CS0-002 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the CS0-002 certification? Take your preparation to the next level with our CS0-002 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a CS0-002 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic CS0-002 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
A security technician is testing a solution that will prevent outside entities from spoofing the company’s email domain, which is comptia.org. The testing is successful, and the security technician is prepared to fully implement the solution. Which of the following actions should the technician take to accomplish this task?
A. Add TXT @ “v=spfl mx include:_spf.comptia.org -all” to the DNS record.
B. Add TXT @ “v=spfl mx include:_spf.comptia.org -all” to the email server.
C. Add TXT @ “v=spfl mx include:_spf.comptia.org +all” to the domain controller.
D. Add TXT @ “v=spfl mx include:_spf.comptia.org +all” to the web server.
A Chief Information Security Officer has asked for a list of hosts that have critical and high-severity findings as referenced in the CVE database. Which of the following tools would produce the assessment output needed to satisfy this request?
A. Nessus
B. Nikto
C. Fuzzer
D. Wireshark
E. Prowler
A company wants to ensure confidential data from its storage media files is sanitized so the drives cannot be reused. Which of the following is the BEST approach?
A. Degaussing
B. Shredding
C. Formatting
D. Encrypting
An analyst needs to provide recommendations based on a recent vulnerability scan:Which of the following should the analyst recommend addressing to ensure potential vulnerabilities are identified?
A. SMB use domain SID to enumerate users
B. SYN scanner
C. SSL certificate cannot be trusted
D. Scan not performed with admin privileges
During a company’s most recent incident, a vulnerability in custom software was exploited on an externally facing server by an APT. The lessons-learned report noted the following: • The development team used a new software language that was not supported by the security team's automated assessment tools. • During the deployment, the security assessment team was unfamiliar with the new language and struggled to evaluate the software during advanced testing. Therefore, the vulnerability was not detected. • The current IPS did not have effective signatures and policies in place to detect and prevent runtime attacks on the new application. To allow this new technology to be deployed securely going forward, which of the following will BEST address these findings? (Choose two.)
A. Train the security assessment team to evaluate the new language and verify that best practices for secure coding have been followed
