CCNA Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the CCNA certification exam? Kickstart your success with our CCNA Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with CCNA practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free CCNA practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
What is the purpose of an ESSID?
A. It allows multiple access points to provide a common network for client connections.
B. It supports fast roaming features such as 802.11 r, 802.11k, and 802.11v.
C. It serves as the wireless MAC address of the access point.
D. It provides greater security than a standard SSI
E.
Which physical component is distributed among multiple virtual machines running on the same hypervisor?
A. external storage
B. network interfaces
C. backplane network
D. hardware resources
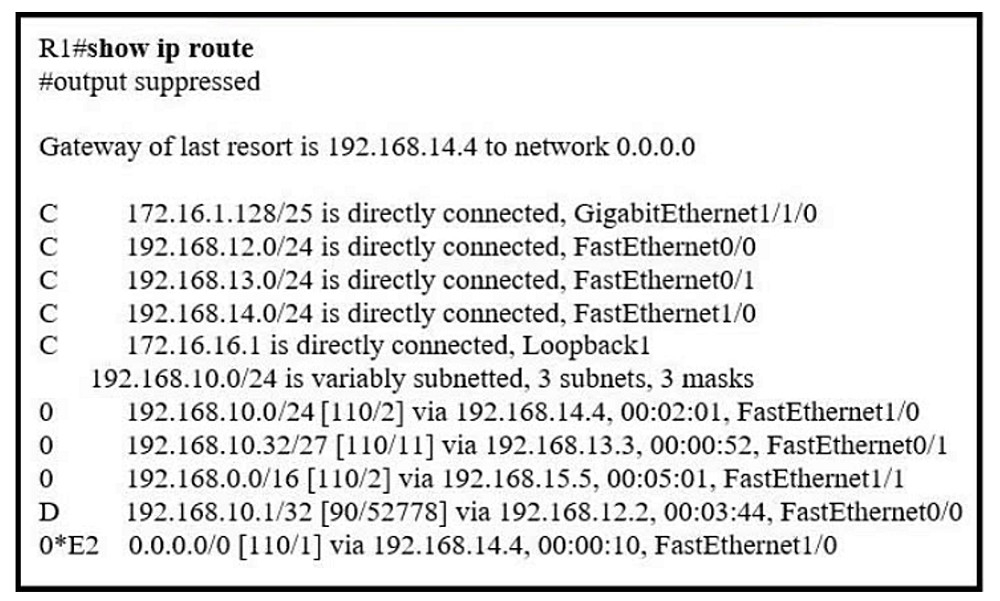
Refer to the exhibit. If R1 receives a packet destined to 172.16.1.1, to which IP address does it send the packet?
A. 192.168.14.4
B. 192.168.12.2
C. 192.168.13.3
D. 192.168.15.5
Refer to the exhibit. Router R14 is in the process of being configured. Which configuration must be used to establish a host route to a PC 10?
A. ip route 10.80.65.10 255.255.255.254 10.80.65.1
B. ip route 10.80.65.10 255.255.255.255 10.73.65.66
C. ip route 10.73.65.66 0.0.0.255 10.80.65.10
D. ip route 10.73.65.66 255.0.0.0 10.80.65.10
Which definition describes JWT in regard to REST API security?
A. an encrypted JSON token that is used for authentication
B. an encrypted JSON token that is used for authorization
C. an encoded JSON token that is used to securely exchange information
D. an encoded JSON token that is used for authentication
Which DSCP per-hop forwarding behavior is divided into subclasses based on drop probability?
A. expedited
B. default
C. assured
D. class-selector
DRAG DROP - Drag and drop the IPv6 address from the left onto the type on the right.
Drag and drop the IPv6 address from the left onto the type on the right.
Select and Place:

A network engineer must configure the router R1 GigabitEthernet1/1 interface to connect to the router R2 GigabitEthernet1/1 interface. For the configuration to be applied, the engineer must compress the address 2001:0db8:0000:0000:0500:000a:400F:583
A. Which command must be issued on the interface?
B. ipv6 address 2001::db8:0000::500:a:400F:583B
C. ipv6 address 2001:db8:0::500:a:4F:583B
D. ipv6 address 2001:db8::500:a:400F:583B
E. ipv6 address 2001:0db8::5:a:4F:583B
Which physical component is distributed among multiple virtual machines running on the same hypervisor?
