N10-008 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the N10-008 certification? Our N10-008 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective N10-008 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic N10-008 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
A network technician crimped a length of UTP with TIAEIA-568A on one end and TIAEIA-568B on the other. Which of the following cable types did the technician create?
A. Crossover cable
B. Patch cable
C. Twinaxial cable
D. Rollover cable
A network engineer needs to enable device monitoring using authentication and encryption. Which of the following protocols offers this option?
A. ESP
B. SNMPv3
C. NetFlow
D. SSLv3
A company is considering shifting its business to the cloud. The management team is concerned about the availability of the third-party cloud service. Which of the following should the management team consult to determine the promised availability of the cloud provider?
A. Memorandum of understanding
B. Business continuity plan
C. Disaster recovery plan
D. Service-level agreement
Which of the following commands can be used to display the IP address, subnet address, gateway address, and DNS address on a Windows computer?
A. netstat -a
B. ifconfig
C. ip addr
D. ipconfig /all
Which of the following OSI model layers is where a technician would view UDP information?
A. Physical
B. Data link
C. Network
D. Transport
A packet is assigned a value to ensure it does not traverse a network inde nitely. Which of the following BEST represents this value?
A. Zero Trust
B. Planned obsolescence
C. Time to live
D. Caching
Which of the following ports is commonly used by VoIP phones?
A. 20
B. 143
C. 445
D. 5060
A technician wants to install a WAP in the center of a room that provides service in a radius surrounding a radio. Which of the following antenna types should the AP utilize?
A. Omni
B. Directional
C. Yagi
D. Parabolic
A network administrator wants to control new router deployments via the use of application programming interfaces (APIs). This would be an example of:
A. software-defined networking.
B. a three-tiered architecture.
C. collapsed backbone.
D. top-of-rack switching.
A business is using the local cable company to provide Internet access. Which of the following types of cabling will the cable company MOST likely use from the demarcation point back to the central office?
A. Multimode
B. Cat 5e
C. RG-6
D. Cat 6
E. 100BASE-T
A network administrator is trying to identify a device that is having issues connecting to a switchport. Which of the following would BEST help identify the issue?
A. A syslog server
B. Change management records
C. A rack diagram
D. The security log
An IT organization needs to optimize speeds for global content distribution and wants to reduce latency in high-density user locations. Which of the following technologies BEST meets the organization's requirements?
A. Load balancing
B. Geofencing
C. Public cloud
D. Content delivery network
E. Infrastructure as a service
A medical building offers patients Wi-Fi in the waiting room. Which of the following security features would be the BEST solution to provide secure connections and keep the medical data protected?
A. Isolating the guest network
B. Securing SNMP
C. MAC filtering
D. Disabling unneeded switchports
Which of the following is conducted frequently to maintain an updated list of a system's weaknesses?
A. Penetration test
B. Posture assessment
C. Risk assessment
D. Vulnerability scan
An IT technician installs five old switches in a network. In addition to the low port rates on these switches, they also have improper network configurations. After three hours, the network becomes overwhelmed by continuous traffic and eventually shuts down. Which of the following is causing the issue?
A. Broadcast storm
B. Collisions
C. IP settings
D. Routing loops
A technician performed a manual reconfiguration of a firewall, and network connectivity was reestablished. Some connection events that were previously sent to a syslog server are no longer being generated by the firewall. Which of the following should the technician perform to fix the issue?
A. Adjust the proper logging level on the new firewall.
B. Tune the filter for logging the severity level on the syslog server.
C. Activate NetFlow traffic between the syslog server and the firewall.
D. Restart the SNMP service running on the syslog server.
A network technician is investigating a trouble ticket for a user who does not have network connectivity. All patch cables between the wall jacks and computers in the building were upgraded over the weekend from Cat 5 to Cat 6. The newly installed cable is crimped with a TIA/EIA 568A on one end and a TIA/EIA 568B on the other end. Which of the following should the technician do to MOST likely x the issue?