B. Work with the automated assessment-tool vendor to add support for the new language so these vulnerabilities are discovered automatically
C. Contact the human resources department to hire new security team members who are already familiar with the new language
D. Run the software on isolated systems so when they are compromised, the attacker cannot pivot to adjacent systems
E. Instruct only the development team to document the remediation steps for this vulnerability
F. Outsource development and hosting of the applications in the new language to a third-party vendor so the risk is transferred to that provider
A security analyst discovers the following firewall log entries during an incident:Which of the following is MOST likely occurring?
A. Banner grabbing
B. Port scanning
C. Beaconing
D. Data exfiltration
An organization has the following risk mitigation policy: • Risks with a probability of 95% or greater will be addressed before all others regardless of the impact. • All other prioritization will be based on risk value. The organization has identified the following risks:Which of the following is the order of priority for risk mitigation from highest to lowest?
A. A, B, D, C
B. A, B, C, D
C. D, A, B, C
D. D, A, C, B
After a series of Group Policy Object updates, multiple services stopped functioning. The systems administrator believes the issue resulted from a Group Policy Object update but cannot validate which update caused the issue. Which of the following security solutions would resolve this issue?
A. Privilege management
B. Group Policy Object management
C. Change management
D. Asset management
A penetration tester physically enters a datacenter and attaches a small device to a switch. As part of the tester's effort to evaluate which nodes are present on the network; the tester places the network agape in promiscuous mode and logs traffic for later analysis. Which of the following is the tester performing?
A. Credential scanning
B. Passive scanning
C. Protocol analysis
D. SCAP scanning
E. Network segmentation
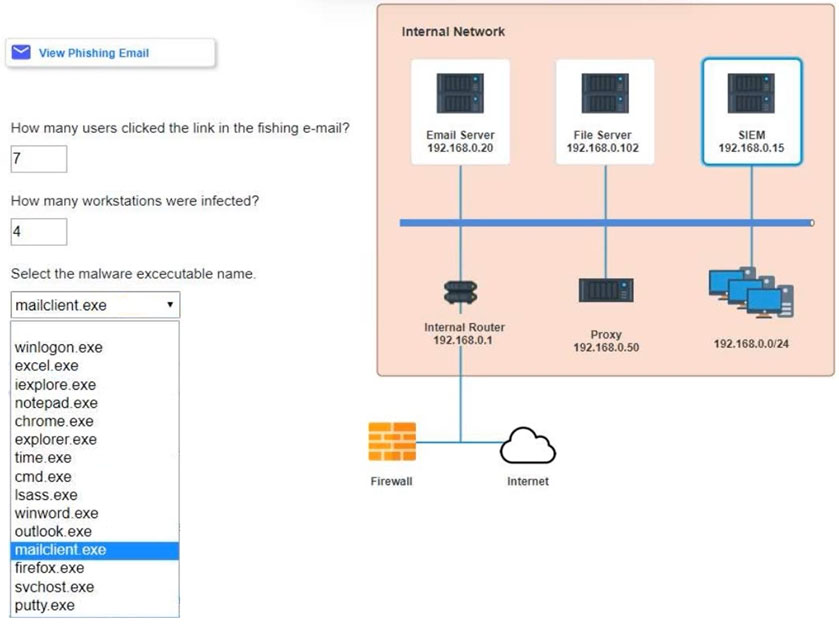
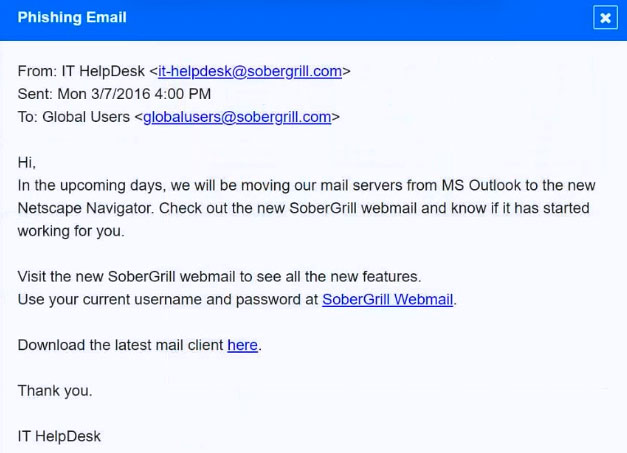
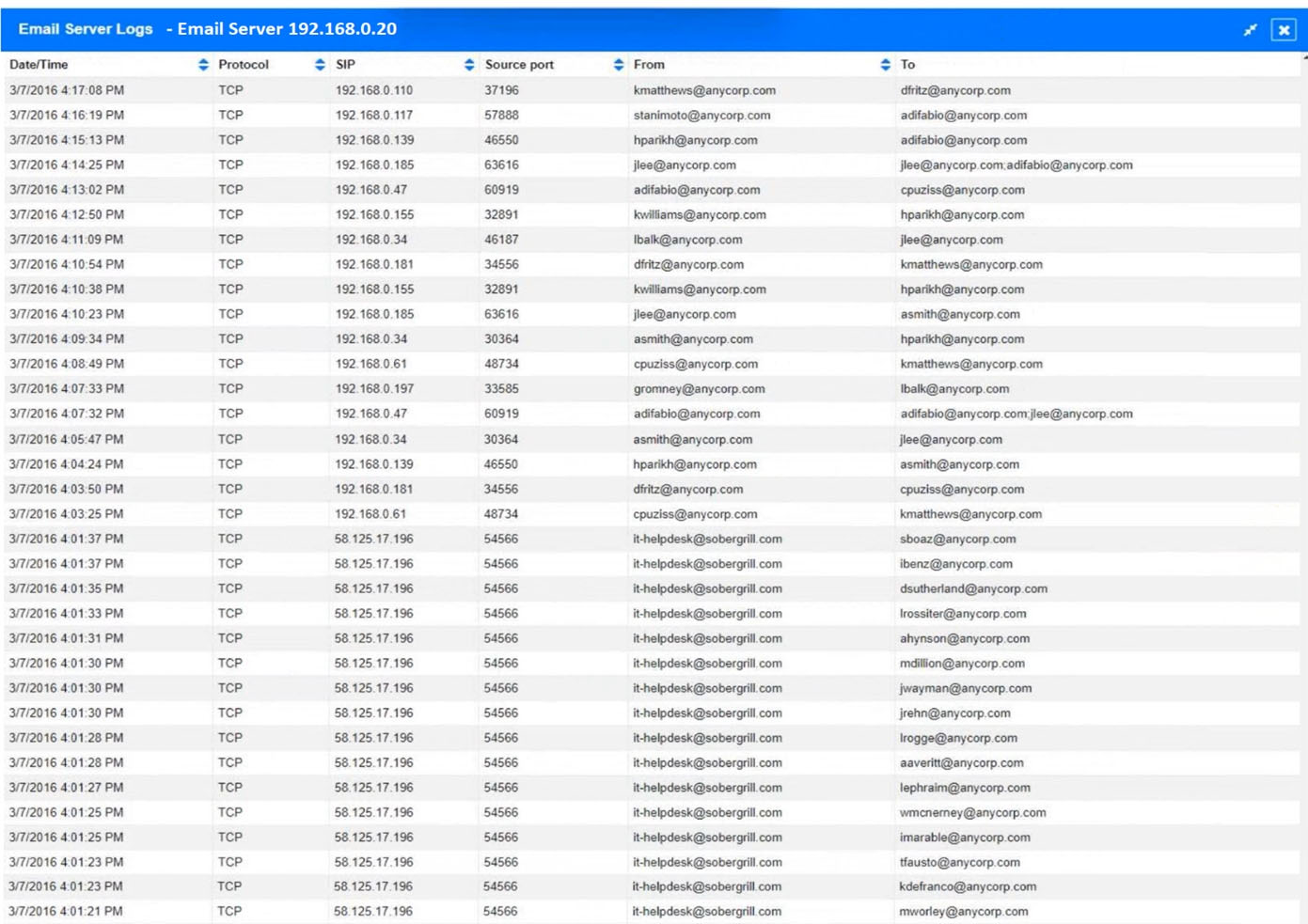
SIMULATION - Approximately 100 employees at your company have received a phishing email. As a security analyst, you have been tasked with handling this situation. INSTRUCTIONS - Review the information provided and determine the following: 1. How many employees clicked on the link in the phishing email? 2. On how many workstations was the malware installed? 3. What is the executable file name of the malware? If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.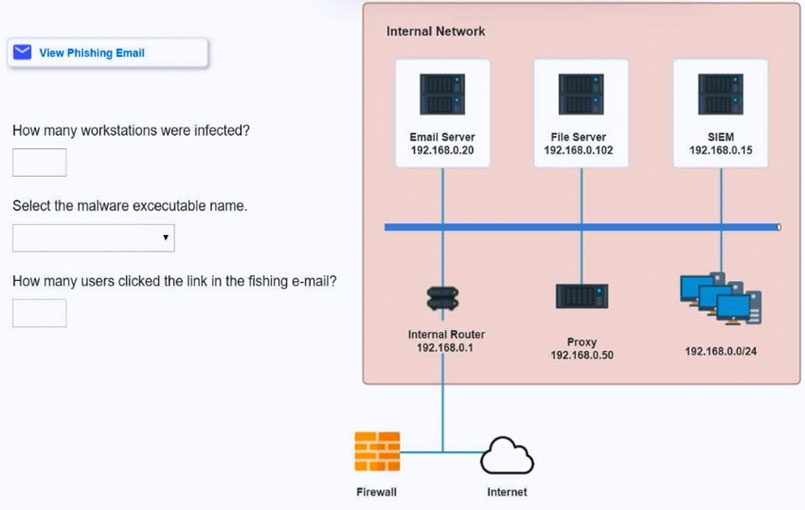
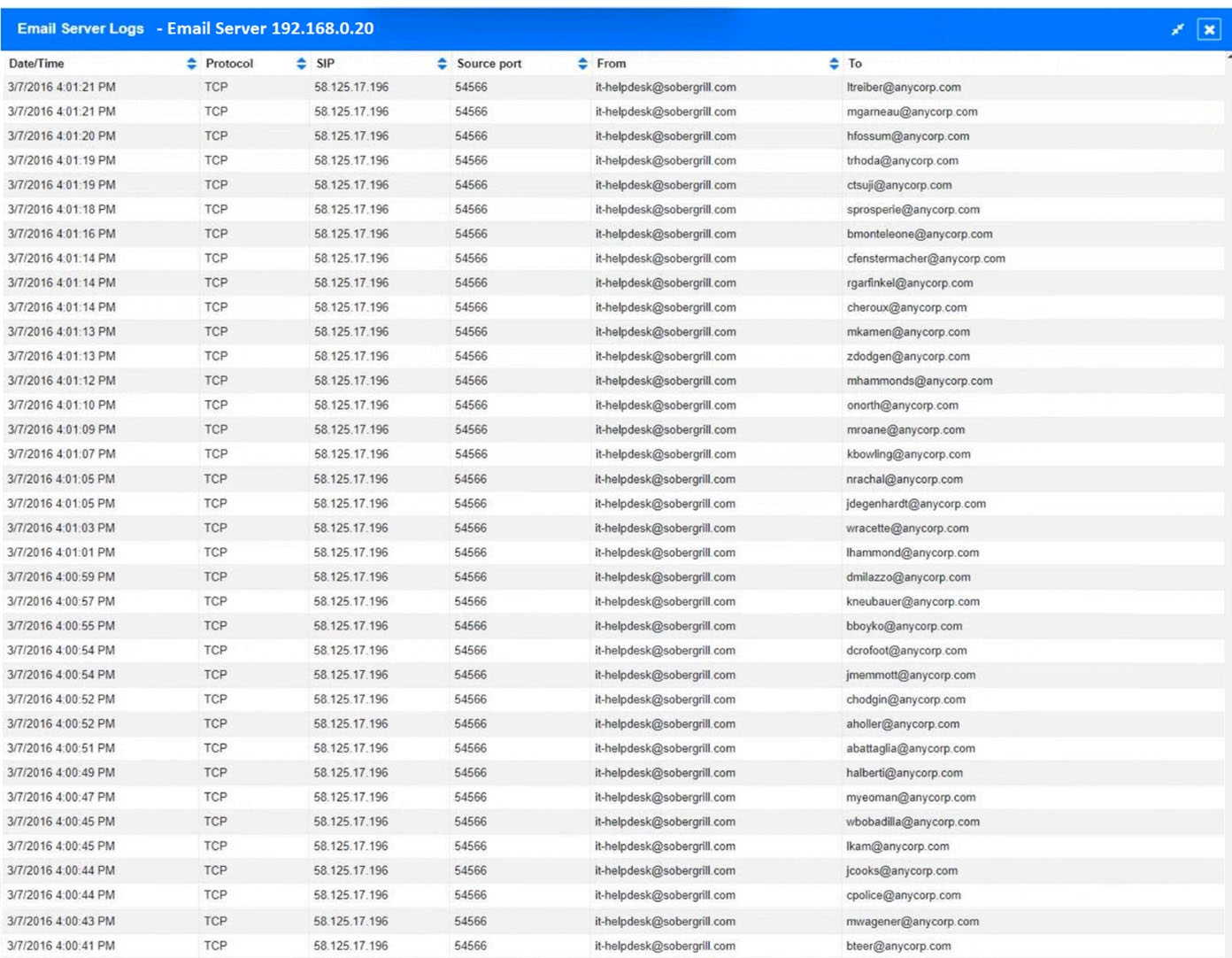
