CS0-002 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your CS0-002 certification? Our CS0-002 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an CS0-002 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our CS0-002 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
Understanding attack vectors and integrating intelligence sources are important components of:
A. a vulnerability management plan.
B. proactive threat hunting.
C. risk management compliance.
D. an incident response plan.
A security analyst needs to reduce the overall attack surface. Which of the following infrastructure changes should the analyst recommend?
A. Implement a honeypot.
B. Air gap sensitive systems.
C. Increase the network segmentation.
D. Implement a cloud-based architecture.
A security analyst is reviewing vulnerability scans from an organization’s internet-facing web services. The following is from an output file called ssl-test_webapps.comptia.org:Which of the following lines from this output most likely indicates that attackers could quickly use brute force and determine the negotiated secret session key?
A. TLS_RSA_WITH_DES_CBC_SHA 56
B. TLS_DHE_RSA_WITH_AES_128_CBC_SHA 128 DH (1024 bits)
C. TLS_RSA_WITH_AES_256_CBC_SHA 256
D. TLS_DHE_RSA_WITH_AES_256_GCM_SHA256 DH (2048 bits)
In SIEM software, a security analyst detected some changes to hash signatures from monitored files during the night followed by SMB brute-force attacks against the file servers. Based on this behavior, which of the following actions should be taken FIRST to prevent a more serious compromise?
A. Fully segregate the affected servers physically in a network segment, apart from the production network.
B. Collect the network traffic during the day to understand if the same activity is also occurring during business hours.
C. Check the hash signatures, comparing them with malware databases to verify if the files are infected.
D. Collect all the files that have changed and compare them with the previous baseline.
A help desk technician inadvertently sent the credentials of the company's CRM in cleartext to an employee's personal email account. The technician then reset the employee's account using the appropriate process and the employee's corporate email, and notified the security team of the incident. According to the incident response procedure, which of the following should the security team do NEXT?
A. Contact the CRM vendor.
B. Prepare an incident summary report.
C. Perform postmortem data correlation.
D. Update the incident response plan.
As part of a merger with another organization, a Chief Information Security Officer (CISO) is working with an assessor to perform a risk assessment focused on data privacy compliance. The CISO is primarily concerned with the potential legal liability and fines associated with data privacy. Based on the CISO’s concerns, the assessor will most likely focus on:
A. qualitative probabilities.
B. quantitative probabilities.
C. qualitative magnitude.
D. quantitative magnitude.
A manager asks a security analyst to provide the web-browsing history of an employee. Which of the following should the analyst do first?
A. Obtain permission to perform the search.
B. Obtain the web-browsing history from the proxy.
C. Obtain the employee’s network ID to form the query.
D. Download the browsing history, encrypt it, and hash it.
A company employee downloads an application from the internet. After the installation, the employee begins experiencing noticeable performance issues, and files are appearing on the desktop:Which of the following processes will the security analyst identify as the MOST likely indicator of system compromise given the processes running in Task Manager?
A. Chrome.exe
B. Word.exe
C. Explorer.exe
D. mstsc.exe
E. taskmgr.exe
While reviewing incident reports from the previous night, a security analyst notices the corporate websites were defaced with political propaganda. Which of the following BEST describes this type of actor?
A. Hacktivist
B. Nation-state
C. Insider threat
D. Organized crime
Security awareness and compliance programs are most effective at reducing the likelihood and impact of attacks from:
A. advanced persistent threats.
B. corporate spies.
C. hacktivists.
D. insider threats.
A company's application development has been outsourced to a third-party development team. Based on the SLA, the development team must follow industry best practices for secure coding. Which of the following is the BEST way to verify this agreement?
A. Input validation
B. Security regression testing
C. Application fuzzing
D. User acceptance testing
E. Stress testing
A security technician configured a NIDS to monitor network traffic. Which of the following is a condition in which harmless traffic is classified as a potential network attack?
