Google Professional Cloud Security Engineer Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the Google Professional Cloud Security Engineer certification? Our Google Professional Cloud Security Engineer Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective Google Professional Cloud Security Engineer exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic Google Professional Cloud Security Engineer Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
You are developing a new application that uses exclusively Compute Engine VMs. Once a day, this application will execute five different batch jobs. Each of the batch jobs requires a dedicated set of permissions on Google Cloud resources outside of your application. You need to design a secure access concept for the batch jobs that adheres to the least-privilege principle. What should you do?
A. 1. Create a general service account “g-sa” to orchestrate the batch jobs.2. Create one service account per batch job ‘b-sa-[1-5]’. Grant only the permissions required to run the individual batch jobs to the service accounts and generate service account keys for each of these service accounts.3. Store the service account keys in Secret Manager. Grant g-sa access to Secret Manager and run the batch jobs with the permissions of b-sa-[1-5].
B. 1. Create a general service account “g-sa” to execute the batch jobs.2. Grant the permissions required to execute the batch jobs to g-sa.3. Execute the batch jobs with the permissions granted to g-sa.
C. 1. Create a workload identity pool and configure workload identity pool providers for each batch job.2. Assign the workload identity user role to each of the identities configured in the providers.3. Create one service account per batch job “b-sa-[1-5]”, and grant only the permissions required to run the individual batch jobs to the service accounts.4. Generate credential configuration files for each of the providers. Use these files to execute the batch jobs with the permissions of b-sa-[1-5].
D. 1. Create a general service account “g-sa” to orchestrate the batch jobs.2. Create one service account per batch job “b-sa-[1-5]”, and grant only the permissions required to run the individual batch jobs to the service accounts.3. Grant the Service Account Token Creator role to g-sa. Use g-sa to obtain short-lived access tokens for b-sa-[1-5] and to execute the batch jobs with the permissions of b-sa-[1-5].
An organization adopts Google Cloud Platform (GCP) for application hosting services and needs guidance on setting up password requirements for their Cloud Identity account. The organization has a password policy requirement that corporate employee passwords must have a minimum number of characters. Which Cloud Identity password guidelines can the organization use to inform their new requirements?
A. Set the minimum length for passwords to be 8 characters.
B. Set the minimum length for passwords to be 10 characters.
C. Set the minimum length for passwords to be 12 characters.
D. Set the minimum length for passwords to be 6 characters.
A customer wants to run a batch processing system on VMs and store the output files in a Cloud Storage bucket. The networking and security teams have decided that no VMs may reach the public internet. How should this be accomplished?
A. Create a firewall rule to block internet traffic from the VM.
B. Provision a NAT Gateway to access the Cloud Storage API endpoint.
C. Enable Private Google Access.
D. Mount a Cloud Storage bucket as a local filesystem on every VM.
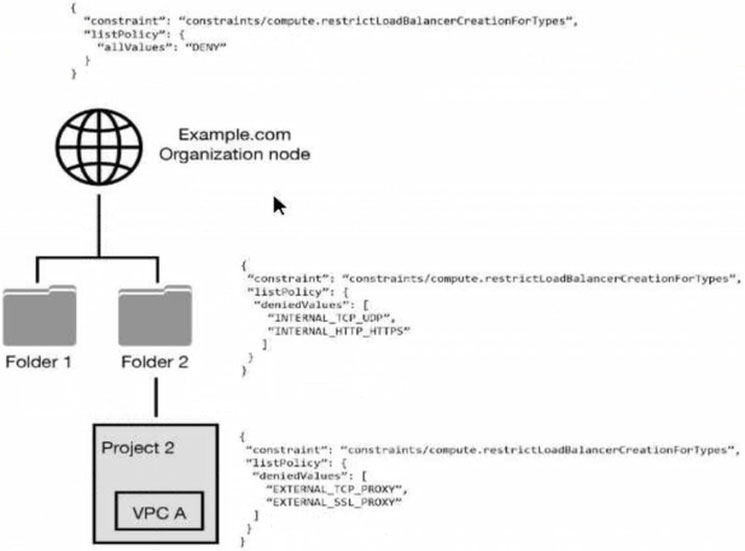
You have the following resource hierarchy. There is an organization policy at each node in the hierarchy as shown. Which load balancer types are denied in VPC
