MS-500 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the MS-500 certification? Our MS-500 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective MS-500 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic MS-500 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
You have a Microsoft 365 subscription that includes a user named Admin1. You need to ensure that Admin1 can retain all the mailbox content of users, including their deleted items. The solution must use the principle of least privilege. What should you do?
A. From the Microsoft 365 admin center, assign the Exchange administrator role to Admin1.
B. From the Exchange admin center, assign the Security Administrator role to Admin1.
C. From the Azure Active Directory admin center, assign the Service administrator role to Admin1.
D. From the Exchange admin center, assign the Recipient Management admin role to Admin1.
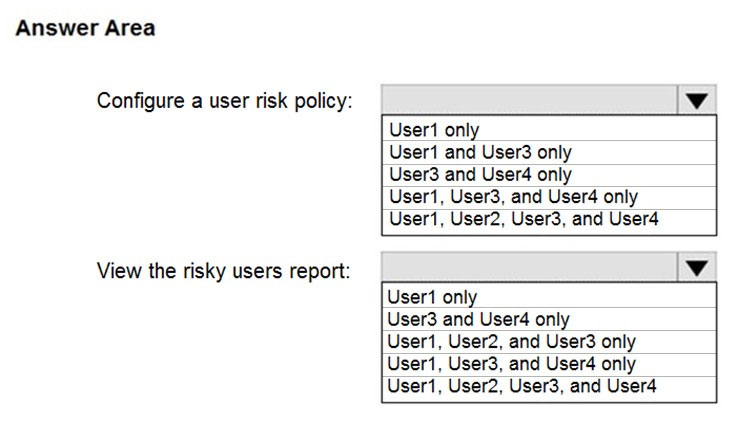
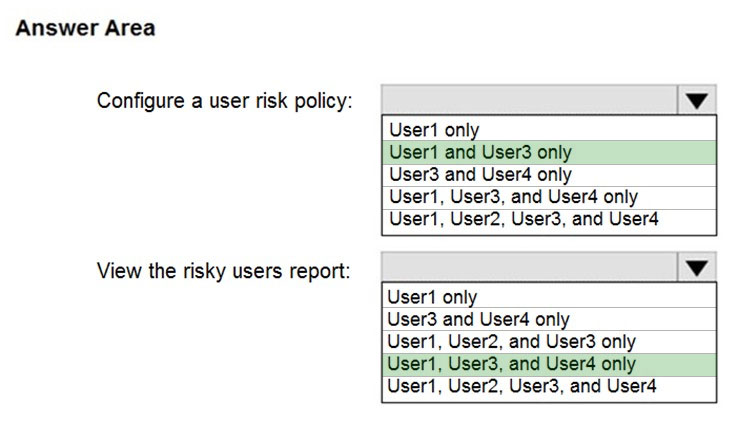
HOTSPOT - You have a Microsoft 365 E5 subscription that contains the users shown in the following table.You plan to implement Azure Active Directory (Azure AD) Identity Protection. You need to identify which users can perform the following actions: ✑ Configure a user risk policy. ✑ View the risky users report. Which users should you identify? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 E5 subscription that contains a user named User1. You need to ensure that User1 can use the Microsoft 365 compliance center to search audit logs and identify which users were added to Microsoft 365 role groups. The solution must use the principle of least privilege. To which role group should you add User1?
A. View-Only Organization Management
B. Security Reader
C. Organization Management
D. Compliance Management
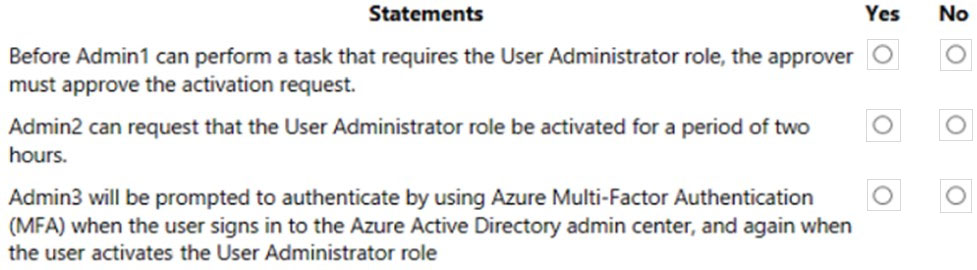
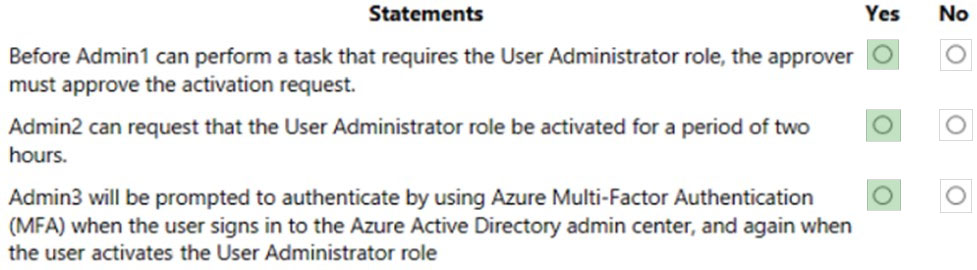
HOTSPOT - You have a Microsoft 365 tenant. A conditional access policy is configured for the tenant as shown in the Policy exhibit. (Click the Policy tab.)The User Administrator role is configured as shown in the Role setting exhibit. (Click the Role setting tab.)
