MD-100 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your MD-100 certification? Our MD-100 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an MD-100 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our MD-100 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
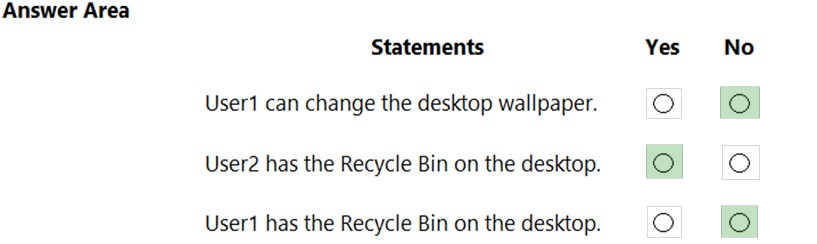
HOTSPOT -
You implement the planned changes for Computer1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
HOTSPOT -
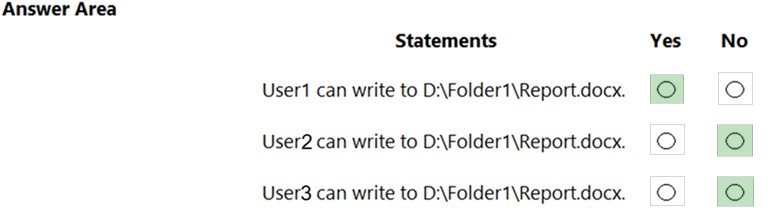
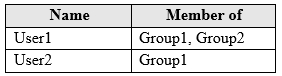
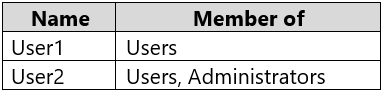
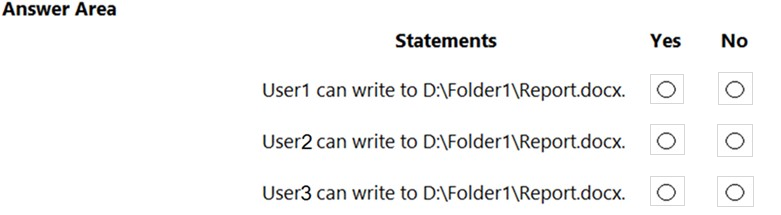
You have a computer named Computer1 that runs Windows 10. Computer1 is in a workgroup.
Computer1 contains the local users shown in the following table.
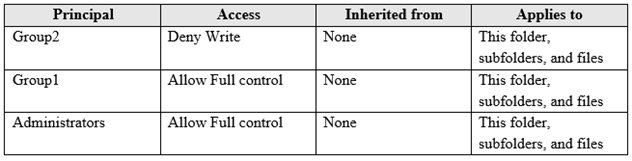
You create a folder named Folder1 that has the permissions shown in the following table.
You create a file named File1.txt in Folder1 and allow Group2 Full control permissions to File1.txt.
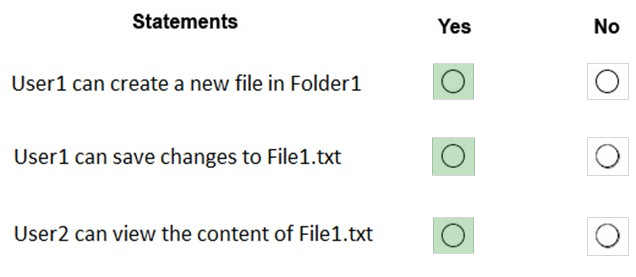
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
SIMULATION -
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab.
But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
Username and password -
Use the following login credentials as needed:
To enter your password, place your cursor in the Enter password box and click on the password below.
Username: Contoso/Administrator -
Password: Passw0rd!
The following information is for technical support purposes only:
Lab Instance: 11145882 -
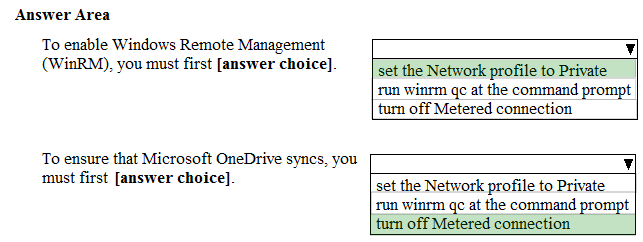
You have already prepared Client1 for remote management.
You need to forward all events from the Application event log on Client1 to DC1.
To complete this task, sign in to the required computer or computers.
HOTSPOT -
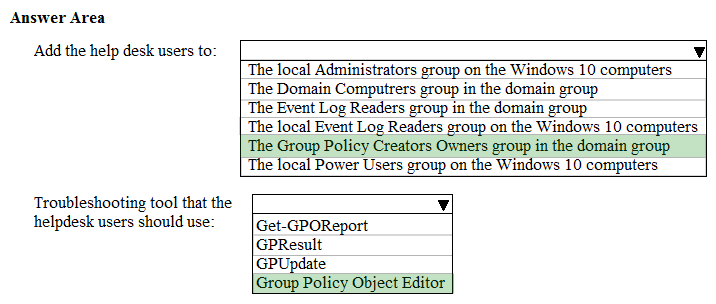
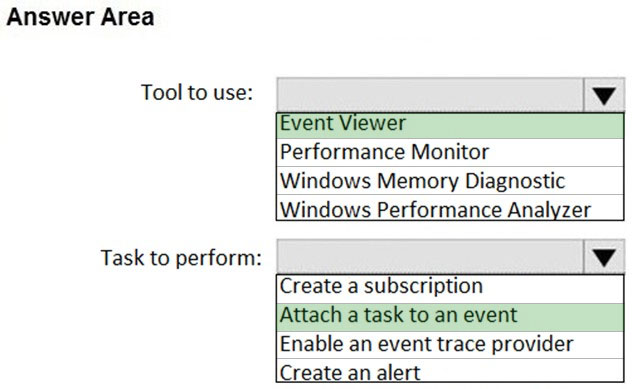
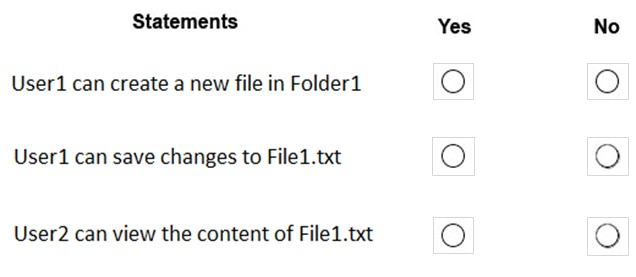
You need to meet the technical requirements for the helpdesk users.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
HOTSPOT
-
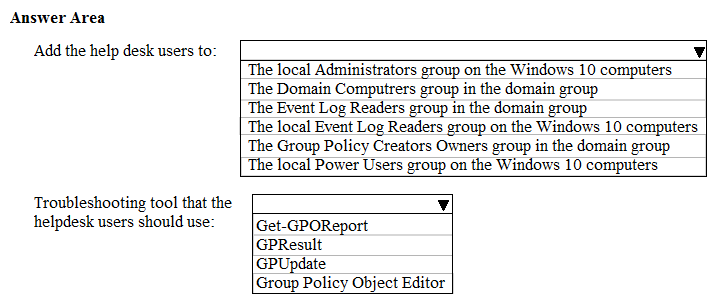
You have a computer that runs Windows 10 and contains a user named User1.