A. All load balancer types are denied in accordance with the global node’s policy.
B. INTERNAL_TCP_UDP, INTERNAL_HTTP_HTTPS is denied in accordance with the folder’s policy.
C. EXTERNAL_TCP_PROXY, EXTERNAL_SSL_PROXY are denied in accordance with the project’s policy.
D. EXTERNAL_TCP_PROXY, EXTERNAL_SSL_PROXY, INTERNAL_TCP_UDP, and INTERNAL_HTTP_HTTPS are denied in accordance with the folder and project’s policies.
Your company is storing sensitive data in Cloud Storage. You want a key generated on-premises to be used in the encryption process. What should you do?
A. Use the Cloud Key Management Service to manage a data encryption key (DEK).
B. Use the Cloud Key Management Service to manage a key encryption key (KEK).
C. Use customer-supplied encryption keys to manage the data encryption key (DEK).
D. Use customer-supplied encryption keys to manage the key encryption key (KEK).
Users are reporting an outage on your public-facing application that is hosted on Compute Engine. You suspect that a recent change to your firewall rules is responsible. You need to test whether your firewall rules are working properly. What should you do?
A. Enable Firewall Rules Logging on the latest rules that were changed. Use Logs Explorer to analyze whether the rules are working correctly.
B. Connect to a bastion host in your VPC. Use a network traffic analyzer to determine at which point your requests are being blocked.
C. In a pre-production environment, disable all firewall rules individually to determine which one is blocking user traffic.
D. Enable VPC Flow Logs in your VPC. Use Logs Explorer to analyze whether the rules are working correctly.
You're developing the incident response plan for your company. You need to define the access strategy that your DevOps team will use when reviewing and investigating a deployment issue in your Google Cloud environment. There are two main requirements: ✑ Least-privilege access must be enforced at all times. ✑ The DevOps team must be able to access the required resources only during the deployment issue. How should you grant access while following Google-recommended best practices?
A. Assign the Project Viewer Identity and Access Management (IAM) role to the DevOps team.
B. Create a custom IAM role with limited list/view permissions, and assign it to the DevOps team.
C. Create a service account, and grant it the Project Owner IAM role. Give the Service Account User Role on this service account to the DevOps team.
D. Create a service account, and grant it limited list/view permissions. Give the Service Account User Role on this service account to the DevOps team.
In a shared security responsibility model for IaaS, which two layers of the stack does the customer share responsibility for? (Choose two.)
A. Hardware
B. Network Security
C. Storage Encryption
D. Access Policies
E. Boot
Which international compliance standard provides guidelines for information security controls applicable to the provision and use of cloud services?
A. ISO 27001
B. ISO 27002
C. ISO 27017
D. ISO 27018
A customer has an analytics workload running on Compute Engine that should have limited internet access. Your team created an egress firewall rule to deny (priority 1000) all traffic to the internet. The Compute Engine instances now need to reach out to the public repository to get security updates. What should your team do?
A. Create an egress firewall rule to allow traffic to the CIDR range of the repository with a priority greater than 1000.
B. Create an egress firewall rule to allow traffic to the CIDR range of the repository with a priority less than 1000.
C. Create an egress firewall rule to allow traffic to the hostname of the repository with a priority greater than 1000.
D. Create an egress firewall rule to allow traffic to the hostname of the repository with a priority less than 1000.
Your organization wants to be General Data Protection Regulation (GDPR) compliant. You want to ensure that your DevOps teams can only create Google Cloud resources in the Europe regions. What should you do?
