MS-500 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your MS-500 certification? Our MS-500 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an MS-500 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our MS-500 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
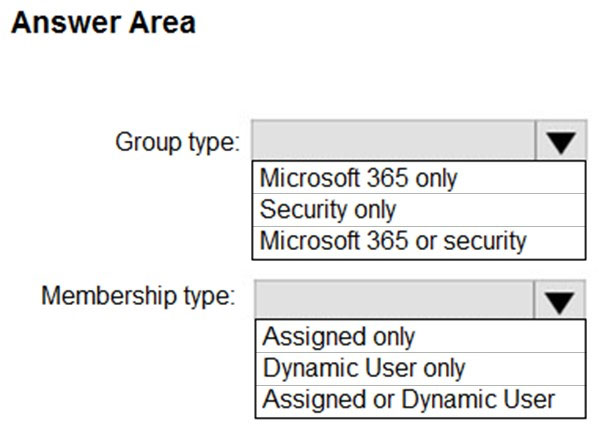
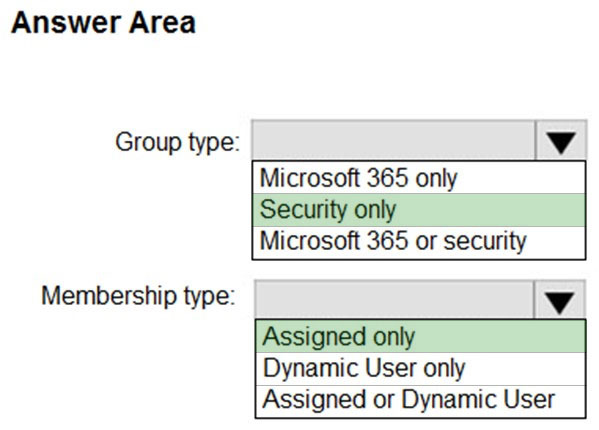
HOTSPOT - You have a Microsoft 365 E5 subscription. You need to create a role-assignable group. The solution must ensure that you can nest the group. How should you configure the group? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
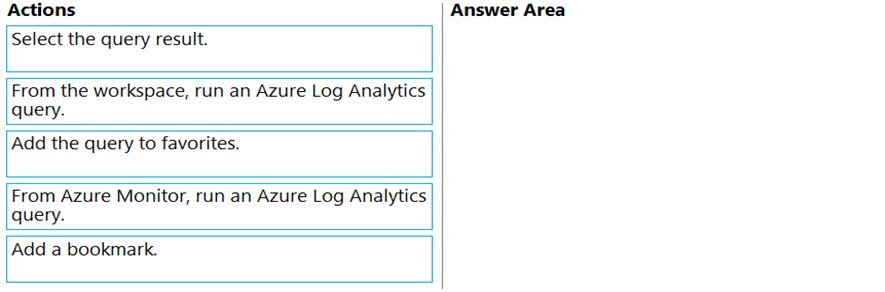
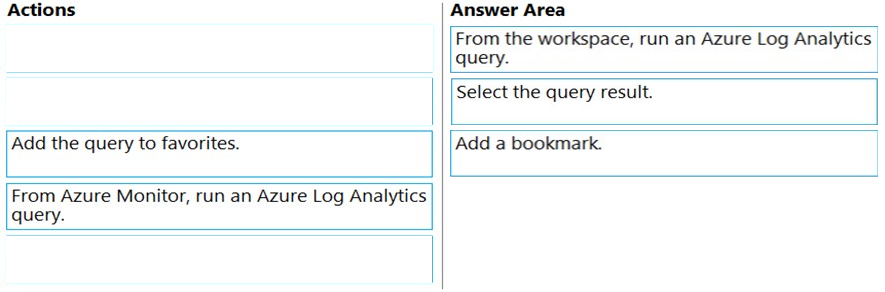
DRAG DROP - You have an Azure Sentinel workspace that has an Office 365 connector. You are threat hunting events that have suspicious traffic from specific IP addresses. You need to save the events and the relevant query results for future reference. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
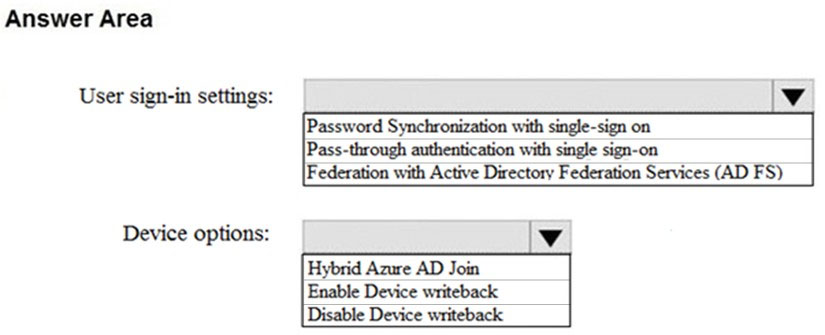
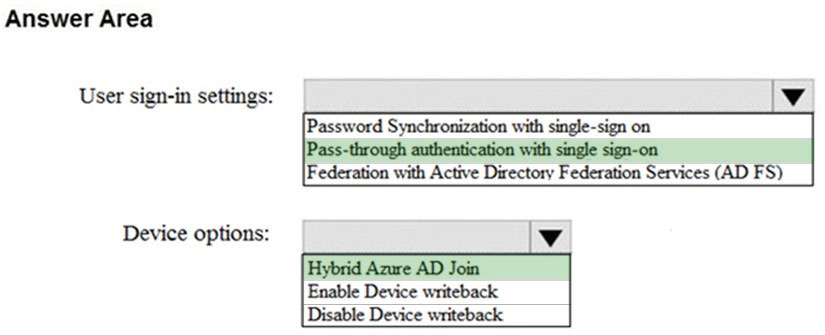
Your network contains an on-premises Active Directory domain named contoso.local that has a forest functional level of Windows Server 2008 R2. You have a Microsoft 365 E5 subscription linked to an Azure Active Directory (Azure AD) tenant named contoso.com. You plan to install Azure AD Connect and enable single sign-on (SSO). You need to prepare the domain to support SSO. The solution must minimize administrative effort. What should you do?