A. Ensure the switchport has PoE enabled.
B. Crimp the cable as a straight-through cable.
C. Ensure the switchport has STP enabled,
D. Crimp the cable as a rollover cable.
Which of the following bandwidth management techniques uses butters at the client side to prevent TCP retransmissions from occurring when the ISP starts to drop packets of specific types that exceed the agreed traffic rate?
A. traffic shaping
B. traffic policing
C. traffic marking
D. traffic prioritization
A technician is assisting a user who cannot connect to a website. The technician attempts to ping the default gateway and DNS server of the workstation. According to troubleshooting methodology, this is an example of:
A. a divide-and-conquer approach.
B. a bottom-up approach.
C. a top-to-bottom approach.
D. implementing a solution.
Which of the following is used to providefinetworking capability for VMs at Layer 2 of the OSI model?
A. VPN
B. VRRP
C. vSwitch
D. VIP
Given the following information:Which of the following would cause performance degradation between PC A and PC B?
A. Attenuation
B. Interference
C. Decibel loss
D. Incorrect pinout
Which of the following is the MOST secure connection used to inspect and provide controlled internet access when remote employees are connected to the corporate network?
A. Site-to-site VPN
B. Full-tunnel VPN
C. Split-tunnel VPN
D. SSH
An application team is deploying a new application. The application team would like the network team to monitor network performance and create alerts if uctuations in the round-trip time occur for that traffic. Which of the following should the network team monitor to meet this requirement?
A. Bandwidth
B. Latency
C. Loss
D. Cyclic redundancy check
A network team is getting reports that air conditioning is out in an ID
A. The team would like to determine whether additional network issues are occurring. Which of the following should the network team do?
B. confirm that memory usage on the network devices in the IDF is normal.
C. Access network baseline data for references to an air conditioning issue.
D. Verify severity levels on the corporate syslog server.
