MS-101 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your MS-101 certification exam? Start your preparation the smart way with our MS-101 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for MS-101 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our MS-101 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
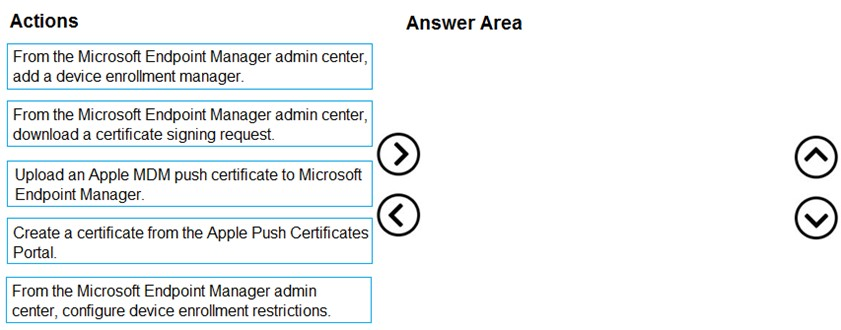
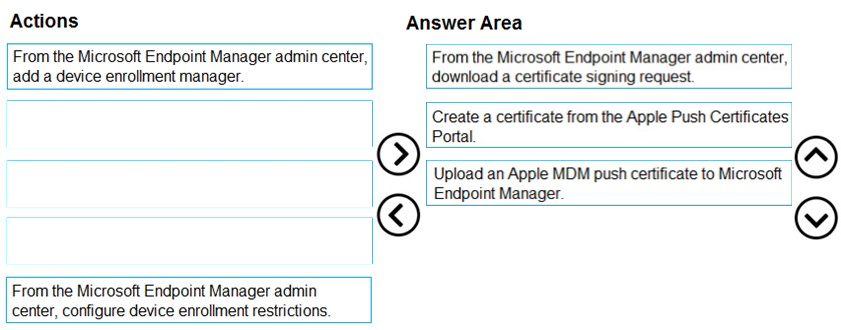
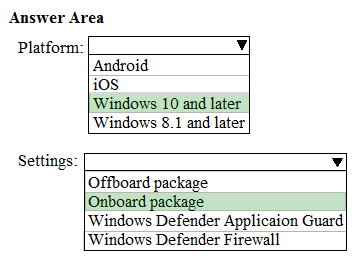
DRAG DROP - You have a Microsoft 365 E5 subscription. Several users have iOS devices. You plan to enroll the iOS devices in Microsoft Endpoint Manager. You need to ensure that you can create an iOS/iPadOS enrollment profile in Microsoft Endpoint Manager. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
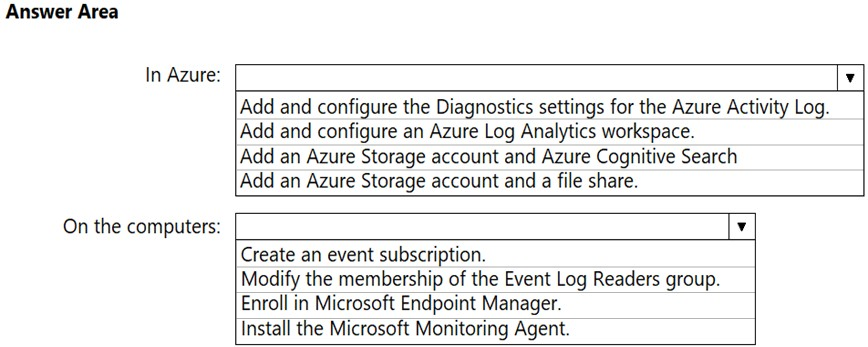
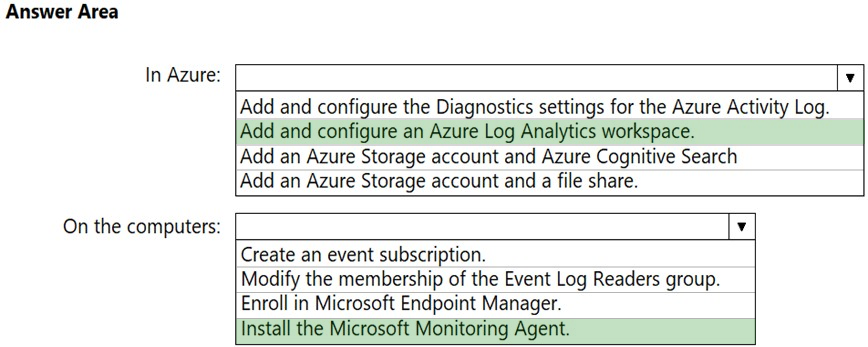
HOTSPOT - You have an Azure subscription and an on-premises Active Directory domain. The domain contains 50 computers that run Windows 10. You need to centrally monitor System log events from the computers. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Azure Active Directory (Azure AD) tenant that contains a user named User1. Your company purchases a Microsoft 365 subscription. You need to ensure that User1 is assigned the required role to create file policies and manage alerts in the Defender for Cloud Apps admin center. Solution: From the Defender for Cloud Apps admin center, you assign the App/instance admin role for all Microsoft Online Services to User1. Does this meet the goal?
