MS-101 Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the MS-101 certification exam? Kickstart your success with our MS-101 Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with MS-101 practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free MS-101 practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
You have a Microsoft 365 E5 subscription. You need to identify which users accessed Microsoft Office 365 from anonymous IP addresses during the last seven days. What should you do?
A. From the Defender for Cloud Apps admin center, select Users and accounts.
B. From the Microsoft 365 Defender, view the Threat tracker.
C. From the Microsoft 365 admin center, view the Security & compliance report.
D. From the Azure Active Directory admin center, view the Risky sign-ins report.
You enable the Azure AD Identity Protection weekly digest email. You create the users shown in the following table.Which users will receive the weekly digest email automatically?
A. Admin2, Admin3, and Admin4 only
B. Admin1, Admin2, Admin3, and Admin4
C. Admin2 and Admin3 only
D. Admin3 only
E. Admin1 and Admin3 only
You have a new Microsoft 365 E5 subscription. You plan to use Activity explorer to monitor data loss prevention (DLP) rule activity. You need to ensure that Activity explorer contains data for analysis. What should you do first?
A. Add a new alert policy.
B. Turn on auditing.
C. Create a sensitivity label.
D. Create a new content search.
You have a Microsoft 365 subscription. All users have their email stored in Microsoft Exchange Online. In the mailbox of a user named User1, you need to preserve a copy of all the email messages that contain the word ProjectX. What should you do?
A. From the Security & Compliance admin center, create a label and a label policy.
B. From the Exchange admin center, create a mail flow rule.
C. From the Security & Compliance admin center, start a message trace.
D. From Exchange admin center, start a mail flow message trace.
You need to create the DLP policy to meet the technical requirements. What should you configure first?
A. sensitive info types
B. the Insider risk management settings
C. the event types
D. the sensitivity labels
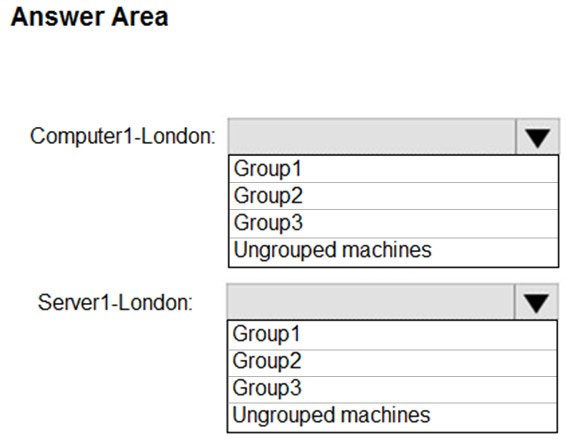
HOTSPOT - You use Microsoft Defender for Endpoint. You have the Microsoft Defender for Endpoint machine groups shown in the following table.You plan to onboard computers to Microsoft Defender for Endpoint as shown in the following table.
To which machine group will each computer be added? To answer, select the appropriate options in the answer are. NOTE: Each correct selection is worth one point. Hot Area:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your network contains an Active Directory domain named contoso.com that is synced to Microsoft Azure Active Directory (Azure AD). You manage Windows 10 devices by using Microsoft System Center Configuration Manager (Current Branch). You configure pilot co-management. You add a new device named Device1 to the domain. You install the Configuration Manager client on Device1. You need to ensure that you can manage Device1 by using Microsoft Intune and Configuration Manager. Solution: You add Device1 to a Configuration Manager device collection. Does this meet the goal?
A. Yes
B. No
You have a Microsoft 365 E5 tenant. You need to evaluate compliance with European Union privacy regulations for customer data. What should you do in the Microsoft 365 compliance center?
A. Create a Data Subject Request (DSR)
B. Create a data loss prevention (DLP) policy for General Data Protection Regulation (GDPR) data
C. Create an assessment based on the EU GDPR assessment template
D. Create an assessment based on the Data Protection Baseline assessment template
You need to notify the manager of the human resources department when a user in the department shares a file or folder from the department's Microsoft SharePoint Online site. What should you do?
A. From the Security & Compliance admin center, create an alert policy.
B. From the SharePoint Online site, create an alert.
C. From the SharePoint Online admin center, modify the sharing settings.
D. From the Security & Compliance admin center, create a data loss prevention (DLP) policy.
Your company has offices in five cities. The company has a Microsoft 365 tenant. Each office is managed by a local administrator. You plan to deploy Microsoft Intune. You need to recommend a solution to manage resources in Intune that meets the following requirements: ✑ Local administrators must be able to manage only the resources in their respective office. ✑ Local administrators must be prevented from managing resources in other offices. ✑ Administrative effort must be minimized. What should you include in the recommendation?
A. scope tags
B. device categories
C. configuration profiles
D. conditional access policies
Your company uses on-premises Windows Server File Classification Infrastructure (FCI). Some documents on the on-premises file servers are classified as Confidential. You migrate the files from the on-premises file servers to Microsoft SharePoint Online. You need to ensure that you can implement data loss prevention (DLP) policies for the uploaded files based on the Confidential classification. What should you do first?