A. Use Identity-Aware Proxy (IAP) with Access Context Manager to restrict the location of Google Cloud resources.
B. Use the org policy constraint ‘Google Cloud Platform – Resource Location Restriction’ on your Google Cloud organization node.
C. Use the org policy constraint ‘Restrict Resource Service Usage’ on your Google Cloud organization node.
D. Use Identity and Access Management (IAM) custom roles to ensure that your DevOps team can only create resources in the Europe regions.
Your privacy team uses crypto-shredding (deleting encryption keys) as a strategy to delete personally identifiable information (PII). You need to implement this practice on Google Cloud while still utilizing the majority of the platform's services and minimizing operational overhead. What should you do?
A. Use client-side encryption before sending data to Google Cloud, and delete encryption keys on-premises.
B. Use Cloud External Key Manager to delete specific encryption keys.
C. Use customer-managed encryption keys to delete specific encryption keys.
D. Use Google default encryption to delete specific encryption keys.
You are deploying a web application hosted on Compute Engine. A business requirement mandates that application logs are preserved for 12 years and data is kept within European boundaries. You want to implement a storage solution that minimizes overhead and is cost-effective. What should you do?
A. Create a Cloud Storage bucket to store your logs in the EUROPE-WEST1 region. Modify your application code to ship logs directly to your bucket for increased efficiency.
B. Configure your Compute Engine instances to use the Google Cloud’s operations suite Cloud Logging agent to send application logs to a custom log bucket in the EUROPE-WEST1 region with a custom retention of 12 years.
C. Use a Pub/Sub topic to forward your application logs to a Cloud Storage bucket in the EUROPE-WEST1 region.
D. Configure a custom retention policy of 12 years on your Google Cloud’s operations suite log bucket in the EUROPE-WEST1 region.
After completing a security vulnerability assessment, you learned that cloud administrators leave Google Cloud CLI sessions open for days. You need to reduce the risk of attackers who might exploit these open sessions by setting these sessions to the minimum duration. What should you do?
A. Set the session duration for the Google session control to one hour.
B. Set the reauthentication frequency for the Google Cloud Session Control to one hour.
C. Set the organization policy constraint constraints/iam.allowServiceAccountCredentialLifetimeExtension to one hour.
D. Set the organization policy constraint constraints/iam.serviceAccountKeyExpiryHours to one hour and inheritFromParent to false.
You manage a fleet of virtual machines (VMs) in your organization. You have encountered issues with lack of patching in many VMs. You need to automate regular patching in your VMs and view the patch management data across multiple projects. What should you do? (Choose two.)
A. View patch management data in VM Manager by using OS patch management.
B. View patch management data in Artifact Registry.
C. View patch management data in a Security Command Center dashboard.
D. Deploy patches with Security Command Genter by using Rapid Vulnerability Detection.
E. Deploy patches with VM Manager by using OS patch management.
You want to prevent users from accidentally deleting a Shared VPC host project. Which organization-level policy constraint should you enable?
A. compute.restrictSharedVpcHostProjects
B. compute.restrictXpnProjectLienRemoval
C. compute.restrictSharedVpcSubnetworks
D. compute.sharedReservationsOwnerProjects
A customer terminates an engineer and needs to make sure the engineer's Google account is automatically deprovisioned. What should the customer do?
A. Use the Cloud SDK with their directory service to remove their IAM permissions in Cloud Identity.
B. Use the Cloud SDK with their directory service to provision and deprovision users from Cloud Identity.
C. Configure Cloud Directory Sync with their directory service to provision and deprovision users from Cloud Identity.
D. Configure Cloud Directory Sync with their directory service to remove their IAM permissions in Cloud Identity.
Your organization's Google Cloud VMs are deployed via an instance template that configures them with a public IP address in order to host web services for external users. The VMs reside in a service project that is attached to a host (VPC) project containing one custom Shared VPC for the VMs. You have been asked to reduce the exposure of the VMs to the internet while continuing to service external users. You have already recreated the instance template without a public IP address configuration to launch the managed instance group (MIG). What should you do?