A. Yes
B. No
You have a Microsoft 365 E5 subscription and an on-premises server named Server1 that runs Windows Server. You plan to implement Cloud Discovery in Microsoft Defender for Cloud Apps. You need to deploy a log collector to Server1. What should you install on Server1 first?
A. the Azure Monitor agent
B. Docker
C. the Azure Connected Machine agent
D. a Microsoft Defender for Identity sensor
You have a Microsoft 365 tenant. You plan to implement Endpoint Protection device configuration profiles. Which platform can you manage by using the profiles?
A. Ubuntu Linux
B. macOS
C. iOS
D. Android
You have a Microsoft 365 subscription that contains a user named User1. You need to ensure that User1 can search the Microsoft 365 audit logs from the Security & Compliance admin center. Which role should you assign to User1?
A. View-Only Audit Logs in the Security & Compliance admin center
B. View-Only Audit Logs in the Exchange admin center
C. Security reader in the Azure Active Directory admin center
D. Security Reader in the Security & Compliance admin center
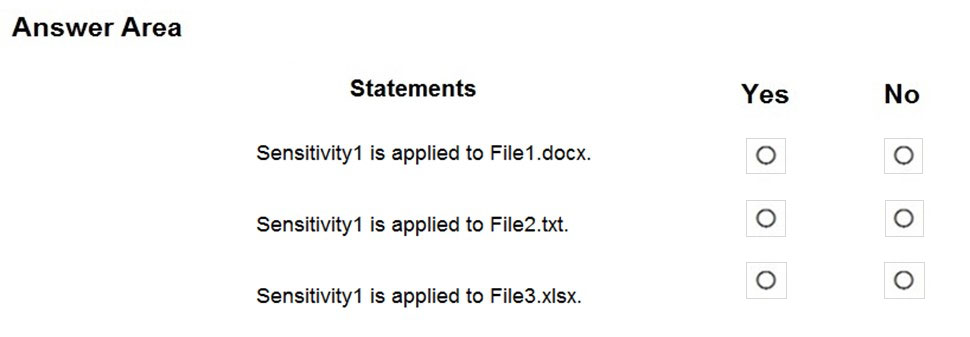
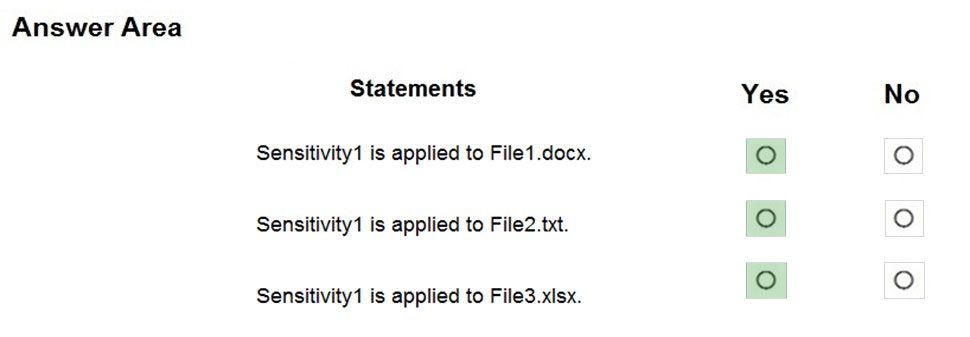
HOTSPOT - You have a Microsoft 365 E5 tenant that contains a Microsoft SharePoint Online site named Site1. Site1 contains the files shown in the following table.You create a sensitivity label named Sensitivity1 and an auto-label policy that has the following configurations: ✑ Name: AutoLabel1 ✑ Label to auto-apply: Sensitivity1 ✑ Rules for SharePoint Online sites: Rule1-SPO ✑ Choose locations where you want to apply the label: Site1 Rule1-SPO is configured as shown in the following exhibit.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
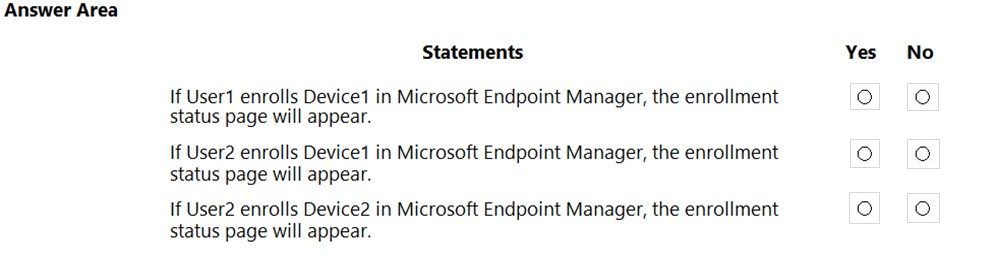
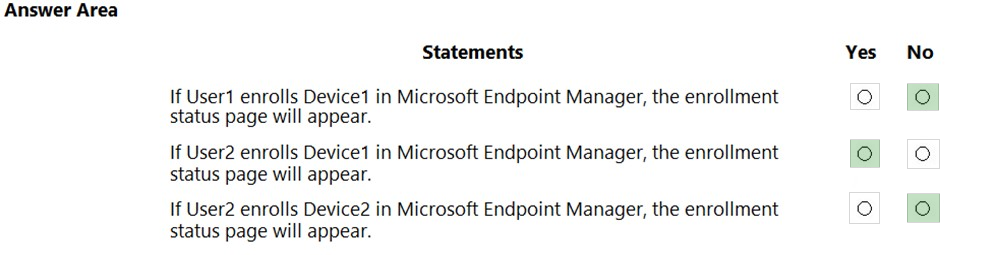
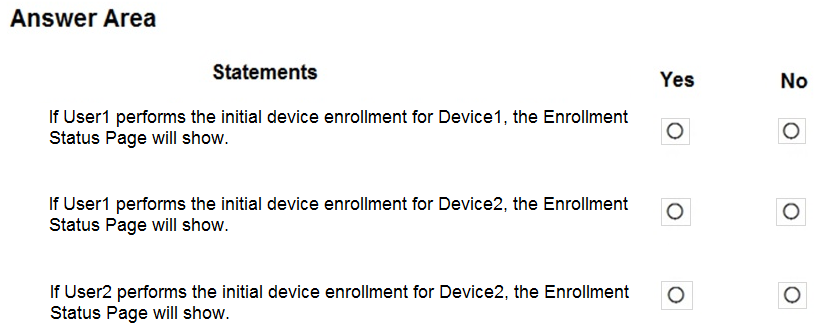
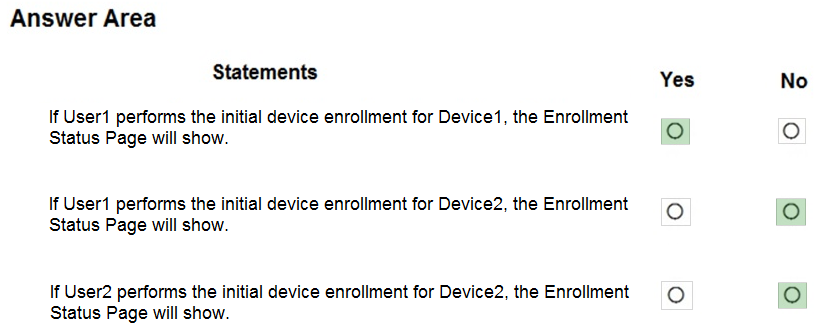
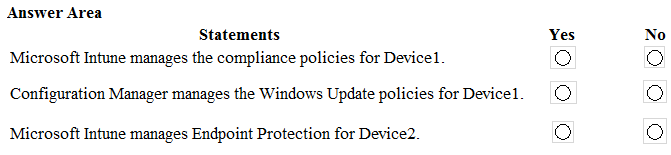
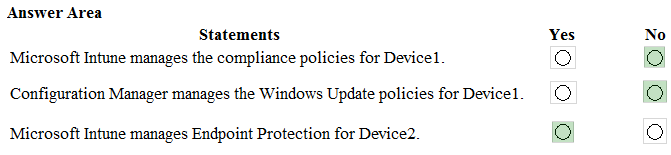
HOTSPOT - You have a Microsoft 365 E5 tenant that contains the users shown in the following table.You purchase the devices shown in the following table.