The User Administrator role has the assignments shown in the Assignments exhibit. (Click the Assignments tab.)
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
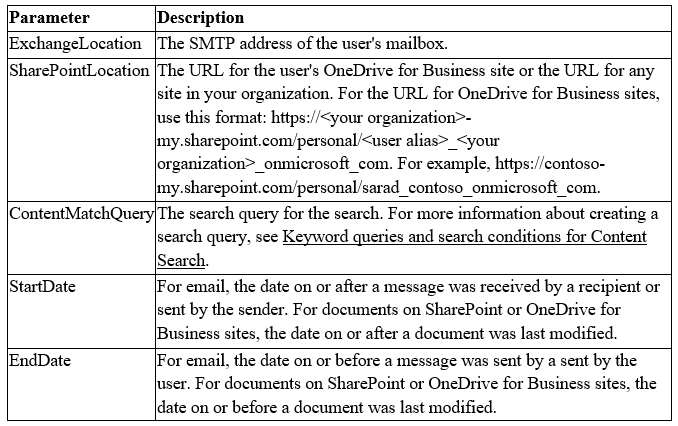
You have a Microsoft 365 subscription. You have a Data Subject Request (DSR) case named Case1. You need to ensure that Case1 includes all the email posted by the data subject to the Microsoft Exchange Online public folders. Which additional property should you include in the Content Search query?
A. kind:externaldata
B. itemclass:ipm.externaldata
C. itemclass:ipm.post
D. kind:email
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 subscription. You have a user named User1. Several users have full access to the mailbox of User1. Some email messages sent to User1 appear to have been read and deleted before the user viewed them. When you search the audit log in Microsoft 365 Compliance admin center to identify who signed in to the mailbox of User1, the results are blank. You need to ensure that you can view future sign-ins to the mailbox of User1. You run the Set-AdminAuditLogConfig -AdminAuditLogEnabled $true -AdminAuditLogCmdlets *Mailbox* command. Does that meet the goal?
A. Yes
B. No
Which role should you assign to User1?
A. Global administrator
B. User administrator
C. Privileged role administrator
D. Security administrator
HOTSPOT - You have a Microsoft 365 E5 subscription that contains the users and groups shown in the following table.You create the communication compliance policy as shown in the exhibit. (Click the Exhibit tab.)
Four emails are sent as shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
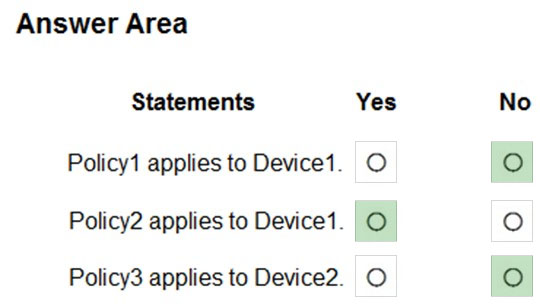
HOTSPOT - You have a Microsoft 365 subscription that contains the users shown in the following table.Group1 is a member of a group named Group3. The Azure Active Directory (Azure AD) tenant contains the Windows 10 devices shown in the following table.
Microsoft Endpoint Manager has the devices shown in the following table.
Microsoft Endpoint Manager contains the compliance policies shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
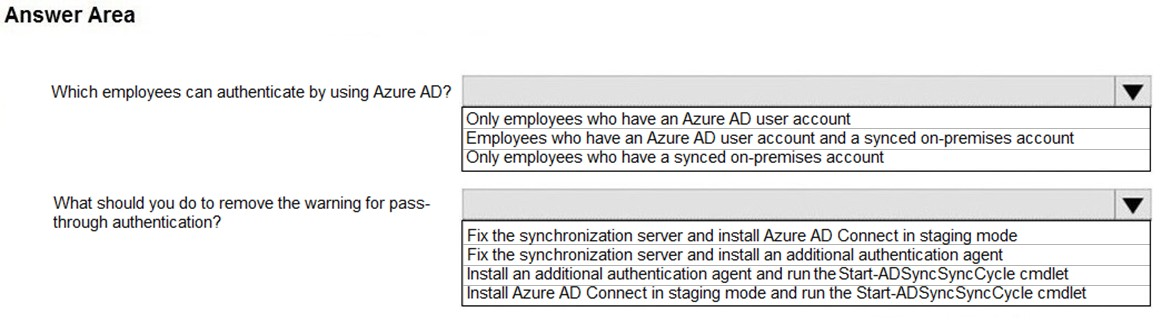
HOTSPOT - Your network contains an on-premises Active Directory domain that syncs to Azure Active Directory (Azure AD) as shown in the following exhibit.The synchronization schedule is configured as shown in the following exhibit.
