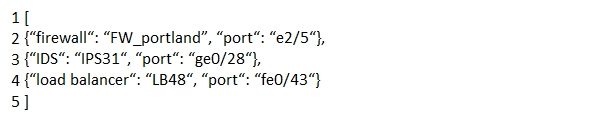CCNA Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the CCNA exam? Start with our CCNA Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a CCNA practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free CCNA practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
Which protocol requires authentication to transfer a backup configuration file from a router to a remote server?
A. FTP
B. SMTP
C. TFTP
D. DTP
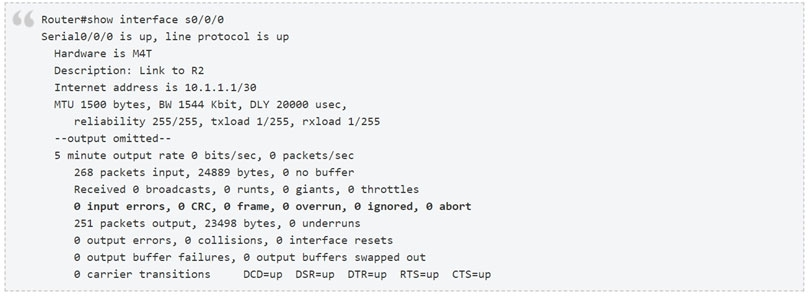
A frame that enters a switch fails the Frame Check Sequence. Which two interface counters are incremented? (Choose two.)
A. input errors
B. frame
C. giants
D. CRC
E. runts
Whenever the physical transmission has problems, the receiving device might receive a frame whose bits have changed values. These frames do not pass the error detection logic as implemented in the FCS field in the Ethernet trailer. The receiving device discards the frame and counts it as some kind of input error.
