MS-101 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the MS-101 certification? Our MS-101 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective MS-101 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic MS-101 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
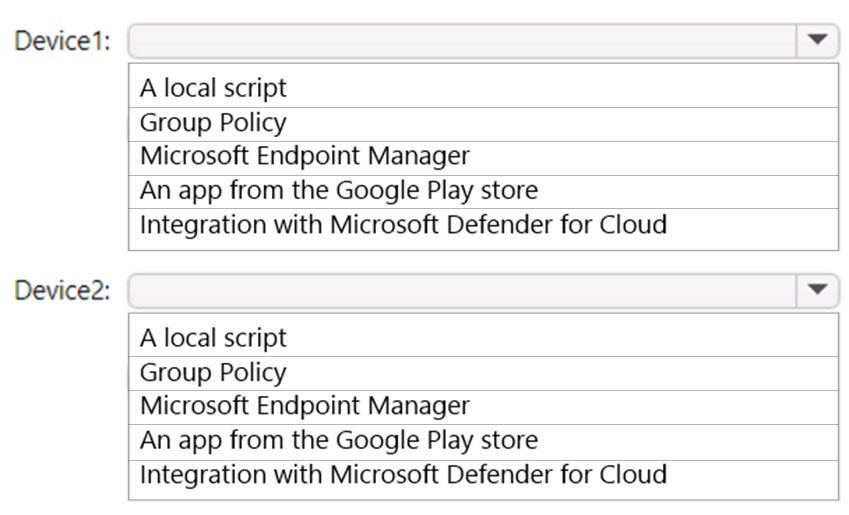
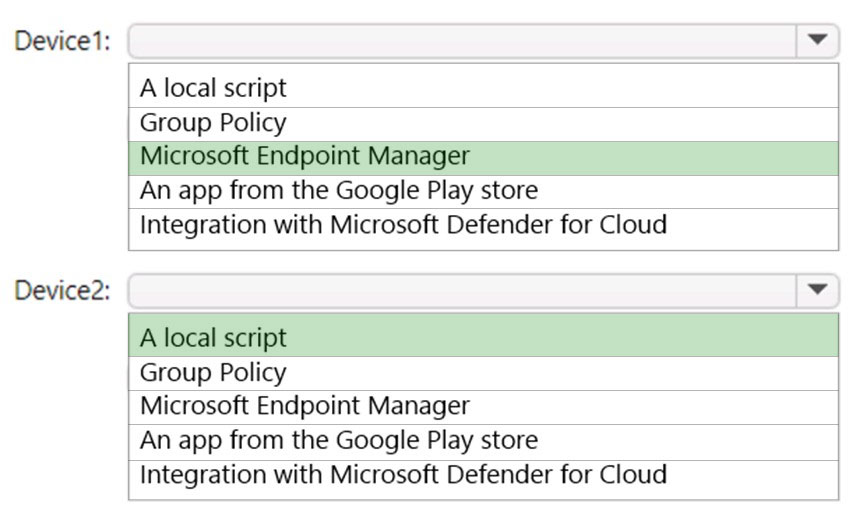
HOTSPOT - You have a Microsoft 365 E5 subscription that uses Microsoft Intune and contains the devices shown in the following table.You need to onboard Device1 and Device2 to Microsoft Defender for Endpoint. What should you use to onboard each device? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
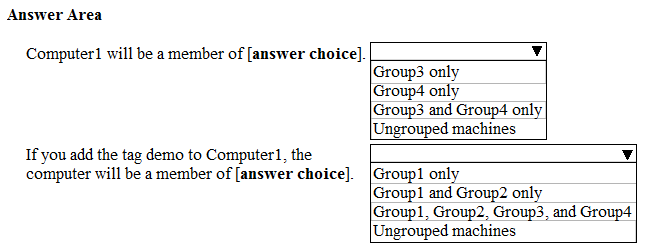
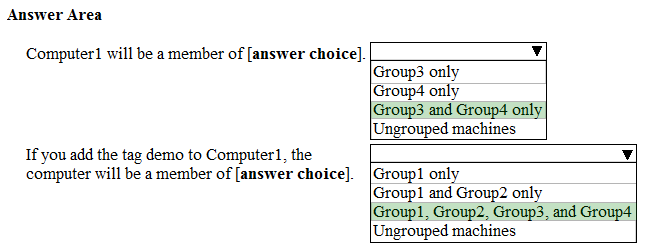
HOTSPOT - Your company uses Microsoft Defender Advanced Threat Protection (ATP). Microsoft Defender ATP includes the machine groups shown in the following table.You onboard a computer named computer1 to Microsoft Defender ATP as shown in the following exhibit.