A. Raise the forest functional level to Windows Server 2016.
B. Modify the UPN suffix of all domain users.
C. Populate the mail attribute of all domain users.
D. Rename the domain.
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.You need to identify which user can enable Microsoft Defender for Endpoint roles. Which user should you identify?
A. User1
B. User4
C. User3
D. User2
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 subscription that contains 1,000 user mailboxes. An administrator named Admin1 must be able to search for the name of a competing company in the mailbox of a user named User5. You need to ensure that Admin1 can search the mailbox of User5 successfully. The solution must prevent Admin1 from sending email messages as User5. Solution: You assign the eDiscovery Manager role to Admin1, and then create an eDiscovery case. Does this meet the goal?
A. Yes
B. No
You have an Azure Sentinel workspace. You need to manage incidents based on alerts generated by Microsoft Cloud App Security. What should you do first?
A. From the Cloud App Security portal, configure security extensions.
B. From the Cloud App Security portal, configure app connectors.
C. From the Cloud App Security portal, configure log collectors.
D. From the Microsoft 365 compliance center, add and configure a data connector.
SIMULATION - You need to ensure that administrators can publish a label that adds a footer to email messages and documents. To complete this task, sign in to the Microsoft Office 365 portal.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your on-premises network contains a server that runs Windows Server 2019, computers that run Windows 10, macOS, or Linux, and a firewall that utilizes syslog. You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint. All the computers are onboarded to Microsoft Defender for Endpoint. You are implementing Microsoft Defender for Cloud Apps. You need to discover which cloud apps are accessed from the computers. Solution: You install a Microsoft Defender for Identity sensor on the server. Does this meet the goal?
A. Yes
B. No
An administrator plans to deploy several Azure Advanced Threat Protection (ATP) sensors. You need to provide the administrator with the Azure information required to deploy the sensors. What information should you provide?
A. an Azure Active Directory Authentication Library (ADAL) token
B. the public key
C. the access key
D. the URL of the Azure ATP admin center
Your network contains an on-premises Active Directory domain. The domain contains servers that run Windows Server and have advanced auditing enabled. The security logs of the servers are collected by using a third-party SIEM solution. You purchase a Microsoft 365 subscription and plan to deploy Microsoft Defender for Identity by using standalone sensors. You need to ensure that you can detect when sensitive groups are modified and when malicious services are created. What should you do?
A. Configure Event Forwarding on the domain controllers.
B. Configure auditing in the Office 365 Security & Compliance center.
C. Turn on Delayed updates for the Microsoft Defender for Identity sensors.
D. Enable the Audit account management Group Policy setting for the servers.
You have a Microsoft 365 tenant that uses Azure Information Protection to encrypt sensitive content. You plan to implement Microsoft Defender for Cloud Apps to inspect protected files that are uploaded to Microsoft OneDrive for Business. You need to ensure that all Azure Information Protection-protected files can be scanned by using Defender for Cloud Apps. Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. From the Microsoft Purview compliance portal, create a data loss prevention (DLP) policy that contains an exception for content that contains a sensitive information type.
B. From the Microsoft Defender for Cloud Apps portal, enable file monitoring of software as a service (SaaS) apps.
C. From the Microsoft Defender for Cloud Apps portal, create an OAuth app policy for apps that have the Have full access to user files permission.
D. From the Azure Active Directory admin center, grant Microsoft Defender for Cloud Apps permission to read all the protected content of the tenant.
You have a Microsoft 365 subscription. You have a Data Subject Request (DSR) case named Case1. You need to ensure that Case1 includes all the email posted by the data subject to the Microsoft Exchange Online public folders. Which additional property should you include in the Content Search query?
A. kind:externaldata
B. itemclass:ipm.externaldata
C. itemclass:ipm.post
D. kind:email
You have a Microsoft 365 E5 subscription. A user reports that changes were made to several files in Microsoft OneDrive. You need to identify which files were modified by which users in the user's OneDrive. What should you do?
