CS0-002 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the CS0-002 certification? Our CS0-002 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective CS0-002 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic CS0-002 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
A routine vulnerability scan detected a known vulnerability in a critical enterprise web application. Which of the following would be the BEST next step?
A. Submit a change request to have the system patched.
B. Evaluate the risk and criticality to determine if further action is necessary.
C. Notify a manager of the breach and initiate emergency procedures.
D. Remove the application from production and inform the users.
A security analyst is reviewing malware files without running them. Which of the following analysis types is the security analyst using?
A. Dynamic
B. Sandbox
C. Static
D. Heuristic
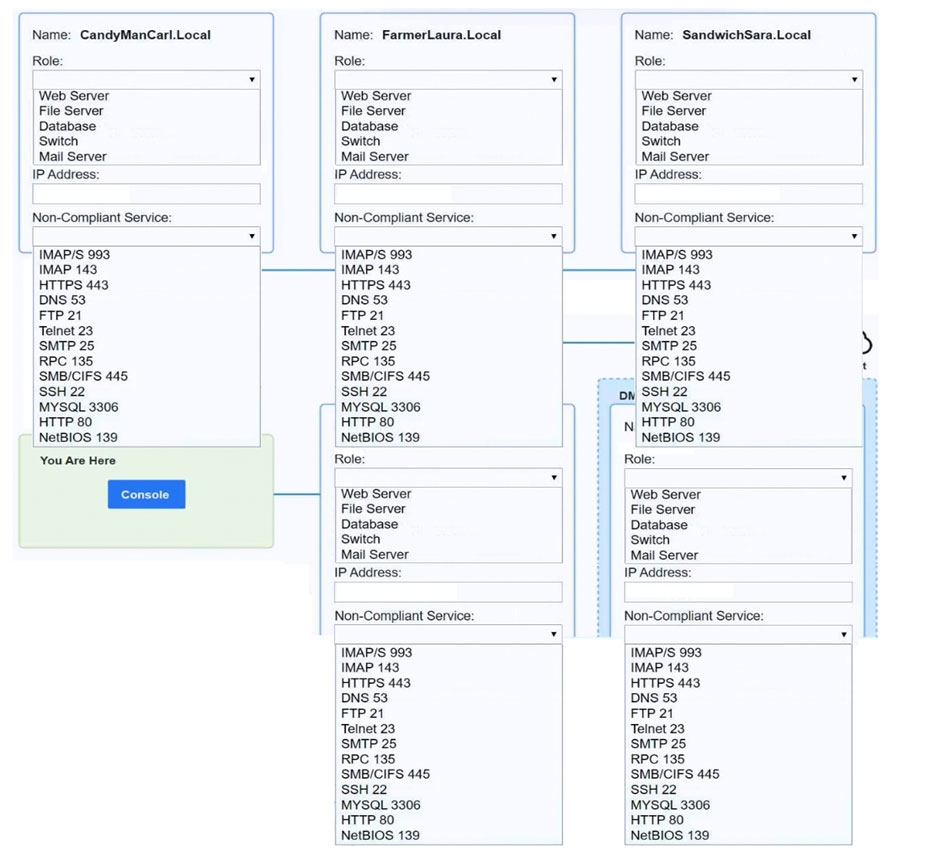
SIMULATION - You are a penetration tester who is reviewing the system hardening guidelines for a company's distribution center. The company's hardening guidelines indicate the following: ✑ There must be one primary server or service per device. ✑ Only default ports should be used. ✑ Non-secure protocols should be disabled. ✑ The corporate Internet presence should be placed in a protected subnet. INSTRUCTIONS - Using the tools available, discover devices on the corporate network and the services that are running on these devices. You must determine: ✑ The IP address of each device. ✑ The primary server or service of each device. ✑ The protocols that should be disabled based on the hardening guidelines. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.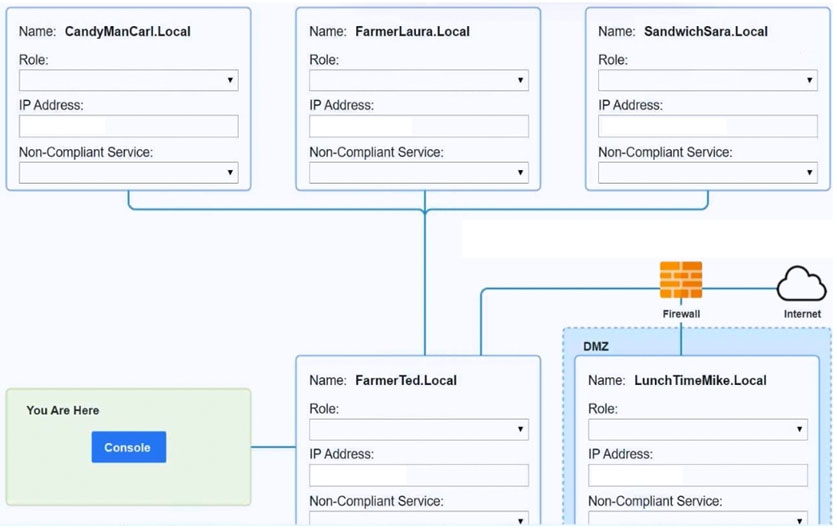
A security analyst needs to provide a copy of a hard drive for forensic analysis. Which of the following would allow the analyst to perform the task?