E. Check for SNMP traps from a network device in the ID
F. Review interface statistics looking for cyclic redundancy errors.
A network administrator is troubleshooting a connection to a remote site. The administrator runs a command and sees the following output:Which of the following is the cause of the connection issue?
A. Routing loop
B. Asymmetrical routing
C. Broadcast storm
D. Switching loop
The power company noti es a network administrator that it will be turning off the power to the building over the weekend. Which of the following is the BEST solution to prevent the servers from going down?
A. Redundant power supplies
B. Uninterruptible power supply
C. Generator
D. Power distribution unit
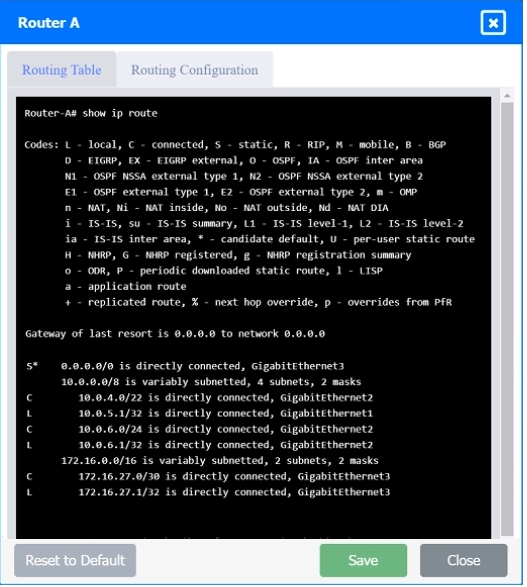
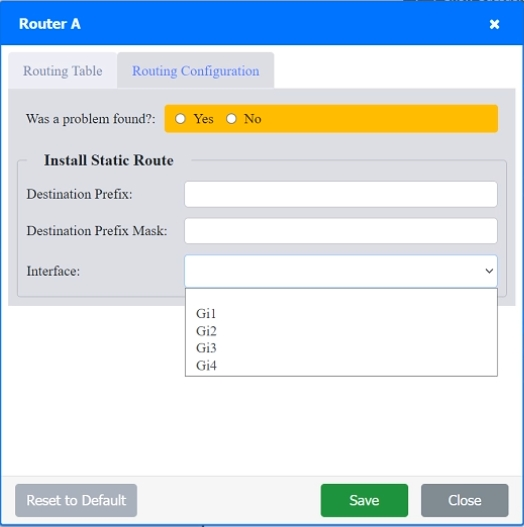
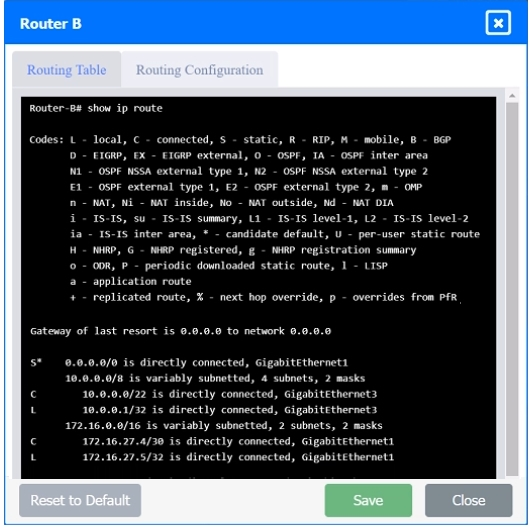
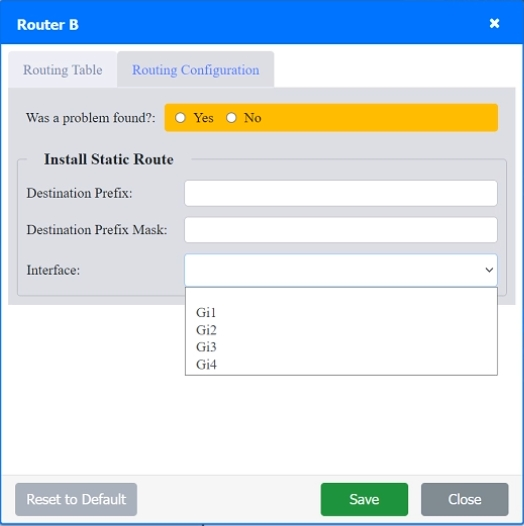
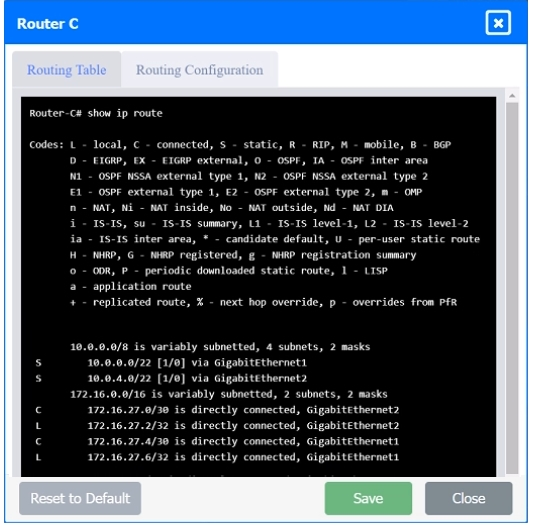
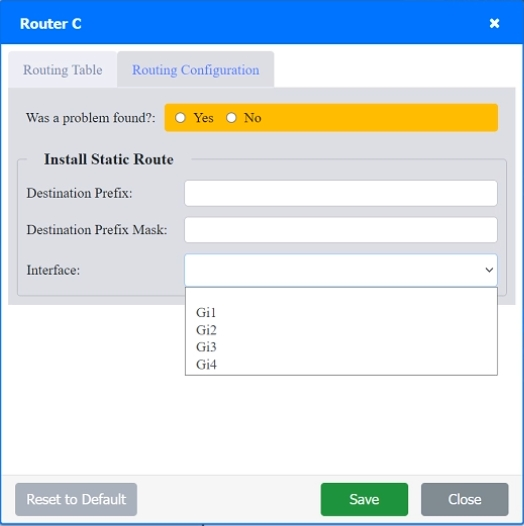
SIMULATION Users are unable to access files on their department share located on file server 2. The network administrator has been tasked with validating routing between networks hosting workstation A and file server 2. INSTRUCTIONS Click on each router to review output, identify any issues, and configure the appropriate solution. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.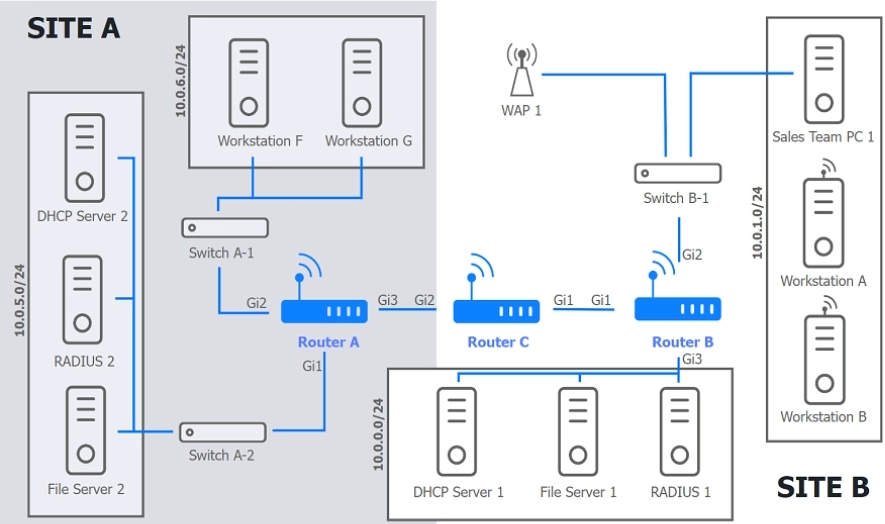

A new company recently moved into an empty office space. Within days, users in the next office began noticing increased latency and packet drops with their Wi-Fi-connected devices. Which of the following is the MOST likely reason for this issue?
A. Channel overlap
B. Distance from the AP
C. Bandwidth latency
D. Disabled WPS
E. Network congestion
Which of the following are environmental factors that should be considered when installing equipment in a building? (Choose two.)
A. Fire suppression system
B. UPS location
C. Humidity control
D. Power load
E. Floor construction type
F. Proximity to nearest MDF
Which of the following would MOST likely be used to review disaster recovery information for a system?