A. True positive
B. True negative
C. False positive
D. False negative
During a review of vulnerability scan results, an analyst determines the results may be flawed because a control-baseline system, which is used to evaluate a scanning tool’s effectiveness, was reported as not vulnerable. Consequently, the analyst verifies the scope of the scan included the control-baseline host, which was available on the network during the scan. The use of a control-baseline endpoint in this scenario assists the analyst in confirming:
A. verification of mitigation.
B. false positives.
C. false negatives.
D. the criticality index.
E. hardening validation.
A security analyst reviews a recent network capture and notices encrypted inbound traffic on TCP port 465 was coming into the company's network from a database server. Which of the following will the security analyst MOST likely identify as the reason for the traffic on this port?
A. The server is configured to communicate on the secure database standard listener port.
B. Someone has configured an unauthorized SMTP application over SSL.
C. A connection from the database to the web front end is communicating on the port.
D. The server is receiving a secure connection using the new TLS 1.3 standard.
A security analyst responds to a series of events surrounding sporadic bandwidth consumption from an endpoint device. The security analyst then identifies the following additional details: • Bursts of network utilization occur approximately every seven days. • The content being transferred appears to be encrypted or obfuscated. • A separate but persistent outbound TCP connection from the host to infrastructure in a third-party cloud is in place. • The HDD utilization on the device grows by 10GB to 12GB over the course of every seven days. • Single file sizes are 10GB. Which of the following describes the most likely cause of the issue?
A. Memory consumption
B. Non-standard port usage
C. Data exfiltration
D. System update
E. Botnet participant
In web application scanning, static analysis refers to scanning:
A. the system for vulnerabilities before installing the application
B. the compiled code of the application to detect possible issues.
C. an application that is installed and active on a system.
D. an application that is installed on a system that is assigned a static IP.
A security operations manager wants to build out an internal threat-hunting capability. Which of the following should be the first priority when creating a threat-hunting program?
A. Establishing a hypothesis about which threats are targeting which systems
B. Profiling common threat actors and activities to create a list of IOCs
C. Ensuring logs are sent to a centralized location with search and filtering capabilities
D. Identifying critical assets that will be used to establish targets for threat-hunting activities
While reviewing log files, a security analyst uncovers a brute-force attack that is being performed against an external webmail portal. Which of the following would be best to prevent this type of attack from being successful?
A. Create a new rule in the IDS that triggers an alert on repeated login attempts.
B. Implement MFA on the email portal using out-of-band code delivery.
C. Alter the lockout policy to ensure users are permanently locked out after five attempts.
D. Leverage password filters to prevent weak passwords on employee accounts from being exploited.
E. Configure a WAF with brute-force protection rules in block mode.
A security analyst observes a large amount of scanning activity coming from an IP address outside the organization's environment. Which of the following should the analyst do to block this activity?
A. Create an IPS rule to block the subnet.
B. Sinkhole the IP address.
C. Create a firewall rule to block the IP address.
D. Close all unnecessary open ports.
A security analyst is researching ways to improve the security of a company's email system to mitigate emails that are impersonating company executives. Which of the following would be BEST for the analyst to configure to achieve this objective?
A. A TXT record on the name server for SPF
B. DNSSEC keys to secure replication
C. Domain Keys Identified Mail
D. A sandbox to check incoming mail
A digital forensics investigator works from duplicate images to preserve the integrity of the original evidence. Which of the following types of media are MOST volatile and should be preserved? (Choose two.)
A. Memory cache
B. Registry file
C. SSD storage
D. Temporary filesystems
E. Packet decoding
F. Swap volume
A security analyst needs to provide a copy of a hard drive for forensic analysis. Which of the following would allow the analyst to perform the task?
A. dcfldd if=/dev/one of=/mnt/usb/evidence.bin hash=md5, sha1 hashlog=/mnt/usb/evidence.bin.hashlog
B. dd if=/dev/sda of=/mnt/usb/evidence.bin bs=4096; sha5l2sum /mnt/usb/evidence.bin > /mnt/usb/evidence.bin.hash
C. tar -zcf /mnt/usb/evidence.tar.gz / -except /mnt; sha256sum /mnt/usb/evidence.tar.gz > /mnt/usb/evidence.tar.gz.hash
D. find / -type f -exec cp {} /mnt/usb/evidence/ ; sha1sum /mnt/usb/evidence/* > /mnt/usb/evidence/evidence.hash
A company's blocklist has outgrown the current technologies in place. The ACLs are at maximum, and the IPS signatures only allow a certain amount of space for domains to be added, creating the need for multiple signatures. Which of the following configuration changes to the existing controls would be the MOST appropriate to improve performance?
