CS0-001 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your CS0-001 certification? Our CS0-001 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an CS0-001 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our CS0-001 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
A system administrator has reviewed the following output:Which of the following can a system administrator infer from the above output?
A. The company email server is running a non-standard port.
B. The company email server has been compromised.
C. The company is running a vulnerable SSH server.
D. The company web server has been compromised.
A company discovers an unauthorized device accessing network resources through one of many network drops in a common area used by visitors. The company decides that it wants to quickly prevent unauthorized devices from accessing the network but policy prevents the company from making changes on every connecting client. Which of the following should the company implement?
A. Port security
B. WPA2
C. Mandatory Access Control
D. Network Intrusion Prevention
A security analyst at a small regional bank has received an alert that nation states are attempting to infiltrate financial institutions via phishing campaigns. Which of the following techniques should the analyst recommend as a proactive measure to defend against this type of threat?
A. Honeypot
B. Location-based NAC
C. System isolation
D. Mandatory access control
E. Bastion host
A manufacturing company has decided to participate in direct sales of its products to consumers. The company decides to use a subdomain of its main site with its existing cloud service provider as the portal for e-commerce. After launch, the site is stable and functions properly, but after a robust day of sales, the site begins to redirect to a competitor's landing page. Which of the following actions should the company's security team take to determine the cause of the issue and minimize the scope of impact?
A. Engage a third party to provide penetration testing services to see if an exploit can be found
B. Check DNS records to ensure Cname or alias records are in place for the subdomain
C. Query the cloud provider to determine the nature of the DNS attack and find out which other clients are affected
D. Check the DNS records to ensure a correct MX record is established for the subdomain
A security analyst is reviewing packet captures to determine the extent of success during an attacker's reconnaissance phase following a recent incident. The following is a hex and ASCII dump of one such packet:Which of the following BEST describes this packet?
A. DNS BIND version request
B. DNS over UDP standard query
C. DNS over TCP server status query
D. DNS zone transfer request
An analyst was testing the latest version of an internally developed CRM system. The analyst created a basic user account. Using a few tools in Kali's latest distribution, the analyst was able to access configuration files, change permissions on folders and groups, and delete and create new system objects. Which of the following techniques did the analyst use to perform these unauthorized activities?
A. Impersonation
B. Privilege escalation
C. Directory traversal
D. Input injection
As part of an upcoming engagement for a client, an analyst is configuring a penetration testing application to ensure the scan complies with information defined in the SOW. Which of the following types of information should be considered based on information traditionally found in the SOW? (Choose two.)
A. Timing of the scan
B. Contents of the executive summary report
C. Excluded hosts
D. Maintenance windows
E. IPS configuration
F. Incident response policies
An analyst was tasked with providing recommendations of technologies that are PKI X.509 compliant for a variety of secure functions. Which of the following technologies meet the compatibility requirement? (Choose three.)
A. 3DES
B. AES
C. IDEA
D. PKCS
E. PGP
F. SSL/TLS
G. TEMPEST
Which of the following is a vulnerability that is specific to hypervisors?
A. DDoS
B. VLAN hopping
C. Weak encryption
D. WMescape
A company decides to move three of its business applications to different outsourced cloud providers. After moving the applications, the users report the applications time out too quickly and too much time is spent logging back into the different web-based applications throughout the day. Which of the following should a security architect recommend to improve the end-user experience without lowering the security posture?