A. Business continuity plan
B. Change management
C. System life cycle
D. Standard operating procedures
A WAN technician reviews activity and identifies newly installed hardware that is causing outages over an eight-hour period. Which of the following should be considered FIRST?
A. Network performance baselines
B. VLAN assignments
C. Routing table
D. Device configuration review
Which of the following ports is a secure protocol?
A. 20
B. 23
C. 443
D. 445
At the destination host, which of the following OSI model layers will discard a segment with a bad checksum in the UDP header?
A. Network
B. Data link
C. Transport
D. Session
A network technician is troubleshooting a network issue for employees who have reported issues with speed when accessing a server in another subnet. The server is in another building that is 410ft (125m) away from the employees' building. The 10GBASE-T connection between the two buildings uses Cat 5e. Which of the following BEST explains the speed issue?
A. The connection type is not rated for that distance.
B. A broadcast storm is occurring on the subnet.
C. The cable run has interference on it.
D. The connection should be made using a Cat 6 cable.
Which of the following would MOST likely utilize PoE?
A. A camera
B. A printer
C. A hub
D. A modem
A network administrator is designing a new datacenter in a different region that will need to communicate to the old datacenter with a secure connection. Which of the following access methods would provide the BEST security for this new datacenter?
A. Virtual network computing
B. Secure Socket Shell
C. In-band connection
D. Site-to-site VPN
Several employees have expressed concerns about the company monitoring their internet activity when they are working from home. The company wants to mitigate this issue and reassure employees that their private internet activity is not being monitored. Which of the following would satisfy company and employee needs?
A. Split tunnel
B. Full tunnel
C. Site-to-site tunnel
D. Virtual desktop
Which of the following issues are present with RIPv2? (Choose two.)