A. From the SharePoint admin center, configure hybrid search.
B. From the SharePoint admin center, create a managed property.
C. From the Security & Compliance Center PowerShell, run the New-DataClassification cmdlet.
D. From the Security & Compliance Center PowerShell, run the New-DlpComplianceRule cmdlet.
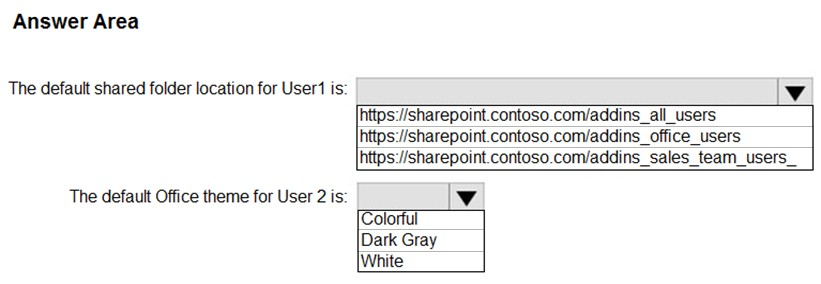
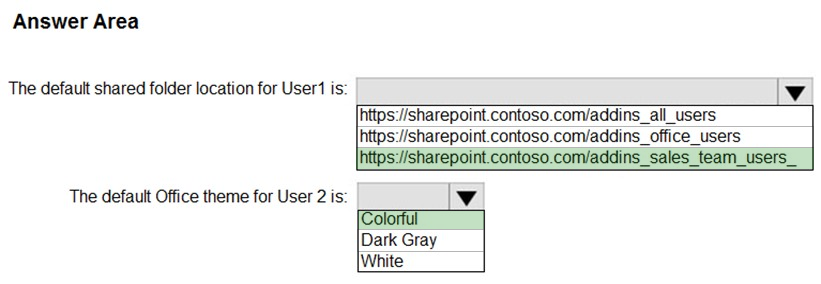
HOTSPOT - You have a Microsoft 365 subscription that contains three groups named All users, Sales team, and Office users, and two users shown in the following table.In Microsoft Endpoint Manager, you have the Policies for Office apps settings shown in the following exhibit.
The policies use the settings shown in the following table.
What is the default share folder location for User1 and the default Office theme for User2? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 subscription. From the Microsoft 365 Defender, you create a role group named US eDiscovery Managers by copying the eDiscovery Manager role group. You need to ensure that the users in the new role group can only perform content searches of mailbox content for users in the United States. Solution: From Windows PowerShell, you run the New-ComplianceSecurityFilter cmdlet with the appropriate parameters. Does this meet the goal?
A. Yes
B. No
From the Microsoft 365 compliance center, you create a content export as shown in the exhibit. (Click the Exhibit tab.)What will be excluded from the export?
A. a 75-MB PDF file
B. a 5-KB RTF file
C. an 80-MB PPTX file
D. a 12-MB BMP file
You need to ensure that User1 can enroll the devices to meet the technical requirements. What should you do?
A. From the Azure Active Directory admin center, assign User1 the Cloud device administrator role.
B. From the Azure Active Directory admin center, configure the Maximum number of devices per user setting.
C. From the Endpoint Manager admin center, add User1 as a device enrollment manager.
D. From the Endpoint Manager admin center, configure the Enrollment restrictions.
You have a Microsoft 365 subscription. All users have their email stored in Microsoft Exchange Online. In the mailbox of a user named User1, you need to preserve a copy of all the email messages that contain the word ProjectX. What should you do first?
A. From the Microsoft Purview compliance portal, create a label and a label policy.
B. From the Exchange admin center, create a mail flow rule.
C. From the Microsoft Purview compliance portal, create a data loss prevention (DLP) policy.
D. From Microsoft Defender for Cloud Apps, create an activity policy.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com. You create a Microsoft Defender for Identity instance named Contoso. The tenant contains the users shown in the following table.You need to modify the configuration of the Defender for Identity sensors. Solution: You instruct User1 to modify the Defender for Identity sensor configuration. Does this meet the goal?