Cisco switches list this error as a CRC error. Cyclic redundancy check (CRC) is a term related to how the FCS math detects an error.
The input errors includes runts, giants, no buffer, CRC, frame, overrun, and ignored counts.
The output below show the interface counters with the show interface s0/0/0 command:
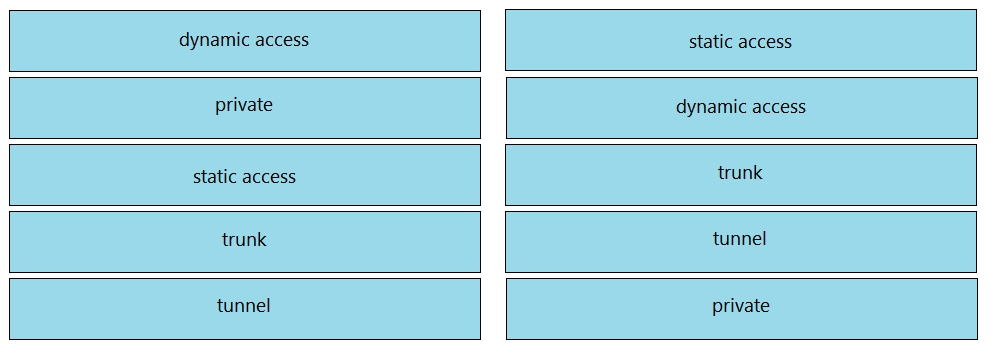
DRAG DROP Drag and drop the VLAN port modes from the left onto the descriptions on the right.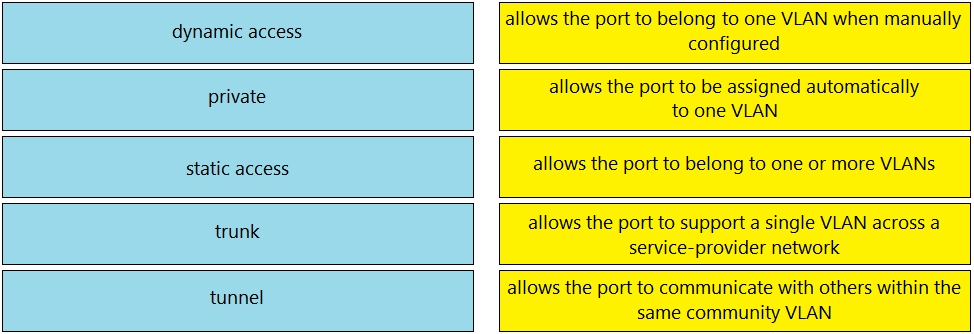
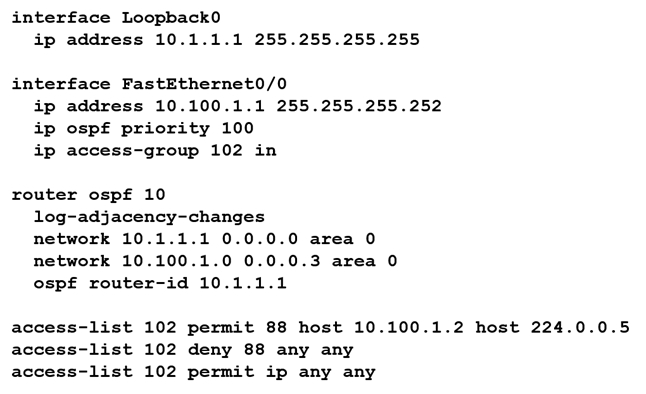
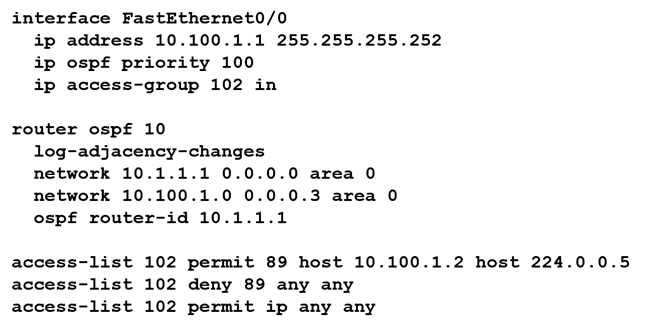
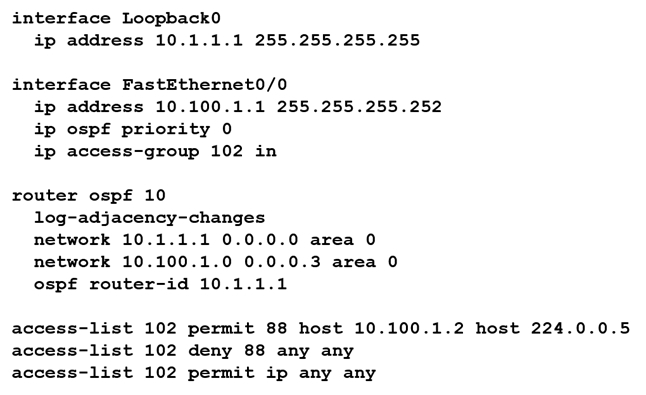
Refer to the exhibit. An OSPF neighbor relationship must be configured using these guidelines: R1 is only permitted to establish a neighbor with R2. R1 will never participate in DR elections. R1 will use a router-id of 10.1.1.1. Which configuration must be used?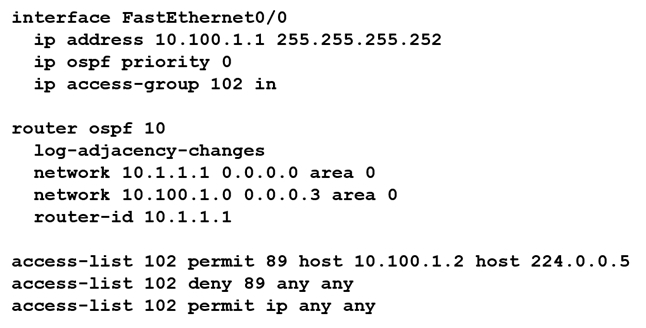
