MD-100 Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the MD-100 exam? Start with our MD-100 Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a MD-100 practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free MD-100 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
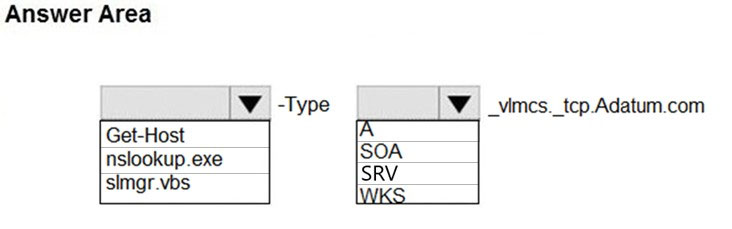
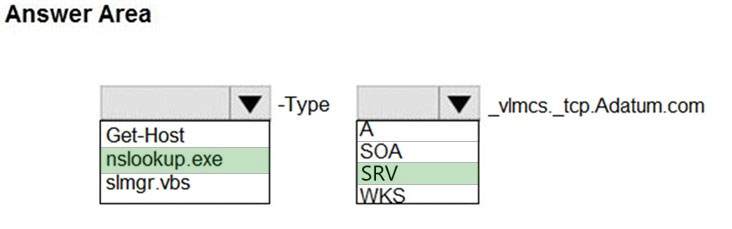
HOTSPOT - Your network contains an Active Directory domain named adatum.com that uses Key Management Service (KMS) for activation. You deploy a computer that runs Windows 10 to the domain. The computer fails to activate. You suspect that the activation server has an issue. You need to identify which server hosts KMS. How should you complete the command? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have 100 computers that run Windows 10. The computers are joined to an Azure AD tenant and enrolled in Microsoft Intune. The computers are in remote locations and connected to public networks. You need to recommend a solution for help desk administrators that meets the following requirements: • Connect remotely to a user's computer to perform troubleshooting. • Connect to a user's computer without disrupting the desktop of the computer. • Remotely view services, performance counters, registry settings, and event logs. Which tool should you include in the recommendation?
A. Quick Assist
B. Intune
C. Remote Assistance
D. Windows Admin Center
E. Remote Desktop
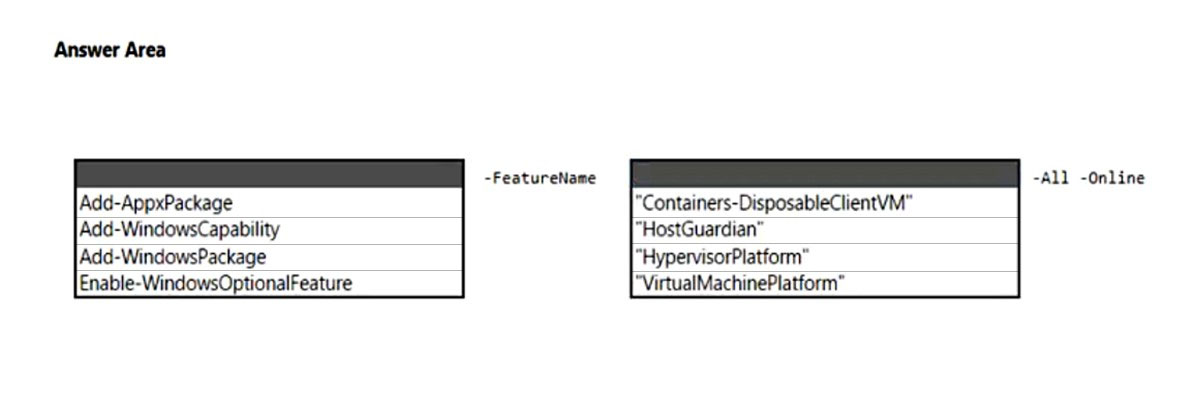
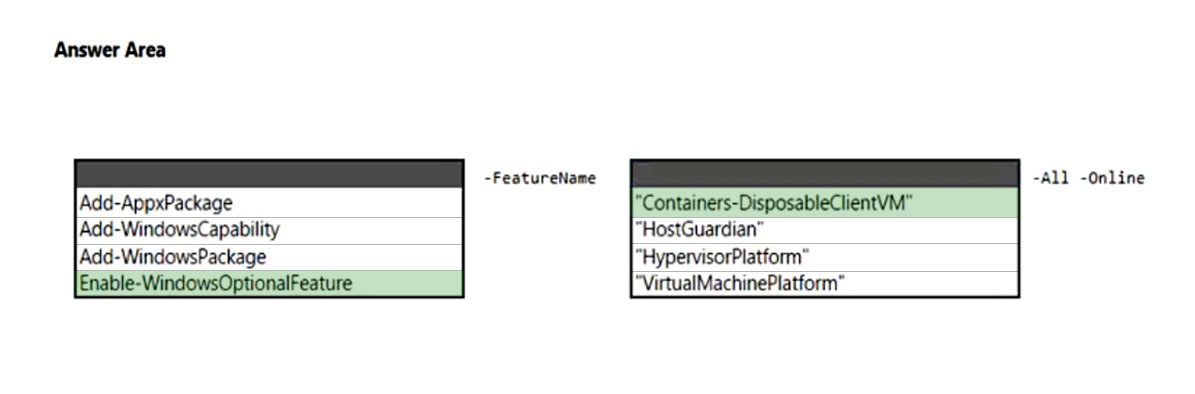
HOTSPOT - You have 20 computers that run Windows 11. You need to enable Windows Sandbox on the computers. How should you complete the command? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a computer that is configured as shown in the following exhibit.What can the computer connect to?
A. all the local computers and the remote computers within your corporate network only
B. all the local computers and the remote computers, including Internet hosts
C. only other computers on the same network segment that have automatic private IP addressing (APIPA)
D. only other computers on the same network segment that have an address from a class A network ID
Your network contains an Active Directory domain. The domain contains 100 computers that run Windows 11. You need to defer the deployment of quality updates by using Group Policy. What is the maximum amount of time that you can defer the updates?
A. 180 days
B. seven days
C. 30 days
D. 365 days
Which users can sign in to Computer3 when the computer starts in Safe Mode?
A. User31 only
B. User31 and User32 only
C. User31 and Admin1 only