A. dcfldd if=/dev/one of=/mnt/usb/evidence.bin hash=md5, sha1 hashlog=/mnt/usb/evidence.bin.hashlog
B. dd if=/dev/sda of=/mnt/usb/evidence.bin bs=4096; sha5l2sum /mnt/usb/evidence.bin > /mnt/usb/evidence.bin.hash
C. tar -zcf /mnt/usb/evidence.tar.gz / -except /mnt; sha256sum /mnt/usb/evidence.tar.gz > /mnt/usb/evidence.tar.gz.hash
D. find / -type f -exec cp {} /mnt/usb/evidence/ ; sha1sum /mnt/usb/evidence/* > /mnt/usb/evidence/evidence.hash
Legacy medical equipment, which contains sensitive data, cannot be patched. Which of the following is the BEST solution to improve the equipment’s security posture?
A. Move the legacy systems behind a WAF
B. Implement an air gap for the legacy systems
C. Place the legacy systems in the perimeter network
D. Implement a VPN between the legacy systems and the local network
A host is spamming the network unintentionally. Which of the following control types should be used to address this situation?
A. Managerial
B. Technical
C. Operational
D. Corrective
An analyst is reviewing the following output:Vulnerability found: Improper neutralization of script-related HTML tag. Which of the following was MOST likely used to discover this?
A. Reverse engineering using a debugger
B. A static analysis vulnerability scan
C. A passive vulnerability scan
D. A web application vulnerability scan
Which of the following will allow different cloud instances to share various types of data with a minimal amount of complexity?
A. Reverse engineering
B. Application log collectors
C. Workflow orchestration
D. API integration
E. Scripting
A user reports a malware alert to the help desk. A technician verifies the alert, determines the workstation is classified as a low-severity device, and uses network controls to block access. The technician then assigns the ticket to a security analyst who will complete the eradication and recovery processes. Which of the following should the security analyst do NEXT?
