CCNA Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your CCNA certification exam? Start your preparation the smart way with our CCNA Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for CCNA exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our CCNA Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
An engineer must configure traffic for a VLAN that is untagged by the switch as it crosses a trunk link. Which command should be used?
A. switchport trunk encapsulation dot1q
B. switchport trunk allowed vlan 10
C. switchport mode trunk
D. switchport trunk native vlan 10
Refer to the exhibit. The administrator must configure a floating static default route that points to 2001:db8:1234:2::1 and replaces the current default route only if it fails. Which command must the engineer configure on the CPE?
A. ipv6 route ::/0 2001:db8:1234:2::1 3
B. ipv6 route ::/128 2001:db8:1234:2::1 3
C. ipv6 route ::/0 2001:db8:1234:2::1 1
D. ipv6 route ::/0 2001:db8:1234:2::1 2
What is a function performed by a web server?
A. send and retrieve email from client devices
B. securely store files for FTP access
C. authenticate and authorize a user’s identity
D. provide an application that is transmitted over HTTP
What is a function of spine-and-leaf architecture?
A. offers predictable latency of the traffic path between end devices
B. mitigates oversubscription by adding a layer of leaf switches
C. exclusively sends multicast traffic between servers that are directly connected to the spine
D. limits payload size of traffic within the leaf layer
Refer to the exhibit. A newly configured PC fails to connect to the internet by using TCP port 80 to www.cisco.com. Which setting must be modified for the connection to work?
A. Subnet Mask
B. DNS Servers
C. Default Gateway
D. DHCP Servers
Refer to the exhibit. Users need to connect to the wireless network with IEEE 802.11r-compatible devices. The connection must be maintained as users travel between floors or to other areas in the building. What must be the configuration of the connection?
A. Disable AES encryption.
B. Enable Fast Transition and select the FT 802.1x option.
C. Enable Fast Transition and select the FT PSK option.
D. Select the WPA Policy option with the CCKM option.
Refer to the exhibit. An administrator is tasked with configuring a voice VLAN. What is the expected outcome when a Cisco phone is connected to the GigabitEthernet 3/1/4 port on a switch?
A. The phone and a workstation that is connected to the phone do not have VLAN connectivity.
B. The phone sends and receives data in VLAN 50, but a workstation connected to the phone sends and receives data in VLAN 1.
C. The phone sends and receives data in VLAN 50, but a workstation connected to the phone has no VLAN connectivity.
D. The phone and a workstation that is connected to the phone send and receive data in VLAN 50.
Which two functions are performed by the core layer in a three-tier architecture? (Choose two.)
A. Provide uninterrupted forwarding service
B. Inspect packets for malicious activity
C. Ensure timely data transfer between layers
D. Provide direct connectivity for end user devices
E. Police traffic that is sent to the edge of the network
Which two pieces of information about a Cisco device can Cisco Discovery Protocol communicate? (Choose two.)
A. the native VLAN
B. the trunking protocol
C. the VTP domain
D. the spanning-tree priority
E. the spanning-tree protocol
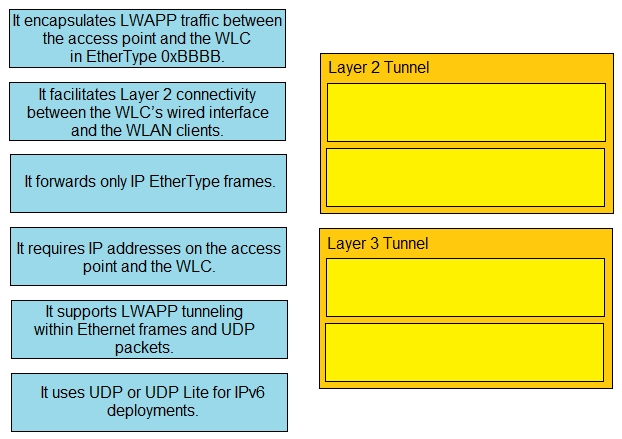
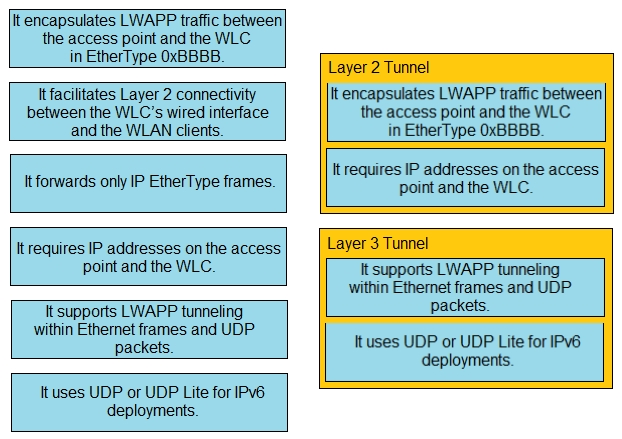
Drag and drop the statements about wireless architectures from the left onto the architectures on the right.