In Microsoft Endpoint Manager, you create an enrollment status page profile that has the following settings: ✑ Show app and profile configuration progress: Yes ✑ Allow users to collect logs about installation errors: Yes ✑ Only show page to devices provisioned by out-of-box experience (OOBE): No ✑ Assignments: Group2 For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
Your company has a Microsoft 365 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com. A user named User1 is a member of a dynamic group named Group1. User1 reports that he cannot access documents shared to Group1. You discover that User1 is no longer a member of Group1. You suspect that an administrator made a change that caused User1 to be removed from Group1. You need to identify which administrator made the change. Which audit log activity should you search in the Security & Compliance admin center?
A. Azure AD group administration activities ג€” Removed member from group
B. User administration activities ג€” Updated user
C. Azure AD group administration activities ג€” Updated group
HOTSPOT - You have a Microsoft 365 subscription that contains the users shown in the following table.You configure an Enrollment Status Page profile as shown in the following exhibit.
You assign the policy to Group1. You purchase the devices shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You have a Microsoft 365 E5 subscription that contains the users shown in the following table.In Microsoft Endpoint Manager, you have the Policies for Office apps configurations shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
You have a Microsoft 365 E5 subscription. You plan to deploy 100 new Windows 10 devices. You need to identify the appropriate version of Windows 10 for the new devices. The version must meet the following requirements: ✑ Be serviced for a minimum of 24 months. Support Microsoft Application Virtualization (App-V).Which version should you identify?
