CCNA Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the CCNA certification? Take your preparation to the next level with our CCNA Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a CCNA practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic CCNA practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
Which type of traffic is sent with pure IPsec?
A. multicast traffic from a server at one site to hosts at another location
B. broadcast packets from a switch that is attempting to locate a MAC address at one of several remote sites
C. unicast messages from a host at a remote site to a server at headquarters
D. spanning-tree updates between switches that are at two different sites
Refer to the exhibit. What must be configured to enable 802.11w on the WLAN?
A. Set Fast Transition to Enabled.
B. Enable WPA Policy.
C. Set PMF to Required.
D. Enable MAC Filtering.
Which technology is used to improve web traffic performance by proxy caching?
A. WSA
B. Firepower
C. ASA
D. FireSIGHT
Which technology is appropriate for communication between an SDN controller end applications running over the network?
A. Southbound API
B. REST API
C. NETCONF
D. OpenFlow
What is the purpose of using First Hop Redundancy Protocol on a specific subnet?
A. forwards multicast hello messages between routers
B. sends the default route to the hosts on a network
C. ensures a loop-free physical topology
D. lters traffic based on destination IP addressing
The routers in the FHRP group share a virtual MAC and Virtual IP and that acts as the Default Gateway for the HOSTS. It provides redundancy is case a router fails, no need to change the default gateway information.
Refer to the exhibit. The network engineer is confining router R2 as a replacement router on the network. After the initial configuration is applied, it is determined that R2 failed to show R1 as a neighbor. Which configuration must be applied to R2 to complete the OSPF configuration and enable it to establish the neighbor relationship with R1?
A. R2(config)#interface g0/0/0 -R2(config-if)#ip ospf hello-interval 10
B. R2(config)#router ospf 1 -R2(config-router)#router-id 192.168.1.1
C. R2(config)#router ospf 1 -R2(config-router)#network 192.168.1.0 255.255.255.0 area 2
D. R2(config)#interface g0/0/0 -R2(config-if)#ip ospf dead-interval 45
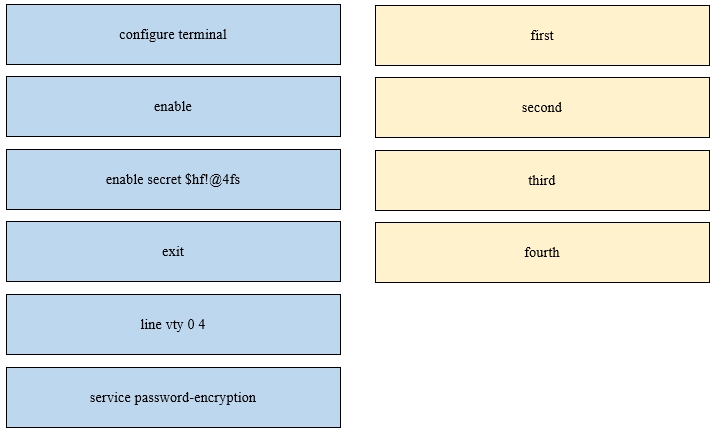
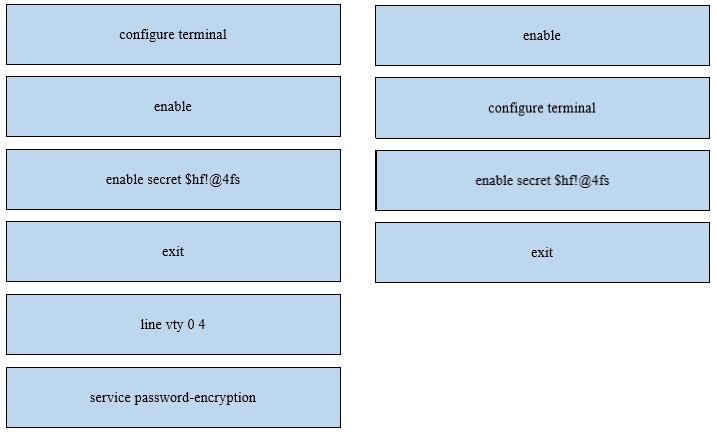
An engineer is configuring an encrypted password for the enable command on a router where the local user database has already been configured. Drag and drop the configuration commands from the left into the correct sequence on the right. Not all commands are used.
