CISSP Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your CISSP certification exam? Start your preparation the smart way with our CISSP Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for CISSP exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our CISSP Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
Which factors MUST be considered when classifying information and supporting assets for risk management, legal discovery, and compliance?
A. System owner roles and responsibilities, data handling standards, storage and secure development lifecycle requirements
B. Compliance office roles and responsibilities, classi ed material handling standards, storage system lifecycle requirements
C. Data stewardship roles, data handling and storage standards, data lifecycle requirements
D. System authorization roles and responsibilities, cloud computing standards, lifecycle requirements A
In a DevOps environment, which of the following actions is MOST necessary to have con dence in the quality of the changes being made?
A. Prepare to take corrective actions quickly.
B. Automate functionality testing.
C. Review logs for any anomalies.
D. Receive approval from the change review board.
When implementing single sign-on (SSO) on a network, which authentication approach BEST allows users to use credentials across multiple applications?
A. Public key infrastructure (PKI)
B. Security Assertion Markup Language (SAML)
C. Delegated Identity Management
D. Federated Identity Management
During the change management process, which of the following is used to identify and record new risks?
A. Risk assessment
B. Lessons learned register
C. Risk register
D. Risk report
An organization contracts with a consultant to perform a System Organization Control (SOC) 2 audit on their internal security controls. An auditor documents a nding a related to an Application Programming Interface (API) performing an action that is not aligned with the scope or objective of the system. Which trust service principle would be MOST applicable in th is situation?
A. confidentiality
B. Processing Integrity
C. Security
D. Availability
In a multi-tenant cloud environment, what approach will secure logical access to assets?
A. Controlled configuration management (CM)
B. Transparency/Auditability of administrative access
C. Virtual private cloud (VPC)
D. Hybrid cloud
A senior security engineer has been tasked with ensuring the confidentiality and integrity of the organization's most valuable personally identi able information (PII). This data is stored on local file and database servers within the organization's data center. The following security measures have been implemented to ensure that unauthorized access is detected and logged. · Network segmentation and enhanced access logging of the database and file servers · Implemented encryption of data at rest · Implemented full packet capture of the network traffic in and out of the sensitive network segment · Ensured all transaction log data and packet captures are backed up to corporate backup appliance within the corporate backup network segment Which of the following is the MOST likely way to ex ltrate PII while avoiding detection?
A. Unauthorized access to the file server via Secure Shell (SSH)
B. Unauthorized access to the database server via a compromised web application
C. Unauthorized access to the database server via a compromised user account
D. Unauthorized access to the backup server via a compromised service account
Which of the following is included in change management?
A. Technical review by business owner
B. User Acceptance Testing (UAT) before implementation
C. Cost-benefit analysis (CBA) after implementation
D. Business continuity testing
In systems security engineering, what does the security principle of modularity provide?
A. Minimal access to perform a function
B. Documentation of functions
C. Isolated functions and data
D. Secure distribution of programs and data
Which of the following is an example of a vulnerability of full-disk encryption (FDE)?
A. Data on the device cannot be restored from backup.
B. Data on the device cannot be backed up.
C. Data in transit has been compromised when the user has authenticated to the device.
D. Data at rest has been compromised when the user has authenticated to the device.
What is the MAIN purpose of a security assessment plan?
A. Provide education to employees on security and privacy, to ensure their awareness on policies and procedures.
B. Provide the objectives for the security and privacy control assessments and a detailed roadmap of how to conduct such assessments.
C. Provide guidance on security requirements, to ensure the identified security risks are properly addressed based on the recommendation.
D. Provide technical information to executives to help them understand information security postures and secure funding.
Which of the following is a term used to describe maintaining ongoing awareness of information security, vulnerabilities, and threats to support organizational risk management decisions?
A. Information Security Continuous Monitoring (ISCM)
B. Risk Management Framework (RMF)
C. Information Sharing & Analysis Centers (ISAC)
D. Information Security Management System (ISMS)
Which of the following would be the BEST guideline to follow when attempting to avoid the exposure of sensitive data?
A. Monitor mail servers for sensitive data being ex ltrated.
B. Educate end-users on methods of attacks on sensitive data.
C. Establish report parameters for sensitive data.
D. Store sensitive data only when necessary.
Which of the following is the MOST important consideration in selecting a security testing method based on different Radio-Frequency identification (RFID) vulnerability types?