A. From the Azure Active Directory admin center, open the audit log.
B. From the OneDrive admin center, select Device access.
C. FromMicrosoft 365 Compliance center, perform an eDiscovery search.
D. From Microsoft Cloud App Security, open the activity log.
Several users in your Microsoft 365 subscription report that they received an email message without the attachment. You need to review the attachments that were removed from the messages. Which two tools can you use? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. the Exchange admin center
B. Azure Defender for Servers
C. Outlook on the web
D. the Microsoft 365 Compliance center.
E. Microsoft Defender for Identity admin center
You have a Microsoft 365 E5 subscription. You implement Microsoft Defender for Office 365 safe attachments policies for all users. User reports that email messages containing attachments take longer than expected to be received. You need to reduce the amount of time it takes to receive email messages that contain attachments. The solution must ensure that all attachments are scanned for malware. Attachments that have malware must be blocked. What should you do?
A. Set the action to Block
B. Add an exception
C. Add a condition
D. Set the action to Dynamic Delivery
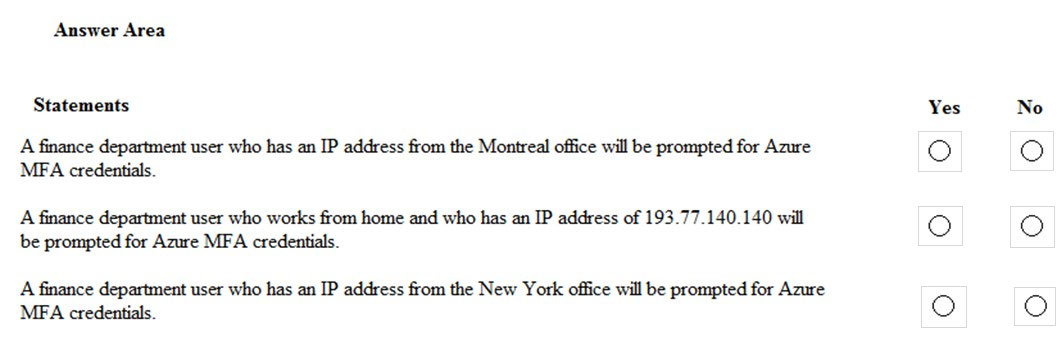
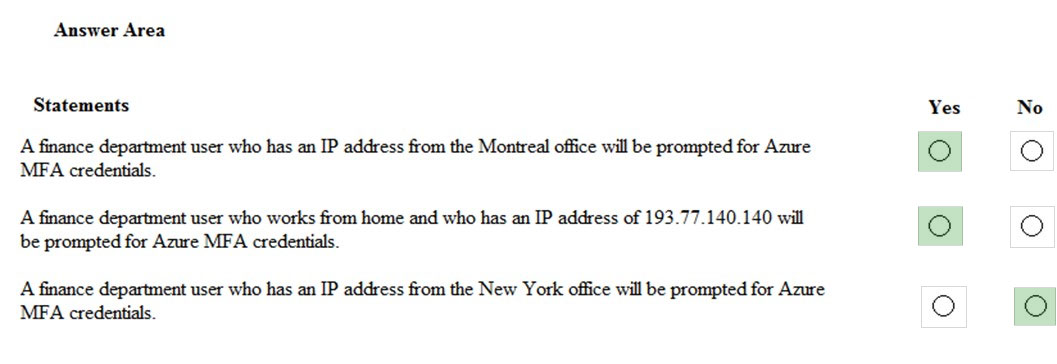
HOTSPOT - You are evaluating which finance department users will be prompted for Azure MFA credentials. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 subscription. Yesterday, you created retention labels and published the labels to Microsoft Exchange Online mailboxes. You need to ensure that the labels will be available for manual assignment as soon as possible. What should you do?
A. From the Microsoft 365 Compliance center, create a label policy
B. From Exchange Online PowerShell, run Start-RetentionAutoTagLearning
C. From Exchange Online PowerShell, run Start-ManagedFolderAssistant
D. From the Microsoft 365 Compliance center, create a data loss prevention (DLP) policy
SIMULATION - You need to ensure that unmanaged mobile devices are quarantined when the devices attempt to connect to Exchange Online. To complete this task, sign in to the Microsoft 365 portal.
You configure several Advanced Threat Protection (ATP) policies in a Microsoft 365 subscription. You need to allow a user named User1 to view ATP reports from the Threat management dashboard. Which role provides User1 with the required role permissions?
A. Compliance administrator
B. Security reader
C. Message center reader
D. Reports reader
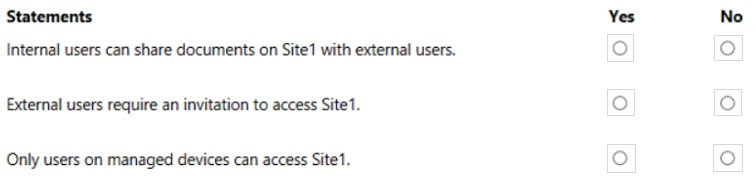
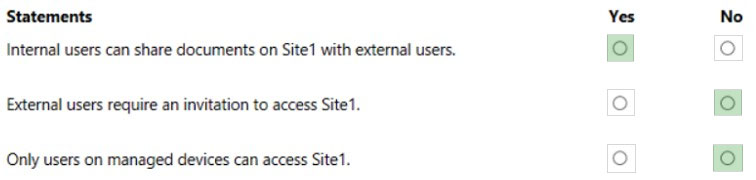
HOTSPOT - You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1 and a sensitivity label named Label1. The external sharing settings for Site1 are configured as shown in the Site1 exhibit. (Click the Site1 tab.)The external sharing settings for Label1 are configured as shown in the Label1 exhibit. (Click the Label1 tab.)