A. Deploy a Cloud NAT Gateway in the service project for the MIG.
B. Deploy a Cloud NAT Gateway in the host (VPC) project for the MIG.
C. Deploy an external HTTP(S) load balancer in the service project with the MIG as a backend.
D. Deploy an external HTTP(S) load balancer in the host (VPC) project with the MIG as a backend.
For compliance reporting purposes, the internal audit department needs you to provide the list of virtual machines (VMs) that have critical operating system (OS) security updates available, but not installed. You must provide this list every six months, and you want to perform this task quickly. What should you do?
A. Run a Security Command Center security scan on all VMs to extract a list of VMs with critical OS vulnerabilities every six months.
B. Run a gcloud CLI command from the Command Line Interface (CLI) to extract the VM’s OS version information every six months.
C. Ensure that the Cloud Logging agent is installed on all VMs, and extract the OS last update log date every six months.
D. Ensure the OS Config agent is installed on all VMs and extract the patch status dashboard every six months.
You have a highly sensitive BigQuery workload that contains personally identifiable information (PII) that you want to ensure is not accessible from the internet. To prevent data exfiltration, only requests from authorized IP addresses are allowed to query your BigQuery tables. What should you do?
A. Use service perimeter and create an access level based on the authorized source IP address as the condition.
B. Use Google Cloud Armor security policies defining an allowlist of authorized IP addresses at the global HTTPS load balancer.
C. Use the Restrict Resource Service Usage organization policy constraint along with Cloud Data Loss Prevention (DLP).
D. Use the Restrict allowed Google Cloud APIs and services organization policy constraint along with Cloud Data Loss Prevention (DLP).
Your organization recently activated the Security Command Center (SCC) standard tier. There are a few Cloud Storage buckets that were accidentally made accessible to the public. You need to investigate the impact of the incident and remediate it. What should you do?
A. 1. Remove the Identity and Access Management (IAM) granting access to all Users from the buckets.2. Apply the organization policy storage.uniformBucketLevelAccess to prevent regressions.3. Query the data access logs to report on unauthorized access.
B. 1. Change permissions to limit access for authorized users.2. Enforce a VPC Service Controls perimeter around all the production projects to immediately stop any unauthorized access.3. Review the administrator activity audit logs to report on any unauthorized access.
C. 1. Change the bucket permissions to limit access.2. Query the bucket’s usage logs to report on unauthorized access to the data.3. Enforce the organization policy storage.publicAccessPrevention to avoid regressions.
D. 1. Change bucket permissions to limit access.2. Query the data access audit logs for any unauthorized access to the buckets.3. After the misconfiguration is corrected, mute the finding in the Security Command Center.
A database administrator notices malicious activities within their Cloud SQL instance. The database administrator wants to monitor the API calls that read the configuration or metadata of resources. Which logs should the database administrator review?
A. Admin Activity
B. System Event
C. Access Transparency
D. Data Access
An organization's security and risk management teams are concerned about where their responsibility lies for certain production workloads they are running in Google Cloud and where Google's responsibility lies. They are mostly running workloads using Google Cloud's platform-as-a-Service (PaaS) offerings, including App Engine primarily. Which area in the technology stack should they focus on as their primary responsibility when using App Engine?
A. Configuring and monitoring VPC Flow Logs
B. Defending against XSS and SQLi attacks
C. Managing the latest updates and security patches for the Guest OS
D. Encrypting all stored data
You need to implement an encryption-at-rest strategy that protects sensitive data and reduces key management complexity for non-sensitive data. Your solution has the following requirements: ✑ Schedule key rotation for sensitive data. ✑ Control which region the encryption keys for sensitive data are stored in. ✑ Minimize the latency to access encryption keys for both sensitive and non-sensitive data. What should you do?