A. Implement a host-file-based solution that will use a list of all domains to deny for all machines on the network.
B. Create an IDS for the current blocklist to determine which domains are showing activity and may need to be removed.
C. Review the current blocklist and prioritize it based on the level of threat severity. Add the domains with the highest severity to the blocklist and remove the lower-severity threats from it.
D. Review the current blocklist to determine which domains can be removed from the list and then update the ACLs and IPS signatures.
A cybersecurity analyst is establishing a threat-hunting and intelligence group at a growing organization. Which of the following is a collaborative resource that would MOST likely be used for this purpose?
A. IoC feeds
B. CVSS scores
C. Scrum
D. ISAC
Given the Nmap request below:Which of the following actions will an attacker be able to initiate directly against this host?
A. Password sniffing
B. ARP spoofing
C. A brute-force attack
D. An SQL injection
A security analyst receives a CVE bulletin, which lists several products that are used in the enterprise. The analyst immediately deploys a critical security patch. Which of the following BEST describes the reason for the analyst’s immediate action?
A. Nation-state hackers are targeting the region.
B. A new vulnerability was discovered by a vendor.
C. A known exploit was discovered.
D. A new zero-day threat needs to be addressed.
E. There is an insider threat.
Which of the following types of controls defines placing an ACL on a file folder?
A. Technical control
B. Confidentiality control
C. Managerial control
D. Operational control
Which of the following best describes the process by which code is developed, tested, and deployed in small batches?
A. Agile
B. Waterfall
C. SDLC
D. Dynamic code analysis
A company is experiencing a malware attack within its network. A security engineer notices many of the impacted assets are connecting outbound to a number of remote destinations and exfiltrating data. The security engineer also sees that deployed, up-to-date antivirus signatures are ineffective. Which of the following is the BEST approach to prevent any impact to the company from similar attacks in the future?
A. IDS signatures
B. Data loss prevention
C. Port security
D. Sinkholing
A security analyst at an organization is reviewing vulnerability reports from a newly deployed vulnerability management platform. The organization is not receiving information about devices that rarely connect to the network. Which of the following will the analyst most likely do to obtain vulnerability information about these devices?
A. Add administrator credentials to mobile devices.
B. Utilize cloud-based agents.
C. Deploy a VPC in front of a NAC.
D. Implement MDM.
According to a static analysis report for a web application, a dynamic code evaluation script injection vulnerability was found. Which of the following actions is the BEST option to fix the vulnerability in the source code?
A. Delete the vulnerable section of the code immediately.
B. Create a custom rule on the web application firewall.
C. Validate user input before execution and interpretation.
D. Use parameterized queries.
Which of the following can detect vulnerable third-party libraries before code deployment?
A. Impact analysis
B. Dynamic analysis
C. Static analysis
D. Protocol analysis
A security analyst recently implemented a new vulnerability scanning platform. The initial scan of 438 hosts found the following vulnerabilities: • 210 critical • 1,854 high • 1,786 medium • 48 low The analyst is unsure how to handle such a large-scale remediation effort. Which of the following would be the next logical step?
A. Identify the assets with a high value and remediate all vulnerabilities on those hosts.
B. Perform remediation activities for all critical and high vulnerabilities first.
C. Perform a risk calculation to determine the probability and magnitude of exposure.
D. Identify the vulnerabilities that affect the most systems and remediate them first.
Which of the following is MOST dangerous to the client environment during a vulnerability assessment/penetration test?
A. There is a longer period of time to assess the environment.
B. The testing is outside the contractual scope.
C. There is a shorter period of time to assess the environment.
D. No status reports are included with the assessment.
A computer hardware manufacturer is developing a new SoC that will be used by mobile devices. The SoC should not allow users or the process to downgrade from a newer firmware to an older one. Which of the following can the hardware manufacturer implement to prevent firmware downgrades?