A. An understanding of the attack surface
B. Adaptability of testing tools to multiple technologies
C. The quality of results and usability of tools
D. The performance and resource utilization of tools
Which of the following BEST represents a defense in depth concept?
A. Network-based data loss prevention (DLP), Network Access Control (NAC), network-based Intrusion prevention system (NIPS), Port security on core switches
B. Host-based data loss prevention (DLP), Endpoint anti-malware solution, Host-based integrity checker, Laptop locks, hard disk drive (HDD) encryption
C. Endpoint security management, network intrusion detection system (NIDS), Network Access Control (NAC), Privileged Access Management (PAM), security information and event management (SIEM)
D. Web application firewall (WAF), Gateway network device tuning, Database firewall, Next-Generation Firewall (NGFW), Tier-2 demilitarized zone (DMZ) tuning
An organization has determined that its previous waterfall approach to software development is not keeping pace with business demands. To adapt to the rapid changes required for product delivery, the organization has decided to move towards an Agile software development and release cycle. In order to ensure the success of the Agile methodology, who is the MOST critical in creating acceptance criteria for each release?
A. Business customers
B. Software developers
C. Independent testers
D. Project managers
Which of the following events prompts a review of the disaster recovery plan (DRP)?
A. Change in senior management
B. Completion of the security policy review
C. Organizational merger
D. New members added to the steering committee
A client server infrastructure that provides user-to-server authentication describes which one of the following?
A. Secure Sockets Layer (SSL)
B. User-based authorization
C. Kerberos
D. X.509
Which is the BEST control to meet the Statement on Standards for Attestation Engagements 18 (SSAE-18) confidentiality category?
A. File hashing
B. Storage encryption
C. Data retention policy
D. Data processing
An organization is implementing data encryption using symmetric ciphers and the Chief Information officer (CIO) is concerned about the risk of using one key to protect all sensitive data. The security practitioner has been tasked with recommending a solution to address the CIO's concerns. Which of the following is the BEST approach to achieving the objective by encrypting all sensitive data?
A. Use a Secure Hash Algorithm 256 (SHA-256).
B. Use Rivest-Shamir-Adleman (RSA) keys.
C. Use a hierarchy of encryption keys.
D. Use Hash Message Authentication Code (HMAC) keys.
While reviewing a web application-to-application connection, a security professional finds the use of Representational State Transfer (REST) application programming interfaces (API) and identifies it as secure. Which one of the following connection Uniform Resource Locators (URL) applies to this scenario?
A. https://url.com/Resources//action?apiKey=a399ikjiuynj
B. http://url.com/SecureTLS//action
C. http://url.com/Resources//action?apiKey=a399ikjiuynj
D. https://url.com/Resources//action
A vendor released a security patch for a dangerous vulnerability affecting thousands of computers in an organization. Which of the following actions will the security practitioner do FIRST to mitigate the security risk?
A. Deploy the patch.
B. Accept the risk.
C. Transfer the risk.
D. Evaluate the patch.
Which of the following services can be deployed via a cloud service or on-premises to integrate with Identity as a Service (IDaaS) as the authoritative source of user identities?
A. Multi-factor authentication (MFA)
B. Directory
C. User database
D. Single sign-on (SSO)
Which of the following contributes MOST to the effectiveness of a security officer?
A. Developing precise and practical security plans
B. Integrating security into the business strategies
C. Understanding the regulatory environment
D. Analyzing the strengths and weakness of the organization
Which of the following measures is the MOST critical in order to safeguard from a malware attack on a smartphone?
A. Enable strong password.
B. Install anti-virus for mobile.
C. Enable biometric authentication.
D. Prevent jailbreaking or rooting.
Why is it important that senior management clearly communicates the formal Maximum Tolerable Downtime (MTD) decision?
A. To provide each manager with precise direction on selecting an appropriate recovery alternative
B. To demonstrate to the board of directors that senior management is committed to continuity recovery efforts
C. To provide a formal declaration from senior management as required by internal audit to demonstrate sound business practices
D. To demonstrate to the regulatory bodies that the company takes business continuity seriously D
An organization implements Network Access Control (NAC) using Institute of Electrical and Electronics Engineers (IEEE) 802.1x and discovers the printers do not support the IEEE 802.1x standard. Which of the following is the BEST resolution?