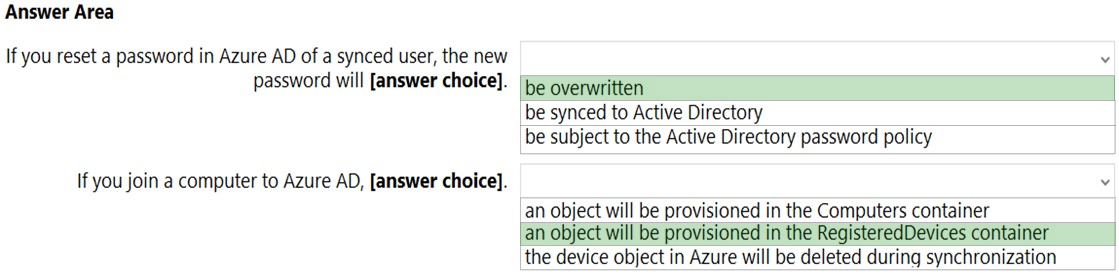
Use the drop-down menus to select the answer choice that answers each question based on the information presented in the graphic. NOTE: Each correct selection is worth one point. Hot Area:
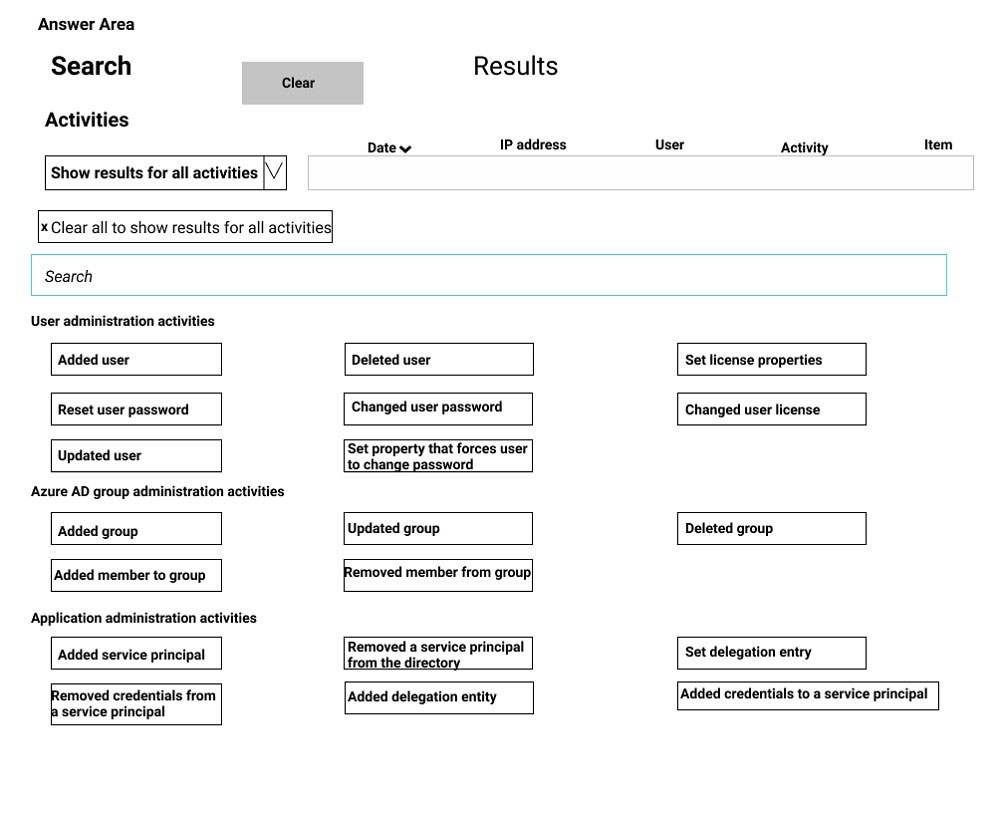
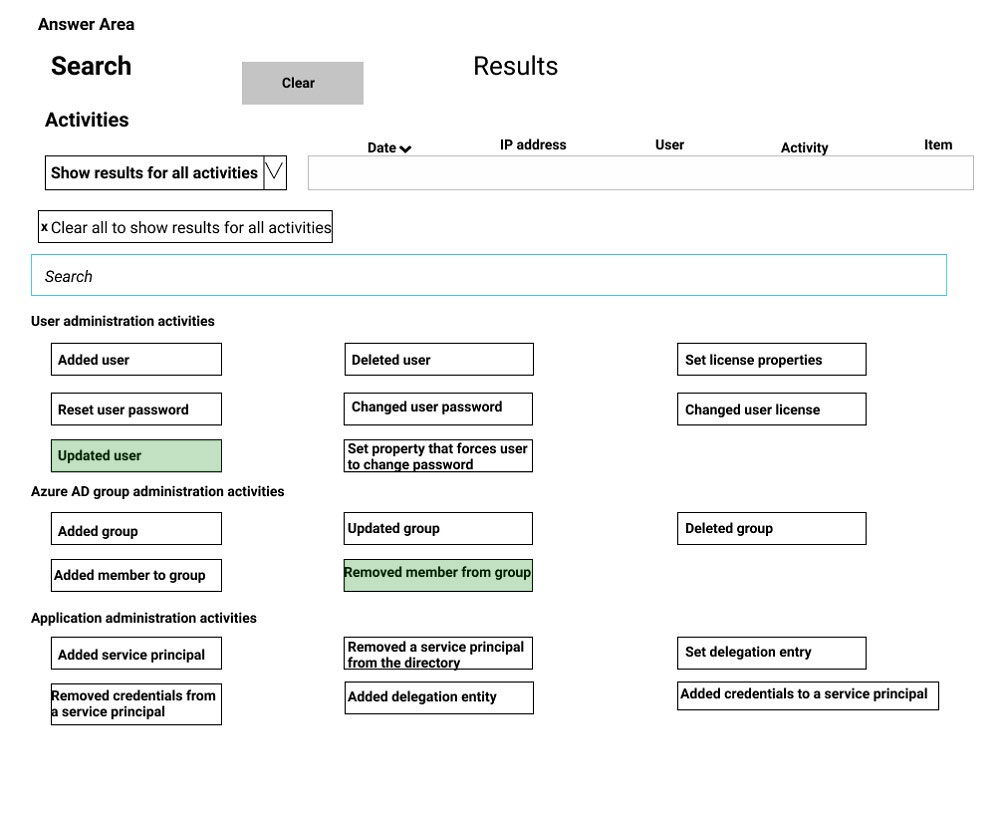
HOTSPOT - You have a Microsoft 365 subscription. Auditing is enabled. A user named User1 is a member of a dynamic security group named Group1. You discover that User1 is no longer a member of Group1. You need to search the audit log to identify why User1 was removed from Group1. Which two activities should you use in the search? To answer, select the appropriate activities in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 tenant. You need to implement a policy to enforce the following requirements: ✑ If a user uses a Windows 10 device that is NOT hybrid Azure Active Directory (Azure AD) joined, the user must be allowed to connect to Microsoft SharePoint Online only from a web browser. The user must be prevented from downloading files or syncing files from SharePoint Online. ✑ If a user uses a Windows 10 device that is hybrid Azure AD joined, the user must be able connect to SharePoint Online from any client application, download files, and sync files. What should you create?
A. a conditional access policy in Azure AD that has Client apps conditions configured
B. a conditional access policy in Azure AD that has Session controls configured
C. a compliance policy in Microsoft Endpoint Manager that has the Device Properties settings configured
D. a compliance policy in Microsoft Endpoint Manager that has the Device Health settings configured
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your on-premises network contains a server that runs Windows Server 2019, computers that run Windows 10, macOS, or Linux, and a firewall that utilizes syslog. You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint. All the computers are onboarded to Microsoft Defender for Endpoint. You are implementing Microsoft Defender for Cloud Apps. You need to discover which cloud apps are accessed from the computers. Solution: You install a Microsoft Defender for Cloud Apps log collector and collect logs from the firewall. Does this meet the goal?