Select and Place:
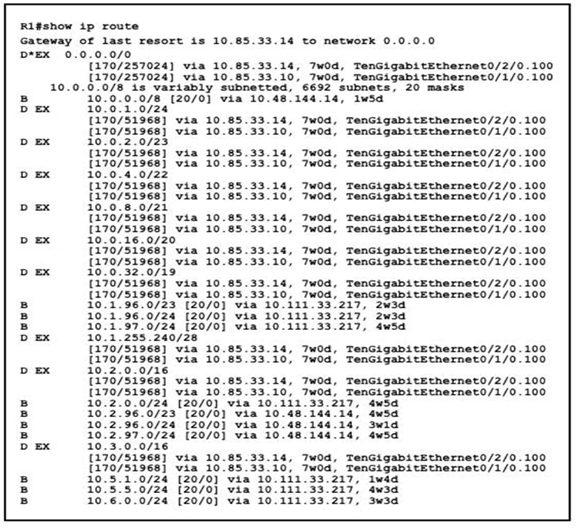
A. The EIGRP administrative distance was manually changed from 90 to 170.
B. There are 20 different network masks within the 10.0.0.0/8 network.
C. Ten routes are equally load-balanced between Te0/1/0.100 and Te0/2/0.100.
D. The 10.0.0.0/8 network was learned via external EIGRP.
E. A static default route to 10.85.33.14 was defined.
Which two HTTP methods are suitable for actions performed by REST-based APIs? (Choose two.)
A. REMOVE
B. REDIRECT
C. POST
D. GET
E. POP
Which protocol should be used to transfer large files on a company intranet that allows TCP 20 and 21 through the firewall?
A. SMTP
B. REST API
C. TFTP
D. FTP
When configuring an EtherChannel bundle, which mode enables LACP only if a LACP device is detected?
A. Passive
B. Desirable
C. On
D. Auto
E. Active
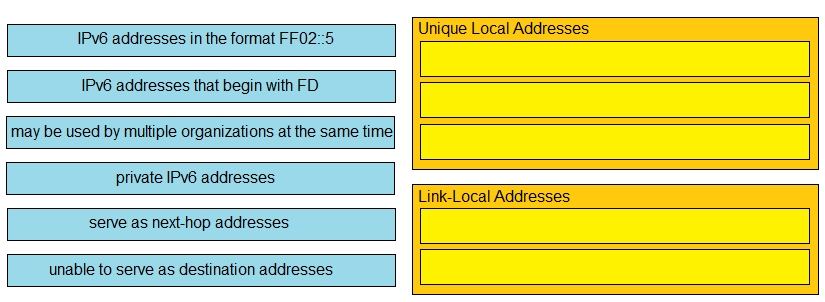
DRAG DROP - Drag and drop the IPv6 address from the left onto the type on the right.