Use the drop-down menus to select the answer choice that completes each statement. NOTE: Each correct selection is worth one point. Hot Area:
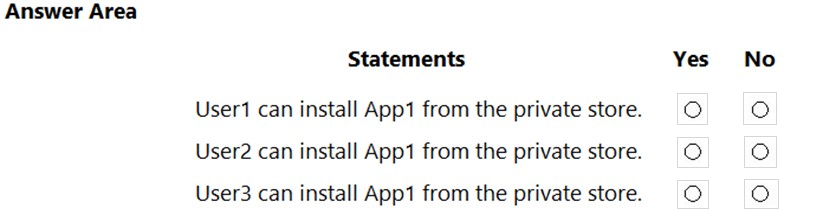
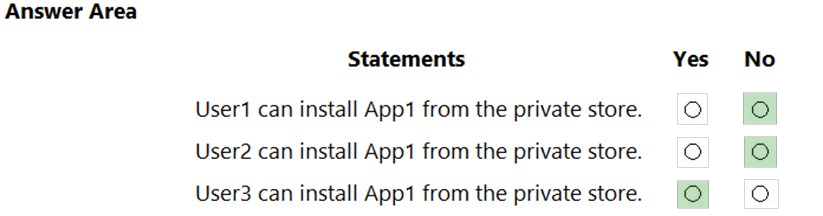
HOTSPOT - You have a Microsoft 365 E5 tenant that contains the users shown in the following table.You perform the following actions: ✑ Provision the private store in Microsoft Store for Business. ✑ Add an app named App1 to the private store. ✑ Set Private store availability for App1 to Specific groups, and then select Group3. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
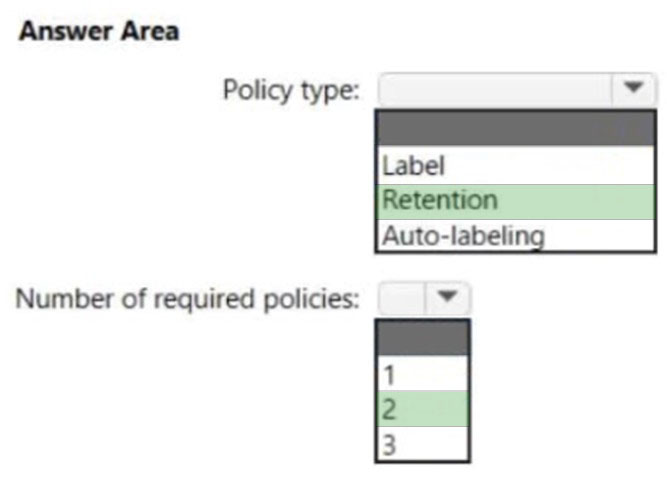
HOTSPOT - You need to configure the Information governance settings to meet the technical requirements. Which type of policy should you configure, and how many policies should you configure? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
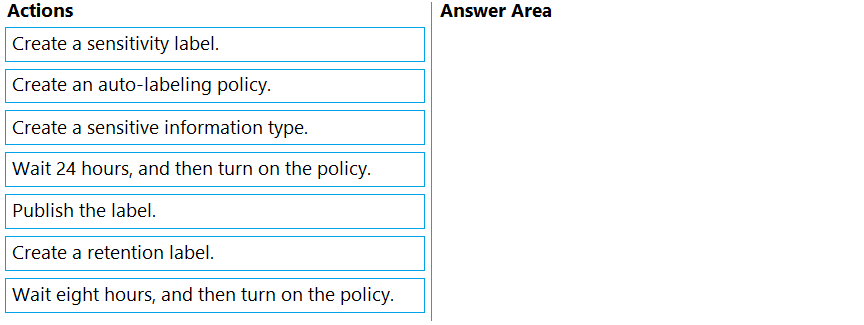
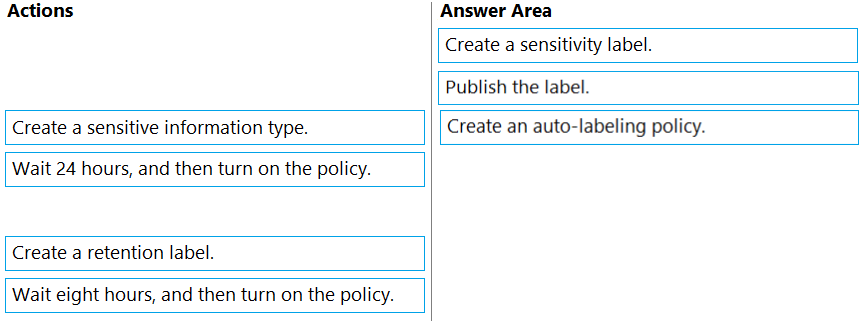
DRAG DROP - You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1. You need to automatically label the documents on Site1 that contain credit card numbers. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
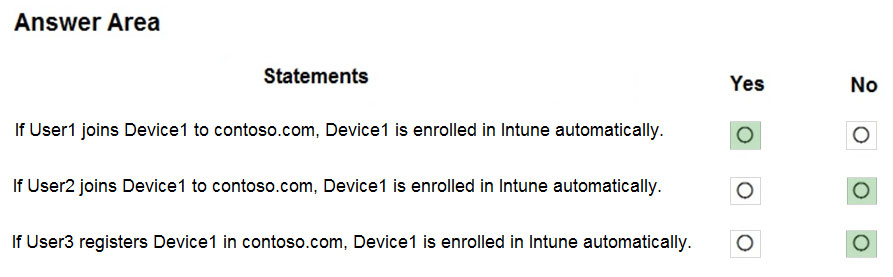
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.You integrate Microsoft Intune and contoso.com as shown in the following exhibit.
You purchase a Windows 10 device named Device1. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
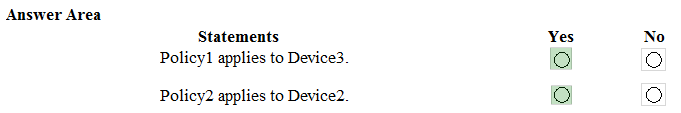
HOTSPOT - You have three devices enrolled in Microsoft Endpoint Manager as shown in the following table.The device compliance policies in Endpoint Manager are configured as shown in the following table.
