MS-203 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your MS-203 certification? Our MS-203 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an MS-203 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our MS-203 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
You have a Microsoft Exchange Server 2019 hybrid deployment. You plan to implement Hybrid Modern Authentication (HMA). You retrieve the Exchange virtual directory settings, and you discover the following output.You need to prepare the virtual directories for the planned implementation of HMA. What should you do?
A. Add OAuth as an authentication method.
B. Remove NTLM as an authentication method.
C. Delete https://mail.contoso.com from the ExternalUrl value.
D. Modify the InternalUrl value to http://mail.contoso.com.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft Exchange Server 2019 hybrid deployment. All user mailboxes are hosted in Microsoft 365. All outbound SMTP email is routed through the on-premises Exchange organization. A corporate security policy requires that you must prevent credit card numbers from being sent to internet recipients by using email. You need to configure the deployment to meet the security policy requirement. Solution: From the Exchange organization, you create a data loss prevention (DLP) policy. Does this meet the goal?
A. Yes
B. No
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft Exchange Online tenant that uses an email domain named contoso.com. You need to prevent all users from performing the following tasks: ✑ Sending out-of-office replies to an email domain named fabrikam.com. ✑ Sending automatic replies to an email domain named adatum.com. The solution must ensure that all the users can send out-of-office replies and automatic replies to other email domains on the internet. Solution: You create two sharing policies. Does this meet the goal?
A. Yes
B. No
You have a Microsoft Exchange Online tenant that has an email domain named contoso.com. Contoso.com routes all inbound email messages through a third-party email protection service. You discover that all the inbound email messages contain the source IP address of the email protection service. You need to ensure that all the inbound email messages retain the source IP address of the original sender. What should you do?
A. Modify the SPF TXT record of contoso.com.
B. Enable Enhanced Filtering for Connectors.
C. Configure a mail flow rule.
D. Add an entry for a spoofed sender to Tenant Allow/Block Lists.
You need to recommend an Office 365 solution that meets the technical requirements for email from adatum.com. Which two components should you recommend configuring from the Exchange admin center in Exchange Online? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. a malware filter
B. a connection filter
C. data loss prevention (DLP) policies
D. DKIM signatures
E. a spam filter
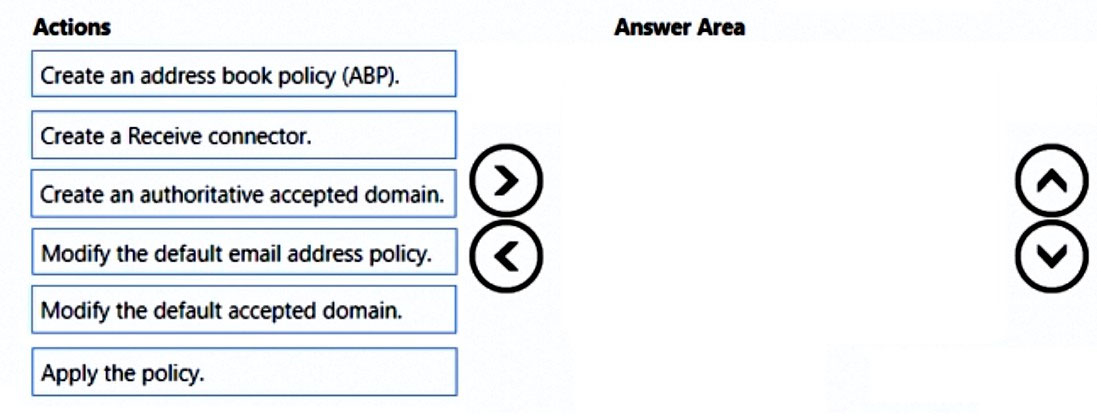
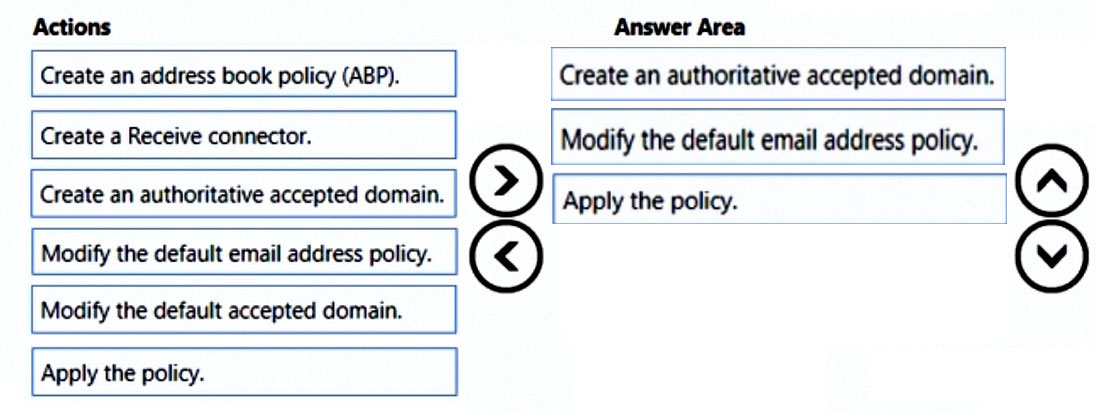
DRAG DROP - You have a Microsoft Exchange Server 2019 organization. All recipients have an SMTP address in the @adatum.com format. You purchase a new domain named contoso.com. You need to configure all the recipients to have a primary SMTP address in the @contoso.com format as soon as possible. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
DRAG DROP - You have a Microsoft Exchange Online tenant that contains two users named User1 and User2. You need to ensure that the users can perform the tasks shown in the following table.The solution must follow the principle of least privilege. To which role group should you add each user? To answer, drag the appropriate role groups to the correct users. Each role group may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
You manage a hybrid deployment between Microsoft Exchange Online and on-premises Exchange Server 2019. The deployment contains a primary SMTP domain named contoso.com. Users have email addresses that use a syntax of firstname.lastname@contoso.com . A user named Ben Smith receives a new client computer. You configure the computer to access Ben Smith's mailbox. Ben Smith reports that he cannot connect to his mailbox from the new computer. You verify that other users can connect successfully to their mailbox and that new users can discover their mailboxes by using Autodiscover. You need to ensure that Ben Smith can connect to his mailbox from the new computer. What should you do?