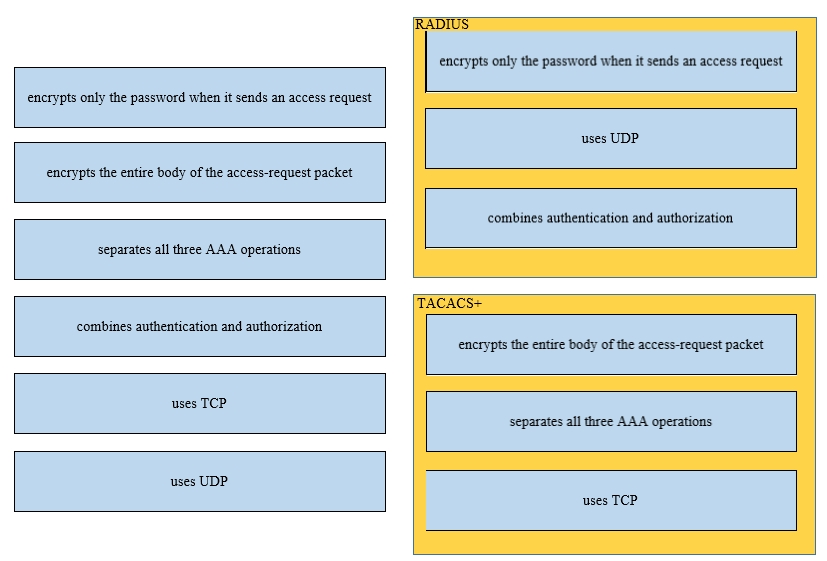
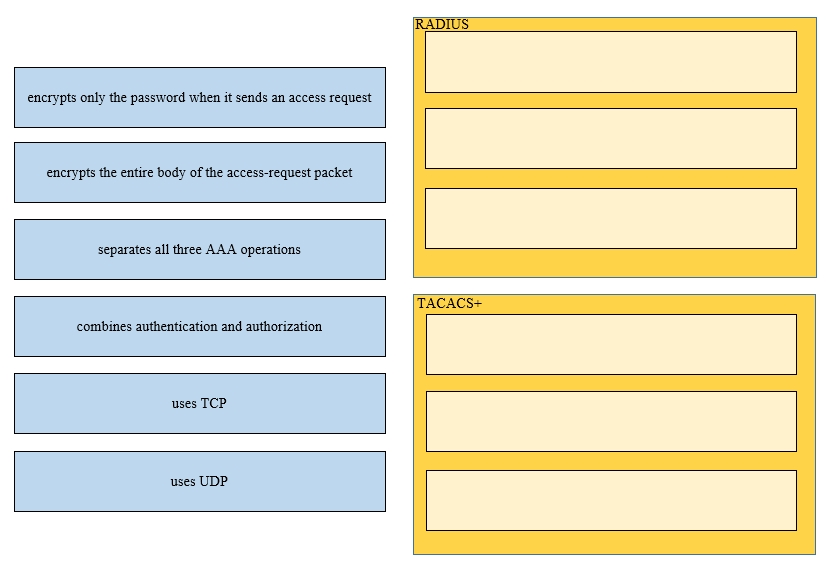
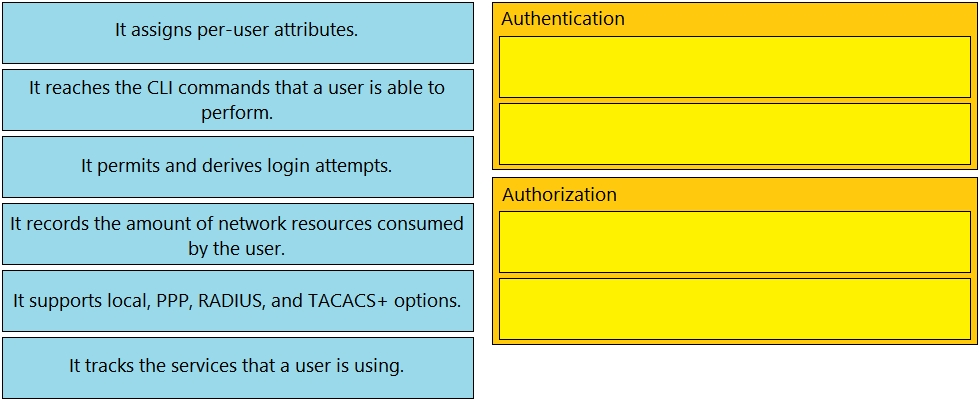
Drag and drop the functions of AAA supporting protocols from the left onto the protocols on the right.