0 How does frame switching function on a switch?
A. oods unknown destinations to all ports except the receiving port
B. modifies frames that contain a known source VLAN
C. rewrites the source and destination MAC address
D. buffers and forwards frames with less than 5 CRCs
SIMULATION - Guidelines - This is a lab item in which tasks will be performed on virtual devices. • Refer to the Tasks tab to view the tasks for this lab item. • Refer to the Topology tab to access the device console(s) and perform the tasks. • Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window. • All necessary preconfigurations have been applied. • Do not change the enable password or hostname for any device. • Save your configurations to NVRAM before moving to the next item. • Click Next at the bottom of the screen to submit this lab and move to the next question. • When Next is clicked, the lab doses and cannot be reopened. Topology -Tasks - SW-3 and SW-4 are preconfigured with all necessary commands. All physical cabling is in place and verified. All connectivity must be operational. 1. Configure both SW-1 and SW-2 switch ports e0/0 and e0/1 for 802.1q trunking with only VLANS 1, 12, and 22 permitted. 2. Configure SW-1 port e0/2 for 802.1q trunking and include only VLANS 12 and 22. 3. Configure both SW-1 and SW-2 switch ports e0/0 and e0/1 for link aggregation using the industry standard protocol. All ports must be configured so that they immediately negotiate the link.