A. Yes
B. No
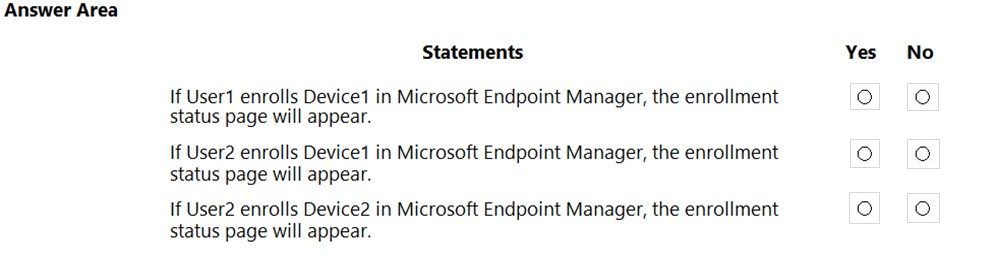
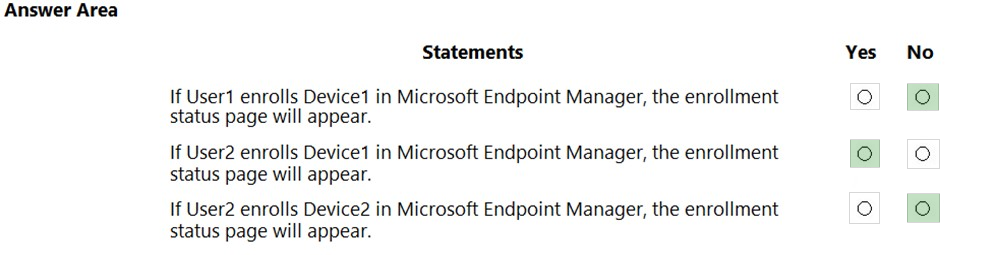
HOTSPOT - You have a Microsoft 365 E5 tenant that contains the users shown in the following table.You purchase the devices shown in the following table.
In Microsoft Endpoint Manager, you create an enrollment status page profile that has the following settings: ✑ Show app and profile configuration progress: Yes ✑ Allow users to collect logs about installation errors: Yes ✑ Only show page to devices provisioned by out-of-box experience (OOBE): No ✑ Assignments: Group2 For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
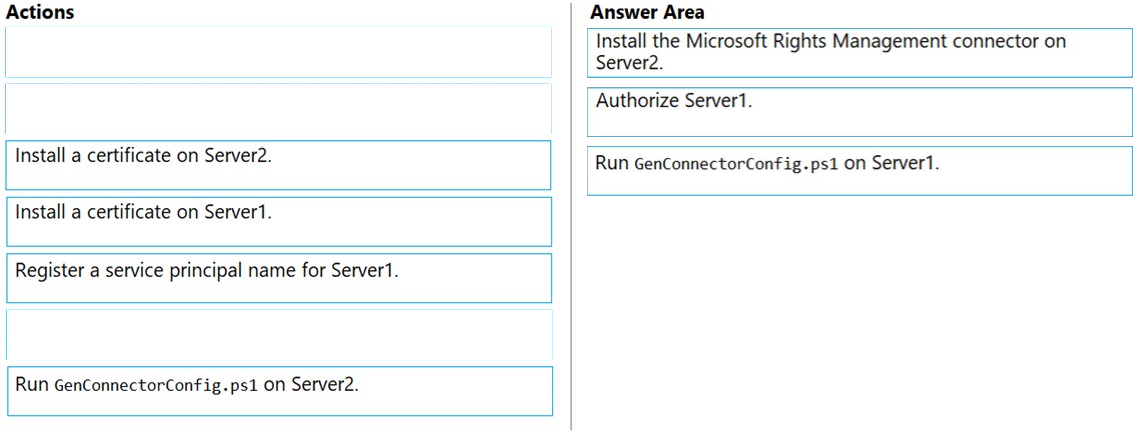
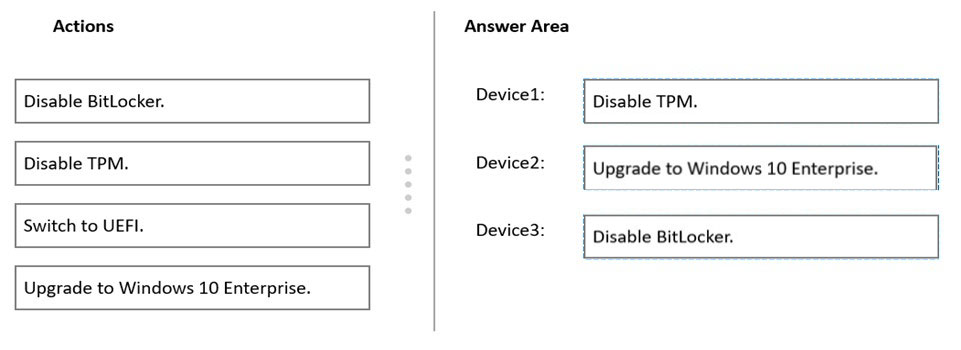
DRAG DROP - Your network contains an on-premises Active Directory domain that syncs to Azure Active Directory (Azure AD). The domain contains the servers shown in the following table.You use Azure Information Protection. You need to ensure that you can apply Azure Information Protection labels to the file stores on Server1. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
You have a Microsoft 365 E5 subscription that contains the devices shown in the following table.You need to implement Windows Information Protection (WIP). The solution must meet the following requirements: • Ensure that users on enrolled devices can override the WIP policy settings. • Prevent users on unenrolled devices from overriding the WIP policy settings. What is the minimum number of app protection policies required?