Select and Place:
Refer to the exhibit. Which IPv6 configuration is required for R17 to successfully ping the WAN interface on R18?
A. R17# ! no ip domain lookup ip cef ipv6 cef ! interface FastEthernet0/0 no ip address duplex auto speed auto ipv6 address 2001:DB8:2::201/64 ! Interface FastEthernet1/0 no ip address duplex auto speed auto ipv6 address 2001:DB8:3::201/64 ! no cdp log mismatch duplex ipv6 route 2001:DB8:4::/64 2001:DB8:4::302
B. R17# ! no ip domain lookup ip cef ipv6 unicast-routing ! interface FastEthernet0/0 no ip address duplex auto speed auto ipv6 address 2001:DB8:2::201/64 ! Interface FastEthernet1/0 no ip address duplex auto speed auto ipv6 address 2001:DB8:3::201/64 ! no cdp log mismatch duplex ipv6 route 2001:DB8:4::/64 2001:DB8:3::301
C. R17# ! no ip domain lookup ip cef ! interface FastEthernet0/0 no ip address duplex auto speed auto ipv6 address 2001:DB8:3::201/64 ! Interface FastEthernet1/0 no ip address duplex auto speed auto ipv6 address 2001:DB8:2::201/64 ! no cdp log mismatch duplex ipv6 route 2001:DB8:4::/64 2001:DB8:5::101
D. R17# ! no ip domain lookup ip cef ipv6 unicast-routing ! interface FastEthernet0/0 no ip address duplex auto speed auto ipv6 address 2001:DB8:2::201/64 ! Interface FastEthernet1/0 no ip address duplex auto speed auto ipv6 address 2001:DB8:3::201/64 ! no cdp log mismatch duplex ipv6 route 2001:DB8:4::/64 2001:DB8:2::201
Which value is the unique identifier that an access point uses to establish and maintain wireless connectivity to wireless network devices?
A. VLAN ID
B. SSID
C. RFID
D. WLAN ID
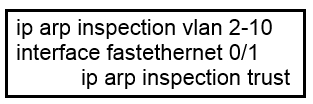
An engineer is asked to protect unused ports that are configured in the default VLAN on a switch. Which two steps will fulfill the request? (Choose two.)
A. configure the ports as trunk ports.
B. Enable the Cisco Discovery Protocol.
C. configure the port type as access and place in VLAN 99.
D. Administratively shut down the ports.
E. configure the ports in an EtherChannel.
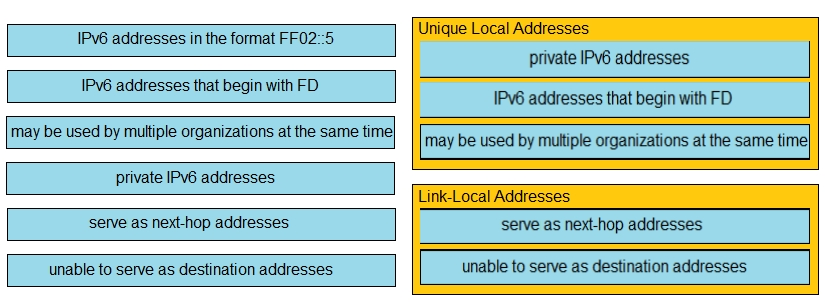
Drag and drop the IPv6 address descriptions from the left onto the IPv6 address types on the right. Not all options are used.
Select and Place:
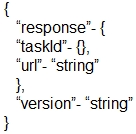
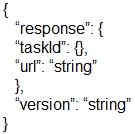
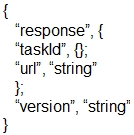
What is represented by the word "port" within this JSON schema?
A. key
B. value
C. array
D. object
What prevents a workstation from receiving a DHCP address?
A. STP
B. VTP
C. 802.1Q
D. DTP
What is a syslog facility?
A. host that is configured for the system to send log messages
B. password that authenticates a Network Management System to receive log messages
C. group of log messages associated with the configured severity level
D. set of values that represent the processes that can generate a log message D
Refer to the exhibit. A network engineer is configuring a wireless LAN with Web Passthrough Layer 3 Web Policy. Which action must the engineer take to complete the configuration?