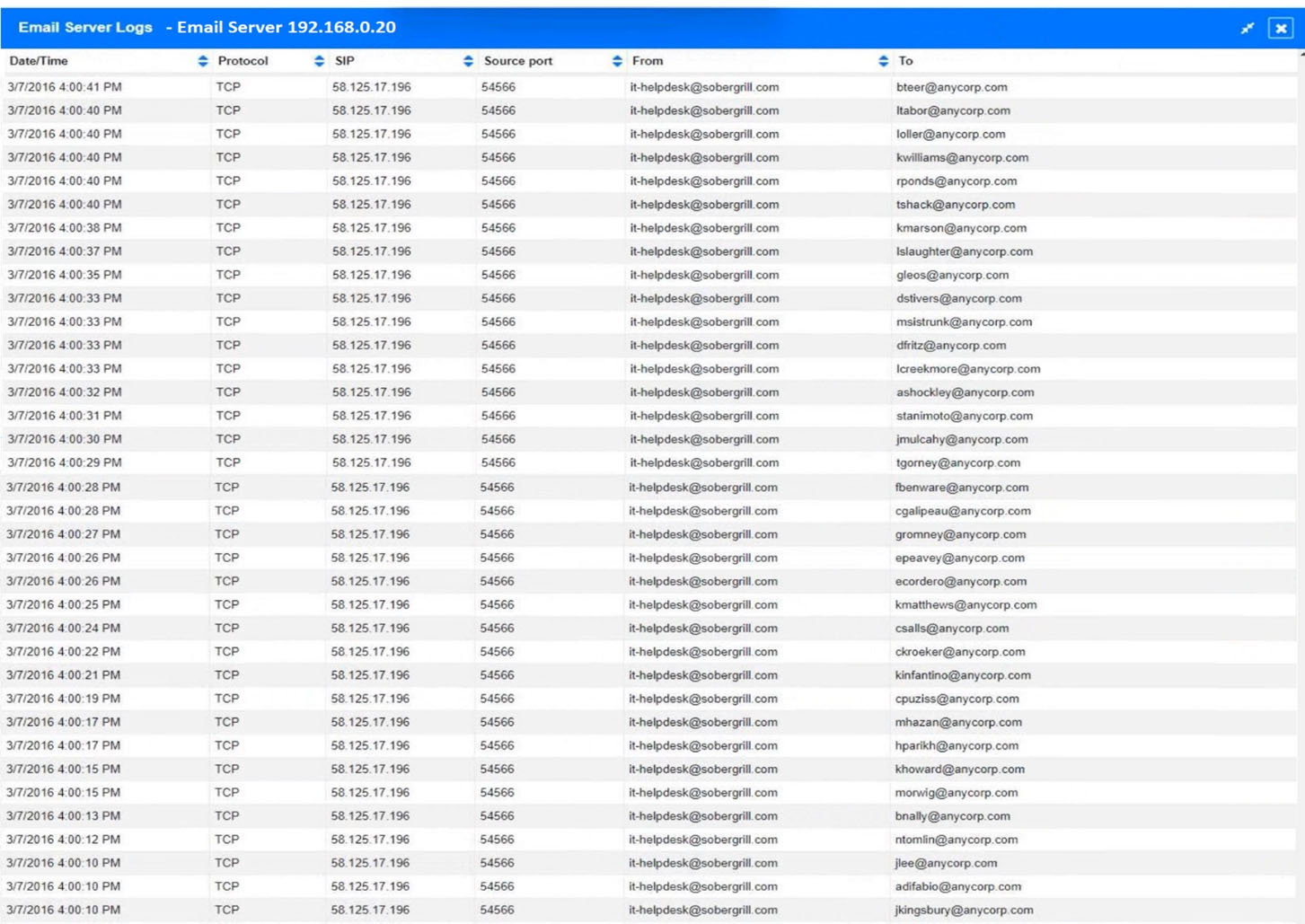
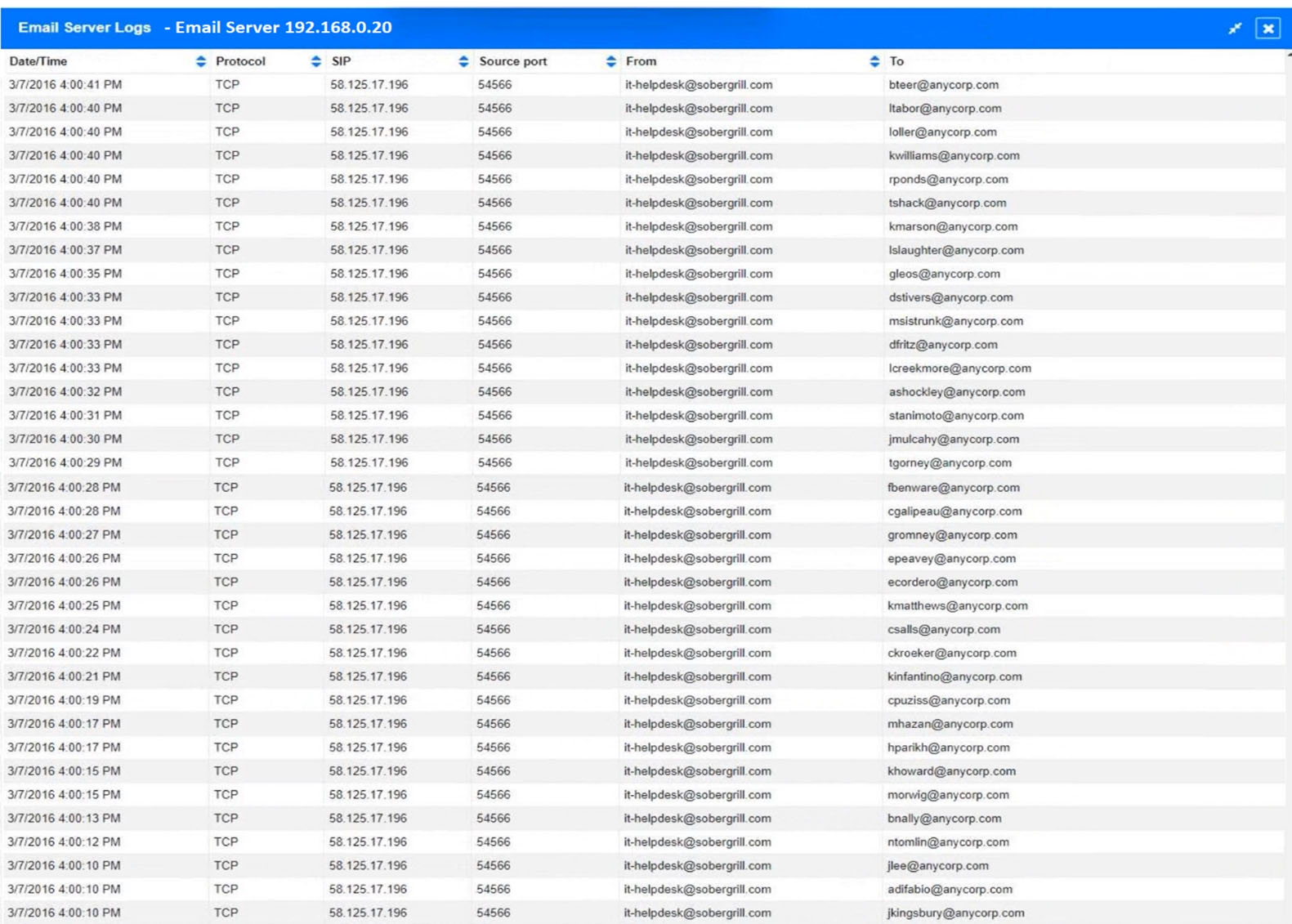

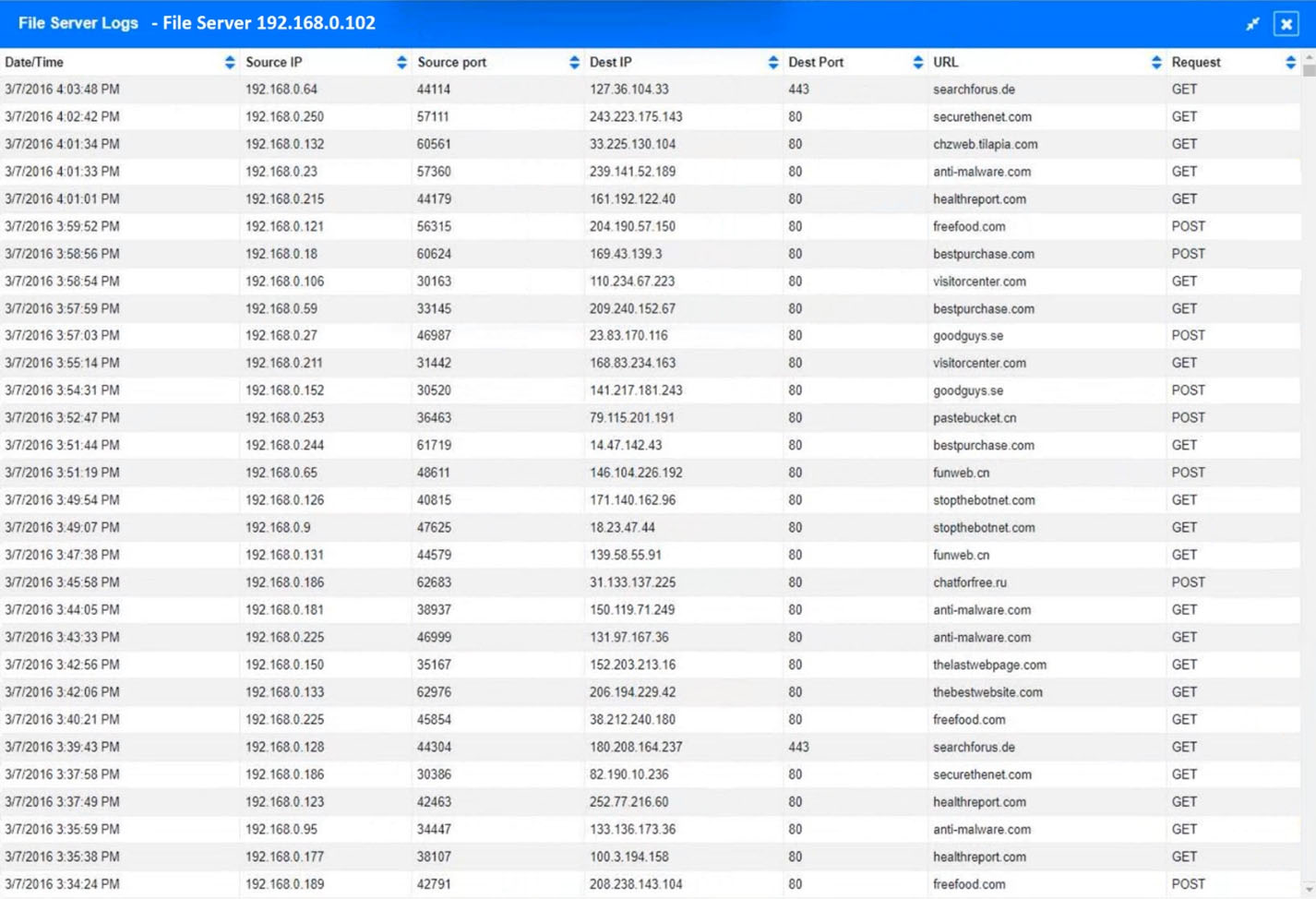
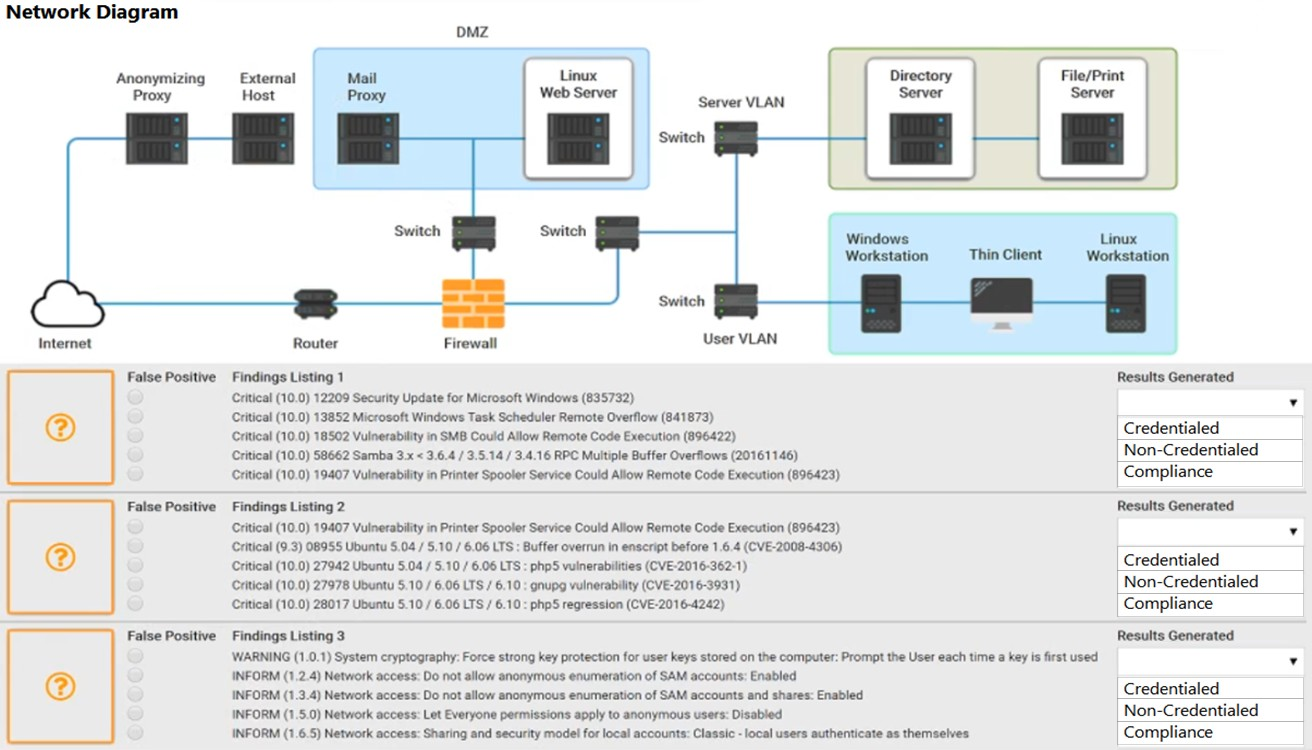
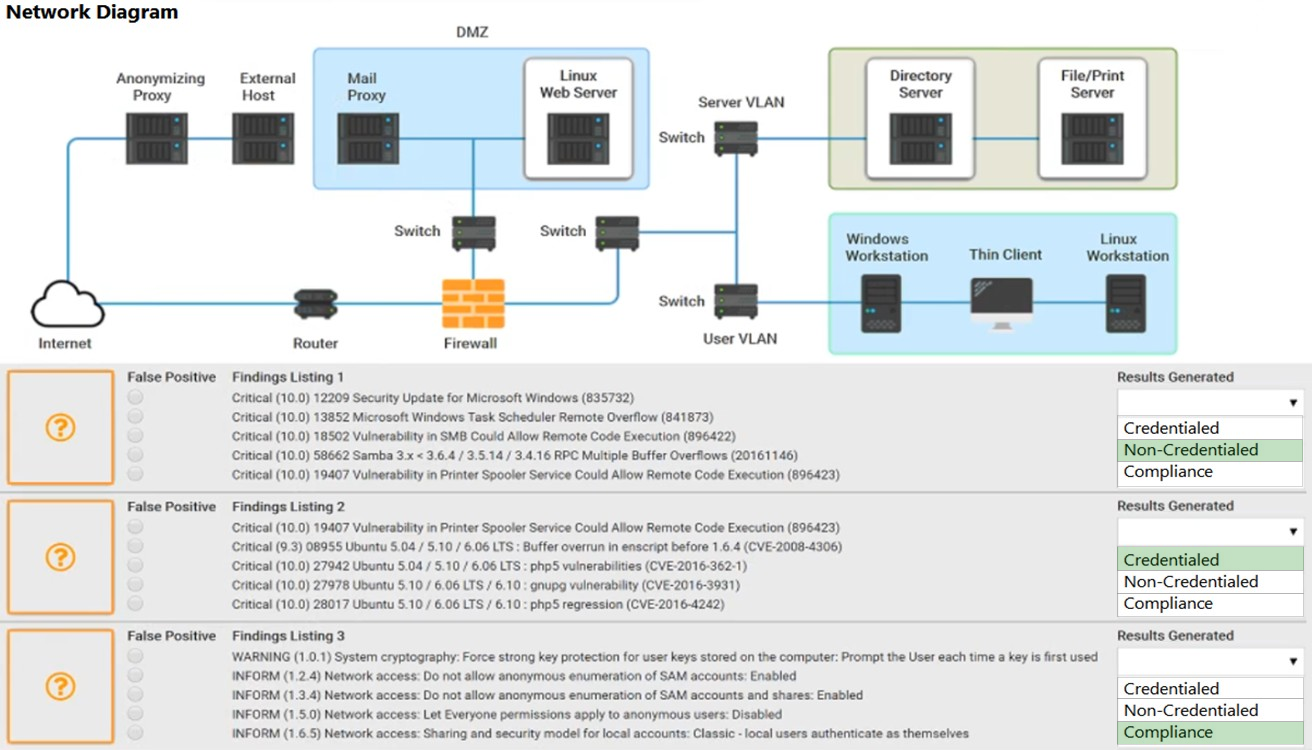
HOTSPOT - A security analyst performs various types of vulnerability scans. Review the vulnerability scan results to determine the type of scan that was executed and if a false positive occurred for each device. INSTRUCTIONS - Select the Results Generated drop-down option to determine if the results were generated from a credentialed scan, non-credentialed scan, or a compliance scan. For ONLY the credentialed and non-credentialed scans, evaluate the results for False Positives and check the Findings that display false positives. NOTE: If you would like to uncheck an option that is currently selected, click on the option a second time. Lastly, based on the vulnerability scan results, identify the type of Server by dragging the Server to the results. The Linux Web Server, File-Print Server, and Directory Server are draggable. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button. Hot Area:
An organization's Chief Information Security Officer has asked department leaders to coordinate on communication plans that can be enacted in response to different cybersecurity incident triggers. Which of the following is a benefit of having these communication plans?