D. User31, User 32, User33, and Admin1
E. User31, User32, and User33 only
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a computer named Computer1 that runs Windows 10. You test Windows updates on Computer1 before you make the updates available to other computers. You install a quality update that conflicts with a custom device driver. You need to remove the update from Computer1. Solution: From an elevated command prompt, you run the wusa.exe command and specify the /uninstall parameter. Does this meet the goal?
A. Yes
B. No
Your network contains an Active Directory domain that is synced to a Microsoft Azure Active Directory (Azure AD) tenant. All users have been issued with laptop computers as well as desktop computers that run Windows 10 Enterprise. All users have Microsoft 365 E3 licenses. A user named Mia Hamm informs you that she must perform a BitLocker recovery on her laptop but she does not have her BitLocker recovery key. You need to ensure that Mia Hamm can perform a BitLocker recovery on her laptop. What should you do?
A. Instruct Mia Hamm to log on to her desktop computer and run the repair-bde.exe command.
B. Instruct Mia Hamm to use the BitLocker Recovery Password Viewer to view the computer object of the laptop.
C. Instruct Mia Hamm to log on to her desktop computer and go to https://account.activedirectory.windowsazure.com and view the user account profile.
D. Instruct Mia Hamm to run the Enable-BitLocker cmdlet on her laptop.
A user named User1 has a computer named Computer1 that runs Windows 10. User1 connects to a Microsoft Azure virtual machine named VM1 by using Remote Desktop. User1 creates a VPN connection named VPN1 to connect to a partner organization. When the VPN1 connection is established, User1 cannot connect to VM1. When User1 disconnects from VPN1, the user can connect to VM1. You need to ensure that User1 can connect to VM1 while connected to VPN1. What should you do?
A. From the proxy settings, add the IP address of VM1 to the bypass list to bypass the proxy.
B. From the properties of VPN1, clear the Use default gateway on remote network check box.
C. From the properties of the Remote Desktop connection to VM1, specify a Remote Desktop Gateway (RD Gateway).
D. From the properties of VPN1, configure a static default gateway address.
You have a public computer named Computer1 that runs Windows 10. Computer1 contains a folder named Folder1. You need to provide a user named User1 with the ability to modify the permissions of Folder1. The solution must use the principle of least privilege. Which NTFS permission should you assign to User1?