A. Document the procedures and walkthrough the incident training guide
B. Reverse engineer the malware to determine its purpose and risk to the organization
C. Sanitize the workstation and verify countermeasures are restored
D. Isolate the workstation and issue a new computer to the user
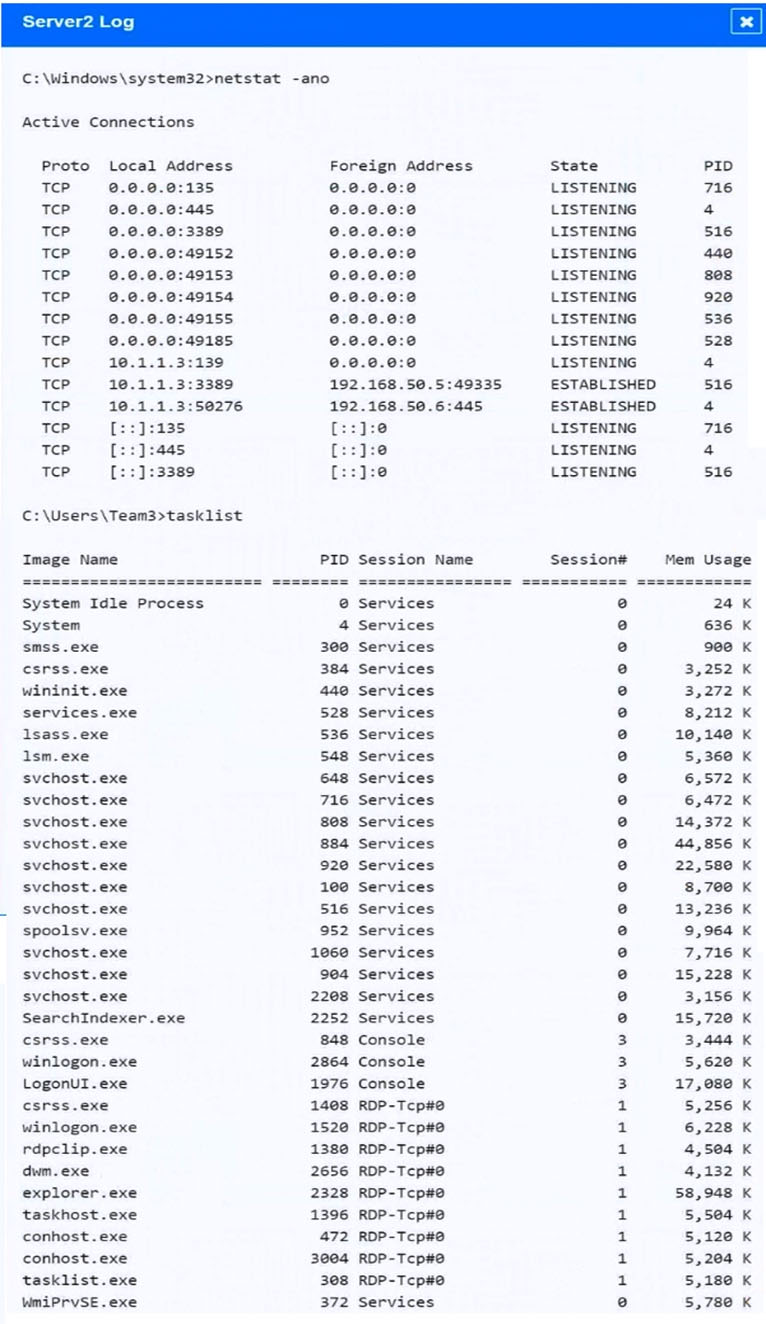
HOTSPOT - Malware is suspected on a server in the environment. The analyst is provided with the output of commands from servers in the environment and needs to review all output files in order to determine which process running on one of the servers may be malware. INSTRUCTIONS - Servers 1, 2, and 4 are clickable. Select the Server and the process that host the malware. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
After receiving reports of high latency, a security analyst performs an Nmap scan and observes the following output:Which of the following suggests the system that produced this output was compromised?
A. Secure shell is operating on a non-standard port.
B. There are no indicators of compromise on this system.
C. MySQL service is identified on a standard PostgreSQL port.
D. Standard HTTP is open on the system and should be closed.
A security analyst found the following entry in a server log:The analyst executed netstat and received the following output:
Which of the following lines in the output confirms this was successfully executed by the server?