A. Modify the primarySmtpAddress property fox the mailbox of Ben Smith.
B. Modify the RemoteRoutingAddress parameter for the mailbox of Ben Smith.
C. Modify the email address of Ben Smith to use a syntax of lastname.firstname@contoso.com.
D. Modify the email address of Ben Smith to use a syntax of firstname.lastname@contoso.onmicrosoft.com.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft Exchange Online tenant that contains 1,000 mailboxes. All the users in the sales department at your company are in a group named Sales. The company is implementing a new policy to restrict the use of email attachments for the users in the Sales group. You need to prevent all email messages that contain attachments from being delivered to the users in the Sales group. Solution: You modify the Exchange Online Protection (EOP) settings. Does this meet the goal?
A. Yes
B. No
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your company has a Microsoft Exchange Server 2019 hybrid deployment that contains two Mailbox servers named MBX1 and MBX2. The company has the departments shown in the following table.From the on-premises organization, outbound email is sent directly to the Internet by using DNS lookups. You are informed that some sales department users send email messages that are identified as spam. You need to automatically block the sales department users from repeatedly sending spam. Solution: You modify the outbound spam filter policy in Exchange Online. Does this meet the goal?
A. Yes
B. No
You have a Microsoft Exchange Server 2019 organization. You plan to migrate all mailboxes to Exchange Online. You need to provide a user with the ability to perform the mailbox migrations. The solution must use the principle of least privilege. Which role should you assign to the user?
A. Recipient Management
B. Server Management
C. Help Desk
D. Organization Management
You need to configure the required objects for the branch office administrators. What should you create for each administrator?
A. a management role assignment policy and a management role group
B. a management role and a management role assignment policy
C. a management role scope and a management role assignment
D. a management role scope and a management role group
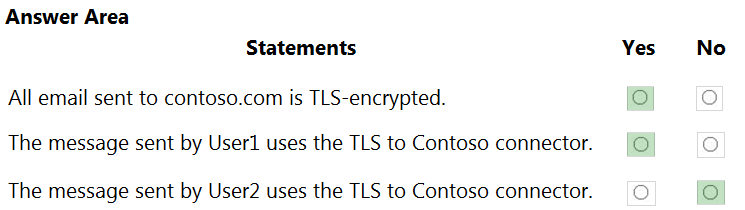
HOTSPOT - You have a Microsoft 365 E5 tenant that contains the users shown in the following table.You have a connector for a remote domain named contoso.com as shown in the following exhibit.
You have a transport rule as shown in the following exhibit.
User1 sends an email message to user3@contoso.com that has a subject line containing the word Confidential. User2 sends an email message to user4@contoso.com that has a subject line of New report. The body of the message contains the word confidential. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You have a Microsoft Exchange Online tenant. You plan to create a mail flow rule that will forward email messages containing specific words to a user’s manager for approval. You need to test the rule. The solution must meet the following requirements: • Prevent users from being notified that their message was forwarded to their manager. • Support the tracking of messages that match the rule by using message tracing. Which two settings should you modify? To answer, select the settings in the answer area. NOTE: Each correct selection is worth one point.
DRAG DROP - You have a Microsoft Exchange Online tenant that contains the users shown in the following table.You need to create audit retention policies to retain the mailbox activity of all the users. What is the maximum duration that you can set for each user? To answer, drag the appropriate duration values to the correct users. Each duration value may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft Exchange Online tenant that uses an email domain named contoso.com. You need to prevent all users from performing the following tasks: ✑ Sending out-of-office replies to an email domain named fabrikam.com. ✑ Sending automatic replies to an email domain named adatum.com. The solution must ensure that all the users can send out-of-office replies and automatic replies to other email domains on the internet. Solution: You create one mail flow rule. Does this meet the goal?