A. Yes
B. No
DRAG DROP - You have a Microsoft 365 E5 subscription. You need to meet the following requirements: • Prevent the sharing of files between the users in a department named department1 and the users in a department named department2. • Generate an alert if a user downloads large quantities of sensitive customer data. Which type of policy should you use for each requirement? To answer, drag the appropriate policy types to the correct requirements. Each policy type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription and a hybrid Microsoft Exchange Server organization. Each member of a group named Executive has an on-premises mailbox. Only the Executive group members have multi-factor authentication (MFA) enabled. Each member of a group named Research has a mailbox in Exchange Online. You need to use Microsoft 365 Attack simulation training to model a spear-phishing attack that targets the Research group members. The email addresses that you intend to spoof belong to the Executive group members. What should you do first?
A. From the Microsoft Azure portal, configure the user risk policy settings in Azure AD Identity Protection.
B. Migrate the Executive group members to Exchange Online.
C. Enable MFA for the Research group members.
D. Enable MFA for your account.
E. From the Microsoft Defender for Identity portal, configure the primary workspace settings.
You have a Microsoft 365 E5 subscription that has Microsoft Defender for Office 365 enabled. You need to review the zero-hour auto purge (ZAP) configuration for the subscription. Which two threat policies should you review? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Safe attachments Built-in protection (Microsoft)
B. Anti-malware (Default) Default
C. Safe links Built-in protection (Microsoft)
D. Anti-spam outbound policy (Default)
E. Office365 AntiPhish Default (Default)
F. Anti-spam inbound policy (Default)
You have a Microsoft 365 subscription that uses Microsoft SharePoint Online. You need to ensure that users can only share files with users at specified partner companies. The solution must minimize administrative effort. What should you do?