A. Set the Layer 2 Security to 802.1X.
B. Enable TKIP and CCMP256 WPA2 Encryption.
C. Enable the WPA Policy.
D. Set the Layer 2 Security to None.
Which two protocols are used by an administrator for authentication and configuration on access points? (Choose two.)
A. 802.1Q
B. RADIUS
C. Kerberos
D. TACACS+
E. 802.1x
What is a feature of TFTP?
A. offers anonymous user login ability
B. uses two separate connections for control and data traffic
C. relies on the well-known TCP port 20 to transmit data
D. provides secure data transfer
Refer to the exhibit. PC A is communicating with another device at IP address 10.225.34.225. Through which router does router Y route the traffic?
A. router A
B. router B
C. router C
D. router D
Which command configures the Cisco WLC to prevent a serial session with the WLC CLI from being automatically logged out?
A. config sessions maxsessions 0
B. config serial timeout 9600
C. config serial timeout 0
D. config sessions timeout 0
Refer to the exhibit. An engineer is configuring a new router on the network and applied this configuration. Which additional configuration allows the PC to obtain its IP address from a DHCP server?
A. configure the ip helper-address 172.16.2.2 command under interface Gi0/0.
B. configure the ip dhcp relay information command under interface Gi0/1
C. configure the ip address dhcp command under interface Gi0/0
D. configure the ip dhcp smart-relay command globally on the router.
What does physical access control regulate?
A. access to networking equipment and facilities
B. access to servers to prevent malicious activity
C. access to specific networks based on business function
D. access to computer networks and file systems
Why would an administrator choose to implement an automated network management solution?
A. to reduce operational costs
B. to support simpler password policies
C. to enable “box by box” configuration and deployment
D. to limit recurrent management costs
How does MAC learning function?
A. sends a retransmission request when a new frame is received
B. enabled by default on all VLANs and interfaces
C. populates the ARP table with the egress port
D. protects against denial of service attacks
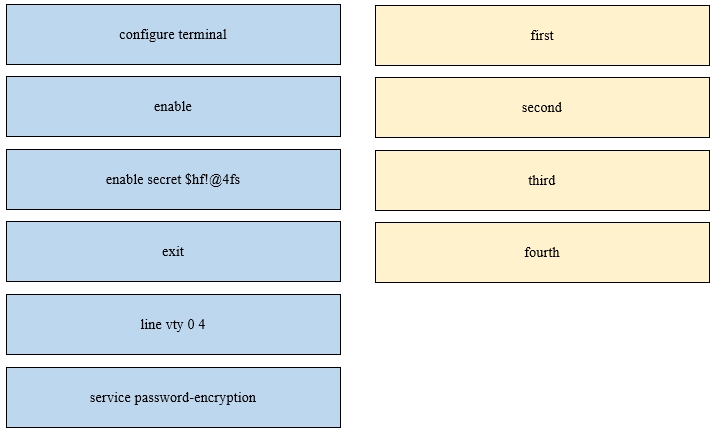
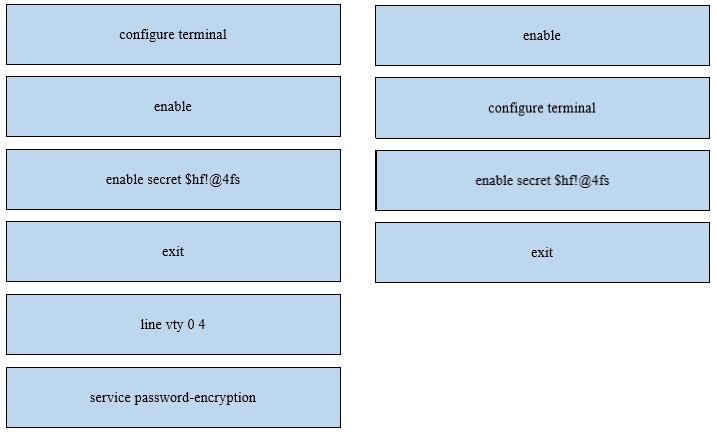
An engineer is configuring an encrypted password for the enable command on a router where the local user database has already been configured. Drag and drop the configuration commands from the left into the correct sequence on the right. Not all commands are used.