A. external storage
B. network interfaces
C. backplane network
D. hardware resources
Refer to the exhibit. When an administrator executes the show ip route command on router D to view its routing table, which value is displayed for the administrative distance for the route to network 192.168 1.0?
A. 110
B. 120
C. 170
D. 90
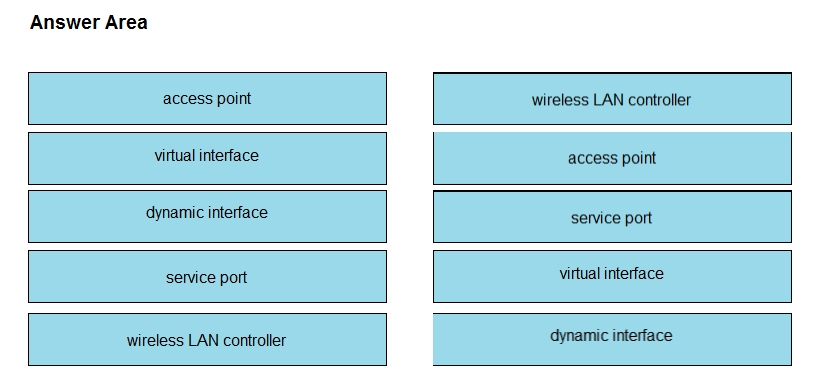
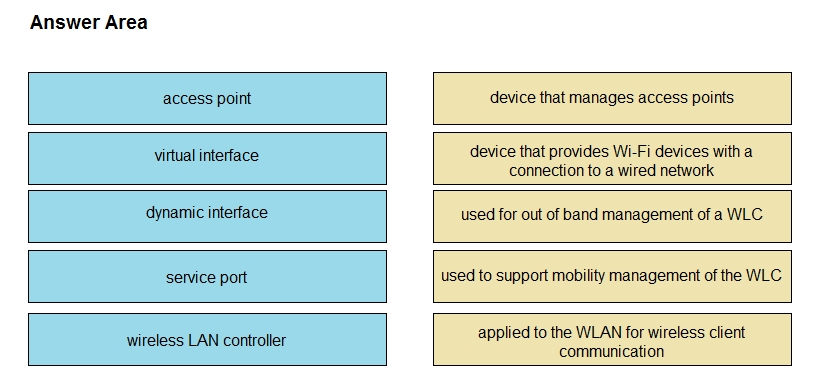
Drag and drop the WLAN components from the left onto the correct descriptions on the right.
Select and Place:
SIMULATION - Guidelines - This is a lab item in which tasks will be performed on virtual devices • Refer to the Tasks tab to view the tasks for this lab item. • Refer to the Topology tab to access the device console(s) and perform the tasks. • Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window. • All necessary pre-configurations have been applied. • Do not remove any existing configurations from the devices, only those necessary to make the appropriate changes required to fulfill the listed tasks. • Do not change the enable password or hostname for any device. • Save your configurations to NVRAM before moving to the next item. • Click Next at the bottom of the screen to submit this lab and move to the next question. • When Next is clicked, the lab closes and cannot be reopened. Topology -Tasks - Task 1 - • Configure a host route on R5 for the destination of 10.200.220.6. • Configure a static default route on R1 preferring the path through R3 towards R6. • From R5, use traceroute and ping to verify the path towards and reachability of R6. Task 2 - • Configure a floating static default route on R1, preferring the path through R2 towards R6 if the link to R3 should fail. • Configure the administrative distance for 225. • Configure a static route on R2 to forward the return traffic towards 10.100.110.0/25. • After shutting interface e0/1 on R1, use traceroute and ping from R5 to verify path towards and reachability of R6.
What is the primary purpose of a First Hop Redundancy Protocol?
A. It allows directly connected neighbors to share configuration information
B. It reduces routing failures by allowing Layer 3 load balancing between OSPF neighbors that have the same link metric
C. It allows a router to use bridge priorities to create multiple loop-free paths to a single destination
D. It reduces routing failures by allowing more than one router to represent itself as the default gateway of a network
What are two differences between optical- fiber cabling and copper cabling? (Choose two.)
A. A BNC connector is used for fiber connections
B. The glass core component is encased in a cladding
C. The data can pass through the cladding
D. Light is transmitted through the core of the fiber
E. Fiber connects to physical interfaces using RJ-45 connections
What is a function of Cisco Advanced Malware Protection for a Next-Generation IPS?