A. Implement port security on the switch ports for the printers.
B. Do nothing; IEEE 802.1x is irrelevant to printers.
C. Install an IEEE 802.1x bridge for the printers.
D. Implement a virtual local area network (VLAN) for the printers.
What is the FIRST step for an organization to take before allowing personnel to access social media from a corporate device or user account?
A. Publish an acceptable usage policy.
B. Publish a social media guidelines document.
C. Deliver security awareness training.
D. Document a procedure for accessing social media sites.
The Chief Information Security officer (CISO) is concerned about business application availability. The organization was recently subject to a ransomware attack that resulted in the unavailability of applications and services for 10 working days that required paper-based running of all main business processes. There are now aggressive plans to enhance the Recovery Time Objective (RTO) and cater for more frequent data captures. Which of the following solutions should be implemented to fully comply to the new business requirements?
A. Virtualization
B. Antivirus
C. Host-based intrusion prevention system (HIPS)
D. Process isolation
Which of the following is the MOST effective way to ensure the endpoint devices used by remote users are compliant with an organization's approved policies before being allowed on the network?
A. Network Access Control (NAC)
B. Privileged Access Management (PAM)
C. Group Policy Object (GPO)
D. Mobile Device Management (MDM)
Which reporting type requires a service organization to describe its system and define its control objectives and controls that are relevant to users' internal control over financial reporting?
A. Statement on Auditing Standards (SAS) 70
B. Service Organization Control 1 (SOC1)
C. Service Organization Control 2 (SOC2)
D. Service Organization Control 3 (SOC3)
To monitor the security of buried data lines inside the perimeter of a facility, which of the following is the MOST effective control?
A. Fencing around the facility with closed-circuit television (CCTV) cameras at all entry points
B. Ground sensors installed and reporting to a security event management (SEM) system
C. Regular sweeps of the perimeter, including manual inspection of the cable ingress points
D. Steel casing around the facility ingress points
What Hypertext Transfer Protocol (HTTP) response header can be used to disable the execution of inline JavaScript and the execution of eval()- type functions?
A. X-XSS-Protection
B. Content-Security-Policy
C. X-Frame-Options
D. Strict-Transport-Security
Which of the following is a MAJOR consideration in implementing a Voice over Internet Protocol (VoIP) network?
A. Use of Request for Comments (RFC) 1918 addressing.
B. Use of Network Access Control (NAC) on switches.
C. Use of separation for the voice network.
D. Use of a unified messaging.
Which of the following are key activities when conducting a security assessment?
A. Schedule, collect, examine
B. Interview, examine, simulate
C. Collect, interview, test
D. Examine, interview, test
An enterprise is developing a baseline cybersecurity standard its suppliers must meet before being awarded a contract. Which of the following statements is TRUE about the baseline cybersecurity standard?
A. It should be expressed as general requirements.
B. It should be expressed as technical requirements.
C. It should be expressed in business terminology.
D. It should be expressed in legal terminology.
The security team is noti ed that a device on the network is infected with malware. Which of the following is MOST effective in enabling the device to be quickly located and remediated?
A. Data loss protection (DLP)
B. Intrusion detection
C. Vulnerability scanner
D. Information Technology Asset Management (ITAM)
A company is enrolled in a hard drive reuse program where decommissioned equipment is sold back to the vendor when it is no longer needed. The vendor pays more money for functioning drives than equipment that is no longer operational. Which method of data sanitization would provide the most secure means of preventing unauthorized data loss, while also receiving the most money from the vendor?