A. Windows 10 Pro, version 1909
B. Windows 10 Pro, version 2004
C. Windows 10 Enterprise, version 1909
D. Windows 10 Enterprise, version 2004
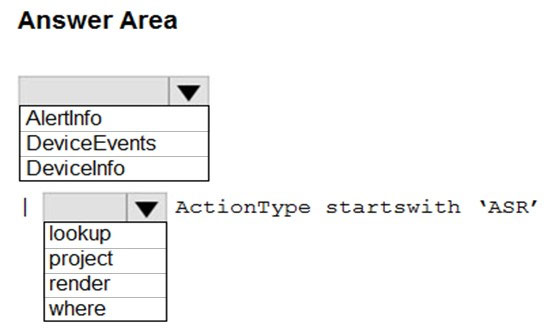
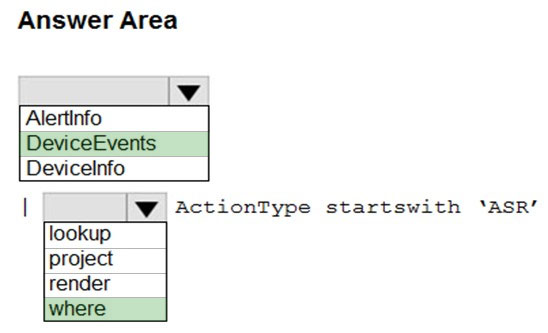
HOTSPOT - You have a Microsoft 365 E5 tenant that contains 100 Windows 10 devices. You plan to attack surface reduction (ASR) rules for the Windows 10 devices. You configure the ASR rules in audit mode and collect audit data in a Log Analytics workspace. You need to find the ASR rules that match the activities on the devices. How should you complete the Kusto query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 E5 subscription. You plan to deploy Microsoft Defender for Cloud Apps. You need to ensure that Microsoft Defender for Cloud Apps can differentiate between internal and external users. What should you do?
A. From the Microsoft 365 admin center, configure the Org settings.
B. From the Microsoft 365 admin center, configure the default domain.
C. From the Microsoft Defender for Cloud Apps portal, add a list of managed domains.
D. From the Microsoft Defender for Cloud Apps portal, configure the Organization details.
You have a Microsoft 365 E5 tenant that contains a user named User1. You plan to implement insider risk management. You need to ensure that User1 can perform the following tasks: ✑ Review alerts. ✑ Manage cases. ✑ Create notice templates. ✑ Review user emails by using Content explorer. The solution must use the principle of least privilege. To which role group should you add User1?
A. Insider Risk Management
B. Insider Risk Management Analysts
C. Insider Risk Management Investigators
D. Insider Risk Management Admin
You purchase a Microsoft 365 subscription. Your company plans to use a third-party security information and event management (SIEM) application. The company does not want to record and retain audit log data in Microsoft 365. You need to turn off Microsoft 365 auditing. What should you use?
A. the Microsoft 365 compliance center
B. Exchange Online PowerShell
C. the Azure Active Directory Module for Windows PowerShell
D. the Microsoft 365 admin center
You need to configure Office on the web to meet the technical requirements. What should you do?
A. Assign the Global reader role to User1.
B. Enable sensitivity labels for Office files in SharePoint Online and OneDrive.
C. Configure an auto-labeling policy to apply the sensitivity labels.
D. Assign the Office apps admin role to User1.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You are deploying Microsoft Endpoint Manager. You successfully enroll Windows 10 devices in Endpoint Manager. When you try to enroll an iOS device in Endpoint Manager, you get an error. You need to ensure that you can enroll the iOS device in Endpoint Manager. Solution: You create an Apple Configurator enrollment profile. Does this meet the goal?
A. Yes
B. No
You have a Microsoft 365 E5 subscription. All users have Mac computers. All the computers are enrolled in Microsoft Endpoint Manager and onboarded to Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP). You need to configure Microsoft Defender ATP on the computers. What should you create from the Endpoint Management admin center?
A. a Microsoft Defender ATP baseline profile
B. a device configuration profile
C. an update policy for iOS
D. a mobile device management (MDM) security baseline profile
You have a Microsoft 365 tenant. You plan to manage incidents in the tenant by using the Microsoft 365 Defender. Which Microsoft service source will appear on the Incidents page of the Microsoft 365 Defender portal?