A. inspecting specific files and file types for malware
B. authorizing potentially compromised wireless traffic
C. authenticating end users
D. URL filtering
Which WAN topology provides a combination of simplicity quality, and availability?
A. partial mesh
B. full mesh
C. point-to-point
D. hub-and-spoke
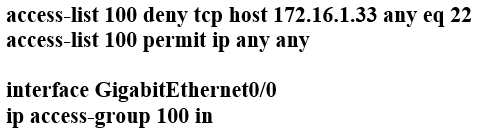
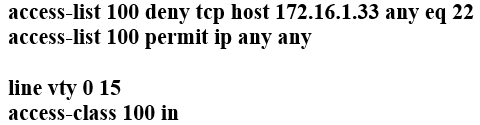
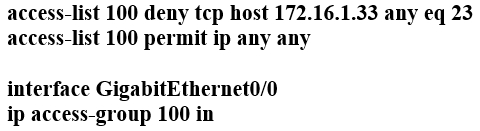
Refer to the exhibit. Which configuration for RTR-1 denies SSH access from PC-1 to any RTR-1 interface and allows all other traffic?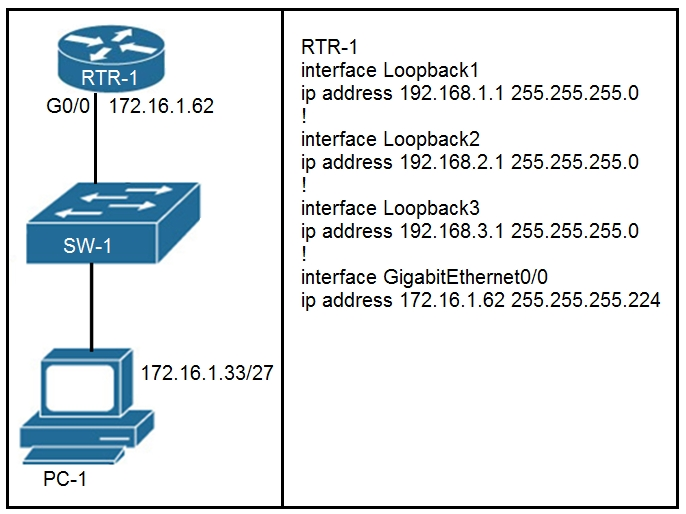
What are the two functions of SSIDs? (Choose two.)
A. uses the maximum of 32 alphanumeric characters
B. controls the speed of the Wi-Fi network
C. used exclusively with controller-based Wi-Fi networks
D. supports a single access point
E. broadcasts by default
The SSID is a unique identifier that wireless networking devices use to establish and maintain wireless connectivity. The SSID can consist of up to 32 alphanumeric, case-sensitive, characters. Wireless clients connect using the SSID for secure communications. The SSID is a unique token that identifies an
802.11 wireless network. It is used by wireless devices to identify a network and to establish and maintain wireless connectivity. An SSID must be configured and assigned to a wireless client device interface before the device can associate with an access point.
Which Layer 2 switch function encapsulates packets for different VLANs so that the packets transverse the same port and maintain traffic separation between the VLANs?
A. VLAN marking
B. VLAN numbering
C. VLAN DSCP
D. VLAN tagging
What is the primary purpose of private address space?
A. limit the number of nodes reachable via the Internet
B. simplify the addressing in the network
C. conserve globally unique address space
D. reduce network complexity
An office has 8 floors with approximately 30-40 users per floor. One subnet must be used. Which command must be configured on the router Switched Virtual Interface to use address space efficiently?
A. ip address 192.168.0.0 255.255.0.0
B. ip address 192.168.0.0 255.255.254.0
C. ip address 192.168.0.0 255.255.255.128
D. ip address 192.168.0.0 255.255.255.224
Which two functions are performed by the core layer in a three-tier architecture? (Choose two.)
A. Provide uninterrupted forwarding service
B. Inspect packets for malicious activity
C. Ensure timely data transfer between layers
D. Provide direct connectivity for end user devices
E. Police traffic that is sent to the edge of the network
Which two circumstances can prevent two routers from establishing an OSPF neighbor adjacency? (Choose two.)