A. Encrypt non-sensitive data and sensitive data with Cloud External Key Manager.
B. Encrypt non-sensitive data and sensitive data with Cloud Key Management Service.
C. Encrypt non-sensitive data with Google default encryption, and encrypt sensitive data with Cloud External Key Manager.
D. Encrypt non-sensitive data with Google default encryption, and encrypt sensitive data with Cloud Key Management Service.
You are creating an internal App Engine application that needs to access a user's Google Drive on the user's behalf. Your company does not want to rely on the current user's credentials. It also wants to follow Google-recommended practices. What should you do?
A. Create a new Service account, and give all application users the role of Service Account User.
B. Create a new Service account, and add all application users to a Google Group. Give this group the role of Service Account User.
C. Use a dedicated G Suite Admin account, and authenticate the application’s operations with these G Suite credentials.
D. Create a new service account, and grant it G Suite domain-wide delegation. Have the application use it to impersonate the user.
In order to meet PCI DSS requirements, a customer wants to ensure that all outbound traffic is authorized. Which two cloud offerings meet this requirement without additional compensating controls? (Choose two.)
A. App Engine
B. Cloud Functions
C. Compute Engine
D. Google Kubernetes Engine
E. Cloud Storage
You need tofficentralize your team's logs for production projects. You want your team to be able to search and analyze the logs using Logs Explorer. What should you do?
A. Enable Cloud Monitoring workspace, and add the production projects to be monitored.
B. Use Logs Explorer at the organization level and filter for production project logs.
C. Create an aggregate org sink at the parent folder of the production projects, and set the destination to a Cloud Storage bucket.
D. Create an aggregate org sink at the parent folder of the production projects, and set the destination to a logs bucket.
You are creating a new infrastructure CI/CD pipeline to deploy hundreds of ephemeral projects in your Google Cloud organization to enable your users to interact with Google Cloud. You want to restrict the use of the default networks in your organization while following Google-recommended best practices. What should you do?
A. Enable the constraints/compute.skipDefaultNetworkCreation organization policy constraint at the organization level.
B. Create a cron job to trigger a daily Cloud Function to automatically delete all default networks for each project.
C. Grant your users the IAM Owner role at the organization level. Create a VPC Service Controls perimeter around the project that restricts the compute.googleapis.com API.
D. Only allow your users to use your CI/CD pipeline with a predefined set of infrastructure templates they can deploy to skip the creation of the default networks.
Your DevOps team uses Packer to build Compute Engine images by using this process: 1. Create an ephemeral Compute Engine VM. 2. Copy a binary from a Cloud Storage bucket to the VM's file system. 3. Update the VM's package manager. 4. Install external packages from the internet onto the VM. Your security team just enabled the organizational policy, constraints/ compute.vmExternalIpAccess, to restrict the usage of public IP Addresses on VMs. In response, your DevOps team updated their scripts to remove public IP addresses on the Compute Engine VMs; however, the build pipeline is failing due to connectivity issues. What should you do? (Choose two.)
A. Provision an HTTP load balancer with the VM in an unmanaged instance group to allow inbound connections from the internet to your VM.
B. Provision a Cloud NAT instance in the same VPC and region as the Compute Engine VM.
C. Enable Private Google Access on the subnet that the Compute Engine VM is deployed within.
D. Update the VPC routes to allow traffic to and from the internet.
E. Provision a Cloud VPN tunnel in the same VPC and region as the Compute Engine VM.
Your team wants tofficentrally manage GCP IAM permissions from their on-premises Active Directory Service. Your team wants to manage permissions by AD group membership. What should your team do to meet these requirements?
A. Set up Cloud Directory Sync to sync groups, and set IAM permissions on the groups.
B. Set up SAML 2.0 Single Sign-On (SSO), and assign IAM permissions to the groups.
C. Use the Cloud Identity and Access Management API to create groups and IAM permissions from Active Directory.
D. Use the Admin SDK to create groups and assign IAM permissions from Active Directory.
You manage your organization's Security Operations Center (SOC). You currently monitor and detect network traffic anomalies in your VPCs based on network logs. However, you want to explore your environment using network payloads and headers. Which Google Cloud product should you use?