You need to ensure that User1 can add a third-party driver package for a printer to the driver store of the computer. The solution must use the principle of the least privilege.
To which local group should you add User1, and what should User1 run? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

SIMULATION -
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab.
But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
Username and password -
Use the following login credentials as needed:
To enter your password, place your cursor in the Enter password box and click on the password below.
Username: Contoso/Administrator -
Password: Passw0rd!
The following information is for technical support purposes only:
Lab Instance: 10921597 -
You need to ensure that a local user named User1 can establish a Remote Desktop connection to Client2.
To complete this task, sign in to the required computer or computers.
You have a Microsoft 365 tenant that contains 70 remote users.
The remote users work from various locations.
Recently, each remote user purchased a personal computer that runs Windows 10 Home.
You need to configure the VPN settings on the computers automatically by using the least amount of administrative effort.
What should you use?A. an unattend answer file
B. a Group Policy Object (GPO)
C. Windows Autopilot
D. a provisioning package
HOTSPOT -
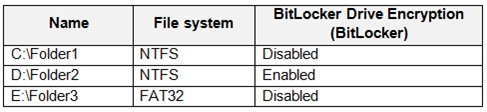
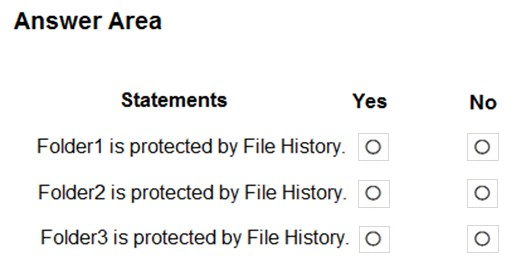
You have a computer named Computer1 that runs Windows 10.
Computer1 contains the folders shown in the following table.
You include Folder1, Folder2, and Folder3 in the Documents library.
You configure File History to run every 15 minutes, and then turn on File History.
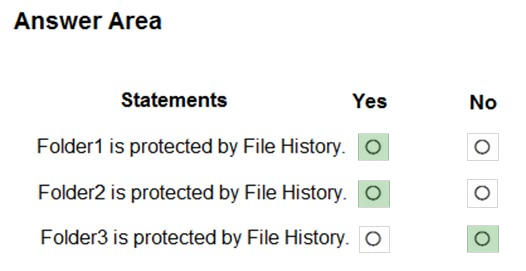
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
An employee reports that she must perform a BitLocker recovery on her laptop. The employee does not have her BitLocker recovery key but does have a
Windows 10 desktop computer.
What should you instruct the employee to do from the desktop computer?A. Run the manage-bde.exe ג€"status command
B. From BitLocker Recovery Password Viewer, view the computer object of the laptop
C. Go to https://aad.portal.azure.com and view the object of the laptop
D. Run the Enable-BitLockerAutoUnlock cmdlet
You customize the Start menu on a computer that runs Windows 10 as shown in the following exhibit.
You need to add Remote Desktop Connection to Group1 and remove Group3 from the Start menu.
Which two actions should you perform from the Start menu customizations? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.A. Unlock Group1.
B. Remove Command Prompt from Group1.
C. Delete Group3.
D. Add Remote Desktop Connection to Group1.
E. Rename Group3 as Group1.
SIMULATION -
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab.
But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
Username and password -
Use the following login credentials as needed:
To enter your password, place your cursor in the Enter password box and click on the password below.
Username: Contoso/Administrator -
Password: Passw0rd!
The following information is for technical support purposes only:
Lab Instance: 10921597 -
You need to create a user account named User5 on Client2. The solution must meet the following requirements:
✑ Prevent User5 from changing the password of the account.
✑ Ensure that User5 can perform backups.
✑ Use the principle of least privilege.
To complete this task, sign in to the required computer or computers.
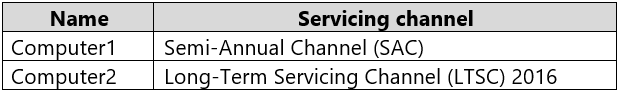
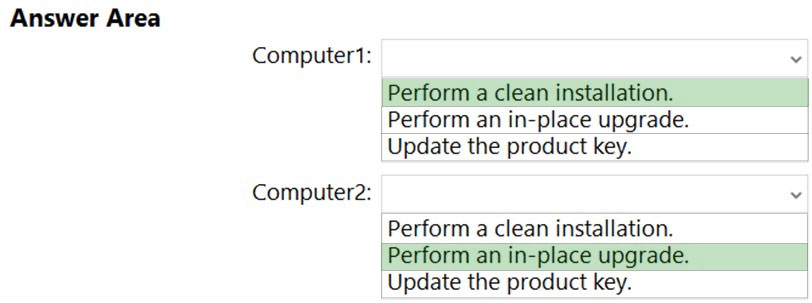
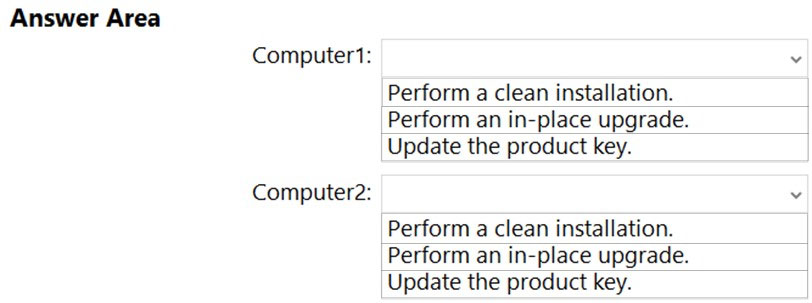
HOTSPOT -
You have computers that run Windows 10 Enterprise as shown in the following table.
Both computers have applications installed and contain user data.
You plan to configure both computers to run Windows 10 Enterprise LTSC 2019 and to retain all the existing applications and data.
You need to recommend a method to deploy Windows 10 Enterprise LTSC 2019 to the computers. The solution must minimize effort to install and configure the applications.