A. mismatched autonomous system numbers
B. an ACL blocking traffic from multicast address 224.0.0.10
C. mismatched process IDs
D. mismatched hello timers and dead timers
E. use of the same router ID on both devices
A Cisco engineer at a new branch office is configuring a wireless network with access points that connect to a controller that is based at corporate headquarters. Wireless client traffic must terminate at the branch office and access-point survivability is required in the event of a WAN outage. Which access point mode must be selected?
A. Lightweight with local switching disabled
B. FlexConnect with local switching enabled
C. officeExtend with high availability disabled
D. Local with AP fallback enabled
Drag and drop the Ansible terms from the left onto the right.
Select and Place:

An email user has been lured into clicking a link in an email sent by their company's security organization. The webpage that opens reports that it was safe, but the link may have contained malicious code. Which type of security program is in place?
A. user awareness
B. brute force attack
C. physical access control
D. social engineering attack
This is a training program which simulates an attack, not a real attack (as it says The webpage that opens reports that it was safe ) so we believed it should be called a user awareness program. Therefore the best answer here should be user awareness . This is the definition of User awareness from CCNA 200-301
O cal Cert Guide Book:
User awareness: All users should be made aware of the need for data confidentiality to protect corporate information, as well as their own credentials and personal information. They should also be made aware of potential threats, schemes to mislead, and proper procedures to report security incidents.
Note: Physical access control means infrastructure locations, such as network closets and data centers, should remain securely locked.
What is a characteristic of cloud-based network topology?
A. onsite network services are provided with physical Layer 2 and Layer 3 components
B. wireless connections provide the sole access method to services
C. physical workstations are configured to share resources
D. services are provided by a public, private, or hybrid deployment
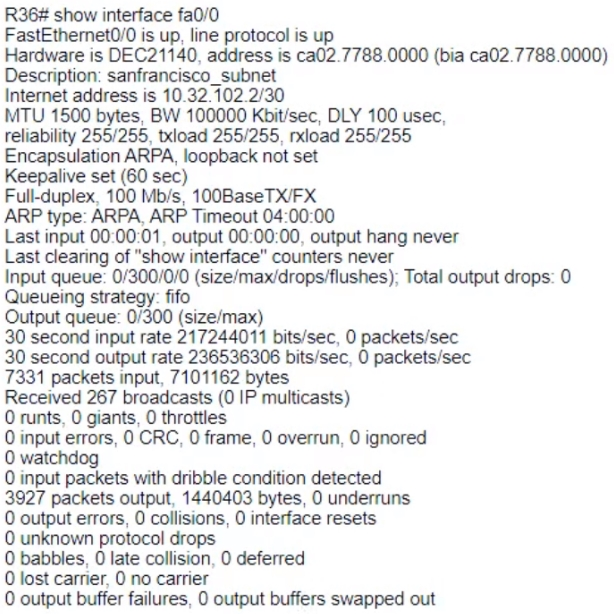
Which interface condition is occurring in this output?
A. duplex mismatch
B. high throughput
C. bad NIC
D. broadcast storm
How will Link Aggregation be implemented on a Cisco Wireless LAN Controller?
A. The EtherChannel must be configured in mode active .
B. When enabled, the WLC bandwidth drops to 500 Mbps.
C. To pass client traffic, two or more ports must be configured.
D. One functional physical port is needed to pass client traffic.
Which global command encrypts all passwords in the running configuration?
A. service password-encryption
B. enable password-encryption
C. enable secret
D. password-encrypt
Which mode must be used to configure EtherChannel between two switches without using a negotiation protocol?
A. active
B. on
C. auto
D. desirable
The Static Persistence (or on mode) bundles the links unconditionally and no negotiation protocol is used. In this mode, neither PAgP nor LACP packets are sent or received.
What prevents a workstation from receiving a DHCP address?