A. Cloud IDS
B. VPC Service Controls logs
C. VPC Flow Logs
D. Google Cloud Armor
E. Packet Mirroring
You need to enforce a security policy in your Google Cloud organization that prevents users from exposing objects in their buckets externally. There are currently no buckets in your organization. Which solution should you implement proactively to achieve this goal with the least operational overhead?
A. Create an hourly cron job to run a Cloud Function that finds public buckets and makes them private.
B. Enable the constraints/storage.publicAccessPrevention constraint at the organization level.
C. Enable the constraints/storage.uniformBucketLevelAccess constraint at the organization level.
D. Create a VPC Service Controls perimeter that protects the storage.googleapis.com service in your projects that contains buckets. Add any new project that contains a bucket to the perimeter.
Your team uses a service account to authenticate data transfers from a given Compute Engine virtual machine instance of to a specified Cloud Storage bucket. An engineer accidentally deletes the service account, which breaks application functionality. You want to recover the application as quickly as possible without compromising security. What should you do?
A. Temporarily disable authentication on the Cloud Storage bucket.
B. Use the undelete command to recover the deleted service account.
C. Create a new service account with the same name as the deleted service account.
D. Update the permissions of another existing service account and supply those credentials to the applications.
Your organization is transitioning to Google Cloud. You want to ensure that only trusted container images are deployed on Google Kubernetes Engine (GKE) clusters in a project. The containers must be deployed from a centrally managed Container Registry and signed by a trusted authority. What should you do? (Choose two.)
A. Enable Container Threat Detection in the Security Command Center (SCC) for the project.
B. Configure the trusted image organization policy constraint for the project.
C. Create a custom organization policy constraint to enforce Binary Authorization for Google Kubernetes Engine (GKE).
D. Enable PodSecurity standards, and set them to Restricted.
E. Configure the Binary Authorization policy with respective attestations for the project.
You have been tasked with implementing external web application protection against common web application attacks for a public application on Google Cloud. You want to validate these policy changes before they are enforced. What service should you use?
A. Google Cloud Armor’s preconfigured rules in preview mode
B. Prepopulated VPC firewall rules in monitor mode
C. The inherent protections of Google Front End (GFE)
D. Cloud Load Balancing firewall rules
E. VPC Service Controls in dry run mode
A customer needs to prevent attackers from hijacking their domain/IP and redirecting users to a malicious site through a man-in-the-middle attack. Which solution should this customer use?
A. VPC Flow Logs
B. Cloud Armor
C. DNS Security Extensions
D. Cloud Identity-Aware Proxy
You are the Security Admin in your company. You want to synchronize all security groups that have an email address from your LDAP directory in Cloud IAM. What should you do?
A. Configure Google Cloud Directory Sync to sync security groups using LDAP search rules that have ג€user email addressג€ as the attribute to facilitate one-way sync.
B. Configure Google Cloud Directory Sync to sync security groups using LDAP search rules that have ג€user email addressג€ as the attribute to facilitate bidirectional sync.
C. Use a management tool to sync the subset based on the email address attribute. Create a group in the Google domain. A group created in a Google domain will automatically have an explicit Google Cloud Identity and Access Management (IAM) role.
D. Use a management tool to sync the subset based on group object class attribute. Create a group in the Google domain. A group created in a Google domain will automatically have an explicit Google Cloud Identity and Access Management (IAM) role.
You need to provide a corporate user account in Google Cloud for each of your developers and operational staff who need direct access to GCP resources. Corporate policy requires you to maintain the user identity in a third-party identity management provider and leverage single sign-on. You learn that a significant number of users are using their corporate domain email addresses for personal Google accounts, and you need to follow Google recommended practices to convert existing unmanaged users to managed accounts. Which two actions should you take? (Choose two.)