A. Yes
B. No
HOTSPOT - You have a Microsoft Exchange Online tenant named adatum.com that contains a user named User1. You plan to perform a new message trace for User1. The message trace must generate an Enhanced summary report. Which three Delivery status options can be included in the report? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
SIMULATION - Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time. When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design. Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task. Labs are not timed separately, and this exam may have more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided. Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.Use the following login credentials as needed: To enter your username, place your cursor in the Sign in box and click on the username below. To enter your password, place your cursor in the Enter password box and click on the password below. Microsoft 365 Username: admin@abc.com Microsoft 365 Password: xxxxxx - If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab. The following information is for technical support purposes only. Lab Instance: XXXXXX - You need to prevent users in your company from sending out-of-office replies to users who use an email address suffix of @contoso.com. The solution must NOT use mail flow rules. To complete this task, sign in to the Exchange admin center.
HOTSPOT - You have a Microsoft Exchange Online tenant. Archive mailboxes are enabled for all users. You need to ensure that the default size of each user’s archive mailbox increases automatically when the mailbox approaches the storage limit. The solution must apply automatically to all current and future mailboxes. How should you complete the PowerShell command? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
SIMULATION - Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time. When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design. Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task. Labs are not timed separately, and this exam may have more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided. Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.Use the following login credentials as needed: To enter your username, place your cursor in the Sign in box and click on the username below. To enter your password, place your cursor in the Enter password box and click on the password below. Microsoft 365 Username: admin@abc.com Microsoft 365 Password: xxxxxx - If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab. The following information is for technical support purposes only. Lab Instance: XXXXXX - You need to prevent email messages from a domain named fabrikam.com from being delivered to the mailboxes of your organization. To complete this task, sign in to the Microsoft 365 admin center.