The device compliance policies have the assignments shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You plan to use Microsoft Sentinel and Microsoft Defender for Cloud Apps. You need to connect Microsoft Defender for Cloud Apps to Microsoft Sentinel. What should you do in the Microsoft Defender for Cloud Apps portal?
A. From Automatic log upload, add a data source.
B. From Automatic log upload, add a log collector.
C. From Connected apps, add an app connector.
D. From Security extensions, add a SIEM agent.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 subscription. You discover that some external users accessed content on a Microsoft SharePoint site. You modify the SharePoint sharing policy to prevent sharing outside your organization. You need to be notified if the SharePoint sharing policy is modified in the future. Solution: From the SharePoint site, you create an alert. Does this meet the goal?
A. Yes
B. No
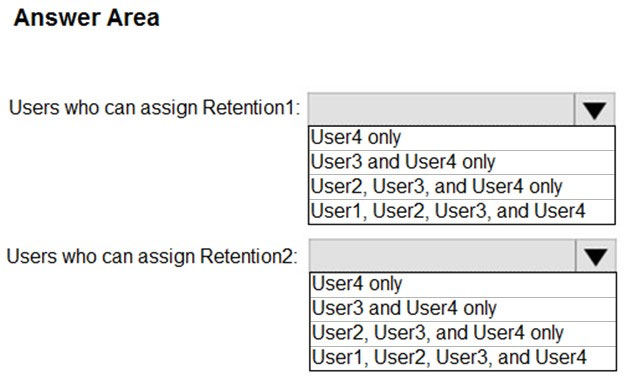
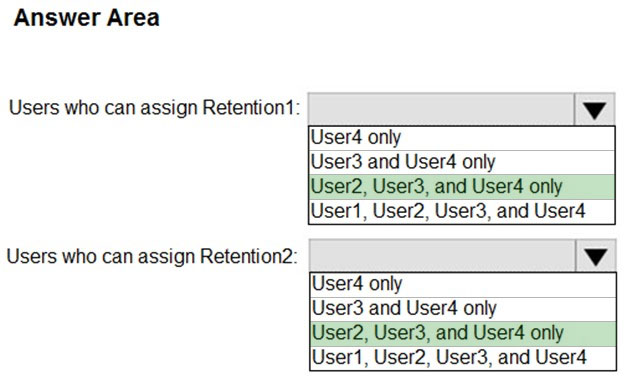
HOTSPOT - You have a Microsoft 365 E5 subscription that contains the users shown in the following table.You have a Microsoft Office 365 retention label named Retention1 that is published to Exchange email. You have a Microsoft Exchange Online retention policy that is applied to all mailboxes. The retention policy contains a retention tag named Retention2. Which users can assign Retention1 and Retention2 to their emails? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 tenant. All users are assigned the Enterprise Mobility + Security license. You need to ensure that when users join their device to Microsoft Azure Active Directory (Azure AD), the device is enrolled in Microsoft Endpoint Manager automatically. What should you configure?
A. Enrollment restrictions from the Endpoint Manager admin center
B. device enrollment managers from the Endpoint Manager admin center
C. MAM User scope from the Azure Active Directory admin center
D. MDM User scope from the Azure Active Directory admin center
You have Windows 10 devices that are managed by using Microsoft Endpoint Manager. You need to configure the security settings in Microsoft Edge. What should you create in Microsoft Endpoint Manager?
A. an app configuration policy
B. an app
C. a device configuration profile
D. a device compliance policy
You have a Microsoft 365 E5 subscription. You need to be notified if users receive email containing a file that has a virus. What should you do?
