N10-007 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your N10-007 certification? Our N10-007 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an N10-007 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our N10-007 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
A technician discovered a company computer had a virus but was unable to remove it. The technician decided to erase the hard drive to eliminate the threat. Which of the following policies did the technician violate?
A. Data loss prevention
B. Incident response
C. Asset disposal
D. Acceptable use
A technician has completed configuration on a new satellite location. The location has a new firewall and a small internal network. The technician has been asked to perform basic vulnerability testing. Which of the following tools would BEST assist the technician in verifying the security of the site?
A. Packet sniffer
B. Bandwidth tester
C. Port scanner
D. Protocol analyzer
A network technician has created a network that consists of a router, a firewall, a switch, and several PCs. Which of the following physical network topologies was created?
A. Star
B. Mesh
C. Ring
D. Bus
A network technician is troubleshooting a connectivity issue with Joe, a user. Joe has reported that when he attempts to RDP to machine1 (192.168.21.21) by name, he is connected to machine3 (192.168.21.23). When the network technician runs the command nslookup machine1, it returns the IP address 192.168.21.23; but when the ping `"a 192.168.21.23 command is run, the results return the hostname machine3. Which of the following DNS records should be updated to allow RDP connections to machine1 by hostname?
A. A
B. SRV
C. PTR
D. TXT
Which of the following can be used to enable and translate the communication between legacy non-IP phone systems with solutions for voice communications that can run over the Internet?
A. Media converter
B. RTP
C. ISDN service
D. VoIP gateway
E. SIP trunk
Ann, a network technician, is told to disable unused ports on a switch. Another technician tells her the policy is to move those ports into a non-routed VLAN and leave them enabled. Which of the following documents should Ann use to ensure she is employing the correct method?
A. Inventory management
B. Wiring and port location
C. Configuration baseline
D. Standard operating procedure
Management has requested that a wireless solution be installed at a new office. Which of the following is the FIRST thing the network technician should do?
A. Order equipment
B. Create network diagrams
C. Perform a site survey
D. Create an SSID.
A network technician receives reports indicating some users are unable to gain access to any network resources. During troubleshooting, the technician discovers the workstations have an IP address of 169.254.x.x. Which of the following is the MOST likely cause?
A. Expired IP address
B. Exhausted dynamic scope
C. Misconfigured VLSM
D. Rogue DHCP server
A SAN serves out storage to a company's virtual environment and provides low-level disk access. The company wants to use its existing IP network and equipment to access the virtual disks. Which of the following network connection types would BEST accomplish this task?
A. InfiniBand
B. iSCSI
C. Fibre Channel
D. CIFS
A network technician needs to configure a device with an embedded OS so it can be connected to a wireless handheld scanner. Which of the following technologies should be configured on the OS to create the wireless connection?
A. Partial mesh
B. Ad hoc
C. Ring
D. Bus
A technician has installed multiple new PC clients and is connecting them to the network. Only one client is receiving IP addressing information. Which of the following should the technician verify as the NEXT troubleshooting step?
A. DHCP scope
B. DHCP lease
C. Default gateway
D. DNS zone
An analyst is developing a proof of concept of a wireless-based attack as part of a penetration test against an organization's network. As part of the attack, the analyst launches a fake access point matching the SSID of the organization's guest access network. When a user connects to the fake access point, the analyst allows the traffic to flow through the access point to the legitimate site while the data traversing the network is logged for latest analysis and exploitation. Which of the following attacks has the analyst successfully performed in this scenario?
A. Bluesnarfing
B. Session hijacking
C. MAC spoofing
D. VLAN hopping
E. Man-in-the-middle
A network administrator is configuring a link-state routing protocol for traffic. Which of the following routing protocols should be implemented?
A. RIPv2
B. BGP
C. EIGRP
D. OSPF
Joe, a network engineer, is attempting to install wireless in a large work area. He installs the access point in the middle of the work space. When testing, he notices a -60dB reading on one side of the room and a -92dB reading on the other side. Which of the following is MOST likely the issue?
A. External interference
B. Distance limitations
C. Channel overlap
D. Incorrect antenna type
A company requires a network storage solution that allows for the use of OS-specific credentials and permissions. The company purchases a SOHO solution, which includes support for SMB, iSCSI, FTP, Telnet, and NFS natively out of the box. Which of the following should be done FIRST?
A. Verify user credentials.
B. Generate new keys and certificates.
C. Disable unnecessary services.
D. Hash files that will be stored.
A network engineer is creating a method for customers to access the company's application in a web browser. Which of the following cloud models should the customers use to access the application?
A. PaaS
B. SaaS
C. MaaS
D. IaaS
After rebooting a PC, a user is no longer able to connect to the corporate network. As a test, the technician plugs a different laptop into the same network jack and receives an IP address of 169.254.112.137. Which of the following is MOST likely causing the issue?