What should you include in the recommendation for each computer? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
DRAG DROP
-
Your network contains an Active Directory domain named contoso.com. The domain contains the objects shown in the following table.
BitLocker Drive Encryption (BitLocker) recovery passwords are stored in Active Directory.
User1 enables the following on Computer1:
• BitLocker on drive C
• BitLocker on a removable drive named E
Which object stores the BitLocker recovery passwords for each drive? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

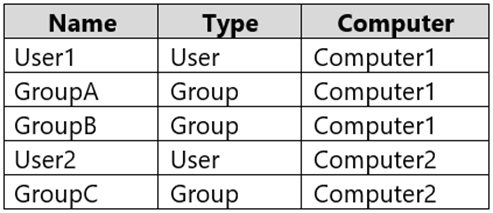
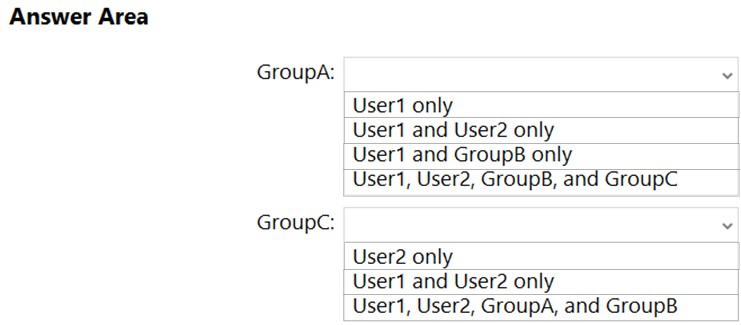
HOTSPOT -
You have two workgroup computers named Computer1 and Computer2 that run Windows 10. The computers contain the local security principals shown in the following table.
Which security principals can be members of GroupA and GroupC? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
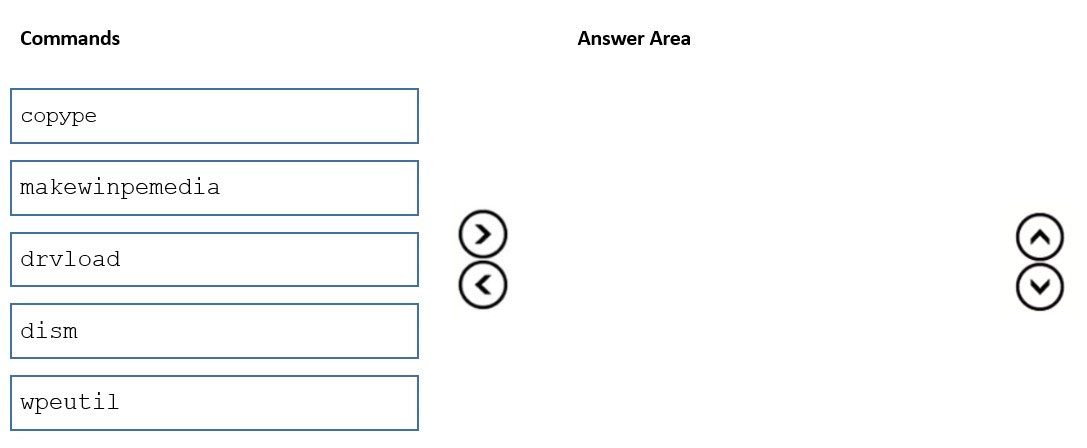
DRAG DROP -
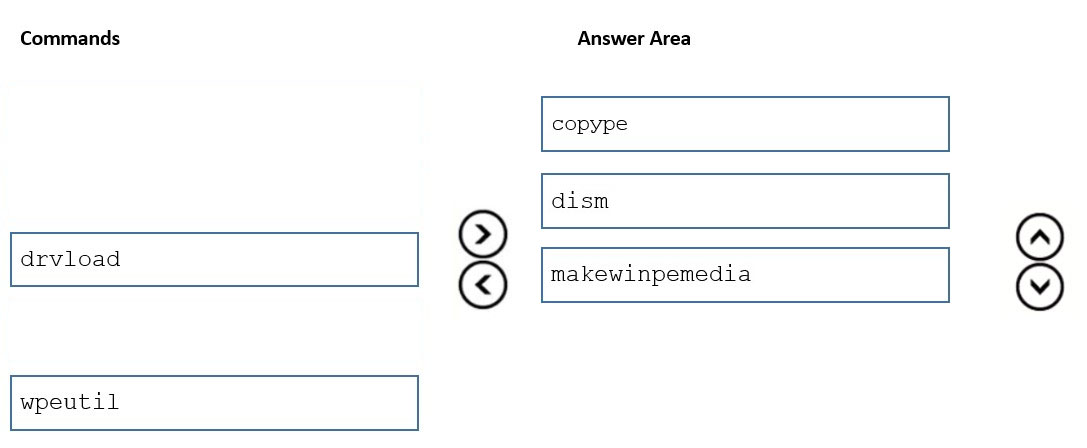
You have a Windows 10 image that was updated to the latest version of Windows 10.
You plan to create a new WinPE bootable ISO file.
You obtain the latest WinPE source files.
You need to create the new ISO file to support PowerShell scripting.
Which three commands should you run in sequence? To answer, move the appropriate commands from the list of commands to the answer area and arrange them in the correct order.
Select and Place:
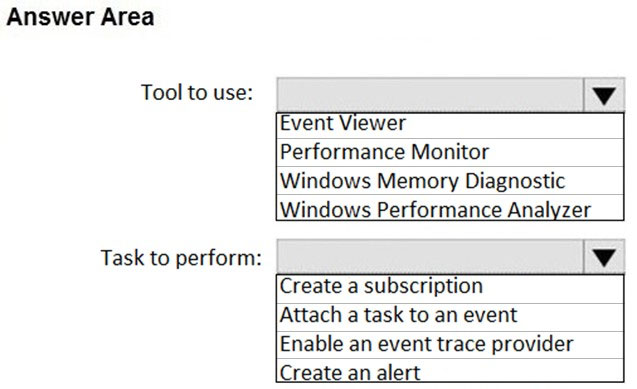
HOTSPOT -
You need to reduce the amount of time it takes to restart Application1 when the application crashes.
What should you include in the solution? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
You have a computer named Computer1 that runs Windows 10. Computer1 contains a folder named Folder1.
You need to log any users who take ownership of the files in Folder1.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.A. Modify the folder attributes of Folder1.
B. Modify the Advanced Security Settings for Folder1.
C. From a Group Policy object (GPO), configure the Audit Sensitive Privilege Use setting.
D. From a Group Policy object (GPO), configure the Audit File System setting.
E. Install the Remote Server Administration Tools (RSAT).
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer that runs Windows 10. The computer contains a folder named D:Scripts. D:Scripts contains several PowerShell scripts.