You have a Microsoft Exchange Online tenant that contains a user named User1. User1 has a mobile device. You need to enable Exchange ActiveSync logging for User1 and retrieve the log files. Which two Exchange Online PowerShell cmdlets should you use? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Get-ActiveSyncDevice
B. Set-ActiveSyncMailboxPolicy
C. Set-ClientAccessRule
D. Get-MobileDeviceStatistics
E. Set-CASMailbox
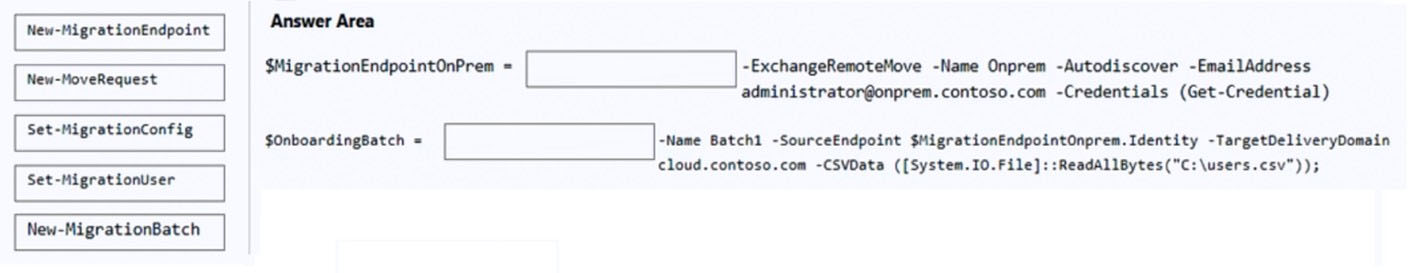
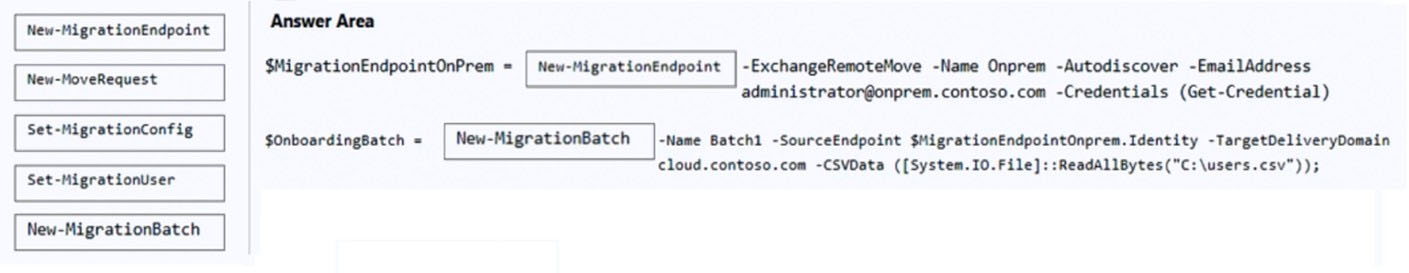
DRAG DROP - You have a hybrid deployment of Microsoft Exchange Server 2019. You need to migrate 500 users to Exchange Online. The details of the users are stored in a file named C:Users.csv. How should you complete the PowerShell commands? To answer, drag the appropriate cmdlets to the correct targets. Each cmdlet may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place:
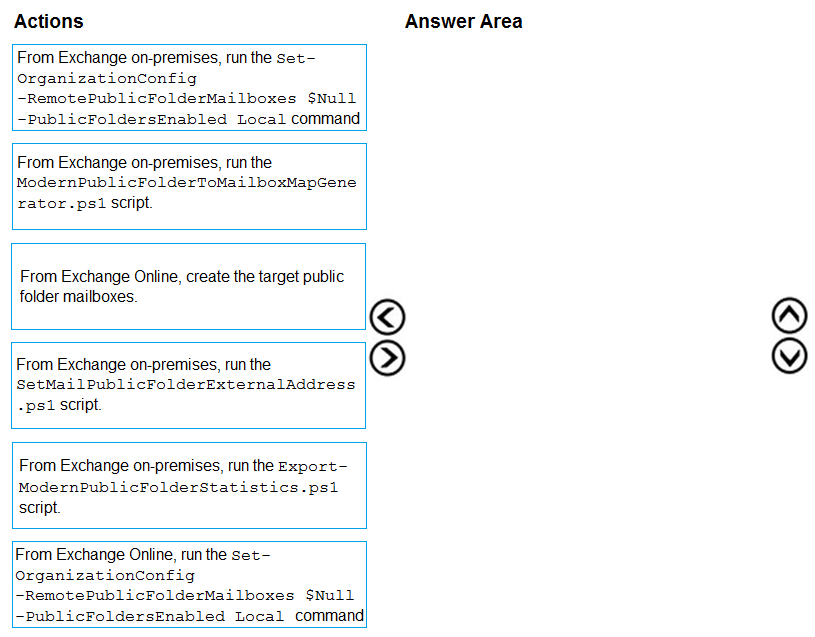
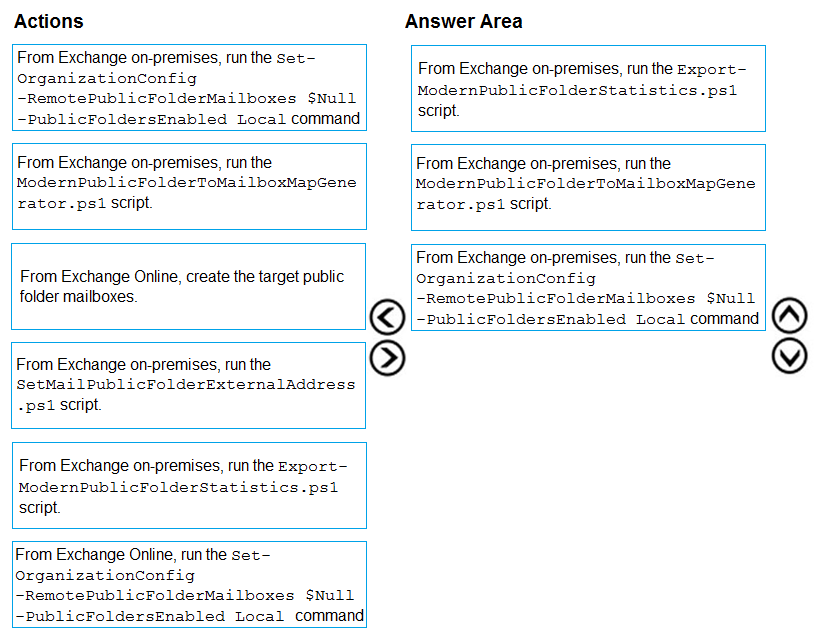
DRAG DROP - You have a Microsoft Exchange Server 2019 hybrid deployment. All user mailboxes are migrated to Exchange Online. You need to migrate the public folders from the on-premises organization to Exchange Online. Which three actions should you perform in sequence before you create the migration batch? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft Exchange Online tenant that contains 1,000 users. A user named User1 receives a non-delivery report (NDR) when attempting to send an email message to an internal group named sales@contoso.com . The NDR contains the following text: `5.7.1 Delivery not authorized.` You need to ensure that User1 can send email to sales@contoso.com successfully. Solution: You instruct User1 to reduce the size of the email message.
A. Yes
B. No
You have a Microsoft Exchange Server 2019 organization. You run the following commands.You have a user named Admin1. You need to ensure that Admin1 can manage the mailboxes of users in the Executives organizational unit (OU) only. What should you do?
A. Modify the membership of VIP Admins.
B. Add Admin1 to the Recipient Management management role group.
C. Move Admin1 to the Executives OU.
D. Create a custom role group.
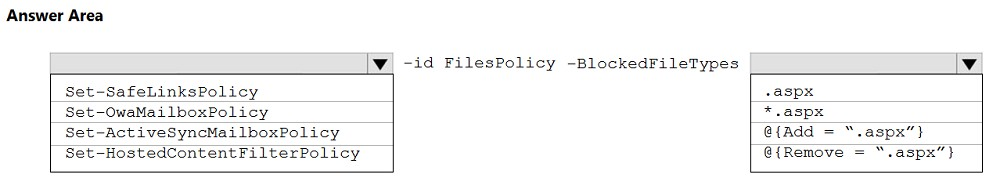
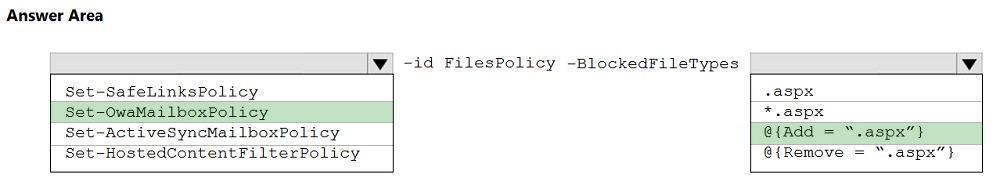
HOTSPOT - You need to modify FilesPolicy to prevent users from downloading ASPX files. The solution must meet the technical requirements. How should you complete the command? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft Exchange Online tenant. You need to ensure that an email notification is sent to a security team every time an email forwarding rule is created in the tenant. What should you create in the Microsoft Purview compliance portal?