A router has two static routes to the same destination network under the same OSPF process. How does the router forward packets to the destination if the net- hop devices are different?
A. The router chooses the route with the oldest age.
B. The router chooses the next hop with the lowest IP address.
C. The router chooses the next hop with the lowest MAC address.
D. The router load-balances traffic over all routes to the destination.
Refer to the exhibit. A Cisco WLC administrator is creating a new wireless network with enhanced SSID security. The new network must operate at 2.4 Ghz with 54 Mbps of throughput. Which set of tasks must the administrator perform to complete the configuration?
A. Uncheck the Broadcast SSID check box and set the Radio Policy to 802.11a/g only.
B. Check the Broadcast SSID check box and set the Radio Policy to 802.11g only.
C. Uncheck the Broadcast SSID check box and set the Radio Policy to 802.11g only.
D. Check the Broadcast SSID check box and set the Radio Policy to 802.11a only.
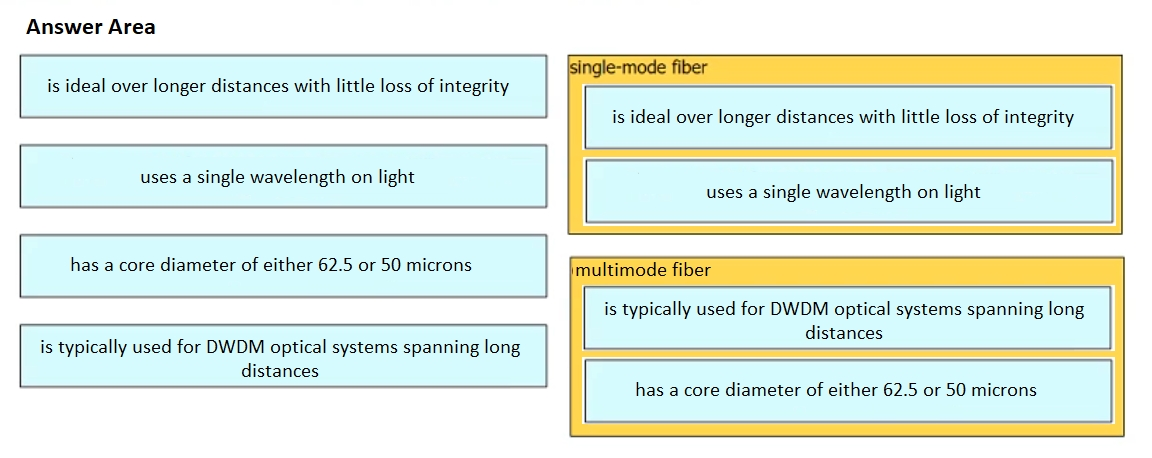
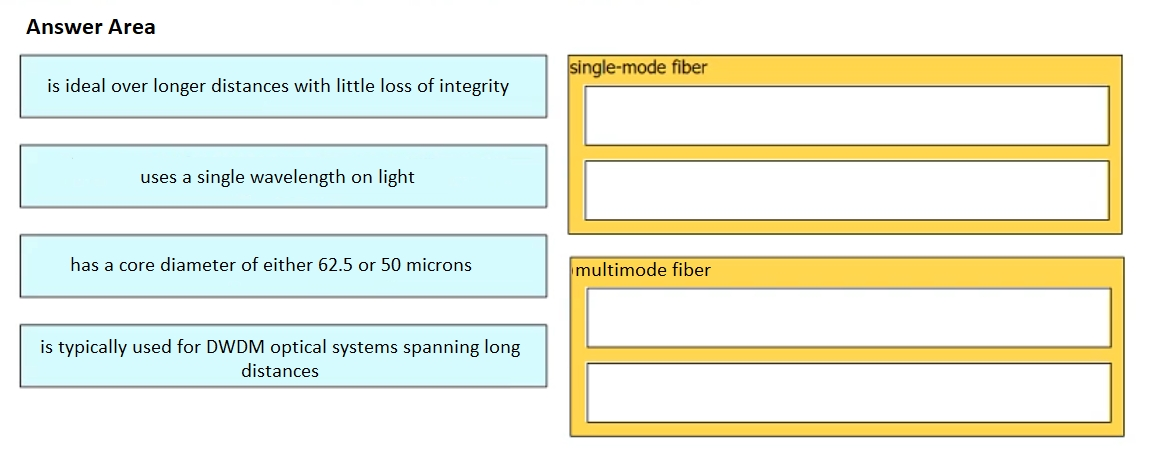
Drag and drop the characteristic from the left onto the cable type on the right.
Select and Place:
Refer to the exhibit. Which change to the configuration on Switch2 allows the two switches to establish an EtherChannel?
A. Change the LACP mode to desirable
B. Change the protocol to PAgP and use auto mode
C. Change the LACP mode to active
D. Change the protocol to EtherChannel mode on
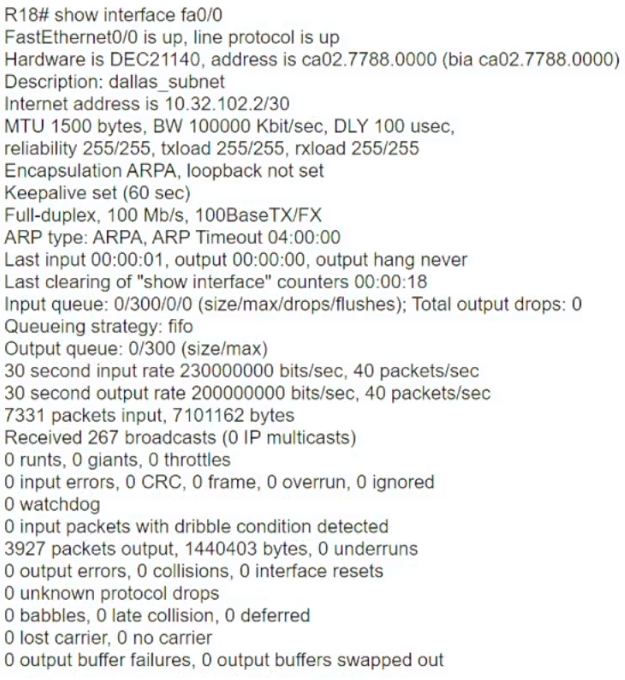
Which interface condition is occurring in this output?