A. Full control
B. Modify
C. Write
D. Read & execute
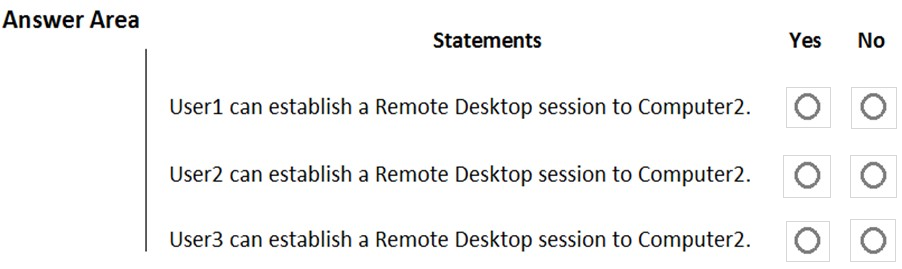
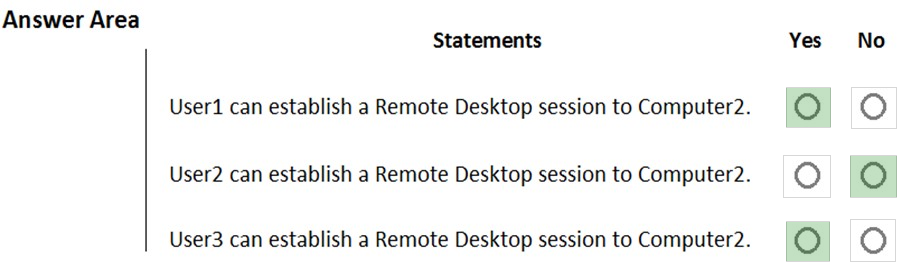
HOTSPOT - Your network contains an Active Directory domain named adatum.com. The domain contains two computers named Computer1 and Computer2 that run Windows 10. The domain contains the user accounts shown in the following table.Computer2 contains the local groups shown in the following table.
The relevant user rights assignments for Computer2 are shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You have a computer named Computer1 that runs Windows 10. You need to enable boot logging on Computer1. What should you do?
A. At a command prompt, run the bcdboot.exe command and specify the /v parameter.
B. From the Settings app, configure the Start settings.
C. From System Properties in Control Panel, configure the Startup and Recovery settings.
D. From System Configuration configure the Boot settings.
You have a computer named Computer1 that runs Windows 10. You need to configure User Account Control (UAC) to prompt administrators for their credentials. Which settings should you modify?
A. Administrators Properties in Local Users and Groups
B. User Account Control Settings in Control Panel
C. Security Options in Local Group Policy Editor
D. User Rights Assignment in Local Group Policy Editor
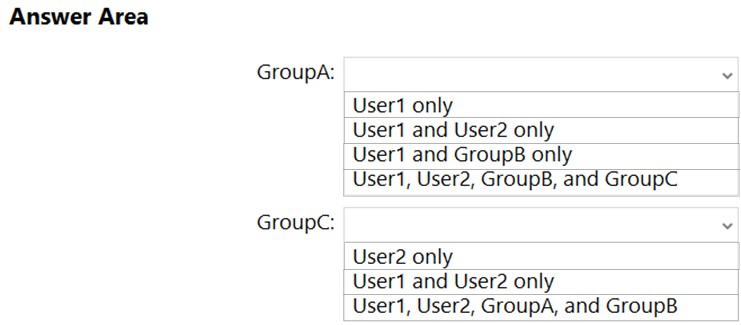
HOTSPOT - You have two workgroup computers named Computer1 and Computer2 that run Windows 10. The computers contain the local security principals shown in the following table.Which security principals can be members of GroupA and GroupC? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
Your network contains an Active Directory domain. The domain contains 1,000 computers that run Windows 10. You discover that when users are on their lock screen, they see a different background image every day, along with tips for using different features in Windows 10. You need to disable the tips and the daily background image for all the Windows 10 computers. Which Group Policy settings should you modify?
A. Turn off the Windows Welcome Experience
B. Turn off Windows Spotlight on Settings
C. Do not suggest third-party content in Windows spotlight
D. Turn off all Windows spotlight features
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a computer that runs Windows 10. The computer contains a folder. The folder contains sensitive data. You need to log which user reads the contents of the folder and modifies and deletes files in the folder. Solution: From the properties of the folder, you configure the Auditing settings and from Audit Policy in the local Group Policy, you configure Audit object access. Does this meet the goal?