You need to ensure that you can run the PowerShell scripts without specifying the full path to the scripts. The solution must persist between PowerShell sessions.
Solution: From PowerShell, you run $env:Path += ";d:scripts".
Does this meet the goal?A. Yes
B. No
You have a public computer named Public1 that runs Windows 10.
Users use Public1 to browse the internet by using Microsoft Edge.
You need to view events associated with website phishing attacks on Public1.
Which Event Viewer log should you view?A. Applications and Services Logs > Microsoft > Windows > SmartScreen > Debug
B. Applications and Services Logs > Microsoft > Windows > Security-Mitigations > User Mode
C. Applications and Services Logs > Microsoft > Windows > Windows Defender > Operational
D. Applications and Services Logs > Microsoft > Windows > DeviceGuard > Operational
SIMULATION -
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab.
But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
Username and password -
Use the following login credentials as needed:
To enter your password, place your cursor in the Enter password box and click on the password below.
Username: Contoso/Administrator -
Password: Passw0rd!
The following information is for technical support purposes only:
Lab Instance: 11145882 -
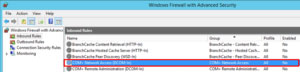
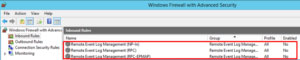
Administrators report that they cannot use Event Viewer to remotely view the event logs on Client3.
You need to ensure that the administrators can access the event logs remotely on Client3. The solution must ensure that Windows Firewall remains enabled.
To complete this task, sign in to the required computer or computers.
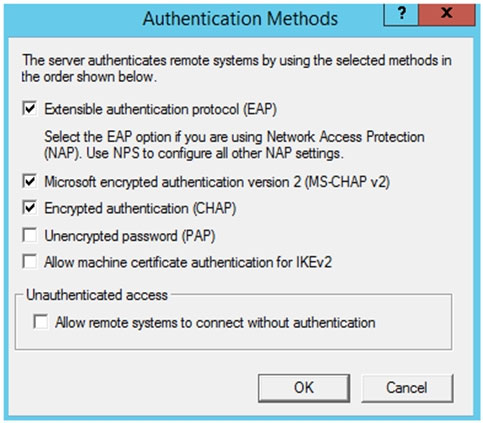
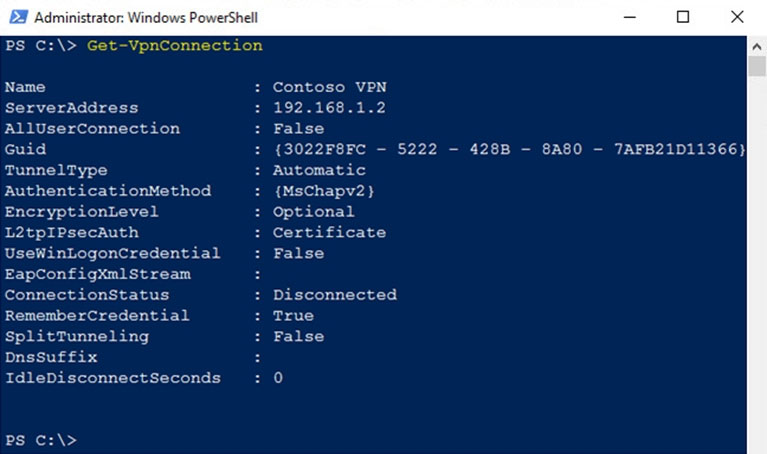
You have a VPN server that accepts PPTP and L2TP connections and is configured as shown in the following exhibit.
A user named User1 has a computer that runs Windows 10 and has a VPN connection configured as shown in the following exhibit.
User1 fails to establish a VPN connection when connected to a home network.
You need to identify which VPN client setting must be modified.
What should you identify?A. ServerAddress
B. TunnelType
C. AuthenticationMethod
D. L2tpIPsecAuth
E. EncryptionLevel
You have a computer named Computer1 that runs Windows 11 and hosts two Hyper-V virtual machines named VM1 and VM2.
You need to ensure that VM1 can connect to the network shares on VM2. The solution must prevent Computer1 from establishing network connections to VM1 or VM2.
Which type of virtual switch should you use?A. external
B. private
C. internal
HOTSPOT -
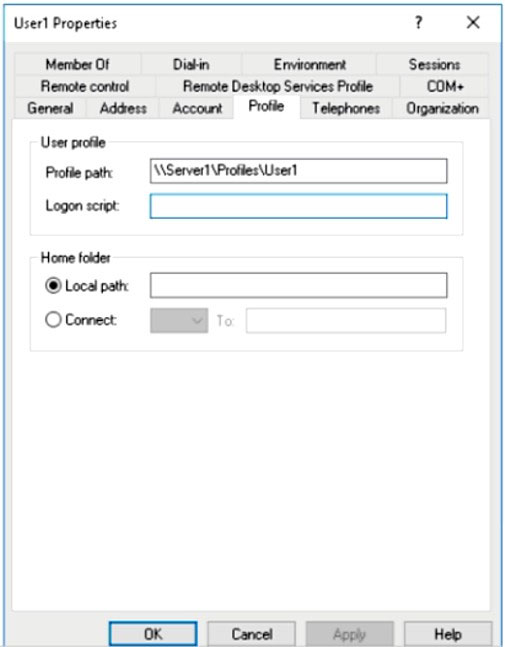
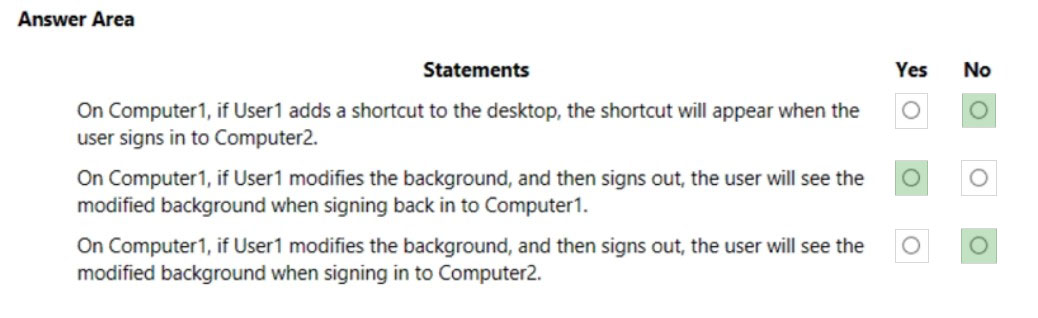
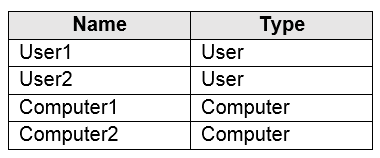
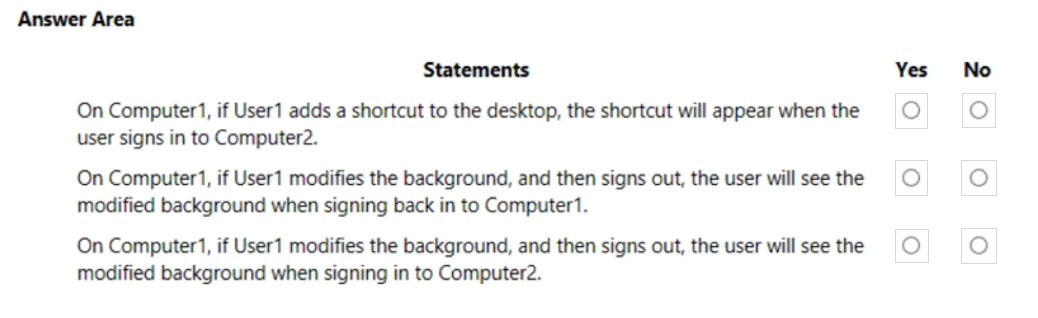
Your network contains an on-premises Active Directory forest named contoso.com. The forest contains a user named User1 and two computers named
Computer1 and Computer2 that run Windows 10.