A. Use Google Cloud Directory Sync to synchronize your local identity management system to Cloud Identity.
B. Use the Google Admin console to view which managed users are using a personal account for their recovery email.
C. Add users to your managed Google account and force users to change the email addresses associated with their personal accounts.
D. Use the Transfer Tool for Unmanaged Users (TTUU) to find users with conflicting accounts and ask them to transfer their personal Google accounts.
E. Send an email to all of your employees and ask those users with corporate email addresses for personal Google accounts to delete the personal accounts immediately.
You manage a BigQuery analytical data warehouse in your organization. You want to keep data for all your customers in a common table while you also restrict query access based on rows and columns permissions. Non-query operations should not be supported. What should you do? (Choose two.)
A. Create row-level access policies to restrict the result data when you run queries with the filter expression set to TRUE.
B. Configure column-level encryption by using Authenticated Encryption with Associated Data (AEAD) functions with Cloud Key Management Service (KMS) to control access to columns at query runtime.
C. Create row-level access policies to restrict the result data when you run queries with the filter expression set to FALSE.
D. Configure dynamic data masking rules to control access to columns at query runtime.
E. Create column-level policy tags to control access to columns at query runtime.
A company is running their webshop on Google Kubernetes Engine and wants to analyze customer transactions in BigQuery. You need to ensure that no credit card numbers are stored in BigQuery What should you do?
A. Create a BigQuery view with regular expressions matching credit card numbers to query and delete affected rows.
B. Use the Cloud Data Loss Prevention API to redact related infoTypes before data is ingested into BigQuery.
C. Leverage Security Command Center to scan for the assets of type Credit Card Number in BigQuery.
D. Enable Cloud Identity-Aware Proxy to filter out credit card numbers before storing the logs in BigQuery.
Your company is using GSuite and has developed an application meant for internal usage on Google App Engine. You need to make sure that an external user cannot gain access to the application even when an employee's password has been compromised. What should you do?
A. Enforce 2-factor authentication in GSuite for all users.
B. Configure Cloud Identity-Aware Proxy for the App Engine Application.
C. Provision user passwords using GSuite Password Sync.
D. Configure Cloud VPN between your private network and GCP.
Your company’s users access data in a BigQuery table. You want to ensure they can only access the data during working hours. What should you do?
A. Assign a BigQuery Data Viewer role along with an IAM condition that limits the access to specified working hours.
B. Run a gsutil script that assigns a BigQuery Data Viewer role, and remove it only during the specified working hours.
C. Assign a BigQuery Data Viewer role to a service account that adds and removes the users daily during the specified working hours.
D. Configure Cloud Scheduler so that it triggers a Cloud Functions instance that modifies the organizational policy constraint for BigQuery during the specified working hours.
You are responsible for protecting highly sensitive data in BigQuery. Your operations teams need access to this data, but given privacy regulations, you want to ensure that they cannot read the sensitive fields such as email addresses and first names. These specific sensitive fields should only be available on a need-to- know basis to the Human Resources team. What should you do?
A. Perform data masking with the Cloud Data Loss Prevention API, and store that data in BigQuery for later use.
B. Perform data redaction with the Cloud Data Loss Prevention API, and store that data in BigQuery for later use.
C. Perform data inspection with the Cloud Data Loss Prevention API, and store that data in BigQuery for later use.
D. Perform tokenization for Pseudonymization with the Cloud Data Loss Prevention API, and store that data in BigQuery for later use.
You need to implement an encryption at-rest strategy that reduces key management complexity for non-sensitive data and protects sensitive data while providing the flexibility of controlling the key residency and rotation schedule. FIPS 140-2 L1 compliance is required for all data types. What should you do?
A. Encrypt non-sensitive data and sensitive data with Cloud External Key Manager.
B. Encrypt non-sensitive data and sensitive data with Cloud Key Management Service
C. Encrypt non-sensitive data with Google default encryption, and encrypt sensitive data with Cloud External Key Manager.