A. They can help to prevent the inadvertent release of damaging information outside the organization
B. They can help to limit the spread of worms by coordinating with help desk personnel earlier in the recovery phase.
C. They can quickly inform the public relations team to begin coordinating with the media as soon as a breach is detected
D. They can help to keep the organization’s senior leadership informed about the status of patching during the recovery phase
A security analyst is reviewing malware files without running them. Which of the following analysis types is the security analyst using?
A. Dynamic
B. Sandbox
C. Static
D. Heuristic
An analyst needs to provide recommendations based on the following vulnerability report:Which of the following vulnerabilities should the analyst recommend addressing first?
A. SSL certificate signed using weak hashing algorithm
B. TLS version 1.0 protocol detection
C. PHP 7.1.x <7.1.25 multiple vulnerabilities
D. RHEL 7 : qemu-kvm (RHSA-2020:1208)
A security analyst is investigating a reported phishing attempt that was received by many users throughout the company. The text of one of the emails is shown below:Office 365 User, It looks like your account has been locked out. Please click this http://accountfix-office356 com/login.php and follow the prompts to restore access. Regards, Security Team - Due to the size of the company and the high storage requirements, the company does not log DNS requests or perform packet captures of network traffic, but it does log network flow data. Which of the following commands will the analyst most likely execute NEXT?
A. telnet off1ce365.com 25
B. tracert 122.167.40.119
C. curl http://accountfix-office356.com/login.php
D. nslookup accountfix-office356.com
A security analyst identified some potentially malicious processes after capturing the contents of memory from a machine during incident response. Which of the following procedures is the NEXT step for further investigation?
A. Data carving
B. Timeline construction
C. File cloning
D. Reverse engineering
A new prototype for a company’s flagship product was leaked on the internet. As a result, the management team has locked out all USB dives. Optical drive writers are not present on company computers. The sales team has been granted an exception to share sales presentation files with third parties. Which of the following would allow the IT team to determine which devices are USB enabled?
A. Asset tagging
B. Device encryption
C. Data loss prevention
D. SIEM logs
A security analyst is reviewing the following requirements for new time clocks that will be installed in a shipping warehouse: • The clocks must be configured so they do not respond to ARP broadcasts. • The server must be configured with static ARP entries for each clock. Which of the following types of attacks will this configuration mitigate?
A. Spoofing
B. Overflows
C. Rootkits
D. Sniffing
A security analyst responds to a series of events surrounding sporadic bandwidth consumption from an endpoint device. The security analyst then identifies the following additional details: • Bursts of network utilization occur approximately every seven days. • The content being transferred appears to be encrypted or obfuscated. • A separate but persistent outbound TCP connection from the host to infrastructure in a third-party cloud is in place. • The HDD utilization on the device grows by 10GB to 12GB over the course of every seven days. • Single file sizes are 10GB. Which of the following describes the most likely cause of the issue?
A. Memory consumption
B. Non-standard port usage
C. Data exfiltration
D. System update
E. Botnet participant
The majority of a company's employees have stated they are unable to perform their job duties due to outdated workstations, so the company has decided to institute BYOD. Which of the following would a security analyst MOST likely recommend for securing the proposed solution?
A. A Linux-based system and mandatory training on Linux for all BYOD users
B. A firewalled environment for client devices and a secure VDI for BYOD users
C. A standardized anti-malware platform and a unified operating system vendor
D. 802.1X to enforce company policy on BYOD user hardware
A security analyst is reviewing existing email protection mechanisms to generate a report. The analysis finds the following DNS records: Record 1 - v=spf1 ip4:192:168.0.0/16 include:_spf.marketing.com include: thirdpartyprovider.com ~all Record 2 - “v=DKIM1 k=rsa; p=MIGfMA0GCSqh7d8hyh78Gdg87gd98hag86ga98dhay8gd7ashdca7yg79auhudig7df9ah8g76ag98dhay87ga9” Record 3 - _dmarc.comptia.com TXT v=DMARC1; p=reject; pct=100; rua=mailto: dmarc-reports@comptia.com Which of the following options provides accurate information to be included in the report?
A. Record 3 serves as a reference of the security features configured at Record 1 and 2.
B. Record 1 is used as a blocklist mechanism to filter unauthorized senders.
C. Record 2 is used as a key to encrypt all outbound messages sent.
D. The three records contain private information that should not be disclosed.
A security analyst reviews the following aggregated output from an Nmap scan and the border firewall ACL:Which of the following should the analyst reconfigure to BEST reduce organizational risk while maintaining current functionality?
A. PC1
B. PC2
C. Server1
D. Server2
E. Firewall
An organization is developing software to match customers' expectations. Before the software goes into production, it must meet the following quality assurance guidelines: Uncover all the software vulnerabilities.✑ Safeguard the interest of the software's end users. ✑ Reduce the likelihood that a defective program will enter production. ✑ Preserve the interests of the software producer. Which of the following should be performed FIRST?
A. Run source code against the latest OWASP vulnerabilities.
B. Document the life-cycle changes that took place.
C. Ensure verification and validation took place during each phase.
D. Store the source code in a software escrow.
E. Conduct a static analysis of the code.
A security team is struggling with alert fatigue, and the Chief Information Security Officer has decided to purchase a SOAR platform to alleviate this issue. Which of the following BEST describes how a SOAR platform will help the security team?
A. SOAR will integrate threat intelligence into the alerts, which will help the security team decide which events should be investigated first.