A. 1
B. 2
C. 3
D. 4
DRAG DROP - You have a Microsoft 365 E5 subscription and an on-premises server named Server1. You plan to configure automatic log upload for continuous reports in Microsoft Defender for Cloud Apps. You download a Docker log collector image to Server1. You need integrate Defender for Cloud Apps with the log collector. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
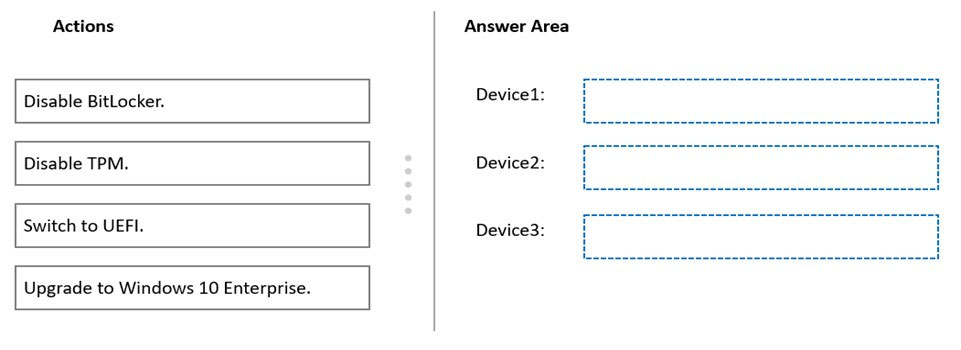
DRAG DROP - You have a Microsoft 365 subscription. You have the devices shown in the following table.You plan to join the devices to Azure Active Directory (Azure AD). What should you do on each device to support Azure AD join? To answer, drag the appropriate actions to the correct devices. Each action may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place:
You have a Microsoft 365 E5 tenant. Users store data in the following locations: Microsoft Teams -✑ Microsoft OneDrive ✑ Microsoft Exchange Online ✑ Microsoft SharePoint Online You need to retain Microsoft 365 data for two years. What is the minimum number of retention policies that you should create?
A. 1
B. 2
C. 3
D. 4
You have a Microsoft 365 E5 subscription that contains the groups shown in the following table.You create a Policies for Office apps configuration named Policy1. You need to deploy Policy1. To which groups can you deploy the configuration?
A. Group3 only
B. Group4 only
C. Group1 and Group2 only
D. Group1 and Group4 only
E. Group1, Group2, Group3, and Group4
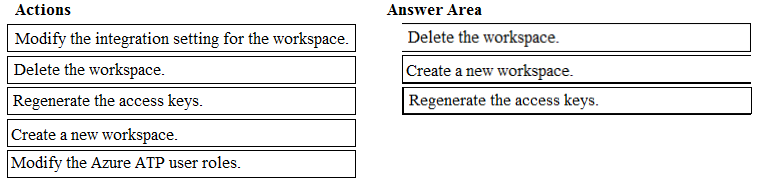
DRAG DROP - You have the Microsoft Azure Advanced Threat Protection (ATP) workspace shown in the Workspace exhibit. (Click the Workspace tab.)The sensors settings for the workspace are configured as shown in the Sensors exhibit. (Click the Sensors tab.)
You need to ensure that Azure ATP stores data in Asia. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
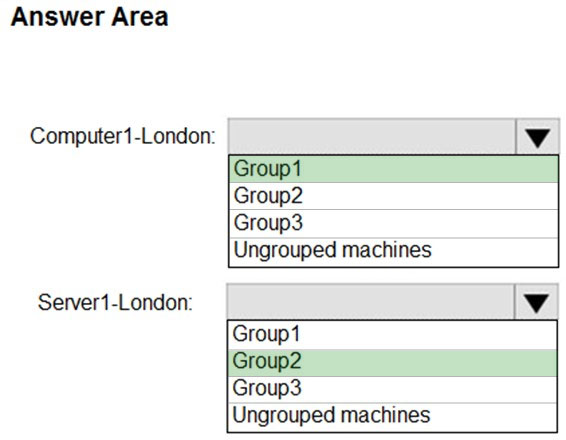
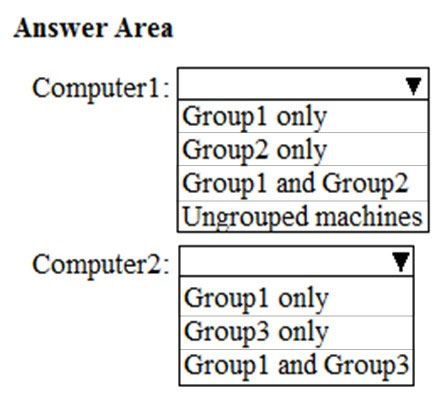
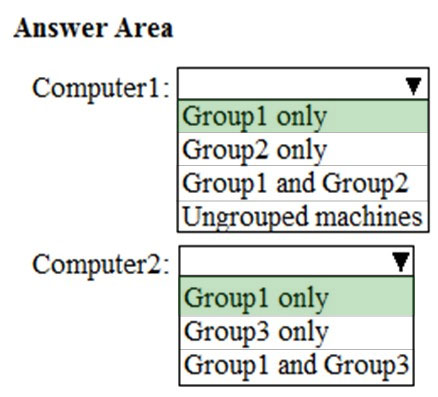
HOTSPOT - Your company uses Microsoft Defender Advanced Threat Protection (ATP). Microsoft Defender ATP contains the device groups shown in the following table.You onboard computers to Microsoft Defender ATP as shown in the following table.