A. 1
B. 2
C. 3
D. 4
E. 5
F. 6
G. 7
A company recently experienced similar network attacks. To determine whether the attacks were identical, the company should gather a list of IPs domains, and files and use:
A. behavior data
B. the Diamond Model of Intrusion Analysis.
C. the attack kill chain.
D. the reputational data.
An organization has the following risk mitigation policies: ✑ Risks without compensating controls will be mitigated first if the risk value is greater than $50,000. ✑ Other risk mitigation will be prioritized based on risk value. The following risks have been identified:Which of the following is the order of priority for risk mitigation from highest to lowest?
A. A, C, D, B
B. B. C, D, A
C. C, B, A, D
D. C, D, A, B
E. D, C, B, A
A company's application development has been outsourced to a third-party development team. Based on the SLA, the development team must follow industry best practices for secure coding. Which of the following is the BEST way to verify this agreement?
A. Input validation
B. Security regression testing
C. Application fuzzing
D. User acceptance testing
E. Stress testing
A security analyst inspects the header of an email that is presumed to be malicious and sees the following:Which of the following is inconsistent with the rest of the header and should be treated as suspicious?
A. The use of a TLS cipher
B. The sender’s email address
C. The destination email server
D. The subject line
A company creates digitally signed packages for its devices. Which of the following BEST describes the method by which the security packages are delivered to the company’s customers?
A. Anti-tamper mechanism
B. SELinux
C. Trusted firmware updates
D. eFuse
An organization is concerned about the security posture of vendors with access to its facilities and systems. The organization wants to implement a vendor review process to ensure the policies implemented by vendors are in line with its own. Which of the following will provide the highest assurance of compliance?
A. An in-house red-team report
B. A vendor self-assessment report
C. An independent third-party audit report
D. Internal and external scans from an approved third-party vulnerability vendor
During a forensic investigation, a security analyst reviews some Session Initiation Protocol packets that came from a suspicious IP address. Law enforcement requires access to a VoIP call that originated from the suspicious IP address. Which of the following should the analyst use to accomplish this task?
A. Wireshark
B. iptables
C. Tcp dump
D. Net flow
A security analyst is supporting an embedded software team. Which of the following is the best recommendation to ensure proper error handling at runtime?
A. Perform static code analysis.
B. Require application fuzzing.
C. Enforce input validation.
D. Perform a code review.
A company recently experienced multiple DNS DDoS attacks, and the information security analyst must provide a DDoS solution to deploy in the company's data center. Which of the following would BEST prevent future attacks?
A. Route the queries on the DNS server to 127.0.0.1.
B. Buy a UTM to block the number of requests.
C. Call the internet service provider to block the attack.
D. Configure a sinkhole on the router.
The help desk is having difficulty keeping up with all onboarding and offboarding requests. Managers often submit requests for new users at the last minute, causing the help desk to scramble to create accounts across many different interconnected systems. Which of the following solutions would work BEST to assist the help desk with the onboarding and offboarding process while protecting the company's assets?
A. MFA
B. CASB
C. SSO
D. RBAC
The IT department is concerned about the possibility of a guest device infecting machines on the corporate network or taking down the company's single Internet connection. Which of the following should a security analyst recommend to BEST meet the requirements outlined by the IT department?
A. Require the guest machines to install the corporate-owned EDR solution
B. Configure NAC to only allow machines on the network that are patched and have active antivirus
C. Place a firewall in between the corporate network and the guest network
D. Configure the IPS with rules that will detect common malware signatures traveling from the guest network
After detecting possible malicious external scanning, an internal vulnerability scan was performed, and a critical server was found with an outdated version of JBoss. A legacy application that is running depends on that version of JBoss. Which of the following actions should be taken FIRST to prevent server compromise and business disruption at the same time?
A. Make a backup of the server and update the JBoss server that is running on it.
B. Contact the vendor for the legacy application and request an updated version.
C. Create a proper DMZ for outdated components and segregate the JBoss server.
D. Apply virtualization over the server, using the new platform to provide the JBoss service for the legacy application as an external service.