Label 1 is applied to Site1. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You have a Microsoft 365 E5 subscription that contains four users named User1, User2, User3, and User4. In Azure AD Identity Protection, you configure User4 as the only recipient of Users at risk detected alerts. You set Alert on user risk level at or above to Low. Azure AD Identity Protection detects the risk events shown in the following table.How many alerts will User4 receive that include User1, and how many alerts will User4 receive that include User2 and User3? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
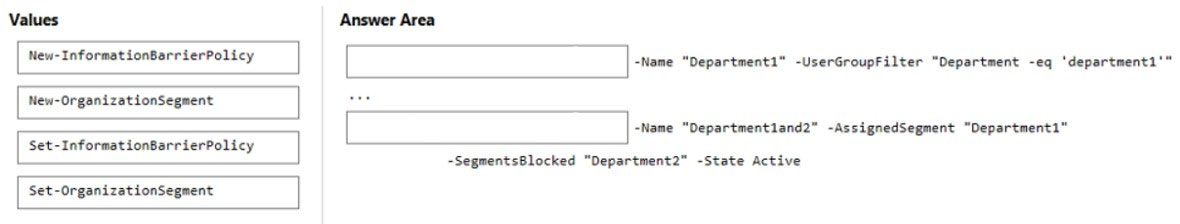
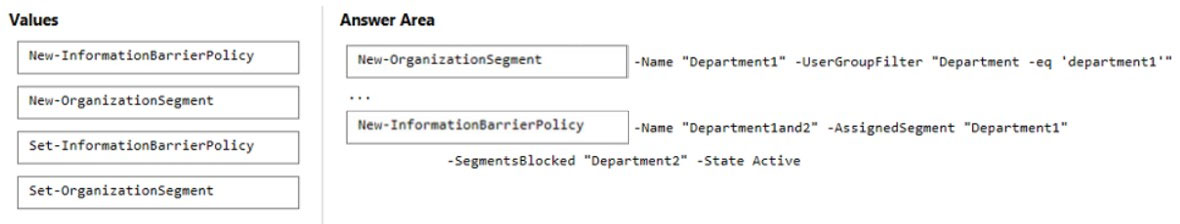
DRAG DROP - Your company has two departments named department1 and department2 and a Microsoft 365 E5 subscription. You need to prevent communication between the users in department1 and the users in department2. How should you complete the PowerShell script? To answer, drag the appropriate values to the correct targets. Each value may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place:
HOTSPOT - You have a Microsoft SharePoint Online site named Site1 that contains the files shown in the following table.You have a data loss prevention (DLP) policy named DLP1 that has the advanced DLP rules shown in the following table.
You apply DLP1 to Site1. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription. You need to enable auditing for all Microsoft Exchange Online users. What should you do?
A. From the Exchange admin center, create a journal rule
B. Run the Set-MailboxDatabase cmdlet
C. Run the Set-Mailbox cmdlet
D. From the Exchange admin center, create a mail flow message trace rule.
You have a Microsoft 365 Enterprise E5 subscription. You use Microsoft Defender for Endpoint. You need to integrate Microsoft Defender for Office 365 and Microsoft Defender for Endpoint. Where should you configure the integration?
A. From the Microsoft 365 admin center, select Settings, and then select Services & add-ins.
B. From the Microsoft 365 security admin center, select Threat management, and then select Explorer.
C. From the Microsoft 365 admin center, select Reports, and then select Security & Compliance.
D. From the Microsoft 365 security admin center, select Threat management and then select Threat tracker.
You have a Microsoft 365 tenant. You need to implement a policy to enforce the following requirements: ✑ If a user uses a Windows 10 device that is NOT hybrid Azure Active Directory (Azure AD) joined, the user must be allowed to connect to Microsoft SharePoint Online only from a web browser. The user must be prevented from downloading files or syncing files from SharePoint Online. ✑ If a user uses a Windows 10 device that is hybrid Azure AD joined, the user must be able connect to SharePoint Online from any client application, download files, and sync files. What should you create?
A. a conditional access policy in Azure AD that has Client apps conditions configured
B. a conditional access policy in Azure AD that has Session controls configured
C. a compliance policy in Microsoft Endpoint Manager that has the Device Properties settings configured
D. a compliance policy in Microsoft Endpoint Manager that has the Device Health settings configured
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 E5 subscription that contains a user named User1. The Azure Active Directory (Azure AD) Identity Protection risky users report identifies User1. For User1, you select Confirm user compromised. User1 can still sign in. You need to prevent User1 from signing in. The solution must minimize the impact on users at a lower risk level. Solution: From the Access settings, you select Block access for User1. Does this meet the goal?
A. Yes
B. No
HOTSPOT - You have the Microsoft Azure Information Protection conditions shown in the following table.You have the Azure Information Protection labels shown in the following table.
You have the Azure Information Protection policies shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You need to resolve the issue that generates the automated email messages to the IT team. Which tool should you run first?