Of which groups are Computer1 and Computer2 members? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
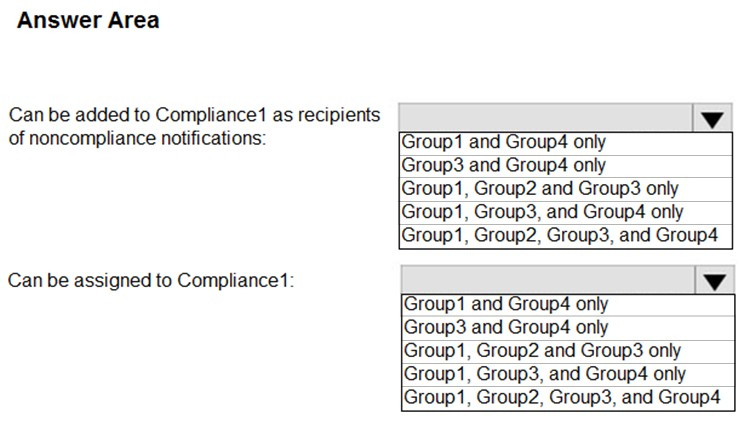
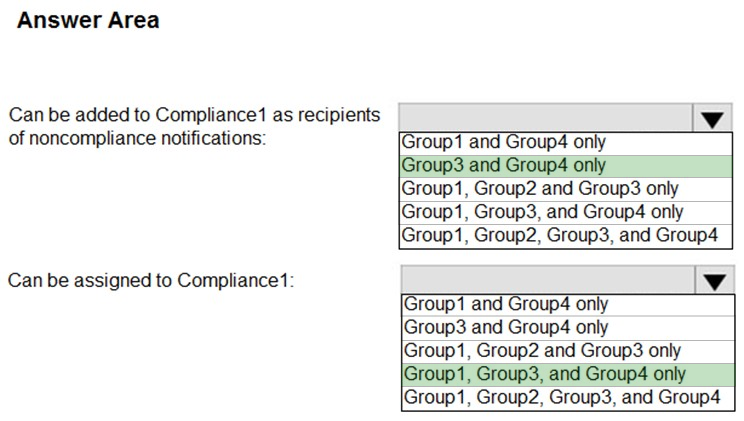
HOTSPOT - You have a Microsoft 365 tenant that contains the groups shown in the following table.You plan to create a compliance policy named Compliance1. You need to identify the groups that meet the following requirements: ✑ Can be added to Compliance1 as recipients of noncompliance notifications ✑ Can be assigned to Compliance1 To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
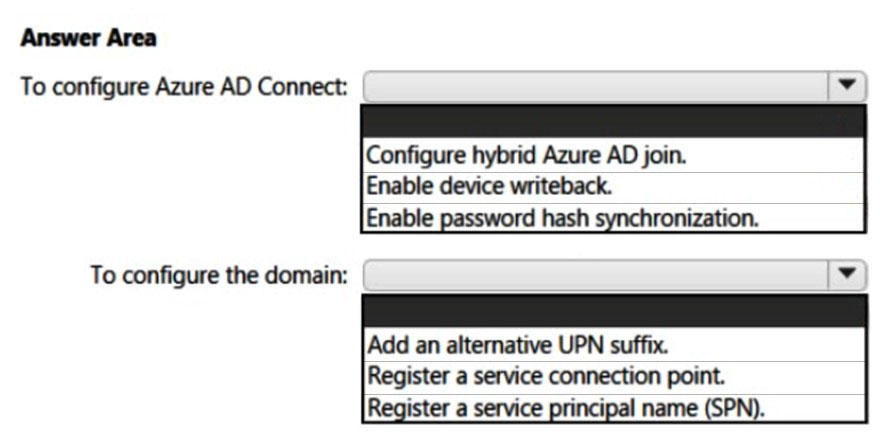
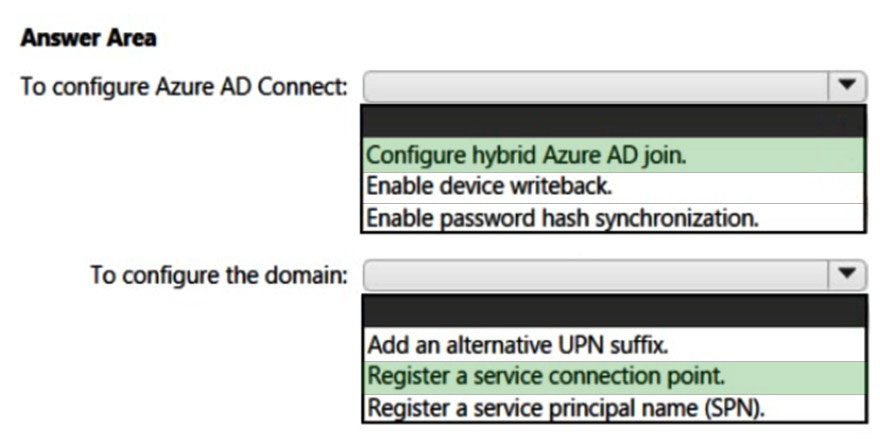
HOTSPOT - Your on-premises network contains an Active Directory domain and a Microsoft Endpoint Configuration Manager site. You have a Microsoft 365 E5 subscription that uses Microsoft Intune. You use Azure AD Connect to sync user objects and group objects to Azure Active Directory (Azure AD). Password hash synchronization is disabled. You plan to implement co-management. You need to configure Azure AD Connect and the domain to support co-management. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You have a Microsoft 365 E5 subscription. You plan to use a mailbox named Mailbox1 to analyze malicious email messages. You need to configure Microsoft Defender for Office 365 to meet the following requirements: • Ensure that incoming email is NOT filtered for Mailbox1. • Detect impersonation and spoofing attacks on all other mailboxes in the subscription. Which two settings should you configure? To answer, select the appropriate settings in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 tenant and a LinkedIn company page. You plan to archive data from the LinkedIn page to Microsoft 365 by using the LinkedIn connector. Where can you store data from the LinkedIn connector?