A. a threat policy
B. a communication compliance policy
C. an alert policy
D. a data loss prevention (DLP) policy
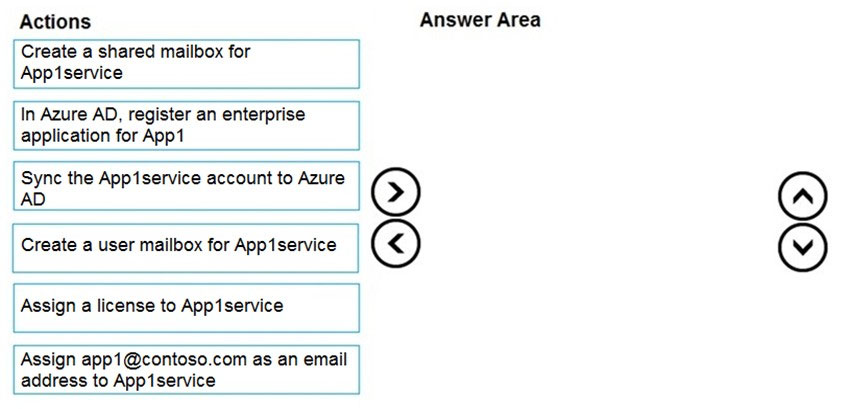
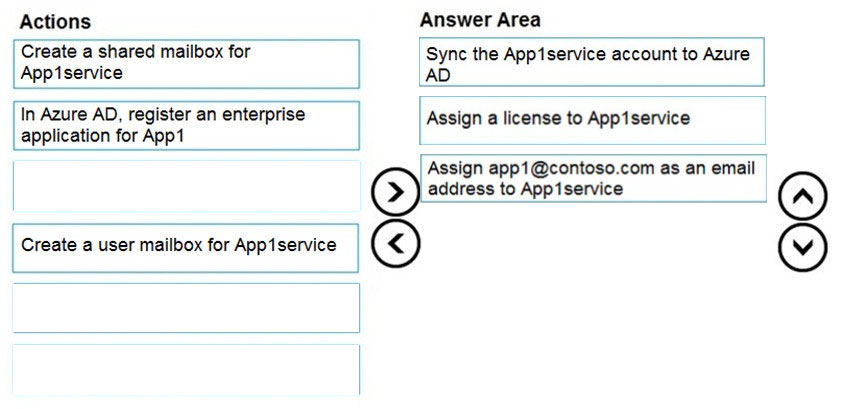
DRAG DROP - Your network contains an Active Directory domain and an Azure Active Directory (Azure AD) tenant in a hybrid deployment. You implement a Microsoft Exchange Online tenant. You plan to deploy a new on-premises app named App1 to a Windows server. The solution must meet the following requirements: ✑ Use an Active Directory user account named App1service as a service account. ✑ Be able to receive email requests by using an email address of app1@contoso.com . ✑ Use App1service to sign in to the mailbox of App1 to view the requests. In the domain, you create App1service. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
You have a hybrid deployment that contains a Microsoft Exchange Online tenant and an on-premises Exchange Server 2019 server named Server1. Server1 uses a certificate from a third-party certification authority (CA). The certificate is enabled for the SMTP service. You replace the certificate with a new certificate. You discover that delivery fails for all email messages sent from Server1 to your Microsoft 365 tenant. You receive the following error message for all the queued email messages: “450 4.4.101 Proxy session setup failed on Frontend with 451 4.4.0 Primary target IP address responded with 451 5.7.3 STARTTLS is required to send mail.” You need to ensure that the messages are delivered successfully from Server1 to the Microsoft 365 tenant. What should you do?