A. Yes
B. No
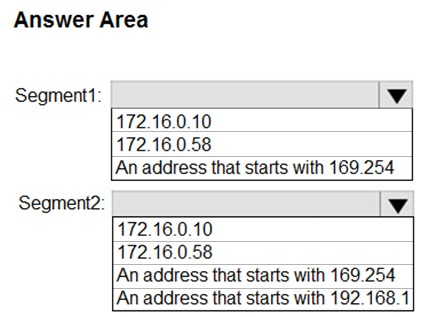
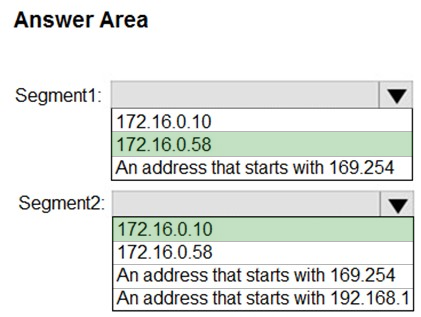
HOTSPOT - Your network contains the segments shown in the following table.You have a computer that runs Windows 10. The network interface of the computer is configured as shown in the exhibit. (Click the Exhibit tab.)
You need to identify which IP address the computer will have on the network when the computer connects to the segments. Which IP address should you identify for each segment? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
Your network contains 500 computers that run Windows 11 and have Delivery Optimization enabled. All the computers contain the following: • Microsoft 365 apps • A Microsoft Store app named App1 • A Windows 11 driver named Driver1 What can use Delivery Optimization to download updates?
A. Driver1 only
B. Microsoft 365 apps only
C. Microsoft 365 apps and Driver1 only
D. Microsoft 365 apps, Driver1, and App1
SIMULATION - Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time. When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design. Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task. Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided. Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab. Username and password -Use the following login credentials as needed: To enter your password, place your cursor in the Enter password box and click on the password below. Username: Contoso/Administrator - Password: Passw0rd! The following information is for technical support purposes only: Lab Instance: 10921597 -
You need to ensure that a local user named User1 can establish a Remote Desktop connection to Client2. To complete this task, sign in to the required computer or computers.
Your network contains an Active Directory domain named contoso.com. The domain contains a computer named Computer1 that runs Windows 10. On Computer1, you create a folder and assign Full control permissions to Everyone. You share the folder as Share1 and assign the permissions shown in the following table.When accessing Share1, which two actions can be performed by User1 but not by User2? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Delete a file created by another user.
B. Set the permissions for a file.
C. Rename a file created by another user.
D. Take ownership of file.
E. Copy a file created by another user to a subfolder.
You sign in to a computer that runs Windows 10 Pro. You need to ensure that after a restart, the computer starts automatically in Safe Mode with Networking. What should you use to configure the restart options?
A. bootcfg
B. BCDEdit
C. Windows System Image Manager (Windows SIM)
D. bootrec
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You manage devices that run Windows 10. Ten sales users will travel to a location that has limited bandwidth that is expensive. The sales users will be at the location for three weeks. You need to prevent all Windows updates from downloading for the duration of the trip. The solution must not prevent access to email and the Internet. Solution: From Accounts in the Settings app, you turn off Sync settings. Does this meet the goal?
A. Yes
B. No
You have a computer named Computer1. Computer1 runs Windows 10 Pro. Computer1 is experiencing connectivity issues. You need to view the IP addresses of any remote computer that Computer1 has an active TCP connection to. Should you do?
A. In Windows Administrative Tools, open Performance Monitor.
B. In the Control Panel, open Network and Internet. Then select Network and Sharing Center.
C. In Windows Administrative Tools, open Resource Monitor.
D. In the Setting app, open Update and Security. Then open Windows Security and select Firewall and Network protection.
You have a computer that runs Windows 10. You use the computer to test new Windows features. You need to configure the computer to receive preview builds of Windows 10 as soon as possible. What should you configure from Update & Security in the Settings app?
A. Windows Insider Program
B. Windows Update
C. Delivery Optimization
D. For developers
You need to meet the technical requirements for the San Diego office computers. Which Windows 10 deployment method should you use?