A. a Microsoft OneDrive for Business folder
B. a Microsoft SharePoint Online document library
C. a Microsoft 365 mailbox
D. Azure Files
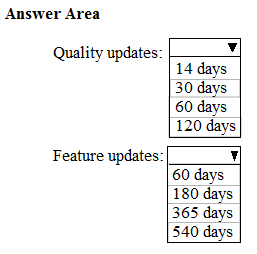
HOTSPOT - Your network contains an Active Directory domain named contoso.com. All client devices run Windows 10 and are joined to the domain. You update the Windows 10 devices by using Windows Update for Business. What is the maximum amount of time you can defer Windows 10 updates? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
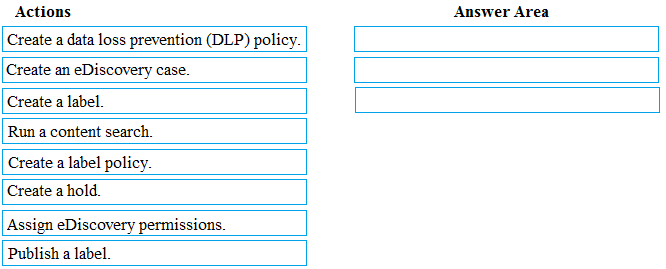
DRAG DROP - You need to meet the requirement for the legal department. Which three actions should you perform in sequence from the Security & Compliance admin center? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
You have a Microsoft 365 subscription. From the Microsoft 365 compliance center, you create a content search of all the mailboxes that contain the word ProjectX. You need to export the results of the content search. What do you need to download the report?
A. a certification authority (CA) certificate
B. an export key
C. a password
D. a user certificate
You have a Microsoft 365 tenant that contains the groups shown in the following table.You plan to create a new Windows 10 Security Baseline profile. To which groups can you assign to the profile?
A. Group3 only
B. Group1 and Group3 only
C. Group2 and Group3 only
D. Group1, Group2, and Group3
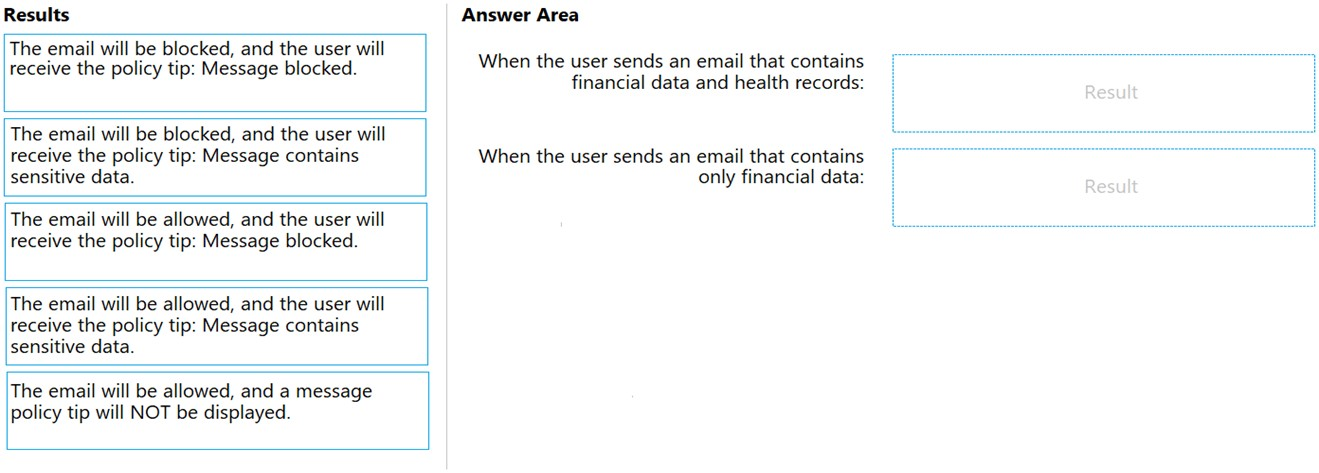
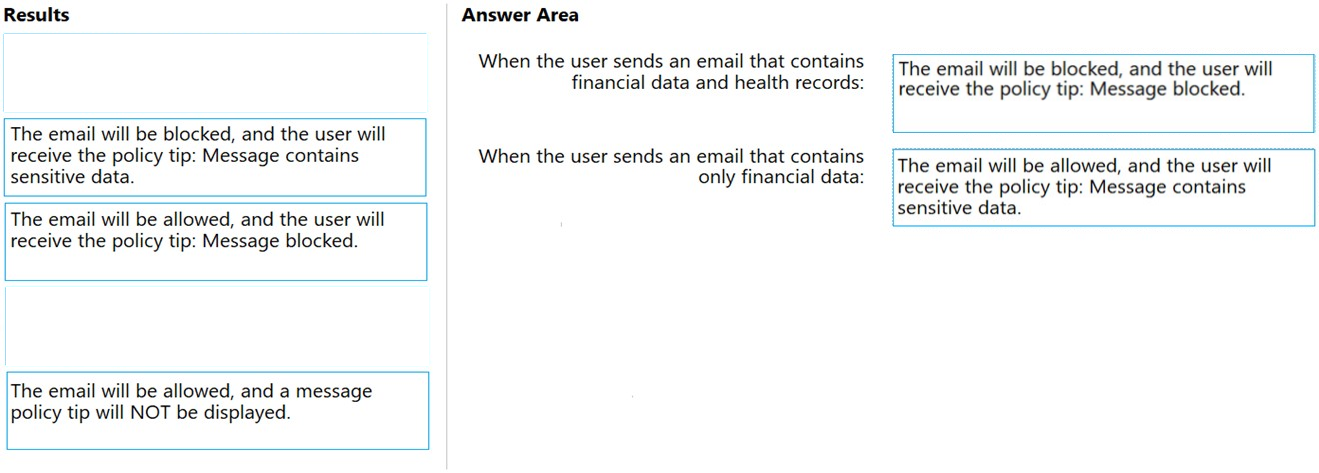
DRAG DROP - You have a Microsoft 365 subscription. In the Exchange admin center, you have a data loss prevention (DLP) policy named Policy1 that has the following configurations: ✑ Block emails that contain financial data. ✑ Display the following policy tip text: Message blocked. From the Microsoft 365 compliance center, you create a DLP policy named Policy2 that has the following configurations: ✑ Use the following location: Exchange email. ✑ Display the following policy tip text: Message contains sensitive data. ✑ When a user sends an email, notify the user if the email contains health records. What is the result of the DLP policies when the user sends an email? To answer, drag the appropriate results to the correct scenarios. Each result may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place:
Your network contains an on-premises Active Directory domain named contoso.com. The domain contains 1,000 Windows 10 devices. You perform a proof of concept (PoC) deployment of Microsoft Defender for Endpoint for 10 test devices. During the onboarding process, you configure Microsoft Defender for Endpoint-related data to be stored in the United States. You plan to onboard all the devices to Microsoft Defender for Endpoint. You need to store the Microsoft Defender for Endpoint data in Europe. What should you do first?