A. Microsoft Sentinel
B. Azure Web Application Firewall
C. Microsoft Defender for Cloud
D. Microsoft Defender for Identity
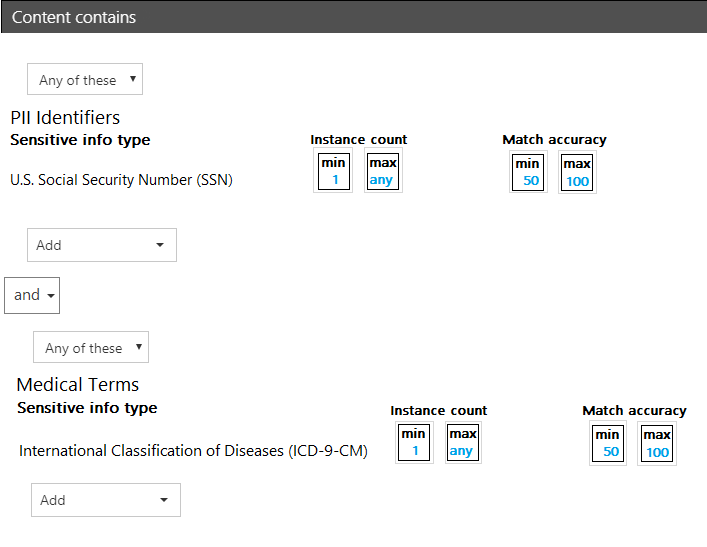
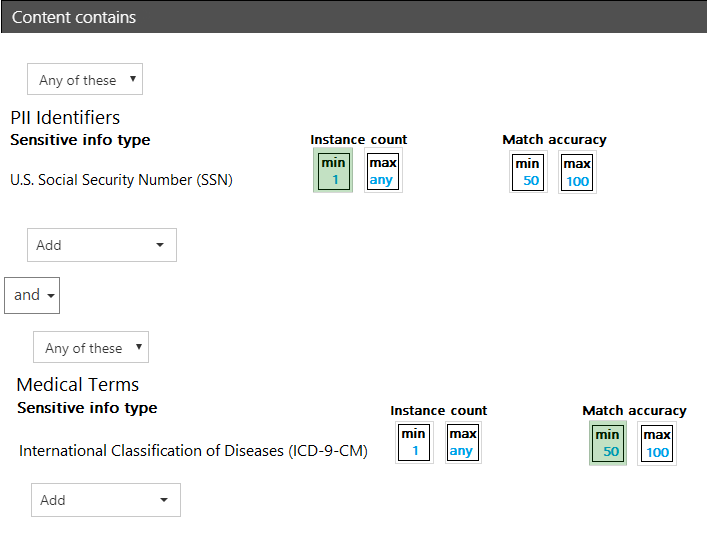
HOTSPOT - You have a data loss prevention (DLP) policy. You need to increase the likelihood that the DLP policy will apply to data that contains medical terms from the International Classification of Diseases (ICD-9-CM). The solution must minimize the number of false positives. Which two settings should you modify? To answer, select the appropriate settings in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com. You create a Microsoft Defender for Identity instance named Contoso. The tenant contains the users shown in the following table.You need to modify the configuration of the Defender for Identity sensors. Solution: You instruct User4 to modify the Defender for Identity sensor configuration. Does this meet the goal?
A. Yes
B. No
HOTSPOT - Your network contains an Active Directory domain named contoso.com. The domain contains the file servers shown in the following table.A file named File1.abc is stored on Server1. A file named File2.abc is stored on Server2. Three apps named App1, App2 and App3 are installed on a Windows 10 device named Device1. All three apps open files that have the .abc file extension. You implement Windows Information Protection (WIP) by creating a policy named Policy1 that has the following configuration: ✑ Exempt apps: App2 ✑ Protected apps: App1 ✑ Windows Information Protection mode: Block ✑ Network boundary: IPv4 range of: 192.168.1.1-192.168.1.255 You ensure that Policy1 applies to Device1. You need to identify the apps from which you can open File1.abc. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
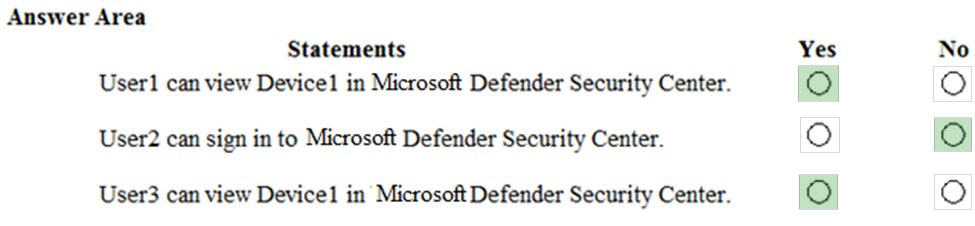
HOTSPOT - You have a Microsoft Azure Activity Directory (Azure AD) tenant contains the users shown in the following table.Group3 is a member of Group1. Your company uses Microsoft Defender Advanced Threat Protection (ATP). Microsoft Defender ATP contains the roles shown in the following table.
Microsoft Defender ATP contains the device groups shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You have a Microsoft 365 subscription. All client devices are managed by Microsoft Endpoint Manager. You need to implement Microsoft Defender Advanced Threat Protection (ATP) for all the supported devices enrolled in mobile device management (MDM). What should you include in the device configuration profile? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 subscription. You need to identify which administrative users performed eDiscovery searches during the past week. What should you do from the Security & Compliance admin center?