Select and Place:
What does a switch do when it receives a frame whose destination MAC address is missing from the MAC address table?
A. It changes the checksum of the frame to a value that indicates an invalid frame.
B. It updates the CAM table with the destination MAC address of the frame.
C. It appends the table with a static entry for the MAC and shuts down the port.
D. It oods the frame unchanged across all remaining ports in the incoming VLAN.
What is a characteristic of frame switching?
A. performs a lookup to learn the destination interface
B. disabled by default on all interfaces and VLANs
C. buffers and forwards frames with less than 5 CRCs
D. protects against denial of service attacks
Refer to the exhibit. What is the metric for the route to the 192.168.10.33 host?
A. 84
B. 110
C. 192
D. 193
Which per-hop traffic-control feature does an ISP implement to mitigate the potential negative effects of a customer exceeding its committed bandwidth?
A. policing
B. queuing
C. marking
D. shaping
What is a characteristic of cloud-based network topology?
A. onsite network services are provided with physical Layer 2 and Layer 3 components
B. wireless connections provide the sole access method to services
C. physical workstations are configured to share resources
D. services are provided by a public, private, or hybrid deployment
What is the benefit of configuring PortFast on an interface?
A. The frames entering the interface are marked with the higher priority and then processed faster by a switch.
B. After the cable is connected, the interface is available faster to send and receive user data.
C. Real-time voice and video frames entering the interface are processed faster.
D. After the cable is connected, the interface uses the fastest speed setting available for that cable type.
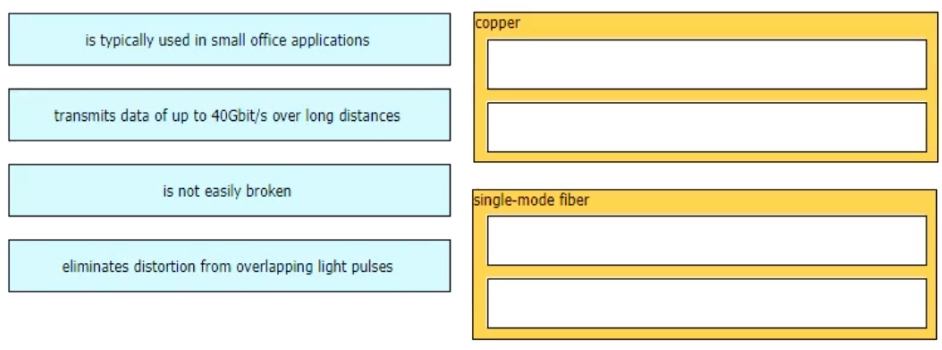
Drag and drop the characteristic from the left onto the cable type on the right.
Select and Place:
Which type of security program is violated when a group of employees enters a building using the ID badge of only one person?
A. intrusion detection
B. network authorization
C. physical access control
D. user awareness
A network engineer is installing an IPv6-only capable device. The client has requested that the device IP address be reachable only from the internal network. Which type of IPv6 address must the engineer assign?
A. IPv4-compatible IPv6 address
B. unique local address
C. link-local address
D. aggregatable global address
Refer to the exhibit. An architect is managing a wireless network with APs from several branch offices connecting to the WLC in the data center. There is a new requirement for a single WLAN to process the client data traffic without sending it to the WL
A. Which action must be taken to complete the request?
B. Enable local HTTP pro ling.
C. Enable FlexConnect Local Switching.
D. Enable local DHCP Pro ling.
E. Enable Disassociation Imminent.
What does WPA3 provide in wireless networking?