Select and Place:
Which plane is centralized in software-defined networking?
A. application
B. services
C. data
D. control
Refer to the exhibit. If the network environment is operating normally, which type of device must be connected to interface fastethernet 0/1?
A. DHCP client
B. access point
C. router
D. PC
Which interface is used to send traffic to the destination network?
A. F0/2
B. F0/20
C. F0/12
D. F0/10
Refer to the exhibit. VoIP is being implemented in the network using VLAN ID 73 and named "VoIP". Each user needs a Cisco IP phone at their desk. Switchport e0/0 has been configured as an access port in the data VLAN. Cisco Discovery Protocol is enabled globally. Which command sequence completed the configuration?
A. vlan73
name VoIP
e0/0
switchport voice vlan dot1p
B. vlan 73
name VoIP
e0/0
switchport trunk allowed vlan 72,73
switchport voice vlan 73
C. vlan 73
name VoIP
e0/0
switchport mode trunk
channel-group 73 mode active
D. vlan 73
name VoIP
e0/0
switchport voice vlan 73
Refer to the exhibit. The network engineer is confining router R2 as a replacement router on the network. After the initial configuration is applied, it is determined that R2 failed to show R1 as a neighbor. Which configuration must be applied to R2 to complete the OSPF configuration and enable it to establish the neighbor relationship with R1?
A. R2(config)#interface g0/0/0 -R2(config-if)#ip ospf hello-interval 10
B. R2(config)#router ospf 1 -R2(config-router)#router-id 192.168.1.1
C. R2(config)#router ospf 1 -R2(config-router)#network 192.168.1.0 255.255.255.0 area 2
D. R2(config)#interface g0/0/0 -R2(config-if)#ip ospf dead-interval 45
What is a characteristic of RSA?
A. It uses preshared keys for encryption.
B. It is a public-key cryptosystem.
C. It is a private-key encryption algorithm.
D. It requires both sides to have identical keys.
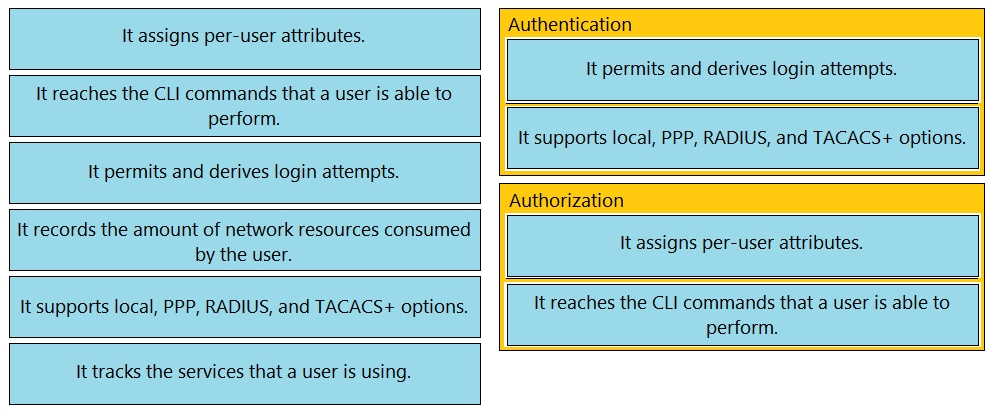
Drag and drop the statements about AAA from the left onto the corresponding AAA services on the right. Not all options are used.
Select and Place:
What is a feature of WPA?
A. TKIP/MIC encryption
B. small Wi-Fi application
C. preshared key
D. 802.1x authentication
Which protocol uses the SSL?
A. SSH
B. HTTPS
C. HTTP
D. Telnet
Drag and drop the IPv6 address from the left onto the type on the right.