A. bad NIC
B. broadcast storm
C. duplex mismatch
D. high throughput
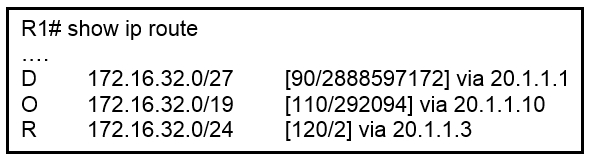
Refer to the exhibit. Router R1 is running three different routing protocols. Which route characteristic is used by the router to forward the packet that it receives for destination IP 172.16.32.1?
A. longest prefix
B. administrative distance
C. cost
D. metric
Which Cisco proprietary protocol ensures traffic recovers immediately, transparently, and automatically when edge devices or access circuits fail?
A. FHRP
B. VRRP
C. HSRP
D. SLB
How does encryption protect the wireless network?
A. via integrity checks to identify wireless forgery attacks in the frame
B. via an algorithm to change wireless data so that only the access point and client understand it
C. via specific ciphers to detect and prevent zero-day network attacks
D. via a policy to prevent unauthorized users from communicating on the wireless network
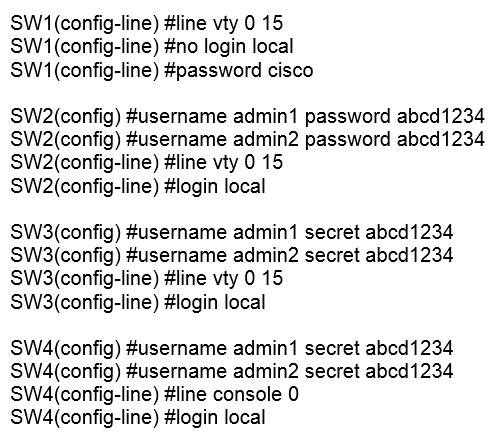
Refer to the exhibit. An administrator configures four switches for local authentication using passwords that are stored as a cryptographic hash. The four switches must also support SSH access for administrators to manage the network infrastructure. Which switch is configured correctly to meet these requirements?
A. SW1
B. SW2
C. SW3
D. SW4
Which API is used in controller-based architectures to interact with edge devices?
A. southbound
B. overlay
C. northbound
D. underlay
What is a function spine-and-leaf architecture?
A. Offers predictable latency of the traffic path between end devices.
B. Exclusively sends multicast traffic between servers that are directly connected to the spine.
C. Mitigates oversubscription by adding a layer of leaf switches.
D. Limits payload size of traffic within the leaf layer.
A WLC sends alarms about a rogue AP, and the network administrator verifies that the alarms are caused by a legitimate autonomous AP. How must the alarms be stopped for the MAC address of the AP?
A. Remove the AP from WLC management
B. Place the AP into manual containment.
C. Manually remove the AP from Pending state.
D. Set the AP Class Type to Friendly.
How does MAC learning function on a switch?
A. associates the MAC address with the port on which it is received
B. rewrites the source and destination MAC address
C. broadcasts frames to all ports without queueing
D. sends an ARP request to locate unknown destinations
What is the difference regarding reliability and communication type between TCP and UDP?
A. TCP is reliable and is a connectionless protocol; UDP is not reliable and is a connection-oriented protocol.
B. TCP is not reliable and is a connectionless protocol; UDP is reliable and is a connection-oriented protocol.
C. TCP is not reliable and is a connection-oriented protocol; UDP is reliable and is a connectionless protocol.
D. TCP is reliable and is a connection-oriented protocol; UDP is not reliable and is a connectionless protocol.
Which QoS per-hop behavior changes the value of the ToS field in the IPv4 packet header?
A. Shaping
B. Policing
C. classification
D. Marking
Which two VLAN IDs indicate a default VLAN? (Choose two.)
A. 0
B. 1
C. 1005
D. 1006
E. 4096
Refer to the exhibit. Which command configures a floating static route to provide a backup to the primary link?