A. Route poisoning
B. Time to converge
C. Scalability
D. Unicast
E. Adjacent neighbors
F. Maximum transmission unit
After rebooting an AP, a user is no longer able to connect to the enterprise LAN. A technician plugs a laptop in to the same network jack and receives the IP 169.254.0.200. Which of the following is MOST likely causing the issue?
A. DHCP scope exhaustion
B. Signal attenuation
C. Channel overlap
D. Improper DNS configuration
Which of the following is used to prioritize Internet usage per application and per user on the network?
A. Bandwidth management
B. Load balance routing
C. Border Gateway Protocol
D. Administrative distance
Which of the following protocols uses Dijkstra's algorithm to calculate the LOWEST cost between routers?
A. RIP
B. OSPF
C. BGP
D. EIGRP
An engineer is using a tool to run an ICMP sweep of a network to find devices that are online. When reviewing the results, the engineer notices a number of workstations that are currently verified as being online are not listed in the report. The tool was configured to scan using the following information: Network address: 172.28.16.0 - CIDR: /22 - The engineer collected the following information from the client workstation: IP address: 172.28.17.206 - Subnet mask: 255.255.252.0 - Which of the following MOST likely explains why the tool is failing to detect some workstations?
A. The scanned network range is incorrect.
B. The subnet mask on the client is misconfigured.
C. The workstation has a firewall enabled.
D. The tool is unable to scan remote networks.
A customer cannot reach a web application on a local server. The network consultant suspects that the server is not accepting the HTTPS connection. Which of the following commands should the consultant run on the server to determine what is occurring?
A. route
B. arp
C. nmap
D. netstat
The following configuration is applied to a DHCP server connected to a VPN concentrator:There are 300 non-concurrent sales representatives who log in for one hour a day to upload reports, and 252 of these representatives are able to connect to the VPN without any Issues. The remaining sales representatives cannot connect to the VPN over the course of the day. Which of the following can be done to resolve the issue without utilizing additional resources?
A. Decrease the lease duration
B. Reboot the DHCP server
C. Install a new VPN concentrator
D. configure a new router
An organization requires the ability to send encrypted email messages to a partner from an email server that is hosted on premises. The organization prefers to use the standard default ports when creating firewall rules. Which of the following ports should be open to satisfy the requirements?
A. 110
B. 143
C. 587
D. 636
A cafeteria is facing lawsuits related to criminal internet access that was made over its guest network. The marketing team, however, insists on keeping the cafeteria's phone number as the wireless passphrase. Which of the following actions would improve wireless security while accommodating the marketing team and accepting the terms of use?
A. Setting WLAN security to use EAP-TLS
B. Deploying a captive portal for user authentication
C. Using geofencing to limit the area covered by the WLAN
D. configuring guest network isolation
A network administrator needs to set up a file server to allow user access. The organization uses DHCP to assign IP addresses. Which of the following is the best solution for the administrator to set up?
A. A separate scope for the file server using a /32 subnet
B. A reservation for the server based on the MAC address
C. A static IP address within the DHCP IP range
D. A SLAAC for the server
An on-call network technician receives an automated email alert stating that a power supply on a firewall has just powered down. Which of the following protocols would BEST allow for this level of detailed device monitoring?
A. TFTP
B. TLS
C. SSL
D. SNMP
A network technician is troubleshooting a new web server connectivity issue. The network technician discovers the following on the support ticket: · The server's IP address can be pinged from the client PCs. · Access to the web resource works correctly when on the server's console. · No clients can access the server's data via URL. · The server does not have a firewall configured. · No ACLs are preventing connectivity from the client's network. · All services on the server are operating normally, which was confirmed by the server team. Which of the following actions will resolve the issue?
A. Reset port security on the switchport connecting the server.
B. Adjust the web server’s NTP setting to match the client settings.
C. configure A records for the web server.
D. Install the correct MIB on the web server.
A technician needs to find the MAC address of a connecting router. Which of the following commands should the technician use?
A. arp
B. traceroute
C. nslookup
D. ping
Access Full N10-008 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of N10-008 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your N10-008 certification journey!