A. Encryption
B. eFuse
C. Secure Enclave
D. Trusted execution
A vulnerability assessment solution is hosted in the cloud. This solution will be used as an accurate inventory data source for both the configuration management database and the governance, risk, and compliance tool. An analyst has been asked to automate the data acquisition. Which of the following would be the BEST way to acquire the data?
A. CSV export
B. SOAR
C. API
D. Machine learning
A security analyst is running a tool against an executable of an unknown source. The input supplied by the tool to the executable program and the output from the executable are shown below:Which of the following should the analyst report after viewing this information?
A. A dynamic library that is needed by the executable is missing.
B. Input can be crafted to trigger an injection attack in the executable.
C. The tool caused a buffer overflow in the executable’s memory.
D. The executable attempted to execute a malicious command.
A security engineer is reviewing security products that identify malicious actions by users as part of a company's insider threat program Which of the following is the MOST appropriate product category for this purpose?
A. SCAP
B. SOAR
C. UEBA
D. WAF
Members of the sales team are using email to send sensitive client lists with contact information to their personal accounts. The company's AUP and code of conduct prohibits this practice. Which of the following configuration changes would improve security and help prevent this from occurring?
A. Configure the DLP transport rules to provide deep content analysis.
B. Put employees’ personal email accounts on the mail server on a blocklist.
C. Set up IPS to scan for outbound emails containing names and contact information.
D. Use Group Policy to prevent users from copying and pasting information into emails.
E. Move outbound emails containing names and contact information to a sandbox for further examination.
A security analyst is investigating a reported phishing attempt that was received by many users throughout the company. The text of one of the emails is shown below:Office 365 User, It looks like your account has been locked out. Please click this http://accountfix-office356 com/login.php and follow the prompts to restore access. Regards, Security Team - Due to the size of the company and the high storage requirements, the company does not log DNS requests or perform packet captures of network traffic, but it does log network flow data. Which of the following commands will the analyst most likely execute NEXT?
A. telnet off1ce365.com 25
B. tracert 122.167.40.119
C. curl http://accountfix-office356.com/login.php
D. nslookup accountfix-office356.com
A security analyst discovers suspicious host activity while performing monitoring activities. The analyst pulls a packet capture for the activity and sees the following:Follow TCP stream:
Which of the following describes what has occurred?
A. The host attempted to download an application from utoftor.com.
B. The host downloaded an application from utoftor.com.
C. The host attempted to make a secure connection to utoftor.com.
D. The host rejected the connection from utoftor.com.
A security analyst sees the following OWASP ZAP output from a scan that was performed against a modern version of Windows while testing for client-side vulnerabilities:Which of the following is the MOST likely solution to the listed vulnerability?
A. Enable the browser’s XSS filter.
B. Enable Windows XSS protection.
C. Enable the private browsing mode.
D. Enable server-side XSS protection.
At which of the following phases of the SDLC should security FIRST be involved?
A. Design
B. Maintenance
C. Implementation
D. Analysis
E. Planning
F. Testing
A manufacturing company has joined the information sharing and analysis center for its sector. As a benefit, the company will receive structured IoC data contributed by other members. Which of the following best describes the utility of this data?
A. Other members will have visibility into instances of positive IoC identification within the manufacturing company’s corporate network.
B. The manufacturing company will have access to relevant malware samples from all other manufacturing sector members.
C. Other members will automatically adjust their security postures to defend the manufacturing company’s processes.
D. The manufacturing company can ingest the data and use tools to autogenerate security configurations for all of its infrastructure.
A company’s security administrator needs to automate several security processes related to testing for the existence of changes within the environment. Conditionally, other processes will need to be created based on input from prior processes. Which of the following is the BEST method for accomplishing this task?