A. backward compatibility with WPA and WPA2
B. safeguards against brute force attacks with SAE
C. increased security and requirement of a complex configuration
D. optional Protected Management Frame negotiation
Refer to the exhibit. The New York router is configured with static routes pointing to the Atlanta and Washington sites. Which two tasks must be performed so that the Se0/0/0 interfaces on the Atlanta and Washington routers reach one another? (Choose two.)
A. configure the ipv6 route 2023::/126 2012::1 command on the Atlanta router.
B. configure the ipv6 route 2012::/126 2023::2 command on the Washington router.
C. configure the ipv6 route 2012::/126 2023::1 command on the Washington router.
D. configure the ipv6 route 2023::/126 2012::2 command on the Atlanta router.
E. configure the ipv6 route 2012::/126 s0/0/0 command on the Atlanta router.
Refer to the exhibit. A newly configured PC fails to connect to the internet by using TCP port 80 to www.cisco.com. Which setting must be modified for the connection to work?
A. Subnet Mask
B. DNS Servers
C. Default Gateway
D. DHCP Servers
Refer to the exhibit. Which configuration enables DHCP addressing for hosts connected to interface FastEthernet0/1 on router R3?
A. interface FastEthernet0/1
ip helper-address 10.0.1.1
access-list 100 permit tcp host 10.0.1.1 eq 67 host 10.148.2.1
B. interface FastEthernet0/1
ip helper-address 10.0.1.1
access-list 100 permit udp host 10.0.1.1 eq 67 host 10.148.2.1
C. interface FastEthernet0/0
ip helper-address 10.0.1.1
access-list 100 permit host 10.0.1.1 host 10.148.2.1 eq bootps
D. interface FastEthernet0/1
ip helper-address 10.0.1.1
access-list 100 permit udp host 10.0.1.1 eq bootps host 10.148.2.1
Refer to the exhibit. If OSPF is running on this network, how does Router2 handle traffic from Site B to 10.10.13.128/25 at Site A?
A. It sends packets out of interface Fa0/1.
B. It sends packets out of interface Fa0/2.
C. It load-balances traffic out of Fa0/1 and Fa0/2.
D. It is unreachable and discards the traffic.
Drag and drop the characteristics of a cloud environment from the left onto the correct examples on the right.
Select and Place:

SW1 supports connectivity for a lobby conference room and must be secured. The engineer must limit the connectivity from PC1 to the SW1 and SW2 network. The MAC addresses allowed must be limited to two. Which configuration secures the conference room connectivity?
A. interface gi1/0/15 switchport port-security switchport port-security maximum 2
B. interface gi1/0/15 switchport port-security switchport port-security mac-address 0000.abcd.0004vlan 100
C. interface gi1/0/15 switchport port-security mac-address 0000.abcd.0004 vlan 100
D. interface gi1/0/15 switchport port-security mac-address 0000.abcd.0004 vlan 100 interface switchport secure-mac limit 2 A
What are two features of the DHCP relay agent? (Choose two.)
A. assigns DNS locally and then forwards request to DHCP server
B. minimizes the necessary number of DHCP servers
C. permits one IP helper command under an individual Layer 3 interface
D. is configured under the Layer 3 interface of a router on the client subnet
E. allows only MAC-to-IP reservations to determine the local subnet of a client
What is represented by the word "LB13" within this JSON schema?
A. array
B. value
C. object
D. key
Drag and drop the commands from the left onto the destination interfaces on the right. Not all commands are used.
Select and Place:
Which Cisco IOS command will indicate that interface GigabitEthernet 0/0 is configured via DHCP?
A. show ip interface GigabitEthernet 0/0 dhcp
B. show interface GigabitEthernet 0/0
C. show ip interface dhcp
D. show ip interface GigabitEthernet 0/0
E. show ip interface GigabitEthernet 0/0 brief
What is represented by the word "switch" within this JSON schema?
A. key
B. object
C. array
D. value
An engineer must establish a trunk link between two switches. The neighboring switch is set to trunk or desirable mode. What action should be taken?