A. From the Exchange admin center, update the certificate thumbprint in the properties of a connector.
B. From Server1, regenerate the certificate and select Make private keys exportable.
C. From Server1, run the iisreset command.
D. From Server1, request a new certificate that support TLS.
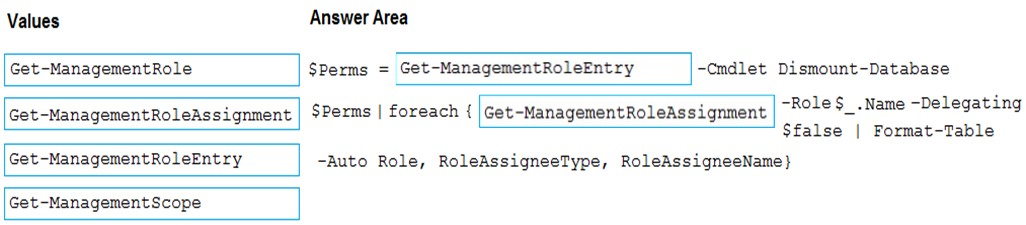
DRAG DROP - You have a Microsoft Exchange Server 2019 organization. You need to identify which accounts in Active Directory are assigned permissions to dismount mailbox databases. How should you complete the command? To answer, drag the appropriate values to the correct targets. Each value may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place:
HOTSPOT - You have a Microsoft Exchange Online tenant. You suspect that an administrator accessed the mailbox of a user named User1. You need to run a PowerShell command to identify which administrator signed in to the mailbox of User1. How should you complete the command? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You need to recommend a solution that meets the security requirements for protecting users. What should you recommend?
A. From the Security & Compliance admin center, create an ATP safe attachments policy.
B. From the Security & Compliance admin center, create an ATP Safe Links policy.
C. From the Security & Compliance admin center, create an ATP anti-phishing policy.
D. From the Exchange admin center in Exchange Online, create a spam filter policy.
You have a Microsoft 365 subscription for a company named Fabrikam, Inc. The company uses an Exchange Online tenant that has an email domain named fabrikam.com. Fabrikam works with a partner company named Contoso, Ltd. that uses an email domain named contoso.com. A new security policy at Contoso states that any email sent from partners to Contoso employees must use TLS encryption. You need to ensure that email sent from Fabrikam to Contoso uses TLS. What should you create in the tenant?
A. a new connector that specifies the contoso.com SMTP domain
B. a new connector that specifies the fabrikam.com SMTP domain
C. a remote domain named fabrikam.com
D. a remote domain named contoso.com
You need to generate a report for the mobile devices that meets the technical requirements. Which PowerShell cmdlet should you use?
A. Get-DevicePolicy
B. Get-MobileDevice
C. Get-MobileDeviceStatistics
D. Get-DeviceTenantPolicy
You have a hybrid deployment between a Microsoft Exchange Online tenant and an on-premises Exchange Server 2019 organization. The on-premises organization contains several Exchange Server 2019 servers. You discover that delivery fails for all email messages sent from the on-premises organization to Microsoft 365. You discover that the certificate for an on-premises Exchange server expired. You need to resolve the issue as quickly possible. The solution must minimize administrative effort. What should you do on the on-premises Exchange server?
A. Create a new self-signed certificate.
B. Generate a certificate renewal request.
C. Generate a certificate request.
D. Add the certificate for a new root certification authority (CA).
You have a Microsoft Exchange Online tenant. You need to identify any changes made to the Recipient Management role group during the past month. What should you do?
A. Run the Get-ManagementRole cmdlet.
B. Run a non-owner mailbox access report.
C. Run an administrator role group report.
D. Run the Get-AuditLogSearch cmdlet.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft Exchange Online tenant that contains the following email domains: ✑ Adatum.com ✑ Contoso.com ✑ Fabrikam.com When external recipients receive email messages from the users in the tenant, all the messages are delivered by using the @contoso.com email domain. You need to ensure that the users send email by using the @fabrikam.com email domain. Solution: From the Microsoft 365 portal, you set fabrikam.com as the default domain. Does this meet the goal?
A. No
B. Yes
HOTSPOT - You are configuring a hybrid deployment between a Microsoft Exchange Online tenant and an on-premises Exchange Server 2019 organization. The Exchange Server organization contains two servers named Server1 and Server2. You have a proxy server named Proxy1 that is accessible by using http://proxy1:8080. You install the Microsoft Hybrid Agent on Server1 and Server2. You need to ensure that the Hybrid Agent uses only Proxy1 to connect to Microsoft Online Services. How should you complete the PowerShell command? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
DRAG DROP - You have a Microsoft 365 E5 subscription that contains a public folder named Folder1 and two users named User1 and User2. You need to ensure that the users can perform the actions shown in the following table.The solution must use the principle of least privilege and minimize administrative effort. Which folder permission should you grant to each user? To answer, drag the appropriate permissions to the correct users. Each permission may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
You have a Microsoft Exchange Server 2019 organization. You need to provide a user named User1 with the ability to create and manage transport rules. To which management role group should you add User1?