A. From the Exchange admin center, create an in-place eDiscovery & hold.
B. From the Exchange admin center, create a spam filter policy.
C. From the Exchange admin center, create an anti-malware policy.
D. From the Exchange admin center, create a mail flow rule.
HOTSPOT - You have a Microsoft 365 E5 subscription that uses sensitivity labels. You need to identify whenever a sensitivity label is applied, changed, or removed within the subscription. Which feature should you use, and how many days will the data be retained? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
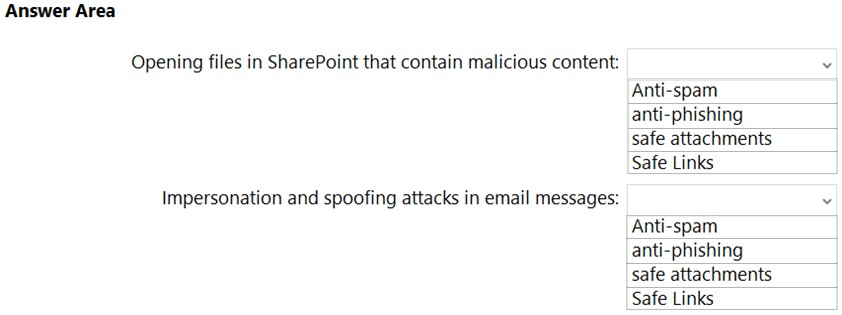
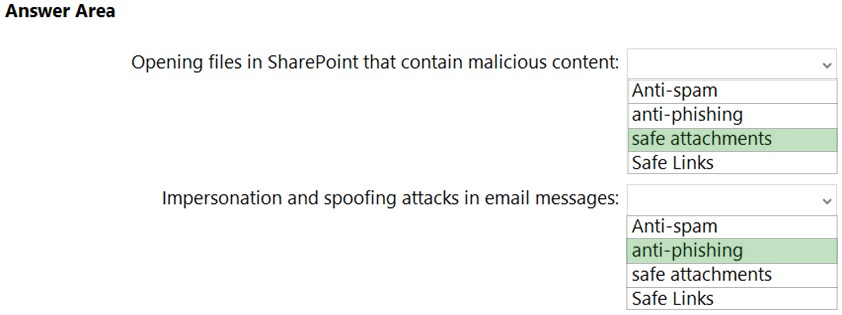
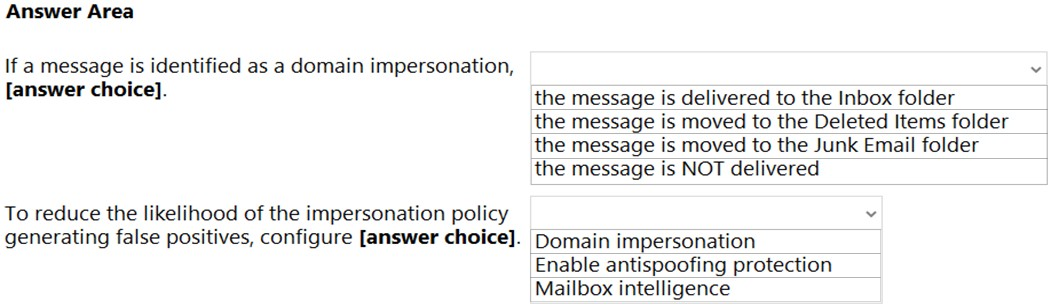
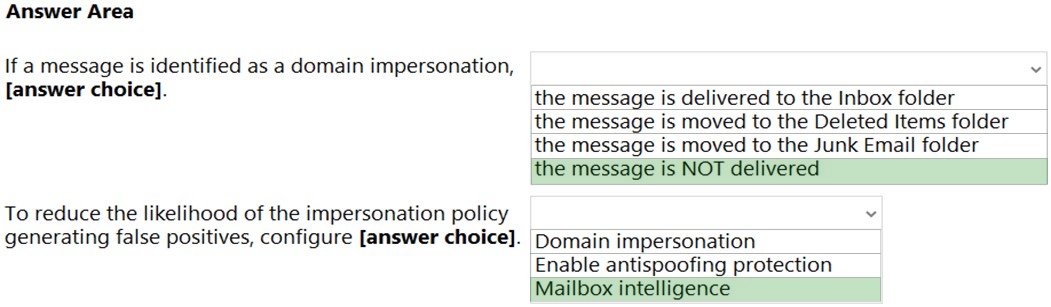
HOTSPOT - You have a Microsoft 365 subscription. You are planning a threat management solution for your organization. You need to minimize the likelihood that users will be affected by the following threats: ✑ Opening files in Microsoft SharePoint that contain malicious content ✑ Impersonation and spoofing attacks in email messages Which policies should you create in the Microsoft 365 Defender? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 tenant that contains devices registered for mobile device management. The devices are configured as shown in the following table.You plan to enable VPN access for the devices. What is the minimum number of configuration policies required?
A. 1
B. 3
C. 4
D. 5
You deploy Microsoft Azure Information Protection. You need to ensure that a security administrator named SecAdmin1 can always read and inspect data protected by Azure Rights Management (Azure RMS). What should you do?
A. From the Security & Compliance admin center, add SecAdmin1 to the eDiscovery Manager role group.
B. From the Azure Active Directory admin center, add SecAdmin1 to the Security Reader role group.
C. From the Security & Compliance admin center, add SecAdmin1 to the Compliance Administrator role group.
D. From Windows PowerShell, enable the super user feature and assign the role to SecAdmin1.
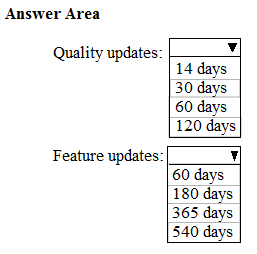
HOTSPOT - Your network contains an Active Directory domain named contoso.com. All client devices run Windows 10 and are joined to the domain. You update the Windows 10 devices by using Windows Update for Business. What is the maximum amount of time you can defer Windows 10 updates? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
Your company uses Microsoft Defender for Identity and Microsoft 365 Defender for Endpoint. You need to integrate Microsoft Defender for Identity and Microsoft 365 Defender for Endpoint. What should you do?
A. From Microsoft Defender for Identity, configure the notifications and reports.
B. From Microsoft Defender for Identity, configure the data sources.
C. From the Microsoft 365 Defender portal, configure general settings for Security center.
D. From the Microsoft 365 Defender portal, configure general settings for Microsoft 365 Defender.
You need to recommend a solution for the security administrator. The solution must meet the technical requirements. What should you include in the recommendation?