A. DHCP scope exhaustion
B. Improper DNS setting
C. Incorrect ACL setting
D. Port-security violation
Multiple users are reporting that they are unable to access the network. The ENTIRE network is shown in the diagram. PCs are not statically assigned IP addresses. The following devices will display settings: ✑ WorkstationA ✑ WorkstationB ✑ WorkstationC ✑ WorkstationD WorkstationE -✑ WorkstationF ✑ WorkstationG ✑ Laptop1 ✑ Laptop2 ✑ DHCP server1 ✑ DHCP server2 Instructions: Review the settings and select the box in the diagram that identifies the device causing the issue. Only one device can be selected at a time. After checking the device that is causing the issue, select the second tab in the lower left hand corner. Identify the reason as to why some users are unable to access the network. When the simulation is complete, select the Done button to submit. Part 1 -
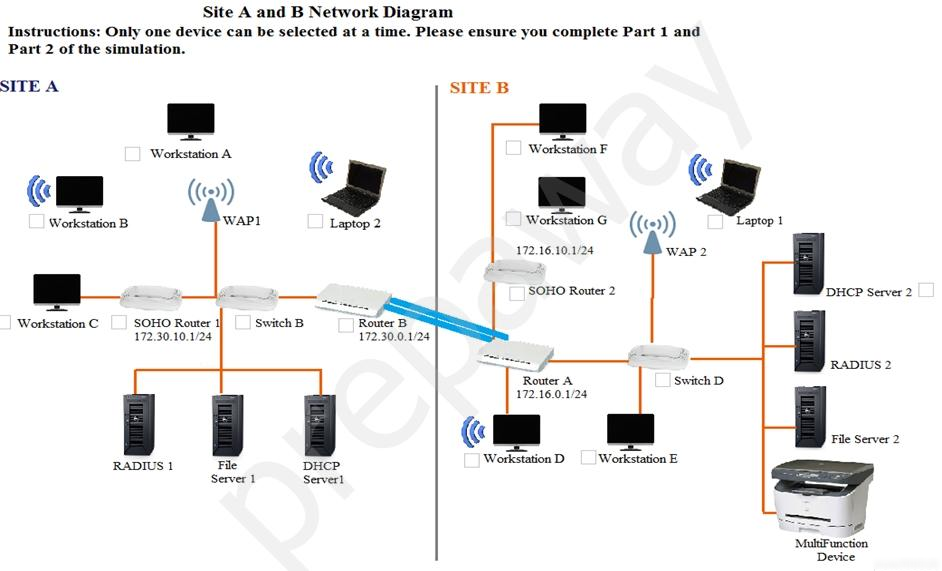
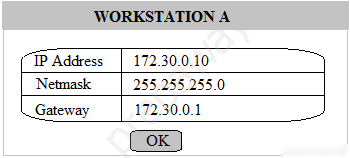
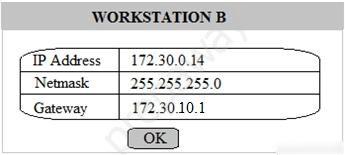

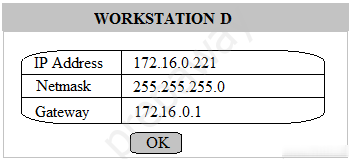
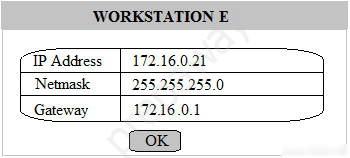
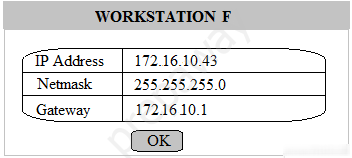
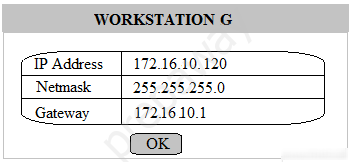
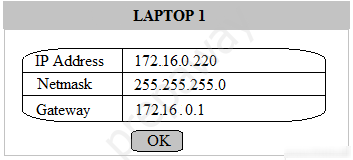
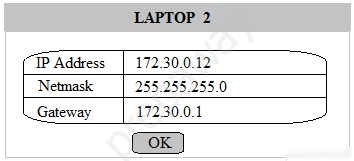
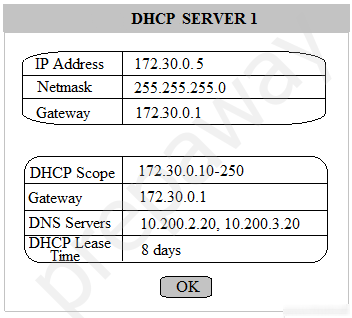
Part 2 - Identify the reason as to why some users are unable to access the network.