A. Server Management
B. Compliance Management
C. Records Management
D. Hygiene Management
You have a Microsoft Exchange Online tenant that uses a third-party email hygiene system named Service1. Service1 blocks all encrypted email. All external email is routed through Service1 by using a connector. Users classify email by using sensitivity labels. Emails classified as Secret are encrypted automatically. You need to ensure that the users can send emails classified as Secret to external recipients. Which two items should you create? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. a remote domain
B. a connector
C. a data loss prevention (DLP) policy
D. a mail flow rule
E. a label policy
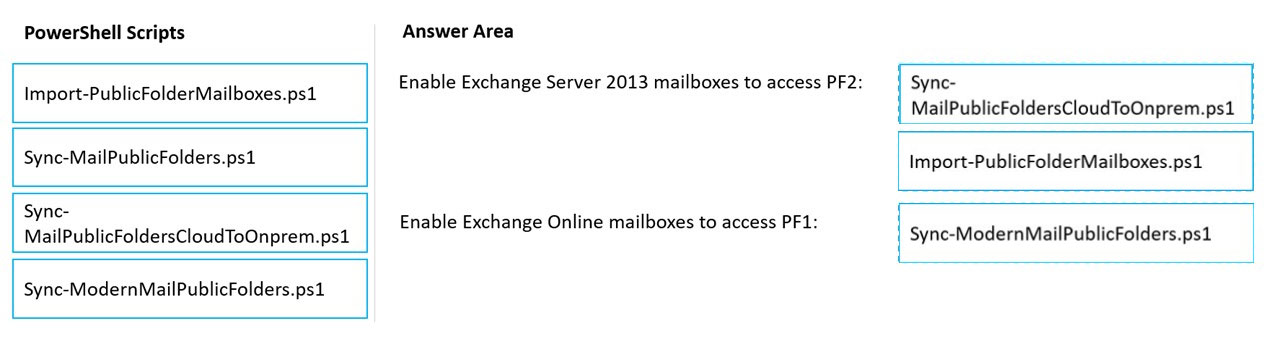
DRAG DROP - You have a hybrid deployment between a Microsoft Exchange Online tenant and an on-premises Exchange Server 2013 organization. The deployment contains the public folders shown in following table.You need to configure the deployment to meet the following requirements: ✑ Exchange Server 2013 mailboxes must be able to access PF2. ✑ Exchange Online mailboxes must be able to access PF1. Which PowerShell script should you run from an Exchange Server 2013 server to meet each requirement? To answer, drag the appropriate scripts to the correct requirements. Each script may be used once, more than once, or at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place:
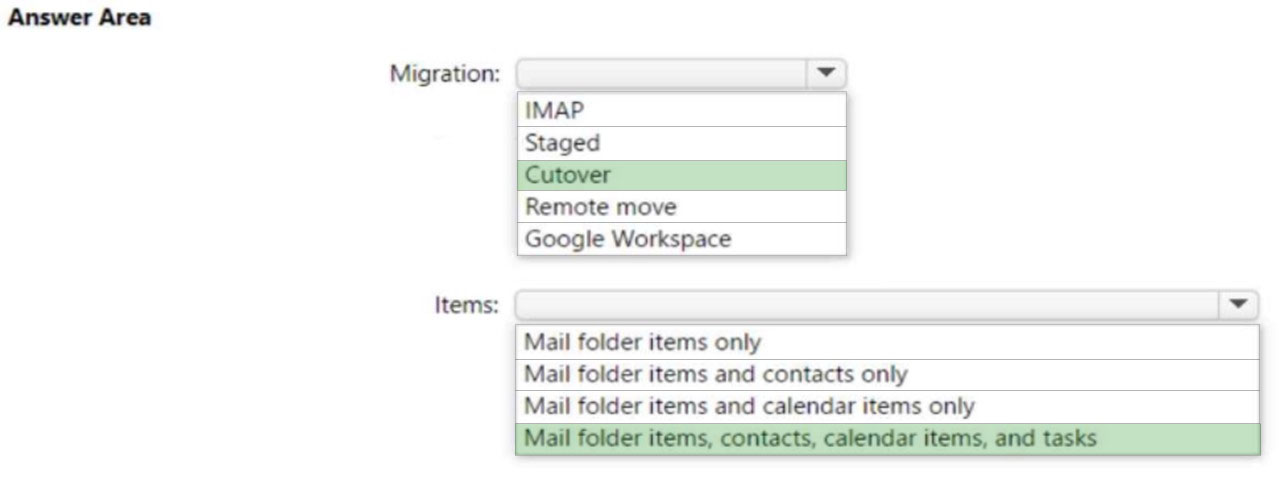
HOTSPOT - You need to migrate 10 Microsoft Outlook.com users to the adatum.com tenant. Which type of migration should you perform, and which items can be migrated? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
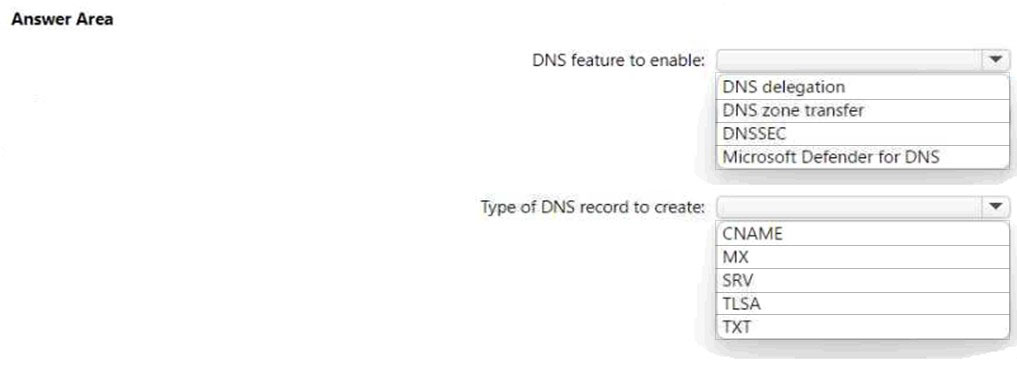
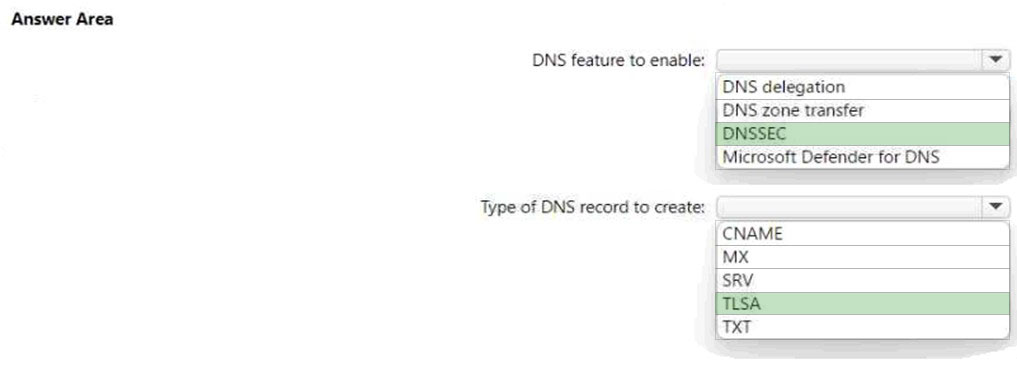
HOTSPOT - You have a Microsoft Exchange Online tenant. You need to use the DANE protocol to protect against mail server spoofing. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
SIMULATION - Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time. When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design. Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task. Labs are not timed separately, and this exam may have more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided. Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.Use the following login credentials as needed: To enter your username, place your cursor in the Sign in box and click on the username below. To enter your password, place your cursor in the Enter password box and click on the password below. Microsoft 365 Username: admin@abc.com Microsoft 365 Password: xxxxxx - If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab. The following information is for technical support purposes only. Lab Instance: XXXXXX - You need to prevent email messages that contain attachments that have the .js file extension from being delivered to any recipients in your organization. To complete this task, sign in to the Microsoft 365 admin center.