A. wipe and load refresh
B. in-place upgrade
C. provisioning packages
D. Windows Autopilot
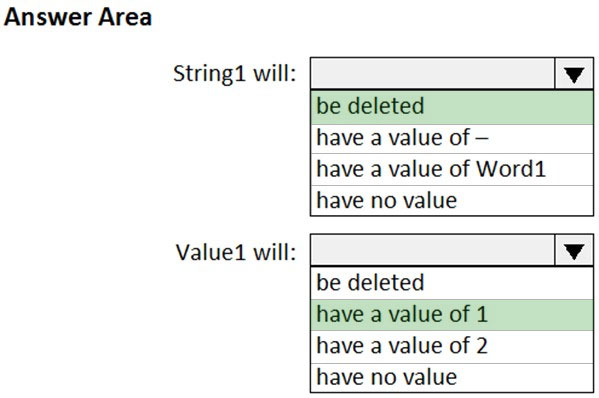
HOTSPOT - You have a computer named Computer1 that runs Windows 10. Computer1 contains a registry key named Key1 that has the values shown in the exhibit. (Click the Exhibit tab.).You have a Registration Entries (.reg) file named File1.reg that contains the following text. Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINESOFTWAREKey1] "String1"=- @="2" You need to identify the effect of importing File1.reg to Computer1. What should you identify? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
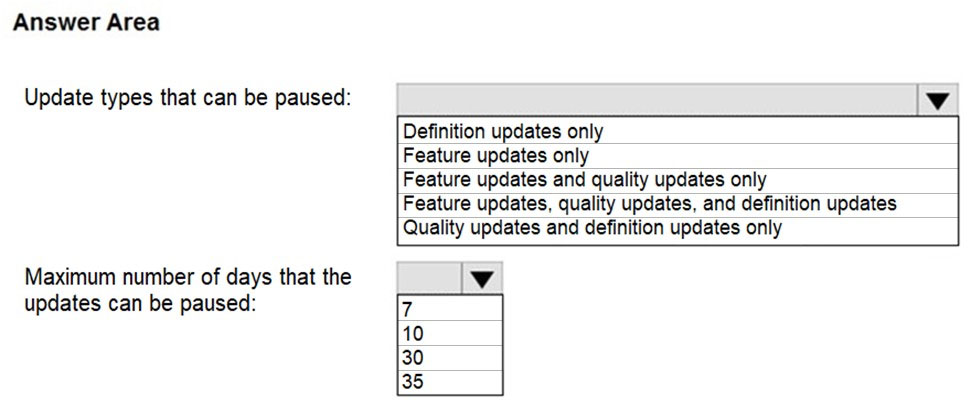
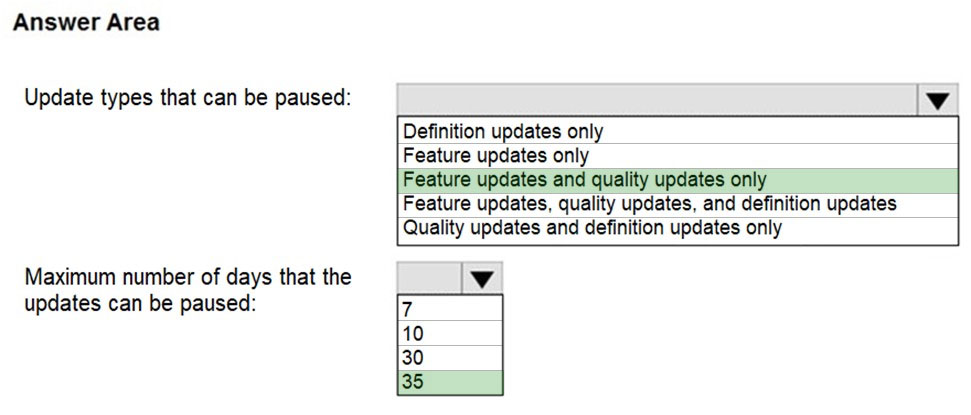
HOTSPOT - You manage Windows updates for a computer that runs Windows 10. You need to identify the following: ✑ Which update types can be paused ✑ The maximum number of days that the updates can be paused What should you identify? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You need to meet the technical requirements for EFS on ComputerA. What should you do?