A. Configure directory services with a federation provider to manage accounts.
B. Create a group policy to extend the default system lockout period.
C. Configure a web browser to cache the user credentials.
D. Configure user accounts for self-service account management.
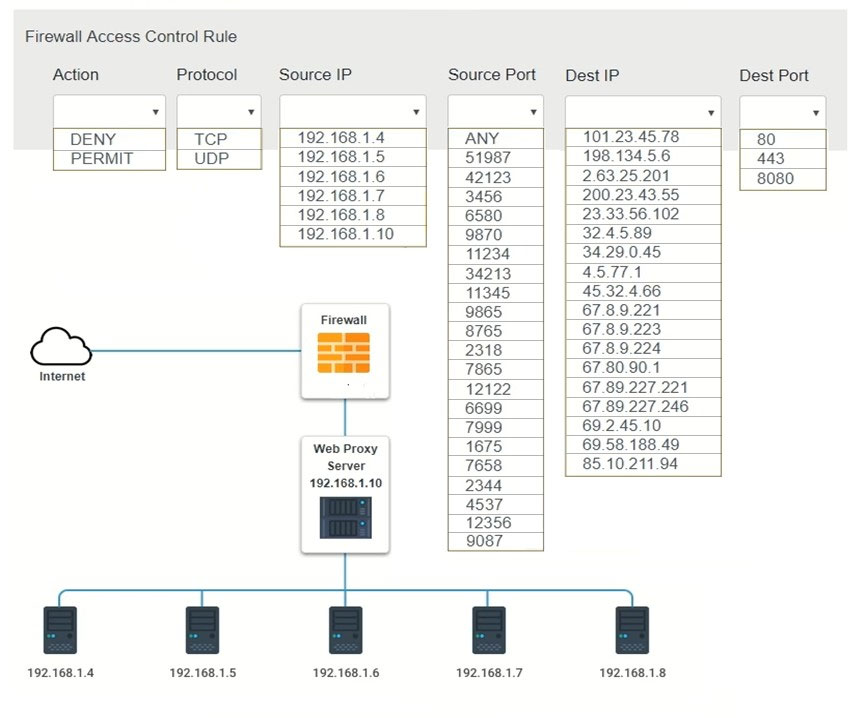
During a review of security controls, an analyst was able to connect to an external, unsecured FTP server from a workstation. The analyst was troubleshooting and reviewed the ACLs of the segment firewall the workstation is connected to:Based on the ACLs above, which of the following explains why the analyst was able to connect to the FTP server?
A. FTP was explicitly allowed in Seq 8 of the ACL.
B. FTP was allowed in Seq 10 of the ACL.
C. FTP was allowed as being included in Seq 3 and Seq 4 of the ACL.
D. FTP was allowed as being outbound from Seq 9 of the ACL.
While preparing for a third-party audit, the vice president of risk management and the vice president of information technology have stipulated that the vendor may not use offensive software during the audit. This is an example of:
A. organizational control.
B. service-level agreement.
C. rules of engagement.
D. risk appetite
An employee was conducting research on the Internet when a message from cyber criminals appeared on the screen, stating the hard drive was just encrypted by a ransomware variant. An analyst observes the following: ✑ Antivirus signatures were updated recently ✑ The desktop background was changed ✑ Web proxy logs show browsing to various information security sites and ad network traffic ✑ There is a high volume of hard disk activity on the file server ✑ SMTP server shown the employee recently received several emails from blocked senders ✑ The company recently switched web hosting providers ✑ There are several IPS alerts for external port scans Which of the following describes how the employee got this type of ransomware?
A. The employee fell victim to a CSRF attack
B. The employee was using another user’s credentials
C. The employee opened an email attachment
D. The employee updated antivirus signatures
A security analyst is creating baseline system images to remediate vulnerabilities found in different operating systems. Each image needs to be scanned before it is deployed. The security analyst must ensure the configurations match industry standard benchmarks and the process can be repeated frequently. Which of the following vulnerability options would BEST create the process requirements?
A. Utilizing an operating system SCAP plugin
B. Utilizing an authorized credential scan
C. Utilizing a non-credential scan
D. Utilizing a known malware plugin
A SIEM analyst noticed a spike in activities from the guest wireless network to several electronic health record (EHR) systems. After further analysis, the analyst discovered that a large volume of data has been uploaded to a cloud provider in the last six months. Which of the following actions should the analyst do FIRST?
A. Contact the Office of Civil Rights (OCR) to report the breach
B. Notify the Chief Privacy Officer (CPO)
C. Activate the incident response plan
D. Put an ACL on the gateway router
A recent vulnerability scan found four vulnerabilities on an organization's public Internet-facing IP addresses. Prioritizing in order to reduce the risk of a breach to the organization, which of the following should be remediated FIRST?
A. A cipher that is known to be cryptographically weak.
B. A website using a self-signed SSL certificate.
C. A buffer overflow that allows remote code execution.
D. An HTTP response that reveals an internal IP address.
A university wants to increase the security posture of its network by implementing vulnerability scans of both centrally managed and student/employee laptops. The solution should be able to scale, provide minimum false positives and high accuracy of results, and be centrally managed through an enterprise console. Which of the following scanning topologies is BEST suited for this environment?
A. A passive scanning engine located at the core of the network infrastructure
B. A combination of cloud-based and server-based scanning engines
C. A combination of server-based and agent-based scanning engines
D. An active scanning engine installed on the enterprise console
When reviewing network traffic, a security analyst detects suspicious activity:Based on the log above, which of the following vulnerability attacks is occurring?