A. Workstation(s) are plugged into switch ports configured with half duplex.
B. The site-to-site router was configured with the incorrect ACL.
C. The DHCP server scope is full and is not providing IP addresses.
D. WAN and LAN ports are reversed on the router.
E. STP has disabled some of the ports on the switch.
F. The NIC driver is not installed.
G. A wireless client is unable to associate to the AP.
A technician has replaced a customer's desktop with a known-good model from storage. However, the replacement desktop will not connect to network resources. The technician suspects the desktop has not been kept up to date with security patches. Which of the following is MOST likely in place?
A. ACL
B. NAC
C. Traffic shaping
D. SDN
E. NTP
A network technician wants to remotely and securely access the desktop of a Linux workstation. The desktop is running remote control software without encryption. Which of the following should the technician use to secure the connection?
A. SSH in tunnel mode
B. RDP set to console connection
C. EAP-PEAP
D. SFTP
A network technician recently installed a new server on a network. The technician must ensure the server does not have any unnecessary services running. The IP address of the server is 204.211.38.50. Which of the following commands would allow the technician to make this determination?
A. nmap
B. pathping
C. route
D. nslookup
A network technician needs to subnet the network. The marketing department has 28 devices. Which of the following private IP address spaces should be used to ensure the MINIMUM number of unused IP addresses?
A. Gateway: 10.10.10.1 Netmask: 255.255.255.192
B. Gateway: 172.15.18.128 Netmask: 255.255.255.224
C. Gateway: 192.168.1.97 Netmask: 255.255.255.224
D. Gateway: 224.102.113.65 Netmask: 255.255.255.192
A network technician needs to install a new access switch. After installing the new switch, the technician begins to move connections from the old switch to the new switch. The old switch used a GBIC with SC connectors, and the new switch uses an SFP with LC connectors. After connecting the SC connector to the SC- to-LC adapter and plugging it into the switch, the link does not come up as expected. Which of the following should a network technician perform NEXT?
A. Replace SFP with a new one.
B. Fall back to the old switch.
C. Transpose the fiber pairs.
D. Replace multimode with single-mode cable.
A company runs Linux servers in its own datacenter and also on a popular public cloud service provider. The servers hosted by the cloud provider can only be accessed with proper authorization and are only accessed by the company's datacenter. Which of the following BEST describes the type of cloud architecture being used? (Choose two.)
A. Private
B. Hybrid
C. Public
D. IaaS
E. PaaS
F. SaaS
Which of the following BEST describes the characteristics of a differential backup solution?
A. Backs up files with the creation or modified date as the current date.
B. Backs up all files and sets the archive bit.
C. Backs up files with a date earlier than today’s date with a clear archive bit.
D. Backs up files with the archive bit set but does not clear the bit.
When connecting to a network device through a remote connection for configuration purposes, which of the following protocols is MOST secure?
A. SFTP
B. SSH
C. SNMPv1
D. LDAPS
A network technician works in a large environment with several thousand users. Due to the needs of the organization, the network manager has asked the technician to design a solution that accommodates the data needs of all the users, while keeping all data on site. Which of the following solutions should the technician implement?
A. SaaS
B. SAN
C. NAS
D. IaaS
A network administrator is setting up several IoT devices on a new VLAN and wants to accomplish the following: 1. Reduce manual configuration on each system. 2. Assign a specific IP address to each system. 3. Allow devices to move to different switchports on the same VLAN. Which of the following should the network administrator do to accomplish these requirements?
A. Set up a reservation for each device.
B. Configure a static IP on each device.
C. Implement private VLANs for each device.
D. Use DHCP exclusions to address each device.
A network technician needs to dedicate a range of addresses in DHCP for statically assigned servers and network devices. Which of the following should be configured to BEST accomplish this?
A. Static addressing
B. Subnetting
C. Advertisements
D. Exclusions
A network administrator notices that network utilization is extremely high around midnight and wonders if this is normal or if there might be a security issue. Which of the following types of documentation should the administrator consult FIRST?
A. Change management documentation
B. Standard operating procedures
C. Network performance baseline
D. Firewall configuration documentation
A customer wants a technician to implement a solution that will allow its critical on-site servers to continue to function in the event of an extended power outage. Which of the following should the technician recommend?
A. Warm site
B. Load balancer
C. Power generator
D. Hot site
A company has multiple site-to-site VPN connections using a pre-shared key. The Chief Information Security Officer (CISO) is concerned about the long-term security of the tunnels and has asked the network technicians to develop a plan to ensure the best security of the tunnels. Which of the following should the network technicians implement?