D. Encrypt non-sensitive data with Google default encryption, and encrypt sensitive data with Cloud Key Management Service.
You need to set up a Cloud interconnect connection between your company's on-premises data center and VPC host network. You want to make sure that on- premises applications can only access Google APIs over the Cloud Interconnect and not through the public internet. You are required to only use APIs that are supported by VPC Service Controls to mitigate against exfiltration risk to non-supported APIs. How should you configure the network?
A. Enable Private Google Access on the regional subnets and global dynamic routing mode.
B. Set up a Private Service Connect endpoint IP address with the API bundle of “all-apis”, which is advertised as a route over the Cloud interconnect connection.
C. Use private.googleapis.com to access Google APIs using a set of IP addresses only routable from within Google Cloud, which are advertised as routes over the connection.
D. Use restricted googleapis.com to access Google APIs using a set of IP addresses only routable from within Google Cloud, which are advertised as routes over the Cloud Interconnect connection.
An office manager at your small startup company is responsible for matching payments to invoices and creating billing alerts. For compliance reasons, the office manager is only permitted to have the Identity and Access Management (IAM) permissions necessary for these tasks. Which two IAM roles should the office manager have? (Choose two.)
A. Organization Administrator
B. Project Creator
C. Billing Account Viewer
D. Billing Account Costs Manager
E. Billing Account User
You are the security admin of your company. Your development team creates multiple GCP projects under the "implementation" folder for several dev, staging, and production workloads. You want to prevent data exfiltration by malicious insiders or compromised code by setting up a security perimeter. However, you do not want to restrict communication between the projects. What should you do?
A. Use a Shared VPC to enable communication between all projects, and use firewall rules to prevent data exfiltration.
B. Create access levels in Access Context Manager to prevent data exfiltration, and use a shared VPC for communication between projects.
C. Use an infrastructure-as-code software tool to set up a single service perimeter and to deploy a Cloud Function that monitors the “implementation” folder via Stackdriver and Cloud Pub/Sub. When the function notices that a new project is added to the folder, it executes Terraform to add the new project to the associated perimeter.
D. Use an infrastructure-as-code software tool to set up three different service perimeters for dev, staging, and prod and to deploy a Cloud Function that monitors the “implementation” folder via Stackdriver and Cloud Pub/Sub. When the function notices that a new project is added to the folder, it executes Terraform to add the new project to the respective perimeter.
Your security team wants to reduce the risk of user-managed keys being mismanaged and compromised. To achieve this, you need to prevent developers from creating user-managed service account keys for projects in their organization. How should you enforce this?
A. Configure Secret Manager to manage service account keys.
B. Enable an organization policy to disable service accounts from being created.
C. Enable an organization policy to prevent service account keys from being created.
D. Remove the iam.serviceAccounts.getAccessToken permission from users.
You are on your company's development team. You noticed that your web application hosted in staging on GKE dynamically includes user data in web pages without first properly validating the inputted data. This could allow an attacker to execute gibberish commands and display arbitrary content in a victim user's browser in a production environment. How should you prevent and fix this vulnerability?
A. Use Cloud IAP based on IP address or end-user device attributes to prevent and fix the vulnerability.
B. Set up an HTTPS load balancer, and then use Cloud Armor for the production environment to prevent the potential XSS attack.
C. Use Web Security Scanner to validate the usage of an outdated library in the code, and then use a secured version of the included library.
D. Use Web Security Scanner in staging to simulate an XSS injection attack, and then use a templating system that supports contextual auto-escaping.
Your team needs to make sure that a Compute Engine instance does not have access to the internet or to any Google APIs or services. Which two settings must remain disabled to meet these requirements? (Choose two.)
A. Public IP
B. IP Forwarding
C. Private Google Access
D. Static routes
E. IAM Network User Role
Access Full Google Professional Cloud Security Engineer Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of Google Professional Cloud Security Engineer exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your Google Professional Cloud Security Engineer certification journey!