A. ip route 209.165.200.224 255.255.255.224 209.165.202.129 254
B. ip route 209.165.201.0 255.255.255.224 209.165.202.130
C. ip route 0.0.0.0 0.0.0.0 209.165.200.224
D. ip route 0.0.0.0 0.0.0.0 209.165.202.131
What is the path for traffic sent from one user workstation to another workstation on a separate switch in a three-tier architecture model?
A. access ” core ” access
B. access ” distribution ” distribution ” access
C. access ” core ” distribution ” access
D. access ” distribution ” core ” distribution ” access
Refer to the exhibit. If the network environment is operating normally, which type of device must be connected to interface fastethernet 0/1?
A. DHCP client
B. access point
C. router
D. PC
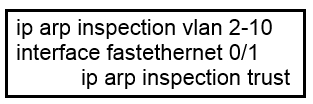
Refer to the exhibit. What is the effect of this configuration?
A. The switch discards all ingress ARP traffic with invalid MAC-to-IP address bindings.
B. All ARP packets are dropped by the switch.
C. Egress traffic is passed only if the destination is a DHCP server.
D. All ingress and egress traffic is dropped because the interface is untrusted.
Dynamic ARP inspection is an ingress security feature; it does not perform any egress checking.
Drag and drop the characteristic from the left onto the IPv6 address type on the right.
Select and Place:
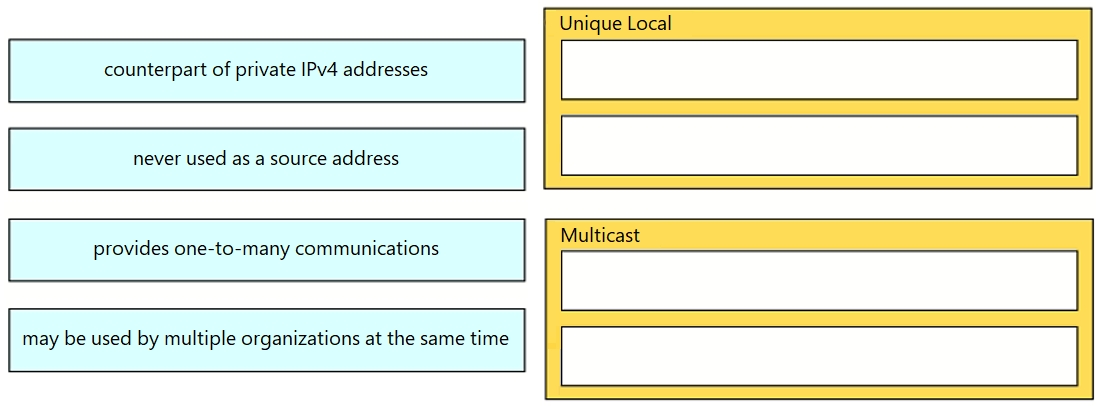
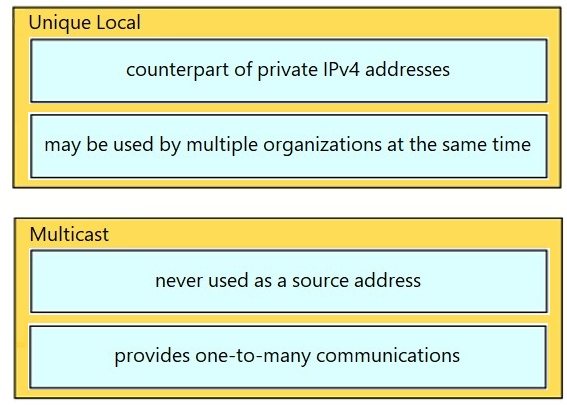
Drag and drop the IPv6 addresses from the left onto the corresponding address types on the right.
Select and Place:


You have two paths for the 10.10.10.0 network - one that has a feasible distance of 3072 and the other of 6144. What do you need to do to load balance your EIGRP routes?