User1 is configured as shown in the following exhibit.
You rename file Server1ProfilesUser1.V6NTUSER.DAT as NTUSER.MAN.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
You have a workgroup computer that runs Windows 10.
You need to set the minimum password length to 12 characters.
What should you use?A. Local Group Policy Editor
B. User Accounts in Control Panel
C. System Protection in System Properties
D. Sign-in options in the Settings app
You have a computer that is configured as shown in the following exhibit.
What can the computer connect to?A. all the local computers and the remote computers within your corporate network only
B. all the local computers and the remote computers, including Internet hosts
C. only other computers on the same network segment that have automatic private IP addressing (APIPA)
D. only other computers on the same network segment that have an address from a class A network ID
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains a user named UserA.
You have two computers named Computer1 and Computer2 that run Windows 10 and are joined to contoso.com.
You need to ensure that UserA can connect to Computer2 from Computer1 by using Remote Desktop.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.A. On Computer1, modify the registry.
B. On Computer2, modify the registry.
C. On Computer1, modify the properties of UserA.
D. On Computer1, enable Remote Desktop.
E. On Computer2, modify the properties of UserA.
F. On Computer 2, enable Remote Desktop.
G. On Computer2, add the Everyone group to the Remote Desktop Users group.
H. On Computer1, add the Everyone group to the Remote Desktop Users group.
DRAG DROP -
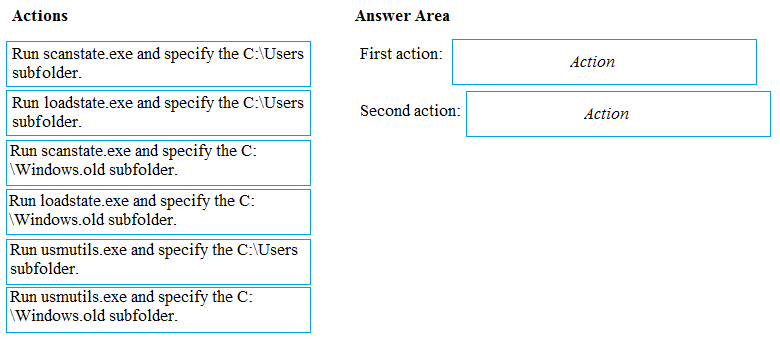
You have a computer named Computer1 that runs Windows 8.1. Computer1 has a local user named User1 who has a customized profile.
On Computer1, you perform a clean installation of Windows 10 without formatting the drives.
You need to migrate the settings of User1 from Windows 8.1 to Windows 10.
Which two actions should you perform? To answer, drag the appropriate actions to the correct targets. Each action may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
You install Windows 10 Pro on a computer named CLIENT1 and join the device to an Active Directory domain.
You need to ensure that all per-user services are disabled on CLIENT1. The solution must minimize administrative effort.
What should you use?A. a Group Policy administrative template
B. the sfc command
C. Services
D. Group Policy preferences
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You deploy Windows 10 to a computer named Computer1.
Computer1 contains a folder named C:Folder1. Folder1 contains multiple documents.
You need to ensure that you can recover the files in Folder1 by using the Previous Versions tab.
Solution: You select Folder is ready for archiving from the properties of Folder1.
Does this meet the goal?A. Yes
B. No
You have a computer named Computer1 that runs Windows 10.
Computer1 has a folder named C:Folder1.
You need to meet the following requirements:
✑ Log users that access C:Folder1.
✑ Log users that modify and delete files in C:Folder1.
Which two actions should you perform?A. From the properties of C:Folder1, configure the Auditing settings.
B. From the properties of C:Folder1, select the Encryption contents to secure data option.
C. From the Audit Policy in the local Group Policy, configure Audit directory service access.
D. From the Audit Policy in the local Group Policy, you configure Audit object access.
E. From the Audit Policy in the local Group Policy, you configure Audit system events.
You have a Windows 10 device that has two local users named User1 and User2.
User1 performs the tasks shown in the following table.
The results of which tasks will be visible when User2 signs in to the device?A. Task3 only
B. Task2 and Task3 only
C. Task3 and Task4 only
D. Task2, Task3, and Task4 only
E. Task1, Task2, Task3, and Task4
A user has a computer that runs Windows 10. The user has access to the following storage locations:
✑ A USB flash drive
✑ Microsoft OneDrive
✑ OneDrive for Business
✑ A drive mapped to a network share
✑ A secondary partition on the system drive
You need to configure Back up using File History from the Settings app.
Which two storage locations can you select for storing File History data? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.A. OneDrive for Business
B. OneDrive
C. the USB flash drive
D. the secondary partition on the system drive
E. the drive mapped to a network share
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer that runs Windows 10. The computer contains a folder named D:Scripts. D:Scripts contains several PowerShell scripts.
You need to ensure that you can run the PowerShell scripts without specifying the full path to the scripts. The solution must persist between PowerShell sessions.
Solution: From System Properties, you add D:Scripts to the PATH environment variable.