A. Machine learning and process monitoring
B. Continuous integration and configuration management
C. API integration and data enrichment
D. Workflow orchestration and scripting
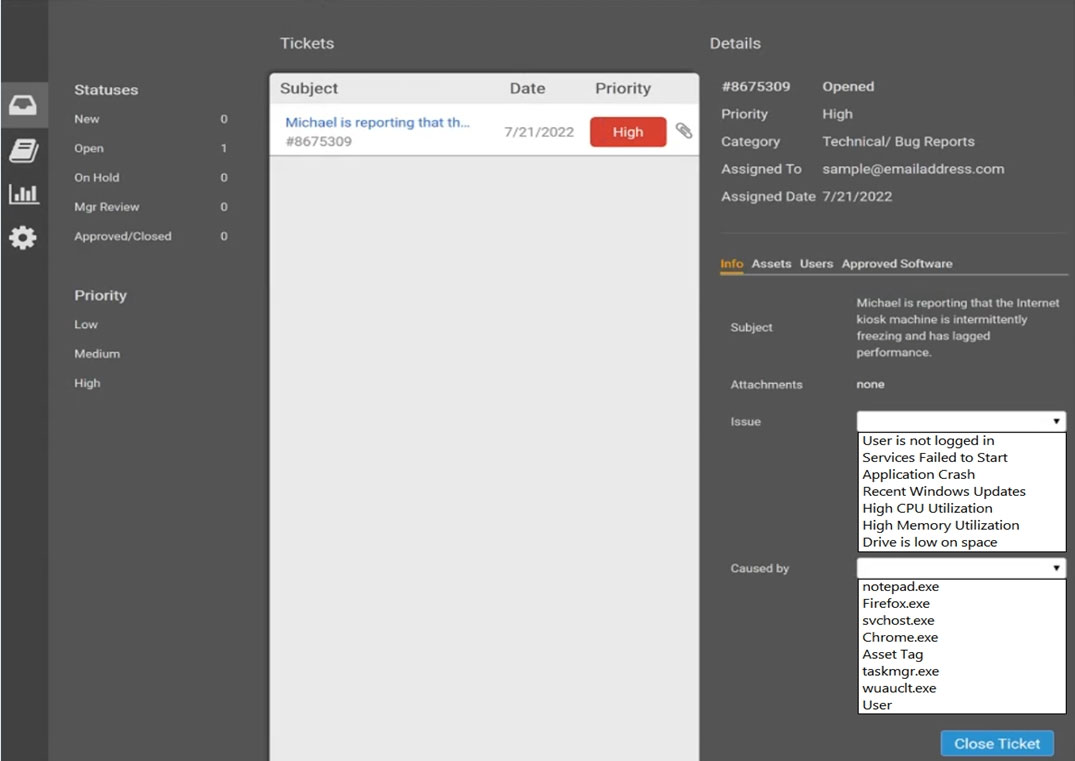
SIMULATION - Welcome to the Enterprise Help Desk System. Please work the ticket escalated to you in the help desk ticket queue. INSTRUCTIONS - Click on the ticket to see the ticket details. Additional content is available on tabs within the ticket. First, select the appropriate issue from the drop-down menu. Then, select the MOST likely root cause from second drop-down menu. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A company offers a hardware security appliance to customers that provides remote administration of a device on the customer's network. Customers are not authorized to alter the configuration. The company deployed a software process to manage unauthorized changes to the appliance, log them, and forward them to a central repository for evaluation. Which of the following processes is the company using to ensure the appliance is not altered from its original configured state?
A. CI/CD
B. Software assurance
C. Anti-tamper
D. Change management
Which of the following organizational initiatives would be MOST impacted by data sovereignty issues?
A. Moving to a cloud-based environment
B. Migrating to locally hosted virtual servers
C. Implementing non-repudiation controls
D. Encrypting local database queries
Which of the following BEST explains the function of a managerial control?
A. To help design and implement the security planning, program development, and maintenance of the security life cycle
B. To guide the development of training, education, security awareness programs, and system maintenance
C. To create data classification, risk assessments, security control reviews, and contingency planning
D. To ensure tactical design, selection of technology to protect data, logical access reviews, and the implementation of audit trails
Due to continued support of legacy applications, an organization's enterprise password complexity rules are inadequate for its required security posture. Which of the following is the BEST compensating control to help reduce authentication compromises?
A. Smart cards
B. Multifactor authentication
C. Biometrics
D. Increased password-rotation frequency
Access Full CS0-002 Dump Free
Looking for even more practice questions? Click here to access the complete CS0-002 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our CS0-002 dump free questions — and get one step closer to exam success!