A. Synchronization Service Manager
B. Azure AD Connect wizard
C. Synchronization Rules Editor
D. IdFix
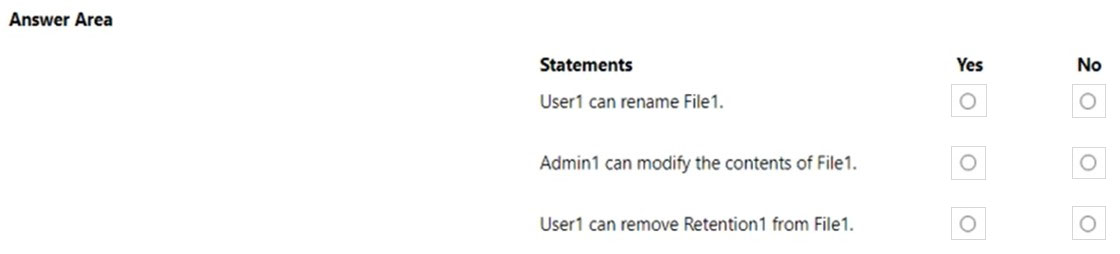
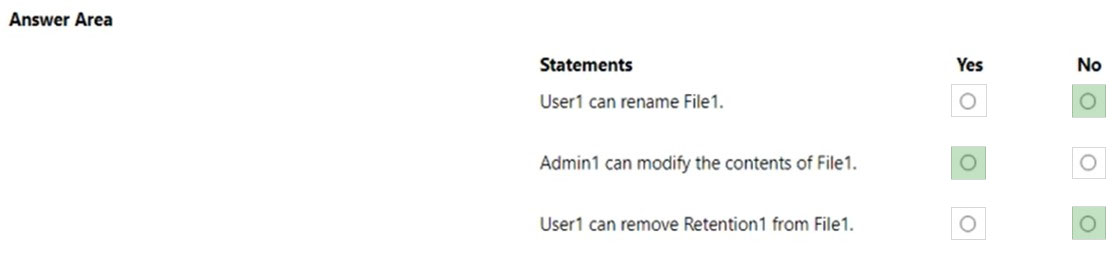
HOTSPOT - You have a Microsoft 365 E5 subscription that contains two users named Admin1 and User1, a Microsoft SharePoint Online site named Site1, and a retention label named Retention1. The role assignments for Site1 are shown in the following table.Site1 includes a file named File1. Rentention1 has the following settings: * Retain items for a specific period: Retention period: 7 years * During the retention period: Mark items as a record * At the end of the retention period: Delete items automatically Rentention1 is published to Site1. User1 applies Retention1 to File1. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
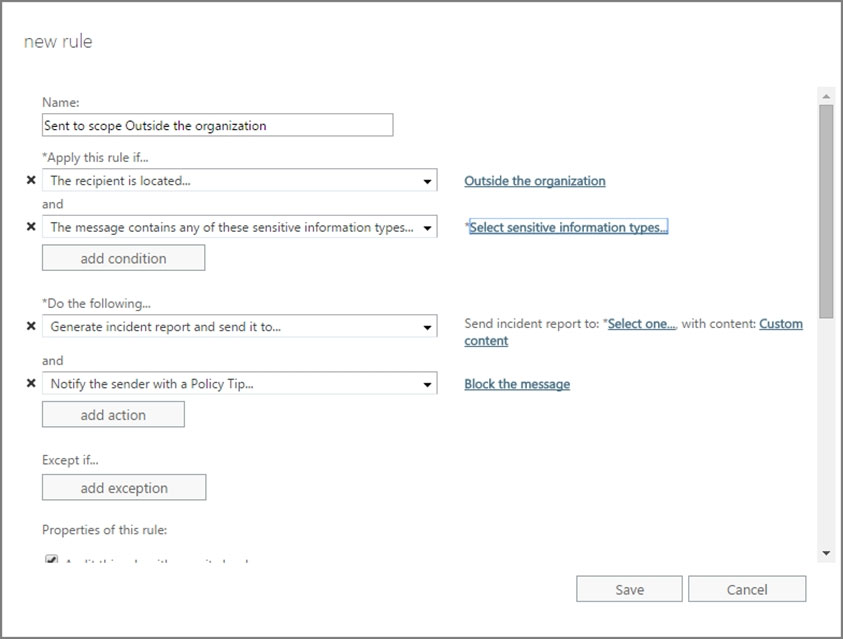
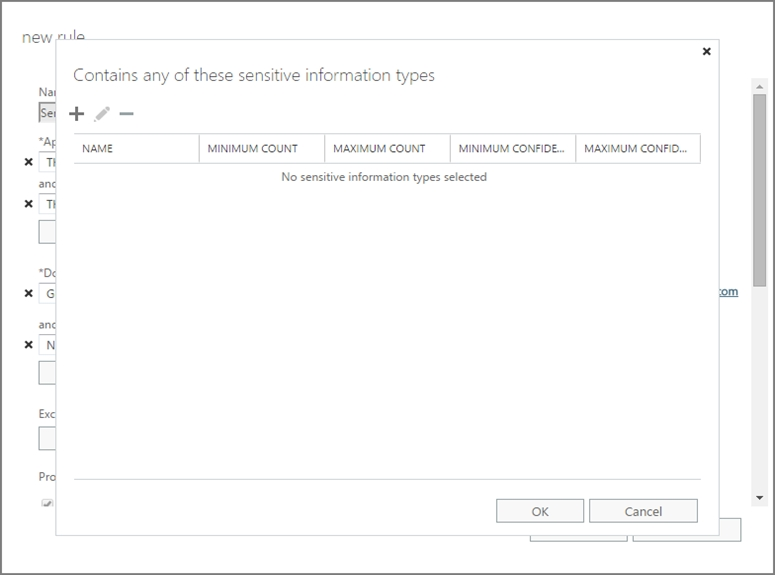
SIMULATION - You need to prevent any email messages that contain data covered by the U.K. Data Protection Act from being sent to recipients outside of your organization, unless the messages are sent to an external domain named adatum.com. To complete this task, sign in to the Microsoft 365 admin center.