A. configure switchport nonegotiate
B. configure switchport mode dynamic desirable
C. configure switchport mode dynamic auto
D. configure switchport trunk dynamic desirable
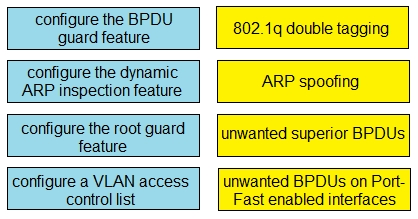
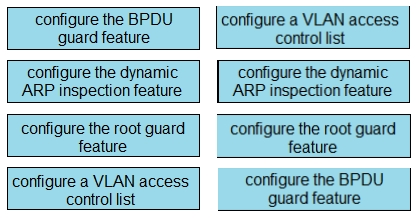
Drag and drop the threat mitigation techniques from the left onto the types of threat or attack they mitigate on the right.
Select and Place:
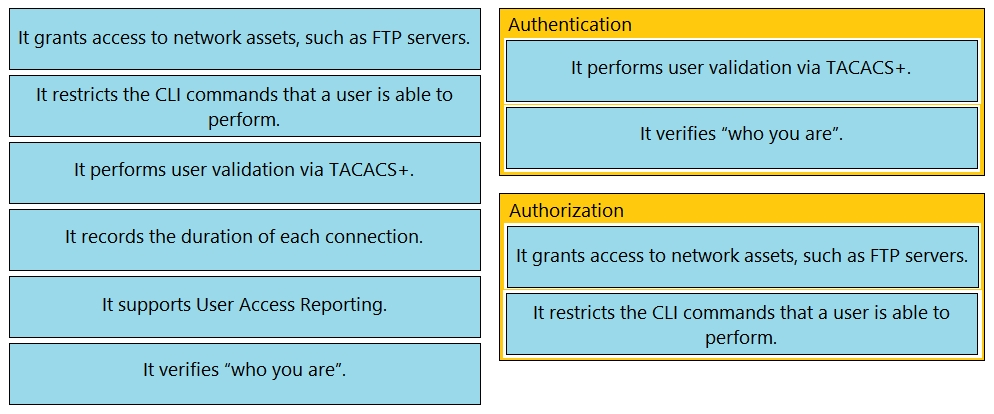
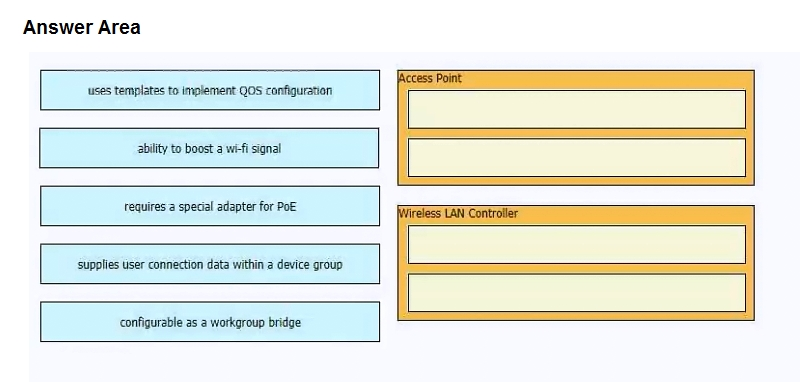
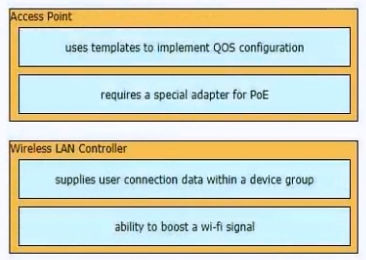
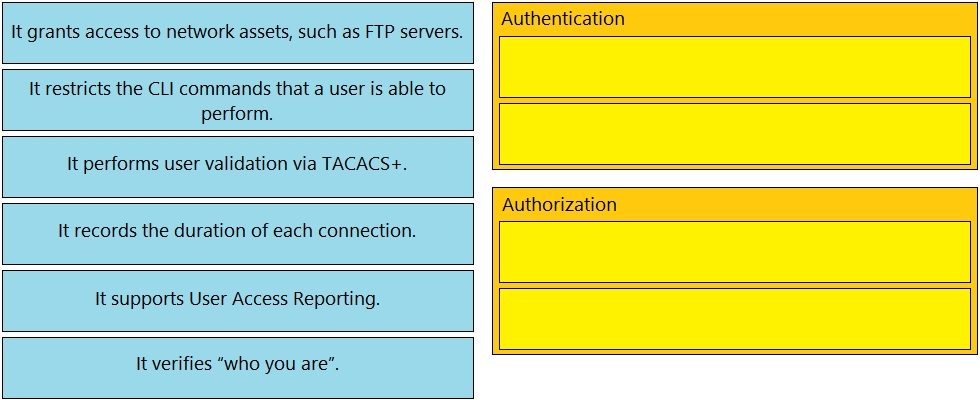
Drag and drop the statements about AAA services from the left to the corresponding AAA services on the right. Not all options are used.