A. Perform a content search
B. Create a supervision policy
C. Create an eDiscovery case
D. Perform an audit log search
You have a Microsoft 365 E5 tenant. You need to ensure that when a document containing a credit card number is added to the tenant, the document is encrypted. Which policy should you use?
A. a retention policy
B. a retention label policy
C. an auto-labeling policy
D. an insider risk policy
HOTSPOT - You have retention policies in Microsoft 365 as shown in the following table.Policy1 is configured as shown in the Policy1 exhibit. (Click the Policy1 tab.)
Policy2 is configured as shown in the Policy2 exhibit. (Click the Policy2 tab.)
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 E5 tenant that contains the resources shown in the following table.To which resources can you apply a sensitivity label by using an auto-labeling policy?
A. Mailbox1 and Site1 only
B. Mailbox1, Account1, and Site1 only
C. Account1 and Site1 only
D. Mailbox1, Account1, Site1, and Channel1
E. Account1, Site1, and Channel1 only
You have a Microsoft 365 E5 tenant that has sensitivity label support enabled for Microsoft Teams and SharePoint. You need to enable unified labeling for Microsoft 365 groups. Which cmdlet should you run?
A. Set-UnifiedGroup
B. Set-LabelPolicy
C. Execute-AzureAdLabelSync
D. Add-UnifiedGroupLinks
You have a Microsoft 365 E5 subscription. You define a retention label that has the following settings: ✑ Retention period: 7 years ✑ Start the retention period based on: When items were created You need to prevent the removal of the label once the label is applied to a file. What should you select in the retention label settings?
A. Mark items as a regulatory record
B. Mark items as a record
C. Retain items forever
D. Retain items even if users delete
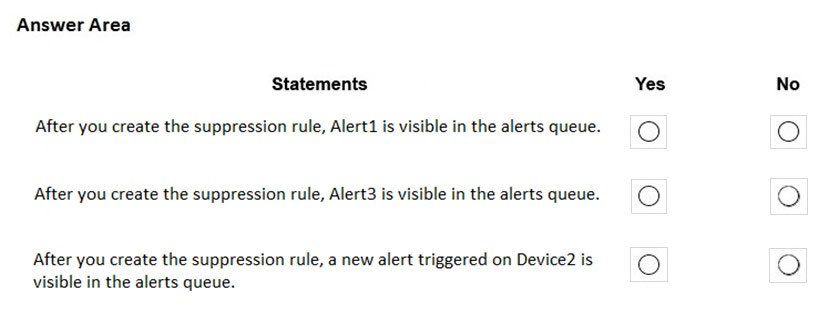
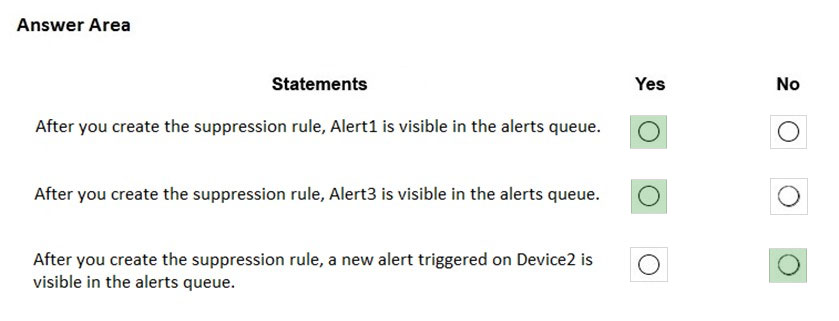
HOTSPOT - Your company uses Microsoft Defender for Endpoint. The devices onboarded to Microsoft Defender for Endpoint are shown in the following table.The alerts visible in the Microsoft Defender for Endpoint alerts queue are shown in the following table.
You create a suppression rule that has the following settings: ✑ Triggering IOC: Any IOC ✑ Action: Hide alert ✑ Suppression scope: Alerts on ATP1 machine group For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
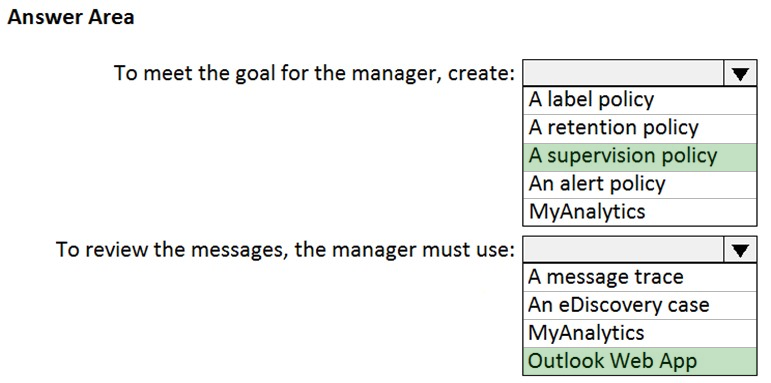
HOTSPOT - You have a Microsoft 365 subscription. You have a group named Support. Users in the Support group frequently send email messages to external users. The manager of the Support group wants to randomly review messages that contain attachments. You need to provide the manager with the ability to review messages that contain attachments sent from the Support group users to external users. The manager must have access to only 10 percent of the messages. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
From the Microsoft 365 compliance center, you create a content export as shown in the exhibit. (Click the Exhibit tab.)What will be excluded from the export?
