fiber patch cord connectors in both buildings.
D. Connect the fiber patch cord to an OTDR at one building.
Which of the following OSI model layers would allow a user to access and download files from a remote computer?
A. Session
B. Presentation
C. Network
D. Application
A company is designing a SAN and would like to use STP as its medium for communication. Which of the following protocols would BEST suit the company's needs?
A. SFTP
B. Fibre Channel
C. iSCSI
D. FTP
A technician notices that equipment is being moved around and misplaced in the server room, even though the room has locked doors and cabinets. Which of the following would be the BEST solution to identify who is responsible?
A. Install motion detection.
B. Install cameras.
C. Install tamper detection.
D. Hire a security guard.
A computer engineer needs to ensure that only a specific workstation can connect to port 1 on a switch. Which of the following features should the engineer configure on the switch interface?
A. Port tagging
B. Port security
C. Port mirroring
D. Port aggregation
A cafeteria is facing lawsuits related to criminal internet access that was made over its guest network. The marketing team, however, insists on keeping the cafeteria's phone number as the wireless passphrase. Which of the following actions would improve wireless security while accommodating the marketing team and accepting the terms of use?
A. Setting WLAN security to use EAP-TLS
B. Deploying a captive portal for user authentication
C. Using geofencing to limit the area covered by the WLAN
D. configuring guest network isolation
An administrator would like to have two servers at different geographical locations provide fault tolerance and high performance while appearing as one URL to users. Which of the following should the administrator implement?
A. Load balancing
B. Multipathing
C. NIC teaming
D. Warm site
An IT technician successfully connects to the corporate wireless network at a bank. While performing some tests, the technician observes that the physical address of the DHCP server has changed even though the network connection has not been lost. Which of the following would BEST explain this change?
A. Server upgrade
B. Duplicate IP address
C. Scope exhaustion
D. Rogue server
An ISP is providing internet to a retail store and has terminated its point of connection using a standard Cat 6 pin-out. Which of the following terminations should the technician use when running a cable from the ISP's port to the front desk?
A. F-type connector
B. TIA/EIA-568-B
C. LC
D. SC
A company needs to virtualize a replica of its internal physical network without changing the logical topology and the way that devices behave and are managed. Which of the following technologies meets this requirement?
A. NVF
B. SDWAN
C. VIP
D. MPLS
Access Full Network+ Practice Test
Want a full-length mock test experience? Click here to unlock the complete Network+ Practice Test set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our Network+ Practice Test today—and take a major step toward exam success!