A. Run certutil.exe, and then add a certificate to the local computer certificate store.
B. Run cipher.exe, and then add a certificate to the local computer certificate store.
C. Run cipher.exe, and then add a certificate to the local Group Policy.
D. Run certutil.exe, and then add a certificate to the local Group Policy.
You have several computers that run Windows 10. The computers are in a workgroup and have BitLocker Drive Encryption (BitLocker) enabled. You join the computers to Microsoft Azure Active Directory (Azure AD). You need to ensure that you can recover the BitLocker recovery key for the computers from Azure AD. What should you do first?
A. Disable BitLocker.
B. Add a BitLocker key protector.
C. Suspend BitLocker.
D. Disable the TMP chip.
SIMULATION - Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time. When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design. Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task. Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided. Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab. Username and password -Use the following login credentials as needed: To enter your password, place your cursor in the Enter password box and click on the password below. Username: Contoso/Administrator - Password: Passw0rd! The following information is for technical support purposes only: Lab Instance: 10921597 -
You need to create a user account named User5 on Client2. The solution must meet the following requirements: ✑ Prevent User5 from changing the password of the account. ✑ Ensure that User5 can perform backups. ✑ Use the principle of least privilege. To complete this task, sign in to the required computer or computers.
You have a workgroup computer that runs Windows 10. You need to set the minimum password length to 12 characters. What should you use?
A. Local Group Policy Editor
B. Local Users and Groups in Computer Management
C. Email & accounts in the Settings app
D. Credential Manager in Control Panel
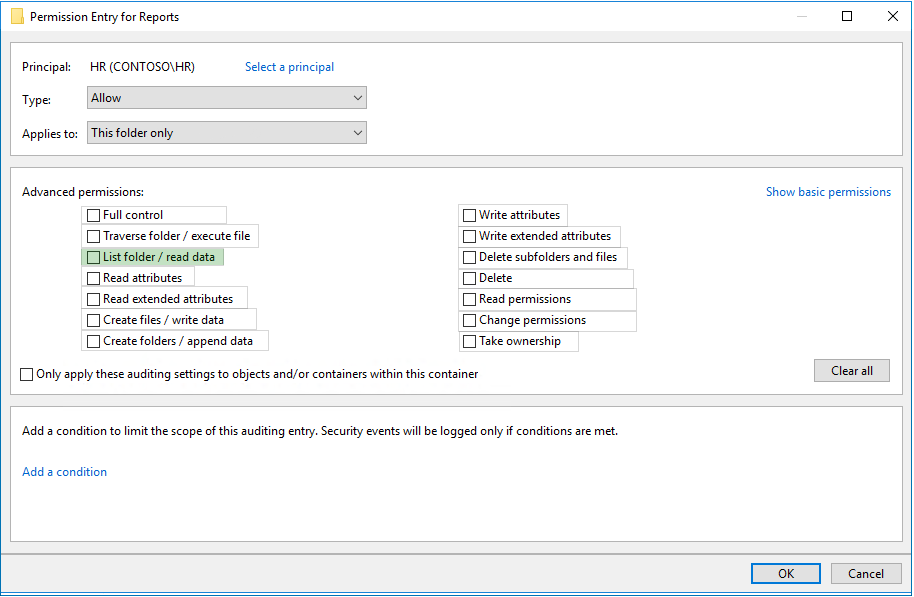
HOTSPOT - You need to meet the technical requirements for the HR department users. Which permissions should you assign to the HR department users for the D:Reports folder? To answer, select the appropriate permissions in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have 10 computers that run Windows 8.1 and have the following configurations: • A single MBR disk • A disabled TPM chip • Disabled hardware virtualization • UEFI firmware running in BIOS mode • Enabled Data Execution Prevention (DEP) You plan to upgrade the computers to Windows 10. You need to ensure that the computers can use Secure Boot. Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Enable hardware virtualization.