A. Create a workspace.
B. Onboard a new device.
C. Delete the workspace.
D. Offboard the test devices.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a computer that runs Windows 10. You need to verify which version of Windows 10 is installed. Solution: From the Settings app, you select Update & Security to view the update history. Does this meet the goal?
A. Yes
B. No
You have a Microsoft 365 subscription that uses Microsoft Defender for Cloud Apps. You configure a session control policy to block downloads from SharePoint Online sites. Users report that they can still download files from SharePoint Online sites. You need to ensure that file download is blocked while still allowing users to browse SharePoint Online sites. What should you configure?
A. an access policy
B. a data loss prevention (DLP) policy
C. an activity policy
D. a Conditional Access policy
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Cloud Apps. You need to be notified when a single user downloads more than 50 files during any 60-second period. What should you configure?
A. a file policy
B. an anomaly detection policy
C. a session policy
D. an activity policy
You have a Microsoft 365 E5 tenant. You plan to create a custom Compliance Manager assessment template based on the ISO 27001:2013 template. You need to export the existing template. Which file format should you use for the exported template?
A. CSV
B. XLSX
C. JSON
D. XML
You have a Microsoft 365 tenant. You plan to enable BitLocker Disk Encryption (BitLocker) automatically for all Windows 10 devices that enroll in Microsoft Intune. What should you use?
A. an attack surface reduction (ASR) policy
B. an app configuration policy
C. a device compliance policy
D. a device configuration profile
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Azure Active Directory (Azure AD) tenant that contains a user named User1. Your company purchases a Microsoft 365 subscription. You need to ensure that User1 is assigned the required role to create file policies and manage alerts in the Defender for Cloud Apps admin center. Solution: From the Azure Active Directory admin center, you assign the Compliance administrator role to User1. Does this meet the goal?
A. Yes
B. No
You have a Microsoft 365 E5 tenant. The Microsoft Secure Score for the tenant is shown in the following exhibit.You plan to enable Security defaults for Azure Active Directory (Azure AD). Which three improvement actions will this affect?