A. Limit external sharing by domain.
B. Set External sharing to New and existing guests.
C. Allow only users in specific security groups to share externally.
D. Set File and folder links to Specific people.
SIMULATION - You plan to create a script to automate user mailbox searches. The script will search the mailbox of a user named Allan Deyoung for messages that contain the word injunction. You need to create the search that will be included in the script. To complete this task, sign in to the Microsoft 365 admin center.
You have a Microsoft 365 subscription. You create and run a content search from the Microsoft 365 Compliance center. You need to download the results of the content search. What should you obtain first?
A. an export key
B. a password
C. a certificate
D. a pin
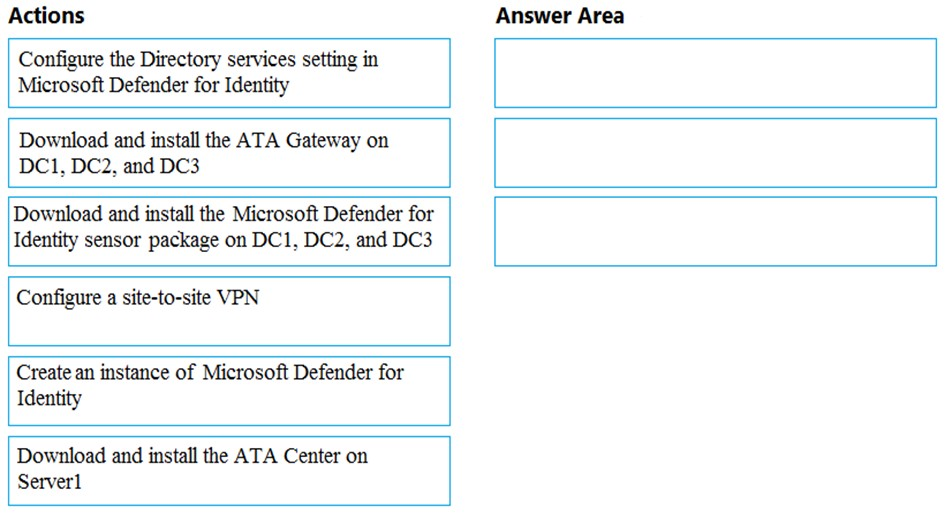
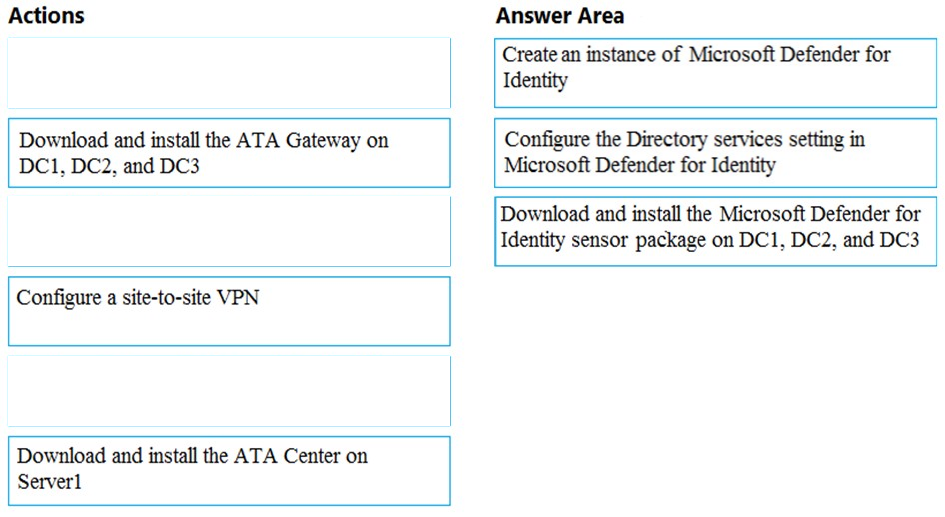
DRAG DROP - You need to configure threat detection for Active Directory. The solution must meet the security requirements. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
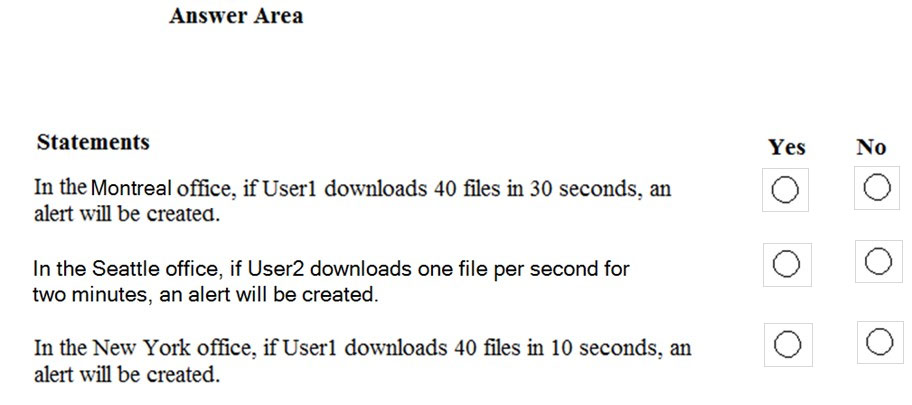
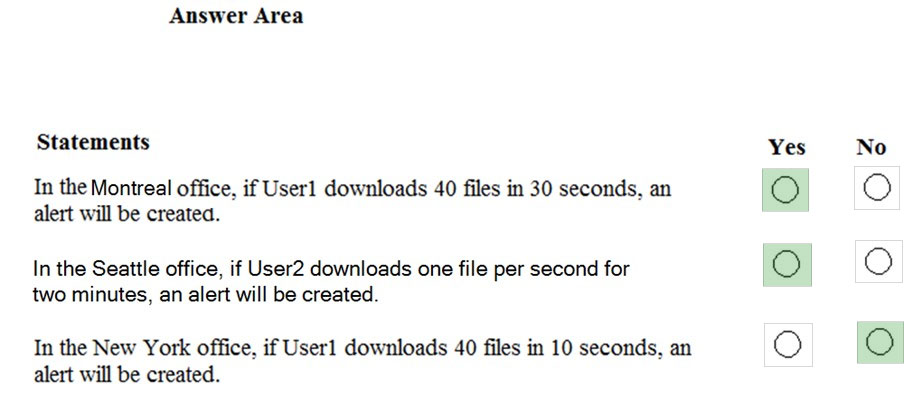
HOTSPOT - Your company has a Microsoft 365 subscription, a Microsoft Azure subscription, and an Azure Active Directory (Azure AD) tenant named contoso.com. The company has the offices shown in the following table.The tenant contains the users shown in the following table.
You create the Microsoft Cloud App Security policy shown in the following exhibit.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You configure Microsoft Azure Active Directory (Azure AD) Connect as shown in the following exhibit.Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point. Hot Area:
SIMULATION - Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time. When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design. Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task. Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided. Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab. Username and password -Use the following login credentials as needed: To enter your username, place your cursor in the Sign in box and click on the username below. To enter your password, place your cursor in the Enter password box and click on the password below. Microsoft 365 Username: admin@LODSe244001.onmicrosoft.com