While reviewing a cyber-risk assessment, an analyst notes there are concerns related to FPGA usage. Which of the following statements would BEST convince the analyst's supervisor to use additional controls?
A. FPGAs are expensive and can only be programmed once. Code deployment safeguards are needed.
B. FPGAs have an inflexible architecture; Additional training for developers is needed.
C. FPGAs are vulnerable to malware installation and require additional protections for their codebase.
D. FPGAs are expensive to produce. Anti-counterfeiting safeguards are needed.
The inability to do remote updates of certificates, keys, software, and firmware is a security issue commonly associated with:
A. web servers on private networks.
B. HVAC control systems.
C. smartphones.
D. firewalls and UTM devices.
SIMULATION - Malware is suspected on a server in the environment. The analyst is provided with the output of commands from servers in the environment and needs to review all output files in order to determine which process running on one of the servers may be malware. INSTRUCTIONS - Servers 1, 2, and 4 are clickable. Select the Server and the process that host the malware. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.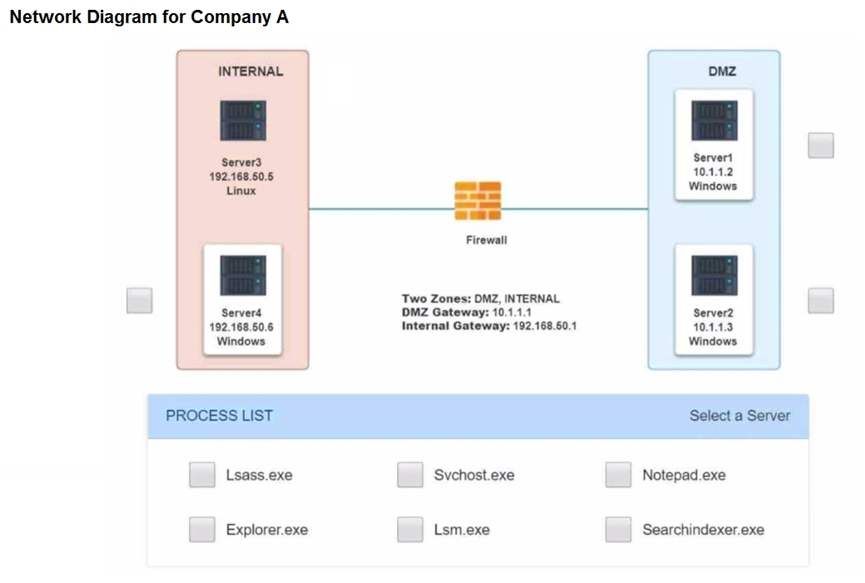
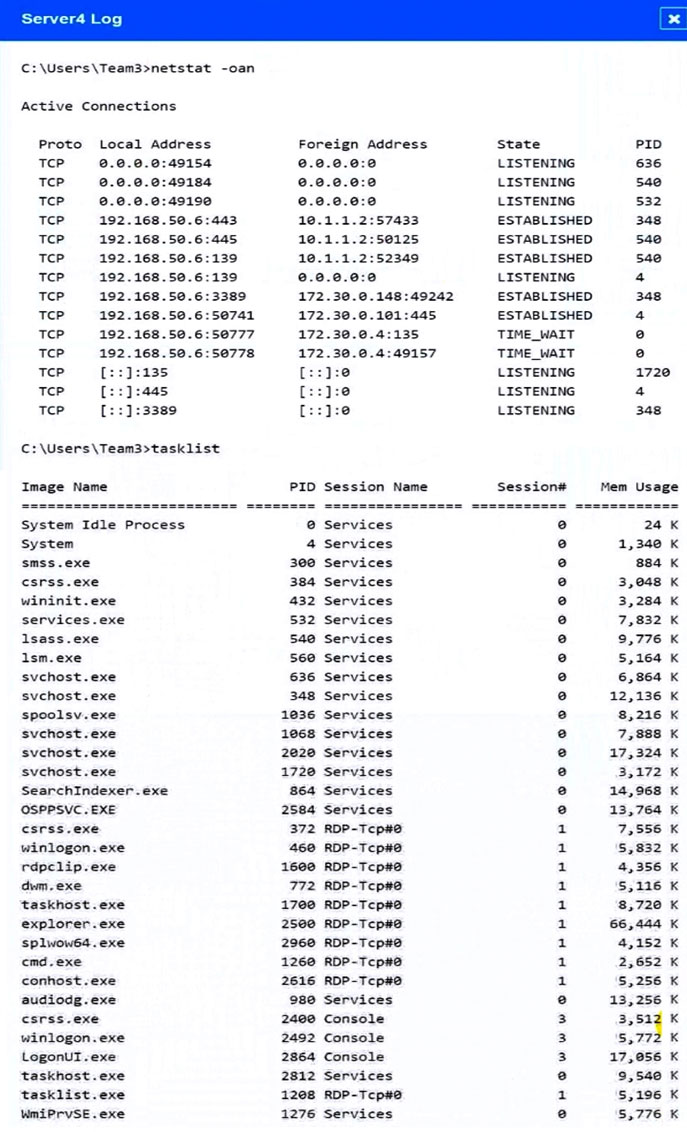
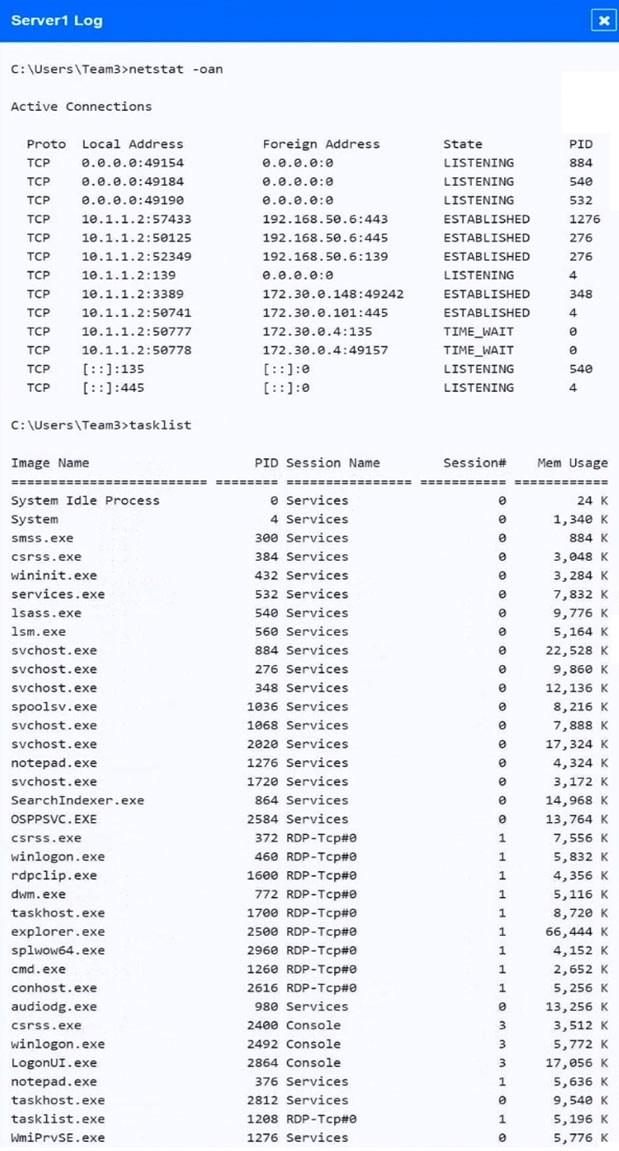
An analyst receives an alert from the continuous-monitoring solution about unauthorized changes to the firmware versions on several field devices. The asset owners confirm that no firmware version updates were performed by authorized technicians, and customers have not reported any performance issues or outages. Which of the following actions would be BEST for the analyst to recommend to the asset owners to secure the devices from further exploitation?