You have a Microsoft 365 subscription. Your company uses Jamf Pro to manage macOS devices. You plan to create device compliance policies for the macOS devices based on the Jamf Pro data. You need to connect Microsoft Endpoint Manager to Jamf Pro. What should you do first?
A. From the Azure Active Directory admin center, add a Mobility (MDM and MAM) application.
B. From the Endpoint Management admin center, add the Mobile Threat Defense connector.
C. From the Endpoint Management admin center, configure Partner device management.
D. From the Azure Active Directory admin center, register an application.
You recently created and published several label policies in a Microsoft 365 subscription. You need to view which labels were applied by users manually and which labels were applied automatically. What should you do from the Microsoft 365 Compliance center?
A. From Search & investigation, select Content search
B. From Alerts, select View alerts
C. From eDiscovery, view an eDiscovery case
D. From Reports, select Dashboard
You have a Microsoft 365 subscription. You create a retention policy and apply the policy to Exchange Online mailboxes. You need to ensure that the retention policy tags can be assigned to mailbox items as soon as possible. What should you do?
A. From Exchange Online PowerShell, run Start-RetentionAutoTagLearning
B. From Exchange Online PowerShell, run Start-ManagedFolderAssistant
C. From the Microsoft 365 Compliance admin center, create a data loss prevention (DLP) policy
D. From the Microsoft 365 Compliance admin center, create a label policy
You need to create Group3. What are two possible ways to create the group?
A. a Microsoft 365 group in the Microsoft 365 admin center
B. a mail-enabled security group in the Microsoft 365 admin center
C. a security group in the Microsoft 365 admin center
D. a distribution group in the Microsoft 365 admin center
E. a security group in the Azure AD admin center
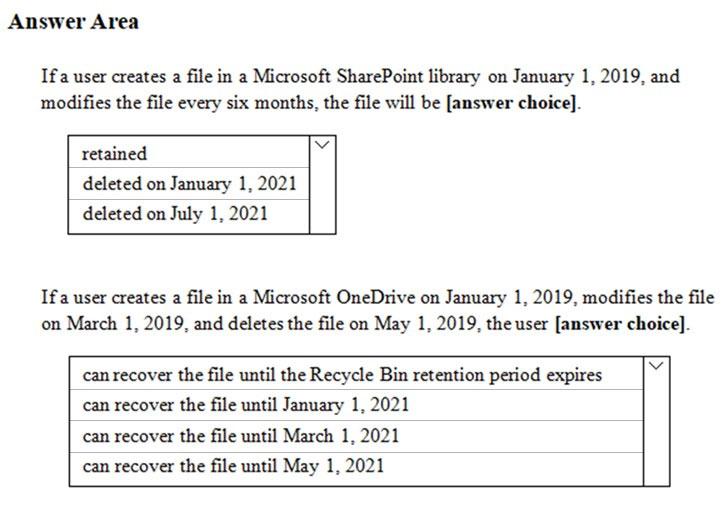
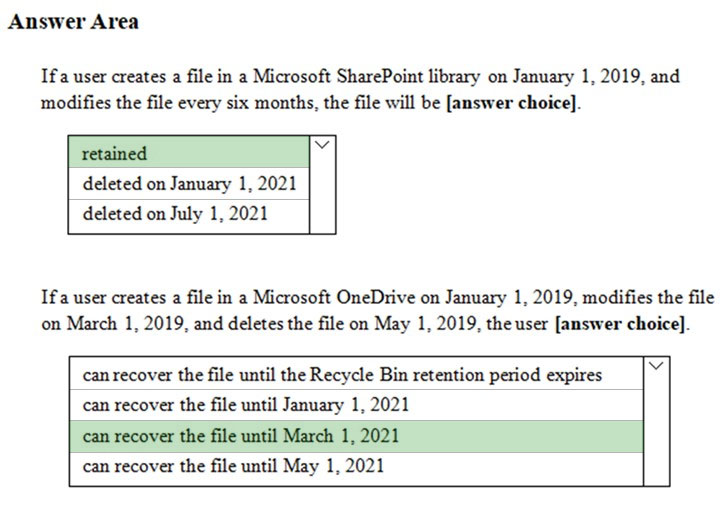
HOTSPOT - You have a Microsoft 365 subscription. You are creating a retention policy named Retention1 as shown in the following exhibit. (Click the Exhibit tab.)You apply Retention1 to SharePoint sites and OneDrive accounts. Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point. Hot Area:
Your network contains an on-premises Active Directory domain and a Microsoft 365 subscription. You plan to deploy a hybrid Azure Active Directory (Azure AD) tenant that has Azure AD Identity Protection risk policies enabled. You need to configure Azure AD Connect to support the planned deployment. Which Azure AD Connect authentication method should you select?