Select and Place:

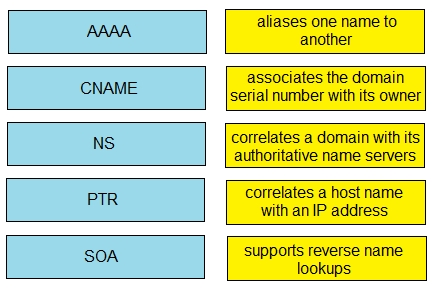
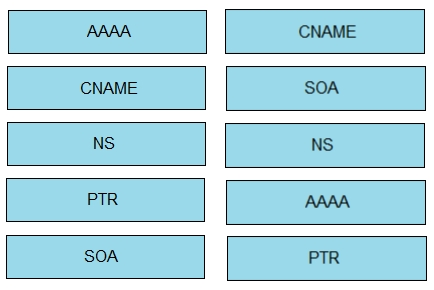
Drag and drop the IPv6 DNS record types from the left onto the description on the right.
Select and Place:
Which step immediately follows receipt of the EAP success message when session resumption is disabled for an EAP-TLS connection?
A. PMKID caching
B. four-way handshake
C. 802.1X authentication
D. EAPOL-key frame
Which two statements about VTP are true? (Choose two.)
A. All switches must be configured with the same VTP domain name
B. All switches must be configured to perform trunk negotiation
C. All switches must be configured with a unique VTP domain name
D. The VTP server must have the highest revision number in the domain
E. All switches must use the same VTP version
Drag and drop the Ansible terms from the left onto the right.
Select and Place:

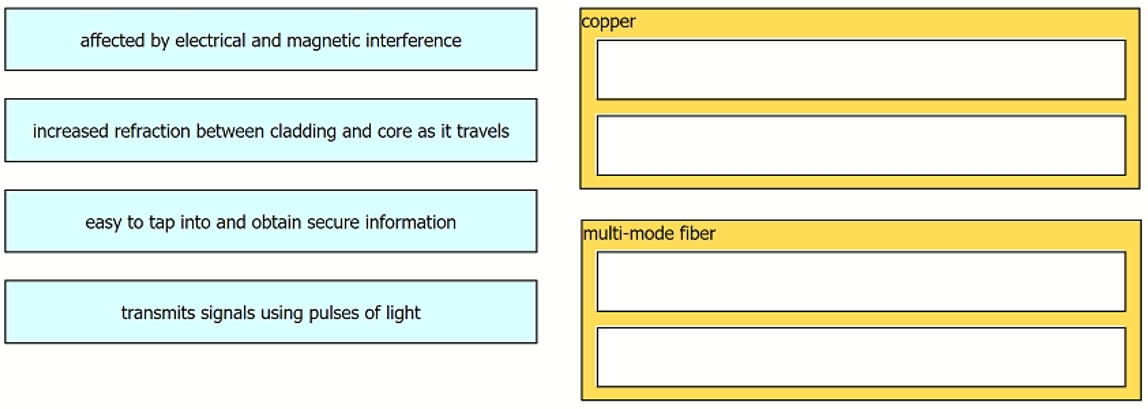
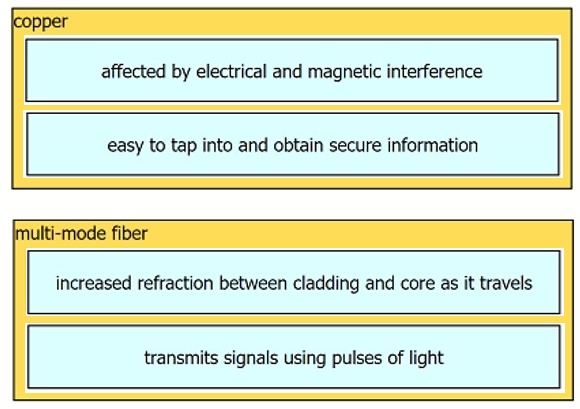
Drag and drop the characteristic from the left onto the cable type on the right.
Select and Place:
Which output displays a JSON data representation?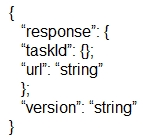
Which switch concept is used to create separate broadcast domains?
A. STP
B. VTP
C. VLAN
D. CSMA/CD
Access Full CCNA Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete CCNA Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our CCNA mock test free today—and take a major step toward exam success!