A. ShellShock
B. DROWN
C. Zeus
D. Heartbleed
E. POODLE
The security team for a large, international organization is developing a vulnerability management program. The development staff has expressed concern that the new program will cause service interruptions and downtime as vulnerabilities are remedied. Which of the following should the security team implement FIRST as a core component of the remediation process to address this concern?
A. Automated patch management
B. Change control procedures
C. Security regression testing
D. Isolation of vulnerable servers
A technician at a company's retail store notifies an analyst that disk space is being consumed at a rapid rate on several registers. The uplink back to the corporate office is also saturated frequently. The retail location has no Internet access. An analyst then observes several occasional IPS alerts indicating a server at corporate has been communicating with an address on a watchlist. Netflow data shows large quantities of data transferred at those times. Which of the following is MOST likely causing the issue?
A. A credit card processing file was declined by the card processor and caused transaction logs on the registers to accumulate longer than usual.
B. Ransomware on the corporate network has propagated from the corporate network to the registers and has begun encrypting files there.
C. A penetration test is being run against the registers from the IP address indicated on the watchlist, generating large amounts of traffic and data storage.
D. Malware on a register is scraping credit card data and staging it on a server at the corporate office before uploading it to an attacker-controlled command and control server.
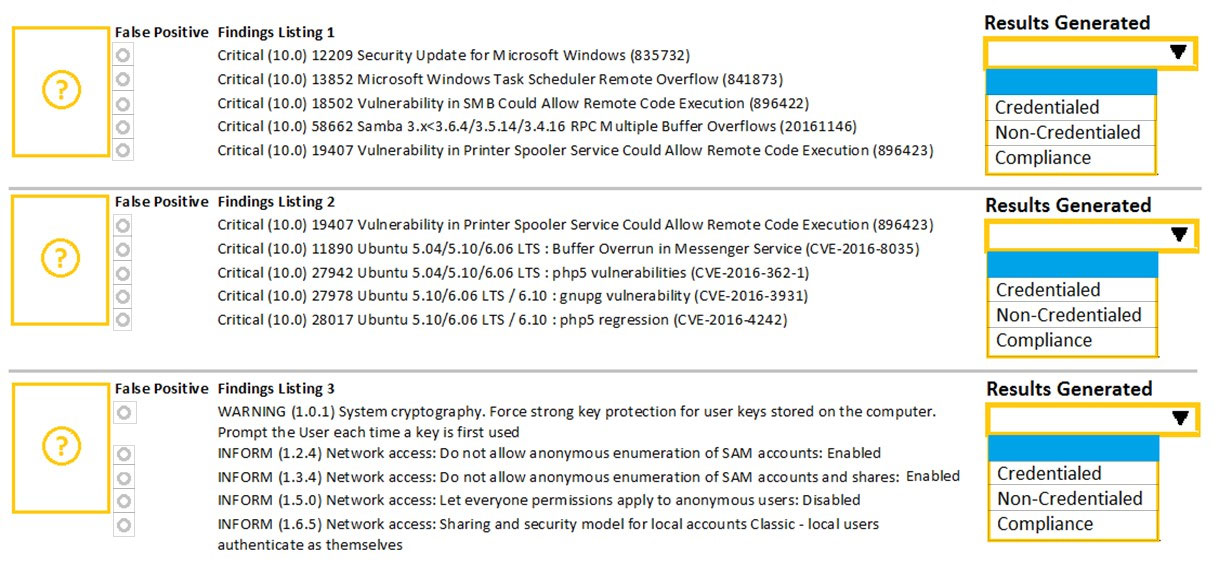
HOTSPOT - A security analyst performs various types of vulnerability scans. Review the vulnerability scan results to determine the type of scan that was executed and if a false positive occurred for each device. Instructions: Select the Results Generated drop-down option to determine if the results were generated from a credentialed scan, non-credentialed scan, or a compliance scan. For ONLY the credentialed and non-credentialed scans, evaluate the results for false positives and check the findings that display false positives. NOTE: If you would like to uncheck an option that is currently selected, click on the option a second time. Lastly, based on the vulnerability scan results, identify the type of Server by dragging the Server to the results. The Linux Web Server, File-Print Server and Directory Server are draggable. If at any time you would like to bring back the initial state of the simulation, please select the Reset All button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.Hot Area:
A software patch has been released to remove vulnerabilities from company's software. A security analyst has been tasked with testing the software to ensure the vulnerabilities have been remediated and the application is still functioning properly. Which of the following tests should be performed NEXT?