A. Purchase dedicated MPLS circuits between each of the sites.
B. Request a change of IP addresses from the ISP semiannually.
C. Perform annual key rotations on the site-to-site VPNs.
D. Terminate tunnels when they are not actively being used.
A vulnerability that would allow an unauthenticated, remote attacker to originate a DoS attack was found in a DHCP client implementation of a switch. Which of the following would BEST resolve the issue?
A. Verify the default passwords have been changed.
B. Upgrade to the latest firmware
C. Generate new SSH keys.
D. Review and modify the firewall rules.
A technician is reviewing network device logs in an attempt to trace an attack that occurred on the network. Which of the following protocols would affect whether or not the technician can properly trace the attack through the network using the logs?
A. HTTP
B. SMTP
C. NTP
D. RDP
A typical cell tower will have microwave and cellular antennas. Which of the following network topologies do these represent? (Choose two.)
A. Point-to-multipoint
B. Bus
C. Point-to-point
D. Mesh
E. Peer-peer
F. Ring
A network technician is implementing a solution on the network to hide the workstation internal IP addresses across a WAN. Which of the following is the technician configuring?
A. QoS
B. DMZ
C. RIP
D. NAT
Which of the following technologies provides a failover mechanism for the default gateway?
A. FHRP
B. LACP
C. OSPF
D. STP
A network technician needs to install new network cables. The technician will be running the cables in the air return space above the drop ceiling. Which of the following cable types should be installed?
A. Plenum
B. Coaxial
C. Shielded twisted pair
D. Fiber optic
A network engineer at a large company is restricting Internet browsing on the corporate WAN to only business-related external websites. Which of the following is the BEST solution to achieve this goal while avoiding the need to configure this restriction on each PC?
A. Web application firewall
B. Content filter
C. IPS
D. VPN concentrator
A company decides to deploy customer-facing, touch-screen kiosks. The kiosks appear to have several open source service ports that could potentially become compromised. Which of the following is the MOST effective way to protect the kiosks?
A. Install an IDS to monitor all traffic to and from the kiosks.
B. Install honeypots on the network to detect and analyze potential kiosk attacks before they occur.
C. Enable switchport security on the ports to which the kiosks are connected to prevent network-level attacks.
D. Create a new network segment with ACLs, limiting kiosks’ traffic with the internal network.
Joe, a network technician, wants to locally back up several router and switch configurations. He wants to store them on a server that can be accessed easily for recovery without authentication. Which of the following servers should Joe use?
A. Telnet
B. LDAP
C. TFTP
D. Samba
A network technician downloaded new firmware for the company firewall. Which of the following should the network technician verify to ensure the downloaded file is correct and complete?
A. File hash
B. File date
C. File type
D. File size
A technician is investigating a server performance issue. The technician has gathered the server utilization statistics. Which of the following should the technician use to determine which statistics are not in the normal range?
A. Baseline review
B. Vulnerability scan
C. System life-cycle report
D. Archiving logs
Which of the following OSI layers is represented by a physical address that is assigned by the manufacturer?
A. Data link
B. Transport
C. Network
D. Session
E. Physical
A small business utilizes a SOHO router and wishes to secure its existing wireless infrastructure. The business has fewer than ten devices, which are a mixture of old and new machines. Due to the varying ages of the machines, the latest wireless encryption methods may not be supported on all devices. Which of the following would be the MOST cost-effective method to add a layer of security while allowing all machines to connect?
A. WPA2
B. EAP-FAST
C. MAC filtering
D. 802.1X
A company is contracting a new third-party organization that will handle storage of the company's critical data. Which of the following policies would ensure the data remains confidential?
A. SLA
B. NDA
C. MOU
D. BYOD
A recent vulnerability was discovered in the code a company is running on its network devices. The vendor has released a security patch to address the vulnerability. To ensure an unaltered version of the patch is downloaded, which of the following should the network technician validate before installing the patch?
A. Date the patch was created
B. Version of the patch
C. Hash values of the patch
D. Change log for the patch
Which of the following would indicate that a circuit speed should be increased?
A. Low latency
B. Low bandwidth consumption
C. High number of SIEM alerts
D. High packet drops
A network administrator migrated the data for the corporate email service from one provider to another. All DNS records were successfully changed and verified. However, many hours later, users are still receiving new emails on the old provider's server. Which of the following should the administrator perform NEXT to troubleshoot the issue?
A. Add a secondary MX server to the DNS records.
B. Remove old SPF records from the DNS host.
C. Create a DMARC record that includes the old server.
D. Check the TTL value on the MX records.
A network technician is required to install a network device to provide service to an office area. The office area has 23 users and two printers that must be able to connect to the file server in a different building. Which of the following network devices should the technician use?
A. Media converter
B. Switch
C. Bridge
D. Wireless range extender
Access Full N10-007 Dump Free
Looking for even more practice questions? Click here to access the complete N10-007 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our N10-007 dump free questions — and get one step closer to exam success!