Does this meet the goal?A. Yes
B. No
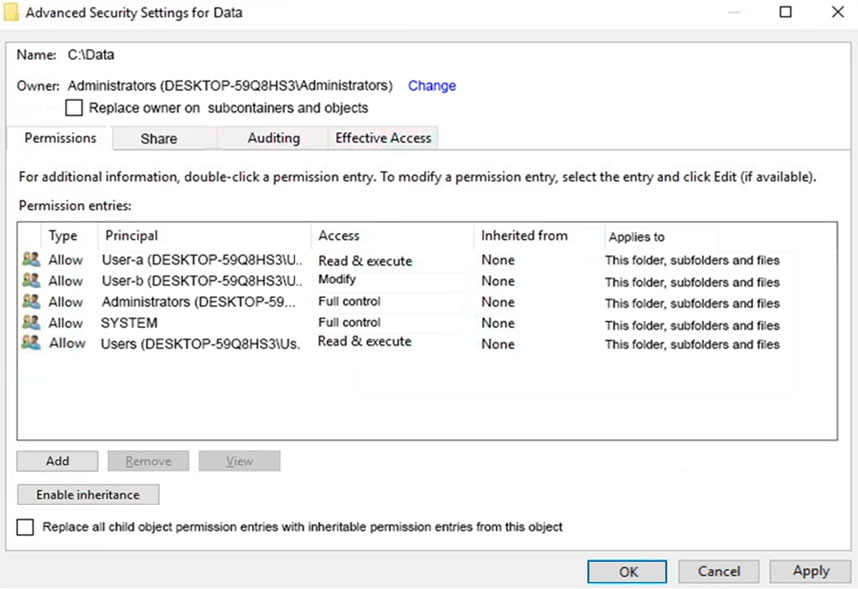
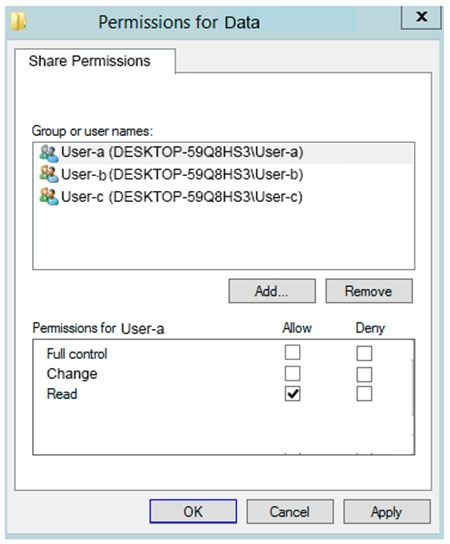
HOTSPOT -
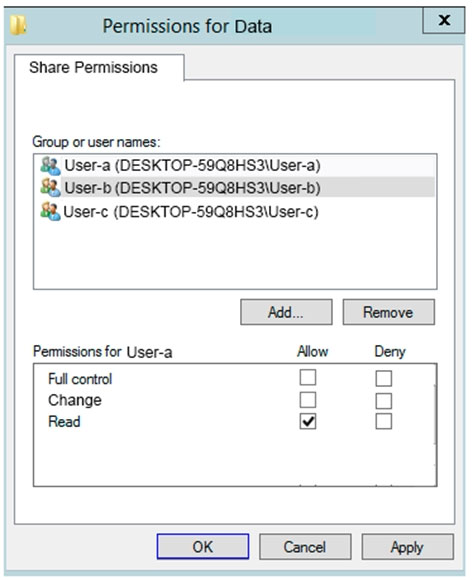
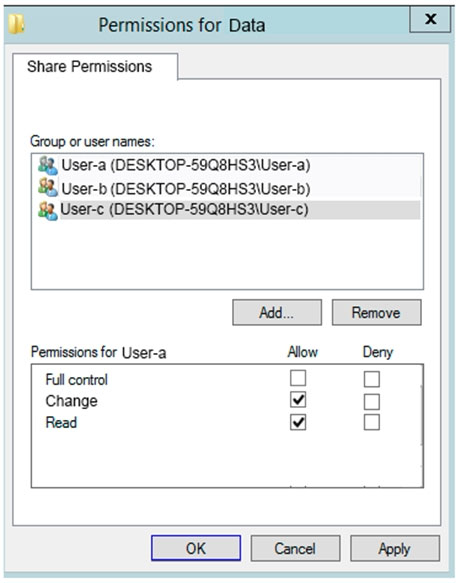
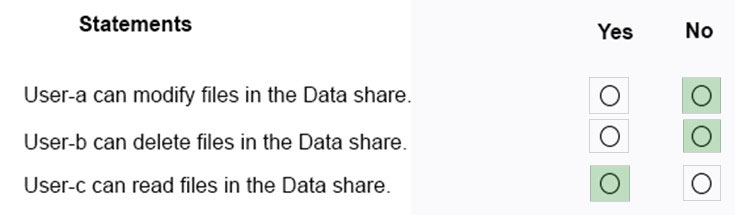
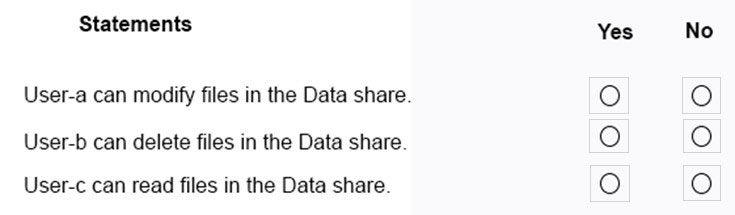
You have a computer named Computer5 that runs Windows 10 that is used to share documents in a workgroup.
You create three users named User-a, User-b, and User-c by using Computer Management. The users plan to access Computer5 from the network only.
You have a folder named Data. The Advanced Security Settings for the Data folder are shown in the Security exhibit. (Click the Security tab).
You share the Data folder. The permissions for User-a are shown in the User-a exhibit (Click the User-a tab.)
The permissions for User-b are shown in the User-b exhibit. (Click the User-b tab.)
The permissions for User-c are shown in the User-c exhibit. (Click the User-c tab.)
For each of the following statements, select Yes if the statements is true. Otherwise, select No.
NOTE: Reach correct selection is worth one point.
Hot Area:
Your network contains an Active Directory domain. The domain contains a computer named Computer1 that runs Windows 10.
Computer1 has a Trusted Platform Module (TPM) version 1.2.
The domain contains a domain controller named DC1 that has all the Remote Server Administration Tools (RSAT) installed.
BitLocker Drive Encryption (BitLocker) recovery passwords are stored in Active Directory.
You enable BitLocker on the operating system drive of Computer1.
A software update on Computer1 disables the TPM, and BitLocker enters recovery mode.
You need to recover your BitLocker password for Computer1.