A. Fuzzing
B. User acceptance testing
C. Regression testing
D. Penetration testing
Which of the following is a vulnerability when using Windows as a host OS for virtual machines?
A. Windows requires frequent patching.
B. Windows virtualized environments are typically unstable.
C. Windows requires hundreds of open firewall ports to operate.
D. Windows is vulnerable to the “ping of death”.
A company requests a security assessment of its network. Permission is given, but no details are provided. It is discovered that the company has a web presence, and the company's IP address is 70.182.11.4. Which of the following Nmap commands would reveal common open ports and their versions?
A. nmap – oV
B. nmap -vO
C. nmap -sv
An executive tasked a security analyst to aggregate past logs, traffic, and alerts on a particular attack vector. The analyst was then tasked with analyzing the data and making predictions on future complications regarding this attack vector. Which of the following types of analysis is the security analyst MOST likely conducting?
A. Trend analysis
B. Behavior analysis
C. Availability analysis
D. Business analysis
A cybersecurity professional typed in a URL and discovered the admin panel for the e-commerce application is accessible over the open web with the default password. Which of the following is the MOST secure solution to remediate this vulnerability?
A. Rename the URL to a more obscure name, whitelist all corporate IP blocks, and require two-factor authentication.
B. Change the default password, whitelist specific source IP addresses, and require two-factor authentication.
C. Whitelist all corporate IP blocks, require an alphanumeric passphrase for the default password, and require two-factor authentication.
D. Change the username and default password, whitelist specific source IP addresses, and require two-factor authentication.
A cybersecurity analyst is reviewing the following outputs:Which of the following can the analyst infer from the above output?
A. The remote host is redirecting port 80 to port 8080.
B. The remote host is running a service on port 8080.
C. The remote host’s firewall is dropping packets for port 80.
D. The remote host is running a web server on port 80.
A cybersecurity analyst has several log files to review. Instead of using grep and cat commands, the analyst decides to find a better approach to analyze the logs. Given a list of tools, which of the following would provide a more efficient way for the analyst to conduct a timeline analysis, do keyword searches, and output a report?
A. Kali
B. Splunk
C. Syslog
D. OSSIM
An incident response report indicates a virus was introduced through a remote host that was connected to corporate resources. A cybersecurity analyst has been asked for a recommendation to solve this issue. Which of the following should be applied?
A. MAC
B. TAP
C. NAC
D. ACL
A security analyst is reviewing the following log after enabling key-based authentication.Given the above information, which of the following steps should be performed NEXT to secure the system?
A. Disable anonymous SSH logins.
B. Disable password authentication for SSH.
C. Disable SSHv1.
D. Disable remote root SSH logins.
A security analyst has just completed a vulnerability scan of servers that support a business critical application that is managed by an outside vendor. The results of the scan indicate the devices are missing critical patches. Which of the following factors can inhibit remediation of these vulnerabilities? (Choose two.)
A. Inappropriate data classifications
B. SLAs with the supporting vendor
C. Business process interruption
D. Required sandbox testing
E. Incomplete asset inventory
A worm was detected on multiple PCs within the remote office. The security analyst recommended that the remote office be blocked from the corporate network during the incident response. Which of the following processes BEST describes this recommendation?
A. Logical isolation of the remote office
B. Sanitization of the network environment
C. Segmentation of the network
D. Secure disposal of affected systems
An analyst is conducting a log review and identifies the following snippet in one of the logs:Which of the following MOST likely caused this activity?
A. SQL injection
B. Privilege escalation
C. Forgotten password
D. Brute force
A cyber-incident response team is responding to a network intrusion incident on a hospital network. Which of the following must the team prepare to allow the data to be used in court as evidence?
A. Computer forensics form
B. HIPAA response form
C. Chain of custody form
D. Incident form
A technician recently fixed a computer with several viruses and spyware programs on it and notices the Internet settings were set to redirect all traffic through an unknown proxy. This type of attack is known as which of the following?
A. Phishing
B. Social engineering
C. Man-in-the-middle
D. Shoulder surfing
A company installed a wireless network more than a year ago, standardizing on the same model APs in a single subnet. Recently, several users have reported timeouts and connection issues with Internet browsing. The security administrator has gathered some information about the network to try to recreate the issues with the assistance of a user. The administrator is able to ping every device on the network and confirms that the network is very slow.Output:
Given the above results, which of the following should the administrator investigate FIRST?