Select and Place:
Refer to the exhibit. Which path is used by the router for Internet traffic?
A. 209.165.200.0/27
B. 0.0.0.0/0
C. 10.10.13.0/24
D. 10.10.10.0/28
A user configured OSPF and advertised the Gigabit Ethernet interface in OSP
A. By default, to which type of OSPF network does this interface belong?
B. point-to-multipoint
C. point-to-point
D. broadcast
E. nonbroadcast
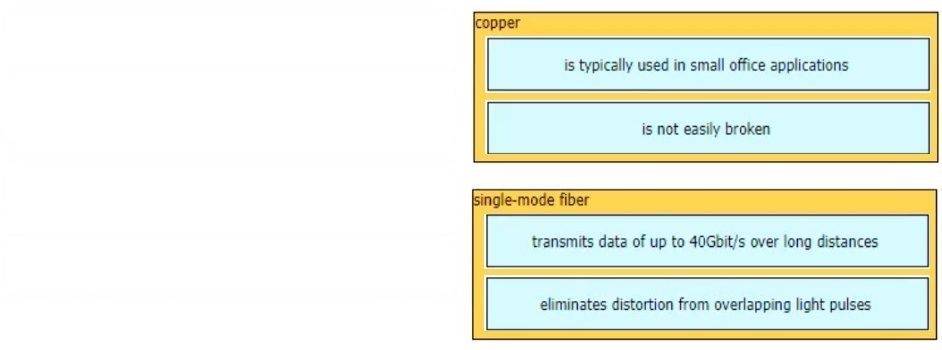
What are two facts that differentiate optical- fiber cabling from copper cabling? (Choose two.)
A. It is less expensive when purchasing patch cables.
B. It carries electrical current further distances for PoE devices.
C. It provides greater throughput options.
D. It has a greater sensitivity to changes in temperature and moisture.
E. It carries signals for longer distances.
Which command prevents passwords from being stored in the configuration as plain text on a router or switch?
A. enable secret
B. enable password
C. service password-encryption
D. username cisco password encrypt
After installing a new Cisco ISE server which task must the engineer perform on the Cisco WLC to connect wireless clients on a specific VLAN based on their credentials?
A. Disable the LAG Mode on Next Reboot.
B. Enable the Event Driven RRM.
C. Enable the Allow AAA Override.
D. Enable the Authorize MIC APs against auth-list or AAA
What is the function of a controller in controller-based networking?
A. It serves as the centralized management point of an SDN architecture
B. It is a pair of core routers that maintain all routing decisions for a campus
C. It centralizes the data plane for the network
D. It is the card on a core router that maintains all routing decisions for a campus.
Refer to the exhibit. VoIP is being implemented in the network using VLAN ID 73 and named "VoIP". Each user needs a Cisco IP phone at their desk. Switchport e0/0 has been configured as an access port in the data VLAN. Cisco Discovery Protocol is enabled globally. Which command sequence completed the configuration?