A. STP
B. VTP
C. 802.1Q
D. DTP
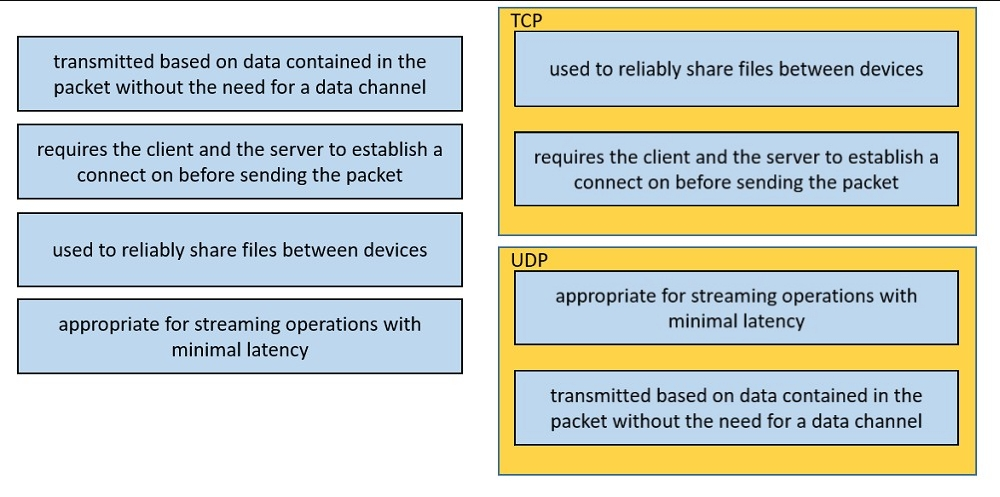
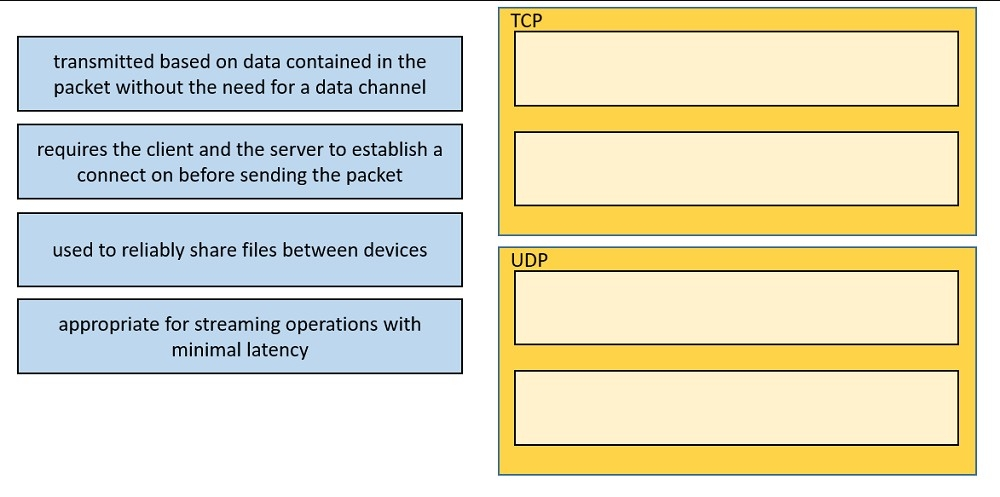
Drag and drop the TCP or UDP details from the left onto their corresponding protocols on the right.
Select and Place:
Which two events occur automatically when a device is added to Cisco DNA Center? (Choose two.)
A. The device is placed into the Managed state.
B. The device is placed into the Unmanaged state.
C. The device is assigned to the Local site.
D. The device is assigned to the Global site.
E. The device is placed into the Provisioned state.
Router A learns the same route from two different neighbors; one of the neighbor routers is an OSPF neighbor, and the other is an EIGRP neighbor. What is the administrative distance of the route that will be installed in the routing table?
A. 20
B. 90
C. 110
D. 115
The Administrative distance (AD) of EIGRP is 90 while the AD of OSPF is 110 so EIGRP route will be chosen to install into the routing table.
Which type of wireless encryption is used for WPA2 in preshared key mode?
A. AES-128
B. TKIP with RC4
C. AES-256
D. RC4
Refer to the exhibit. Which path is used by the router for Internet traffic?
A. 209.165.200.0/27
B. 0.0.0.0/0
C. 10.10.13.0/24
D. 10.10.10.0/28
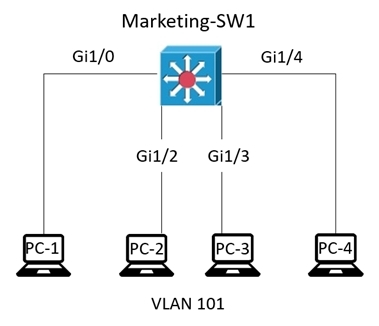
Refer to the exhibit. The entire Marketing-SW1 MAC address table is shown here: What does the switch do when PC-4 sends a frame to PC-1?