A. Microsoft Azure Active Directory (Azure AD) Privileged Identity Management
B. Microsoft Azure Active Directory (Azure AD) Identity Protection
C. Microsoft Azure Active Directory (Azure AD) conditional access policies
D. Microsoft Azure Active Directory (Azure AD) authentication methods
DRAG DROP - You have a Microsoft 365 subscription that contains the devices shown in the following table.You install Microsoft Word on all the devices. You plan to configure policies to meet the following requirements: • Word files created by using Windows devices must be encrypted automatically. • If an Android device becomes jailbroken, access to corporate data must be blocked from Word. • For iOS devices, users must be prevented from using native or third-party mail clients to connect to Microsoft 365. Which type of policy should you configure for each device? To answer, drag the appropriate policy types to the correct devices. Each policy type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
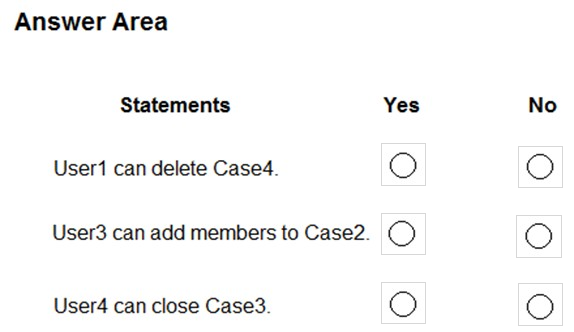
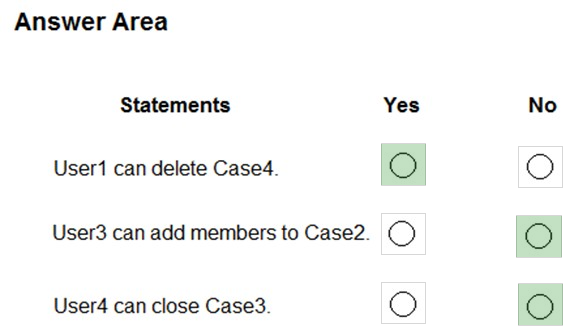
HOTSPOT - You have a Microsoft 365 tenant named contoso.com. The tenant contains the users shown in the following table.You have the eDiscovery cases shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 E5 subscription. You need to identify which users accessed Microsoft Office 365 from anonymous IP addresses during the last seven days. What should you do?
A. From the Microsoft 365 Defender portal, view the Threat tracker.
B. From the Microsoft 365 admin center, view the Usage report.
C. From Microsoft Defender for Cloud Apps, select Users and accounts.
D. From the Azure Active Directory admin center, view the Risky sign-ins report.
You need to configure Office on the web to meet the technical requirements. What should you do?
A. Assign the Global reader role to User1.
B. Enable sensitivity labels for Office files in SharePoint Online and OneDrive.
C. Configure an auto-labeling policy to apply the sensitivity labels.
D. Assign the Office apps admin role to User1.
You have a Microsoft 365 subscription. All users have their email stored in Microsoft Exchange Online. In the mailbox of a user named User1, you need to preserve a copy of all the email messages that contain the word ProjectX. What should you do first?
A. From the Exchange admin center, start a mail flow message trace.
B. From the Microsoft Purview compliance portal, create an eDiscovery case.
C. From Microsoft Defender for Cloud Apps, create an activity policy.
D. From the Microsoft Purview compliance portal, create a data loss prevention (DLP) policy.
Your company has a Microsoft 365 subscription. You need to identify which users performed the following privileged administration tasks: ✑ Deleted a folder from the second-stage Recycle Bin of Microsoft SharePoint ✑ Opened a mailbox of which the user was not the owner ✑ Reset a user password What should you use?
A. Microsoft Azure Active Directory (Azure AD) audit logs
B. Microsoft 365 compliance content search
C. Microsoft Azure Active Directory (Azure AD) sign-ins
D. Microsoft 365 compliance audit log search
You have a Microsoft 365 E5 subscription that contains a user named User1. The subscription has a single anti-malware policy as shown in the following exhibit.An email message that contains text and two attachments is sent to User1. One attachment is infected with malware. How will the email message and the attachments be processed?
A. Both attachments will be removed. The email message will be quarantined, and User1 will receive an email message without any attachments and an email message that includes the following text: ג€Malware was removed.ג€
B. The email message will be quarantined, and the message will remain undelivered.
C. Both attachments will be removed. The email message will be quarantined, and User1 will receive a copy of the message containing the original text and a new attachment that includes the following text: ג€Malware was removed.ג€
D. The malware-infected attachment will be removed. The email message will be quarantined, and User1 will receive a copy of the message containing only the uninfected attachment.
Your company has a Microsoft 365 E3 subscription. All devices run Windows 10 Pro and are joined to Microsoft Azure Active Directory (Azure AD). You need to change the edition of Windows 10 to Enterprise the next time users sign in to their computer. The solution must minimize downtime for the users. What should you use?