What should you use to retrieve the recovery password?A. Disk Management
B. manage ג€"bde with the ג€"unlock parameter
C. Active Directory Users and Computers
D. repair-bde with the ג€"f parameter
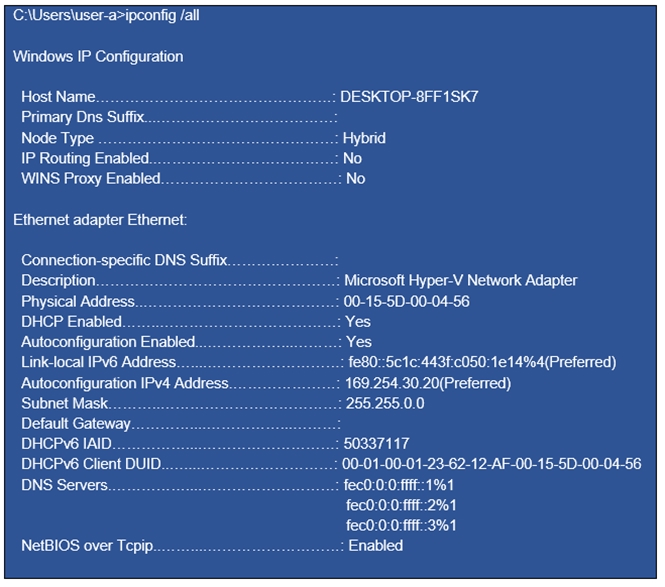
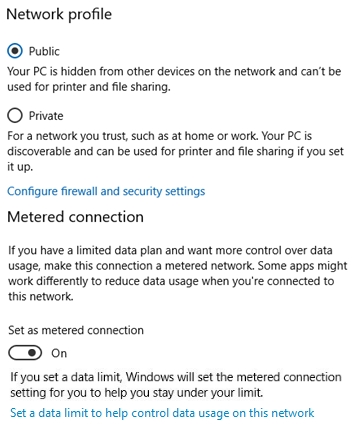
HOTSPOT -
You have a computer that runs Windows 10.
From the Settings app, you view the connection properties shown in the following exhibit.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Hot Area:

After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a laptop named Computer1 that runs Windows 10.
When in range, Computer1 connects automatically to a Wi-Fi network named Wireless1.
You need to prevent Computer1 from automatically connecting to Wireless1.
Solution: From the Services console, you disable the Link-Layer Topology Discovery Mapper service.
Does this meet the goal?A. Yes
B. No
Your company has a main office and a branch office. The offices connect to each other by using a WAN link. Access to the Internet is provided through the main office.
The branch office contains 25 computers that run Windows 10. The computers contain small hard drives that have very little free disk space.
You need to prevent the computers in the branch office from downloading updates from peers on the network.
What should you do?A. From the Settings app, modify the Delivery Optimizations settings.
B. Configure the network connections as metered connections.
C. Configure the computers to use BranchCache in hosted cache mode.
D. Configure the updates to use the Semi-Annual Channel (Targeted) channel.
You have a computer that runs Windows 10 Home.
You need to upgrade the computer to Windows 10 Enterprise as quickly as possible. The solution must retain the user settings.
What should you do first?A. Run the scanstate command.
B. Perform an in-place upgrade to Windows Pro.
C. Install the latest feature updates.
D. Run the sysprep command.
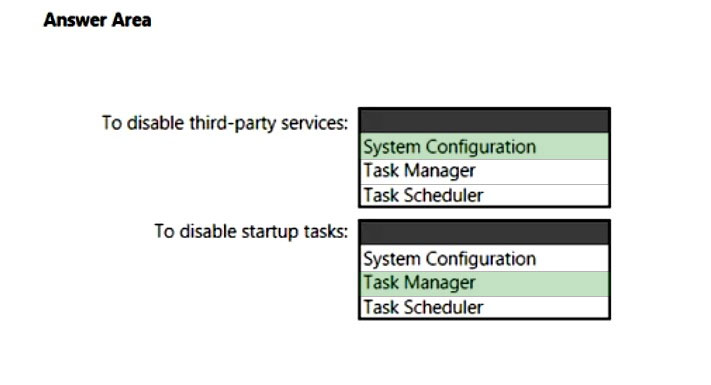
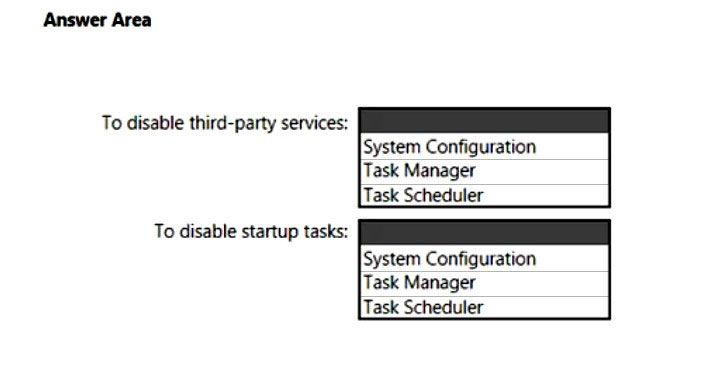
HOTSPOT -
You are troubleshooting a Windows 10 update that fails to install.
You need to start Windows 10 with non-essential, third-party services disabled and all startup tasks disabled. The solution must minimize administrative effort to disable the services and tasks.
What should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
HOTSPOT -
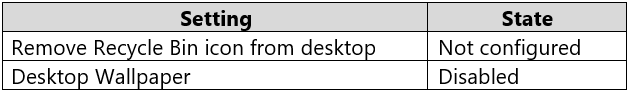
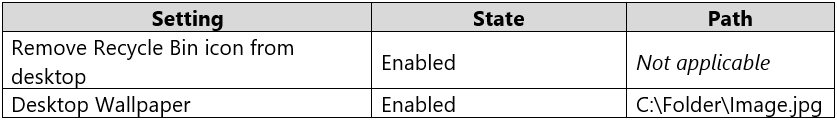
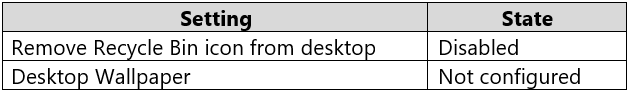
You have a workgroup computer named Computer1 that runs Windows 10 and has the users shown in the following table.
[1]
Computer1 has the Local ComputerAdministrators Policy shown in the following table.
Computer1 has the Local ComputerNon-Administrators Policy shown in the following table.
Computer1 has the local computer policy shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
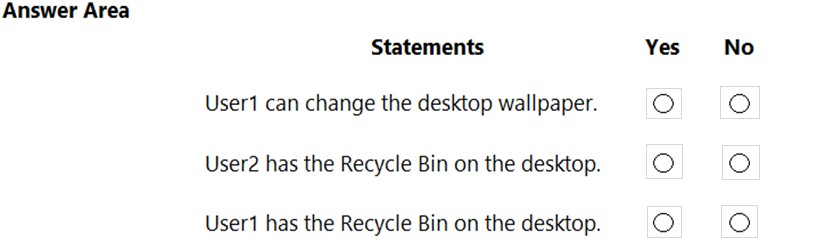
HOTSPOT
-
You have a Windows 10 device.