A. Federation with AD FS
B. Federation with PingFederate
C. Password Hash Synchronization
D. Pass-through authentication
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your on-premises network contains a server that runs Windows Server 2019, computers that run Windows 10, macOS, or Linux, and a firewall that utilizes syslog. You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint. All the computers are onboarded to Microsoft Defender for Endpoint. You are implementing Microsoft Defender for Cloud Apps. You need to discover which cloud apps are accessed from the computers. Solution: You enable Defender for Endpoint and Defender for Cloud Apps integration. Does this meet the goal?
A. Yes
B. No
You have a Microsoft 365 E5 subscription that uses Microsoft Teams and contains a user named User1. You configure information barriers. You need to identify which information barrier policies apply to User1. Which cmdlet should you use?
A. Get-InformationBarrierRecipientStatus
B. Get-InformationBarrierPoliciesApplicationStatus
C. Get-InformationBarrierPolicy
D. Get-OrganizationSegment
You have a Microsoft SharePoint Online site named Site1 that contains the files shown in the following table.You have a data loss prevention (DLP) policy named DLP1 that has the advanced DLP rules shown in the following table.
You apply DLP1 to Site1. Which policy tips will appear for File2?
A. Tip2 only
B. Tip3 only
C. Tip1 only
D. Tip1 and Tip2 only
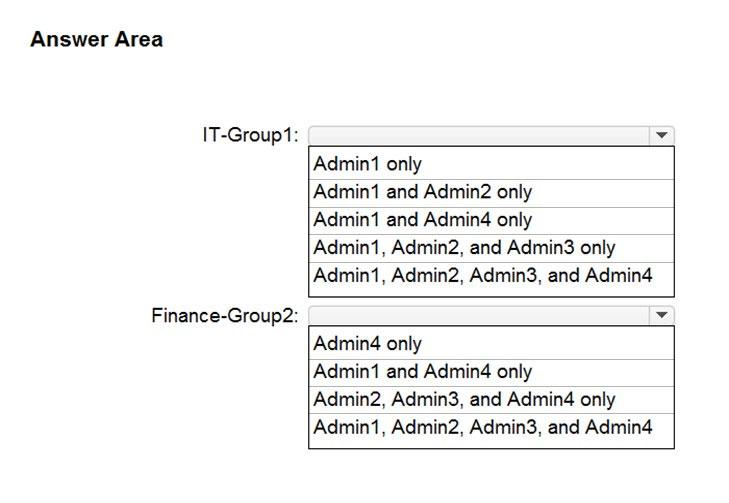
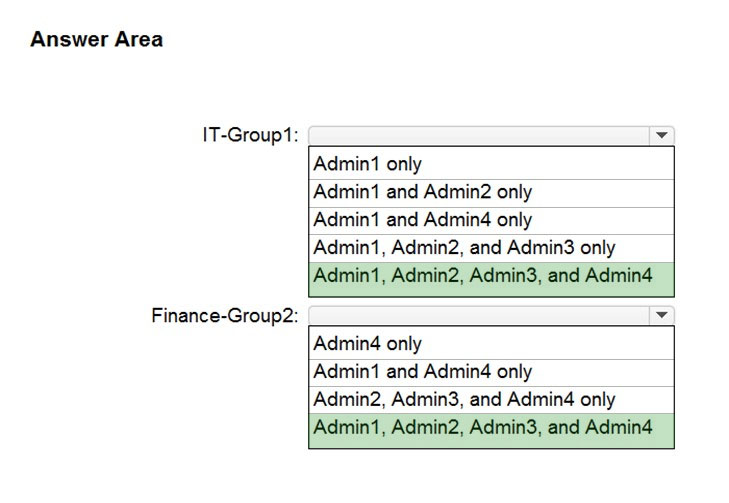
HOTSPOT - You have a Microsoft 365 E5 subscription that contains the users shown in the following table.For contoso.com, you create a group naming policy that has the following configuration. - You plan to create the groups shown in the following table.
Which users can be used to create each group? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 E5 subscription that contains two users named User1 and Admin1. Admin1 manages audit retention policies for the subscription. You need to ensure that the audit logs of User1 will be retained for 10 years. What should you do first?
A. Assign a 10-year audit log retention add-on license to Admin1.
B. Assign a Microsoft Purview Audit (Premium) add-on license to User1.
C. Assign a 10-year audit log retention add-on license to User1.
D. Assign a Microsoft Purview Audit (Premium) add-on license to Admin1.
HOTSPOT - You have a Microsoft 365 E5 subscription that contains two groups named Group1 and Group2 and the users shown in the following table.You have the Privileged Access settings configured as shown in the following exhibit.