A. Pinning
B. Single-pass wipe
C. Multi-pass wipes
D. Degaussing
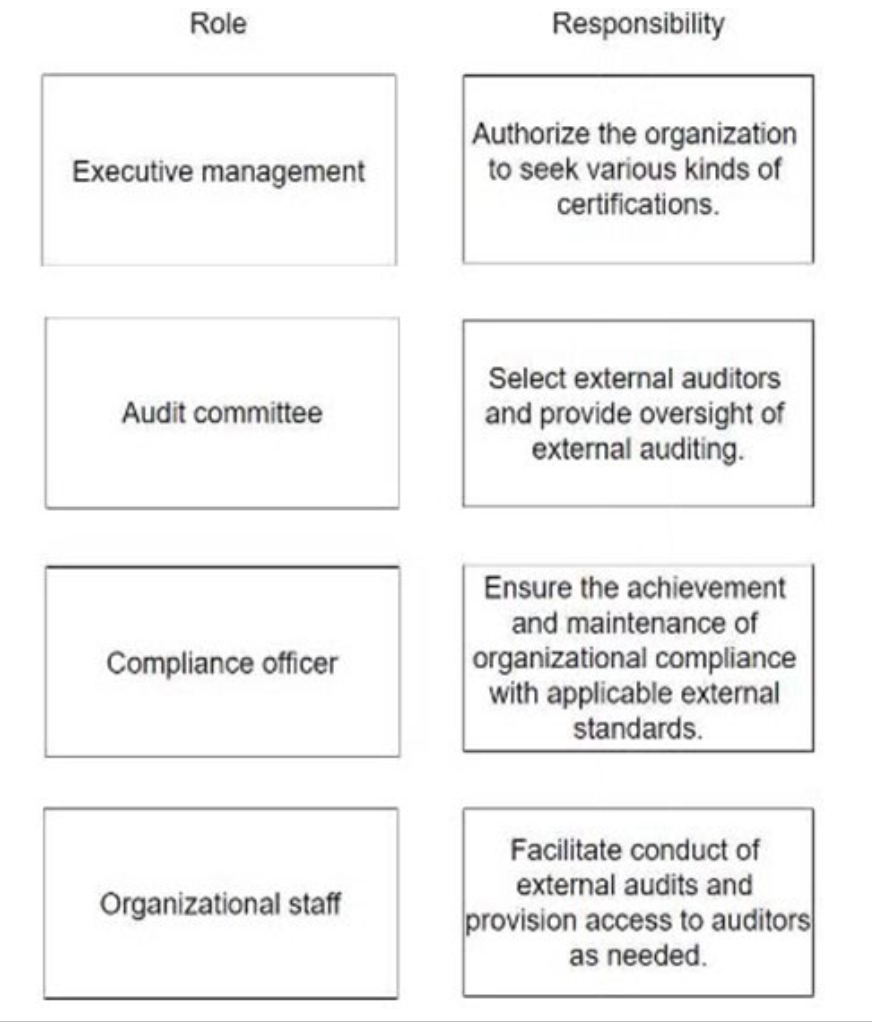
DRAG DROP - Match the roles for an external audit to the appropriate responsibilities. Drag each role on the left to its corresponding responsibility on the right. Select and Place: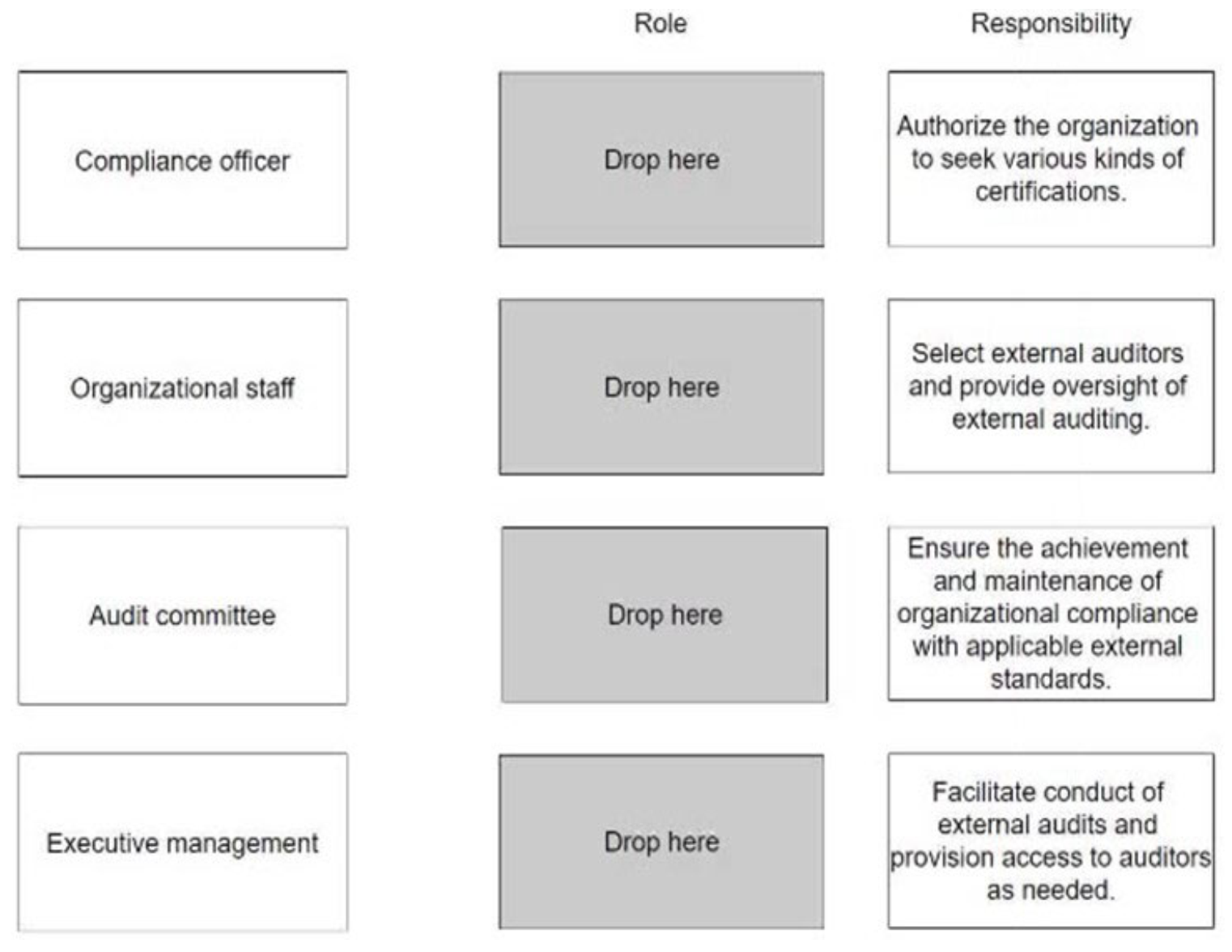
Which of the following is the PRIMARY objective of performing scans with an active discovery tool?
A. Discovering virus and malware activity
B. Discovering changes for security configuration management (CM)
C. Asset identification (ID) and inventory management
D. Vulnerability management and remediation
Why is data classification control important to an organization?
A. To enable data discovery
B. To ensure security controls align with organizational risk appetite
C. To ensure its integrity, confidentiality and availability
D. To control data retention in alignment with organizational policies and regulation B
Which of the following attack types can be used to compromise the integrity of data during transmission?
A. Synchronization flooding
B. Session hijacking
C. Keylogging
D. Packet sni ng
When designing a new Voice over Internet Protocol (VoIP) network, an organization's top concern is preventing unauthorized users accessing the VoIP network. Which of the following will BEST help secure the VoIP network?
A. 802.11g
B. Web application firewall (WAF)
C. Transport Layer Security (TLS)
D. 802.1x
To minimize the vulnerabilities of a web-based application, which of the following FIRST actions will lock down the system and minimize the risk of an attack?
A. Apply the latest vendor patches and updates