A. Change the maximum paths to 2
B. Change the configuration so they both have the same feasible distance
C. Change the variance for the path that has a feasible distance of 3072 to 2
D. Change the IP addresses so both paths have the same source IP address
0 What are two reasons to configure PortFast on a switch port attached to an end host? (Choose two.)
A. to block another switch or host from communicating through the port
B. to enable the port to enter the forwarding state immediately when the host boots up
C. to prevent the port from participating in Spanning Tree Protocol operations
D. to protect the operation of the port from topology change processes
E. to limit the number of MAC addresses learned on the port to 1
Which interface is used to send traffic to the destination network?
A. G0/6
B. G0/3
C. G0/16
D. G0/23
Which interface condition is occurring in this output?
A. bad NIC
B. broadcast storm
C. duplex mismatch
D. high throughput
SIMULATION - Guidelines - This is a lab item in which tasks will be performed on virtual devices. • Refer to the Tasks tab to view the tasks for this lab item. • Refer to the Topology lab to access the device console(s) and perform the tasks. • Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window. • All necessary preconfigurations have been applied. • Do not change the enable password or hostname for any device. • Save your configurations to NVRAM before moving to the next item. • Click Next at the bottom of the screen to submit this lab and move to the next question. • When Next is clicked, the lab closes and cannot be reopened. Topology -Tasks - All physical cabling is in place and verified. Router R1 is configured and passing traffic for VLANs 5 and 6. All relevant ports are pre-configured as 802.1q trunks. 1. Configure SW-1 port E0/0 to permit only VLANS 5 and 6 2. Configure both SW-1 and SW-2's E0/1 ports to send and receive untagged traffic over VLAN 77 3. Configure SW-2 E0/2 port to permit only VLAN 6 4. Configure both SW-3 and SW-4 ports e0/0 and e0/1 for link aggregation using the industry standard protocol with the following requirements: o SW-3 ports must immediately negotiate the aggregation protocol o SW-4 ports must not initiate the negotiation for the aggregation protocol o Use the designated number assignment
Which CRUD operation corresponds to the HTTP GET method?
A. create
B. read
C. delete
D. update
Which type of attack is mitigated by dynamic ARP inspection?
A. DDoS
B. malware
C. man-in-the-middle
D. worm
Which MAC address is recognized as a VRRP virtual address?
A. 0000.5E00.010a
B. 0005.3709.8968
C. 0000.0C07.AC99
D. 0007.C070.AB01
Why would an administrator choose to implement an automated network management solution?
A. to reduce operational costs
B. to support simpler password policies
C. to enable “box by box” configuration and deployment
D. to limit recurrent management costs
What is a characteristic of an SSID in wireless networks?
A. allows easy file sharing between endpoints
B. provides protection against spyware
C. associates a name to a wireless network
D. eliminates network piggybacking
Which two actions influence the EIGRP route selection process? (Choose two.)
A. The advertised distance is calculated by a downstream neighbor to inform the local router of the bandwidth on the link.
B. The router calculates the feasible distance of all paths to the destination route.
C. The router must use the advertised distance as the metric for any given route.
D. The router calculates the best backup path to the destination route and assigns it as the feasible successor.
E. The router calculates the reported distance by multiplying the delay on the exiting interface by 256.
The reported distance (or advertised distance) is the cost from the neighbor to the destination. It is calculated from the router advertising the route to the network.
For example in the topology below, suppose router A & B are exchanging their routing tables for the first time. Router B says Hey, the best metric (cost) from me to IOWA is 50 and the metric from you to IOWA is 90 and advertises it to router
F. Router A considers the first metric (50) as the Advertised distance. The second metric (90), which is from NEVADA to IOWA (through IDAHO), is called the Feasible distance.