A. Windows Autopilot
B. Windows Update
C. Subscription Activation
D. an in-place upgrade
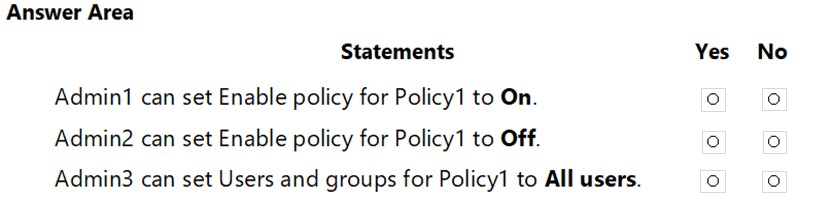
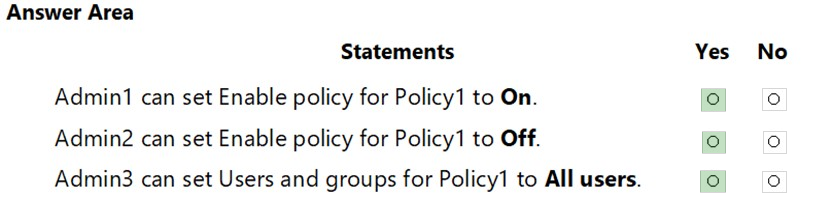
HOTSPOT - You have a Microsoft 365 E5 subscription linked to an Azure Active Directory (Azure AD) tenant. The tenant contains a group named Group1 and the users shown in the following table:The tenant has a conditional access policy that has the following configurations: ✑ Name: Policy1 ✑ Assignments: - Users and groups: Group1 - Cloud aps or actions: All cloud apps ✑ Access controls: ✑ Grant, require multi-factor authentication ✑ Enable policy: Report-only You set Enabled Security defaults to Yes for the tenant. For each of the following settings select Yes, if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You configure an anti-phishing policy as shown in the following exhibit.Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You have three devices enrolled in Microsoft Intune as shown in the following table.The device compliance policies in Intune are configured as shown in the following table.
The device compliance policies have the assignments shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
Your network contains an Active Directory domain named contoso.com. The domain contains 100 Windows 8.1 devices. You plan to deploy a custom Windows 10 Enterprise image to the Windows 8.1 devices. You need to recommend a Windows 10 deployment method. What should you recommend?
A. a provisioning package
B. an in-place upgrade
C. wipe and load refresh
D. Windows Autopilot
Your company has a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com. You sign up for Microsoft Store for Business. The tenant contains the users shown in the following table.Microsoft Store for Business has the following Shopping behavior settings: ✑ Make everyone a Basic Purchaser is set to Off. ✑ Allow app requests is set to On. You need to identify which users can add apps to the Microsoft Store for Business private store. Which users should you identify?
A. User1 and User2 only
B. User3 only
C. User1 only
D. User3 and User4 only
Your company has five security information and event management (SIEM) appliances. The traffic logs from each appliance are saved to a file share named Logs. You need to analyze the traffic logs. What should you do from Microsoft Defender for Cloud Apps?
A. Click Investigate, and then click Activity log.
B. Click Control, and then click Policies. Create a file policy.
C. Click Discover, and then click Create snapshot report.
D. Click Investigate, and then click Files.
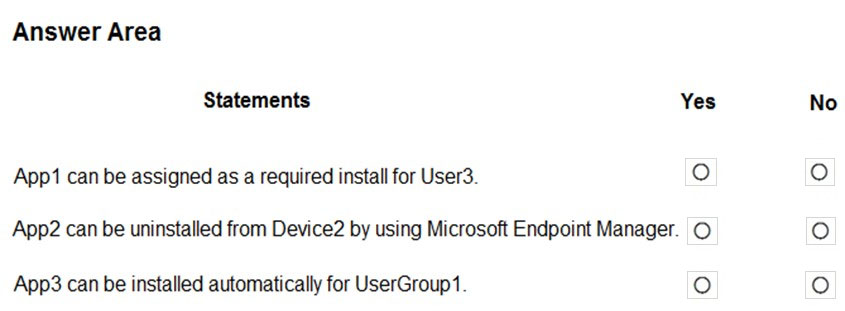
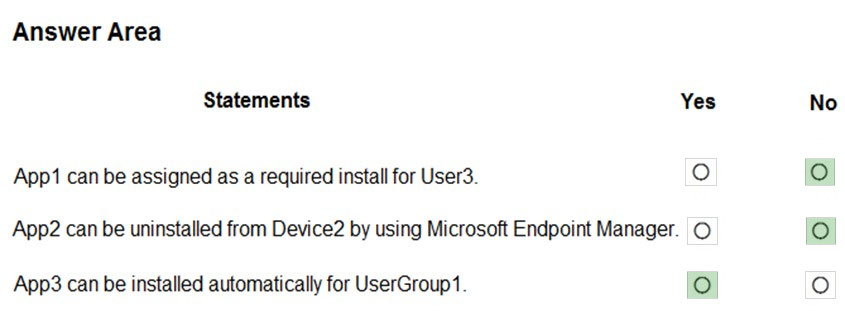
HOTSPOT - You have a Microsoft 365 E5 tenant that contains the users shown in the following table.The tenant contains the devices shown in the following table.
You have the apps shown in the following table.