B. Disable DEP.
C. Convert the MBR disk to a GPT disk.
D. Enable the TPM chip.
E. Convert the firmware from BIOS to UEFI.
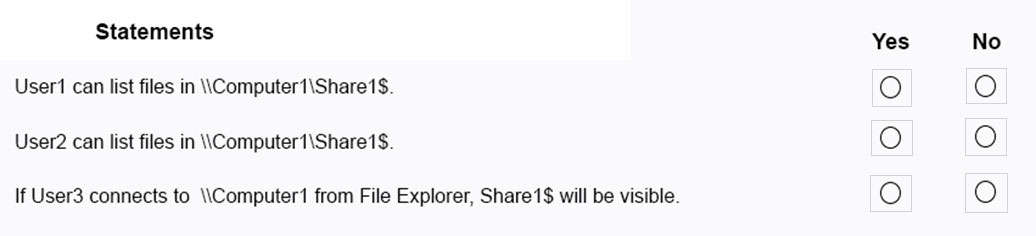
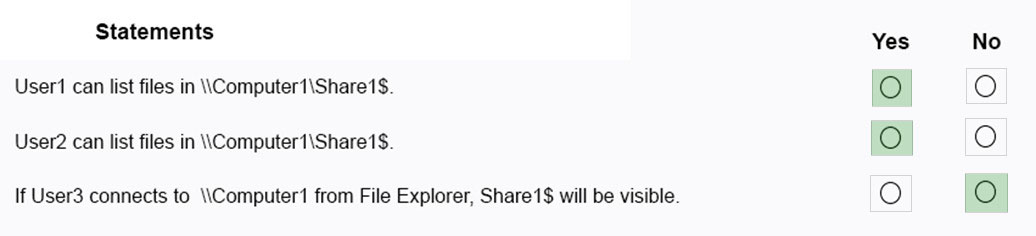
HOTSPOT - Your network contains an Active Directory domain. The domain contains the users shown in the following table.The domain contains a computer named Computer1 that runs Windows 10. Computer1 contains a folder named Folder1 that has the following permissions: ✑ User2: Deny Write ✑ Group1: Allow Read ✑ Group2: Allow Modify Folder1 is shared as Share1$. Share1$ has the following configurations: ✑ Everyone: Allow Full control ✑ Access-based enumeration: Enabled For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
Your network contains an Active Directory domain. The domain contains two computers named Computer1 and Computer2 that run Windows 10. You need to modify the registry of Computer1 by using Registry Editor from Computer2. Which two registry hives can you modify? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. HKEY_CURRENT_USER
B. HKEY_LOCAL_MACHINE
C. HKEY_USERS
D. HKEY_CLASSES_ROOT
E. HKEY_CURRENT_CONFIG
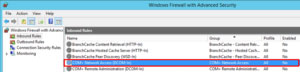
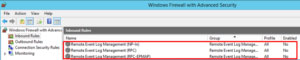
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have two computers named Computer1 and Computer2 that run Windows 10. You have an Azure Active Directory (Azure AD) user account named admin@contoso.com that is in the local Administrators group on each computer. You sign in to Computer1 by using admin@contoso.com . You need to ensure that you can use Event Viewer on Computer1 to connect to the event logs on Computer2. Solution: On Computer2, you enable the Remote Event Log Management inbound rule from Windows Defender Firewall. Does this meet the goal?
A. Yes
B. No
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a computer named Computer1 that runs Windows 10. You test Windows updates on Computer1 before you make the updates available to other computers. You install a quality update that conflicts with a custom device driver. You need to remove the update from Computer1. Solution: From System Restore, you revert the system state to a restore point that was created before the update was installed. Does this meet the goal?
A. Yes
B. No
Your network contains an Active Directory domain. The domain contains 10 computers that run Windows 10. On a different computer named Computer1, you plan to create a collector-initiated subscription to gather the event logs from the Windows 10 computers. You need to configure the environment to support the event log collection. Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Add Computer1 to the Event Log Readers group on the Windows 10 computers
B. Add Computer1 to the Event Log Readers group on Computer1
C. On the Windows 10 computers, change the Startup Type of Windows Event Collector to Automatic
D. Enable Windows Remote Management (WinRM) on the Windows 10 computers
E. Enable Windows Remote Management (WinRM) on Computer1
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have computers that run Windows 11 as shown in the following table.You ping 192.168.10.15 from Computer1 and discover that the request timed out. You need to ensure that you can successfully ping 192.168.10.15 from Computer1. Solution: On Computer1, you turn off Windows Defender Firewall. Does this meet the goal?
A. Yes
B. No
You have a Microsoft Azure Active Directory (Azure AD) tenant. Some users sign in to their computer by using Windows Hello for Business. A user named User1 purchases a new computer and joins the computer to Azure AD. User1 is not able to use Windows Hello for Business on his computer. User1 sign-in options are shown on the exhibit. (Click the Exhibit tab.)You open Device Manager and confirm that all the hardware works correctly. You need to ensure that User1 can use Windows Hello for Business facial recognition to sign in to the computer. What should you do first?