Microsoft 365 Password: &=Q8v@2qGzYz If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab. The following information is for technical support purposes only: Lab instance: 11032396 - You need to ensure that each user can join up to five devices to Azure Active Directory (Azure AD). To complete this task, sign in to the Microsoft Office 365 admin center.
SIMULATION - You need to create an Azure Information Protection label to meet the following requirements: ✑ Content must expire after 21 days. ✑ Offline access must be allowed for 21 days only. ✑ Documents must be protected by using a cloud key. ✑ Authenticated users must be able to view content only. To complete this task, sign in to the Microsoft 365 admin center.
You have a Microsoft 365 tenant that is linked to a hybrid Azure Active Directory (Azure AD) tenant named contoso.com. You need to enable Azure AD Seamless Single Sign-On (Azure AD SSO) for contoso.com. What should you use?
A. Azure AD Connect
B. the Microsoft 365 Defender portal
C. the Microsoft 365 Security admin center
D. the Microsoft 365 admin center
HOTSPOT - You have the Microsoft Azure Information Protection conditions shown in the following table.You have the Azure Information Protection labels shown in the following table.
You have the Azure Information Protection policies shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 E5 subscription that contains 500 Windows 10 devices. The subscription uses Microsoft Defender for Endpoint and is integrated with Microsoft Endpoint Manager. All the devices have Defender for Endpoint deployed. You create a Conditional Access policy as shown in the following table.You need to ensure that devices that have a machine risk score of high are blocked. What should you do in Microsoft Endpoint Manager?
A. Apply a security baseline to all the devices.
B. Apply an endpoint detection and response policy to the subscription.
C. Apply a compliance policy to all the devices.
D. Configure the Compliance policy settings.
You have a Microsoft 365 subscription. All computers run Windows 10 Enterprise and are managed by using Microsoft Endpoint Manager. You plan to view only security-related Windows telemetry data. You need to ensure that only Windows security data is sent to Microsoft. What should you create from the Endpoint Management admin center?