You have a Microsoft Exchange Online tenant that has an email domain named contoso.com. You collaborate with a partner company that has an email domain named adatum.com. You need to ensure that all the email messages sent to and received from adatum.com are encrypted in transit. Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct answer is worth one point.
A. Create a connector from adatum.com to Microsoft Office 365 and configure the connector to use SMTP relay.
B. Create a connector from adatum.com to Microsoft Office 365 and configure the connector to require TLS.
C. Create a connector from Microsoft Office 365 to adatum.com and configure the connector to require TLS.
D. Issue S/MIME certificates to all the users in contoso.com.
E. Configure Exchange Online to use direct send to adatum.com.
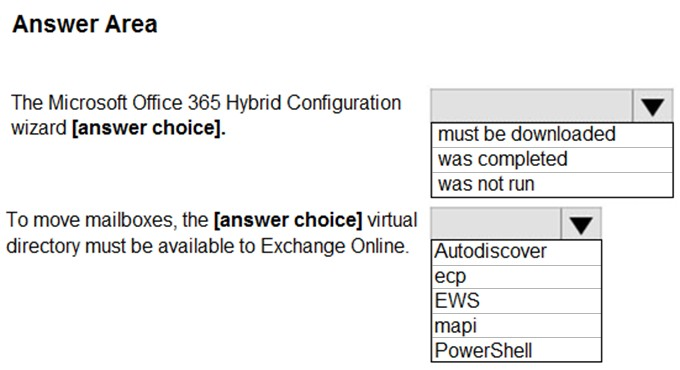
HOTSPOT - You have a Microsoft Exchange Server 2019 organization and a Microsoft 365 E5 subscription. From the Microsoft 365 admin center, you open Data migration as shown in the following exhibit.Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 subscription that contains a verified domain named contoso.com. You have an app named App1 that sends meeting invitations on behalf of users. The invitations are sent from a Microsoft Exchange Online mailbox that has a sender address of app1@contoso.com and a reply-to address of the user scheduling the meeting. You create an anti-phishing policy named Policy1 that includes all the users in contoso.com. Policy1 is configured to protect the domain against impersonation. You discover that email messages sent from App1 are quarantined. You need to ensure that App1 can send messages that impersonate any contoso.com user. How should you modify Policy1?
A. Add app1@contoso.com as a trusted sender.
B. Enable spoof intelligence.
C. Add app1@contoso.com as an excluded user.
D. Enable mailbox intelligence.
HOTSPOT - You have a Microsoft Exchange Online tenant. You need to be notified when more than 1,000 email messages are queued in Exchange for more than one hour. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Your company has the offices and subnets shown in the following table.Each office has an IT department. You have a Microsoft Exchange Online tenant. You need to ensure that only users in the IT department who sign in from the London office can access the Exchange admin center. What should you use?
A. a Conditional Access policy
B. named locations
C. a client access rule
D. a custom role group
Access Full MS-203 Dump Free
Looking for even more practice questions? Click here to access the complete MS-203 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our MS-203 dump free questions — and get one step closer to exam success!