You plan to use Microsoft Endpoint Manager to manage the apps for the users. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
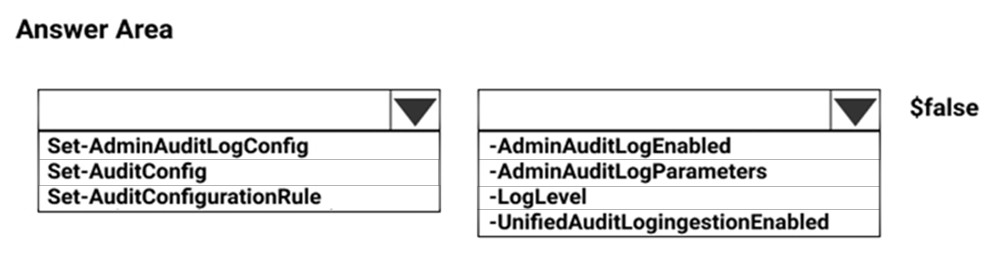
HOTSPOT - You create a Microsoft 365 subscription. Your company's privacy policy states that user activities must NOT be audited. You need to disable audit logging in Microsoft 365. How should you complete the command? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 subscription. You need to be notified if users receive email containing a file that has a virus. What should you do?
A. From the Exchange admin center, create an in-place eDiscovery & hold.
B. From the Security & Compliance admin center, create a data loss prevention (DLP) policy.
C. From the Exchange admin center, create an anti-malware policy.
D. From the Exchange admin center, create a mail flow rule.
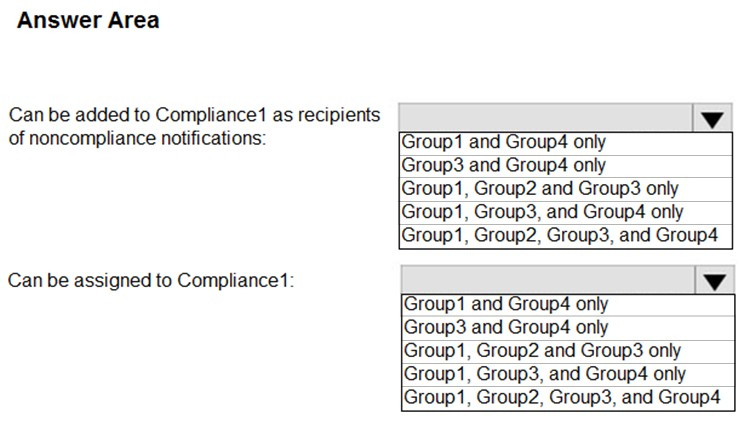
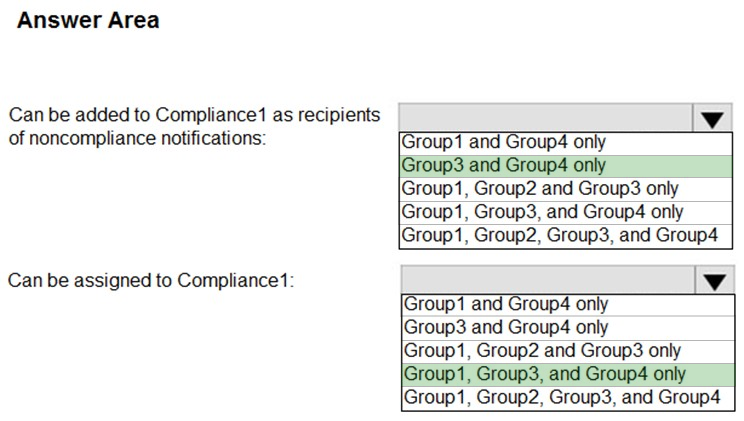
HOTSPOT - You have a Microsoft 365 tenant that contains the groups shown in the following table.You plan to create a compliance policy named Compliance1. You need to identify the groups that meet the following requirements: ✑ Can be added to Compliance1 as recipients of noncompliance notifications ✑ Can be assigned to Compliance1 To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 subscription that contains 500 users. You have several hundred computers that run the 64-bit version of Windows 10 Enterprise and have the following configurations: ✑ Two volumes that contain data ✑ A CPU that has two cores ✑ TPM disabled ✑ 4 GB of RAM All the computers are managed by using Microsoft Endpoint Manager. You need to ensure that you can turn on Windows Defender Application Guard on the computers. What should you do first?
A. Modify the edition of Windows 10.
B. Create an additional volume.
C. Replace the CPU and enable TPM.
D. Replace the CPU and increase the RAM.
You have a Microsoft 365 tenant. You plan to manage incidents in the tenant by using the Microsoft 365 Defender. Which Microsoft service source will appear on the Incidents page of the Microsoft 365 Defender portal?
A. Azure Information Protection
B. Azure Arc
C. Microsoft Sentinel
D. Microsoft Defender for Identity
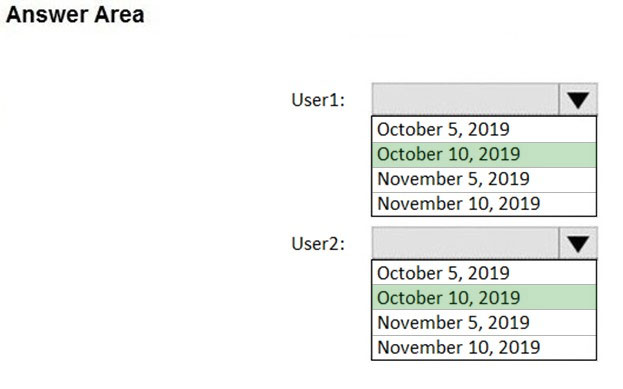
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant that contains two users named User1 and User2. On September 5, 2019, you create and enforce a terms of use (ToU) in the tenant. The ToU has the following settings: ✑ Name: Terms1 ✑ Display name: Terms1 name ✑ Require users to expand the terms of use: Off ✑ Require users to consent on every device: Off ✑ Expire consents: On ✑ Expire starting on: October 10, 2019 ✑ Frequency: Monthly User1 accepts Terms1 on September 5, 2019. User2 accepts Terms1 on October 5, 2019. When will Terms1 expire for the first time for each user? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your network contains an on-premises Active Directory domain. The domain contains 2,000 computers that run Windows 8.1 and have applications installed as shown in the following table.You enroll all the computers in Upgrade Readiness. You need to ensure that App1 and App2 have an UpgradeDecision status of Ready to upgrade. Solution: You set the Importance status of App1 to Business critical. Does this meet the goal?