A. a 10-MB XLSX file
B. a 5-MB MP3 file
C. a 5-KB RTF file
D. an 80-MB PPTX file
Your company has 5,000 Windows 10 devices. All the devices are protected by using Microsoft Defender Advanced Threat Protection (ATP). You need to create a filtered view that displays which Microsoft Defender ATP alert events have a high severity and occurred during the last seven days. What should you use in Microsoft Defender ATP?
A. the threat intelligence API
B. Automated investigations
C. Threat analytics
D. Advanced hunting
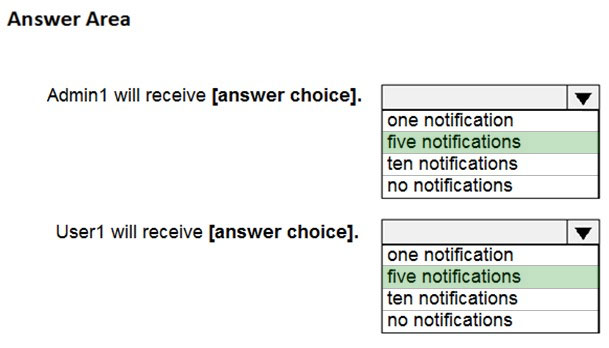
HOTSPOT - You have a Microsoft 365 subscription. You create a Microsoft Defender for Cloud Apps policy named Risk1 based on the Logon from a risky IP address template as shown in the following exhibit.You have two users named User1 and User2. Each user signs in to Microsoft SharePoint Online from a risky IP address 10 times within 24 hours. Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - Your network contains an Active Directory forest named contoso.com that is synced to Microsoft Azure Active Directory (Azure AD). You use Microsoft Endpoint Configuration Manager for device management. You have the Windows 10 devices shown in the following table.You configure Endpoint Configuration Manager co-management as follows: ✑ Automatic enrollment in Intune: Pilot ✑ Pilot collection for all workloads: Collection2 You configure co-management workloads as shown in the following exhibit.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
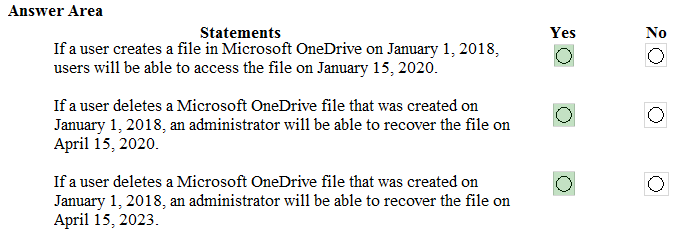
HOTSPOT - You have a Microsoft 365 E5 subscription. You need meet the following requirements: • Automatically encrypt documents stored in Microsoft OneDrive and SharePoint Online. • Enable co-authoring for Microsoft Office documents encrypted by using a sensitivity label. Which two settings should you use in the Microsoft Purview compliance portal? To answer, select the appropriate settings in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT - You have a Microsoft 365 E5 subscription. You plan to use a mailbox named Mailbox1 to analyze malicious email messages. You need to configure Microsoft Defender for Office 365 to meet the following requirements: • Ensure that incoming email is NOT filtered for Mailbox1. • Detect impersonation and spoofing attacks on all other mailboxes in the subscription. Which two settings should you configure? To answer, select the appropriate settings in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription that uses Microsoft 365 compliance center retention policies. You implement a preservation lock on a retention policy that is assigned to all executive users. Which two actions can you perform on the retention policy? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point?
A. Add locations to the policy
B. Reduce the duration of policy
C. Remove locations from the policy
D. Extend the duration of the policy
E. Disable the policy
You have a Microsoft 365 E5 subscription. Users have the devices shown in the following table.On which devices can you manage apps by using app configuration policies in Microsoft Endpoint Manager?