A. The AP-Workshop device
B. The AP-Reception device
C. The device at 192.168.1.4
D. The AP-IT device
E. The user’s PC
Which of the following describes why it is important to include scope within the rules of engagement of a penetration test?
A. To ensure the network segment being tested has been properly secured
B. To ensure servers are not impacted and service is not degraded
C. To ensure all systems being scanned are owned by the company
D. To ensure sensitive hosts are not scanned
A web developer wants to create a new web part within the company website that aggregates sales from individual team sites. A cybersecurity analyst wants to ensure security measurements are implemented during this process. Which of the following remediation actions should the analyst take to implement a vulnerability management process?
A. Personnel training
B. Vulnerability scan
C. Change management
D. Sandboxing
Due to new regulations, a company has decided to institute an organizational vulnerability management program and assign the function to the security team. Which of the following frameworks would BEST support the program? (Choose two.)
A. COBIT
B. NIST
C. ISO 27000 series
D. ITIL
E. OWASP
Which of the following should be found within an organization's acceptable use policy?
A. Passwords must be eight characters in length and contain at least one special character.
B. Customer data must be handled properly, stored on company servers, and encrypted when possible
C. Administrator accounts must be audited monthly, and inactive accounts should be removed.
D. Consequences of violating the policy could include discipline up to and including termination.
A security analyst receives a mobile device with symptoms of a virus infection. The virus is morphing whenever it is from sandbox to sandbox to analyze. Which of the following will help to identify the number of variations through the analysis life cycle?
A. Journaling
B. Hashing utilities
C. Log viewers
D. OS and process analysis
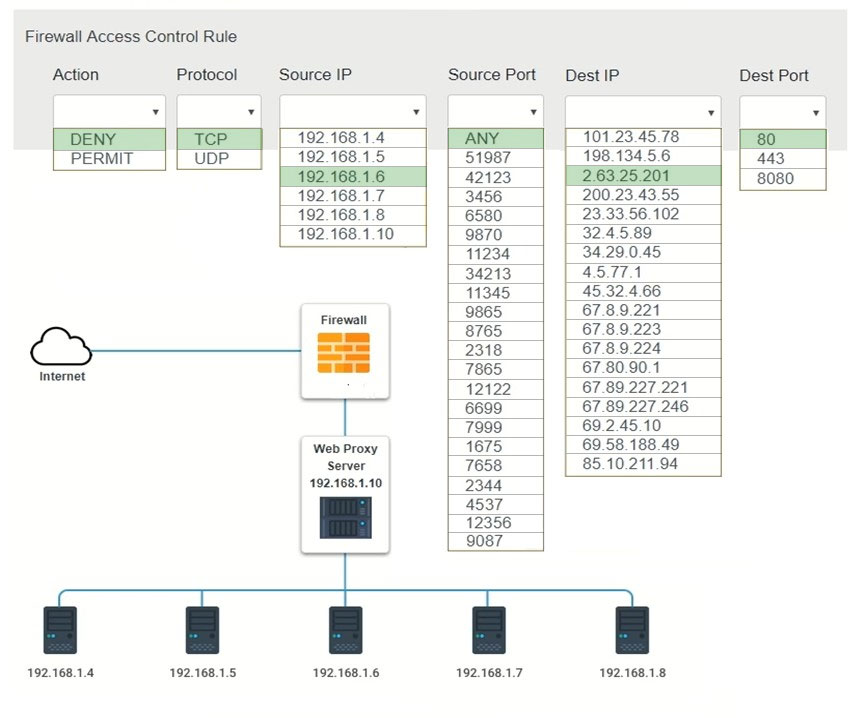
HOTSPOT - A security analyst suspects that a workstation may be beaconing to a command and control server. Inspect the logs from the company's web proxy server and the firewall to determine the best course of action to take in order to neutralize the threat with minimum impact to the organization. Instructions: Modify the firewall ACL, using the Firewall ACL form to mitigate the issue. If at any time you would like to bring back the initial state of the simulation, please select the Reset All button.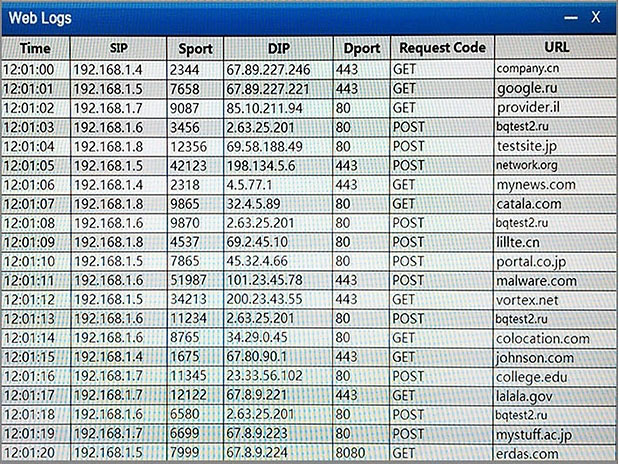
Hot Area:
A human resources employee sends out a mass email to all employees that contains their personnel records. A security analyst is called in to address the concern of the human resources director on how to prevent this from happening in the future. Which of the following would be the BEST solution to recommend to the director?