You need to ensure that only priority notifications are displayed during business hours.
Which settings in the Settings app should you configure, and where will standard notifications be sent during business hours? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Your network contains an Active Directory domain. The domain contains the objects shown in the following table.
The domain is configured to store BitLocker Drive Encryption (BitLocker) recovery passwords.
User1 encrypts an external disk on Computer1 by using BitLocker to Go.
User2 moves the external disk to Computer2 and unlocks the disk.
You need to view the BitLocker recovery password.
Which objects are used to store the recovery password?A. Computer1 and Computer2 only
B. User1 only
C. Computer1 only
D. User1 and Computer1 only
E. User1 and User2 only
Your network contains an Active Directory domain. The domain contains computers that run Windows 10.
You must ensure that Windows BitLocker Drive Encryption is enabled on all client computers, even though a Trusted Platform Module (TPM) chip is installed in only some of them.
You need to accomplish this goal by using one Group Policy object (GPO).
What should you do?A. Enable the Allow enhanced PINs for startup policy setting, and select the Allow BitLocker without a compatible TPM check box.
B. Enable the Enable use of BitLocker authentication requiring preboot keyboard input on slates policy setting, and select the Allow BitLocker without a compatible TPM check box.
C. Enable the Require additional authentication at startup policy setting, and select the Allow BitLocker without a compatible TPM check box.
D. Enable the Control use of BitLocker on removable drives policy setting, and select the Allow BitLocker without a compatible TPM check box.
You have a computer named Computer1 that runs Windows 10.
You need to prevent standard users from changing the wireless network settings on Computer1. The solution must allow administrators to modify the wireless network settings.
What should you use?A. Windows Configuration Designer
B. MSConfig
C. Local Group Policy Editor
D. an MMC console that has the Group Policy Object Editor snap-in
You have a computer named Computer1 that has the following configurations:
• RAM: 4 GB
• CPU: 1.6 GHz
• Hard drive: 128 GB
• Operating system: Windows 10 Pro in S mode
You need to upgrade Computer1 to Windows 11.
What should you do first?A. Increase the amount of RAM.
B. Increase the storage capacity of the hard drive.
C. Switch out of S mode.
D. Upgrade the CPU.
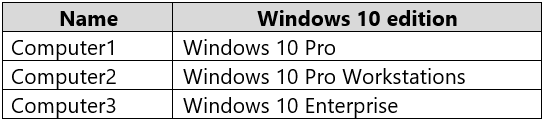
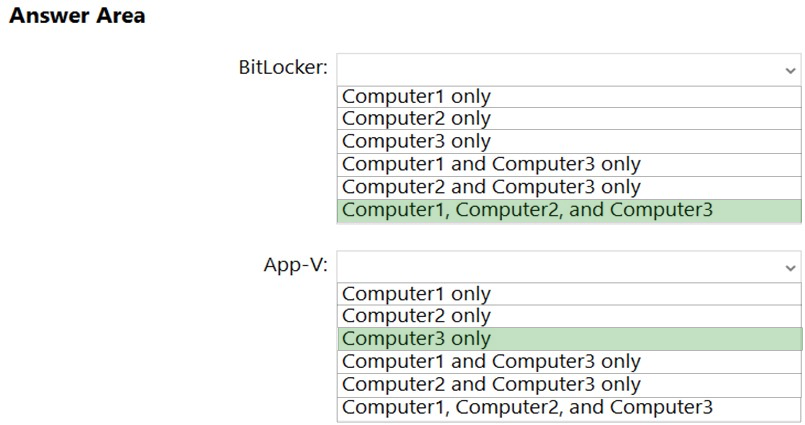
HOTSPOT -
You have the computers shown in the following table.
You need to identify which computers support the features.
✑ BitLocker Drive Encryption (BitLocker)
✑ Microsoft Application Virtualization (App-V)
Which computers support the features? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
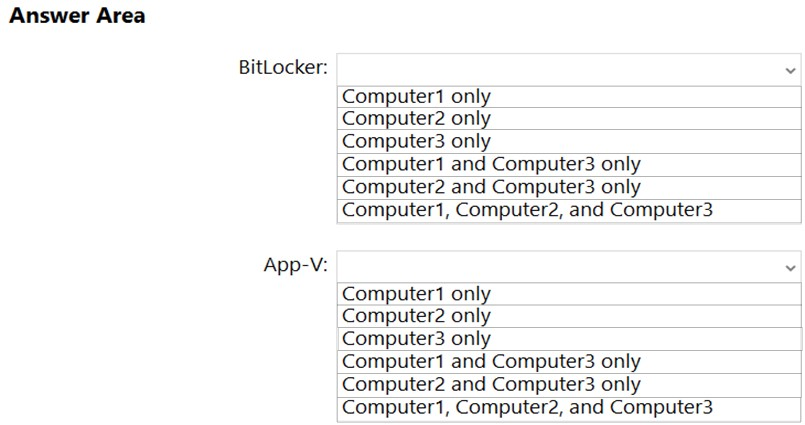
Your network contains an Active Directory domain named contoso.com.
A user named User1 has a personal computer named Computer1 that runs Windows 10 Pro. User1 has a VPN connection to the corporate network.
You need to ensure that when User1 connects to the VPN, network traffic uses a proxy server located in the corporate network. The solution must ensure that
User1 can access the Internet when disconnected from the VPN.
What should you do?A. From Control Panel, modify the Windows Defender Firewall settings
B. From the Settings app, modify the Proxy settings for the local computer
C. From Control Panel, modify the properties of the VPN connection
D. From the Settings app, modify the properties of the VPN connection
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer that runs Windows 10. The computer contains a folder. The folder contains sensitive data.
You need to log which user reads the contents of the folder and modifies and deletes files in the folder.
Solution: From the properties of the folder, you configure the Auditing settings and from the Audit Policy in the local Group Policy, you configure Audit directory service access.
Does this meet the goal?A. Yes
B. No
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer that runs Windows 10. The computer contains a folder named D:Scripts. D:Scripts contains several PowerShell scripts.
You need to ensure that you can run the PowerShell scripts without specifying the full path to the scripts. The solution must persist between PowerShell sessions.
Solution: From a command prompt, you run set.exe PATHEXT=d:scripts.
Does this meet the goal?A. Yes
B. No
Access Full MD-100 Dump Free
Looking for even more practice questions? Click here to access the complete MD-100 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our MD-100 dump free questions — and get one step closer to exam success!