A. Change the passwords on the devices.
B. Implement BIOS passwords.
C. Remove the assets from the production network for analysis.
D. Report the findings to the threat intel community.
A cybersecurity analyst is reading a daily intelligence digest of new vulnerabilities. The type of vulnerability that should be disseminated FIRST is one that:
A. enables remote code execution that is being exploited in the wild.
B. enables data leakage but is not known to be in the environment.
C. enables lateral movement and was reported as a proof of concept.
D. affected the organization in the past but was probably contained and eradicated.
Which of the following can detect vulnerable third-party libraries before code deployment?
A. Impact analysis
B. Dynamic analysis
C. Static analysis
D. Protocol analysis
A Chief Information Security Officer (CISO) is concerned about new privacy regulations that apply to the company. The CISO has tasked a security analyst with finding the proper control functions to verify that a user's data is not altered without the user's consent. Which of the following would be an appropriate course of action?
A. Automate the use of a hashing algorithm after verified users make changes to their data.
B. Use encryption first and then hash the data at regular, defined times.
C. Use a DLP product to monitor the data sets for unauthorized edits and changes.
D. Replicate the data sets at regular intervals and continuously compare the copies for unauthorized changes.
Which of the following BEST explains the function of a managerial control?
A. To help design and implement the security planning, program development, and maintenance of the security life cycle
B. To guide the development of training, education, security awareness programs, and system maintenance
C. To create data classification, risk assessments, security control reviews, and contingency planning
D. To ensure tactical design, selection of technology to protect data, logical access reviews, and the implementation of audit trails
During the security assessment of a new application, a tester attempts to log in to the application but receives the following message: incorrect password for given username. Which of the following can the tester recommend to decrease the likelihood that a malicious attacker will receive helpful information?
A. Set the web page to redirect to an application support page when a bad password is entered.
B. Disable error messaging for authentication.
C. Recognize that error messaging does not provide confirmation of the correct element of authentication.
D. Avoid using password-based authentication for the application.
Which of the following describes the difference between intentional and unintentional insider threats?
A. Their access levels will be different.
B. The risk factor will be the same.
C. Their behavior will be different.
D. The rate of occurrence will be the same.
Which of the following SCAP standards provides standardization for measuring and describing the severity of security-related software flaws?
A. OVAL
B. CVSS
C. CVE
D. CCE
A security analyst s monitoring a company’s network traffic and finds ping requests going to accounting and human resources servers from a SQL server. Upon investigation, the analyst discovers a technician responded to potential network connectivity issues. Which of the following is the best way for the security analyst to respond?
A. Report this activity as a false positive, as the activity is legitimate.
B. Isolate the system and begin a forensic investigation to determine what was compromised.
C. Recommend network segmentation to the management team as a way to secure the various environments.
D. Implement host-bases firewalls on all systems to prevent ping sweeps in the future.
An information security analyst observes anomalous behavior on the SCADA devices in a power plant. This behavior results in the industrial generators overheating and destabilizing the power supply. Which of the following would BEST identify potential indicators of compromise?
A. Use Burp Suite to capture packets to the SCADA device’s IP.
B. Use tcpdump to capture packets from the SCADA device IP.
C. Use Wireshark to capture packets between SCADA devices and the management system.
D. Use Nmap to capture packets from the management system to the SCADA devices.
Which of the following should a database administrator implement to BEST protect data from an untrusted server administrator?
A. Data deidentification
B. Data encryption
C. Data masking
D. Data minimization
Which of the following incident response components can identify who is the liaison between multiple lines of business and the public?
A. Red-team analysis
B. Escalation process and procedures
C. Triage and analysis
D. Communications plan
During an investigation, an analyst discovers the following rule in an executive’s email client:The executive is not aware of this rule. Which of the following should the analyst do first to evaluate the potential impact of this security incident?