A. Install a data loss prevention system, and train human resources employees on its use. Provide PII training to all employees at the company. Encrypt PII information.
B. Enforce encryption on all emails sent within the company. Create a PII program and policy on how to handle data. Train all human resources employees.
C. Train all employees. Encrypt data sent on the company network. Bring in privacy personnel to present a plan on how PII should be handled.
D. Install specific equipment to create a human resources policy that protects PII data. Train company employees on how to handle PII data. Outsource all PII to another company. Send the human resources director to training for PII handling.
Using a heuristic system to detect an anomaly in a computer's baseline, a system administrator was able to detect an attack even though the company signature based IDS and antivirus did not detect it. Further analysis revealed that the attacker had downloaded an executable file onto the company PC from the USB port, and executed it to trigger a privilege escalation flaw. Which of the following attacks has MOST likely occurred?
A. Cookie stealing
B. Zero-day
C. Directory traversal
D. XML injection
A cybersecurity analyst was asked to review several results of web vulnerability scan logs. Given the following snippet of code:Which of the following BEST describes the situation and recommendations to be made?
A. The security analyst has discovered an embedded iframe pointing to source IP 65.240.22.1 network. The code should include the domain name. Recommend the entry be updated with the domain name.
B. The security analyst has discovered an embedded iframe that is hidden from users accessing the web page. This code is correct. This is a design preference, and no vulnerabilities are present.
C. The security analyst has discovered an embedded iframe pointing to source IP 65.240.22.1 network. The link is hidden and suspicious. Recommend the entry be removed from the web page.
D. The security analyst has discovered an embedded iframe pointing to source IP 65.240.22.1 network. Recommend making the iframe visible. Fixing the code will correct the issue.
A web application has a newly discovered vulnerability in the authentication method used to validate known company users. The user ID of Admin with a password of "password" grants elevated access to the application over the Internet. Which of the following is the BEST method to discover the vulnerability before a production deployment?
A. Manual peer review
B. User acceptance testing
C. Input validation
D. Stress test the application
A network administrator is attempting to troubleshoot an issue regarding certificates on a secure website. During the troubleshooting process, the network administrator notices that the web gateway proxy on the local network has signed all of the certificates on the local machine. Which of the following describes the type of attack the proxy has been legitimately programmed to perform?
A. Transitive access
B. Spoofing
C. Man-in-the-middle
D. Replay
A security analyst positively identified the threat, vulnerability, and remediation. The analyst is ready to implement the corrective control. Which of the following would be the MOST inhibiting to applying the fix?
A. Requiring a firewall reboot.
B. Resetting all administrator passwords.
C. Business process interruption.
D. Full desktop backups.
A security analyst is reviewing logs and discovers that a company-owned computer issued to an employee is generating many alerts and warnings. The analyst continues to review the log events and discovers that a non-company-owned device from a different, unknown IP address is generating the same events. The analyst informs the manager of these findings, and the manager explains that these activities are already known and part of an ongoing events. Given this scenario, which of the following roles are the analyst, the employee, and the manager filling?
A. The analyst is red team. The employee is blue team. The manager is white team.
B. The analyst is white team. The employee is red team. The manager is blue team.
C. The analyst is red team. The employee is white team. The manager is blue team.
D. The analyst is blue team. The employee is red team. The manager is white team.
A security analyst is assisting in the redesign of a network to make it more secure. The solution should be low cost, and access to the secure segments should be easily monitored, secured, and controlled. Which of the following should be implemented?
A. System isolation
B. Honeyport
C. Jump box
D. Mandatory access control
Access Full CS0-001 Dump Free
Looking for even more practice questions? Click here to access the complete CS0-001 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our CS0-001 dump free questions — and get one step closer to exam success!