A. a device configuration profile that has device restrictions configured
B. a device configuration profile that has the Endpoint Protection settings configured
C. a device compliance policy that has the System Security settings configured
D. a device compliance policy that has the Device Health settings configured
You have a hybrid Microsoft 365 environment. All computers run Windows 10 Enterprise and have Microsoft 365 Apps for enterprise installed. All the computers are joined to Active Directory. You have a server named Server1 that runs Windows Server 2016. Server1 hosts the telemetry database. You need to prevent private details in the telemetry data from being transmitted to Microsoft. What should you do?
A. On Server1, run readinessreportcreator.exe
B. Configure a registry entry on Server1
C. Configure a registry entry on the computers
D. On the computers, run tdadm.exe
You have a hybrid deployment of Azure Active Directory (Azure AD) that contains two users named User1 and User2. You need to assign Role Based Access Control (RBAC) roles to User1 and User2 to meet the following requirements: ✑ Use the principle of least privilege. ✑ Enable User1 to view sync errors by using Azure AD Connect Health. ✑ Enable User2 to configure Azure Active Directory Connect Health Settings. Which two roles should you assign? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. The Monitoring Reader role in Azure AD Connect Health to User1
B. The Security reader role in Azure AD to User1
C. The Reports reader role in Azure AD to User1
D. The Contributor role in Azure AD Connect Health to User2
E. The Monitoring Contributor role in Azure AD Connect Health to User2
F. The Security operator role in Azure AD to User2
You have a Microsoft 365 E5 subscription that uses Azure Active Directory (Azure AD) Privileged Identity Management (PIM). A user named User1 is eligible for the User Account Administrator role. You need User1 to request to activate the User Account Administrator role. From where should User1 request to activate the role?
A. the My Access portal
B. the Microsoft 365 Defender portal
C. the Microsoft 365 admin center
D. the Azure Active Directory admin center
You have a Microsoft 365 subscription. You have a Microsoft SharePoint Online site named Site1. You have a Data Subject Request (DSR) case named Case1 that searches Site1. You create a new sensitive information type. You need to ensure that Case1 returns all the documents that contain the new sensitive information type. What should you do?
A. From the Microsoft 365 Compliance center, create a new Search by ID List.
B. From Site1, modify the search dictionary.
C. From the Microsoft 365 Compliance center, create a new Content search.
D. From Site1, initiate a re-indexing of Site1.
You have a Microsoft 365 E5 subscription that uses Privacy Risk Management in Microsoft Priva. You need to review the personal data type instances that were detected in the subscription. What should you use in the Microsoft Purview compliance portal?
A. Content search
B. an eDiscovery case
C. Content explorer
D. User data search
SIMULATION - You need to configure your organization to automatically quarantine all phishing email messages. To complete this task, sign in to the Microsoft 365 portal.
HOTSPOT - You have a Microsoft 365 E5 tenant that contains two users named User1 and User2 and a Microsoft SharePoint Online site named Site1 as shown in the following exhibit.For Site1, the users are assigned the roles shown in the following table.
You publish a retention label named Retention1 to Site1. To which files can the users apply Retention1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
An administrator configures Azure AD Privileged Identity Management as shown in the following exhibit.What should you do to meet the security requirements?
A. Change the Assignment Type for Admin2 to Permanent
B. From the Azure Active Directory admin center, assign the Exchange administrator role to Admin2
C. From the Azure Active Directory admin center, remove the Exchange administrator role to Admin1
D. Change the Assignment Type for Admin1 to Eligible
You have a Microsoft 365 subscription. You create a supervision policy named Policy1, and you designate a user named User1 as the reviewer. What should User1 use to view supervised communications?
A. a team in Microsoft Teams
B. the Microsoft 365 Compliance center
C. Outlook on the web
D. the Exchange admin center
You have a Microsoft 365 tenant. You have a database that stores customer details. Each customer has a unique 13-digit identifier that consists of a fixed pattern of numbers and letters. You need to implement a data loss prevention (DLP) solution that meets the following requirements: ✑ Email messages that contain a single customer identifier can be sent outside your company. ✑ Email messages that contain two or more customer identifiers must be approved by the company's data privacy team. Which two components should you include in the solution? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. a sensitive information type
B. a sensitivity label
C. a retention label
D. a DLP policy
E. a mail flow rule
You have a Microsoft 365 E5 subscription and a Microsoft Sentinel workspace named Sentinel1. You need to launch the Guided Investigation – Process Alerts notebook in Sentinel1. What should you create first?
A. an Azure logic app
B. a Log Analytics workspace
C. an Azure Machine Learning workspace
D. a Kusto query
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 subscription that contains the users shown in the following table.You need to ensure that User1, User2, and User3 can use self-service password reset (SSPR). The solution must not affect User4. Solution: You enable SSPR for Group2. Does that meet the goal?
A. Yes
B. No
You have a Microsoft 365 E5 subscription. You implement Microsoft Defender for Office 365 safe attachments policies for all users. User reports that email messages containing attachments take longer than expected to be received. You need to reduce the amount of time it takes to receive email messages that contain attachments. The solution must ensure that all attachments are scanned for malware. Attachments that have malware must be blocked. What should you do?