B. A SOAR platform connects the SOC with the asset database, enabling the security team to make informed decisions immediately based on asset criticality.
C. The security team will be able to use the SOAR framework to integrate the SIEM with a TAXII server, which has an automated intelligence feed that will enhance the alert data.
D. Logic can now be created that will allow the SOAR platform to block specific traffic at the firewall according to predefined event triggers and actions.
The incident response team is working with a third-party forensic specialist to investigate the root cause of a recent intrusion. An analyst was asked to submit sensitive network design details for review. The forensic specialist recommended electronic delivery for efficiency, but email was not an approved communication channel to send network details. Which of the following BEST explains the importance of using a secure method of communication during incident response?
A. To prevent adversaries from intercepting response and recovery details
B. To ensure intellectual property remains on company servers
C. To have a backup plan in case email access is disabled
D. To ensure the management team has access to all the details that are being exchanged
Which of the following ICS network protocols has no inherent security functions on TCP port 502?
A. CIP
B. DHCP
C. SSH
D. Modbus
During the threat modeling process for a new application that a company is launching, a security analyst needs to define methods and items to take into consideration. Which of the following are part of a known threat modeling method?
A. Threat profile, infrastructure and application vulnerabilities, security strategy and plans
B. Purpose, objective, scope, team management, cost, roles and responsibilities
C. Spoofing, tampering, repudiation, information disclosure, denial of service, elevation of privilege
D. Human impact, adversary’s motivation, adversary’s resources, adversary’s methods
A proposed network architecture requires systems to be separated from each other logically based on defined risk levels. Which of the following explains the reason why an architect would set up the network this way?
A. To complicate the network and frustrate a potential malicious attacker
B. To create a design that simplifies the supporting network
C. To reduce the attack surface of those systems by segmenting the network based on risk
D. To reduce the number of IP addresses that are used on the network
As part of the senior leadership team's ongoing risk management activities, the Chief Information Security Officer has tasked a security analyst with coordinating the right training and testing methodology to respond to new business initiatives or significant changes to existing ones. The management team wants to examine a new business process that would use existing infrastructure to process and store sensitive data. Which of the following would be appropriate for the security analyst to coordinate?
A. A black-box penetration testing engagement
B. A tabletop exercise
C. Threat modeling
D. A business impact analysis
While planning segmentation for an ICS environment, a security engineer determines IT resources will need access to devices within the ICS environment without compromising security. To provide the MOST secure access model in this scenario, the jumpbox should be:
A. placed in an isolated network segment, authenticated on the IT side, and forwarded into the ICS network.
B. placed on the ICS network with a static firewall rule that allows IT network resources to authenticate.
C. bridged between the IT and operational technology networks to allow authenticated access.
D. placed on the IT side of the network, authenticated, and tunneled into the ICS environment.
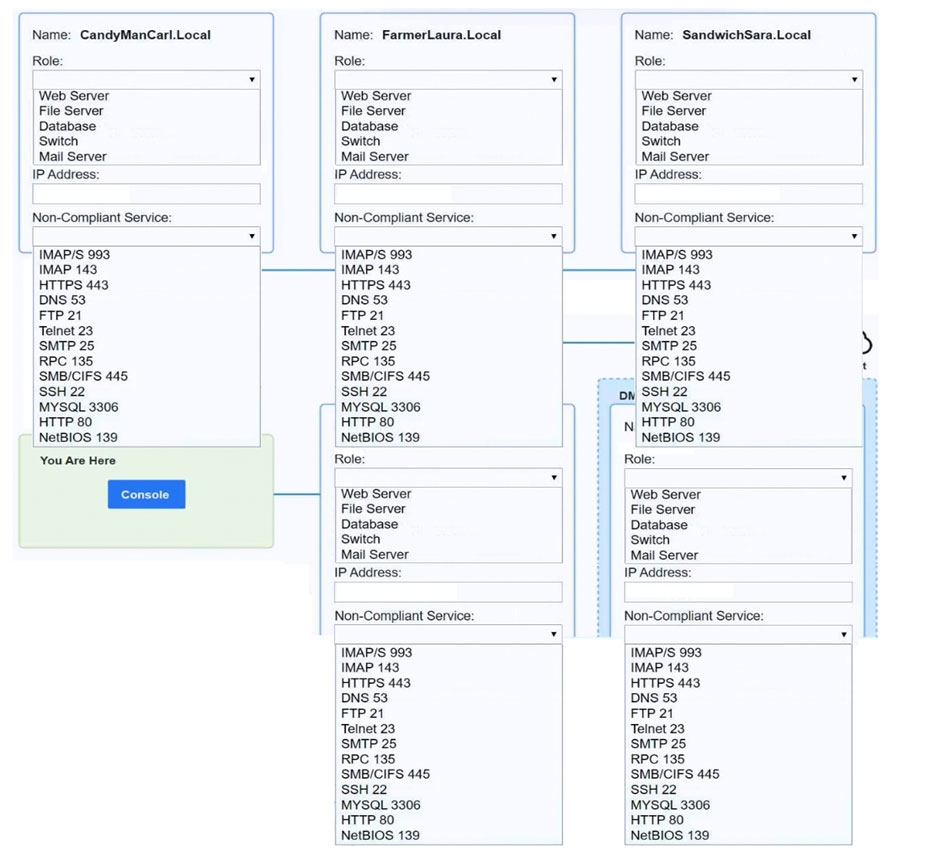
SIMULATION - You are a penetration tester who is reviewing the system hardening guidelines for a company's distribution center. The company's hardening guidelines indicate the following: ✑ There must be one primary server or service per device. ✑ Only default ports should be used. ✑ Non-secure protocols should be disabled. ✑ The corporate Internet presence should be placed in a protected subnet. INSTRUCTIONS - Using the tools available, discover devices on the corporate network and the services that are running on these devices. You must determine: ✑ The IP address of each device. ✑ The primary server or service of each device. ✑ The protocols that should be disabled based on the hardening guidelines. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
During an audit, several customer order forms were found to contain inconsistencies between the actual price of an item and the amount charged to the customer. Further investigation narrowed the cause of the issue to manipulation of the public-facing web form used by customers to order products. Which of the following would be the best way to locate this issue?
A. Reduce the session timeout threshold.
B. Deploy MFA for access to the web server.
C. Implement input validation.
D. Run a dynamic code analysis.
A security analyst received a series of antivirus alerts from a workstation segment, and users reported ransomware messages. During lessons-learned activities, the analyst determines the antivirus was able to alert to abnormal behavior but did not stop this newest variant of ransomware. Which of the following actions should be taken to BEST mitigate the effects of this type of threat in the future?