A. Check the server logs to evaluate which emails were sent to .
B. Use the SIEM to correlate logging events from the email server and the domain server.
C. Remove the rule from the email client and change the password.
D. Recommend that the management team implement SPF and DKIM.
A security analyst is reviewing the following Internet usage trend report:Which of the following usernames should the security analyst investigate further?
A. User 1
B. User 2
C. User 3
D. User 4
A security analyst is revising a company's MFA policy to prohibit the use of short message service (SMS) tokens. The Chief Information Officer has questioned this decision and asked for justification. Which of the following should the analyst provide as justification for the new policy?
A. SMS relies on untrusted, third-party carrier networks.
B. SMS tokens are limited to eight numerical characters.
C. SMS is not supported on all handheld devices in use.
D. SMS is a cleartext protocol and does not support encryption.
A company employee downloads an application from the internet. After the installation, the employee begins experiencing noticeable performance issues, and files are appearing on the desktop:Which of the following processes will the security analyst identify as the MOST likely indicator of system compromise given the processes running in Task Manager?
A. Chrome.exe
B. Word.exe
C. Explorer.exe
D. mstsc.exe
E. taskmgr.exe
Which of the following threat classifications would MOST likely use polymorphic code?
A. Known threat
B. Zero-day threat
C. Unknown threat
D. Advanced persistent threat
An analyst is reviewing email headers to determine if an email has been sent from a legitimate sender. The organization uses SPF to validate email origination. Which of the following most likely indicates an invalid originator?
A. Received-SPF: neutral
B. Received-SPF: none
C. Received-SPF: softfail
D. Received-SPF: error
An organization is developing software to match customers' expectations. Before the software goes into production, it must meet the following quality assurance guidelines: Uncover all the software vulnerabilities.✑ Safeguard the interest of the software's end users. ✑ Reduce the likelihood that a defective program will enter production. ✑ Preserve the interests of the software producer. Which of the following should be performed FIRST?
A. Run source code against the latest OWASP vulnerabilities.
B. Document the life-cycle changes that took place.
C. Ensure verification and validation took place during each phase.
D. Store the source code in a software escrow.
E. Conduct a static analysis of the code.
The incident response team is working with a third-party forensic specialist to investigate the root cause of a recent intrusion. An analyst was asked to submit sensitive network design details for review. The forensic specialist recommended electronic delivery for efficiency, but email was not an approved communication channel to send network details. Which of the following BEST explains the importance of using a secure method of communication during incident response?
A. To prevent adversaries from intercepting response and recovery details
B. To ensure intellectual property remains on company servers
C. To have a backup plan in case email access is disabled
D. To ensure the management team has access to all the details that are being exchanged
A security analyst receives a CVE bulletin, which lists several products that are used in the enterprise. The analyst immediately deploys a critical security patch. Which of the following BEST describes the reason for the analyst’s immediate action?
A. Nation-state hackers are targeting the region.
B. A new vulnerability was discovered by a vendor.
C. A known exploit was discovered.
D. A new zero-day threat needs to be addressed.
E. There is an insider threat.
An analyst is responding to an incident within a cloud infrastructure. Based on the logs and traffic analysis, the analyst thinks a container has been compromised. Which of the following should the analyst do FIRST?
A. Perform threat hunting in other areas of the cloud infrastructure.
B. Contact law enforcement to report the incident.
C. Perform a root cause analysis on the container and the service logs.
D. Isolate the container from production using a predefined policy template.
While reviewing log files, a security analyst uncovers a brute-force attack that is being performed against an external webmail portal. Which of the following would be best to prevent this type of attack from being successful?
A. Create a new rule in the IDS that triggers an alert on repeated login attempts.
B. Implement MFA on the email portal using out-of-band code delivery.
C. Alter the lockout policy to ensure users are permanently locked out after five attempts.
D. Leverage password filters to prevent weak passwords on employee accounts from being exploited.
E. Configure a WAF with brute-force protection rules in block mode.
Access Full CS0-002 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of CS0-002 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your CS0-002 certification journey!