You have a privileged access policy that has the following settings: • Policy name: New Transport Rule • Policy type: Task • Policy scope: Exchange • Approval Type: Manual • Approver group: Group1 User1 requests access to the New Transport Rule policy for a duration of two hours. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
HOTSPOT - How should you configure Azure AD Connect? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You create a label that encrypts email data. Users report that they cannot use the label in Outlook on the web to protect the email messages they send. You need to ensure that the users can use the new label to protect their email. What should you do?
A. Modify the priority order of label policies
B. Wait six hours and ask the users to try again
C. Create a label policy
D. Create a new sensitive information type
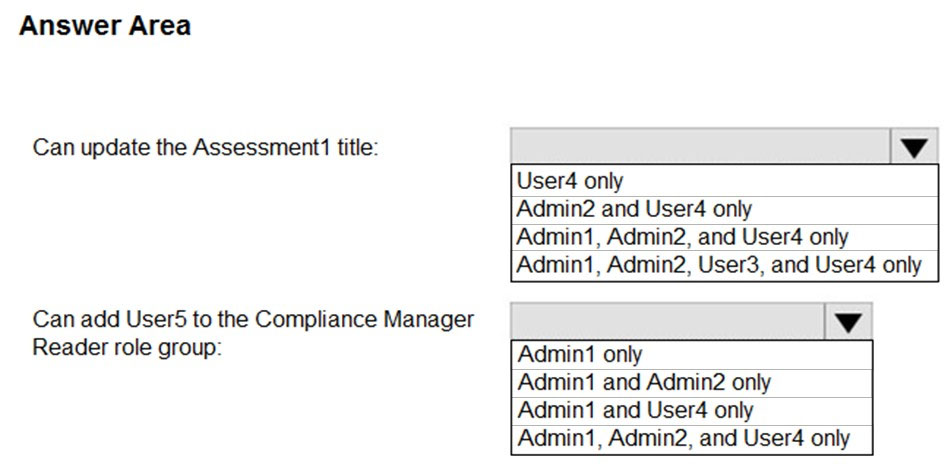
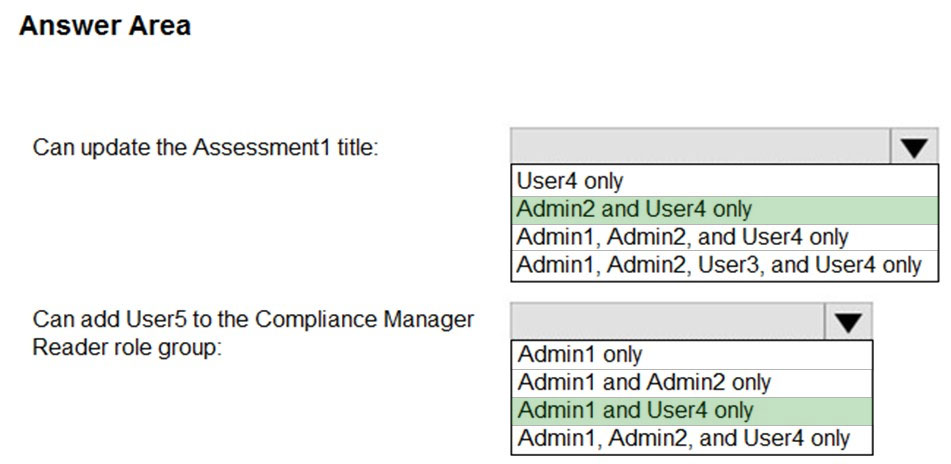
HOTSPOT - You have a Microsoft 365 E5 subscription that contains the users shown in the following table.You create an assessment named Assessment1 as shown in the following exhibit.
Which users can update the title of Assessment1, and which users can add User5 to the Compliance Manager Readers role group? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
SIMULATION - You need to ensure that all users must change their password every 100 days. To complete this task, sign in to the Microsoft 365 portal.
You have a Microsoft 365 E5 subscription. A customer requests access to all his personal data. You need to manage the customer’s request. What should you do first?
A. Create a content search.
B. Enable sharing with external users.
C. Set Require approval for all data access requests to On for Customer Lockbox.
D. Create a Data Subject Request (DSR) case.
Your company has 500 computers. You plan to protect the computers by using Microsoft Defender for Endpoint. Twenty of the computers belong to company executives. You need to recommend a remediation solution that meets the following requirements: ✑ Microsoft Defender for Endpoint administrators must manually approve all remediation for the executives ✑ Remediation must occur automatically for all other users What should you recommend doing from Microsoft 365 Defender portal?
A. Configure 20 system exclusions on automation allowed/block lists
B. Configure two alert notification rules
C. Download an offboarding package for the computers of the 20 executives
D. Create two device groups
You have a hybrid deployment of Microsoft 365 that contains the users shown in the following table.You plan to use Microsoft 365 Attack Simulator. You need to identify the users against which you can use Attack Simulator. Which users should you identify?
A. User3 only
B. User1, User2, User3, and User4
C. User3 and User4 only
D. User1 and User3 only
Access Full MS-500 Dump Free
Looking for even more practice questions? Click here to access the complete MS-500 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our MS-500 dump free questions — and get one step closer to exam success!