A. It performs a lookup in the MAC address table and discards the frame due to a missing entry.
B. It maps the Layer 2 MAC address to the Layer 3 IP address and forwards the frame.
C. It inserts the source MAC address and port into the table and forwards the frame to PC-1.
D. It oods the frame out of all ports except on the port where PC-1 is connected.
Refer to the exhibit. PC A is communicating with another device at IP address 10.227.151.255. Through which router does router Y route the traffic?
A. router A
B. router B
C. router C
D. router D
Which protocol prompts the Wireless LAN Controller to generate its own local web administration SSL certificate for GUI access?
A. RADIUS
B. HTTPS
C. TACACS+
D. HTTP
SIMULATION -R1 has been pre-configured with all the necessary commands. All physical cabling is in place and verified. Connectivity to the end devices must be configured. 1. Configure SW-1 switch port 0/1 to carry traffic for the Cisco IP phone and PC 2. Configure SW-2 E0/1 to carry traffic for PC2 3. Configure VLAN 10 with the name “Engineering” on SW-1 4. Configure the link between SW-1 and SW-2 to use the vendor neutral neighbor discovery protocol 5. Configure the link on SW-1 to R1 so that it does not allow the Cisco neighbor discovery protocol to pass
Refer to the exhibit. A network technician is asked to design a small network with redundancy. The exhibit represents this design, with all hosts configured in the same VLAN. What conclusions can be made about this design?
A. This design will function as intended.
B. Spanning-tree will need to be used.
C. The router will not accept the addressing scheme.
D. The connection between switches should be a trunk.
E. The router interfaces must be encapsulated with the 802.1Q protocol.
Each interface on a router must be in a different network. If two interfaces are in the same network, the router will not accept it and show error when the administrator assigns it.
Refer to the exhibit. An IPv6 address must be obtained automatically on the LAN interface on R1. Which command must be implemented to accomplish the task?
A. ipv6 address autocontig
B. ipv6 address dhcp
C. ipv6 address fe80::/10
D. ipv6 address 2001:db8:d8d2:1008:4332:45:0570::/64
A Cisco engineer notices that two OSPF neighbors are connected using a crossover Ethernet cable. The neighbors are taking too long to become fully adjacent. Which command must be issued under the interface configuration on each router to reduce the time required for the adjacency to reach the FULL state?
A. ip ospf dead-interval 40
B. ip ospf network broadcast
C. ip ospf priority 0
D. ip ospf network point-to-point
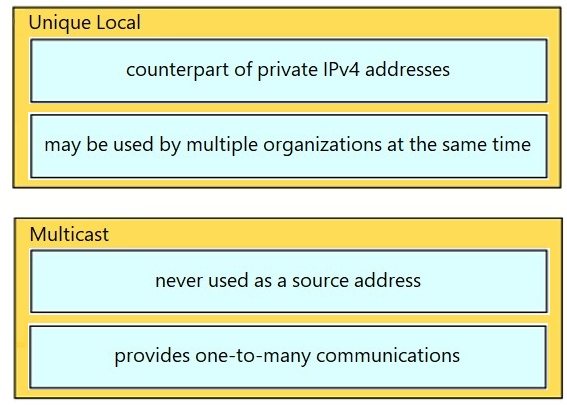
Drag and drop the characteristic from the left onto the IPv6 address type on the right.
Select and Place:
A WLC sends alarms about a rogue AP, and the network administrator verifies that the alarms are caused by a legitimate autonomous AP. How must the alarms be stopped for the MAC address of the AP?
A. Remove the AP from WLC management
B. Place the AP into manual containment.
C. Manually remove the AP from Pending state.
D. Set the AP Class Type to Friendly.
What is the purpose of the service-set identifier?
A. It identifies the wireless network to which an application must connect.
B. It identifies the wired network to which a network device is connected.
C. It identifies the wired network to which a user device is connected.
D. It identifies a wireless network for a mobile device to connect.
Which device protects an internal network from the Internet?
A. router
B. firewall
C. access point
D. Layer 2 switch
Refer to the exhibit. Which type of JSON data is shown?
A. Boolean
B. string
C. object
D. sequence
Free Access Full CCNA Practice Questions Free
Want more hands-on practice? Click here to access the full bank of CCNA practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your CCNA certification journey!