A. Device1, Device4, and Device6
B. Device2, Device3, and Device5
C. Device1, Device2, Device3, and Device6
D. Device1, Device2, Device4, and Device5
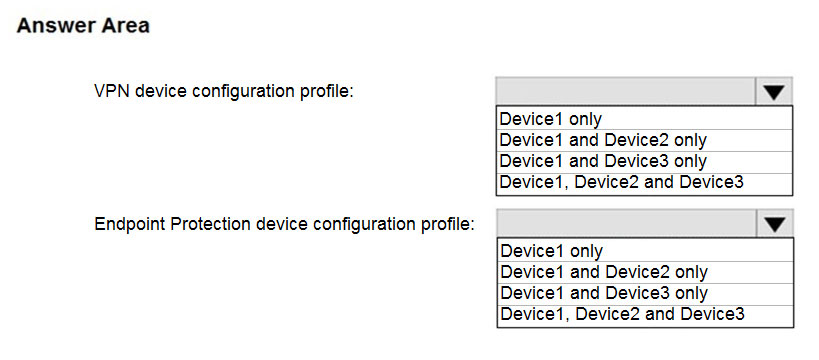
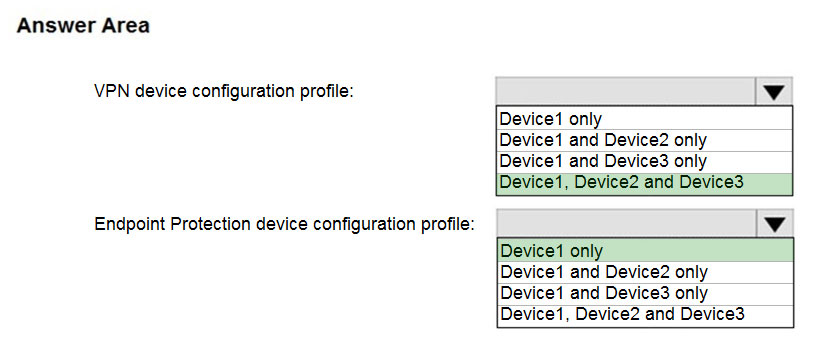
HOTSPOT - You have a Microsoft 365 tenant that contains devices enrolled in Microsoft Intune. The devices are configured as shown in the following table.You plan to perform the following device management tasks in Microsoft Endpoint Manager: Deploy a VPN connection by using a VPN device configuration profile.
✑ Configure security settings by using an Endpoint Protection device configuration profile. You need to identify which devices will support the management tasks. What should you identify? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 tenant. You plan to manage incidents in the tenant by using the Microsoft 365 Defender. Which Microsoft service source will appear on the Incidents page of the Microsoft 365 Defender?
A. Microsoft Defender for Cloud Apps
B. Azure Sentinel
C. Azure Web Application Firewall
D. Azure Information Protection
You have a Microsoft 365 tenant that is signed up for Microsoft Store for Business and contains a user named User1. You need to ensure that User1 can perform the following tasks in Microsoft Store for Business: ✑ Assign licenses to users. ✑ Procure apps from Microsoft Store. ✑ Manage private store availability for all items. The solution must use the principle of least privilege. Which Microsoft Store for Business role should you assign to User1?
A. Admin
B. Device Guard signer
C. Basic Purchaser
D. Purchaser
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your network contains an on-premises Active Directory domain. The domain contains 2,000 computers that run Windows 8.1 and have applications installed as shown in the following table.You enroll all the computers in Upgrade Readiness. You need to ensure that App1 and App2 have an UpgradeDecision status of Ready to upgrade. Solution: You set the importance status of App2 to Low install count. Does this meet the goal?
A. Yes
B. No
You have a Microsoft 365 E5 tenant. You create a retention label named Retention1 as shown in the following exhibit.When users attempt to apply Retention1, the label is unavailable. You need to ensure that Retention1 is available to all the users. What should you do?
A. Create a new label policy
B. Modify the Authority type setting for Retention1.
C. Modify the Business function/department setting for Retention1.
D. Use a file plan CSV template to import Retention1.
HOTSPOT - You have a Microsoft 365 E5 subscription that uses device management in Microsoft Endpoint Manager. You purchase five new Android devices and five new macOS devices. You need to enroll the new devices in Microsoft Intune. What should you use to enroll each device type? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Your company has a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com. You sign for Microsoft Store for Business. The tenant contains the users shown in the following table.Microsoft Store for Business has the following Shopping behavior settings: ✑ Allow users to shop is set to On ✑ Make everyone a Basic Purchaser is set to Off You need to identify which users can install apps from the Microsoft for Business private store. Which users should you identify?
A. User3 only
B. User1 only
C. User1 and User2 only
D. User3 and User4 only
HOTSPOT - You create two device compliance policies for Android devices as shown in the following table.You have the Android devices shown in the following table.
The users belong to the groups shown in the following table.
The users enroll their device in Microsoft Endpoint Manager. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 subscription that contains 500 Windows 11 devices enrolled in Microsoft Intune. You deploy a new Win32 app named App1 to all the devices and verify that users can install App1 manually by using the Company Portal app. You need to configure App1 to ensure that all future deployments of the app install automatically without user intervention. The solution must minimize administrative effort. What should you do?
A. Modify the detection rules for App1.
B. Delete App1, and then redeploy App1.
C. Modify the assignments for App1.
D. Modify the install command for App1.
Access Full MS-101 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete MS-101 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our MS-101 mock test free today—and take a major step toward exam success!