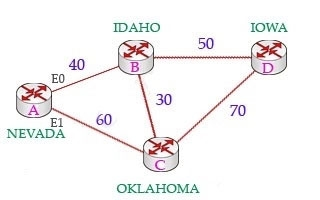
The reported distance is calculated in the same way of calculating the metric. By default (K1 = 1, K2 = 0, K3 = 1, K4 = 0, K5 = 0), the metric is calculated as follows:

Feasible successor is the backup route. To be a feasible successor, the route must have an Advertised distance (AD) less than the Feasible distance (FD) of the current successor route.
Feasible distance (FD): The sum of the AD plus the cost between the local router and the next-hop router. The router must calculate the FD of all paths to choose the best path to put into the routing table.
Note: Although the new CCNA exam does not have EIGRP topic but you should learn the basic knowledge of this routing protocol.
Refer to the exhibit. Local access for R4 must be established and these requirements must be met: · Only Telnet access is allowed. · The enable password must be stored securely. · The enable password must be applied in plain text. · Full access to R4 must be permitted upon successful login. Which configuration script meets the requirements?
A. !
conf t
username test1 password testpass1
enable secret level 15 0 Test123
line vty 0 15
login local
transport input telnet
B. !
config t
username test1 password testpass1
enable password level 15 0 Test123
line vty 0 15
login local
transport input all
C. !
config t
username test1 password testpass1
enable password level 1 7 Test123
line vty 0 15
accounting exec default
transport input all
D. !
config t
username test1 password testpass1
enable secret level 1 0 Test123
line vty 0 15
login authentication
password Test123
transport input telnet
How does CAPWAP communicate between an access point in local mode and a WLC?
A. The access point must not be connected to the wired network, as it would create a loop
B. The access point must be connected to the same switch as the WLC
C. The access point must directly connect to the WLC using a copper cable
D. The access point has the ability to link to any switch in the network, assuming connectivity to the WLC
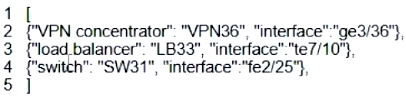
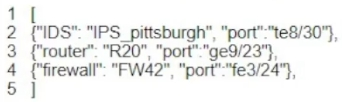
What is represented by the word "ge3/36" within this JSON schema?
A. value
B. array
C. object
D. key
Refer to the exhibit. The entire MAC address table for SW1 is shown here:
What does SW1 do when Br-4 sends a frame for Br-2
A. It performs a lookup in the MAC address table for Br-4 and discards toe frame due to a missing entry.
B. It oods the frame out or all ports except on the port where Br-2 is connected.
C. It Inserts the source MAC address and port into the forwarding table and forwards the frame to Br-2.
D. It maps the Layer 2 MAC address for Fa0/3 to the Layer 3 IP address and towards the frame.
A packet is destined for 10.10.1.22. Which static route does the router choose to forward the packet?
A. ip route 10.10.1.0 255.255.255.240 10.10.255.1
B. ip route 10.10.1.20 255.255.255.252 10.10.255.1
C. ip route 10.10.1.16 255.255.255.252 10.10.255.1
D. ip route 10.10.1.20 255.255.255.254 10.10.255.1
Which script paradigm does Puppet use?
A. recipes and cookbooks
B. playbooks and roles
C. strings and marionettes
D. manifests and modules
What is the default port-security behavior on a trunk link?
A. It places the port in the err-disabled state if it learns more than one MAC address.
B. It causes a network loop when a violation occurs.
C. It disables the native VLAN configuration as soon as port security is enabled.
D. It places the port in the err-disabled state after 10 MAC addresses are statically configured.
Refer to the exhibit. Which type of configuration is represented in the output?
A. Ansible
B. JSON
C. Chef
D. Puppet
What is represented by the word "IDS" within this JSON schema?
A. object
B. value
C. array
D. key
What is represented by the word "port" within this JSON schema?
A. value
B. array
C. key
D. object
Drag and drop the statements about device management from the left onto the corresponding types on the right.
Select and Place:

Free Access Full CCNA Practice Test Free Questions
If you’re looking for more CCNA practice test free questions, click here to access the full CCNA practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your CCNA certification journey!