A. Purchase an infrared (IR) camera.
B. Upgrade the computer to Windows 10 Enterprise.
C. Enable UEFI Secure Boot.
D. Install a virtual TPM driver.
You have 10 computers that run Windows 10 and have BitLocker Drive Encryption (BitLocker) enabled. You plan to update the firmware of the computers. You need to ensure that you are not prompted for the BitLocker recovery key on the next restart. The drive must be protected by BitLocker on subsequent restarts. Which cmdlet should you run?
A. Unlock-BitLocker
B. Disable-BitLocker
C. Add-BitLockerKeyProtector
D. Suspend-BitLocker
You need to sign in as LocalAdmin on Computer11. What should you do first?
A. From the LAPS UI tool, view the administrator account password for the computer object of Computer11.
B. From Windows Configuration Designer, create a configuration package that sets the password of the LocalAdmin account on Computer11.
C. Use a Group Policy object (GPO) to set the local administrator password.
D. From Microsoft Intune, set the password of the LocalAdmin account on Computer11.
Which users can create a new group on Computer3?
A. User31 and User32 only
B. Admin1, User31, and User32 only
C. User31 only
D. Admin1 and User31 only
You have computers that run Windows 10. The computers are joined to an Azure Active Directory (Azure AD) tenant and enrolled in Microsoft Intune. You need to recommend a solution for help desk administrators that meets the following requirements: ✑ The administrators must assist users remotely by connecting to each user's computer. ✑ The remote connections must be initiated by the administrators. The users must approve the connection. ✑ Both the users and the administrators must be able to see the screen of the users' computer. ✑ The administrators must be able to make changes that require running applications as a member of each computer's Administrators group. Which tool should you include in the recommendation?
A. Remote Desktop
B. Intune
C. Remote Assistance
D. Quick Assist
You have a computer named Client' that runs Windows 11. You perform the following actions on Client1: ✑ Enable Hyper-V. Create a virtual machine that runs Windows 11 Pro.You need to connect to VM1 by using enhanced session mode. What should you do first?
A. Enable Remote Desktop on VM1.
B. Enable Remote Assistance on Client1.
C. Enable Remote Assistance on VM1.
D. Enable Remote Desktop on Client1.
SIMULATION - Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time. When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design. Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task. Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided. Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab. Username and password -Use the following login credentials as needed: To enter your password, place your cursor in the Enter password box and click on the password below. Username: Contoso/Administrator - Password: Passw0rd! The following information is for technical support purposes only: Lab Instance: 11145882 -
Administrators report that they cannot use Event Viewer to remotely view the event logs on Client3. You need to ensure that the administrators can access the event logs remotely on Client3. The solution must ensure that Windows Firewall remains enabled. To complete this task, sign in to the required computer or computers.
You have a computer that runs Windows 10. You can start the computer but cannot sign in. You need to start the computer into the Windows Recovery Environment (WinRE). What should you do?
A. Turn off the computer. Turn on the computer, and then press F8.
B. Turn off the computer. Turn on the computer, and then press F10.
C. From the sign-in screen, hold the Shift key, and then click Restart.
D. Hold Alt+Ctrl+Delete for 10 seconds.
You have a Windows 10 device. You need to enable an experimental feature in Microsoft Edge. What should you enter in the address bar?
A. edge://flags
B. edge://components
C. edge://management
D. edge://extensions
You need to recommend a solution to configure the employee VPN connections. What should you include in the recommendation?
A. Remote Access Management Console
B. Group Policy Management Console (GPMC)
C. Connection Manager Administration Kit (CMAK)
D. Microsoft Intune
You have a computer that runs Windows 10 and has File History enabled. File History is configured to save copies of files every 15 minutes. At 07:55, you create a file named D:Folder1File1.docx. You add D:Folder1 to File History and manually run File History at 08:00. You modify File1.docx at the following times: ✑ 08:05 ✑ 08:12 08:20✑ 08:24 ✑ 08:50 At 08:55, you attempt to restore File1.docx. How many previous versions of File1.docx will be available to restore?
A. 2
B. 3
C. 4
D. 5
Free Access Full MD-100 Practice Test Free Questions
If you’re looking for more MD-100 practice test free questions, click here to access the full MD-100 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your MD-100 certification journey!