A. Yes
B. No
You have a Microsoft 365 subscription that uses a default domain named contoso.com. You have two users named User1 and User2. From the Microsoft 365 compliance center, you add User1 to the eDiscovery Manager role group. From the Microsoft 365 compliance center, User1 creates a case named Case1. You need to ensure that User1 can add User2 as a case member. The solution must use the principle of least privilege. To which role group should you add User2?
A. eDiscovery Manager
B. eDiscovery Administrator
C. Security Administrator
You have a Microsoft 365 E5 tenant. You need to be notified when emails with attachments that contain sensitive personal data are sent to external recipients. Which two policies can you use? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. a data loss prevention (DLP) policy
B. a sensitivity label policy
C. a Microsoft Defender for Cloud Apps file policy
D. a communication compliance policy
E. a retention label policy
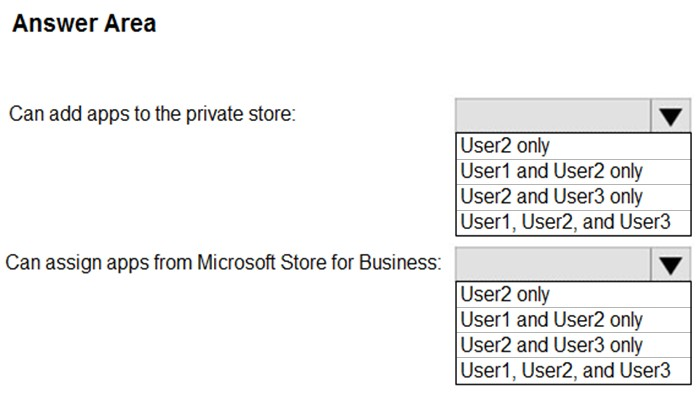
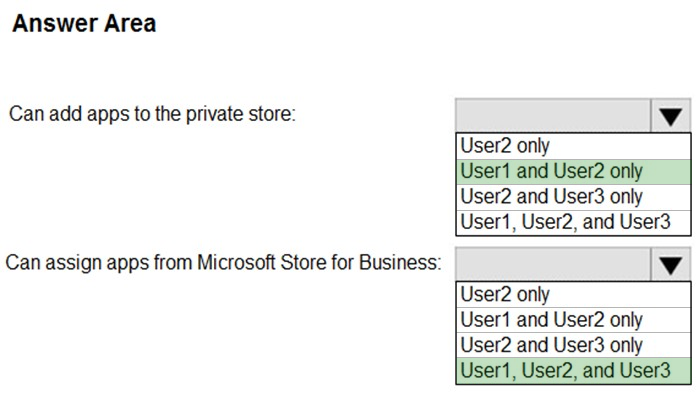
HOTSPOT - You have a Microsoft 365 E5 tenant that contains the users shown in the following table.You provision the private store in Microsoft Store for Business. You assign Microsoft Store for Business roles to the users as shown in the following table.
You need to identify which users can add apps to the private store, and which users can assign apps from Microsoft Store for Business. Which users should you identify? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You have a Microsoft 365 E5 subscription that uses device management in Microsoft Endpoint Manager. You purchase five new Android devices and five new macOS devices. You need to enroll the new devices in Microsoft Intune. What should you use to enroll each device type? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription. All users have their email stored in Microsoft Exchange Online. In the mailbox of a user named User1, you need to preserve a copy of all the email messages that contain the word ProjectX. What should you do?
A. From the Security & Compliance admin center, create an eDiscovery case.
B. From the Exchange admin center, create a mail flow rule.
C. From the Security & Compliance admin center, start a message trace.
D. From Microsoft Defender for Cloud Apps, create an access policy.
You need to meet the compliance requirements for the Windows 10 devices. What should you create from the Endpoint Management admin center?
A. a device compliance policy
B. a device configuration profile
C. an app protection policy
D. an app configuration policy
You have a Microsoft 365 E5 subscription. The subscription contains users that have the following types of devices: • Windows 10 • Android • iOS On which devices can you configure the Endpoint DLP policies?
A. Windows 10 only
B. Windows 10 and Android only
C. Windows 10 and iOS only
D. Windows 10, Android, and iOS
HOTSPOT - You have a Microsoft 365 subscription that contains an Endpoint data loss prevention (Endpoint DLP) policy named Policy1 and the devices shown in the following table.For Policy1, the Audit or restrict activities on devices settings are configured as shown in the Activities exhibit. (Click the Activities tab.)
For Policy1, the Allow override from Endpoint devices settings are configured as shown in the Devices exhibit. (Click the Devices tab.)
Test users discover that they cannot copy data to their network shares while working remotely. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Access Full MS-101 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of MS-101 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your MS-101 certification journey!