A. Require MFA for administrative roles.
B. Ensure all users can complete multi-factor authentication for secure access
C. Enable policy to block legacy authentication
D. Enable self-service password reset
E. Use limited administrative roles
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 subscription. You discover that some external users accessed content on a Microsoft SharePoint site. You modify the SharePoint sharing policy to prevent sharing outside your organization. You need to be notified if the SharePoint sharing policy is modified in the future. Solution: From the Security & Compliance admin center, you create a threat management policy. Does this meet the goal?
A. Yes
B. No
You have a Microsoft 365 tenant that contains devices registered for mobile device management. The devices are configured as shown in the following table.You plan to enable VPN access for the devices. What is the minimum number of configuration policies required?
A. 1
B. 3
C. 4
D. 5
From the Microsoft 365 compliance center, you create a content export shown in the exhibit. (Click the Exhibit tab.)What will be excluded from the export?
A. a 100-MB VSDX file
B. a 5-MB MP3 file
C. a 10-MB XLSX file
D. a 75-MB PDF file
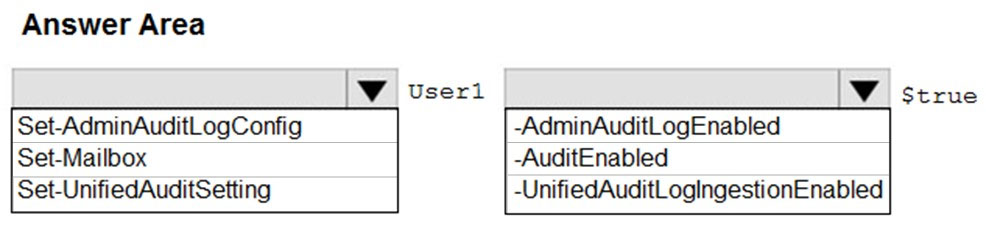
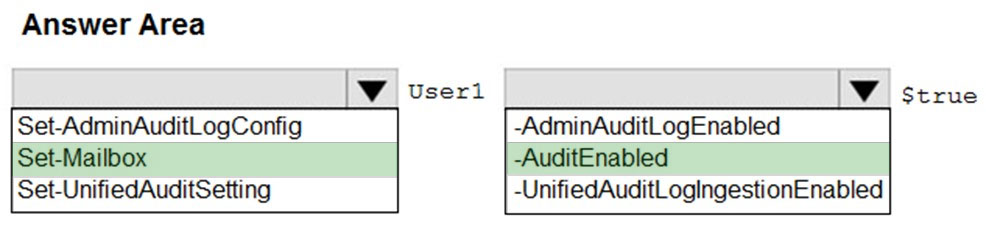
HOTSPOT - You have a new Microsoft 365 subscription. A user named User1 has a mailbox in Microsoft Exchange Online. You need to log any changes to the mailbox folder permissions of User1. Which command should you run? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
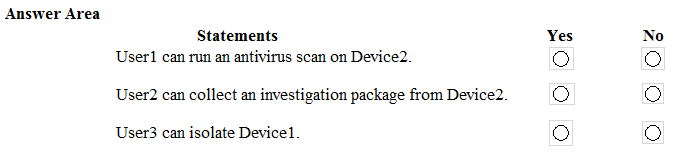
HOTSPOT - You have a Microsoft Azure Activity Directory (Azure AD) tenant that contains the users shown in the following table.Your company uses Microsoft Defender for Endpoint. Microsoft Defender for Endpoint contains the roles shown in the following table.
Microsoft Defender for Endpoint contains the device groups shown in the following table.
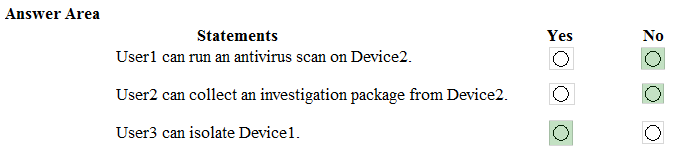
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 subscription. All users have their email stored in Microsoft Exchange Online. In the mailbox of a user named User1, you need to preserve a copy of all the email messages that contain the word ProjectX. What should you do?
A. From Microsoft Defender for Cloud Apps, create an activity policy.
B. From the Security & Compliance admin center, create a data loss prevention (DLP) policy.
C. From the Exchange admin center, start a mail flow message trace.
D. From the Security & Compliance admin center, create an eDiscovery case.
You have a Microsoft 365 E5 tenant that contains four devices enrolled in Microsoft Intune as shown in the following table.You plan to deploy Microsoft 365 Apps for enterprise by using Microsoft Endpoint Manager. To which devices can you deploy Microsoft 365 Apps for enterprise?
A. Device1 only
B. Device1 and Device3 only
C. Device2 and Device4 only
D. Device1, Device2, and Device3 only
E. Device1, Device2, Device3, and Device4
Free Access Full MS-101 Practice Questions Free
Want more hands-on practice? Click here to access the full bank of MS-101 practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your MS-101 certification journey!