A. Set the action to Block
B. Add an exception
C. Add a condition
D. Set the action to Dynamic Delivery
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 subscription that contains 1,000 user mailboxes. An administrator named Admin1 must be able to search for the name of a competing company in the mailbox of a user named User5. You need to ensure that Admin1 can search the mailbox of User5 successfully. The solution must prevent Admin1 from sending email messages as User5. Solution: You start a message trace, and then create a Data Subject Request (DSR) case. Does this meet the goal?
A. Yes
B. No
Your company uses Microsoft Azure Advanced Threat Protection (ATP). You enable the delayed deployment of updates for an Azure ATP sensor named Sensor1. How long after the Azure ATP cloud service is updated will Sensor1 be updated?
A. 7 days
B. 24 hours
C. 1 hour
D. 48 hours
E. 12 hours
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 tenant. You create a label named CompanyConfidential in Microsoft Azure Information Protection. You add CompanyConfidential to a global policy. A user protects an email message by using CompanyConfidential and sends the label to several external recipients. The external recipients report that they cannot open the email message. You need to ensure that the external recipients can open protected email messages sent to them. You create a new label in the global policy and instruct the user to resend the email message. Does that meet the goal?
A. Yes
B. No
You have a Microsoft 365 subscription. You create a retention policy and apply the policy to Exchange Online mailboxes. You need to ensure that the retention policy tags can be assigned to mailbox items as soon as possible. What should you do?
A. From Exchange Online PowerShell, run Start-RetentionAutoTagLearning
B. From Exchange Online PowerShell, run Start-ManagedFolderAssistant
C. From the Microsoft 365 Compliance admin center, create a data loss prevention (DLP) policy
D. From the Microsoft 365 Compliance admin center, create a label policy
HOTSPOT - You have a Microsoft 365 E5 subscription that contains the users shown in the following table.You need to delegate the following tasks: • Create and manage data loss prevention (DLP) policies. • Review classified content by using Content explorer. The solution must use the principle of least privilege. Which user should perform each task? To answer, drag the appropriate users to the correct tasks. Each user may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription. Some users are required to use an authenticator app to access Microsoft SharePoint Online. You need to view which users have used an authenticator app to access SharePoint Online. The solution must minimize costs. What should you do?
A. From the Azure Active Directory admin center, view the sign-ins.
B. From the Microsoft 365 Security admin center, download a report.
C. From the Enterprise applications blade of the Azure Active Directory admin center, view the audit logs.
D. From the Azure Active Directory admin center, view the authentication methods.
You have a Microsoft 365 subscription that contains a user named User1. You need to assign User1 permissions to search Microsoft Office 365 audit logs. What should you use?
A. the Azure Active Directory admin center
B. the Exchange admin center
C. the Microsoft 365 Defender portal
D. the Microsoft 365 Compliance center
You create an Azure Sentinel workspace. You configure Azure Sentinel to ingest data from Azure Active Directory (Azure AD). In the Azure Active Directory admin center, you discover Azure AD Identity Protection alerts. The Azure Sentinel workspace shows the status as shown in the following exhibit.In Azure Log Analytics, you can see Azure AD data in the Azure Sentinel workspace. What should you configure in Azure Sentinel to ensure that incidents are created for detected threats?
A. data connectors
B. rules
C. workbooks
D. hunting queries
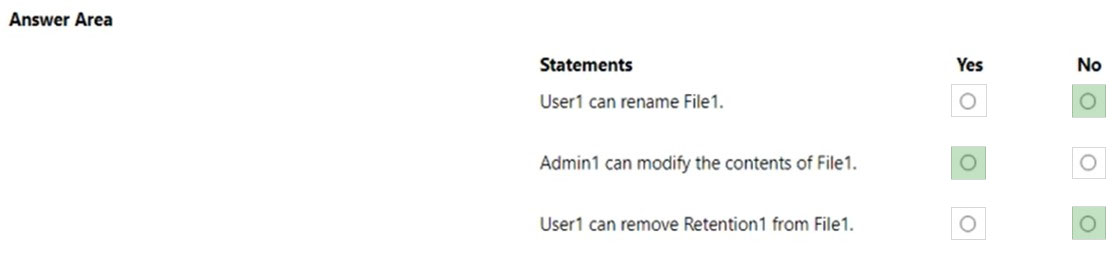
HOTSPOT - You have a Microsoft 365 E5 subscription that contains two users named Admin1 and User1, a Microsoft SharePoint Online site named Site1, and a retention label named Retention1. The role assignments for Site1 are shown in the following table.Site1 includes a file named File1. Rentention1 has the following settings: * Retain items for a specific period: Retention period: 7 years * During the retention period: Mark items as a record * At the end of the retention period: Delete items automatically Rentention1 is published to Site1. User1 applies Retention1 to File1. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
Access Full MS-500 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of MS-500 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your MS-500 certification journey!