A. Enabling sandboxing technology
B. Purchasing cyber insurance
C. Enabling application blacklisting
D. Installing a firewall between the workstations and internet
When attempting to do a stealth scan against a system that does not respond to ping, which of the following Nmap commands BEST accomplishes that goal?
A. nmap –sA –O -noping
B. nmap –sT –O -Pn
C. nmap –sS –O -Pn
D. nmap –sQ –O -Pn
Which of the following organizational initiatives would be MOST impacted by data sovereignty issues?
A. Moving to a cloud-based environment
B. Migrating to locally hosted virtual servers
C. Implementing non-repudiation controls
D. Encrypting local database queries
An executive assistant wants to onboard a new cloud-based product to help with business analytics and dashboarding. Which of the following would be the BEST integration option for this service?
A. Manually log in to the service and upload data files on a regular basis.
B. Have the internal development team script connectivity and file transfers to the new service.
C. Create a dedicated SFTP site and schedule transfers to ensure file transport security.
D. Utilize the cloud product’s API for supported and ongoing integrations.
A company that uses email for all internal and external communications received a legal notice from a vendor that was disputing a contract award. The company needs to implement ta legal hold on the email of users who were involved in the vendor selection process and the awarding of the contract. Which of the following describes the appropriate steps that should be taken to comply with the legal notice?
A. Notify the security team of the legal hold and remove user access to the email accounts.
B. Coordinate with legal counsel and then not the security team to ensure the appropriate email accounts are frozen.
C. Disable the user accounts that are associated with the legal hold and create new user accounts so they can continue doing business.
D. Encrypt messages that are associated with the legal hold and initiate a chain of custody to ensure admissibility in future legal proceedings.
A security analyst receives a CVE bulletin, which lists several products that are used in the enterprise. The analyst immediately deploys a critical security patch. Which of the following BEST describes the reason for the analyst’s immediate action?
A. Nation-state hackers are targeting the region.
B. A new vulnerability was discovered by a vendor.
C. A known exploit was discovered.
D. A new zero-day threat needs to be addressed.
E. There is an insider threat.
Which of the following describes the main difference between supervised and unsupervised machine-learning algorithms that are used in cybersecurity applications?
A. Supervised algorithms can be used to block attacks, while unsupervised algorithms cannot.
B. Supervised algorithms require security analyst feedback, while unsupervised algorithms do not.
C. Unsupervised algorithms are not suitable for IDS systems, while supervised algorithms are.
D. Unsupervised algorithms produce more false positives than supervised algorithms.
A security analyst discovers a vulnerability on an unpatched web server that is used for testing machine learning on Big Data sets Exploitation of the vulnerability could cost the organization $1.5 million in lost productivity. The server is located on an isolated network segment that has a 5% chance of being compromised. Which of the following is the value of this risk?
A. $75,000
B. $300,000
C. $1,425 million
D. $1.5 million
A security analyst notices the following entry while reviewing the server logs: OR 1=1' ADD USER attacker' PW 1337password' -- Which of the following events occurred?
A. CSRF
B. XSS
C. SQLi
D. RCE
Which of the following BEST explains the function of a managerial control?
A. To help design and implement the security planning, program development, and maintenance of the security life cycle
B. To guide the development of training, education, security awareness programs, and system maintenance
C. To create data classification, risk assessments, security control reviews, and contingency planning
D. To ensure tactical design, selection of technology to protect data, logical access reviews, and the implementation of audit trails
Which of the following BEST describes what an organization's incident response plan should cover regarding how the organization handles public or private disclosures of an incident?
A. The disclosure section should focus on how to reduce the likelihood customers will leave due to the incident.
B. The disclosure section should contain the organization’s legal and regulatory requirements regarding disclosures.
C. The disclosure section should include the names and contact information of key employees who are needed for incident resolution.
D. The disclosure section should contain language explaining how the organization will reduce the likelihood of the incident from happening in the future.
An organization is focused on restructuring its data governance programs, and an analyst has been tasked with surveying sensitive data within the organization. Which of the following is the MOST accurate method for the security analyst to complete this assignment?
A. Perform an enterprise-wide discovery scan.
B. Consult with an internal data custodian.
C. Review enterprise-wide asset inventory.
D. Create a survey and distribute it to data owners.
An organization has a policy that requires servers to be dedicated to one function and unneeded services to be disabled. Given the following output from an Nmap scan of a web server:Which of the following ports should be closed?
A. 21
B. 80
C. 443
D. 1433
A small electronics company decides to use a contractor to assist with the development of a new FPGA-based device. Several of the development phases will occur off-site at the contractor's labs. Which of the following is the main concern a security analyst should have with this arrangement?
A. Making multiple trips between development sites increases the chance of physical damage to the FPGAs.
B. Moving the FPGAs between development sites will lessen the time that is available for security testing.
C. Development phases occurring at multiple sites may produce change management issues.
D. FPGA applications are easily cloned, increasing the possibility of intellectual property theft.
An analyst needs to understand how an attacker compromised a server. Which of the following procedures will best deliver the information that is necessary to reconstruct the steps taken by the attacker?
A. Scan the affected system with an anti-malware tool and check for vulnerabilities with a vulnerability scanner.
B. Extract the server’s system timeline, verifying hashes and network connections during a certain time frame.
C. Clone the entire system and deploy it in a network segment built for tests and investigations while monitoring the system during a certain time frame.
D. Clone the server’s hard disk and extract all the binary files, comparing hash signatures with malware databases.
A security analyst is reviewing the output of tcpdump to analyze the type of activity on a packet capture:Which of the following generated the above output?
A. A port scan
B. A TLS connection
C. A vulnerability scan
D. A ping sweep
A company recently experienced a breach of sensitive information that affects customers across multiple geographical regions. Which of the following roles would be BEST suited to determine the breach notification requirements?
A. Legal counsel
B. Chief Security Officer
C. Human resources
D. Law enforcement
A cybersecurity analyst is working with a SIEM tool and reviewing the following table:When creating a rule in the company's SIEM, which of the following would be the BEST approach for the analyst to use to assess the risk level of each vulnerability that is discovered by the vulnerability assessment tool?
A. Create a trend with the table and join the trend with the desired rule to be able to extract the risk level of each vulnerability
B. Use Boolean filters in the SIEM rule to take advantage of real-time processing and RAM to store the table dynamically, generate the results faster, and be able to display the table in a dashboard or export it as a report
C. Use a static table stored on the disk of the SIEM system to correlate its data with the data ingested by the vulnerability scanner data collector
D. Use the table as a new index or database for the SIEM to be able to use multisearch and then summarize the results as output
Free Access Full CS0-002 Practice Exam Free
Looking for additional practice? Click here to access a full set of CS0-002 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your CS0-002 certification journey!