B. Run a vulnerability scanner
C. Review access controls
D. Install an antivirus on the server
Dumpster diving is a technique used in which stage of penetration testing methodology?
A. Attack
B. Reporting
C. Planning
D. Discovery
The security organization is looking for a solution that could help them determine with a strong level of con dence that attackers have breached their network. Which solution is MOST effective at discovering a successful network breach?
A. Developing a sandbox
B. Installing an intrusion detection system (IDS)
C. Deploying a honeypot
D. Installing an intrusion prevention system (IPS)
What documentation is produced FIRST when performing an effective physical loss control process?
A. Deterrent controls list
B. Security standards list
C. Asset valuation list
D. Inventory list
During a disruptive event, which security continuity objectives will maintain an organization's information security to a predetermined level?
A. Disaster recovery plan (DRP)
B. Impact assessment report
C. Information security continuity plan
D. Business continuity plan (BCP)
Which of the following methods provides the MOST protection for user credentials?
A. Forms-based authentication
B. Self-registration
C. Basic authentication
D. Digest authentication
Which of the following is the MOST comprehensive Business Continuity (BC) test?
A. Full interruption
B. Full simulation
C. Full table top
D. Full functional drill
Access Full CISSP Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete CISSP Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our CISSP mock test free today—and take a major step toward exam success!