A. vlan73
name VoIP
e0/0
switchport voice vlan dot1p
B. vlan 73
name VoIP
e0/0
switchport trunk allowed vlan 72,73
switchport voice vlan 73
C. vlan 73
name VoIP
e0/0
switchport mode trunk
channel-group 73 mode active
D. vlan 73
name VoIP
e0/0
switchport voice vlan 73
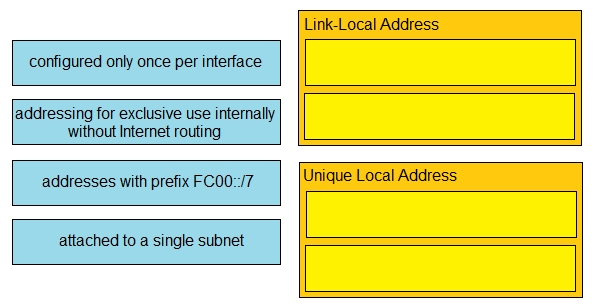
Drag and drop the IPv6 address type characteristics from the left to the right.
Select and Place:

Refer to the exhibit. Which configuration issue is preventing the OSPF neighbor relationship from being established between the two routers?
A. R1 has an incorrect network command for interface Gi1/0.
B. R2 should have its network command in area 1.
C. R1 interface Gi1/0 has a larger MTU size.
D. R2 is using the passive-interface default command.
What is the default port-security behavior on a trunk link?
A. It places the port in the err-disabled state if it learns more than one MAC address.
B. It causes a network loop when a violation occurs.
C. It disables the native VLAN configuration as soon as port security is enabled.
D. It places the port in the err-disabled state after 10 MAC addresses are statically configured.
Refer to the exhibit. The DHCP server and clients are connected to the same switch. What is the next step to complete the DHCP configuration to allow clients on VLAN 1 to receive addresses from the DHCP server?
A. configure the ip dhcp snooping trust command on the interface that is connected to the DHCP client.
B. configure ip dhcp relay information option command on the interface that is connected to the DHCP server.
C. configure ip dhcp snooping trust command on the interface that is connected to the DHCP server.
D. configure the ip dhcp information option command on the interface that is connected to the DHCP client.
Refer to the exhibit. Which switch becomes the root bridge?
A. SW 4 –
Bridge Priority – 49152 –
mac-address 06:8e:bc:7e:5b:85
B. SW 3 –
Bridge Priority – 49152 –
mac-address 0d:e4:96:da:ee:95
C. SW 1 –
Bridge Priority – 36864 –
mac-address 05:a7:23:5b:52:25
D. SW 2 –
Bridge Priority – 36864 –
mac-address 04:1e:c4:bf:02:55
Refer to the exhibit. How many objects are present in the given JSON-encoded data?
A. One
B. Four
C. Seven
D. Nine
A network engineer must migrate a router loopback interface to the IPv6 address space. If the current IPv4 address of the interface is 10.54.73.1/32, and the engineer configures IPv6 address 0:0:0:0:0:ffff:a36:4901, which prefix length must be used?
A. /64
B. /96
C. /124
D. /128
DRAG DROP - Drag and drop the commands from the left onto the destination interfaces on the right. Not all commands are used.
What are two capabilities provided by VRRP within a LAN network? (Choose two.)
A. redundancy
B. granular QoS
C. load sharing
D. dynamic routing updates
E. bandwidth optimization
Refer to the exhibit. With which metric was the route to host 172.16.0.202 learned?
A. 0
B. 110
C. 38443
D. 3184439
What provides centralized control of authentication and roaming in an enterprise network?
A. a lightweight access point
B. a wireless LAN controller
C. a firewall
D. a LAN switch
Free Access Full CCNA Practice Exam Free
Looking for additional practice? Click here to access a full set of CCNA practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your CCNA certification journey!